A Secure and Sustainable Transition from Legacy Smart Cards to Mobile Credentials in University Access Control Systems
Abstract
1. Introduction and Motivation
1.1. Research Questions and Theoretical Framing
- RQ1
- What strategies can be developed to quantitatively evaluate institutional risks arising from legacy RFID credentials and to support secure migration within a multi-vendor (Gallagher–Salto) access ecosystem?
- RQ2
- What system improvements can be achieved through replacing the traditional card-based systems by mobile credentials in the campus environment?
- RQ3
- What sustainability and policy outcomes emerge from a mobile-first credential programme, and how can these outcomes inform institutional ICT decarbonisation and access governance?
1.2. Research Scope and Contribution
- We propose a secure and sustainable university building access control system using a mobile credential. To this end we develop a mobile App to provide building access rights to authorize users such as staff, students, and visitors.
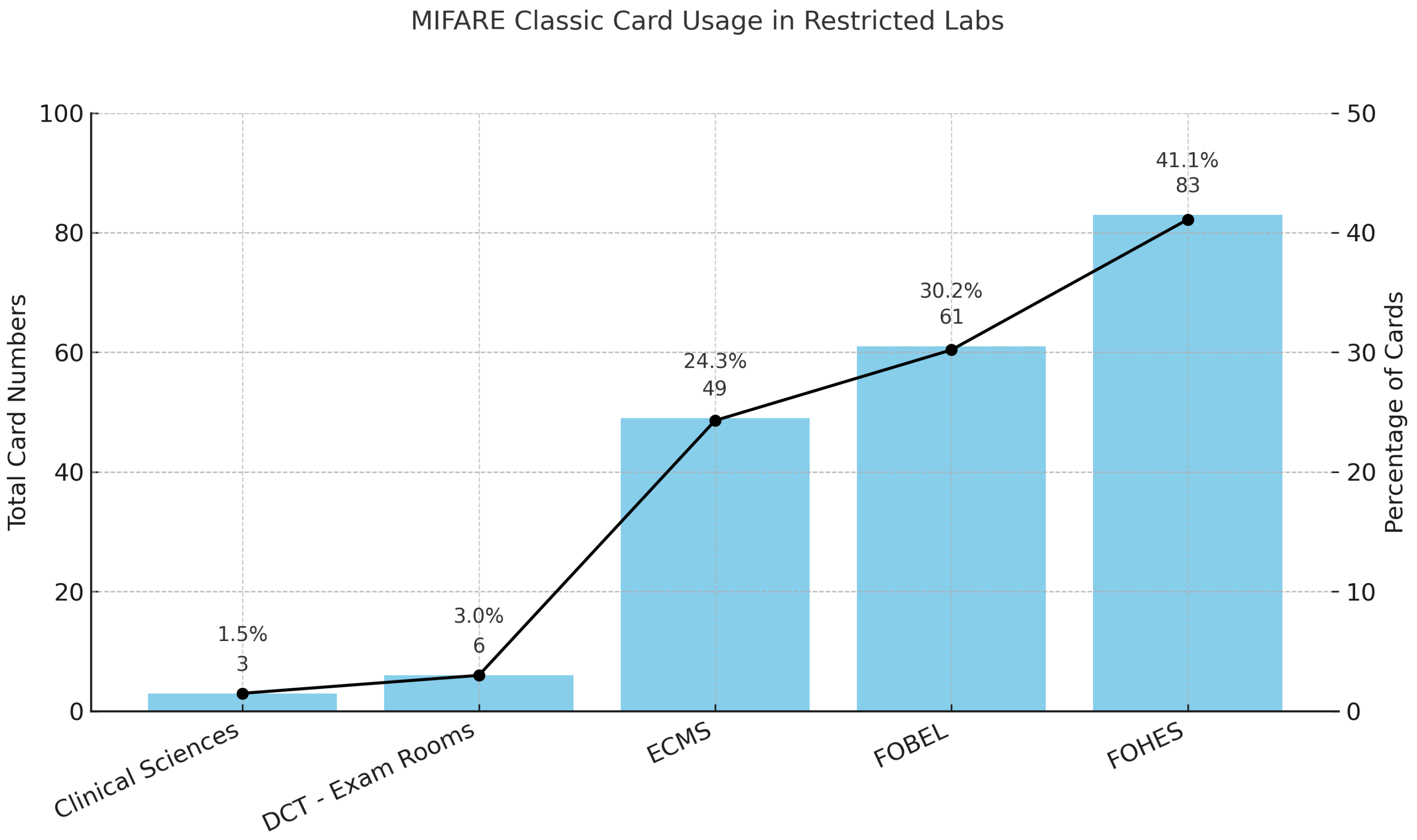
- We conducted risk analysis of the university’s existing infrastructure to map potential operational continuity threats. To this end, we analyse card issuance records, identify high-risk areas such as restricted laboratories, and evaluate the resilience of the current Gallagher–Salto system against cloning and replay attacks.
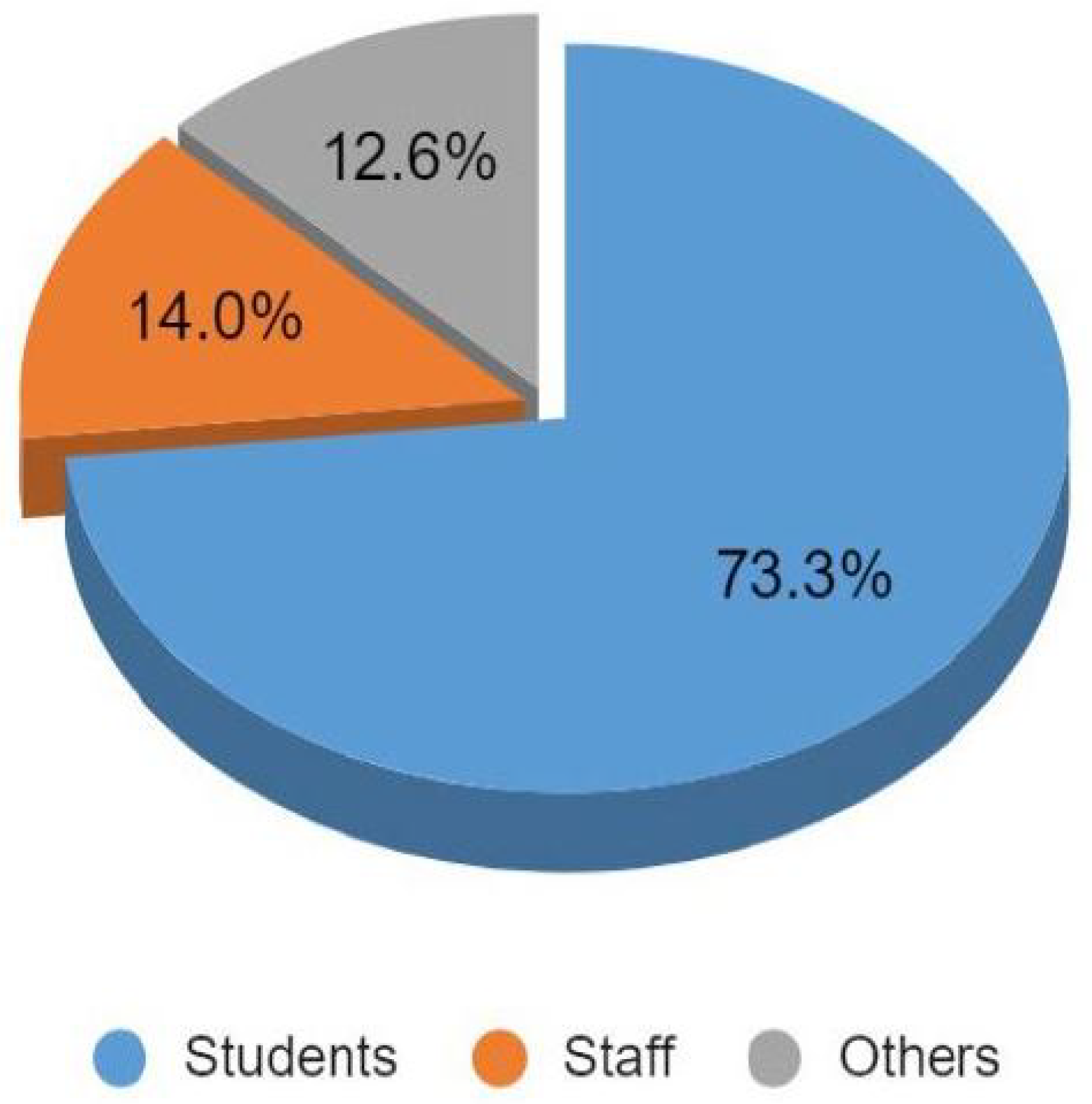
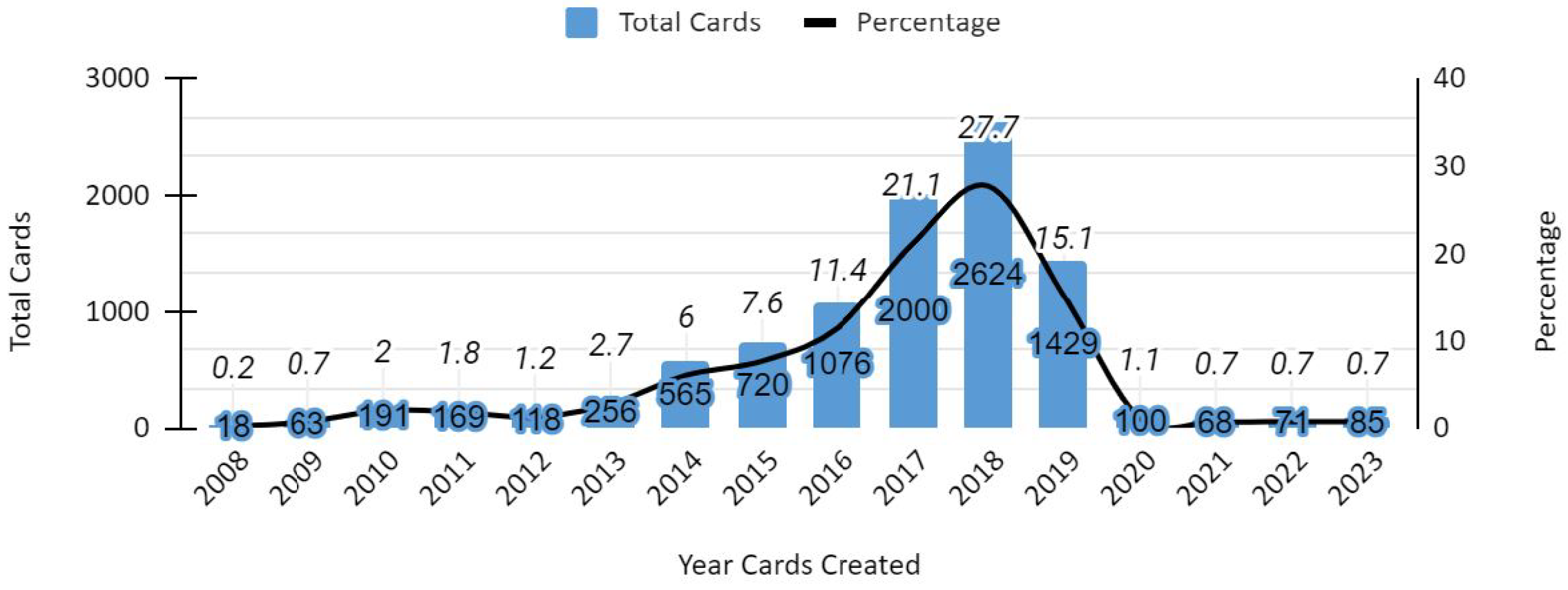
- We quantify the distribution and usage of cards that are vulnerable to Crypto1-based exploits, highlighting that more than two-fifths of active credentials remain insecure. This quantification allows us to prioritise mitigation strategies, demonstrate the scale of institutional exposure, and provide a clear evidence base for transitioning towards mobile credentials.
