A Conceptual Consent Request Framework for Mobile Devices
Abstract
:1. Introduction
- We propose the CURLED conceptual framework, which incorporates four different consent request variations for mobile apps: custom, functionality-based, app-based, and usage-based;
- We demonstrate the applicability of the different consent mechanisms in a mobile setting by incorporating them into our City Explorer mobile app prototype; and
- We perform a comparative analysis of the effectiveness of the various consent requests by conducting a usability evaluation.
2. Related Work
3. Methodology and Background
3.1. Methodology
3.2. GDPR Consent Request Requirements
3.3. Exemplifying Use Case
Eva and Peter, who moved to Vienna for work, want to adjust to the new city as easily as possible. They install all the relevant apps offered by the city of Vienna and are presented with the CURLED-based personal data processing consent request. Peter is a recent supporter of the citizen science concept and would like to contribute his data to improve the city of Vienna via its apps. Eva does not mind providing her data to have a better city but would rather agree to a consent request tailored to her needs based on app usage.
4. The Conceptual Consent Request Framework & The City Explorer App
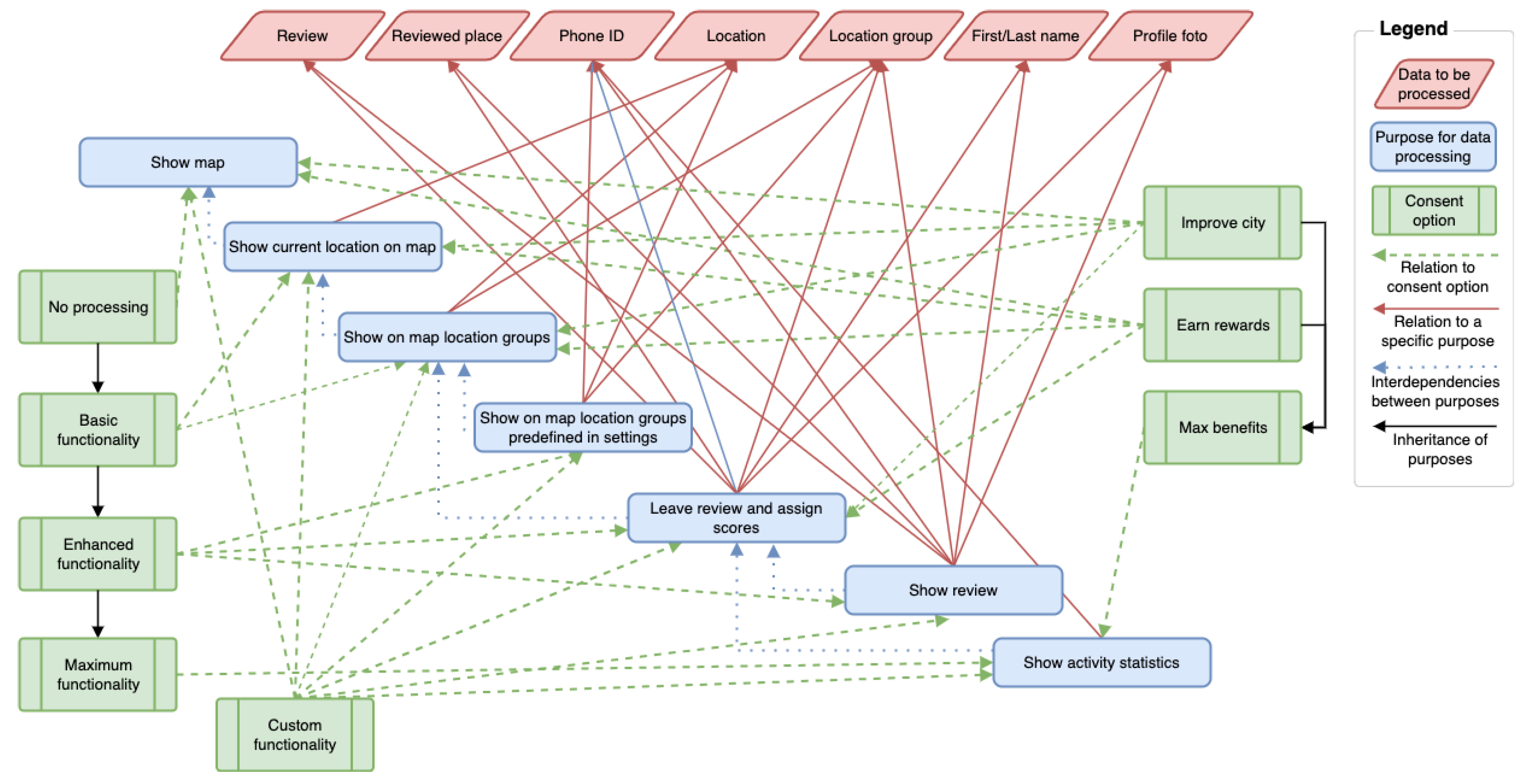
4.1. General CURLED Framework Concept
4.1.1. Custom Consent Request
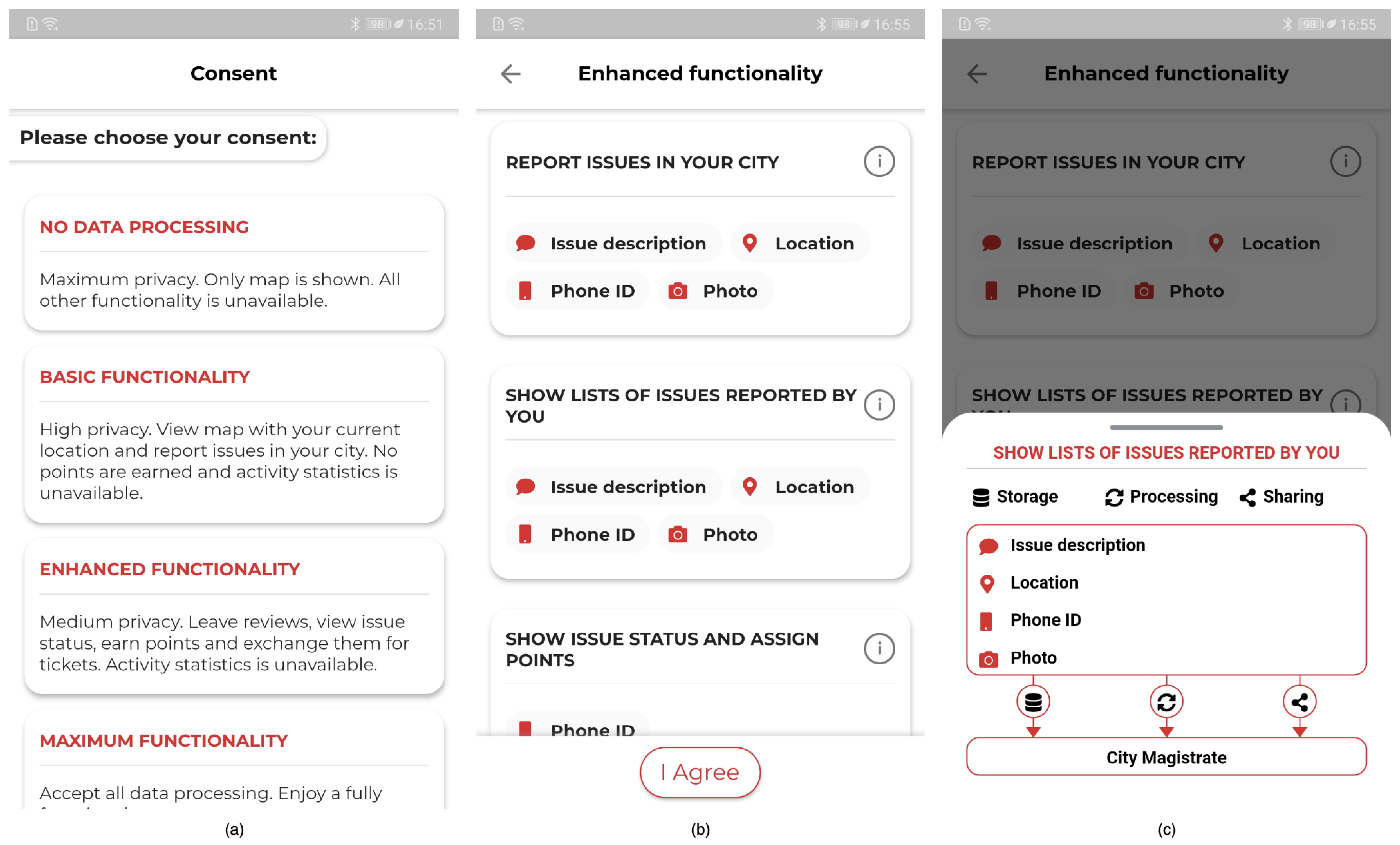
4.1.2. Functionality- and App-Based Consent Requests
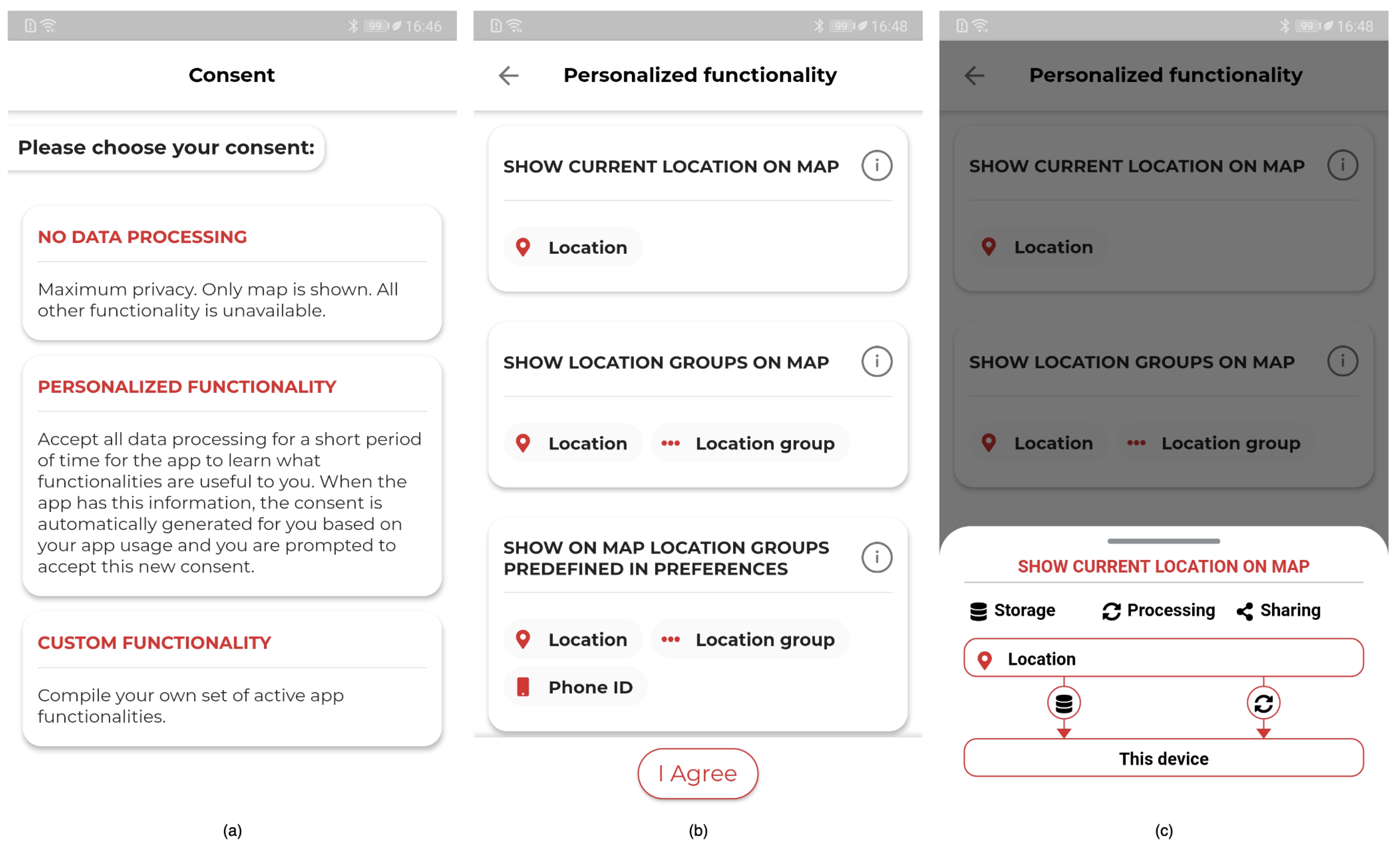
4.1.3. Usage-Based Consent Request
4.2. City Explorer App Prototype
4.3. CURLED-Based Consent Requests Applied to the City Explorer App
4.3.1. Custom Consent Request
4.3.2. Functionality-Based Consent Request
4.3.3. App-Based Consent Request
4.3.4. Usage-Based Consent Request
4.4. CURLED Conceptual Framework Reusability
4.4.1. Consent Content Compilation
- Identification of all purposes for data processing based on the app concept.
