Elevating Security in Migration: An Enhanced Trusted Execution Environment-Based Generic Virtual Remote Attestation Scheme
Abstract
1. Introduction
- We propose a generic virtual remote attestation scheme which can be adapted to multiple hardware environments.
- We present a novel virtual remote attestation scheme which supports the secure migration of virtual machines across clouds without loss or leakage of confidential data and sensitive information.
- We propose a VRASM scheme which bestows VM with a Virtual Root of Trust (VRoT). This VRoT not only functions as an identity credential for VMs but also serves as a pivotal trust anchor, enabling VMs to place their trust in a virtualized environment.
- We evaluate the performance overhead introduced by the proposed schema and the overhead required for VM migration through the presented scheme.
2. Background
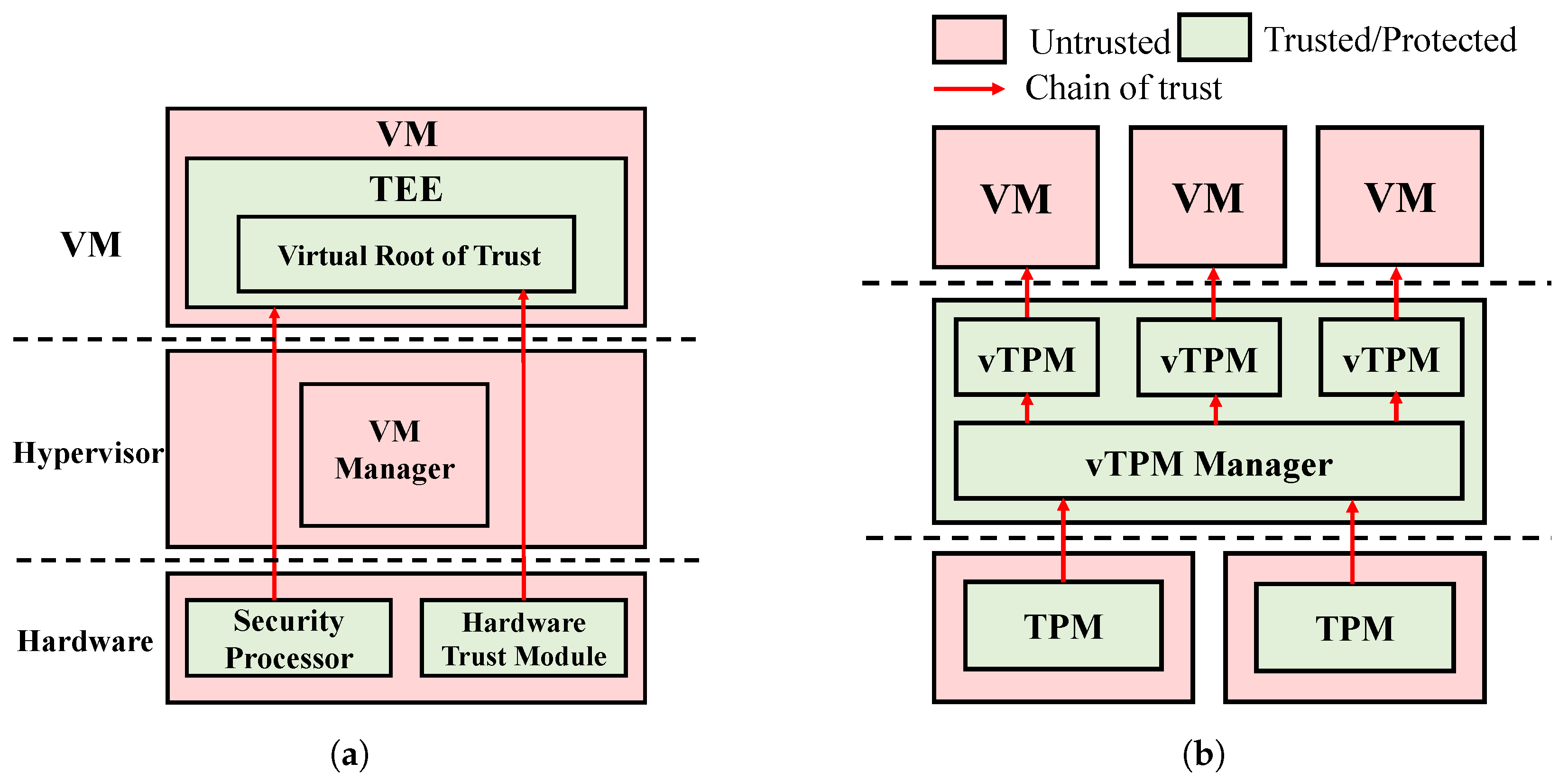
2.1. Trusted Execution Environments
2.2. Remote Attestation
- Attestation Request: The party initiating the attestation, usually referred to as the verifier, dispatches a challenge or request to the remote device or system under evaluation.
- Remote System Response: The remote system, acting as the prover, generates an attestation report, which typically encompasses details regarding its hardware, software configuration, and possibly other pertinent data.