1.3. Structure of the Paper
2. Related Work
3. Methodology and Risk Model
3.1. Mathematical Risk Model
- : the proportion of active credentials of type t issued to category i;
- : an access privilege weight, higher for zones classified as high-risk (e.g., restricted labs);
- : a normalised activity factor, representing the relative frequency of access for category i in zone z;
- : a vulnerability factor for credential type t (e.g., , , ) to reflect the likelihood of cloning or compromise.
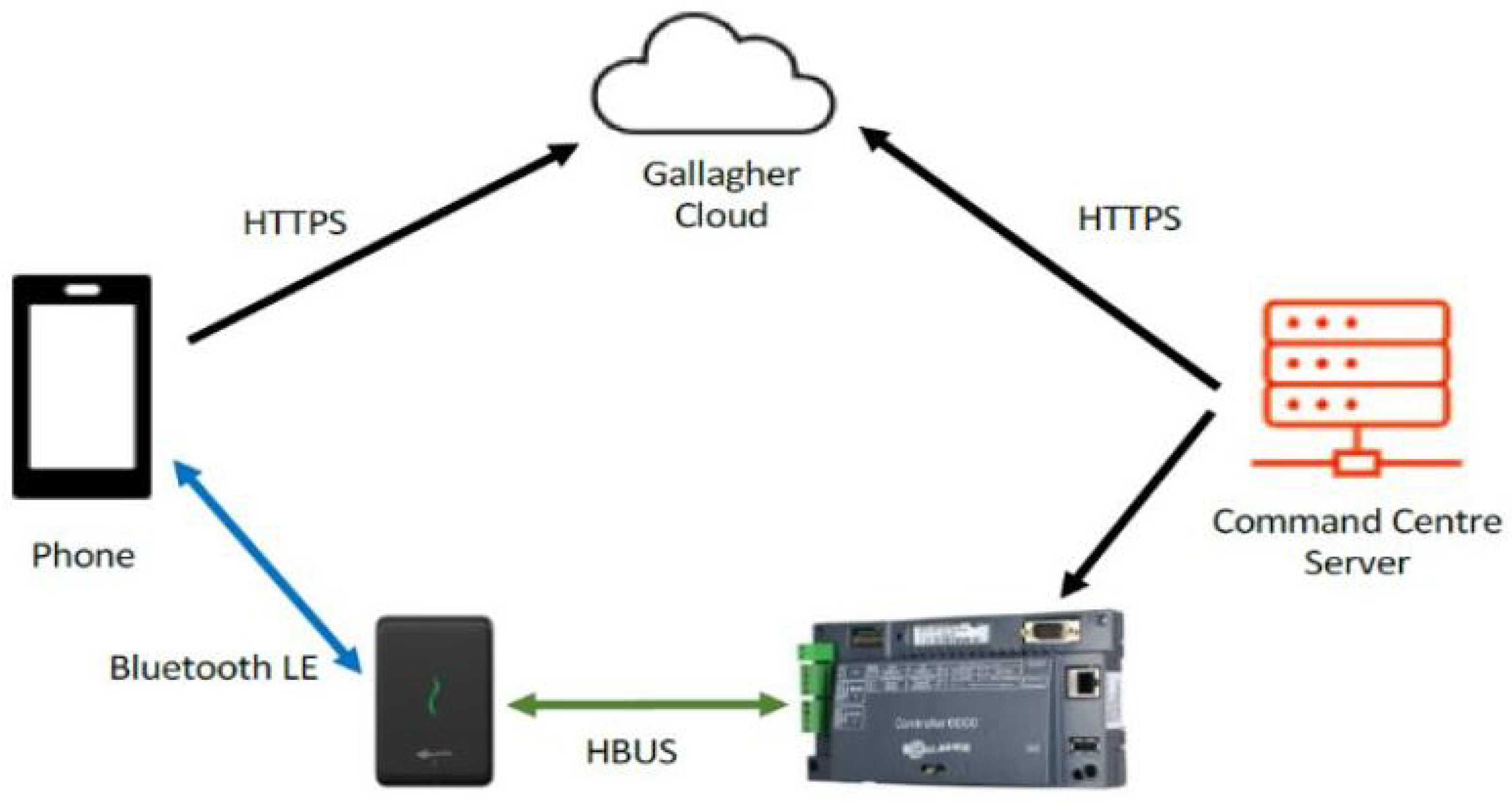
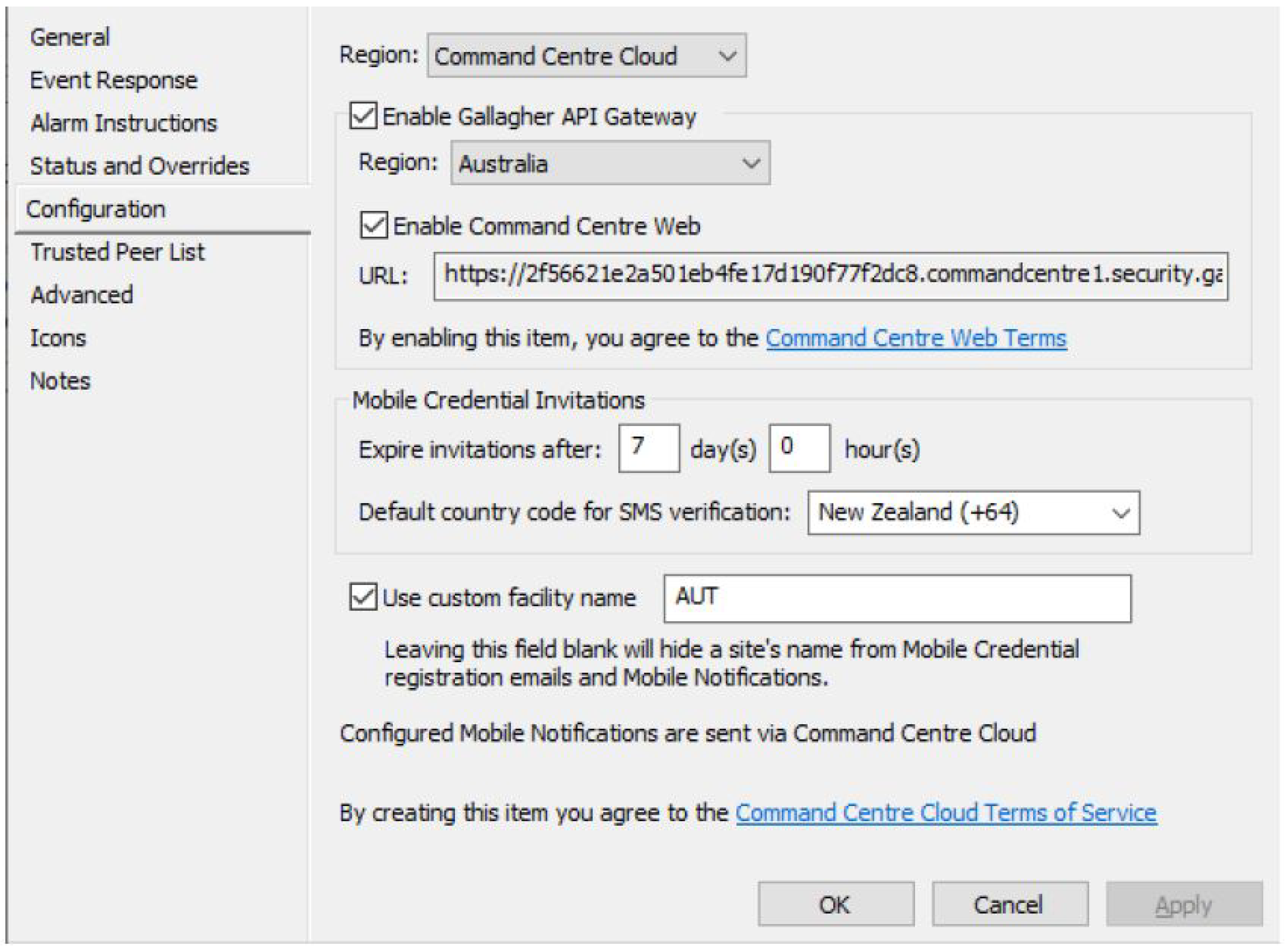
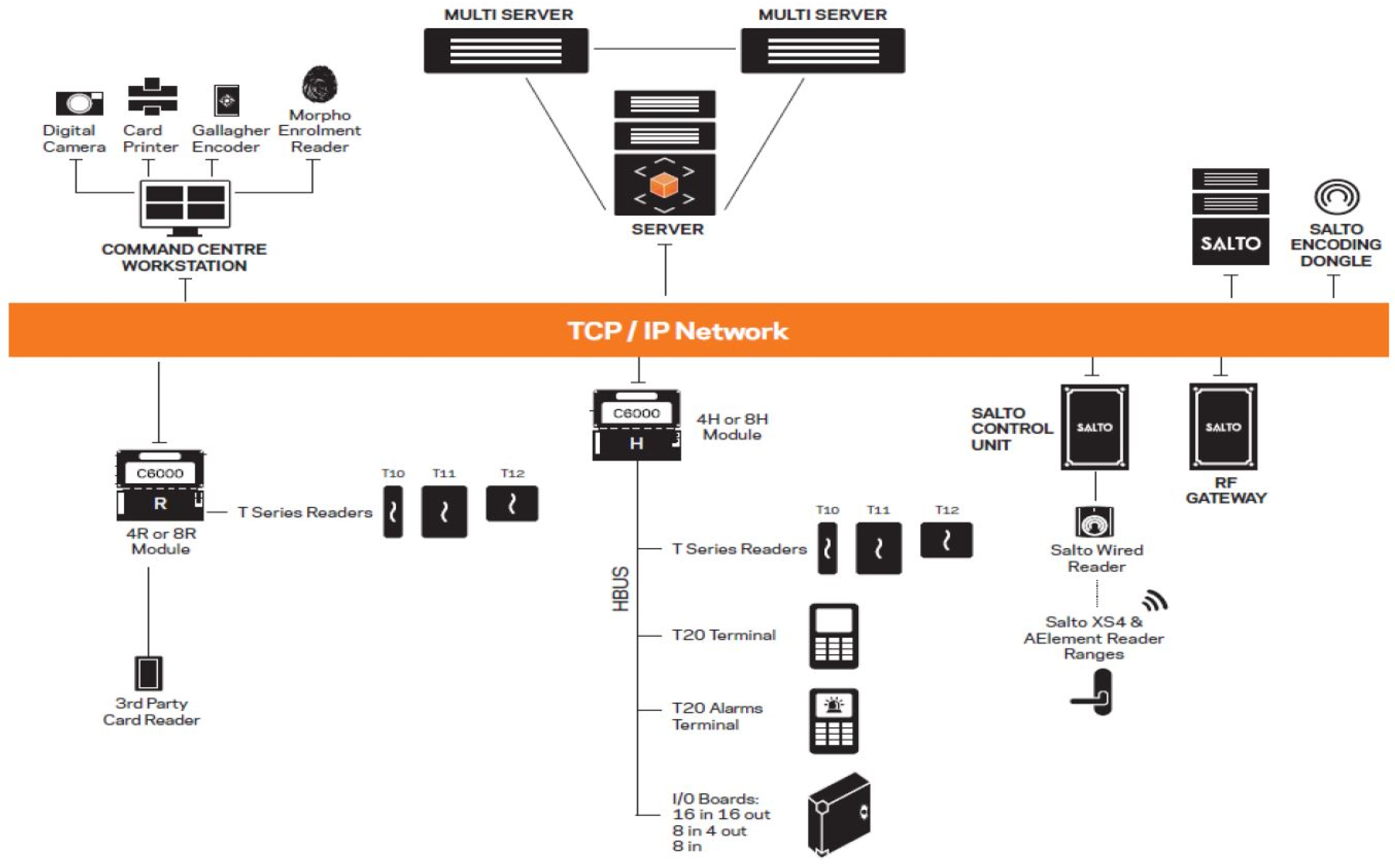
3.2. System Implementation Issues
3.3. Scalability, Stress, and Resilience Testing (Pre-Production)
- Baseline (W1): a steady flow of activity matching the usual arrival rate , such as the movement of students between regular classes.
