Towards an Innovative Model for Cybersecurity Awareness Training
Abstract
1. Introduction
- Development of the iCAT model integrating knowledge graphs and gamification.
- Introduction of a micro-learning module for enhanced flexibility.
- Implementation of real-time progress monitoring and feedback mechanisms.
- Comprehensive evaluation demonstrating increased engagement and knowledge retention.
2. Background
3. Literature Review
3.1. Cybersecurity Advancements
3.2. Serious Games and Gamification for Effective Cybersecurity Awareness
3.3. Discussion
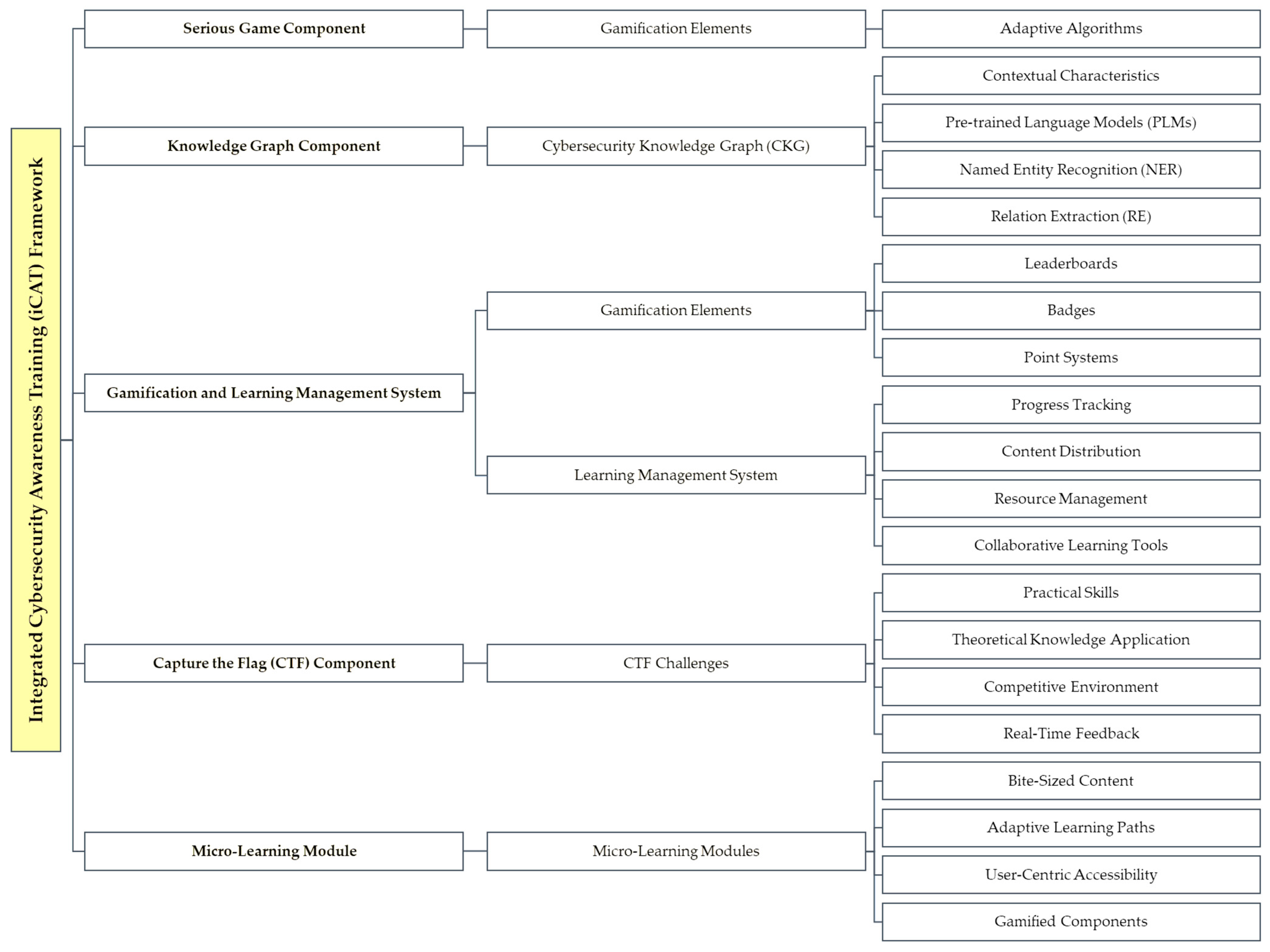
4. Proposed Framework
4.1. Design
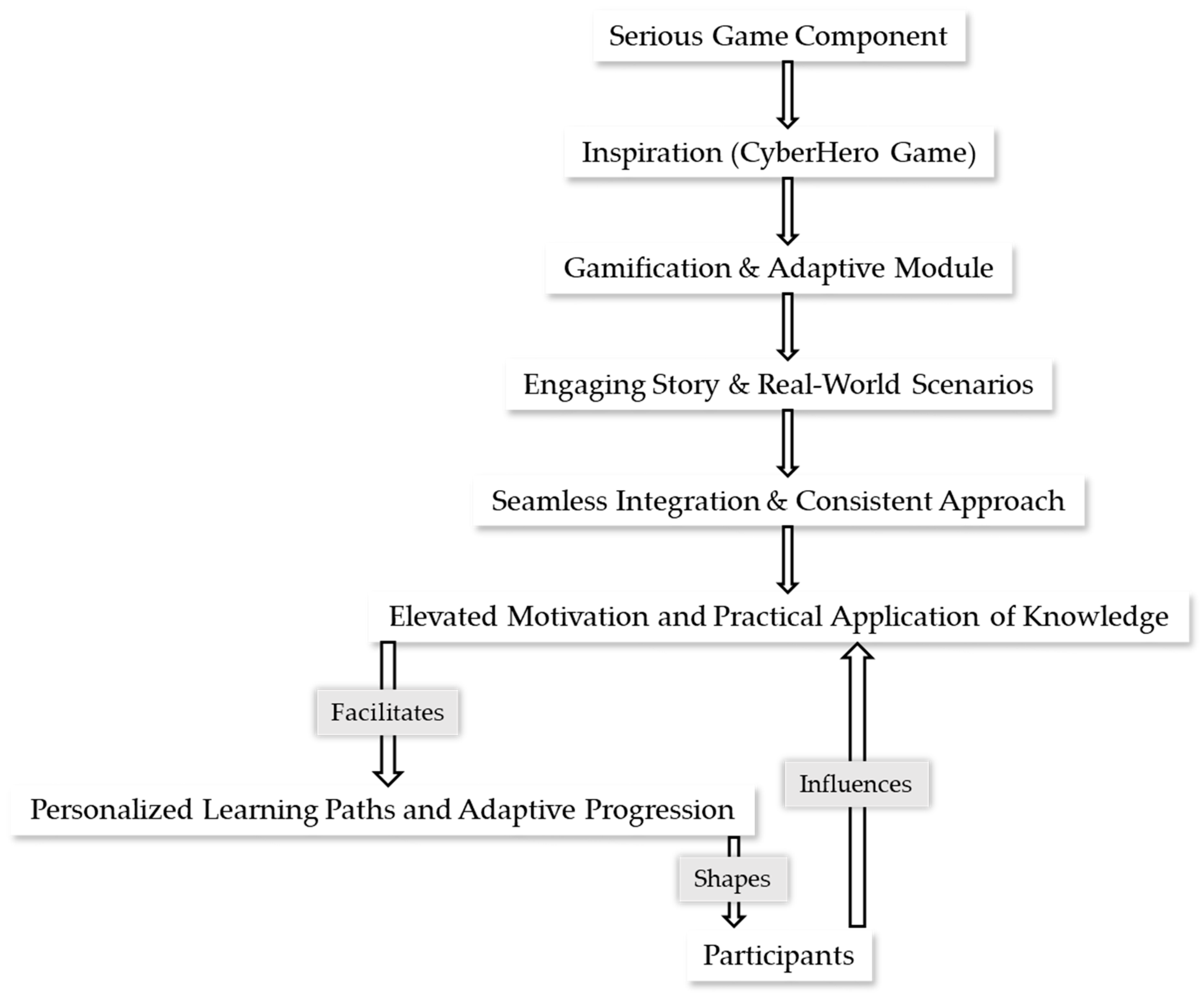
4.1.1. Serious Game Component
4.1.2. Knowledge Graph Component
4.1.3. Gamification and Learning Management System
4.1.4. Capture the Flag (CTF) Component
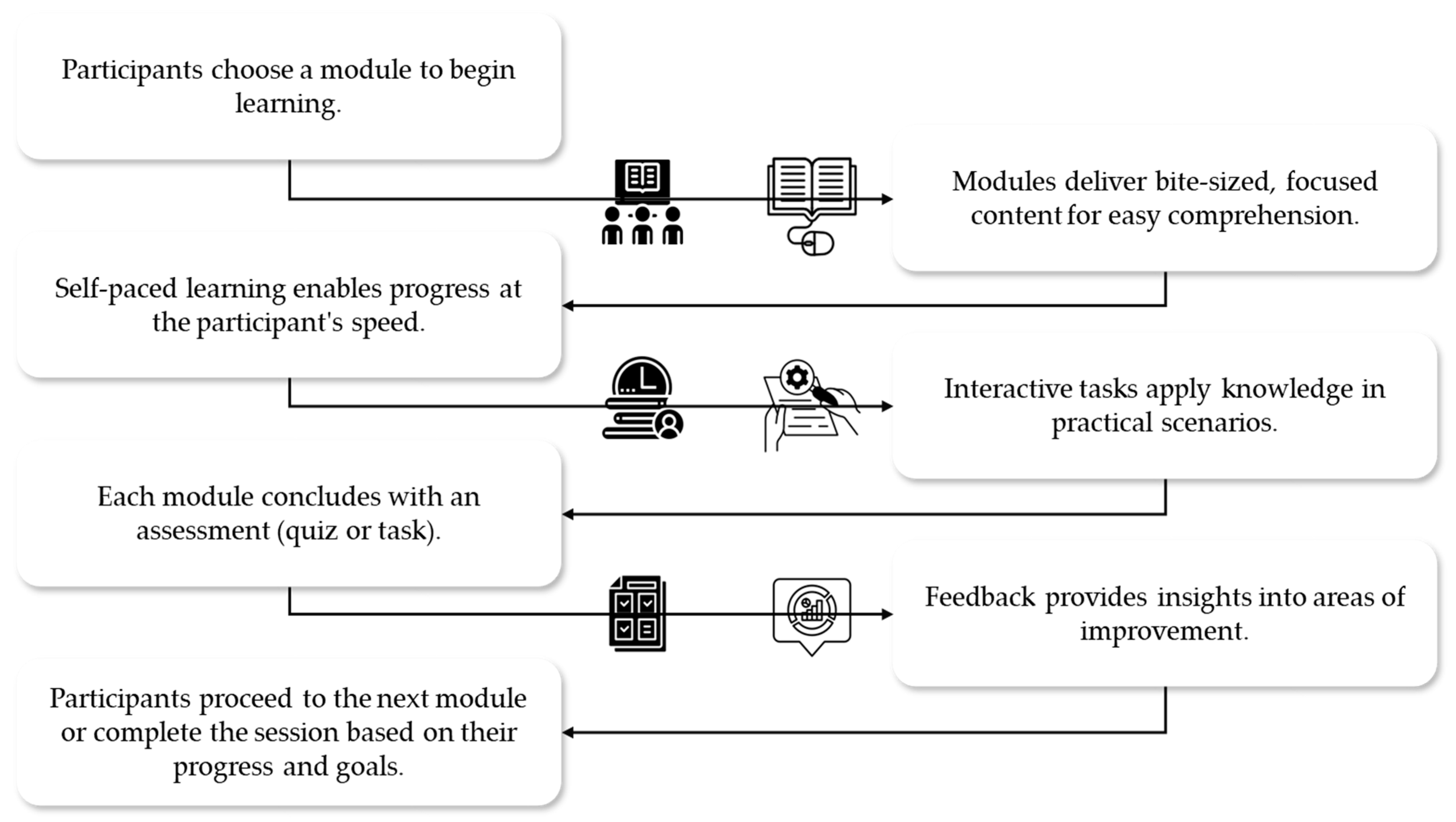
4.1.5. Enhanced Flexibility through Micro-Learning
5. Implications
6. Future Research
7. Conclusions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Bossler, A.M.; Berenblum, T. Introduction: New directions in cybercrime research. J. Crime Justice 2019, 42, 495–499. [Google Scholar] [CrossRef]
- Taherdoost, H. An overview of trends in information systems: Emerging technologies that transform the information technology industry. Cloud Comput. Data Sci. 2023, 4, 1–16. [Google Scholar] [CrossRef]
- Khan, M.A.; Merabet, A.; Alkaabi, S.; El Sayed, H. Game-based learning platform to enhance cybersecurity education. Educ. Inf. Technol. 2022, 27, 5153–5177. [Google Scholar] [CrossRef]
- Prümmer, J.; van Steen, T.; Berg, B.v.D. A systematic review of current cybersecurity training methods. Comput. Secur. 2024, 136, 103585. [Google Scholar] [CrossRef]
- Lab, K. The Human Factor in IT Security: How Employees Are Making Businesses Vulnerable from within; Kaspersky Daily: Moscow, Russia, 2018. [Google Scholar]
- Williams, S. More than Half of Personal Data Breaches Caused by Human Error; IT Brief: Melbourne, Australia, 2019. [Google Scholar]
- Hadlington, L. Human factors in cybersecurity; examining the link between Internet addiction, impulsivity, attitudes towards cybersecurity, and risky cybersecurity behaviours. Heliyon 2017, 3, e00346. [Google Scholar] [CrossRef] [PubMed]
- Okechukwu, J.C. Forensic Accountants’ Strategies and Cybercrime Mitigation; Northcentral University: Scottsdale, AZ, USA, 2020. [Google Scholar]
- Momoh, I.; Adelaja, G.; Ejiwumi, G. Analysis of the Human Factor in Cybersecurity: Identifying and Preventing Social Engineering Attacks in Financial Institution; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar]
- Wendt, D.W. Exploring the Strategies Cybersecurity Specialists Need to Improve Adaptive Cyber Defenses within the Financial Sector: An Exploratory Study; Colorado Technical University: Colorado Springs, CO, USA, 2020. [Google Scholar]
- Jasper, S. Strategic Cyber Deterrence: The Active Cyber Defense Option; Rowman & Littlefield: Lanham, MD, USA, 2017. [Google Scholar]