- Remote Attestation Evidence: Subsequently, the remote system signs this report using its cryptographic keys and transmits it back to the verifier.
- Verification: The verifier employs cryptographic techniques to authenticate the attestation evidence, ensuring its integrity and its origin from a trusted party. This step may also include verifying the authenticity of the signer’s identity.
- Trust Assessment: Based on the verification results, the verifier can make an evaluation of the trustworthiness of the remote system. If the verification is successful, the verifier can trust that the remote system is in a known, secure state. In case of discrepancies or failed verification, appropriate security measures can be initiated, such as denying access to the remote system.
3. Overview of VRASM
3.1. Threat Model
3.2. Design Goals
- Hardware-Agnostic: The VRASM schema is designed to be hardware-agnostic. It accommodates deployment across a range of certified hardware environments, without being tied to any particular vendor’s hardware or technology. This commitment to hardware neutrality underscores the openness and universality of VRASM schema, thereby affording users a wider array of choices.
- Serves as a trust anchor for virtual machines: The VRASM schema establishes a Virtual Root of Trust for each virtual machine, serving as the foundational point of trust in virtualization environments. This trust anchor paves the way for virtual remote attestation, secure migration, and various other trust-centric operations.
- Enabling Secure VM Migration: The VRASM schema is meticulously crafted to facilitate secure, uninterrupted migration of virtual machines (VMs) to designated secure migration destinations. This process is executed without compromising vital information, safeguarding sensitive data, or succumbing to potential tampering by malicious attackers. This comprehensive approach to VM migration mitigates the associated risks and effectively curtails migration costs.
3.3. Key Approach
4. Virtual Remote Attestation
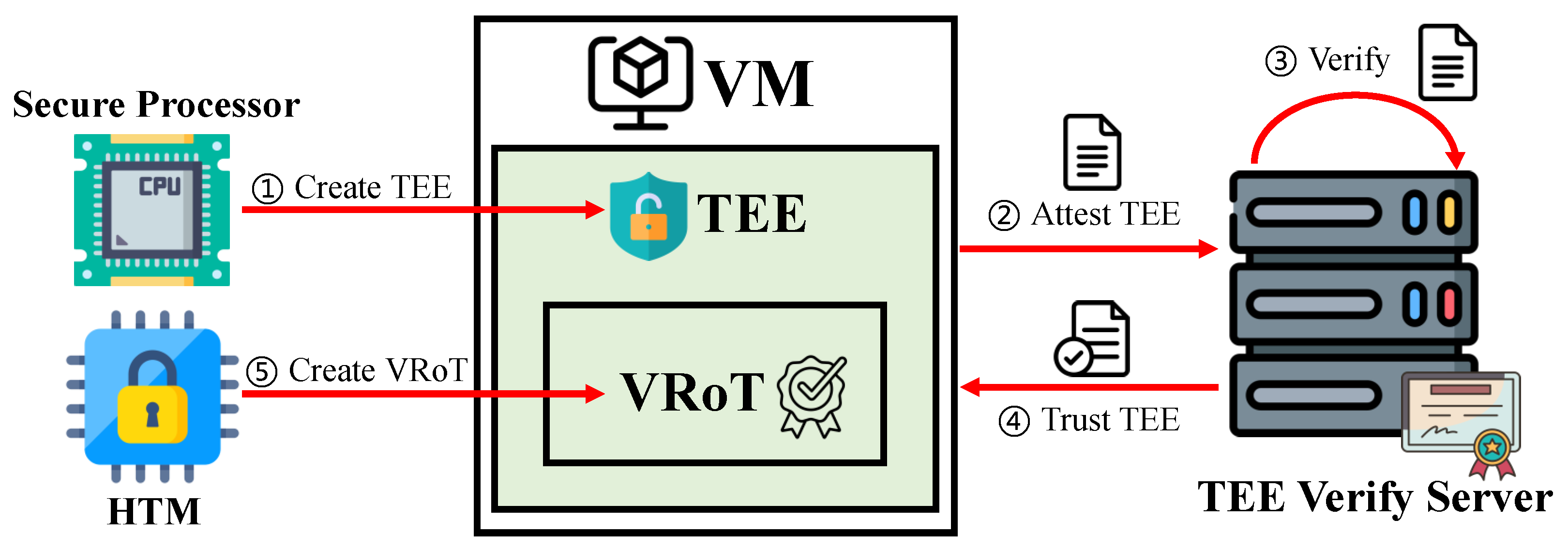
4.1. Initialization
- The VRoT enables VMs to authenticate their identity by verifying the VRoT’s certificate, thus thwarting identity forgery and tampering.
- The VRoT supports virtual remote attestation by signing and encrypting the evidence, ensuring the integrity and confidentiality of the VRA process.
- The VRoT guarantees the secure and unaltered migration of VMs.
- The VRoT facilitates encryption, decryption, and signature operations within the TEE, thereby reducing the HRoT’s performance burden, thus preventing performance bottlenecks akin to those experienced by the TPM in scenarios involving multiple vTPMs.