- Peak (W2): a short burst of heavy use, approximately 4– for a 15-min period, representing pressure at the beginning of exams or major events.
- Soak (W3): a prolonged load of held for eight hours to expose any gradual resource or thermal issues.
- Surge (W4): irregular, bursty arrivals following a Pareto-style pattern, including brief spikes reaching up to .
- Network: intentional delays (50–300 ms), jitter (coefficient of variation 0.3), controlled packet loss (1–10%), and short interruptions (10–60 s) on the cloud link.
- Reader/Controller: cycling 5–15% of readers, rebooting a controller, simulating a firmware rollback, and briefly dropping selected HBUS connections.
- Cloud: closing WebSocket sessions, slowing API responses, delaying credential updates (up to 60 s), and initiating a regional failover.
- Credential Layer: replaying invalid Classic-style frames, inserting duplicate device identifiers, and revoking 2000 synthetic credentials within a one-minute window.
- Correctness: overall authorisation success rate, and changes in false accept (FAR) and false reject (FRR) rates relative to the baseline.
- Performance: median, 95th percentile, and 99th percentile delay from credential presentation to door unlock; queue depth at controllers; retry counts; and reader reconnection time.
- Reliability: command-processing backlog, cloud-synchronisation delay, message-loss rate (expected to be zero), and consistency of credential state across replicas.
- Operations: mean time to recovery (MTTR) for injected faults, number of doors degraded for more than one minute, and completeness of audit logs.
- Availability/Accuracy: success rate ; no increase in FAR; FRR rise during W2–W4.
- Latency: 95th percentile s; 99th percentile s; median s.
- Recovery: reader reconnection s; controller recovery s; cloud resubscription s.
- Data/Audit: zero message loss; cloud-sync delay s under throttling; audit completeness at 100%.
3.4. Methodological Structure and Case-Study Integration
4. Results
4.1. Quantitative Validation and Evidence of Claimed Improvements
4.2. Long-Term Security and Energy Impact Assessment
4.2.1. Security Continuity Metrics
4.2.2. Energy and Sustainability Metrics
5. Discussion and Practical Implications
5.1. Practical Implications
5.2. Biometric Integration: A Future Consideration
5.3. Open Issues and Future Directions
- Integrating mobile credentials with multi-factor authentication frameworks that adapt dynamically to risk levels (e.g., stricter checks in high-risk labs).
- Assessing the long-term reliability of mobile solutions under conditions of high user density, such as lecture theatres and examination halls.
- Expanding sustainability analysis beyond PVC cards to include the energy consumption of mobile infrastructure, ensuring that security gains do not introduce hidden environmental costs.
- Exploring how biometric authentication can be layered into the mobile ecosystem once costs and hardware barriers decrease.
5.4. Proposed Scalability and Resilience Testing Framework
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AUT | Auckland University of Technology |
| DCT | Department of Clinical Training |
| ECMS | School of Engineering, Computer and Mathematical Sciences |
| FOBEL | Faculty of Business, Economics and Law |
| FOHES | Faculty of Health and Environmental Sciences |
| HBUS | High-Speed Bus is Gallagher’s proprietary high-speed |
| RFID | Radio Frequency Identification |
| NFC | Near Field Communication |
| NFV | Network Function Virtualisation |
| ISO | International Standardization Organization |
| IEC | International Electrotechnical Commission |
| RNG | Random Number Generator |
| TCP | Transmission Control Protocol |
| SQL | Structured Querry language |
| PVC | Polyvinyl Chloride |
| REST | Representational State Transfer |
| API | Application Programming Interface |
| FIDO | Fast Identity Online |
| TLS | Transport Layer Security |
| MIFARE | MIkron FARE collection system |
References
- de Koning Gans, G.; Hoepman, J.; Garcia, F.D. A Practical Attack on the MIFARE Classic. In Lecture Notes in Computer Science, Proceedings of the Smart Card Research and Advanced Applications—CARDIS 2008, London, UK, 8–11 September 2008; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5189, pp. 267–282. [Google Scholar] [CrossRef]
- Garcia, F.D.; de Koning Gans, G.; Verdult, R. Dismantling MIFARE Classic. In Lecture Notes in Computer Science, Proceedings of the Applied Cryptography and Network Security (ACNS 2009), Paris-Rocquencourt, France, 2–5 June 2009; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5536, pp. 201–220. [Google Scholar] [CrossRef]
- Meijer, C.; Verdult, R. Ciphertext-Only Cryptanalysis on Hardened MIFARE Classic Cards. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security (CCS 2015), Denver, CO, USA, 12–16 October 2015; pp. 18–30. [Google Scholar] [CrossRef]
- Gray, A.R. Managing Change in Higher Education: Implementing Mobile Credentials Across USNH. Master’s Thesis, University of New Hampshire, Durham, NH, USA, 2025. Available online: https://scholars.unh.edu/ms_leadership/143 (accessed on 30 November 2025).