- Angafor, G.N.; Yevseyeva, I.; He, Y. Game-based learning: A review of tabletop exercises for cybersecurity incident response training. Secur. Priv. 2020, 3, e126. [Google Scholar] [CrossRef]
- Franke, U.; Brynielsson, J. Cyber situational awareness—A systematic review of the literature. Comput. Secur. 2014, 46, 18–31. [Google Scholar] [CrossRef]
- Haney, J.; Lutters, W. Security awareness training for the workforce: Moving beyond “check-the-box” compliance. Computer 2020, 53, 91–95. [Google Scholar] [CrossRef]
- Wash, R.; Rader, E. Too much knowledge? security beliefs and protective behaviors among united states internet users. In Eleventh Symposium on Usable Privacy and Security (SOUPS 2015); Michigan State University: East Lansing, MI, USA, 2015. [Google Scholar]
- Wash, R. Folk models of home computer security. In Proceedings of the Sixth Symposium on Usable Privacy and Security, Redmond, WA, USA, 14–16 July 2010. [Google Scholar]
- Camp, L.J. Mental models of privacy and security. IEEE Technol. Soc. Mag. 2009, 28, 37–46. [Google Scholar] [CrossRef]
- Grinter, R.E.; Edwards, W.K.; Newman, M.W.; Ducheneaut, N. The work to make a home network work. in ECSCW 2005. In Proceedings of the Ninth European Conference on Computer-Supported Cooperative Work, Paris, France, 18–22 September 2005. [Google Scholar]
- Bada, M.; Sasse, A.M.; Nurse, J.R. Cyber security awareness campaigns: Why do they fail to change behaviour? arXiv 2019, arXiv:1901.02672. [Google Scholar]
- Furnell, S.; Vasileiou, I. Security education and awareness: Just let them burn? Netw. Secur. 2017, 2017, 5–9. [Google Scholar] [CrossRef]
- Katsikas, S.K. Health care management and information systems security: Awareness, training or education? Int. J. Med. Inform. 2000, 60, 129–135. [Google Scholar] [CrossRef] [PubMed]
- ENISA. The New Users’ Guide: How to Raise Information Security Awareness. 2008. Available online: https://www.europeansources.info/record/the-new-users-guide-how-to-raise-information-security-awareness/ (accessed on 1 August 2024).
- de Zafra, D.E.; Pitcher, S.I.; Tressler, J.D.; Ippolito, J.B. Information technology security training requirements: A role-and performance-based model. NIST Spec. Publ. 1998, 800, 800–816. [Google Scholar]
- Chaudhary, S.; Gkioulos, V.; Katsikas, S. Developing metrics to assess the effectiveness of cybersecurity awareness program. J. Cybersecur. 2022, 8, tyac006. [Google Scholar] [CrossRef]
- Kruger, H.A.; Kearney, W.D. A prototype for assessing information security awareness. Comput. Secur. 2006, 25, 289–296. [Google Scholar] [CrossRef]
- Fan, J.; Zhang, P. Study on e-government information misuse based on General Deterrence Theory. In Proceedings of the ICSSSM11, Tianjin, China, 22–27 June 2011. [Google Scholar]
- Ng, B.-Y.; Kankanhalli, A.; Xu, Y. Studying users’ computer security behavior: A health belief perspective. Decis. Support Syst. 2009, 46, 815–825. [Google Scholar] [CrossRef]
