Considerations, Advances, and Challenges Associated with the Use of Specific Emitter Identification in the Security of Internet of Things Deployments: A Survey
Abstract
:1. Introduction
2. Related Works
- Universality: every emitter possesses the characteristics or features used to identify it.
- Uniqueness: no two emitters have the same RF fingerprint or SEI exploited features.
- Permanence: the RF fingerprint features are invariant to time or environmental conditions.
- Collectability: the exploited features can be quantitatively measured.
- Performing SEI under changing operating conditions such as alternate channels, Section 5.1, and environmental temperatures, Section 5.2.
- Investigating threats focused on reducing SEI’s effectiveness or defeating SEI altogether, Section 6.
- Performing SEI as the number of emitters increases, Section 7.1, and using multiple collections conducted by the same receiver, Section 7.2.
- Identifying publicly available signal sets to standardize SEI process benchmarking, Section 8.
- Integrating SEI on resource-constrained IoT devices, Section 9.1, and using multiple receivers to collect signals from the same emitter or set of emitters, Section 9.2.
- Including additional literature that is relevant to IoT deployable SEI but does not fall into the research mentioned above, Section 10.
3. Process for Identification of the Reviewed Literature
4. The Essence of Specific Emitter Identification
5. Specific Emitter Identification Operating Conditions
5.1. Operating Channel Conditions
Technical Gaps—Channel Conditions
5.2. Operating Temperature Conditions
Technical Gaps—Operating Temperature
6. Threats to Specific Emitter Identification
Technical Gaps—Threats to SEI
7. Specific Emitter Identification at Scale
7.1. Increasing Number of Emitters
Technical Gaps—Increasing Number of Emitters
7.2. Cross-Collection SEI
Technical Gaps—Cross-Collection SEI
8. SEI Data Sets
- POWDER Signals Set: The POWDER signals set is used to evaluate SEI performance in vendor-neutral hardware deployments of 5G and Open Radio Access Networks (ORANs) [134,159]. The new 5G and ORANs paradigm includes emitters transmitting different protocol signals such as 5G, Long-Term Evolution (LTE), and Wi-Fi at different times. The work in [159] evaluates SEI as a PHY layer authentication technique in such networks using over-the-air signals collected by the large-scale POWDER platform. The signals set includes IQ samples collected from four base stations in different geographical areas. Each base station is implemented using an Ettus USRP X310 SDR and is used to transmit standard-compliant IEEE 802.11a Wi-Fi, LTE, and Fifth Generation-New Radio (5G-NR) frames generated using MATLAB®’s Wireless Local Area Network (WLAN), LTE, and 5G toolboxes. A USRP B210 SDR—located at a fixed point—collects the signals transmitted by the four base stations at a sampling frequency of 5 MHz for Wi-Fi and 7.69 MHz for LTE and 5G. For each base station, the receiver is used to collect IQ samples for two independent days. A single-day collection comprises five sets of IQ samples per base station and protocol, each two seconds long. The data are stored in binary files using Signal Metadata Format (SigMF). Each SigMF file consists of a metadata file containing a description of the collected signals and a data file holding the actual collected signals’ IQ samples.