- Mustafa, R.; Sarkar, N.I.; Mohaghegh, M.; Pervez, S. A Cross-Layer Secure and Energy-Efficient Framework for the Internet of Things: A Comprehensive Survey. Sensors 2024, 24, 7209. [Google Scholar] [CrossRef] [PubMed]
- Szymoniak, S.; Kesar, S. Key Agreement and Authentication Protocols in the Internet of Things: A Survey. Appl. Sci. 2023, 13, 404. [Google Scholar] [CrossRef]
- Namane, S.; Dhaou, I.B. Blockchain-Based Access Control Techniques for IoT Applications. Electronics 2022, 11, 2225. [Google Scholar] [CrossRef]
- Cäsar, M.; Pawelke, T.; Steffan, J.; Terhorst, G. A survey on Bluetooth Low Energy security and privacy. Comput. Netw. 2022, 203, 108712. [Google Scholar] [CrossRef]
- Onumadu, P.; Abroshan, H. Near-Field Communication (NFC): Cyber Threats and Mitigation Solutions in Payment Transactions: A Review. Sensors 2024, 24, 7423. [Google Scholar] [CrossRef]
- Veľas, A.; Boroš, M.; Kuffa, R.; Lenko, F. Testing of Permeability of RFID Access Control System for the Needs of Security Management. Appl. Sci. 2024, 14, 4227. [Google Scholar] [CrossRef]
- Vestenický, P.; Hruboš, M.; Kolla, E. Evaluation of Contactless Identification Card Immunity against a Current Pulse in an Adjacent Conductor. Electronics 2023, 12, 4875. [Google Scholar] [CrossRef]
- Greß, H.; Krüger, B.; Tischhauser, E. The Newer, the More Secure? Standards-Compliant Bluetooth Low Energy Man-in-the-Middle Attacks on Fitness Trackers. Sensors 2025, 25, 1815. [Google Scholar] [CrossRef]
- Peker, Y.K.; Bello, G.; Perez, A.J. On the Security of Bluetooth Low Energy in Two Consumer Wearable Heart Rate Monitors/Sensing Devices. Sensors 2022, 22, 988. [Google Scholar] [CrossRef]
- Hasan, S.S.U.; Ghani, A.; Daud, A.; Akbar, H.; Khan, M.F. A Review on Secure Authentication Mechanisms for Mobile Devices. Sensors 2025, 25, 700. [Google Scholar] [CrossRef] [PubMed]
- Gong, Y.; Li, K.; Xiao, L.; Cai, J.; Xiao, J.; Liang, W.; Liang, W.; Khan, M.K. An Adaptive, Lightweight, Secure, and Efficient RFID Fast Authentication Protocol. Sensors 2023, 23, 5198. [Google Scholar] [CrossRef] [PubMed]
- Gong, Y.; Li, K.; Xiao, L.; Cai, J.; Xiao, J.; Liang, W.; Liang, W.; Khan, M.K. VASERP: An Adaptive, Lightweight, Secure, and Efficient RFID-Based Authentication Scheme for IoV. Sensors 2023, 23, 5198. Available online: https://pubmed.ncbi.nlm.nih.gov/37299924/ (accessed on 27 November 2025). [CrossRef]
- Wang, S.; Fan, Z.; Su, Y.; Zheng, B.; Liu, Z.; Dai, Y. A Lightweight, Efficient, and Physically Secure Key Agreement Authentication Protocol for Vehicular Networks. Electronics 2024, 13, 1418. [Google Scholar] [CrossRef]
- Muñoz-Ausecha, C.; Ruiz-Rosero, J.; Ramírez-González, G. RFID Applications and Security Review. Computation 2021, 9, 69. [Google Scholar] [CrossRef]
- Corches, C.; Daraban, M.; Miclea, L. Availability of an RFID Object-Identification System in IoT Environments. Sensors 2021, 21, 6220. [Google Scholar] [CrossRef]
- Natgunanathan, I.; Fernando, N.; Loke, S.W.; Weerasuriya, C. Bluetooth Low Energy Mesh: Applications, Considerations and Current State-of-the-Art. Sensors 2023, 23, 1826. [Google Scholar] [CrossRef]
- Sun, D.; Tian, Y. Study on Address Privacy for Bluetooth Low Energy. Mathematics 2022, 10, 4346. [Google Scholar] [CrossRef]
- Chen, W.; Wei, Z.; Yang, Z. Robust Beamfocusing for Secure NFC with Imperfect CSI. Sensors 2025, 25, 1240. [Google Scholar] [CrossRef] [PubMed]
- Rehman, A.; Alharbi, O.; Qasaymeh, Y.; Aljaedi, A. DC-NFC: A Custom Deep Learning Framework for Security and Privacy in NFC-Enabled IoT. Sensors 2025, 25, 1381. [Google Scholar] [CrossRef] [PubMed]
- Firlej, A.; Musial, S.; Kubiak, I. Data Immunity in Near Field Radio Frequency Communication Systems—NFC as an Aspect of Electromagnetic Information Security. Appl. Sci. 2024, 14, 5854. [Google Scholar] [CrossRef]
- Ragothaman, K.; Wang, Y.; Rimal, B.; Lawrence, M. Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions. Sensors 2023, 23, 1805. [Google Scholar] [CrossRef]
- Bukova, B.; Tengler, J.; Brumercikova, E.; Brumercik, F.; Kissova, O. Environmental Burden Case Study of RFID Technology in Logistics Centre. Sensors 2023, 23, 1268. [Google Scholar] [CrossRef]
- Ding, S.; Cucurachi, S.; Tukker, A.; Ward, H. The Environmental Benefits and Burdens of RFID Systems in Li-Ion Battery Supply Chains—An Ex-Ante LCA Approach. Resour. Conserv. Recycl. 2024, 209, 107829. [Google Scholar] [CrossRef]
- Aliakbarian, B.; Ghirlandi, S.; Rizzi, A.; Stefanini, R.; Vignali, G. Life Cycle Assessment of Plastic and Paper-Based Ultra High Frequency RFID Tags. Radio Freq. Technol. 2024, 14, 17–32. [Google Scholar] [CrossRef]
- Segkoulis, T.; Limniotis, K. Enhancing Multi-Factor Authentication for Mobile Devices Through Cryptographic Zero-Knowledge Protocols. Electronics 2025, 14, 1846. [Google Scholar] [CrossRef]
- Musa, A.; Dabo, A.-A.A. A Review of RFID in Supply Chain Management: 2000–2015. Glob. J. Flex. Syst. Manag. 2016, 17, 189–228. [Google Scholar] [CrossRef]
- ISO/IEC 27005:2022; Information Security, Cybersecurity and Privacy Protection—Guidance on Managing Information Security Risks. International Standard: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/80585.html (accessed on 27 November 2025).
- Aven, T. Risk Analysis, 2nd ed.; John Wiley & Sons: Chichester, UK, 2015. [Google Scholar] [CrossRef]
- Khan, T.A. Secure and Sustainable Transition from Legacy RFID Cards to Mobile Credentials at AUT. Master’s Thesis, Auckland University of Technology, Auckland, New Zealand, 2024. [Google Scholar]
- ISO/IEC 14443-1:2018; Cards and Security Devices for Personal Identification—Contactless Proximity Object—Part 1: Physical Characteristics. International Organization for Standardization: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/73597.html (accessed on 27 November 2025).
- ISO 31000:2018; Risk Management—Guidelines. International Organization for Standardization: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/65694.html (accessed on 27 November 2025).
- NIST Special Publication 800-30 Revision 1. Guide for Conducting Risk Assessments; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012. Available online: https://csrc.nist.gov/pubs/sp/800/30/r1/final (accessed on 27 November 2025).