- Sabillon, R. The cybersecurity awareness training model (CATRAM). In Research Anthology on Advancements in Cybersecurity Education; IGI Global: Hershey, PA, USA, 2022; pp. 501–520. [Google Scholar]
- Longo, G.; Orlich, A.; Musante, S.; Merlo, A.; Russo, E. MaCySTe: A virtual testbed for maritime cybersecurity. SoftwareX 2023, 23, 101426. [Google Scholar] [CrossRef]
- Li, J.; Li, J.; Xie, C.; Liang, Y.; Qu, K.; Cheng, L.; Zhao, Z. PipCKG-BS: A Method to Build Cybersecurity Knowledge Graph for Blockchain Systems via the Pipeline Approach. J. Circuits Syst. Comput. 2023, 32, 2350274. [Google Scholar] [CrossRef]
- Lee, C.; Lee, S. Evaluating the Vulnerability of YOLOv5 to Adversarial Attacks for Enhanced Cybersecurity in MASS. J. Mar. Sci. Eng. 2023, 11, 947. [Google Scholar] [CrossRef]
- Löffler, E.; Schneider, B.; Zanwar, T.; Asprion, P.M. CySecEscape 2.0-A virtual escape room to raise cybersecurity awareness. Int. J. Serious Games 2021, 8, 59–70. [Google Scholar] [CrossRef]
- Tai, Y.; Wei, L.; Zhou, H.; Peng, J.; Li, Q.; Li, F.; Zhang, J.; Shi, J. Augmented-reality-driven medical simulation platform for percutaneous nephrolithotomy with cybersecurity awareness. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719840173. [Google Scholar] [CrossRef]
- Hodhod, R.; Hardage, H.; Abbas, S.; Aldakheel, E.A. CyberHero: An Adaptive Serious Game to Promote Cybersecurity Awareness. Electronics 2023, 12, 3544. [Google Scholar] [CrossRef]
- Sharif, K.H.; Ameen, S.Y. A Intelligent Security Power Lab (SPL): The Ultimate Serious Game Training in Cybersecurity. Int. J. Intell. Syst. Appl. Eng. 2023, 11, 245–259. [Google Scholar]
- Wang, P.; Liu, J.; Zhong, X.; Zhou, S. A Cybersecurity Knowledge Graph Completion Method for Penetration Testing. Electronics 2023, 12, 1837. [Google Scholar] [CrossRef]
- Tran, T.M.; Beuran, R.; Hasegawa, S. Gamification-Based Cybersecurity Awareness Course for Self-regulated Learning. Int. J. Inf. Educ. Technol. 2023, 13, 724–730. [Google Scholar] [CrossRef]
- Douha, N.Y.-R.; Sasabe, M.; Taenaka, Y.; Kadobayashi, Y. An Evolutionary Game Theoretic Analysis of Cybersecurity Investment Strategies for Smart-Home Users against Cyberattacks. Appl. Sci. 2023, 13, 4645. [Google Scholar] [CrossRef]
- Ortiz-Garces, I.; Gutierrez, R.; Guerra, D.; Sanchez-Viteri, S.; Villegas-Ch, W. Development of a Platform for Learning Cybersecurity Using Capturing the Flag Competitions. Electronics 2023, 12, 1753. [Google Scholar] [CrossRef]
- Hijji, M.; Alam, G. Cybersecurity Awareness and Training (CAT) Framework for Remote Working Employees. Sensors 2022, 22, 8663. [Google Scholar] [CrossRef] [PubMed]
- Puys, M.; Thevenon, P.H.; Mocanu, S.; Gallissot, M.; Sivelle, C. SCADA Cybersecurity Awareness and Teaching with Hardware-In-The-Loop Platforms. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2022, 13, 4–32. [Google Scholar]
