Abstract
This paper presents a hardware-assisted security primitive that integrates the Trusted Platform Module (TPM) into IoT devices for authentication in smart grids. Data and device security plays a pivotal role in smart grids since they are vulnerable to various attacks that could risk grid failure. The proposed Fortified-Grid security primitive provides an innovative solution, leveraging the TPM for attestation coupled with standard X.509 certificates. This methodology serves a dual purpose, ensuring the authenticity of IoT devices and upholding software integrity, an indispensable foundation for any resilient smart grid security system. TPM is a hardware security module that can generate keys and store them with encryption so they cannot be compromised. Formal security verification has been performed using the random or real Oracle (ROR) model and widely accepted AVISPA simulation tool, while informal security verification uses the DY and CK adversary model. Fortified-Grid helps to validate the attested state of IoT devices with a minimal network overhead of 1984 bits.
1. Introduction
The advancement of technology for the IoT has paved the way for effective ways of communication for smart grid technology [1]. The smart grid can replace the traditional grid to cater to the energy demand. The smart grid would allow two-way communication between utilities and consumers during power transactions. Advanced metering infrastructure (AMI) and smart metering (SM) technologies can upgrade the conventional power grid by disclosing the hidden features of electrical power. The vehicle-to-grid (V2G) network offers bidirectional energy, information transmission, and other characteristics [2]. Smart grids use various devices for monitoring, analyzing, and controlling the grids deployed in power plants, transmission systems, and consumer premises. The security and reliability of the smart grid system are the real challenges due to its heterogeneous connectivity over the network. Hence, smart grids require the connectivity, authentication, automation, and tracking of such devices through the IoT. The Internet of Things (IoT) is a network of cyber-physical objects comprising sensors, actuators, and software that communicate continuously with their surroundings. IoT devices are used in smart grids for generation, transmission, distribution, and consumer purposes with various systems, such as supervisory control and data acquisition (SCADA), AMI, smart meters, etc. The system-level overview of the Fortified-Grid is shown in Figure 1.
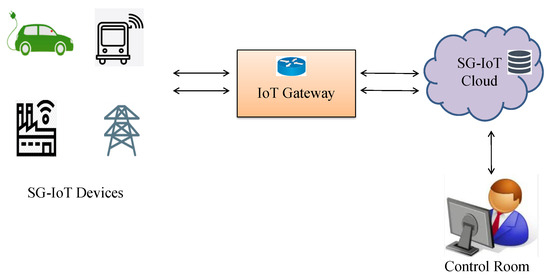
Figure 1.
System-level overview of Fortified-Grid.
The smart grid IoT devices and gateway usually communicate over wireless media; hence, the security of IoT devices has become more challenging. The attacker may compromise the data of devices that are being collected during communication. Hence, IoT devices need more security features, such as authentication, encryption, proper configuration, and the timely updating of software [3,4]. A Raspberry Pi 4 device equipped with TPM for attestation as an IoT device was proposed by reference [5]. The integrity of remote attestation was continuously monitored.
The uses of IoT devices in daily life, such as in the home, the office, transportation systems, smart agriculture, Industry 4.0, and healthcare systems, are increasing rapidly by the day. It is estimated that about 70% of devices will be IoT-based due to the continuously increasing industrialization and urbanization [6]. As per the CISCO survey report, there will be around USD 14.4 trillion worth of devices by the end of 2025 [7]. There will be a huge demand for IoT devices in smart grids applications. IoT smart grids are expected to contribute USD 1.1–2.5 trillion in growth per annum. Hence, in the future, many sensors will be deployed in IoT networks. A protocol for IoT security using TPM and PUF was proposed by reference [8]. The TPM stores the PUF key; hence, any adversary cannot access it from outside.
An effective mutual authentication procedure is required for trusted communication between smart grid IoT devices. Digital certificates are electronic files that prove the authenticity of devices or servers using device identity, the public key, and a cryptographic key. The certificate authority (CA) signs the digital certificate, and all entities trust the CA. In addition to evidence verification using a digital certificate, remote attestation would check the integrity of the IoT software state and would also detect any change. In the remote attestation mechanism, the state of the software or memory proof of untrusted devices is exchanged with the server or another device for verification. RA mechanisms rely on Trusted Platform Modules (TPMs) to generate attestation proofs. The TPM protocol can provide security to manufacturers of IoT devices and service providers, as well as more confidence in certificate-based authentication processes for IoT devices containing a TPM [9]. A TPM wallet security protocol based on blockchain was proposed by reference [10] and can provide security for IoT devices.
An integrity certificate checks software updation, and the results are decided according to the attestation. These certificates in IoT networks are different from conventional certificates due to the different constraints of IoT devices. However, RA results rely on integrity certificates for software state guarantees [11].
This paper’s organization is as follows. Section 2 defines the prior work related to the IoT device security of the smart grid. Section 3 highlights the research gaps and novel contributions. The roles of the Trusted Platform Module (TPM) for hardware-assisted security (HAS) for smart grids are covered in Section 4. Section 5 elaborates the proposed Fortified-Grid model. Section 6 describes the proposed scheme for TPM-based authentication in smart grids. Section 7 explains the security analysis of the proposed TPM-based IoT smart grid network. Section 8 describes the experiment results and a comparison with the state-of-the-art work, while Section 9 discusses the conclusion and final results.
2. Prior Work Related to IoT Device Security for Smart Grids
Secure, reliable, and efficient communication is essential in the IoT-based smart grid network [12]. Various schemes have been proposed in the literature to address smart grid IoT security and privacy challenges. A layered perspective of smart grid security using game theory was proposed by reference [13]. Another lightweight scheme [14,15] provided a basic concept and introduced the idea of smart grids, IoT device authentication, and grid resilience. A batch authentication technique for smart grid IoT devices based on HMAC codes was proposed by reference [16].