4.2. Virtual Remote Attestation
5. Secure Migration
5.1. Details of the Model
- Controller. The controller plays a pivotal role throughout the entire migration process. Its primary responsibilities encompass overseeing the migration of virtual machines, determining the feasibility of the migration, and facilitating secure key exchanges between different HTMs. Simultaneously, the controller assumes a partial role as a attestation server during the migration process, verifying whether the cloud environment meets migration prerequisites and ensuring the security integrity of the virtual machines. Consequently, the security of the controller is paramount in determining the safety of the virtual machine migration process. Hence, it is imperative to deploy the controller in a secure and trustworthy environment.
- Trust Domain. To ensure the security of the controller, it is imperative to deploy it within a trust domain. We recommend placing the trust domain within a secure realm that users can control, allowing them to guarantee the security of virtual machine migration. However, for the sake of flexibility, if users place trust in the cloud service provider, the controller can also be deployed in a secure and trustworthy cloud environment.
- Cloud. A cloud environment that supports secure migration must possess HTM and the capability to construct TEE. In the absence of remote attestation by the controller to verify the hardware capabilities of either migration party’s cloud environment, the controller will deem the migration unfeasible. This precaution ensures the security of both cloud environments involved in the migration and mitigates the risk of malicious attacks on the migrated virtual machines.
5.2. The Secure Migration Process of Virtual Machines
- The source virtual machine located in Cloud 1 sends a migration request to the controller situated in the trust domain controlled by the user.
- Upon receiving the migration request, the controller simultaneously conducts remote attestation for both the source virtual machine in Cloud 1 and the destination Cloud 2. This process ensures the authenticity and effectiveness of the HTM and the capability to provide TEE in both clouds. Once both clouds have successfully passed the remote attestation process, the controller can ensure that they meet the security requirements for migration, thereby preventing potential malicious attackers from migrating virtual machines from a secure cloud environment to an insecure one for malicious purposes.
- After completing the remote attestation for the hardware security capabilities of both cloud environments, it is essential to ensure the security and trustworthiness of the virtual machine itself. This step is crucial because if the virtual machine is insecure or under the control of an attacker, it could pose a threat to the security of the destination cloud, leading to lateral movement attacks across cloud environments. Therefore, before migration, it is imperative to conduct virtual remote attestation for the virtual machine, as outlined in the previously described process, to guarantee the security and trustworthiness of the virtual machine.
- Upon the completion of the aforementioned remote attestation and virtual remote attestation processes, the controller will notify Cloud 2 to prepare for the reception of the virtual machine migration.
- After receiving the migration notification, Cloud 2 sends the public key of HTM2 to the controller for later use in the encryption of the virtual machine during subsequent steps.
- The controller sends the public key of HTM2, along with its own public key, to HTM1. The public key of HTM2 will be used to encrypt the virtual machine in step 8, while the controller’s public key is utilized in the TEE to encrypt the hash value of the private key of the VRoT. This encrypted hash is then sent back to the controller, enabling it to verify that the VRoT has not been tampered with before and after migration, ensuring the security and integrity of the VRoT.
- HTM1 invokes the interface of the TEE to send the received public key of the controller into the TEE. Within the TEE, the VRoT hashes its private key and encrypts it with the controller’s public key. Subsequently, the encrypted hash is transmitted to HTM1 via an interface. Finally, HTM1 forwards the encrypted hash back to the controller. The primary objective of this step is to ensure that, upon completion of the migration process and reconstruction of the trust chain, the VRoT remains unaltered, consistent, and secure before and after migration. This safeguards the integrity of the trust anchor for the virtual machine.
- Within the TEE, the content and certain confidential information in the TEE are first signed using the private key of HTM1. This signing process, in step with HTM1’s private key, aims to ensure that the protected content remains intact and consistent with its state before migration upon completion of the migration process. After the signing by HTM1, the confidential information that requires protection is encrypted using the public key of HTM2, received in step 6. The purpose of encryption, distinct from signing, is primarily to safeguard confidential information from unauthorized disclosure. Once both the signing and encryption steps are completed, the virtual machine is prepared for migration.
- The virtual machine undergoes migration. It is noteworthy to mention that the proposed solution can accommodate both cold migration and live migration scenarios.
- After the completion of the virtual machine migration, HTM1 sends its public key to the controller. This step is crucial for subsequent processes to verify the ongoing validity of HTM1’s signature. This verification serves as evidence that the virtual machine migration process was not compromised or tampered with by attackers, thereby confirming the security of the migration process.
- The controller forwards the received public key of HTM1 to HTM2 for subsequent signature verification in the upcoming steps.
- At this stage, Cloud 2 has successfully received the migrated virtual machine. It is imperative to initiate the reconstruction of the TEE within the virtual machine, which entails completing the VRASM initialization process. This step is essential for reconstructing the trust chain from HTM to the VRoT. Once the TEE is established, subsequent operations must be performed within the TEE to ensure the security of the data. Within the TEE, HTM2 decrypts the confidential information using its private key and subsequently verifies the virtual machine’s signature to ensure it originates from HTM1 and is valid, using the public key received in the previous step. With the completion of decryption and signature verification operations, the secure migration process of the virtual machine is essentially concluded.