- Abu-Amara, F.; Almansoori, R.; Alharbi, S.; Alharbi, M.; Alshehhi, A. A novel SETA-based gamification framework to raise cybersecurity awareness. Int. J. Inf. Technol. 2021, 13, 2371–2380. [Google Scholar] [CrossRef]
- Khader, M.; Karam, M.; Fares, H. Cybersecurity awareness framework for academia. Information 2021, 12, 417. [Google Scholar] [CrossRef]
- Back, S.; Guerette, R.T. Cyber Place Management and Crime Prevention: The Effectiveness of Cybersecurity Awareness Training Against Phishing Attacks. J. Contemp. Crim. Justice 2021, 37, 427–451. [Google Scholar] [CrossRef]
- Nikoloudakis, Y.; Kefaloukos, I.; Klados, S.; Panagiotakis, S.; Pallis, E.; Skianis, C.; Markakis, E.K. Towards a machine learning based situational awareness framework for cybersecurity: An SDN implementation. Sensors 2021, 21, 4939. [Google Scholar] [CrossRef]
- Alves, F.; Bettini, A.; Ferreira, P.M.; Bessani, A. Processing tweets for cybersecurity threat awareness. Inf. Syst. 2020, 95, 101586. [Google Scholar] [CrossRef]
- Gasiba, T.E.; Lechner, U.; Pinto-Albuquerque, M. Sifu—A cybersecurity awareness platform with challenge assessment and intelligent coach. Cybersecurity 2020, 3, 24. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M. Design and evaluation of an augmented reality game for cybersecurity awareness (CybAR). Information 2020, 11, 121. [Google Scholar] [CrossRef]
- Brilingaitė, A.; Bukauskas, L.; Juozapavičius, A.; Bukauskas, A. Juozapavičius, A framework for competence development and assessment in hybrid cybersecurity exercises. Comput. Secur. 2020, 88, 101607. [Google Scholar] [CrossRef]
- Beuran, R.; Tang, D.; Tan, Z.; Hasegawa, S.; Tan, Y.; Shinoda, Y. Supporting cybersecurity education and training via LMS integration: CyLMS. Educ. Inf. Technol. 2019, 24, 3619–3643. [Google Scholar] [CrossRef]
- Giannakas, F.; Papasalouros, A.; Kambourakis, G.; Gritzalis, S. A comprehensive cybersecurity learning platform for elementary education. Inf. Secur. J. Glob. Perspect. 2019, 28, 81–106. [Google Scholar] [CrossRef]
- Sabillon, R.; Serra-Ruiz, J.; Cavaller, V. An effective cybersecurity training model to support an organizational awareness program: The Cybersecurity Awareness Training Model (CATRAM). A case study in Canada. J. Cases Inf. Technol. 2019, 21, 26–39. [Google Scholar] [CrossRef]
- Zhang, Z.; He, W.; Li, W.; Abdous, M. Cybersecurity awareness training programs: A cost–benefit analysis framework. Ind. Manag. Data Syst. 2021, 121, 613–636. [Google Scholar] [CrossRef]
- Fatokun, F.; Awang, Z.; Hamid, S.; Fatokun, J.O.; Norman, A. Cybersecurity Knowledge Deterioration and the role of Gamification Intervention. J. Adv. Res. Appl. Sci. Eng. Technol. 2024, 43, 66–94. [Google Scholar] [CrossRef]
- Tay, A.; Hayes, S.M.; Wilson, D.; Hall, E.; Kaufman, D. Gamified Cybersecurity Education Through the Lens of the Information Search Process: An Exploratory Study of Capture-the-Flag Competitions [Research-in-Progress]. Issues Informing Sci. Inf. Technol. 2024, 21, 001. [Google Scholar] [CrossRef]