In this scheme, they used identity-based signatures to perform batch authentication and used pseudonyms to protect their identities. This scheme outperforms in terms of latency in comparison to other popular schemes. However, this scheme did not provide any solution for trust measurement. In addition, this scheme required extra overhead due to the certificate revocation list. Scheme [17] described the attack detection and mitigation during wireless data transmissions in WSNs, MANETs, and IoT-enabled smart grid networks; the approaches were broadly classified as trust-based and cryptography-based. Figure 2 shows a four-layer IoT-aided smart grid network.
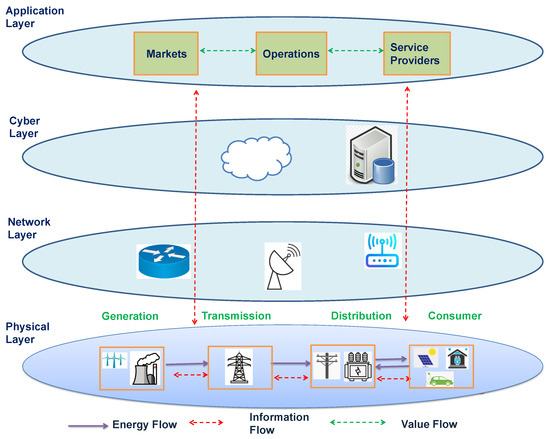
Figure 2.
Four-layer IoT-aided smart grid network.
A Chinese-remainder-theorem-based security of VANETs smart grid system suing TPD, ECDLP, was proposed by reference [18]. However, this scheme suffered from integrity measurement and a lack of security. Later, secure message transmission using remote attestation and HMAC techniques was suggested by reference [19]. More importantly, the scheme proved to be secure using the random oracle model under the Diffi Helman key exchange. They used Intel-SGX, which was designed to ensure integrity against physical adversaries. However, it suffers from high communication and computation overheads. A certificate extension-based scheme was proposed by reference [20]. However, this scheme was unable to protect the identity of IoT devices [21]. Remote attestation based on the digital certificate was suggested by reference [22]. However, the scheme did not support hardware-assisted security and firmware integrity. A mutual authentication protocol based on DAA was suggested by the authors of reference [23]. This scheme addresses unmanned aerial vehicle communication security and uses asymmetric key pairing and TPM to combat malicious modular attacks [23]. Similarly, scheme [24] suggested an executable monitoring system with evidence to verify the system’s status. Recently, a TPM-based scheme for smart grid IoT devices and server authentication was suggested by the authors of reference [25]. It used remote attestation and integrity measurement methods to authenticate smart grid remote IoT devices. However, the scheme generated auto-certificates each time during authentication, and one more entity, CAB, was introduced, making the protocol complicated and vulnerable.
The later scheme [26] proposed a certificate-less protocol based on a hash chain base and hash-chain-less framework. However, scheme [27] demonstrated that the above scheme is vulnerable to replay attacks and does not suggest any method to regenerate the hash chain.
Scheme [28] pointed out that TPM is unsuitable for resource-constrained devices due to space, power, and cost limitations, and suggested a crypto acceleration module. However, this was unable to prove the root of trust management. A survey of remote attestation in the Internet of Things [29] proposed a state-of-the-art remote attestation scheme for attestation and summarized the basic features of the protocol. Remote attestation gives attestation responsibility to resource-rich entities, i.e., servers, to make protocols suitable for smart grid IoT networks. To show various characteristics, existing RA was classified into five categories. However, the scheme could not demonstrate a secure attestation algorithm and security analysis. This scheme was vulnerable to replay attacks. A comparison of popular schemes is shown in Table 1.

Table 1.
A comparative analysis of different popular schemes.
Most schemes discussed above have security flaws, cryptographic key security issues, or large overheads. The proposed scheme also supports adding new smart grid IoT devices after smart grid network deployment. The formal security verification of the scheme is performed using the widely used AVISPA tool and the ROR model against various attacks. Informal security verification is performed using the DY and CK adversary models.
3. Research Gaps and Novel Contributions
3.1. Problem Formulation
In the smart grid, a compromised IoT device’s firmware enables device impersonation and the transmission of false messages to the server. The absence of firmware measurement would compromise the device identity, which causes incorrect data processing and potentially erroneous decisions impacting the smart grid’s functionality. Numerous cryptographic schemes have been suggested to address this issue, yet these protocols often necessitate memory for storing security keys, rendering them susceptible to diverse attacks. The Trusted Platform Module (TPM) offers an innovative solution through an efficient key generation mechanism that enhances security in IoT applications. It can generate keys using a trustworthy route and firmware integrity checks using Platform Configuration Registers (PCR). It showcases the simplicity and resilience in design and implementation. This positions TPM as a dependable and robust security alternative for the smart grid environment.
3.2. Research Gaps
The following research gaps are identified from the literature survey [18,19,22,25]
- To the best of our knowledge, most IoT authentication schemes provide attestation and authentication mechanisms without considering the integrity of the device software.
- Most schemes use a cryptography key for attestation but may be vulnerable to software or intruders.
- Very few schemes provide complete authentication between IoT devices and servers for smart grids.
- Lightweight authentication schemes such as IoT devices in smart grids are generally resource constraints.
3.3. Research Contribution
The novel contributions of the paper are as follows:
- The paper proposes a certificate-based authentication scheme for IoT devices containing a TPM in a smart grid.
- Device authentication utilizes a preloaded certificate and establishes a secret session key after mutual authentication.
- The integrity of device software is ensured using TPM PCR measurement and comparison.
- The proposed scheme has validated its performance on the widely acceptable AVISPA tool and the random or real (ROR) model.
- Our analysis illustrates that the proposed model is secure, privacy-preserving, and supports minimal communicational overhead.
4. The Roles of the Trusted Platform Module (TPM) for Hardware-Assisted Security (HAS) for Smart Grids
IoT aids smart grids to face various security challenges such as integrity, impersonation, denial of service (DoS), replay attacks, malware attacks, etc. A TPM is a cryptography co-processor hardware chip, developed by the Trusted Computing Group (TCG), embedded in SG IoT devices. TPM is integrated with IoT devices, gateway nodes, and servers. In remote attestation and firmware updating, a TPM-based server, which is placed away from the smart grid of IoT devices, collects and checks the measurement results. This section describes the technology and background information required for Fortified-Grid security and authentication.