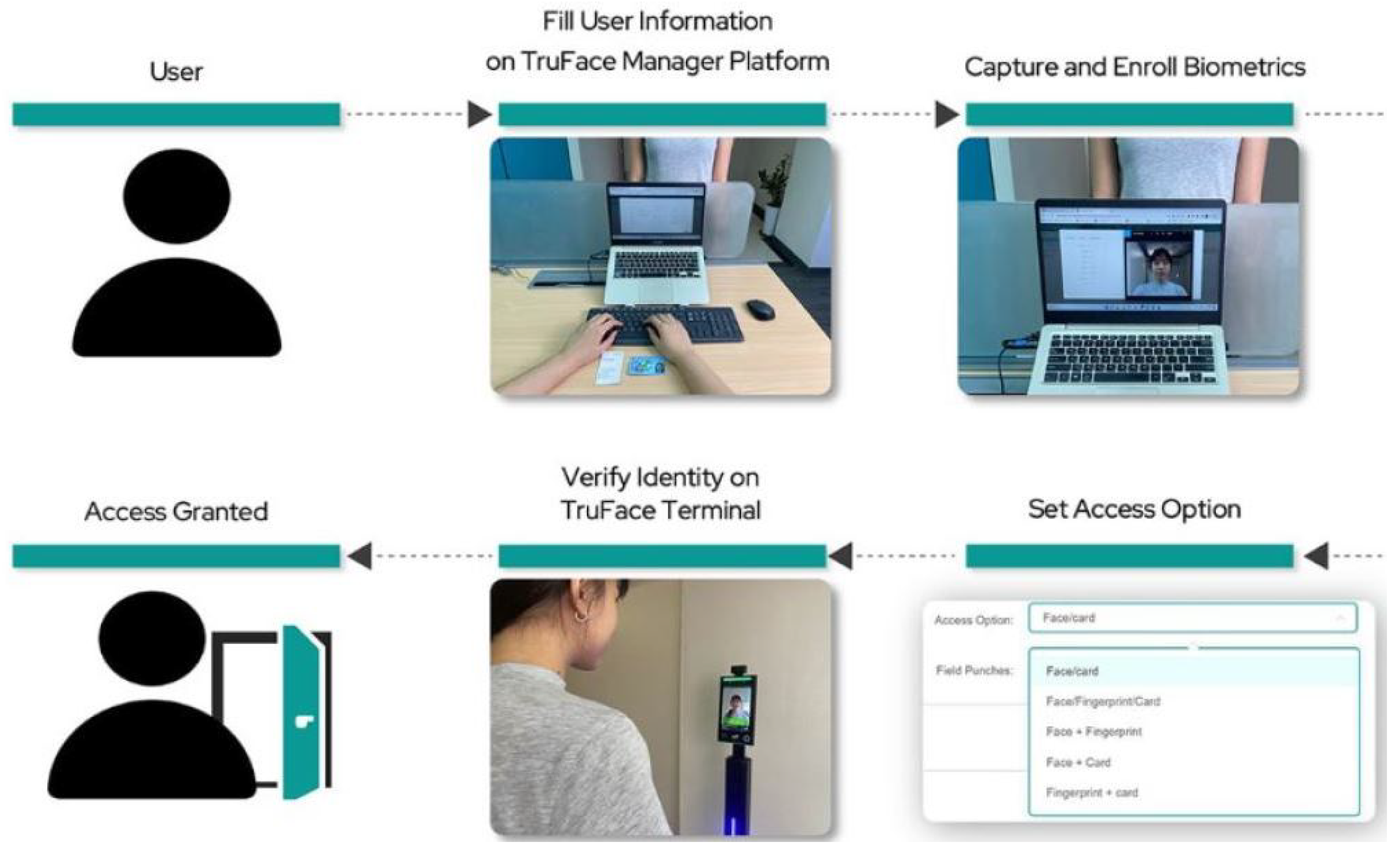
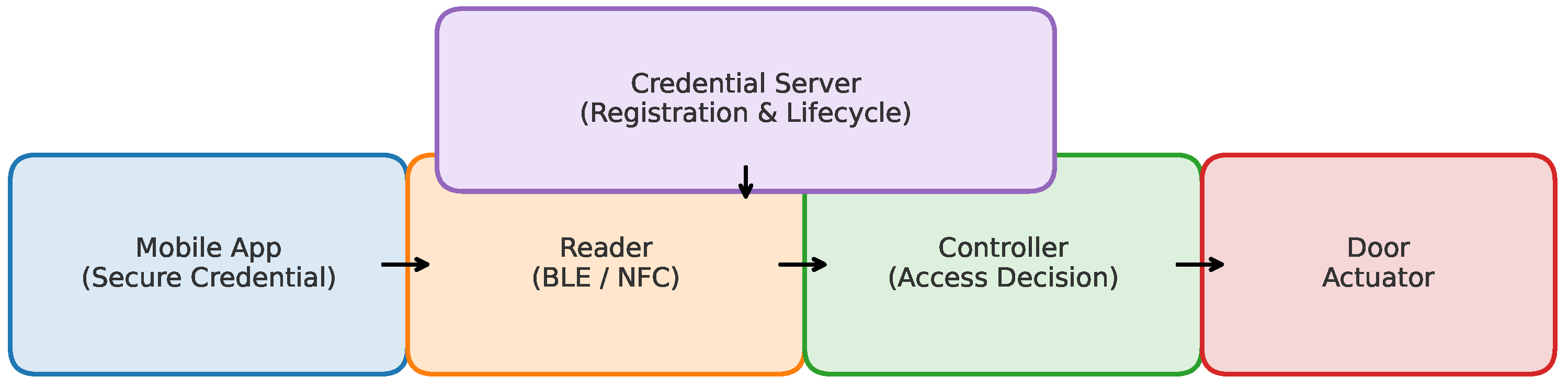
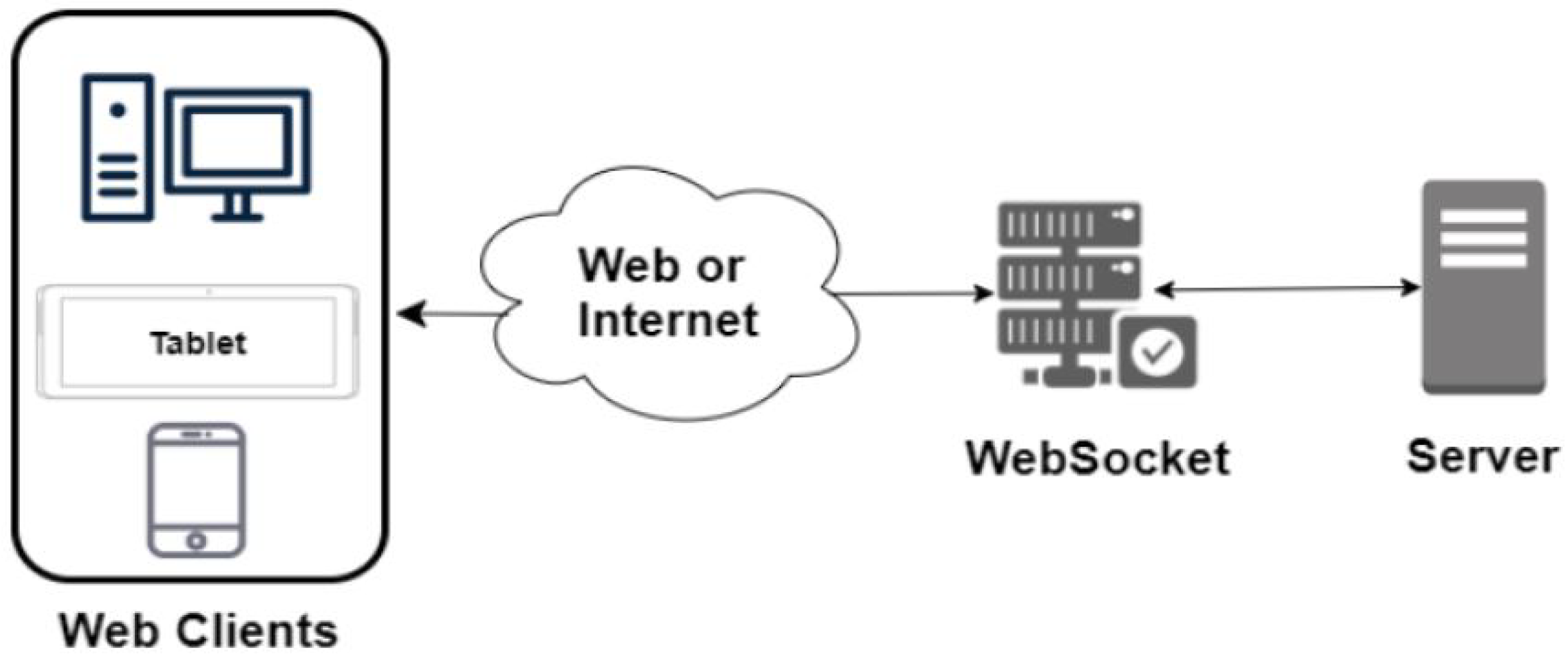
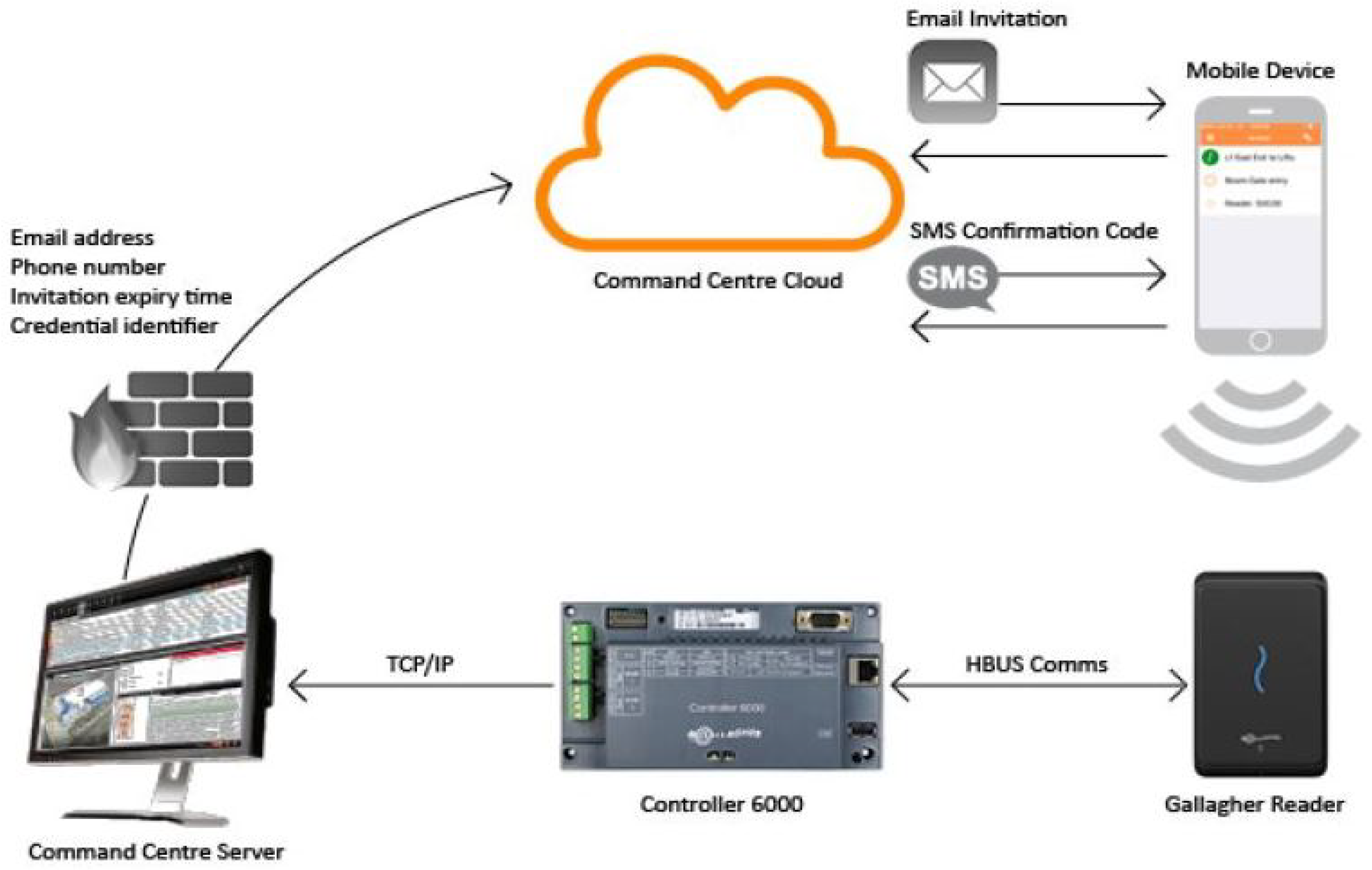

| Ref. | Domain/Focus | Main Contribution/Relevance |
|---|---|---|
| [6] | IoT Protocols | Reviews auth/key-agreement; trade-offs in lightweight vs. secure schemes. |
| [7] | Blockchain AC | Taxonomy of blockchain-based IoT access control. |
| [8] | BLE Security Survey | Maps BLE flaws and defences; foundation for secure mobile credential design. |
| [9] | NFC Threat Review | Systematic review of NFC attacks/mitigations; supports secure migration to mobile. |
| [10] | RFID System Reliability | Quantifies throughput/permeability in access control; informs door/mobile deployments. |
| [11] | Contactless Chip Immunity | Tests card chip performance under EMI; justifies replacing MIFARE Classic. |
| [12] | BLE Security Evolution | Assesses newer BLE devices; shows progress but persistent risks. |
| [13] | BLE Device Weaknesses | Empirical flaws in consumer BLE devices; relevance to PACS readers. |
| [14] | Mobile Authentication | Survey of MFA, biometrics, cryptographic methods; informs mobile credential policy. |
| [15] | Lightweight RFID Protocols | Reviews RFID auth protocols; categorises by scalability, overhead, security. |
| [16] | Fast RFID Authentication | New lightweight protocol; efficient against cloning/relay. |
| [17] | Key Agreement (IoV) | PUF + ECC protocol; shows resilience transferable to PACS. |
| [18] | RFID Applications | Broad survey of RFID uses/security; underscores legacy risks. |
| [19] | RFID Reliability | Models IoT RFID availability; relevant to continuous door operation. |
| [20] | Bluetooth Mesh | Surveys BLE Mesh uses, challenges; scalability insights for campus-wide access. |
| [21] | BLE Address Privacy | Analyzes randomization weaknesses; implications for mobile credential privacy. |
| [22] | NFC Physical Security | Robust beamfocusing to improve NFC resilience. |
| [23] | NFC + Deep Learning | Proposes DL-based DC-NFC; adaptive security for mobile apps. |
| [24] | Near-field RFID | Studies data immunity/interference; improves secure door placement. |
| [25] | IoT Access Control | Surveys AC models/policies; relevance to dynamic campus contexts. |
| [26] | RFID Sustainability | Case study of RFID in logistics; ecological trade-offs highlight plastic card waste. |
| [27] | RFID LCA | Ex-ante LCA of RFID; shows sustainability benefits and burdens. |
| [28] | UHF Tag Lifecycle | Compares paper vs. plastic RFID tags; supports greener material transition. |
| [29] | Mobile MFA | Reviews contextual/biometric MFA; relevant for mobile credential security. |
| [30] | RFID in Supply Chains | Reviews RFID benefits/flaws; analogy to PACS risk vs. enabler. |
| Evaluation Dimension | Research Article Characteristics | Features of AUT Secure Credential Framework |
|---|---|---|
| Strengthening Scientific Foundation Impact | Demonstrates integration of theoretical grounding, quantitative modelling, and reproducible validation. | Builds a hybrid empirical–analytical framework linking credential security theory with real AUT data. Mathematical risk models, pilot deployment, and sustainability analysis collectively establish this as a scientifically grounded study rather than a descriptive project. |
| Scientific Foundation | Rooted in measurable constructs, quantitative parameters, and verifiable modelling. | Employs a structured risk quantification model (Equations (1)–(3)) that relates credential categories, vulnerabilities, and access frequencies using normalised coefficients. |
