Abstract
Revocable attribute-based encryption (RABE) provides greater flexibility and fine-grained access control for data sharing. However, the revocation process for most RABE schemes today is performed by the cloud storage provider (CSP). Since the CSP is an honest and curious third party, there is no guarantee that the plaintext data corresponding to the new ciphertext after revocation is the same as the original plaintext data. In addition, most attribute-based encryption schemes suffer from issues related to key escrow. To overcome the aforementioned issues, we present an efficient RABE scheme that supports data integrity while also addressing the key escrow issue. We demonstrate the security for our system, which is reduced to the decisional q-parallel bilinear Diffie-Hellman exponent (q-PBDHE) assumption and discrete logarithm (DL) assumption. The performance analysis illustrates that our scheme is efficient.
1. Introduction
Cloud storage services provide major advantages in data management as data continues to grow and digitization processes accelerate, and more and more companies and individuals are choosing to employ cloud storage services to satisfy their data storage demands. Compared with traditional local storage, cloud storage has the advantages of high storage efficiency, high scalability, and low management overhead. However, cloud storage providers (CSP) may attempt to access sensitive data, which can lead to potential privacy risks [1,2,3]. The key to solving this problem is to store the data in ciphertext. The traditional method can only achieve one-to-one sharing. If the file is shared with several users, it must be encrypted multiple times, which lacks flexibility and fine-grained access control. Attribute-based encryption (ABE) [4] technology effectively solves this problem; it can provide file confidentiality and a one-to-many sharing mechanism over encrypted data. Data in an ABE scheme is encrypted using access policy. The user can decrypt and achieve plaintext when the user’s attributes match the access policy in the ciphertext. Therefore, the user fully utilizes cloud storage services to maintain data security and privacy. Ciphertext-policy attribute-based encryption (CP-ABE) [5] and key-policy attribute-based encryption (KP-ABE) [6] are two types of ABE. In CP-ABE, the user’s attribute set corresponds to the key, and the access policy corresponds to the ciphertext, while the opposite is true for KP-ABE. The user can decrypt only when the attributes match the access policy.
Currently, CP-ABE is widely used in healthcare, financial services, e-commerce, and other scenarios, but in many practical application scenarios, CP-ABE is still confronted with numerous challenges, such as user revocation [7] and key escrow issues. Revocable attribute-based encryption restricts access to data by controlling user attributes such as job titles or security clearance levels. It allows data owners to revoke access to certain users when necessary, thus providing greater flexibility and fine-grained control over data sharing, enabling greater data security and privacy.
1.1. Related Works
More and more programs are now focusing on the issue of revocation. Pirretti et al. [8] developed a revocable encryption scheme that supports indirect revocation, where each attribute in the scheme contains a valid time range and the authority periodically updates the attribute and redistributes the user’s key information. Li et al. [9] constructed a revocable scheme that introduces the concept of user groups to achieve efficient user revocation, where the group administrator updates the keys of unrevoked users when any user leaves, and the scheme outsources part of the computation to the CSP to reduce the user computation burden. In [10], an efficient direct RABE scheme was provided. In the scheme, a user revocation list and a time interval are added. The revoked users are added to the revocation list and can not decrypt the ciphertext after the key time expires, and the key of the unrevoked users will be updated. Xiang et al. [11] adopted version control technology to support real-time revocation and the private key for the unrevoked user is updated by the subset covering technique. In [12], the data owner does not need to be online during the revocation process, but the unrevoked user is required to update the decryption key frequently, and the data storage center needs to re-encrypt the ciphertext, which is computationally intensive and not suitable for resource-constrained environments. Xiong et al. [13] combined revocable encryption with cloud-assisted IoT, where the trusted authority center manages a user revocation list. The identities and current time nodes of these users will be added to the list once they have been deleted from the system. Using key update parameters generated by the trusted authority center, users who are not revoked will update their own decryption keys. Lan et al. [14] constructed an efficient revocable ABE scheme with rich attribute representation. The proxy server is in charge of partial decryption and receives a conversion key from the key generating center. When a user’s attributes change or he or she is deleted from the system, both the decryption key and the conversion key for unrevoked users need to be updated. The above scheme achieves revocation by maintaining a revocation list or updating the key periodically, but the length of the list increases with the rapid change of personnel flow, and this method requires the user to update the key frequently online at any time, which has a large computational overhead.