4.1. Hardware Assisted Security (HAS)
Hardware-assisted security involves integrating specialized hardware components and functionalities to bolster the security of digital systems. These hardware elements work in conjunction with software-based security measures, adding an extra layer of defence against a range of threats. Examples encompass TPM, Hardware Security Modules (HSM), secure enclaves, and hardware-based encryption accelerators. These components provide capabilities such as secure key storage, encryption and decryption, secure boot, and isolated execution environments. Doing so enhances overall system security by minimizing attack opportunities and enhancing resilience against diverse cyber threats.
In smart grid IoT networks, the security of data can be put at risk regardless of which technique is used. In these systems, different types of security challenges exist, such as physical attacks, side-channel attacks, firmware or software modification, information security, privacy, protection, Bluetooth hardware security, etc. However, the severity and complexity of these attacks require a level of security. This would be ensured through hardware support. Due to the several advantages of TPM, we have used it with IoT devices for hardware security in our scheme. Security, by design, must be energy efficient, robust, low-cost, fast, and reliable.
4.2. Trusted Platform Module (TPM) for Smart Grid IoT Devices
The TPM is an encryption co-processor built by the Trusted Computing Group (TCG). Smart grid IoT devices and servers contain TPM. TPM is a hardware security module that can generate and store encrypted keys, so they cannot be compromised. Every TPM has its own private endorsement key (EK) issued by a reliable Certified Authority (CA). It allows for easy authentication methods to be established, guaranteeing that the communication device in question includes a genuine and recognizable TPM. The security of a smart grid IoT deployment can be significantly bolstered by combining TPM features like secure boot and hardware/software attestation. The following are some of TPM’s most important characteristics:
- Key generation and secure storage: Communication mainly occurs in the smart grid system in an open environment. Hence, secure storage and key generation are fundamental requirements in the smart grid network. The generation of cryptographic keys is one of the TPM’s fundamental functions. The secret key is generated by a random number generator (RNG) or a secret seed. TPM can generate an infinite number of keys. The endorsement key (EK) always remains inside the TPM, while the Attestation Identification Key (AIK) is used for attestation purposes.
- Integrity management: This is another vital feature of TPM. For the integrity of devices in smart grid IoT systems, all devices must be periodically configured because any vulnerability in any device increases the likelihood that the entire system will fail. TPM has multiple Platform Configuration Registers (PCRs), and the PCRs hash and store system states. After the defined interval, each execution hash value is recomputed and compared with the previous accumulated value. As resetting or rolling back the PCR to its original state is impossible, any suspicious activity can be easily detected. An integrity measurement at system boot or startup ensures the client’s trust [30].
- Remote attestation: The advantages of the remote attestation technique for smart grid systems include confidentiality and defense against the man in the middle (MITM). Cryptography-based systems are considered secure against various attacks, but in some instances, cryptography keys are compromised, resulting in the entire system being under threat. Therefore, validating the entity or key became imperative before allowing system access. TPM performs an attestation to validate the entity’s or key’s trustworthiness and authenticity. TPM generates a quote that contains the hash of the PCR state and nonce, signed by TPM. At the other end, if the TPM signature is validated, it is authenticated, and the nonce ensures the freshness of the quote and avoids a replay attack.
- Authorization of an entity: This gives an authenticated device or user the necessary permissions to access smart grid resources. Access control ensures that correctly recognized entities only access SG resources. By managing an entity’s authorization, malicious attackers can alter the status or data of the entity. TPM can be used to mitigate these security threats. The PCR can be set to a specific value by defining a specific policy for an entity, so that when PCR is set to a desirable value, devices are only accessible. Hence, all IoT devices are protected from unauthorized access, as all PCRs can roll back to the desired value.
- User Identification and Secure Communication: One of the key differences between smart and traditional grids is their two-way communication. This has several potential benefits, such as distributed smart sensors, distributed power generation, real-time measurements with metering infrastructure, monitoring systems, and fast response, which require reliable communication and information exchange. It enables smart grids to communicate effectively to provide dependable electricity generation and distribution. TPM generates a random nonce that prevents replay attacks and secures communication between smart grid IoT devices [31].
4.3. Digital Certificate Extensions in SG-IoT Network
An X.509 certificate is a digital certificate that uses the public key infrastructure (PKI) standard and contains an additional extension field to be used in the certificate. The digital certificate is a safeguard against various attacks. It enables IoT devices and servers to exchange information securely. X.509 v3 contains several additional fields, such as the device’s unique identification string, serial number, the public part of a secret key, issuer name, validity period, signature, etc. The digital certificate X.509 profile is depicted in Figure 3.
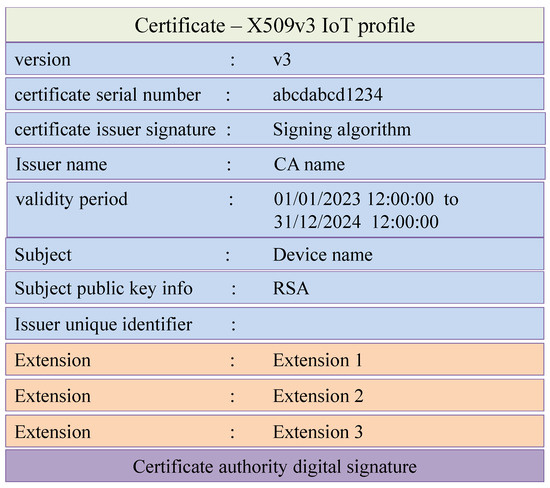
Figure 3.
Smart grid IoT certificate.
4.4. Remote Attestation Procedures (RATS) in IoT-Aided Smart Grids
In a smart grid IoT network, untrusted devices communicate or authenticate with trusted or untrusted devices. The remote attestation procedure (RATS) technique determines whether a smart grid device can trust the remote entity. This establishment of trust is achieved using a two-stage challenge–response algorithm facilitated by a trusted third party (TTP), also known as a certificate authority.