- Bandeira, M.; Vairinhos, M.; Dias, P.; Soengas, R.; Silva, V. ChemXP AR Edition, a Serious Game. In Videogame Sciences and Arts; Springer Nature: Cham, Switzerland, 2024. [Google Scholar]
- Kalmpourtzis, G. Educational Game Design Fundamentals: A Journey to Creating Intrinsically Motivating Learning Experiences; AK Peters/CRC Press: Natick, MA, USA, 2018. [Google Scholar]
- Stylianidou, N.; Sofianidis, A.; Manoli, E.; Meletiou-Mavrotheris, M. “Helping Nemo!”—Using augmented reality and alternate reality games in the context of universal design for learning. Educ. Sci. 2020, 10, 95. [Google Scholar] [CrossRef]
- Katsantonis, M.N.; Manikas, A.; Mavridis, I.; Fouliras, P. tCOFELET: Conceptual Framework for Team-Centric e-Learning and Training. IEEE Access 2024, 12, 78878–78894. [Google Scholar] [CrossRef]
- Yadav, P. Gamification and Personalised Learning: Enhancing Student Engagement in Higher Education, in Transforming Education for Personalized Learning; IGI Global: Hershey, PA, USA, 2024; pp. 85–99. [Google Scholar]
- Wang, S.; Kong, X.; Wang, N. Gamification for Learning: Development and Application of Learning Software for Enhancing Student Engagement and Motivation. In Proceedings of the 2024 13th International Conference on Educational and Information Technology (ICEIT), Chengdu, China, 22–24 March 2024. [Google Scholar]
- Rosedi, S.R.b.H.M. The Use of Gamification in Improving Student Engagement When Learning the Standard Marine Communication Phrases (SMCP). KMI Int. J. Marit. Aff. Fish. 2024, 16, 1–20. [Google Scholar] [CrossRef]
- Cortes, A.A. Gamifing the Classroom: Bringing Videogames to Life Through Innovation in Education to Increase Student Engagement in STEM Subjects. In Proceedings of the 2024 IEEE Gaming, Entertainment, and Media Conference (GEM), Turin, Italy, 5–7 June 2024. [Google Scholar]
- Faith, B.F.; Long, Z.A.; Hamid, S. Promoting cybersecurity knowledge via gamification: An innovative intervention design. In Proceedings of the 2024 Third International Conference on Distributed Computing and High Performance Computing (DCHPC), Tehran, Iran, 14–15 May 2024. [Google Scholar]
- Zhang, W.; Wang, M.; Han, G.; Feng, Y.; Tan, X. A Knowledge Graph Completion Algorithm Based on the Fusion of Neighborhood Features and vBiLSTM Encoding for Network Security. Electronics 2024, 13, 1661. [Google Scholar] [CrossRef]
- Barron, R.; Eren, M.E.; Bhattarai, M.; Wanna, S.; Solovyev, N.; Rasmussen, K.; Alexandrov, B.S.; Nicholas, C.; Matuszek, C. Cyber-Security Knowledge Graph Generation by Hierarchical Nonnegative Matrix Factorization. In Proceedings of the 2024 12th International Symposium on Digital Forensics and Security (ISDFS), San Antonio, TX, USA, 29–30 April 2024. [Google Scholar]
- Serles, U.; Kärle, E.; Hunkel, R.; Fensel, D. German Tourism Knowledge Graph. arXiv 2024, arXiv:2404.09587. [Google Scholar]
- Shi, Z.; Matyunin, N.; Graffi, K.; Starobinski, D. Uncovering CWE-CVE-CPE Relations with threat knowledge graphs. ACM Trans. Priv. Secur. 2024, 27, 1–26. [Google Scholar] [CrossRef]