| Empirical Validation | Relies on experimental or field-based testing. | Demonstrates in-field deployment at AUT facilities, capturing authentication accuracy, latency, and reliability metrics under real operational load. |
| Analytical Depth | Combines statistical evaluation with interpretive synthesis. | Merges quantitative risk outcomes with user experience data, producing design implications generalizable to broader academic and institutional security contexts. |
| Reproducibility | Methodology and data structures must allow independent verification. | All configurations, network diagrams, and system parameters are fully documented, following ISO/IEC 14443 and FIDO2 compliance for future replication. |
| Scholarly Impact | Extends domain understanding through theory-driven experimentation. | Establishes a cross-layer model merging access control, environmental sustainability, and institutional resilience—contributing to the evolving field of secure digital infrastructure. |
| ID | Workload | Injected Condition (s) | Primary KPIs & Acceptance Criteria |
|---|---|---|---|
| S1 | W3 Soak (8 h, 3×) | None (baseline endurance) | Success ≥ 99.7%; 99p ≤ 1.6 s; no drift/leaks; full audit verification. |
| S2 | W2 Peak (15 min, 5×) | Cloud latency 150 ms with 3% packet loss | Success ≥ 99.5%; 95p ≤ 1.2 s; reconnect < 20 s; no message loss. |
| S3 | W4 Surge (bursty) | Reboot one controller; 10% readers flap | Door degradation < 2 min; auto-reconnect < 30 s; success ≥ 99.5%. |
| S4 | W2 Peak | WebSocket drop (60 s) and sync throttle (60 s) | Synchronisation lag ≤ 60 s; no stale grants; success ≥ 99.5%. |
| S5 | W3 Soak | Mass revoke of 2000 credentials within 60 s | Revocation propagation ≤ 45 s; FAR ; audit completeness 100%. |
| S6 | W4 Surge | Replay/duplicate device IDs (synthetic test) | Reject rate 100%; FRR ≤ +1.0%; latency within operational target. |
| S7 | W2 Peak | Regional failover event | Recovery < 120 s; success ≥ 99.5% post-failover; zero transaction loss. |
| Performance metrics | MIFARE Classic (Legacy) | Mobile Credential (Post-Migration) | Relative Change |
|---|---|---|---|
| Annualised risk index () | 0.599 | 0.120 | ↓ 80.0% |
| Expected credential breaches/year () | ↓ 80.0% | ||
| Cumulative energy demand (MJ/year) | 26,200 | 600 | ↓ 97.7% |
| Composite sustainability index () | 15.3 | 146.7 | ↑ 9.6× |
| Theme | Evidence/Trigger (from This Study) | Operational Action/Recommendation | Expected Impact |
|---|---|---|---|
| Legacy credential risk | High share of MIFARE Classic in circulation; exposure in restricted labs (Figure 2 and Figure 4) | Prioritise migration of high-privilege users (staff, lab supervisors) first; revoke/replace Classic cards on a rolling schedule | Immediate reduction of cloning/replay risk in critical areas |
| Sustainable security | PVC card dependence; mobile credentials reduce material use (Results & Discussion) | Adopt mobile credentials as default issuance for new users; phase out plastic reprints | Security uplift with parallel progress on sustainability targets |
| Architecture fit | Proven Gallagher–Salto integration; Controller 6000 policy enforcement. | Keep policy logic central in Command Centre; standardise reader protocols (NFC/BLE) | Consistent enforcement and simpler operations campus-wide |