The primary role of RATS is generating, transmitting, and evaluating attestation evidence. An attester would generate the evidence, which would be transmitted to verifiers for the process of verification. Here, attestation can be implemented using TPM quotes, PCR values, and PCR log evidence, which provides the state of the software. During attestation, the PCR computes the hash value of the current state and updates the previous store value. The TPM can report the hash value of a signed PCR and nonce, known as the quote.
5. The Proposed Fortified-Grid Model
5.1. Network Model
In the Fortified-Grid model, we have considered the example of a power quality monitoring system in SCADA of the proposed energy cyber-physical system (E-CPS). Power quality monitoring devices are connected to the network for harmonics monitoring, voltage sags, swells, and unbalances. Here, IoT device A connects to the measure voltage fluctuations, while IoT device B connects to the capacitor banks. Here, device A continues to monitor the voltages and, if required, it instructs device B to take a corrective measurement. Such measurement includes as switching the capacitor bank and voltage regulator to improve the power quality so that the customer receives a quality power supply all the time. This type of device integration may be used for another part of SG-CPS.
The Fortified-Grid network model is depicted in Figure 4. The Fortified-Grid consists of three entities: smart grid IoT devices, gateway nodes (GWN), and servers. A certificate authority (CA) is a trusted authority and may be an IoT owner, manufacturer, or trusted third party (TTP). The smart grid IoT entities contain a hardware chip called TPM, which provides true random number generation, cryptographic key generation, the secure storage of keys, quotes, and software state measurement. Smart grid IoT devices connected via the internet can communicate with each other in real time by establishing a secret session key.
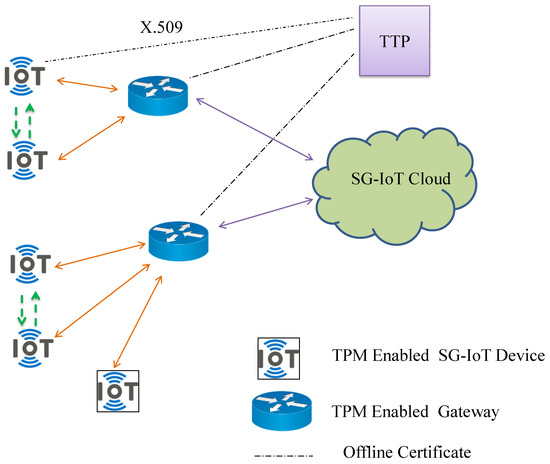
Figure 4.
TPM enabled IoT smart grid network.
Before communicating with other entities, the devices prove their authenticity and integrity to each other. Generally, several schemes adopt certificate-based single-factor authentication, but our protocol considers two-factor authentication, where the integrity of local devices is also validated. A session key is only to be established when both credentials are validated.
5.2. Assumptions
We have assumed that TCG specifications are truly implemented in our TPM-based proposed scheme. The root of trust management is adopted correctly. We have assumed that the smart grid IoT manufacturer has installed the TPM in devices and certificates. We have also assumed that CA, GWN, and servers are trusted entities that are secure from internal and external attacks. We have assumed that adversaries cannot manipulate the TPM configuration. Further, we have assumed that the devices are physically inaccessible and the adversary is unable to perform the side-channel attack.
5.3. Threat Model
Dolev and Yao introduced the Dolev–Yao adversary model in 1983. We consider the two famous Dolev Yao (DY) and Canetti–Krawczyk (CK) adversary models for security analysis in this paper [32]. In the DY model, an adversary has the following capacity and can perform the below attacks:
- An adversary can control the insecure communication channels of an SG network and hence eavesdrop, modify, alter, or block transmitted messages on the smart grid IoT network.
- An adversary can obtain secrets stored in NVM for smart grid devices via a side-channel attack.
- An adversary cannot compromise GWN since it is fully trusted in a smart grid system.
- An adversary can perform clone or physical attacks, a man in the middle, password guessing, etc., except they cannot perform cryptanalysis in a smart grid network.
The CK adversary model is more potent than the DY model and is popularly used in authentication and key exchange schemes. In addition to the above attacks, the CK adversary model can access ephemeral or secret parameters stored in the memory of an entity via explicit attack. The CK adversary model guarantees that information leakage in any session does not affect the security of the next session.
6. Proposed Scheme for TPM-Based Authentication in Smart Grids
Table 2 defines the notations used in this scheme. The detailed sequence of the proposed security scheme is shown below. It may be classified into four steps: (a) Registration, (b) Initialization, (c) Remote attestation, and (d) Session key generation. Detailed information about these steps is defined in the subsequent subsection. The initialization phase steps are depicted in Algorithm 1, while the registration phase steps are depicted in Algorithm 2. The session key steps are described in Algorithm 3.

Table 2.
List of symbols.
6.1. Registration Phase
During the registration phase, IoT devices in the smart grid obtain a digital certificate from CA offline. The TPM is equipped with an Endorsement Key (EK). The attestation key (AIK) is generated using an EK.
6.2. Initialization Phase
During the initialization phase, device A generates a random nonce A using TPM and sends it toward device B. Similarly, device B generates nonce Nb and sends it toward device A. Further, both devices generate and transmit PCR event values toward each side.
| Algorithm 1: Initialization Process |
: Smart grid IoT device A creates a random nonce and measure PCR event log →: , : IoT device B creates a random nonce and measure PCR event log →: , |
| Algorithm 2: Authentication Process |
: Smart gird IoT device A creates a TPM Quote quote = () →: quote,PCR, cert,Ta : verify the signature of CA and extracts from : unsign and verify contains expected and : verify if event log of = : IoT device B creates a TPM Quote quote = () →: quote, cert,Tb : verify the signature of CA and extracts from : verify contains expected and : verify if = : verify if ≤ Ta − Tb |
| Algorithm 3: Session Key Generation and Exchange |
: smart gird IoT device A TPM generates ephemeral key pair , public part of ephemeral key : calculates secret →: secret, , cert,Ta : verify the signature of CA and extracts from : verify contains expected and : IoT device B TPM generates ephemeral key pair , public part of ephemeral key : calculates session key SKba = kdf(‖‖‖) : calculates secret →: secret, , cert,Tb : verify the signature of CA and extracts from : verify contains expected and : calculates session key SKab = kdf(‖‖‖) |
6.3. Remote Attestation Phase
The previously exchanged nonce is included in this signature to avoid a replay attack. During this phase, quotes are exchanged and verified. This is done according to the Trusted Computing Group (TCG) protocol [33]. The step-by-step attestation procedure is shown in Figure 5.