- Definition of the data, the processing of which, is needed for each purpose.
- Identification of the required data processing.
- Specification of the interdependencies among purposes.
- Selection of a suitable consent request approach, from the ones presented in Section 4.3, based on the information received from the previous steps.
- Where necessary, definition of the inheritance relations among purposes that belong to certain consent options of the selected consent request approach.
4.4.2. Application Programming Interface for Consent Requests
5. Usability Evaluation
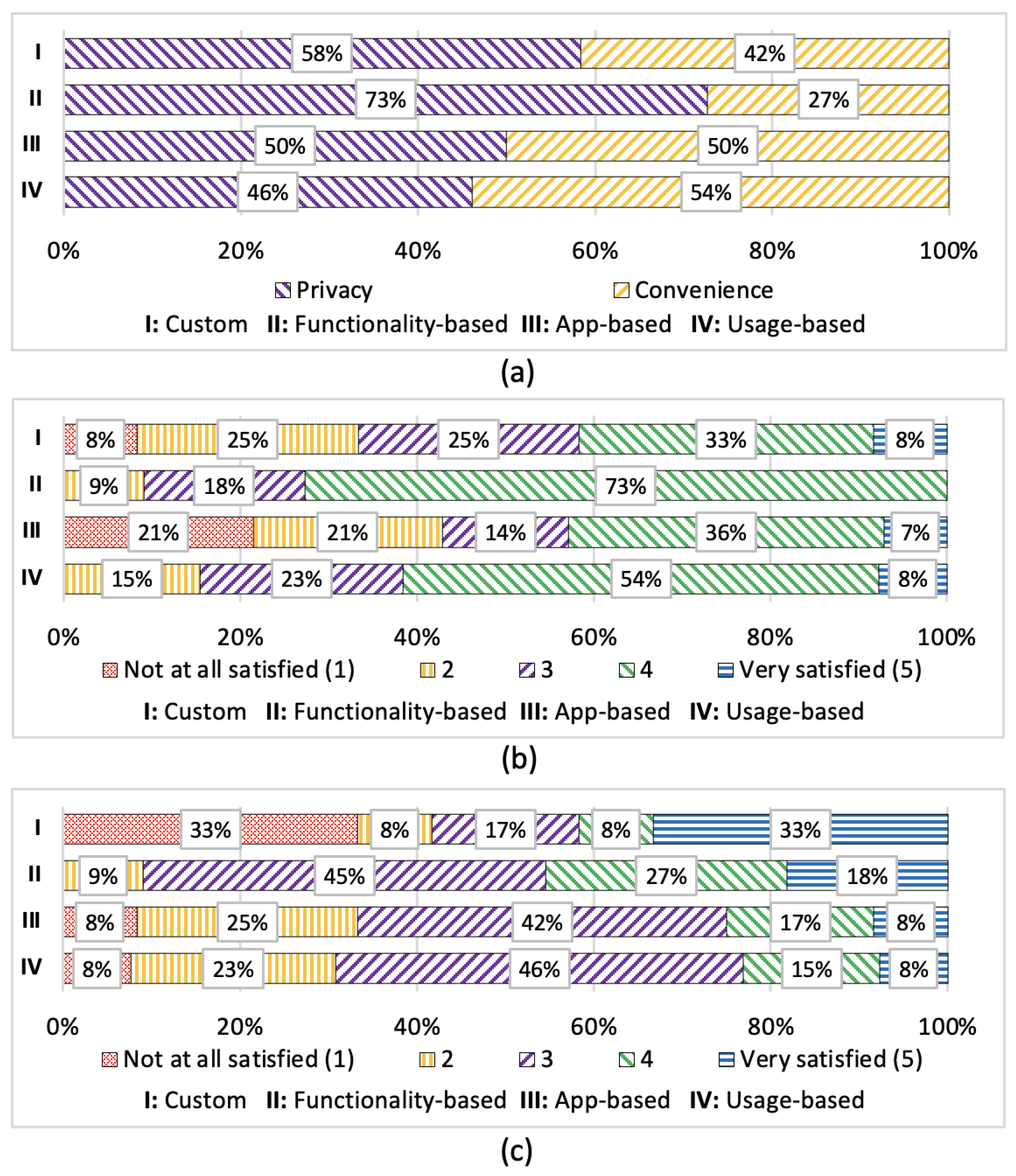
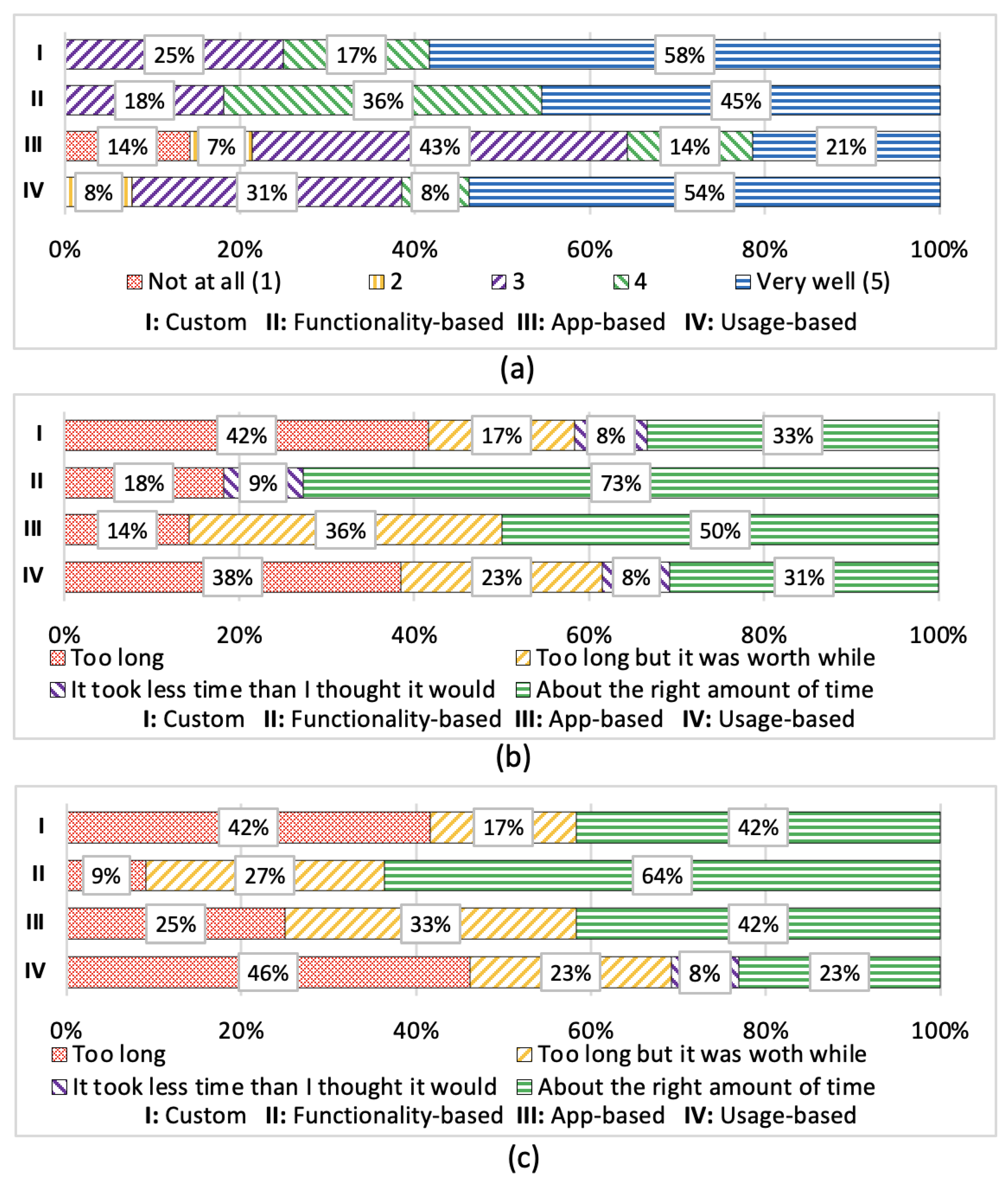
5.1. Overall Satisfaction and Memorability
5.2. Time Perception
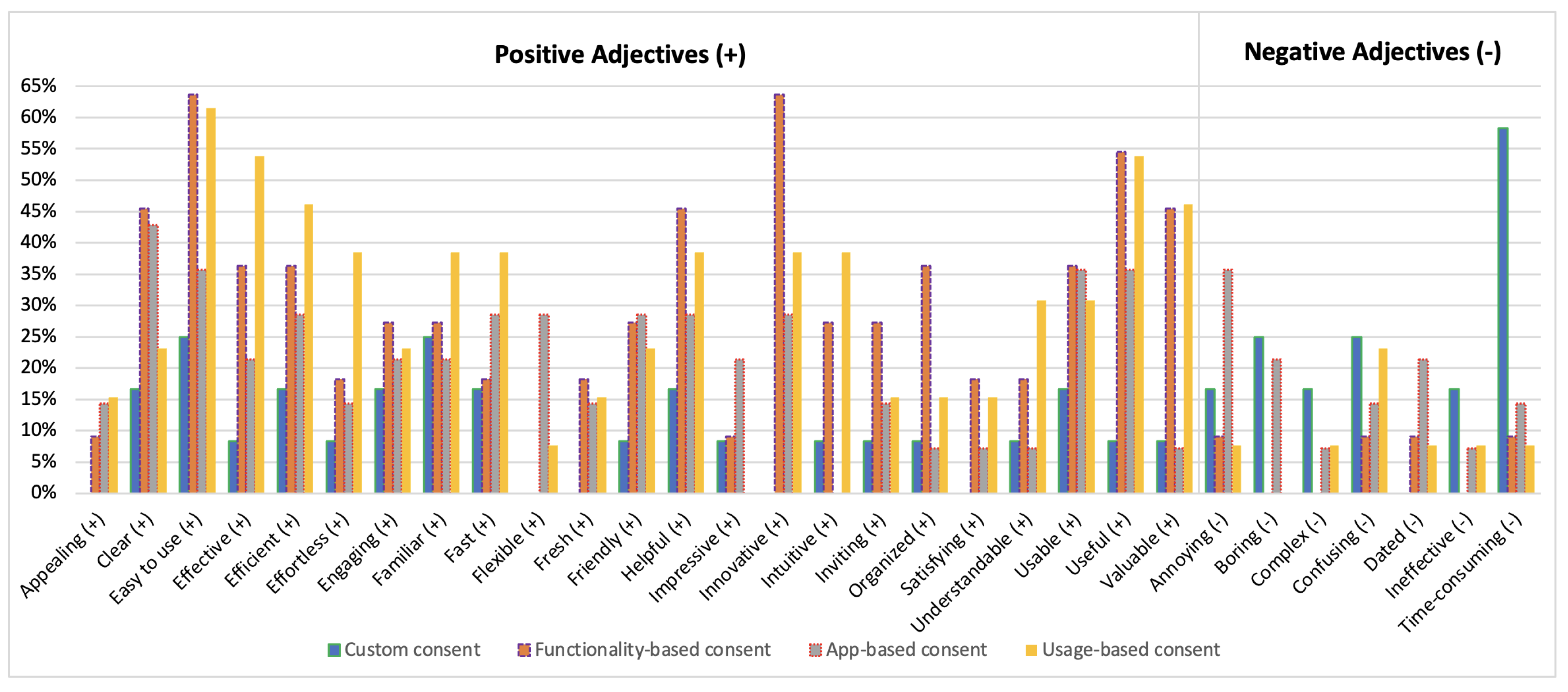
5.3. Adjectival Description
5.4. System Usability Scale Scores
6. Discussion
6.1. Functional Alignment of Consent Request Information
6.2. Customization and Ease of Use
6.3. Task Completion Time
6.4. App Benefits and User Concerns
6.5. Cognitive Load
6.6. UI Design and Data Processing Description
7. Limitations
8. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Consent Request Framework: CURE Component
Appendix A.1. Component Installation
Appendix A.2. Component Usage
- List<Consent> consents
- List<Purpose> purposes
- List<Data> data
- List<Data> activities
- List<Data> processors
- Function(int consentId, List<int> purposeIds) onClose
Appendix A.3. Parameter Description
- class Consent {
- final int id; // The unique identifier of a consent.