- To ensure the security of the virtual machine, it is imperative to conduct an additional round of virtual remote attestation after the completion of the secure virtual machine migration process. This step is essential to verify the post-migration security and integrity of the virtual machine.
5.3. Security Analysis
- Data Leakage Protection. In our proposed solution, before virtual machine migration, the VRoT and critical confidential data within the virtual machine are encrypted using HTM. Consequently, during the migration process, attackers are thwarted from accessing the virtual machine’s sensitive data, thus preventing data leakage. The migrated virtual machine is encrypted with the public key of the destination HTM, ensuring that only the destination can decrypt the confidential data within the virtual machine. Importantly, all encryption and decryption operations take place within the TEE. After the virtual machine arrives at the destination, decryption of sensitive data and the VRoT can only occur within the TEE after its reconstruction, preventing potential data leaks. Additionally, since communication between HTM and the controller is conducted through secure channels such as TLS, the information exchanged during this process remains secure. Therefore, our proposed virtual machine migration scheme provides robust privacy and data security protection.
- Defense Against Tampering. Addressing the integrity protection concern before and after virtual machine migration is a cornerstone of our proposed solution, achieved through a robust signing mechanism. Firstly, before migration, the confidential data within the virtual machine are signed by the HTM at the migration source. After migration, a simple verification using the public key of the source HTM reveals whether the virtual machine data have been tampered with. Secondly, before migration, the hash value of the VRoT of the virtual machine is encrypted using the controller’s key and stored at the controller. After migration, a virtual remote attestation can be employed to verify if the hash value of the VRoT remains consistent with the pre-migration state. Through this dual-signature mechanism, our proposed virtual machine migration scheme effectively ensures the prevention of malicious tampering with critical virtual machine data, providing robust resistance against attacks such as man-in-the-middle attacks.
- Adaptation to Heterogeneous Environments. Our proposed migration scheme exhibits strong versatility, making it well suited for diverse and heterogeneous cloud environments. The requirements for our solution are minimal, necessitating only HTM and hardware with TEE functionality. This results in a small TCB. As a result, regardless of the complexity of the underlying cloud environment, as long as it can provide this minimal TCB, our solution is applicable and ensures the security of the migration process.