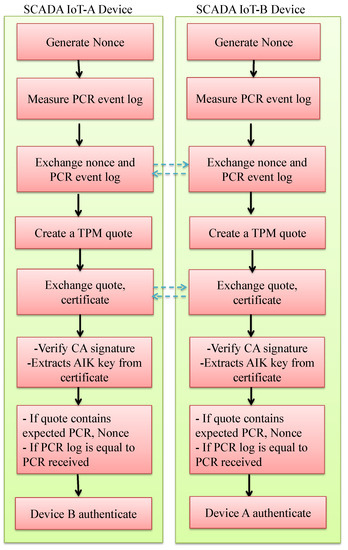
Figure 5.
Attestation of SG-IoT devices.
- Step 1: Device A, which wants to communicate with B, generates a unique random nonce (Na). It sends the value of Na towards B and makes a request for a PCR event log. Attesting device PCRs ( and ) are extended with measurements. Device B generates a unique random nonce (Nb) PCR event log (PCReveB) and sends it toward A. After that, device A sends the PCR event log (PCReveA) towards B. Finally, both devices exchange the nonce, and send the PCR event logs to each other.
- Step 2: IoT device A creates a TPM quote and sends , , towards device B.
- Step 3: Device B verifies the signature of CA and extracts from and unsign and verify contains expected and . Further verify if event log of =
- Step 4: Device B transmits , , toward device A.
- Step 5: Device A verifies the signature of CA and extracts from and unsign and verify contains expected and . Further verify if event log of =
- Step 6: Verify if the time difference is within the threshold limit ≤ Ta − Tb.
The device should not be trusted, and it should be discarded if any one of theses is satisfied:
- The signature of TPM evidence does not match;
- If the nonce in the quote does not match the original quote, as it may be a replay message;
- If the PCR value received in the quote does not match the PCR evidence log;
- If the time difference Ta or Tb exceeds the threshold limit set for the freshness of messages.
6.4. Session Key Establishment Phase
At first, smart grid device creates a fresh ephemeral key pair using the TPM. Ephemeral keys are generated each time a fresh session is established. As ephemeral key pairs are generated inside the TPM, its public part is signed using the attestation key of TPM . A randomly generated previously exchanged nonce is included in the secret parameter to avoid the replay of messages. Finally, device A sends , , towards device B. Device B checks the dh key generated by the trusted system by verifying the signature with the certificate of device A. Device B also checks the nonce sent earlier and generates the session key SKab = kdf(‖‖‖). Similarly, Device B generates fresh ephemeral pairs using TPM. The signed public part of the pair using AIK Pvt key sends , , towards device A. A session key is generated using kdf SKab = kdf(‖‖‖).
7. Security Analysis of Proposed TPM-Based IoT Smart Grid Network
The proposed protocol’s formal security is examined using the ROR oracle model and the automatic security verification tool, AVISPA. In contrast, informal security is examined in various attack situations.
7.1. Security Verification Using AVISPA Tool
We formally verify our security protocol using the popular AVISPA simulation tool. The role of each entity is defined using the HLPSL programming language.
It uses two popular backends for the program’s execution, i.e., OFMC and Cl-AtSe. The results show that our protocol is safe. The security of the protocol is verified on both backends. AVISPA shows different security attacks during the protocol simulation in the intruder section if the protocol is unsafe. This protocol uses the Dolev–Yao model as the intruder model [34]. The result of the AVISPA simulation is depicted in Figure 6.
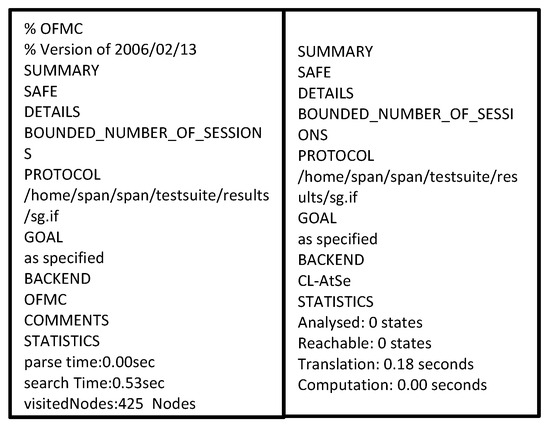
Figure 6.
AVISPA OFMC and CL-Atse.
7.2. Formal Verification Using Random or Real Oracle Model
Formal security verification is based on the ROR model, which measures protocol security by evaluating the probability of SK cracking on the repeated game round in the smart grid. The proposed ROR model assumes that the adversary can interact with another communicating entity Y = (, , GWN); here, , , and can perform the following queries:
- Send (Y, M): In this query, can send message M to Y in the smart grid and receive a specific entity’s response.
- Execution (Y): uses this query to launch a passive attack in the smart grid. It can eavesdrop on all messages transmitted between , , and .
- Reveal (Y): can get the session key SK of , by executing this query.
- Corrupt (Y): If this query is executed, it will obtain the long-term session key SK in the smart grid.
- Test (Y): can send a query to any participant in V2G, and it tosses a coin. Obtain the correct secret key if C = 1 . If C = 0, then a randomly selected value of the same bit string, which equals SK, is returned.
Theorem 1.
Assume that is a running polynomial-time adversary and performs the queries, then the probability that can break protocol is
where and indicates the number of send and TPM queries, respectively, l represents the number of bits, and is a constant [35].
Proof.
We present the proof of the theorem with the help of seven game rounds . indicates the probability of winning in various rounds of the game, and indicates the advantage of breaking the protocol.