- final String name; // Consent name.
- final String description; // Consent description.
- final List<int> purposeIds; // List of purpose ids.
- final bool isSelected; // Is consent selected?
- final bool isCustomisable; // Is consent customisable?
- final int orderIndex; // Specifies the custom consent order.
- }
- class Purpose {
- final int id; // The unique identifier of a purpose.
- final String name; // Purpose name.
- final String name; // Purpose name.
- final bool isSelectable; // Identifies if a purpose is
- // selectable.
- // It’s used when a purpose belongs
- // to a customisable consent.
- final bool isSelected; // Is purpose selected?
- final List<int> parentIds; // Specifies dependent purposes. It’s
- // used for automatic selection or
- // deselection of dependent purposes.
- final List<Activity> activities; // List of data processing activities.
- }
- class Activity {
- final String processor; // Data processor
- // name.
- final Map<String, List<String>> processorActivity; // List of data
- // processing
- // activities per
- // processor.
- }
- class Data {
- final String id; // The unique identifier of a data category.
- final IconData icon; // The icon of a data category.
- final String label; // The name of a data category.
- }
- class Data {
- final String id; // The unique identifier of a data processing
- // activity.
- final IconData icon; // The icon of a data processing activity.
- final String label; // The name of a data processing activity.
- }
- class Data {
- final String id; // The unique identifier of a data processor.
- final String label; // The name of a data processor.
- }
- int consentId; // Consent id that was selected by a user.
- List<int> purposeIds; // Purpose ids that were selected by a user.
Appendix B. Questionnaire
Appendix B.1. City Explorer App
- 1.
- Overall, how satisfied are you with the City Explorer app?◯ 1—Not at all satisfied ◯ 2 ◯ 3 ◯ 4 ◯ 5—Very satisfied
- 2.
- Read the following statements about the City Explorer app and mark your immediate response. If you feel that you cannot respond, mark the center point of the scale.
- (a)
- I think I would like to use the City Explorer app frequently.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (b)
- I found the City Explorer app unnecessarily complex.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (c)
- I thought the City Explorer app was easy to use.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (d)
- I think I would need Tech Support to be able to use the City Explorer app.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (e)
- I found various functions of the City Explorer app were well integrated.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (f)
- I thought there was too much inconsistency in the City Explorer app.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (g)
- I would imagine that most people would learn to use the City Explorer app very quickly.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (h)
- I found the City Explorer app very cumbersome to use.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (i)
- I felt very confident using the City Explorer app.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- (j)
- I need to learn a lot about the City Explorer app before I could effectively use it.◯ 1—Strongly disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly agree
- 3.
- What was your impression of the time it took you to complete the tasks?◯ Too long ◯ Too long but it was worth while ◯ About the right amount of time ◯ It took less time than I thought it would
Appendix B.2. Consent Request for Personal Data Processing
- 1.
- Since most of the City Explorer app functionalities require personal data processing, you were asked to provide your consent for your data processing. How well do you remember giving consent for your data processing? (Questions 2–15 are shown to the participants only if they answer that they remember giving their consent.)◯ 1—Not at all (i.e., I do not remember giving any consent for data processing) ◯ 2 ◯ 3 ◯ 4 ◯ 5—Very Well
- 2.
- Have you agreed to the processing of your “location” for the app to show your location on the map?◯ Yes ◯ No
- 3.
- Have you agreed to the processing of your “phone ID”, “location”, “first/last name”, and “profile photo” to be able to leave a review about the places on a map?◯ Yes ◯ No
- 4.
- Have you agreed to the processing of your “first/last name”, “profile photo”, “review”, and “location group” for your review to be shown together with the reviews of other users?◯ Yes ◯ No
- 5.
- Have you agreed to the processing of your “phone ID” to be able to see your activity statistics (i.e., amount of scores you’ve earned, number of reported issues, and number of reviews you’ve provided)?◯ Yes ◯ No
- 6.
- Have you agreed to the processing of the following data: “location”, “photo”, “issue description”, “phone ID” to be able to report an issue in your city?◯ Yes ◯ No
- 7.
- Have you agreed to the processing of the following data: “location”, “photo”, “issue description”, “phone ID” to be able to see the list of issues in your city reported by you?◯ Yes ◯ No
- 8.
- Have you agreed to the processing of your “phone ID” to see the status of issues reported by you?◯ Yes ◯ No
- 9.
- Have you agreed to the processing of your “phone ID”, “first/last name”, and “home address” for the purpose of exchanging your points for tickets to museums?◯ Yes ◯ No
- 10.
- Have you agreed to the processing of your “home address”, so it can be filled in automatically from your profile?◯ Yes ◯ No
- 11.
- Have you agreed to the processing of your “first/last name”, so it can be filled in automatically from your profile?◯ Yes ◯ No
- 12.
- Have you agreed to the processing of your “profile photo” so it can be visible in the reviews you’ve provided?◯ Yes ◯ No
- 13.
- Overall, how satisfied are you with the way the City Explorer app requested your consent for your data processing?◯ 1—Not at all satisfied ◯ 2 ◯ 3 ◯ 4 ◯ 5—Very satisfied
- 14.
- Read the following statements about the consent request of the City Explorer app and mark your immediate response. If you feel that you cannot respond, mark the center point of the scale.