6. Implementation and Evaluation
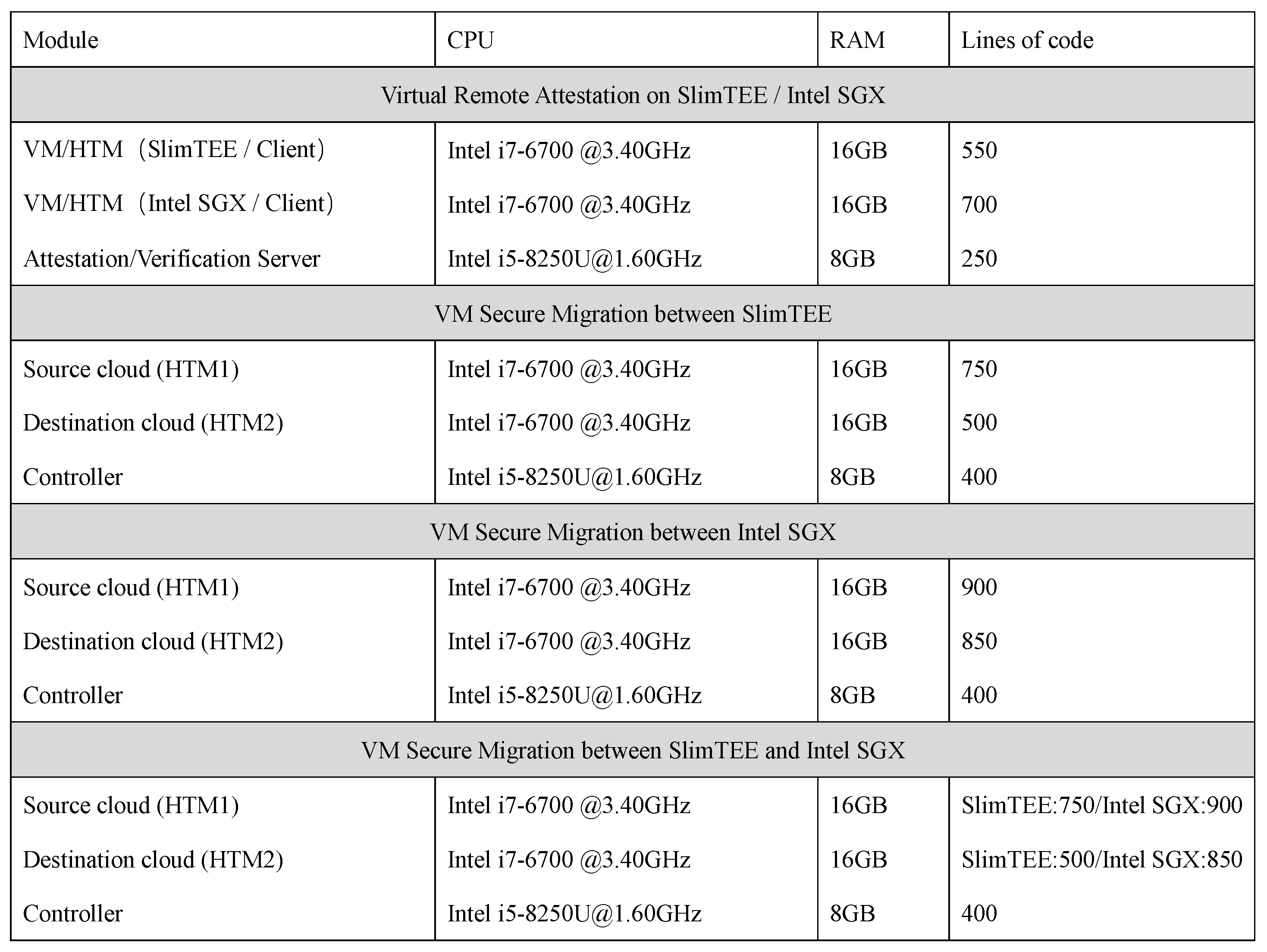
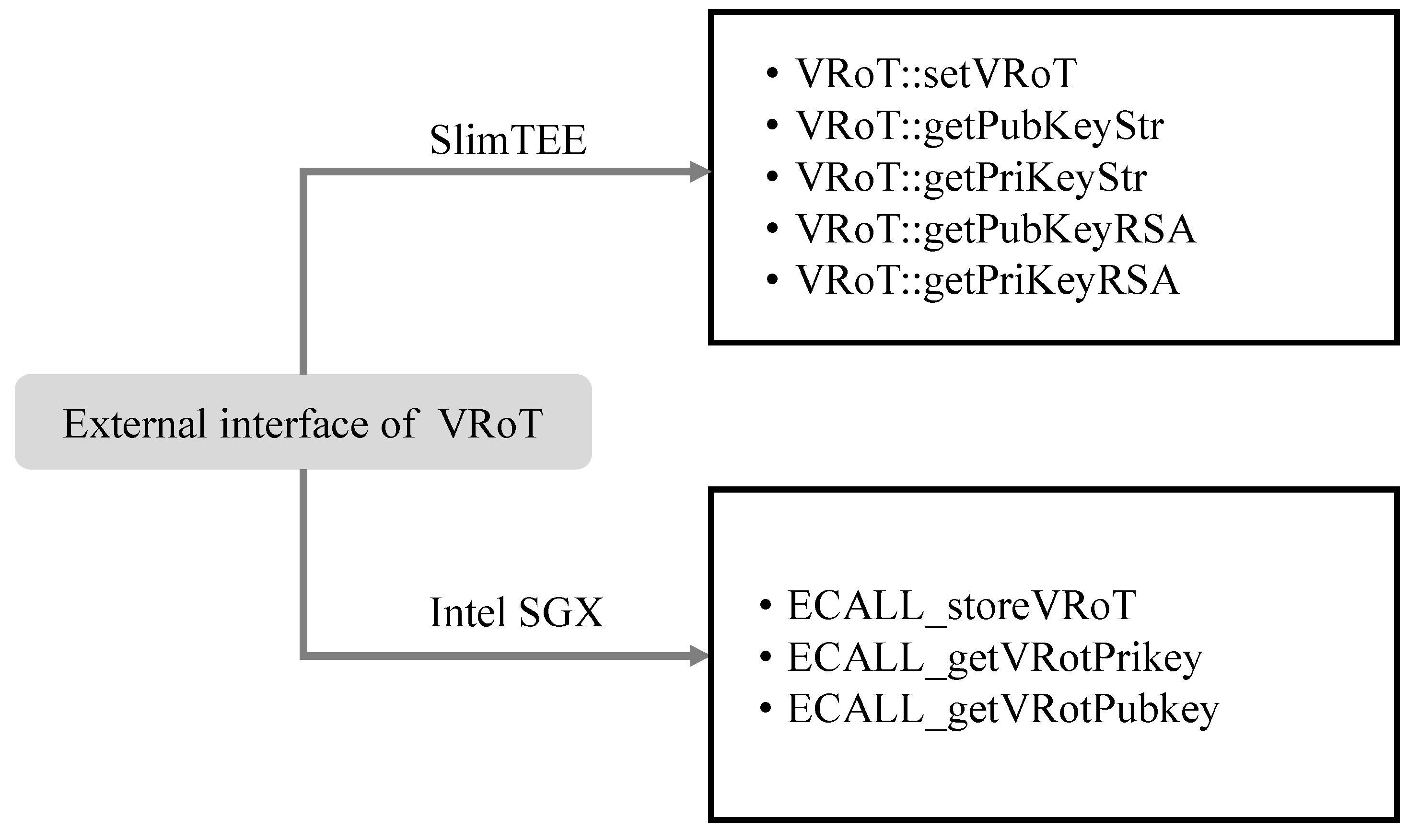
6.1. Implementation Details
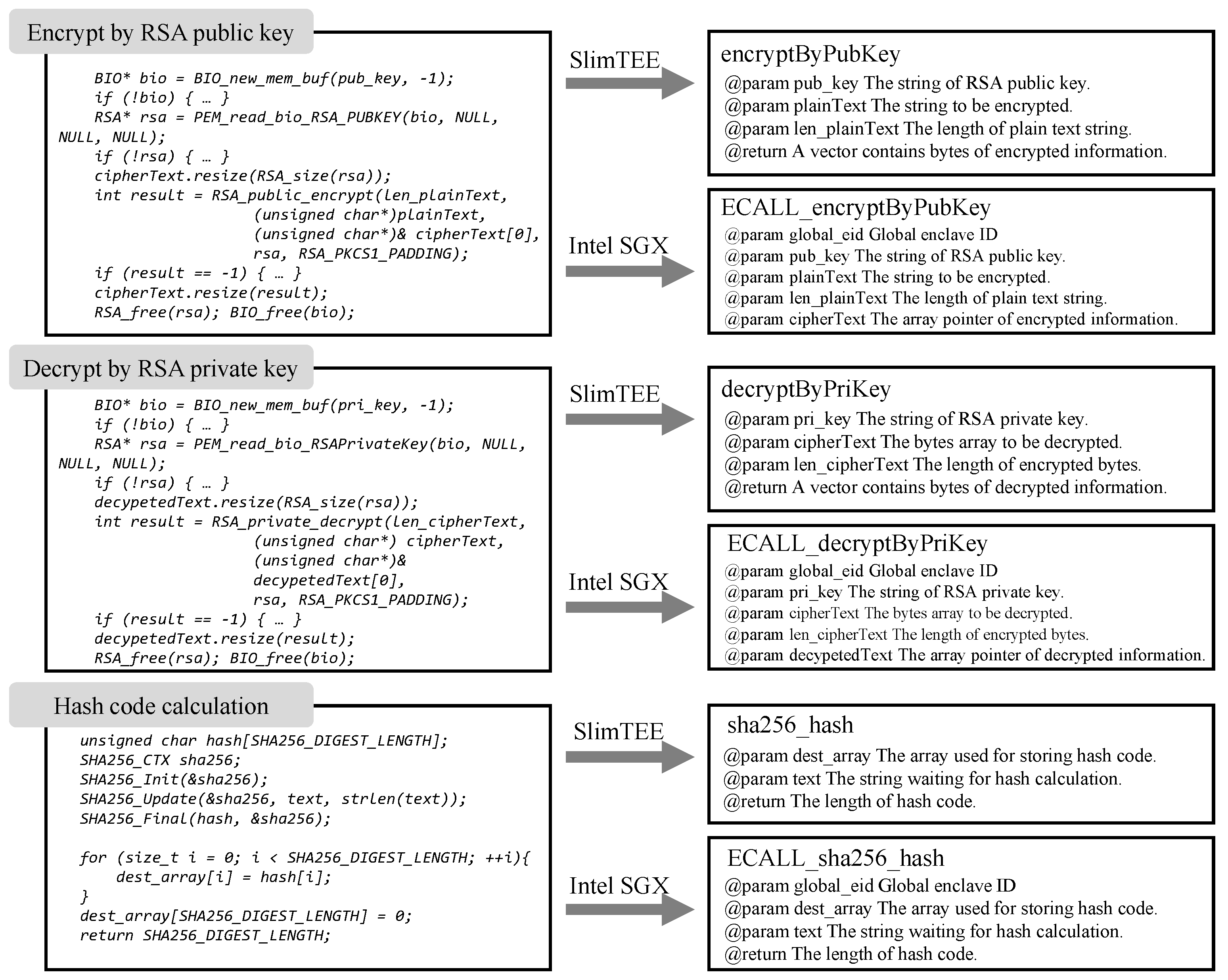
- SlimTEE: Inspired by OP-TEE, we created a simple Trusted Execution Environment named SlimTEE based on C++ and OpenSSL library. Its security is higher than bare metal operation systems but inferior to complicated TEEs like AMD SEV or Intel SGX. It provides core functions like isolating data from directly reading/writing, calculating hash code for strings, and encrypting/decrypting information by RSA keys.
- Intel SGX: Intel Software Guard Extensions (SGX) (Intel, Santa Clara, CA, USA) is an innovative security technology developed by Intel that enables the creation of a secure area within the processor called an enclave. This enclave is isolated from the normal operation of the computer and is designed to keep the code and data it processes safe from unauthorized access or tampering, even if the operating system or other software is compromised. The official Intel SGX SDK for Linux provides developers with the ability to compile projects in SGX simulation mode, without the need for physical processors to be equipped with SGX, since only certain models of Intel processors are equipped with SGX. Our experiments are conducted based on the SGX simulation mode.