Sahai et al. [15] introduced the ciphertext delegation technique, in which the cloud server achieves user revocation by re-encrypting the ciphertext, but the scheme cannot be applied in CP-ABE. In [16], a server-assisted RABE scheme is constructed, in which the ciphertext should be converted by the CSP using the relevant conversion key, and if the user is removed from the system, the CSP will no longer be able to help him or her to convert the ciphertext. The CP-ABE scheme in [17] applied a modular ciphertext delegation method that allows third parties to convert ciphertexts under a stricter policy, enabling user revocation. Ma et al. [18] constructed a revocable, secure data deletion and authentication CP-ABE scheme. The scheme uses attribute association trees to reconstruct new access policy and re-encrypts ciphertext data when a user is deleted, so that the deleted user is unable to decrypt the new ciphertext. In [19], a traceable RABE scheme is constructed by uploading the revocation list along with the ciphertext to CSP. When a user revokes from the system, the CSP updates the ciphertext using the update key transmitted by the authorization center, and the user’s identity is related to the leaf node to achieve user tracking. In [20], the CSP re-encrypts the ciphertext by combining the original ciphertext with the updated material broadcast by the authority center using the ciphertext delegation algorithm. These schemes use the CSP to update the ciphertext to achieve revocation, which saves computing resources to a certain extent. However, since the proxy third-party server is honest and curious, there is no guarantee that the plaintext data corresponding to the new ciphertext after revocation is consistent with the original plaintext data, which is what we call the data integrity issue. Aiming to resolve this problem, Ge et al. [21] used a user-verifiable approach to construct a new RABE scheme that supports data integrity. Based on Waters’ scheme [22], they encrypted both the plaintext data and a random value, allowing the user to check the consistency for the plaintext data. However, the scheme has a key escrow problem.
In addition, ABE schemes also come with the key escrow problem. In the traditional ABE scheme, the key generation center (KGC) generates the decryption keys for the users, which means that the KGC has the ability to access and decrypt data. To overcome this issue, the schemes in [23,24] generate decryption keys for users by introducing multiple authorization centers, each of which can only calculate partial keys. The scheme in [25] used an unmanaged key issue protocol executed between the CSP and the KGC, but the computational cost is too high. The scheme in [26] used an unmanaged key issue protocol executed between the KGC and the user, solving the key escrow issue effectively. Recently, some novel ABE schemes were presented, such as CP-ABE with shared decryption [27], ABE with privacy protection and accountability [28], multi-authority CP-ABE [29,30], and revocable blockchain-aided ABE [31].
Therefore, to address the integrity issue and the key escrow issue in revocation, we constructed an efficient revocable ABE scheme that supports data integrity and solves the key escrow issue. The specific contributions are as follows:
- Data integrity: Under the new access policy, when the CSP performs the revocation operation to generate the ciphertext, the user can check whether the plaintext corresponding to the new ciphertext is the same as the original encrypted plaintext.
- Key-escrow free: Attribute authority was introduced, and a secure 2PC protocol is executed between the key authority and the attribute authority to generate the user’s private key. Neither side can get the complete private key, which solved the key escrow problem.
- Security and efficiency: Based on the assumption of decisional q-PBDHE, our scheme is secure under chosen plaintext attacks. Performance analysis illustrates the practicability and effectiveness of the proposed scheme.
1.2. Organization
We review some knowledge about topics like bilinear maps and linear secret sharing in Section 2. We provide an overview of the security model and the system model in Section 3. We present an efficient RABE scheme based on the Waters’ scheme in Section 4. Section 5 and Section 6 discuss the safety and feasibility of our scheme, respectively. Finally, we summarize our work in Section 7.
2. Preliminaries
We focus on describing the specific construction of our RABE scheme, and the notation used in the paper is explained in Table 1.

Table 1.
Symbols Definition.
Bilinear maps The bilinear map has the following properties:
- Bilinear: , holds.
- Non-degeneracy: .
- Computability: can be effectively calculated.
Access policy The set is called monotonous if and , we have . The access policy is the monotone set in all non-empty subsets for P, i.e., . The sets are referred to as the authorization sets, otherwise, the sets are referred to as the unauthorized sets.
Linear secret sharing scheme (LSSS) A linear secret sharing scheme on meets the following two conditions:
- Each participant’s share is the component of the vector on .
- Define a share generating matrix and for all , we define a function , where is the number of rows in . Randomly choosing vector , where is a secret shared value, was picked randomly. represents secret share values shared according to .
LSSS satisfies the linear reconfiguration property that members in the authorization set can recover secret as follows: For an access policy , let be any authorized set, and let , we can compute the constant set in polynomial time using the knowledge of linearity algebra such that , where . In this paper, stands for access policy, and s can be recovered only when the attributes of the user meet .
Discrete logarithm assumption (DL) Let be a group of prime order , and be a generator. The DL assumption says, that given for randomly chosen , for the PPT algorithm , is negligible.
Decisional q-Parallel Bilinear Diffie-Hellman Exponent assumption (q-PBDHE) Let be chosen randomly, and be a bilinear map. Given tuple:
The decisional q-PBDHE assumption means that there is no PPT algorithm to distinguish the distribution of and , where be a random element in . The decisional q-PBDHE assumption was first defined and proved to be safe in [22].
3. System Model
We will give the roles of each entity, the formal definition, and the security model for the RABE scheme.