- DeepSig RadioML Signals Sets: These signals sets are used to evaluate the classification performance of emitter signals in [62,160]. The work in [62] studies the effects of symbol rate and channel impairments on RF signals classification performance by (i) simulating the effects of CFO, symbol rate, and multipath as well as (ii) measuring over-the-air classification performance using software emitters. The signals set used in [62] captures twenty-four different digital and analog single-carrier modulation schemes, including On-Off Keying (OOK), 4-ary Amplitude Shift Keying (ASK), 8-ary ASK, Binary Phase Shift Keying (BPSK), Quadrature Phase-Shift Keying (QPSK), 8-ary Phase Shift-Keying (PSK), 16-ary PSK, 32-ary PSK, 16-ary Amplitude and Phase-Shift keying (APSK), 32-ary APSK, 64-ary APSK, 128-ary APSK, 16QAM, 32QAM, 64QAM, 128QAM, 256QAM, Amplitude Modulation-Single Side-Band-Without Carrier (AM-SSB-WC), AM-SSB with Suppressed Carrier (AM-SSB-SC), AM-Double Side-Band (DSB)-WC, AM-DSB-SC, Frequency Modulation (FM), Gaussian Minimum-Shift Keying (GMSK), and Offset Quadrature Phase-Shift Keying (OQPSK). The resulting modulated symbols are shaped using a root-raised cosine pulse shaping filter. Channel parameters such as Rayleigh fading delay spread are randomly initialized before each transmission to simulate a time-varying wireless channel. The signals are transmitted and collected using USRP B210 SDRs in an indoor channel on the 900 MHz Industrial, Scientific, and Medical (ISM) band for the over-the-air portion of the signals set. Each captured signal in this data set is composed of 1024 samples. The signals of two million samples are encoded using the hdf5 file format.Another DeepSig signal set was generated by the authors of [160]. The authors of [160] investigate the feasibility of applying machine learning to the signal processing domain. The authors use the GNU Radio platform to generate a synthetic collection of signals with varying SNR and eleven types of analog and digital modulation, including 8-ary PSK, AM-DSB, AM-SSB, BPSK, Continuous-Phase Frequency-Shift Keying (CPFSK), Gaussian Frequency Shift Keying (GFSK), PAM4, 16QAM, 64QAM, QPSK, and Wide-Band FM (WBFM). For the analog and digital portion of the signal set, the authors use a continuous data source from acoustic voice speech and Gutenberg’s works of Shakespeare in ASCII, respectively. The data are organized in a multidimensional float32 vector with a size ofwhere refers to the number of signals. is set to one, refers to the I and Q channels, and is the number of samples in each signal. The four-dimensional data set is stored in cPickle format to facilitate access and integration of machine-learning platforms such as Keras, Theano, and TensorFlow.
- ORACLE Signal Set: This set of signals was collected by the authors of [161] to evaluate their Optimized Radio clAssification through Convolutional neuraL nEtworks (ORACLE) approach. The authors of [161] evaluate the classification (identification) performance of the proposed approach within static and dynamic channels that are simulated using MATLAB® toolboxes. The ORACLE data set includes signals collected from sixteen USRP X310 emitters transmitting IEEE 802.11a Wi-Fi-compliant frames. A stationary USRP B210 SDR collects all of the IEEE 802.11a Wi-Fi frames at a sampling frequency of 5 MHz and a center frequency of 2.45 GHz. More than twenty million signals are collected for each emitter. Each signal is divided into 128 sub-sequences and stored as float64 in binary files.
- WiSig Signal Set: This signal set is generated by the authors of [162]. It includes ten million IEEE 802.11 Wi-Fi signals collected from one hundred and seventy-four COTS Wi-Fi emitters using forty-one USRP receivers over four captures representing four days. The authors of [162] attempt to address degrading SEI performance due to channel variations caused by using different receivers or signals collected over multiple days. The Wi-Fi signals sent by one hundred and seventy-four Wi-Fi nodes to the AP are captured by forty-one USRP receivers, including B210s, X310s, and N210s. To create the raw WiSig data set, four single-day captures were performed and combined to generate a 1.4 terabyte data set. The collected raw signals are prepossessed to extract the first 256 IQ samples from each Wi-Fi frame with and without channel equalization. The authors provide the steps and scripts to preprocess the collected signals and the data set. For convenience, the authors of [162] subdivided the data set into four smaller subsets:
- ManyTx: contains fifty signals for each of the one hundred and fifty emitters and the signals collected by eighteen receivers over four days.
- ManyRx: contains two hundred signals for each of the ten emitters and the signals collected using thirty-two receivers over four days.
- ManySig: contains one thousand signals for each of the six emitters and the signals collected using twelve receivers over four days.
- SingleDay: contains eight hundred signals for each of the twenty-eight emitters and the signals collected by ten receivers in a single day.
The WiSig signal set signals are detected using auto-correlation performed using the Wi-Fi preamble’s STS portion and re-sampled to a rate of 20 MHz.
Technical Gaps—Signal Data Sets
9. Considerations for SEI in IoT Deployments
9.1. SEI on Resource-Constrained Devices
Technical Gaps—SEI on Resource-Constrained Devices
9.2. Receiver-Agnostic SEI
Technical Gaps—Receiver-Agnostic SEI
10. Supplemental Challenges
10.1. Quantization of Deep Learning Models
- The authors of [193] present a flexible open-source mixed low-precision library referred to as CMix-NN for low-bit quantization of weights and activations into 8-, 4-, and 2-bit integers. The proposed quantization method targets micro-controller units with a few megabytes of memory and without hardware support for floating-point operations. The quantization library can convert convolutional kernels of CNNs to any bit precision in the 8-, 4-, and 2-bits sets. The authors of [193] used the CMix-NN library to compress, deploy, and evaluate the performance of multiple Mobile-net family models on an STM32H7 microcontroller. The CMix-NN library achieves up to an 8% improvement in accuracy compared to the other state-of-the-art quantization and compression solutions for microcontroller units.