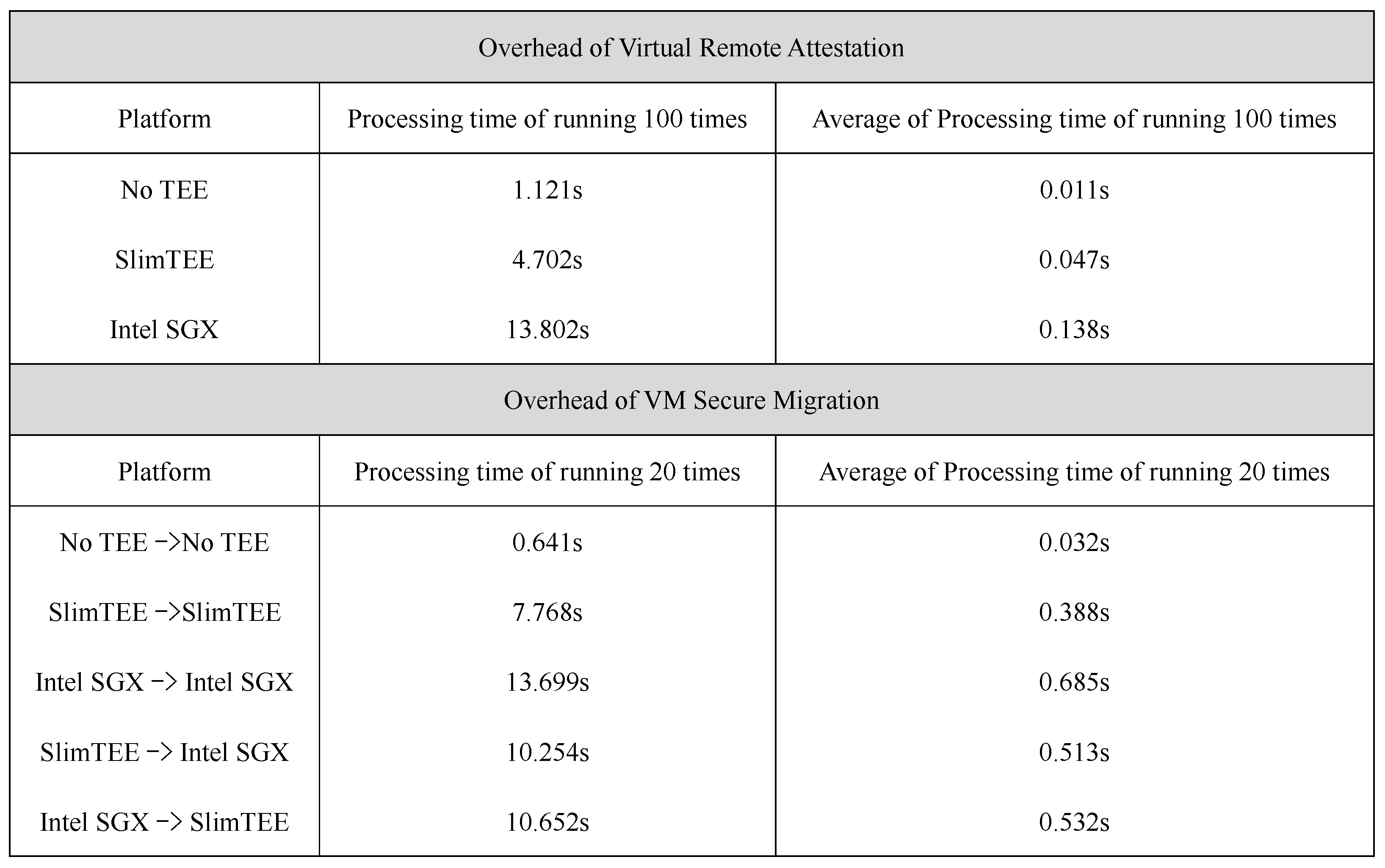
6.2. Evaluation
6.3. Security
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cao, J.; Zhu, T.; Ma, R.; Guo, Z.; Zhang, Y.; Li, H. A Software-Based Remote Attestation Scheme for Internet of Things Devices. IEEE Trans. Dependable Secur. Comput. 2022, 20, 1422–1434. [Google Scholar] [CrossRef]
- Kuang, B.; Fu, A.; Gao, Y.; Zhang, Y.; Zhou, J.; Deng, R.H. FeSA: Automatic Federated Swarm Attestation on Dynamic Large-Scale IoT Devices. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2954–2969. [Google Scholar] [CrossRef]
- Dushku, E.; Rabbani, M.M.; Conti, M.; Mancini, L.V.; Ranise, S. SARA: Secure asynchronous remote attestation for IoT systems. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3123–3136. [Google Scholar] [CrossRef]
- Nunes, I.D.O.; Eldefrawy, K.; Rattanavipanon, N.; Steiner, M.; Tsudik, G. {VRASED}: A Verified {Hardware/Software}{Co-Design} for Remote Attestation. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 1429–1446. [Google Scholar]
- Nunes, I.D.O.; Dessouky, G.; Ibrahim, A.; Rattanavipanon, N.; Sadeghi, A.R.; Tsudik, G. Towards systematic design of collective remote attestation protocols. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–9 July 2019; pp. 1188–1198. [Google Scholar]
- Perez, R.; Sailer, R.; van Doorn, L. vTPM: Virtualizing the trusted platform module. In Proceedings of the 15th USENIX Security Symposium, Vancouver, BC, Canada, 31 July–4 August 2006; pp. 305–320. [Google Scholar]
- Zheng, W.; Wu, Y.; Wu, X.; Feng, C.; Sui, Y.; Luo, X.; Zhou, Y. A survey of Intel SGX and its applications. Front. Comput. Sci. 2021, 15, 1–15. [Google Scholar] [CrossRef]
- Sev-Snp, A. Strengthening VM isolation with integrity protection and more. White Pap. January 2020, 53, 1450–1465. [Google Scholar]
- Cheng, P.C.; Ozga, W.; Valdez, E.; Ahmed, S.; Gu, Z.; Jamjoom, H.; Franke, H.; Bottomley, J. Intel TDX Demystified: A Top-Down Approach. arXiv 2023, arXiv:2303.15540. [Google Scholar] [CrossRef]
- Narayanan, V.; Carvalho, C.; Ruocco, A.; Almási, G.; Bottomley, J.; Ye, M.; Feldman-Fitzthum, T.; Buono, D.; Franke, H.; Burtsev, A. Remote attestation of SEV-SNP confidential VMs using e-vTPMs. arXiv 2023, arXiv:2303.16463. [Google Scholar]
- Kucab, M.; Boryło, P.; Chołda, P. Remote attestation and integrity measurements with Intel SGX for virtual machines. Comput. Secur. 2021, 106, 102300. [Google Scholar] [CrossRef]
- Cheng, J.; Zhang, K.; Tu, B. Remote Attestation of Large-scale Virtual Machines in the Cloud Data Center. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 20–22 October 2021; pp. 180–187. [Google Scholar]