- Nelson, C.; Shoshitaishvili, Y. PWN The Learning Curve: Education-First CTF Challenges. In Proceedings of the 55th ACM Technical Symposium on Computer Science Education V. 1, Portland, OR, USA, 20–23 March 2024. [Google Scholar]
- Érsok, M.; Erdődi, L.; Balogh, Á.; Bánáti, A. Improving CTF Event Organization: A Case Study on Utilizing Open Source Technologies. In Proceedings of the 2024 IEEE 22nd World Symposium on Applied Machine Intelligence and Informatics (SAMI), Stará Lesná, Slovakia, 25–27 January 2024. [Google Scholar]
- Karampidis, K.; Panagiotakis, S.; Vasilakis, M.; Lamari, A.T.; Markakis, E.; Papadourakis, G. Digital Training for Cybersecurity in Industrial Fields via virtual labs and Capture-The-Flag challenges. In Proceedings of the 2023 32nd Annual Conference of the European Association for Education in Electrical and Information Engineering (EAEEIE), Eindhoven, The Netherlands, 14–16 June 2023. [Google Scholar]
- Savin, G.M.; Asseri, A.; Dykstra, J.; Goohs, J.; Melaragno, A.; Casey, W. Battle ground: Data collection and labeling of ctf games to understand human cyber operators. In Proceedings of the 16th Cyber Security Experimentation and Test Workshop, Marina del ReyMarina del Rey, CA, USA, 7–8 August 2023. [Google Scholar]
- Rashkevych, Y.; Semigina, T. Analysis of micro-credentials implementation opportunities in Ukraine and other European countries, International Educational Space. Educ. Anal. Ukr. 2024, 1, 110–122. [Google Scholar]



| Study | Concepts Supporting the Model | Tool’s Components | Context | Findings |
|---|---|---|---|---|
| [30] | PLMs, contextual features, prompt-based learning, NER, RE | Named entity recognition (NER), relation extraction (RE) models, PLMs | Blockchain systems | Outperforms advanced methods in CTI extraction for blockchain CKG. |
| [34] | Engaging and personalized experiences | Serious game for cybersecurity awareness | General cybersecurity | 79% learned new things, 84% engaged, 68% had fun, 84% would recommend. |
| [35] | Real-time feedback, KSAs, Godot engine | SPL game, real-time feedback system, educational content tailored to user preferences | General cybersecurity | Crucial training tool, strong system usability (74.09%), inclusive content. |
| [29] | Reproducing network infrastructure, realistic testing | Open-source project, ship simulators, cybersecurity testing | Maritime cybersecurity | Realistic testing for cybersecurity in the maritime sector. |
| [31] | Adversarial attacks, transfer learning | YOLOv5 model, adversarial attack methods, parameter changes | AI cybersecurity, maritime systems | Raises awareness of AI algorithm vulnerability to attacks. |
| [36] | BiLSTM, neural network, tensor decomposition, self-distillation strategy | CSNT model, Pearson Mix Net | Penetration testing | CSNT has advantages for completing cybersecurity data in the knowledge graph. |