Our RABE system includes five entities: Data Owner (DO), Data User (DU), Cloud Service Provider (CSP), Key Authority (KA), and Attribute Authority (AA), which is illustrated in Figure 1.
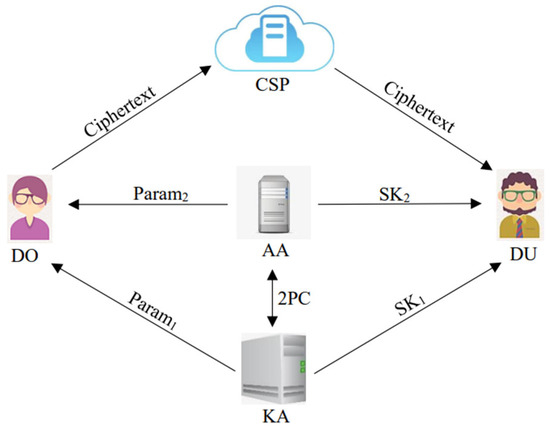
Figure 1.
System structure for RABE.
DO: The DO sets an access policy for the data, generates file ciphertext using a combination of symmetric encryption (AES) and the CP-ABE algorithm, and finally sends the complete ciphertext to the CSP.
CSP: The CSP stores ciphertext uploaded by the DO and performs the revocation operation.
DU: The DU downloads ciphertext from the CSP. If the attributes of the DU match the access policy embedded in the ciphertext, he or she can decrypt the data to obtain plaintext.
KA/AA: The KA and AA are responsible for system initialization and generating user private keys.
3.1. Formal Definition
The algorithms in the RABE scheme are as below:
- (1)
- . This algorithm generates the public key and private key of the KA according to the security parameter and system attribute set .
- (2)
- . This algorithm generates the public key and private key of the AA according to .
- (3)
- . This algorithm generates the user’s private key through a secure 2PC protocol.
- (4)
- . This algorithm encrypts data files and uploads the ciphertext to the CSP.
- (5)
- . This algorithm inputs and , and outputs a shared data file or a special symbol .
- (6)
- . This algorithm inputs and a revocation access policy , and it outputs a revoked ciphertext .
- (7)
- . This algorithm inputs updated private key , and , and outputs a shared data file or a special symbol .
3.2. Security Model
We define two security models for the RABE scheme, namely the selective plaintext attack and the data integrity attack. These are described through the interactive attack games (Game-I and Game-II) between adversary and challenger .
Game-I describes a security game under selective plaintext attack.
- Initialization: chooses a challenge access policy and sends it to challenger .
- Setup: executes the algorithm to obtain the master public key and returns it to .
- Private key query phase 1: chooses a user attribute set , which requires that cannot meet . runs the , and generates the private key and returns it to .
- Challenge: chooses two data files and of equal length to . chooses randomly and encrypts to get the challenge ciphertext . returns the ciphertext to .
- Private key query phase 2: Similar to the previous stage, continues to answer ’s query.
- Guess: outputs its guess for .
We define ’s advantage in the above game as .
Definition 1.
Our RABE scheme is selective plaintext attack secure, if for all PPT adversary , the advantage is negligible.
Game-II describes a security game under data integrity attack.
- Setup: executes algorithm to get public parameter and returns it to .
- Private key query phase 1: can perform the key extraction query on the user attribute set . returns to by executing the algorithm.
- Challenge: sends the data file and a challenge access policy to . Then sends challenge ciphertext to by executing the algorithm.
- Private key query phase 2: Similar with the previous stage, continues to answer ’s query.
- Guess: outputs attribute set and revoked ciphertext . wins the integrity game if .
We define to represent the adversary ’ s advantage in the above game.
Definition 2.
The proposed scheme achieves the data integrity of ciphertext after revocation if for all PPT adversary , the advantage is negligible.
4. Our RABE Construction
- (1)
- . This algorithm inputs system security parameter , and attribute set , generates two cyclic groups , with prime order and bilinear map . Let be a generator in . The KA randomly selects , , hash function and , then the algorithm outputsThe KA publishes and keeps secretly, where .
- (2)
- . The AA selects randomly, outputs , . The AA keeps secretly and publishes . Then we havewhere .
- (3)
- . In this algorithm, the KA and the AA use the secure 2PC protocol to generate the user’s private key. Firstly, the KA inputs , the AA inputs , the protocol computes and returns to the AA, where the KA does not know and the AA does not know , then the AA and the KA interact to generate :
- The AA selects at random, the AA computes , and generates the knowledge proof of , then sends and to the KA.
- The KA selects at random, computes , , then transmits and to the AA.
- The AA selects at random, computes , then sends and to KA.
- The KA computes , sends and to the AA.
- The AA calculates , and then the AA transmits to the DU.
- The KA computes and sends to the DU.