- Ozga, W.; Fetzer, C. TRIGLAV: Remote Attestation of the Virtual Machine’s Runtime Integrity in Public Clouds. In Proceedings of the 2021 IEEE 14th International Conference on Cloud Computing (CLOUD), Chicago, IL, USA, 5–11 September 2021; pp. 1–12. [Google Scholar]
- Coppolino, L.; D’Antonio, S.; Formicola, V.; Mazzeo, G.; Romano, L. Vise: Combining intel sgx and homomorphic encryption for cloud industrial control systems. IEEE Trans. Comput. 2020, 70, 711–724. [Google Scholar] [CrossRef]
- Pinto, S.; Santos, N. Demystifying arm trustzone: A comprehensive survey. ACM Comput. Surv. (CSUR) 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Birkholz, H.; Thaler, D.; Richardson, M.; Smith, N.; Pan, W. Remote ATtestation procedureS (RATS) Architecture. RFC 9334. 2023. Available online: https://www.rfc-editor.org/info/rfc9334 (accessed on 1 January 2023).
- Feng, W.; Qin, Y.; Zhao, S.; Feng, D. AAoT: Lightweight attestation and authentication of low-resource things in IoT and CPS. Comput. Netw. 2018, 134, 167–182. [Google Scholar] [CrossRef]
- De Oliveira Nunes, I.; Jakkamsetti, S.; Rattanavipanon, N.; Tsudik, G. On the TOCTOU problem in remote attestation. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 15–19 November 2021; pp. 2921–2936. [Google Scholar]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Schwarz, M.; Lipp, M.; Moghimi, D.; Van Bulck, J.; Stecklina, J.; Prescher, T.; Gruss, D. ZombieLoad: Cross-privilege-boundary data sampling. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 753–768. [Google Scholar]
- Qiu, P.; Gao, Q.; Liu, C.; Wang, D.; Lyu, Y.; Li, X.; Wang, C.; Qu, G. PMU-Spill: A New Side Channel for Transient Execution Attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2023, 70, 5048–5059. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yuan, J.; Shen, Y.; Xu, R.; Wei, X.; Liu, D. Elevating Security in Migration: An Enhanced Trusted Execution Environment-Based Generic Virtual Remote Attestation Scheme. Information 2024, 15, 470. https://doi.org/10.3390/info15080470
Yuan J, Shen Y, Xu R, Wei X, Liu D. Elevating Security in Migration: An Enhanced Trusted Execution Environment-Based Generic Virtual Remote Attestation Scheme. Information. 2024; 15(8):470. https://doi.org/10.3390/info15080470
Chicago/Turabian StyleYuan, Jie, Yinghua Shen, Rui Xu, Xinghai Wei, and Dongxiao Liu. 2024. "Elevating Security in Migration: An Enhanced Trusted Execution Environment-Based Generic Virtual Remote Attestation Scheme" Information 15, no. 8: 470. https://doi.org/10.3390/info15080470
APA StyleYuan, J., Shen, Y., Xu, R., Wei, X., & Liu, D. (2024). Elevating Security in Migration: An Enhanced Trusted Execution Environment-Based Generic Virtual Remote Attestation Scheme. Information, 15(8), 470. https://doi.org/10.3390/info15080470