- (a)
- I think I would like to use apps with a consent request as in the City Explorer app frequently.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (b)
- I found the consent request of the City Explorer app unnecessarily complex.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (c)
- I thought the consent request of the City Explorer app was easy to use.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (d)
- I think I would need Tech Support to be able to use the consent request of the City Explorer app.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (e)
- I found various functions of the consent request of the City Explorer app were well integrated.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (f)
- I thought there was too much inconsistency in the consent request of the City Explorer app.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (g)
- I would imagine that most people would learn to use the consent request of the City Explorer app very quickly.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (h)
- I found the consent request of the City Explorer app very cumbersome to use.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (i)
- I felt very confident using the consent request of the City Explorer app.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- (j)
- I need to learn a lot about the consent request of the City Explorer app before I could effectively use it.◯ 1—Strongly Disagree ◯ 2 ◯ 3 ◯ 4 ◯ 5—Strongly Agree
- 15.
- What was your impression of the time it took you to give your consent for the data processing?◯ Too long ◯ Too long but it was worth while ◯ About the right amount of time ◯ It took less time than I thought it would
Appendix B.3. Demographic Data
- What is your gender?◯ Male ◯ Female
- What is your age?◯ less than 16 years old ◯ 16–25 years old ◯ 26–35 years old ◯ 36–45 years old ◯ 46–55 years old ◯ 55 years +
- What is your nationality? ____________________
- What is the highest level of education you have completed?◯ Some high school, no diploma ◯ High school graduate, diploma or the equivalent Trade/technical/vocational training ◯ Some college, no degree ◯ Bachelor’s degree ◯ Mater’s degree ◯ Doctorate degree
- On average, how many hours per day do you spend on the Internet?◯ Less than 1 hour a day 1–3 hours ◯ 3–6 hours ◯ 6–8 hours ◯ More than 8 hours a day
- What is your preferred device to surf the Internet?◯ Desktop computer ◯ Lapto ◯ Table ◯ Smartphone
- How would you assess your current skills for using smartphones?◯ Novice ◯ Advanced beginner ◯ Competent ◯ Proficient ◯ Expert
- On average, how many hours per day do you spend on the smartphone?◯ Less than 1 hour a day ◯ 1–3 hours ◯ 3–6 hours ◯ 6–8 hours ◯ More than 8 hours a day
- In general, which is more important to you: CONVENIENCE or PRIVACY?◯ Convenience ◯ Privacy
References
- Kranig, T. Report of the Bavarian State Office for Data Protection Supervision; Technical Report; Bavarian State Office for Data Protection Supervision: Ansbach, Germany, 2019. [Google Scholar]
- European Data Protection Board. Belgian DPA Imposes €50,000 Fine on Family Service; European Data Protection Board: Brussels, Belgium, 2021. [Google Scholar]
- European Data Protection Board. Norwegian DPA: Order to Improve Solutions for Consent; European Data Protection Board: Brussels, Belgium, 2021. [Google Scholar]
- Steinsbekk, K.S.; Myskja, B.K.; Solberg, B. Broad consent versus dynamic consent in biobank research: Is passive participation an ethical problem? Eur. J. Hum. Genet. 2013, 21, 897–902. [Google Scholar] [CrossRef]
- Costante, E.; Sun, Y.; Petković, M.; den Hartog, J. A Machine Learning Solution to Assess Privacy Policy Completeness: (Short Paper). In Proceedings of the 2012 ACM Workshop on Privacy in the Electronic Society, WPES ’12, Raleigh, NC, USA, 15 October 2012; Association for Computing Machinery: New York, NY, USA, 2012; pp. 91–96. [Google Scholar]
- Fabian, B.; Ermakova, T.; Lentz, T. Large-Scale Readability Analysis of Privacy Policies. In Proceedings of the International Conference on Web Intelligence, WI ’17, Leipzig, Germany, 23–26 August 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 18–25. [Google Scholar] [CrossRef]
- Maler, E. Extending the Power of Consent with User-Managed Access: A Standard Architecture for Asynchronous, Centralizable, Internet-Scalable Consent. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; IEEE: New York, NY, USA, 2015; pp. 175–179. [Google Scholar] [CrossRef]
- Schaub, F.; Balebako, R.; Durity, A.L.; Cranor, L.F. A Design Space for Effective Privacy Notices. In Proceedings of the Eleventh USENIX Symposium on Usable Privacy and Security, SOUPS ’15, Ottawa, ON, Canada, 22–24 July 2015; USENIX Association: Berkeley, CA, USA, 2015; pp. 1–17. [Google Scholar]
- Friedman, B.; Howe, D.C.; Felten, E. Informed consent in the Mozilla browser: Implementing value-sensitive design. In Proceedings of the 35th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 10 January 2002; IEEE: Piscataway, NJ, USA, 2002; p. 10. [Google Scholar] [CrossRef]
- Kelley, P.G.; Bresee, J.; Cranor, L.F.; Reeder, R.W. A “Nutrition Label” for Privacy. In Proceedings of the 5th Symposium on Usable Privacy and Security, SOUPS ’09, Mountain View, CA, USA, 15–17 July 2009; Association for Computing Machinery: New York, NY, USA, 2009; pp. 1–12. [Google Scholar] [CrossRef]
- Reeder, R.W.; Bauer, L.; Cranor, L.F.; Reiter, M.K.; Bacon, K.; How, K.; Strong, H. Expandable Grids for Visualizing and Authoring Computer Security Policies. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Florence, Italy, 5–10 April 2008; Association for Computing Machinery: New York, NY, USA, 2008; pp. 1473–1482. [Google Scholar] [CrossRef]
- Railean, A.; Reinhardt, D. Let There Be LITE: Design and Evaluation of a Label for IoT Transparency Enhancement. In Proceedings of the 20th International Conference on Human–Computer Interaction with Mobile Devices and Services Adjunct, Mobile HCI ’18, Barcelona, Spain, 3–6 September 2018; ACM: New York, NY, USA, 2018; pp. 103–110. [Google Scholar]