- The DU’s final private key is . The above protocol is illustrated in Figure 2.
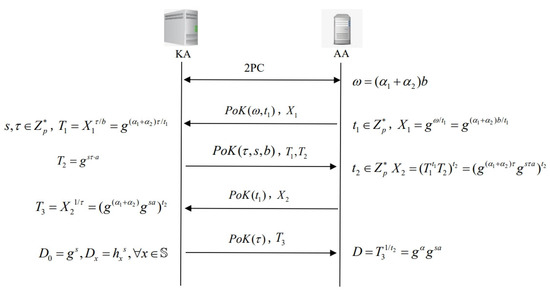 Figure 2. The proposed key issuing protocol.
Figure 2. The proposed key issuing protocol.
- (4)
- . This algorithm inputs the shared data file , and access policy , for each row of , the function associates rows of to attributes, which is . The algorithm encrypts the file using the AES algorithm, then gets the shared data ciphertext , where is a symmetric key. The DO selects a vector , randomly, computes , . ThenLet , then the DO sends to the CSP for storage.
- (5)
- . The DU runs the algorithm and decrypts the ciphertext . The algorithm inputs private key , . If the attribute set satisfies , lets , calculates the constant such that , the algorithm computesThen checks if , outputs and decrypts the shared file further. Otherwise, outputs . If does not satisfy , decryption fails.
- (6)
- . The CSP runs the algorithm. It inputs , a revocation access policy , and for each row of , defines the function . It outputs a revoked ciphertext under a revoked access policy , where , , . Then, it randomly selects and for each , computes , . The algorithm computes :where is the identity element of . Then the algorithm computes :And computes :Let , outputs .
- (7)
- . The algorithm inputs , and , verifies whether , if not, outputs . Then, if the set of attribute of meets , let , and there is a constant such that . Then the DU computes:otherwise, outputs . Finally, checks if , outputs , and decrypts the shared file further. Otherwise, outputs .
Kim et al. [17] proved that is a valid access policy with respect to a LSSS scheme. Therefore is a valid revoked ciphertext.
5. Scheme Analysis
5.1. Correctness Analysis
In algorithm:
5.2. Security Analysis
Theorem 1.
Assuming that the decisional q-PBDHE assumption holds, then our RABE construction described above is semantic secure under chosen plaintext attack.
Proof.
Assume a PPT adversary exists with a non-negligible advantage to break the security for our RABE construction, so we construct a polynomial time simulator using to break the decisional q-PBDHE assumption.
- Init. picks a bilinear map , and randomly. exposes:randomly selects , if , take , let ; if , take and let , picks a challenge access policy to .
- Setup. picks randomly, computes . This implicitly sets . orchestrates group element as follows: For attributes , chooses a value at random, let be the set of such that . sets asBecause of the randomness of , is distributed randomly. If , then . The simulator chooses a hash function and randomly, returns the public parametersto .
- Private key query phase 1. submits attribute set , where does not satisfy . Simulator chooses at random and finds the vector such that . For , we have . computesthus, implicitly definingBy defining so that contains , the unknown term can be eliminated when constructing . computesNow compute for . If there is no that makes , then ; if there is multiple that makes , since cannot simulate , it is necessary to ensure that the expression for does not contain terms shaped like . Because , everything in this form can be cancelled. Let and calculateThe simulator returns to .
- Challenge. selects two messages and of equal length. Simulator chooses a coin randomly and encrypts the file using the AES algorithm to generate the shared data ciphertext , where is a symmetric key, then . chooseswhere randomly, is the secret value to be shared. In addition, chooses , at random, we define to be the set of all satisfying such that , , compute. The simulator returns to .
- Private key query phase 2. Similar with the previous stage, continues to answer ’s query.
- Guess. outputs guess of . outputs when , it means ; outputs when , it means .When , does not obtain any information from , so .When , guesses , .When , knows the ciphertext of , because the advantage of is , . When , guesses , .The advantages of obtained from the above areTherefore, Theorem 1 holds. □
Theorem 2.
The proposed scheme supports data integrity under the DL assumption.
Proof.
Assume a PPT adversary exists with a non-negligible advantage to break the security for our RABE construction, so we can construct a polynomial time simulator using to break the DL assumption.
- Setup. obtains a discrete logarithmic tuple , and attempts to compute the value . generates public parameters through the following steps. sets a bilinear map , selects , , and computes , , . picks hash function at random, and returnsto adversary .
- Private key query phase 1. selects an attribute set , and executes and returns to .
- Challenge. submits and a challenge access policy to . execute , where , , . returns to .
- Private key query phase 2. Similar to the previous stage, continues to answer ’s query.
- Output. outputs a revoked ciphertext , where , . wins if and .
If wins, the simulator selects the attribute set that meets access policy . generates the private key , decrypts the ciphertext to get the symmetric key , and then gets the . According to , computes . Since , so that means . Finally, the simulator gets .