| [37] | Gamification, self-regulated learning | Gamified courses, Moodle integration | General cybersecurity | Supports self-regulated learning for cyberspace users. |
| [38] | Evolutionary game theory, cybersecurity investment strategies | Game theory model, replicator dynamics | Smart-home cybersecurity | Costs should be low for smart-home users, and rewards should be crucial for commitment. |
| [39] | Capture the Flag (CTF) competitions, educational challenges | Learning platform with CTF section, teacher, and competition modes | General cybersecurity | Proposed solution for cybersecurity knowledge, positive results. |
| [40] | Capability evaluation, security management | CAT framework, case studies | Remote working cybersecurity | Three levels, 25 core practices, effective in real-world settings. |
| [41] | HIL technology, real sensors, and actuators | WonderICS, G-ICS, APT demonstrator, real industrial control devices | Industrial control systems (SCADA) | Platforms for awareness and training in SCADA cybersecurity. |
| [42] | SETA framework, interactive video game | Cyber shield game, threat scenarios, pre-game and post-game surveys | General cybersecurity | Interactive game improves cybersecurity awareness by 51.4%. |
| [43] | Continuous improvement, curriculum integration | Cybersecurity Awareness Framework, policy and procedure development | Academia | Improves cybersecurity awareness among university graduates. |
| [44] | Place management techniques, anti-phishing training | Anti-phishing training program | General cybersecurity | Positive impact of anti-phishing training on reducing cybercrime. |
| [45] | SDN, real-time awareness, ML-based IDS | Situational awareness framework, neural network, SDN paradigm | General cybersecurity | Increases prediction accuracy by more than 4%. |
| [32] | Cost–benefit analysis, CSAT program types | Theoretical framework for cost–benefit analysis, CSAT program categorization | General cybersecurity | Transforms physical escape room into virtual setting with positive immersion. |
| [46] | Escape room game, immersive learning | Virtual escape room, cybersecurity challenges for SMEs | SMEs | SYNAPSE successfully identifies security-related tweets with high accuracy. |
| [47] | Twitter-based threat monitoring, IoCs | SYNAPSE system, tweet-processing pipeline, feature extraction, binary classification, clustering strategy | Social media monitoring, IT infrastructure | Raises industry software developers’ awareness of secure coding. |
| [48] | Secure coding guidelines, AI-guided hints | Sifu platform, automatic challenge assessment, AI coach | Industry software development | Positive responses and increased understanding of cybersecurity concepts. |
| [49] | AR technology, active learning | CybAR game, mobile application, AR feedback | General cybersecurity | Aids in developing and assessing cybersecurity competencies during exercises. |
| [50] | Hybrid exercises, formative assessment, ARCS model | Competence development framework, assessment stages, hybrid CDX | General cybersecurity | Applicable to actual training activities. |