- : In the first round of the game, does not make any query. The probability of successfully cracking is
- : In this round, performs Execute (Y) operation. only intercepts message QuoteA, QuoteB, CertA, and CertB transmitted over an insecure communication channel. Since the value of dhA.pvt and dhB.pvt are unknown, can not calculate the secret session key SKab and SKba. Hence, the probability of is same as .
- : In this round, performs a Send (Y) operation other than . As per Zipf’s law, the probability of is
- : In this round, performs one more query (Y) operation and one less operation Send (Y). According to the birthday paradox, the probability of collusion occurring during the hash query simulation is
- : In this game uses , to acquire the or secret dh key . Assume that acquires the dh key . Because cannot calculate the value of , it cannot calculate the SK, where SKab = kdf(‖‖‖). Therefore, the probability of is
- : uses Corrupt (Y) to capture the parameters in is , . Therefore, the probability of is
- : In this game, can guess session key SKab and SKba. The session key remains independent from oracle and other parameters. Hence, the probability of isHence, the probability that can guess isbased on Equations (1)–(8), we obtain the following result:Based on Equations (1)–(8), we obtained Equation (10), which proves the theorem.
□
7.3. Informal Security Analysis
This section examines several security threats using informal security analysis, which is extensively used to demonstrate the cryptographic protocol’s features. The protocol can withstand numerous attacks, such as replay, man-in-the-middle, impersonation, and anonymity attacks.
Proposition 1.
The proposed scheme can mitigate man-in-the-middle attacks.
Proof.
During a MiTM attack, an intruder in the smart gird inserts themselves between the and message exchanges and obtains control of their communication. Suppose an intruder intercepts the relayed transmissions and attempts to alter , , or , , by impersonating a legal entity in front of the other. This is not possible until the adversary obtains the ( or ) of the / . Without knowledge of the quote, an adversary cannot calculate the PCR. Further, authentication is terminated if and are not the same. Consequently, the adversary cannot perform the MITM attack under the analyzed scenarios. □
Proposition 2.
The proposed scheme can resist a replay attack.
Proof.
In this attack, an intruder cannot use the message or as / and Ta, Tb change in each session; hence, the adversary cannot reuse the message or in each session as a new quote message is generated. □
Proposition 3.
The proposed protocol can ensure message integrity.
Proof.
In the smart grid, and generate a new session key in each session. and produce fresh (dhA, dhB, , ) and new timestamps (Ta, Tb). The message confirms the integrity and authentication of the message data transmission. □
Proposition 4.
The proposed protocol can mitigate DoS attacks.
Proof.
In this attack, an adversary may flood the network by delivering unwanted and bogus packets to all protocol entities of smart gird. In our proposed scheme, every entity immediately verifies the received messages against bogus messages and checks the freshness of the timestamp. and generate a new session key in each session. and produce fresh (, ) and new timestamps (Ta, Tb). Hence, they protect against DOS attacks. □
Proposition 5.
The proposed protocol is resilient against backward and forward key secrecy.
Proof.
Only a legitimate can generate , hence calculating fresh SKab = kdf(‖‖‖). Similarly, legitimate can generate fresh SKba = kdf(‖‖‖). If any session key is compromised, this does not help to recover the past or future session keys. Hence, this provides session key security against any attack. □
Proposition 6.
The proposed protocol supports anonymity.
Proof.
Anonymity means the identity of the and is not disclosed during communication. In TPM-SGIoT, every and have TPM, which generates a unique AIK during registration with GWN, and the key is not transmitted during communication. Moreover, the dh of and is different in each session. Thus, an adversary cannot identify the same or in a different session. □
8. Experimental Results
This section provides a detailed comparison of various schemes’ computational and communication overheads. Specifically, it focuses on comparing the computational costs of different schemes. The computations involving large integers are performed using GMP library version 6.1.2 while pairing calculations utilize PBC library version 0.5.14. The experimental setup employs Ubuntu 16.04 as the operating system, an Intel Core i7-6700 CPU running at 4 GHz, and a memory capacity of 16 GB.
Table 3 shows some basic operation execution times; Table 4 provides a comparison of the computation overhead; and Table 5 defines the comparison of the communication overheads of different schemes.

Table 3.
Execution time of different cryptographic operations.

Table 4.
Computational cost comparison.

Table 5.
Communication cost comparison.
8.1. Computational Overhead Analysis
This subsection compares our scheme’s computational cost with those in references [18,19,22,25]. To achieve authentication, scheme [18] will cost 6 Te + 3 Th = 23.75 s. Scheme [19] will cost 2 Tbp + 3 Th = 84.48 s. Similarly, scheme [22] will cost 12 Tem + 23 Th = 56.26 s and scheme [25] will cost 4 Trn + 6 Te + 6 Td + 2 Th = 37.78 s, respectively.
The proposed scheme will cost 4 Trn + 4 Te + 4 Td = 37.78 s. However, the computational cost of our scheme is higher than the scheme in reference [18], but our scheme has the added advantage of the TPM–IoT security layer for a secure smart grid network.
8.2. Communicational Overhead Analysis
As mentioned earlier, the certificate cost is 160 bits, the timestamp is 32 bits, the secret concatenation (quote and secret) is 160 bits, the random nonce is 160 bits, and the public dh key is 320 bits. A comparison of the communication cost of the Fortified-Grid and other popular schemes is shown in Figure 7. In this subsection, the Fortified-Grid communicational cost is compared with those in references [18,19,22,25] for the attestation and key procedures. The communication cost of scheme [22] will be 2176 bits, and scheme [18] cost will be 672 bits. Similarly, scheme [19]’s cost will be 2848 bits, while scheme [25]’s cost will be 2800 bits.
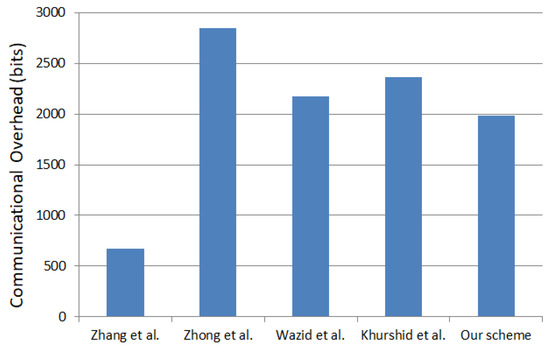
Figure 7.