Therefore, Theorem 2 holds. □
6. Performance Analysis
The performance of our scheme is analyzed in terms of functionality, computational cost, and experimental perspectives.
6.1. Functional Analysis
The functional analysis between our scheme and the schemes in [21,24,26] is shown in Table 2. None of the comparison schemes can simultaneously meet the three functional requirements listed in the table, that is, cannot simultaneously meet integrity, key escrow, and revocation. The scheme in this paper can simultaneously meet the above three functional requirements and adopts LSSS with strong expression ability as the access policy. Therefore, from the perspective of functionality, our scheme is more suitable for practical application.

Table 2.
Functionality.
6.2. Computation Analysis
In this section, we compare our scheme with other schemes in terms of calculated costs, as shown in Table 3. It can be seen from Table 3, in the key generation phase, the computational cost required by our scheme is consistent with that in [21,24], and lower than that of [26]. In the encryption stage, our scheme has more advantages than those in [21,24,26]. At the decryption stage, the computational cost of our scheme is consistent with reference [24] and lower than [21,26]. In the revocation phase, the calculation cost of our scheme is lower than that of [21], which is almost the same as that of [26]. In general, the approach in this paper has a low computing overhead, where represents the number of rows of the matrix in LSSS, represents the number of leaf nodes in the access tree, both and correspond to the number of attributes, so their meanings in Table 3 are the same.

Table 3.
Calculations cost.
In Table 3, represents the number of attributes for the user, represents the number of rows of the matrix in LSSS, represents the number of leaf nodes in the access tree, represents exponential operations in group , represents exponential operations in group , represents bilinear pair operation.
6.3. Experimental Analysis
In this section, in order to better evaluate the performance of our scheme, we conducted simulation experiments between our scheme and the scheme in reference [21] (abbreviated as RI-CP-ABE). The experimental environment configuration is as follows: AMD Ryzen 5 5600U with Radeon Graphics 2.30 GHz, 16.0 GB RAM, Windows 10 operating system. Our scheme used the IntelliJIDEA2018 tool, jPBC2.0 open-source encryption library, and we selected a Type A elliptic curve with group order bit length of 512 bits for the experiment, the expression is . We used JAVA language for programming, and the LSSS access matrix is programmed in the form of a binary tree.
We conducted simulation experiments in the aspects of system establishment time, key generation time, encryption time, decryption time, revocation time, and decryption after revocation time. Since only scheme RI-CP-ABE has integrity, therefore, we compared our scheme with RI-CP-ABE. The specific algorithm of reference in RI-CP-ABE is shown in Appendix A. Because our computer runs with limited memory, the number of attributes in the access policy is set to 4, 8, 16, and 32 (the number of attributes in the system). The experiment was conducted 100 times in total, and the average value of the experimental results of 100 times was taken as the final result of this experiment to ensure the accuracy of the experiment.
The time cost of system setup is shown in Figure 3, indicating that the calculation cost of the method in this article is basically the same as that described in the literature RI-CP-ABE. The system key generation time overhead is illustrated in Figure 4. The results of experimental simulations demonstrate that the calculation cost in our scheme is more than that of the literature in RI-CP-ABE. Because we introduced the 2PC protocol to solve the key escrow issue, which guards against the misuse of users’ private keys, it is more useful in real-world applications. The figure shows that the time growth rates of the two systems are nearly equal as the number of attributes increases. Furthermore, the key is generated only once, and the impact on the overall system efficiency can be ignored.
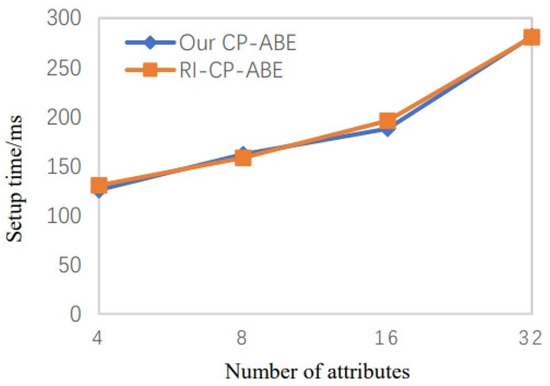
Figure 3.
Setup time when the number of attributes increases [21].
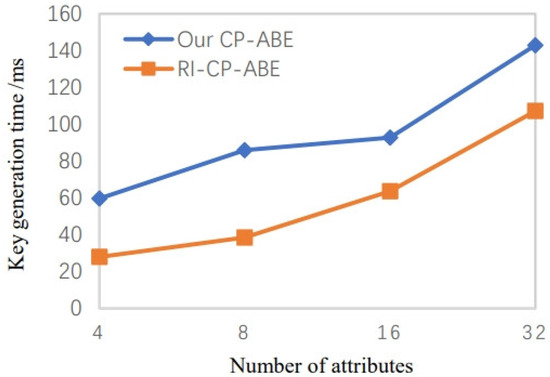
Figure 4.