| [51] | LMS integration, SCORM format | CyLMS system, Moodle integration, standard interfaces for training management | General cybersecurity | App significantly increases participant performance by almost 20%. |
| [33] | ARCS model, elementary education | Learning Content Management System (LCMS), mobile app, suite of quick games | Elementary education | Reliable and versatile in percutaneous renal access surgical training. |
| [52] | AR technology, medical simulation | SimPCNL simulator, visual–haptic environment, clinical database | Medical cybersecurity | CATRAM is designed for different organizational audiences with specific content and objectives. |
| Awareness methodologies, targeted training content | CATRAM model, organizational training | General cybersecurity |
| Element | Strategy | Implementation Tools | Evaluation Metrics |
|---|---|---|---|
| Gamification Elements | Game Mechanics Model | Gamification platform, Point system algorithm | Participation rates, Points earned, Leaderboard rankings |
| Narrative Design Model | Storyboarding tools, Scenario creation software | Participant engagement, Story progression assessment | |
| Learning Management System | User-Friendly Interface Model | Learning Management System platform (e.g., Moodle, Canvas) | Usability feedback, Navigation efficiency, and User satisfaction surveys |
| Content Delivery Model | Content management system, SCORM compliance | Content completion rates, Timely delivery assessment | |
| Progress Tracking Model | Learning analytics tools, Progress tracking features | Completion rates, Time spent on modules, Assessment scores | |
| Collaborative Learning Model | Collaboration tools (e.g., forums, chat), Group project platforms | Forum participation, Group project completion, Peer assessment scores | |
| Integration Approach | Holistic Integration Model | Custom integration scripts, API connections | Integration efficiency, Data consistency, User experience |
| Micro-Learning Module Component | Segmentation into Bite-Sized Modules | Adaptive Learning Paths | User-Centric Accessibility |
|---|---|---|---|
| Bite-sized Content | ✔ | ||
| Personalized Learning | ✔ | ||
| Interactive Delivery | ✔ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Taherdoost, H. Towards an Innovative Model for Cybersecurity Awareness Training. Information 2024, 15, 512. https://doi.org/10.3390/info15090512
Taherdoost H. Towards an Innovative Model for Cybersecurity Awareness Training. Information. 2024; 15(9):512. https://doi.org/10.3390/info15090512
Chicago/Turabian StyleTaherdoost, Hamed. 2024. "Towards an Innovative Model for Cybersecurity Awareness Training" Information 15, no. 9: 512. https://doi.org/10.3390/info15090512
APA StyleTaherdoost, H. (2024). Towards an Innovative Model for Cybersecurity Awareness Training. Information, 15(9), 512. https://doi.org/10.3390/info15090512