| Hardware constraints | Pilot showed gaps where legacy readers persist (Figure 10) | Tie credential migration to phased reader upgrades (replace GBUS-bound paths first) | Fewer access failures; smoother user experience |
| User experience | Positive feedback on biometrics; concerns on battery reliance (pilot notes) | Enable MFA (PIN/biometric) on high-risk doors; publish device/ battery good-practice | Higher acceptance with minimal friction; predictable entry reliability |
| Policy integrity | Dual issuance weakens control (Figure 11) | Enforce mutually exclusive policy: mobile or card per user, not both | Reduces sharing/abuse; clearer audit and revocation |
| Open Issue | Research/Engineering Question | Proposed Approach/Next Step | Anticipated Outcome |
|---|---|---|---|
| Hybrid infrastructure | How to ensure consistent UX when legacy and modern readers coexist? (cf. Figure 10) | Map “weak segments”; prioritise upgrades on critical paths; certify doors for mobile before go-live | Uniform reliability and reduced incident rates |
| Credential policy | How to enforce mobile or card without user resistance? (Figure 11) | Stage policy with grace periods; auto-revoke on acceptance of mobile; clear comms and support | Stronger governance; fewer policy exceptions |
| Cost of transition | How to finance reader/cloud upgrades at scale? | Phased CAPEX tied to risk hotspots; explore SaaS licensing; inter-faculty cost-sharing | Predictable spend; quicker risk reduction where it matters most |
| Adaptive MFA | When should authentication step-up be required? | Risk-based MFA: door sensitivity, time-of-day, anomaly score; pilot ABAC+MFA on lab doors | Higher assurance with minimal added friction |
| Peak-load performance | Will mobile scale during surges (exams/lectures)? | Load tests on busy entries; queue telemetry; BLE/NFC tuning and reader placement | Verified throughput; fewer bottlenecks at turnstiles |
| Sustainability accounting | What is the whole-of-life footprint post-migration? | Extend LCA to include reader power, cloud ops, device charging; compare to PVC baseline | Evidence-backed sustainability reporting |
| Biometrics roadmap | When do biometrics become viable campus-wide? | Targeted rollout on highest-risk doors; TCO/benefit study; privacy and consent framework | Clear path to stronger assurance with compliance |
| Incident response | How to handle lost phones and rapid revocation? | MDM hooks/self-service portal; instant credential kill-switch; audit trails | Faster containment; improved user trust |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mustafa, R.; Khan, T.A.; Sarkar, N.I. A Secure and Sustainable Transition from Legacy Smart Cards to Mobile Credentials in University Access Control Systems. Information 2025, 16, 1073. https://doi.org/10.3390/info16121073
Mustafa R, Khan TA, Sarkar NI. A Secure and Sustainable Transition from Legacy Smart Cards to Mobile Credentials in University Access Control Systems. Information. 2025; 16(12):1073. https://doi.org/10.3390/info16121073
Chicago/Turabian StyleMustafa, Rashid, Toseef Ahmed Khan, and Nurul I. Sarkar. 2025. "A Secure and Sustainable Transition from Legacy Smart Cards to Mobile Credentials in University Access Control Systems" Information 16, no. 12: 1073. https://doi.org/10.3390/info16121073
APA StyleMustafa, R., Khan, T. A., & Sarkar, N. I. (2025). A Secure and Sustainable Transition from Legacy Smart Cards to Mobile Credentials in University Access Control Systems. Information, 16(12), 1073. https://doi.org/10.3390/info16121073