Key generation time when the number of attributes increases [21].
The system encryption time and the initial decryption time overhead are shown in Figure 5 and Figure 6. The figures demonstrate that compared to the technique in RI-CP-ABE, ours takes much less encryption and decryption time. Therefore, our scheme significantly reduces the computing burden on users.
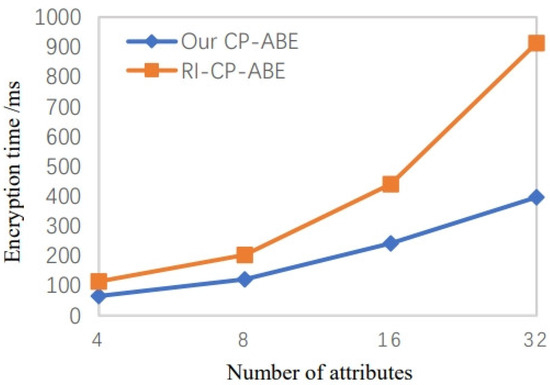
Figure 5.
Encryption time when the number of attributes increases [21].
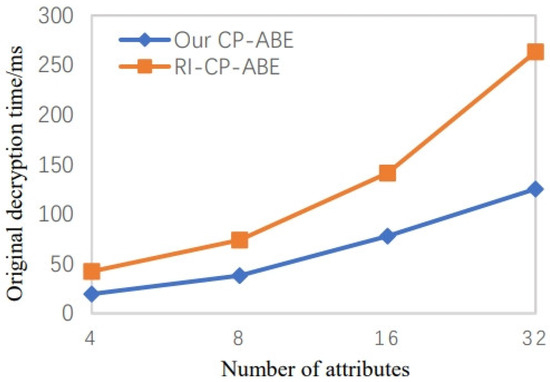
Figure 6.
Original decryption time when the number of attributes increases [21].
The system revocation time and the decryption time after the user is revoked overhead are illustrated in Figure 7 and Figure 8, respectively. Our scheme requires less time calculation in the user revocation stage and the decryption step than RI-CP-ABE. As a result, our scheme has higher efficiency in practical applications.
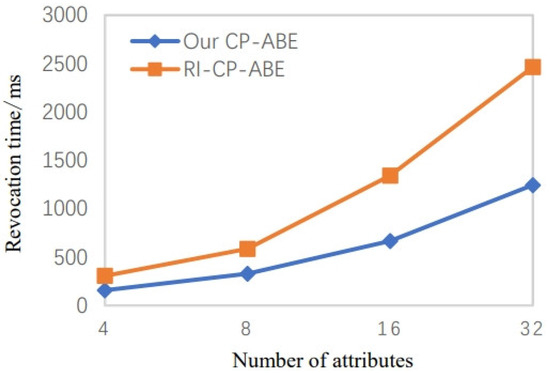
Figure 7.
Revocation time when the number of attributes increases [21].
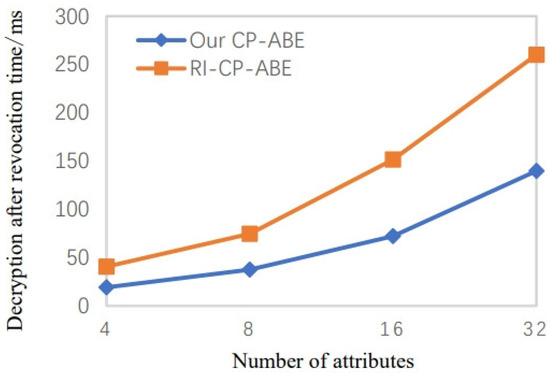
Figure 8.
Decryption time after revoking user when the number of attributes increases [21].
7. Conclusions and Prospect
In this article, we construct an efficient RABE scheme that supports data integrity and solves the key escrow problem. User revocation is achieved using the ciphertext delegation algorithm, and the user can check whether the plaintext corresponding to the new ciphertext is the same as the original plaintext. Compared with the previous scheme with integrity verification, our scheme is more efficient. In addition, we introduced an attribute authority, and the key authority and attribute authority jointly generate private keys for users, which solve the key escrow issue effectively. Finally, the safety of the scheme is proved under the standard model and we give a performance analysis of our scheme. The scheme in this paper only supports the integrity verification under user revocation. Our next research will address the question of how to support the integrity verification under attribute revocation.