- Habib, H.; Zou, Y.; Yao, Y.; Acquisti, A.; Cranor, L.; Reidenberg, J.; Sadeh, N.; Schaub, F. Toggles, Dollar Signs, and Triangles: How to (In)Effectively Convey Privacy Choices with Icons and Link Texts. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems, Yokohama, Japan, 8–13 May 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 1–25. [Google Scholar] [CrossRef]
- Cranor, L. Giving notice: Why privacy policies and security breach notifications are not enough. IEEE Commun. Mag. 2005, 43, 18–19. [Google Scholar] [CrossRef]
- Jesus, V.; Silva, C.; Barraca, J.P.; Rosner, G.; Nehme, A.; Waqas, M.; Aguiar, R.L. Permission and Privacy Challenges in Alternate-Tenant Smart Spaces. In Proceedings of the Open Identity Summit 2021, Copenhagen, Denmark, 1–2 June 2021; Gesellschaft für Informatik e.V.: Bonn, Germany, 2021; pp. 217–222. [Google Scholar]
- Drozd, O.; Kirrane, S. I Agree: Customize Your Personal Data Processing with the CoRe User Interface. In Proceedings of the 16th International Conference on Trust and Privacy in Digital Business, TrustBus 2019, Linz, Austria, 26–29 August 2019; Springer International Publishing: Cham, Switzerland, 2019; pp. 17–32. [Google Scholar] [CrossRef]
- Drozd, O.; Kirrane, S. Privacy CURE: Consent Comprehension Made Easy. In Proceedings of the 35th IFIP TC 11 International Conference on ICT Systems Security and Privacy Protection, SEC 2020, Maribor, Slovenia, 21–23 September 2020; Hölbl, M., Rannenberg, K., Welzer, T., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 124–139. [Google Scholar] [CrossRef]
- Liccardi, I.; Pato, J.; Weitzner, D.J. Improving mobile app selection through transparency and better permission analysis. J. Priv. Conf. 2014, 5, 1–55. [Google Scholar]
- Liccardi, I.; Pato, J.; Weitzner, D.J.; Abelson, H.; De Roure, D. No Technical Understanding Required: Helping Users Make Informed Choices about Access to Their Personal Data. In Proceedings of the 11th International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, MOBIQUITOUS ’14, London, UK, 2–5 December 2014; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2014; pp. 140–150. [Google Scholar] [CrossRef]
- McDonald, A.M.; Reeder, R.W.; Kelley, P.G.; Cranor, L.F. A Comparative Study of Online Privacy Policies and Formats. In Proceedings of the 9th International Symposium on Privacy Enhancing Technologies, PETS 2009, Seattle, WA, USA, 5–7 August 2009; Goldberg, I., Atallah, M.J., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 37–55. [Google Scholar]
- Kumar, P. Privacy Policies and Their Lack of Clear Disclosure Regarding the Life Cycle of User Information. In Proceedings of the AAAI Fall Symposium Series, Arlington, VA, USA, 17–19 November 2016. [Google Scholar]
- Council, N.C. DECEIVED BY DESIGN: How Tech Companies Use Dark Patterns to Discourage Us from Exercising Our Rights to Privacy; Technical Report; Norwegian Consumer Council: Oslo, Norway, 2018. [Google Scholar]
- Utz, C.; Degeling, M.; Fahl, S.; Schaub, F.; Holz, T. (Un)Informed Consent: Studying GDPR Consent Notices in the Field. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, CCS ’19, London, UK, 11–15 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 973–990. [Google Scholar] [CrossRef]
- Nouwens, M.; Liccardi, I.; Veale, M.; Karger, D.; Kagal, L. Dark Patterns after the GDPR: Scraping Consent Pop-Ups and Demonstrating Their Influence. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, CHI ’20, Honolulu, HI, USA, 25–30 April 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1–13. [Google Scholar]
- Matte, C.; Bielova, N.; Santos, C. Do Cookie Banners Respect my Choice?: Measuring Legal Compliance of Banners from IAB Europe’s Transparency and Consent Framework. In Proceedings of the 2020 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 17–21 May 2020; IEEE: San Francisco, CA, USA, 2020; pp. 791–809. [Google Scholar]
- Sanchez-Rola, I.; Dell’Amico, M.; Kotzias, P.; Balzarotti, D.; Bilge, L.; Vervier, P.A.; Santos, I. Can I Opt Out Yet? GDPR and the Global Illusion of Cookie Control. In Proceedings of the 2019 ACM Asia Conference on Computer and Communications Security, Asia CCS ’19, Auckland, New Zealand, 9–12 July 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 340–351. [Google Scholar]
- Trevisan, M.; Traverso, S.; Bassi, E.; Mellia, M. 4 Years of EU Cookie Law: Results and Lessons Learned. Proc. Priv. Enhancing Technol. 2019, 2019, 126–145. [Google Scholar] [CrossRef]
- Traverso, S.; Trevisan, M.; Giannantoni, L.; Mellia, M.; Metwalley, H. Benchmark and comparison of tracker-blockers: Should you trust them? In Proceedings of the 2017 Network Traffic Measurement and Analysis Conference (TMA), Dublin, Ireland, 21–23 June 2017; IEEE: Dublin, Ireland, 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Carpineto, C.; Lo Re, D.; Romano, G. Automatic Assessment of Website Compliance to the European Cookie Law with CooLCheck. In Proceedings of the 2016 ACM on Workshop on Privacy in the Electronic Society, WPES ’16, Vienna, Austria, 24 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 135–138. [Google Scholar] [CrossRef]
- Peffers, K.; Tuunanen, T.; Rothenberger, M.; Chatterjee, S. A Design Science Research Methodology for Information Systems Research. J. Manage. Inf. Syst. 2007, 24, 45–77. [Google Scholar] [CrossRef]
- Checkland, P.; Holwell, S. Action research. In Information Systems Action Research: An Applied View of Emerging Concepts and Methods; Springer: Boston, MA, USA, 2007; Volume 13, pp. 3–17. [Google Scholar] [CrossRef]
- Article 29 Data Protection Working Party. Article 29 Working Party Guidelines on Consent under Regulation 2016/6791; Directorate General Justice: Brussels, Belgium, 2018. [Google Scholar]
- Nielsen, J. Enhancing the Explanatory Power of Usability Heuristics. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, CHI ’94, Boston, MA, USA, 24–28 April 1994; Association for Computing Machinery: New York, NY, USA, 1994; pp. 152–158. [Google Scholar] [CrossRef]
- Nielsen, J. Finding Usability Problems through Heuristic Evaluation. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, CHI ’92, Monterey, CA, USA, 3–7 May 1992; Association for Computing Machinery: New York, NY, USA, 1992; pp. 373–380. [Google Scholar] [CrossRef]
- Nielsen, J. Severity Ratings for Usability Problems. 1994. Available online: https://www.nngroup.com/articles/how-to-rate-the-severity-of-usability-problems/ (accessed on 30 June 2021).