Comparison of smart grid IoT overhead [18,19,22,25].
In the Fortified-Grid, quotes, PCR, and certificates are exchanged during authentication. Hence, overhead A to B (160 + 32 + 160) = 352 bits; similarly, overhead B to A is (160 + 32 + 160) = 352 bits. The overhead is (160 + 160 + 320) = 640 bits during a key exchange between A and B. Hence, the total overhead on both sides is 1280 bits. As a result, the total communication overhead in our scheme is (704 + 1280) = 1984 bits. The communication cost of our scheme, the Fortified-Grid, is less than the schemes of references [19,22,25]. However, it is more than the scheme of reference [18].
However, it has added the advantage of the TPM–IoT security layer for a secure smart grid network. The results show that our scheme provides security against all major attacks.
8.3. Discussion
This subsection presents the proposed TPM-based attestation scheme’s challenges, advantages, and limitations.
- The major challenges for secure IoT redeployment in a smart gird are secret key leakage, firmware compromise, and hardware-based routes of trust. To mitigate these challenges, we propose an X.509 certificate-based TPM protocol.
- The proposed scheme addresses hardware security challenges, secret key storage, integrity measurement, and remote firmware upgrades. TPM protects against ransomware or any other kind of hack and malware.
- However, these schemes have limitations, such as the dynamic addition of new nodes. Due to space, power, and cost limitations, TPM is unsuitable for resource-constrained devices. Research is needed to reduce the cost and power consumption for the wide application of TPM in security. A trusted third party or certificate authority (CA) is required for the validation of digital certificate X.509. The results are also compared with other state-of-the-art methods, where our proposed model outperforms other related work in terms of computational overhead and robustness.
9. Conclusions
This paper presents a smart grid security framework through the integration of TPM into IoT devices. TPM prevents the malicious modification of firmware during the secure boot and authentication process. This framework relies on the IETF RATS attestation scheme, based on TPM2.0, to generate integrity proof and evidence that utilizes X.509 certificates loaded into IoT devices for authentication and session key generation. The certificates for IoT devices are created by the TTPs using a private key only. The security advantages of integrating TPM into IoT devices also open up the potential for more widespread use in other CPS. We have proposed integrating the Fortify-Grid mechanisms into existing standards to facilitate their adoption in the emerging smart grid.
The threat model uses the CK adversary and ROR models for security verification. A detailed security analysis using the ROR model, AVSIPA, and CK adversary model shows that our proposed scheme is safe against attacks such as man in the middle, replay, denial of service, etc. In addition, integrity measurements are only maintained in the Fortify-Grid, whereas other comparable schemes do not fulfil these requirements. Our scheme’s computational overhead is less than other popular schemes with enhanced security.
Author Contributions
Conceptualization, G.S. and A.M.J.; methodology, G.S.; validation, G.S., A.M.J. and S.P.M.; formal analysis, G.S.; investigation, A.M.J.; resources, G.S.; writing—original draft preparation, G.S.; writing—review and editing, A.M.J.; visualization, A.M.J.; supervision, S.P.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wang, B.; Ma, H.; Wang, F.; Dampage, U.; Al-Dhaifallah, M.; Ali, Z.M.; Mohamed, M.A. An IoT-Enabled Stochastic Operation Management Framework for Smart Grids. IEEE Trans. Intell. Transp. Syst. 2022, 24, 1025–1034. [Google Scholar] [CrossRef]
- Sharma, G.; Joshi, A.M.; Mohanty, S.P. An efficient physically unclonable function based authentication scheme for V2G network. In Proceedings of the IEEE International Symposium on Smart Electronic Systems (iSES) (Formerly iNiS), Jaipur, India, 20–22 December 2021; pp. 421–425. [Google Scholar]
- Kim, Y.; Hakak, S.; Ghorbani, A. Smart grid security: Attacks and defence techniques. IET Smart Grid 2022, 6, 103–123. [Google Scholar] [CrossRef]
- Kim, K.T.; Lim, J.D.; Kim, J.N. An iot device-trusted remote attestation framework. In Proceedings of the 2022 24th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 13–16 February 2022; IEEE: New York, NY, USA, 2022; pp. 218–223. [Google Scholar]
- Berbecaru, D.G.; Sisinni, S. Counteracting software integrity attacks on IoT devices with remote attestation: A prototype. In Proceedings of the 2022 26th International Conference on System Theory, Control and Computing (ICSTCC), Sinaia, Romania, 19–21 October 2022; pp. 380–385. [Google Scholar]
- Jain, A.; Joshi, A.M. Device authentication in IoT using reconfigurable PUF. In Proceedings of the 2nd IEEE Middle East and North Africa COMMunications Conference (MENACOMM), Manama, Bahrain, 19–21 November 2019; pp. 1–4. [Google Scholar]
- Sharma, G.; Joshi, A.M.; Mohanty, S.P. sTrade: Blockchain based secure energy trading using vehicle-to-grid mutual authentication in smart transportation. Sustain. Energy Technol. Assess. 2023, 57, 103296. [Google Scholar] [CrossRef]
- Bathalapalli, V.K.; Mohanty, S.P.; Kougianos, E.; Iyer, V.; Rout, B. PUFchain 4.0: Integrating PUF-based TPM in Distributed Ledger for Security-by-Design of IoT. In Proceedings of the Great Lakes Symposium on VLSI 2023, Knoxville, TN, USA, 5–7 June 2023; pp. 231–236. [Google Scholar]
- Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies 2022, 15, 6984. [Google Scholar] [CrossRef]
- Chiu, W.-Y.; Meng, W.; Li, W. TPMWallet: Towards Blockchain Hardware Wallet using Trusted Platform Module in IoT. In Proceedings of the 2023 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 20–22 February 2023; pp. 336–342. [Google Scholar]
- Jain, H.; Kumar, M.; Joshi, A.M. Intelligent energy cyber physical systems (iECPS) for reliable smart grid against energy theft and false data injection. Electr. Eng. 2021, 104, 331–346. [Google Scholar] [CrossRef]
- Sharma, R.; Joshi, A.M.; Sahu, C.; Sharma, G.; Akindeji, K.T.; Sharma, S. Semi Supervised Cyber Attack Detection System For Smart Grid. In Proceedings of the 30th Southern African Universities Power Engineering Conference (SAUPEC), Durban, South Africa, 25–27 January 2022; pp. 1–5. [Google Scholar]
- Zhu, Q. Multilayer cyber-physical security and resilience for smart grid. In Smart Grid Control: Overview and Research Opportunities; Springer: Cham, Switzerland, 2019; pp. 225–239. [Google Scholar]
- Haggi, H.; Song, M.; Sun, W. A review of smart grid restoration to enhance cyber-physical system resilience. In Proceedings of the IEEE Innovative Smart Grid Technologies-Asia (ISGT Asia), Chengdu, China, 21–24 May 2019; pp. 4008–4013. [Google Scholar]
- Puthal, D.; Mohanty, S.P. Proof of authentication: IoT-friendly blockchains. IEEE Potentials 2018, 38, 26–29. [Google Scholar] [CrossRef]
- Xu, L.; Guo, Q.; Yang, T.; Sun, H. Robust routing optimization for smart grids considering cyber-physical interdependence. IEEE Trans. Smart Grid 2018, 10, 5620–5629. [Google Scholar] [CrossRef]
- Halle, P.D.; Shiyamala, S. Secure advance metering infrastructure protocol for smart grid power system enabled by the Internet of Things. Microprocess. Microsyst. 2022, 95, 104708–104718. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks. IEEE Trans. Dependable Secur. Comput. 2019, 18, 722–735. [Google Scholar] [CrossRef]
- Zhong, H.; Cao, W.; Zhang, Q.; Zhang, J.; Cui, J. Toward trusted and secure communication among multiple internal modules in CAV. IEEE Internet Things J. 2021, 8, 17734–17746. [Google Scholar] [CrossRef]
- Fuchs, A.; Kern, D.; Krauß, C.; Zhdanova, M. HIP: HSM-based identities for plug-and-charge. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtual, 25–28 August 2020; pp. 1–6. [Google Scholar]
- Dave, A.; Wiseman, M.; Safford, D. SEDAT: Security Enhanced Device Attestation with TPM2. 0. arXiv 2021, arXiv:2101.06362. [Google Scholar]
- Wazid, M.; Das, A.K.; Shetty, S. TACAS-IoT: Trust Aggregation Certificate-Based Authentication Scheme for Edge-Enabled IoT Systems. IEEE Internet Things J. 2022, 9, 22643–22656. [Google Scholar] [CrossRef]
- Chen, L.; Qian, S.; Lim, M.; Wang, S. An enhanced direct anonymous attestation scheme with mutual authentication for network-connected UAV communication systems. China Commun. 2018, 15, 61–76. [Google Scholar] [CrossRef]
- Kabir, S.; Gope, P.; Mohanty, S.P. A Security-enabled Safety Assurance Framework for IoT-based Smart Homes. IEEE Trans. Ind. Appl. 2022, 59, 6–14. [Google Scholar] [CrossRef]
- Khurshid, A.; Raza, S. AutoCert: Automated TOCTOU-secure digital certification for IoT with combined authentication and assurance. Comput. Secur. 2023, 124, 102952–102962. [Google Scholar] [CrossRef]
- Huang, H.F.; Liu, K.C. A new dynamic access control in wireless sensor networks. In Proceedings of the IEEE Asia-Pacific Services Computing Conference, Yilan, Taiwan, 9–12 December 2008; pp. 901–906. [Google Scholar]
- Kim, H.S.; Lee, S.W. Enhanced novel access control protocol over wireless sensor networks. IEEE Trans. Consum. Electron. 2009, 55, 492–498. [Google Scholar] [CrossRef]
- Broström, T.; Zhu, J.; Robucci, R.; Younis, M. IoT boot integrity measuring and reporting. ACM SIGBED Rev. 2018, 15, 14–21. [Google Scholar] [CrossRef]
- Kuang, B.; Fu, A.; Susilo, W.; Yu, S.; Gao, Y. A survey of remote attestation in Internet of Things: Attacks, countermeasures, and prospects. Comput. Secur. 2022, 112, 102498. [Google Scholar] [CrossRef]
- Biswas, S.; Sharif, K.; Li, F.; Maharjan, S.; Mohanty, S.P.; Wang, Y. PoBT: A lightweight consensus algorithm for scalable IoT business blockchain. IEEE Internet Things J. 2019, 7, 2343–2355. [Google Scholar] [CrossRef]
- Puthal, D.; Obaidat, M.S.; Nanda, P.; Prasad, M.; Mohanty, S.P.; Zomaya, A.Y. Secure and sustainable load balancing of edge data centers in fog computing. IEEE Commun. Mag. 2018, 56, 60–65. [Google Scholar] [CrossRef]
- Shen, J.; Zhou, T.; Wei, F.; Sun, X.; Xiang, Y. Privacy-preserving and lightweight key agreement protocol for V2G in the social Internet of Things. IEEE Internet Things J. 2017, 5, 2526–2536. [Google Scholar] [CrossRef]
- Trusted Company Group. TCG TPM 2.0 Automotive Thin Profile For TPM Family 2.0; Trusted Company Group: Beaverton, OR, USA, 2018. [Google Scholar]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuéllar, J.; Drielsma, P.H.; Héam, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In Proceedings of the 17th International Conference, CAV 2005, Edinburgh, UK, 6–10 July 2005; pp. 281–285. [Google Scholar]
- Malani, S.; Srinivas, J.; Das, A.K.; Srinathan, K.; Jo, M. Certificate-based anonymous device access control scheme for IoT environment. IEEE Internet Things J. 2019, 6, 9762–9773. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).