Author Contributions
Conceptualization and methodology, M.H.; software and validation, Y.Z. and M.Z.; writing—original draft preparation, Y.L.; writing—review and editing, M.H. and Y.L.; funding acquisition, M.H. and Y.Z.; proof reading, B.Y.; validation of results, Y.L. and M.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, grant number 62202375, the Natural Science Basic Research Program of Shaanxi Province, grant number 2021MJ-514 and 2022JQ-604, the Young Talent Fund of Association for Science and Technology in Shaanxi, China, grant number 20220134.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Appendix A
To facilitate the readers’ understanding, we give the algorithm flow of reference [21] as follows:
- (1)
- The authority center generates a bilinear pairing tuple . Chooses random value and a hash function . Sets the master secret key and public parameters
- (2)
- : The authority center chooses a random value , and computes .
- (3)
- : On input a message m and an access policy , is an matrix and associates each row of to an attribute. The algorithm selects two random vectors and . For each row of , computes and , . Randomly chooses for each and . Then computes . .Outputs the ciphertext as .
- (4)
- : On input a secret key and a ciphertext , the recipient first checks whether . If , outputs an error symbol . Otherwise, finds the set and . Computes constant element , such that . Then the recipient computesChecks if , outputs . Otherwise outputs an error symbol .
- (5)
- : On input a ciphertext and a revocation access policy , where and are and matrixes, outputs a revoked ciphertext for access policy . Sets aswhere is the first column of . Note that is an matrix, where , . Computes ,where is the identity element of group .Then selects a random vector . For each row of , computes , . Randomly chooses for each . Then computes a random ciphertext asThen, computesThe value can be computed in the same manner. Sets . Finally, outputs the revoked ciphertext
- (6)
- : On input a secret of attribute set , an original ciphertext and a revoked ciphertext , it verifies whether . If not, outputs an error symbol and abort. Then, it checks whether . If , outputs an error symbol and abort. Otherwise, finds the set and .Computes constant element , such that . Then, it computesChecks if , outputs . Otherwise outputs an error symbol .
References
- Zhang, L.; Xiong, H.; Huang, Q.; Li, J.; Choo, K.; Li, J. Cryptographic Solutions for Cloud Storage: Challenges and Research Opportunities. IEEE Trans. Serv. Comput. 2022, 15, 567–587. [Google Scholar] [CrossRef]
- Kang, Z.; Li, J.; Shen, J.; Han, J.; Zuo, Y.; Zhang, Y. TFS-ABS: Traceable and Forward-Secure Attribute-based Signature Scheme with Constant-Size. IEEE Trans. Knowl. Data Eng. 2023, 35, 9514–9530. [Google Scholar] [CrossRef]
- Chen, Y.; Li, J.; Liu, C.; Han, J.; Zhang, Y.; Yi, P. Efficient Attribute Based Server-Aided Verification Signature. Trans. Serv. Comput. 2022, 15, 3224–3232. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy Identity-Based Encryption. In Proceedings of the International Conference on Theory and Applications of Cryptographic Techniques (EUROCRYPT), Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security (CCS), Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 89–98. [Google Scholar]
- Li, J.; Yao, W.; Han, J.; Zhang, Y.; Shen, J. User Collusion Avoidance CP-ABE with Efficient Attribute Revocation for Cloud Storage. IEEE Syst. J. 2018, 12, 1767–1777. [Google Scholar] [CrossRef]
- Pirretti, M.; Traynor, P.; McDaniel, P.; Waters, B. Secure Attribute-Based Systems. In Proceedings of the 13th ACM Conference on Computer and Communications Security (CCS), Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 99–112. [Google Scholar]
- Li, J.; Yao, W.; Zhang, Y.; Qian, H.; Han, J. Flexible and Fine-Grained Attribute-Based Data Storage in Cloud Computing. IEEE Trans. Serv. Comput. 2017, 10, 785–796. [Google Scholar] [CrossRef]
- Liu, J.K.; Yuen, T.H.; Zhang, P.; Liang, K. Time-based Direct Revocable Ciphertext-Policy Attribute-Based Encryption with Short Revocation List. In Proceedings of the 16th International Conference on Applied Cryptography and Network Security (ACNS), Leuven, Belgium, 2–4 July 2018; Springer: Cham, Switzerland, 2018; pp. 516–534. [Google Scholar]
- Xiang, G.; Li, B.; Fu, X.; Xia, M.; Ke, W. An Attribute Revocable CP-ABE Scheme. In Proceedings of the 2019 Seventh International Conference on Advanced Cloud and Big Data (CBD), Suzhou, China, 21–22 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 198–203. [Google Scholar]