- Rebelo, F.; Soares, M. Advances in Ergonomics in Design, Usability & Special Populations: Part II; AHFE Conference: Krakow, Poland, 2014. [Google Scholar]
- Bastien, J.C. Usability testing: A review of some methodological and technical aspects of the method. Int. J. Med. Inform. 2010, 79, e18–e23. [Google Scholar] [CrossRef] [PubMed]
- Charters, E. The use of think-aloud methods in qualitative research: An introduction to think-aloud methods. Brock Educ. J. 2003, 12, 68–82. [Google Scholar] [CrossRef]
- Seidman, I. Interviewing as Qualitative Research: A guide for Researchers in Education and the Social Sciences; Teachers College Press: New York, NY, USA, 2013. [Google Scholar]
- Van Someren, M.; Barnard, Y.; Sandberg, J. The Think Aloud Method: A Practical Approach to Modelling Cognitive Processes; Academic Press: London, UK, 1994. [Google Scholar]
- Ivory, M.Y.; Hearst, M.A. The State of the Art in Automating Usability Evaluation of User Interfaces. ACM Comput. Surv. 2001, 33, 470–516. [Google Scholar] [CrossRef]
- Hartson, H.R.; Castillo, J.C.; Kelso, J.; Neale, W.C. Remote Evaluation: The Network as an Extension of the Usability Laboratory. In Proceedings of the SIGCHI Conference on Human Factors in Computing System, CHI ’96, Vancouver, BC, Canada, 13–18 April 1996; Association for Computing Machinery: New York, NY, USA, 1996; pp. 228–235. [Google Scholar] [CrossRef]
- Brewer, M.B. Research design and issues of validity. In Handbook of Research Methods in Social and Personality Psychology; Reis, H.T., Judd, C.M., Eds.; Cambridge University Press: Cambridge, UK, 2000; pp. 3–16. [Google Scholar]
- Benedek, J.; Miner, T. Measuring Desirability: New methods for evaluating desirability in a usability lab setting. In Proceedings of the Usability Professionals Association Conference, Orlando, FL, USA, 8–12 July 2002. [Google Scholar]
- Lewis, J.R.; Sauro, J. The Factor Structure of the System Usability Scale. In Human Centered Design; Kurosu, M., Ed.; Springer Berlin Heidelberg: Berlin/Heidelberg, Germany, 2009; pp. 94–103. [Google Scholar] [CrossRef]
- Bangor, A.; Kortum, P.; Miller, J. Determining What Individual SUS Scores Mean: Adding an Adjective Rating Scale. J. Usability Stud. 2009, 4, 114–123. [Google Scholar]
- Frik, A.; Kim, J.; Sanchez, J.R.; Ma, J. Users’ Expectations About and Use of Smartphone Privacy and Security Settings. In Proceedings of the CHI Conference on Human Factors in Computing Systems, CHI ’22, New Orleans, LA, USA, 29 April–5 May 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 1–24. [Google Scholar] [CrossRef]




| Consent Requests | Custom Consent Request | Functionality-Based Consent Request | App-Based Consent Request | Usage-Based Consent Request |
|---|---|---|---|---|
| Data processing options |
|
|
|
|
| Not applicable |
|
|
| |
|
|
|
|
| Demographic Data Category | Subcategory | % |
|---|---|---|
| Gender | Male | 66% |
| Female | 34% | |
| Age Group | 16 to 25 years old | 52% |
| 26 to 35 years old | 38% | |
| 36 to 45 years old | 4% | |
| 55 years old and over | 4% | |
| 46 to 55 years old | 2% | |
| Education | High school graduate | 54% |
| Master’s degree | 16% | |
| Bachelor’s degree | 12% | |
| Some college, no degree | 8% | |
| Some high school | 8% | |
| Trade/Technical/Vocational training | 2% | |
| Country of origin | Austria | 64% |
| Serbia | 12% | |
| Germany | 8% | |
| Hungary | 8% | |
| Croatia | 4% | |
| North Macedonia | 4% | |
| Smartphone usage skills | Proficient | 44% |
| Competent | 30% | |
| Expert | 24% | |
| Advanced beginner | 2% | |
| Daily Internet usage | 3–6 h | 50% |
| 1–3 h | 34% | |
| 6–8 h | 6% | |
| 8+ h | 6% | |
| Less than 1 h | 4% | |
| Daily smartphone usage | 1–3 h | 56% |
| 3–6 h | 28% | |
| 6–8 h | 10% | |
| Less than 1 h | 4% | |
| 8+ h | 2% | |
| Preferred device for Internet surfing | Smartphone | 54% |
| Laptop | 28% | |
| Desktop computer | 14% | |
| Tablet | 4% | |
| Privacy vs. Convenience preference | Privacy | 56% |
| Convenience | 44% |
| Task # | Text of the Task |
|---|---|
| T1 | Report three issues that you encounter in your city (e.g., graffiti on the wall, trash on the street, broken bench in the park, broken traffic lights, etc.) |
| T2 | Make a profile picture. |
| T3 | Leave a review of a bicycle rent station. If there are no bicycle stations in your city, please review any point of interest. |
| T4 | Leave a review of a park. |
| T5 | Leave a review of a point of interest. |
| T6 | Exchange some of your scores for three tickets of your choice. |
| T7 | Have a look (in the statistics section) at how many scores you have earned by reporting issues in your city. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Drozd, O.; Kirrane, S. A Conceptual Consent Request Framework for Mobile Devices. Information 2023, 14, 515. https://doi.org/10.3390/info14090515
Drozd O, Kirrane S. A Conceptual Consent Request Framework for Mobile Devices. Information. 2023; 14(9):515. https://doi.org/10.3390/info14090515
Chicago/Turabian StyleDrozd, Olha, and Sabrina Kirrane. 2023. "A Conceptual Consent Request Framework for Mobile Devices" Information 14, no. 9: 515. https://doi.org/10.3390/info14090515
APA StyleDrozd, O., & Kirrane, S. (2023). A Conceptual Consent Request Framework for Mobile Devices. Information, 14(9), 515. https://doi.org/10.3390/info14090515