- Lan, C.; Wang, C.; Li, H.; Liu, L. Comments on “Attribute-Based Data Sharing Scheme Revisited in Cloud Computing”. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2579–2580. [Google Scholar] [CrossRef]
- Xiong, H.; Huang, X.; Yang, M.; Wang, L.; Yu, S. Unbounded and Efficient Revocable Attribute-Based Encryption with Adaptive Security for Cloud-Assisted Internet of Things. IEEE Int. Things J. 2022, 9, 3097–3111. [Google Scholar] [CrossRef]
- Lan, C.; Liu, L.; Wang, C.; Li, H. An efficient and revocable attribute-based data sharing scheme with rich expression and escrow freedom. Inf. Sci. 2023, 624, 435–450. [Google Scholar] [CrossRef]
- Sahai, A.; Seyalioglu, H.; Waters, B. Dynamic credentials and ciphertext delegation for attribute-based encryption. In Proceedings of the 32nd Annual International Cryptology Conference (CRYPTO), Santa Barbara, CA, USA, 19–23 August 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 199–217. [Google Scholar]
- Qin, B.; Zhao, Q.; Zheng, D.; Cui, H. (Dual) server-aided revocable attribute-based encryption with decryption key exposure resistance. Inf. Sci. 2019, 490, 74–92. [Google Scholar] [CrossRef]
- Kim, J.; Susilo, W.; Baek, J.; Nepal, S.; Liu, D. Ciphertext-delegatable CP-ABE for a Dynamic Credential: A Modular Approach. In Proceedings of the Australasian Conference on Information Security and Privacy (ACISP), Christchurch, New Zealand, 3–5 July 2019; Springer: Cham, Switzerland, 2019; pp. 3–20. [Google Scholar]
- Ma, J.; Wang, M.; Xiong, J.; Hu, Y. CP-ABE-based secure and verifiable data deletion in cloud. Secur. Commun. Netw. 2021, 2021, 1–14. [Google Scholar] [CrossRef]
- Han, D.; Pan, N.; Li, K. A Traceable and Revocable Ciphertext-policy Attribute-based Encryption Scheme Based on Privacy Protection. IEEE Trans. Dependable Secur. Comput. 2022, 19, 316–327. [Google Scholar] [CrossRef]
- Deng, S.; Yang, G.; Dong, W.; Xia, M. Flexible revocation in ciphertext-policy attribute-based encryption with verifiable ciphertext delegation. Multimed. Tools Appl. 2023, 82, 22251–22274. [Google Scholar] [CrossRef]
- Ge, C.; Susilo, W.; Baek, J.; Liu, Z.; Xia, J.; Fang, L. Revocable Attribute-Based Encryption with Data Integrity in Clouds. IEEE Trans. Depend. Secure Comput. 2021, 19, 2864–2872. [Google Scholar] [CrossRef]
- Waters, B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization. In Proceedings of the 14th International Conference on Practice and Theory in Public Key Cryptography (PKC), Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Chase, M.; Chow, S. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM Conference on Computer and Communications Security (CCS), Chicago, IL, USA, 9–13 November 2009; ACM: New York, NY, USA, 2009; pp. 121–130. [Google Scholar]
- Varri, U.; Pasupuleti, S.; Kadambari, K.V. Key-Escrow Free Attribute-Based Multi-Keyword Search with Dynamic Policy Update in Cloud Computing. In Proceedings of the 2020 20th IEEE/ACM International Symposium on Cluster, Cloud and Internet Computing (CCGRID), Melbourne, VIC, Australia, 11–14 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 450–458. [Google Scholar]
- Hur, J. Improving Security and Efficiency in Attribute-Based Data Sharing. IEEE Trans. Knowl. Data Eng. 2013, 25, 2271–2282. [Google Scholar] [CrossRef]
- Zhang, R.; Li, J.; Lu, Y.; Han, J.; Zhang, Y. Key escrow-free attribute-based encryption with user revocation. Inf. Sci. 2022, 600, 59–72. [Google Scholar] [CrossRef]
- Chen, N.; Li, J.; Zhang, Y.; Guo, Y. Efficient CP-ABE Scheme with Shared Decryption in Cloud Storage. IEEE Trans. Comput. 2022, 71, 175–184. [Google Scholar] [CrossRef]
- Li, J.; Zhang, Y.; Ning, J.; Huang, X.; Poh, G.; Wang, D. Attribute Based Encryption with Privacy Protection and Accountability for CloudIoT. IEEE Trans. Cloud Comput. 2022, 10, 762–773. [Google Scholar] [CrossRef]
- Banerjee, S.; Roy, S.; Odelu, V.; Das, A.; Chattopadhyay, S.; Rodrigues, J.; Park, Y. Multi-Authority CP-ABE-Based user access control scheme with constant-size key and ciphertext for IOT deployment. J. Inf. Secur. Appl. 2020, 53, 102503. [Google Scholar] [CrossRef]
- Reena Catherine, A.; Shajin Nargunam, A. Multi authority ciphertext-policy attribute-based encryption for security enhancement in cloud storage unit. Sustain. Energy Technol. Assess. 2022, 53, 102556. [Google Scholar] [CrossRef]
- Guo, Y.; Lu, Z.; Ge, H.; Li, J. Revocable Blockchain-Aided Attribute-Based Encryption with Escrow-Free in Cloud Storage. IEEE Trans. Comput. 2023, 72, 1901–1912. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).