- The authors of [194] present effective quantization approaches for Recurrent Neural Network (RNN) implementations that includes LSTM, Gated Recurrent Units (GRU), and Convolutional Long-Short Term Memory (ConvLSTM). The proposed quantization methods are intended for FPGAs and embedded devices such as low-power mobile devices. The authors of [194] evaluated the performance of their quantization approach using the IMDb and moving MNIST data sets.
- Access Point (AP): Provides traditional AP functionality as well as SEI. The AP is powered by a Raspberry Pi 4 model B.
- Authorized Users: each authorized user is a TP-Link AC1300 USB Wi-Fi adapter and a computer running Ubuntu Linux 16.0.
- Adversary: The adversary is implemented using an Ettus USRP B210 SDR powered by an NVIDIA Jetson Nano Developer Kit. The adversary actively learns the SEI features of an authorized emitter and then modifies its own signals’ SEI features to match those of the selected authorized emitter before transmission to hinder or defeat the AP co-located SEI process.
10.2. Unlocking the Secrets of SEI
10.3. Availability and Format of Large Signal Data Sets
10.4. Standardization of Language
- Classification: (a.k.a., Identification) The process through which emitters are assigned to different classes or categories. Classification is the result of a one-to-many comparison between the emitter’s signal or its representation and each of the known classes or categories using a measure of similarity (e.g., distance, probability, etc.).
- Authentication: (a.k.a., Verification or Validation) The process through which an emitter’s identity—typically a digital one such as a MAC address—is authenticated or verified by performing a one-to-one comparison between the emitter’s signal or its representation and the stored model or representation associated with the identity claimed by the to-be-authenticated emitter.
10.5. IoT-Imposed Temperature Considerations
11. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| 5G-NR | Fifth Generation-New Radio |
| ABL | Adaptive Broad Learning |
| ADA | Adversarial Domain Adaption |
| ADLM | Analog Devices Active Learning Module |
| ADS-B | Automatic Dependent Surveillance-Broadcast |
| AE | AutoEncoder |
| AI | Artificial Intelligence |
| AIS | Automatic Identification System |
| AM | Amplitude Modulation |
| AP | Access Point |
| APG | Average Path Gain |
| ASCII | American Standard Code for Information Interchange |
| ASK | Amplitude Shift-Keying |
| AWG | Arbitrary Waveform Generator |
| AWGN | Additive White Gaussian Noise |
| BER | Bit-Error-Rate |
| BLE | Bluetooth Low Energy |
| BLS | Broad Learning System |
| BP | Back Propagation |
| BPSK | Binary Phase Shift-Keying |
| BS | Base Station |
| CAE | Convolutional AutoEncoder |
| CFO | Carrier Frequency Offset |
| ChaRRNets | Channel Robust Representation Networks |
| CGAN | Conditional Generative Adversarial Network |
| CNN | Convolutional Neural Network |
| ConvLSTM | Convolutional Long Short-Term Memory |
| COTS | Commercial-Off-The-Shelf |
| CPFSK | Continuous-Phase Frequency-Shift Keying |
| CPU | Central Processing Unit |
| CSI | Channel State Information |
| CuSI | Cubic-Spline Interpolation |
| CvT | Convolutions to Vision Transformers |
| C&W | Carlini & Wagner |
| DAC | Digital-to-Analog Converter |
| DCFT | Differential Constellation Trace Figure |
| DCT | Discrete Cosine Transform |
| DDoS | Distributed Denial-of-Service |
| DFT | Discrete Fourier Transform |
| DI | Differential Interval |
| DNA | Distinct, Native, Attribute |
| DNN | Deep Neural Network |
| DoLoS | Difference of the Logarithm of the Spectrum |
| DSB | Double Side-Band |
| EMD | Empirical Mode Decomposition |
| FAR | False Accept Rate |
| FGSM | Fast Gradient Sign Method |
| FLOPS | Floating Point Operations Per Second |
| FM | Frequency Modulation |
| FPGA | Field Programmable Gate Array |
| FRR | False Reject Rate |
| GAN | Generative Adversarial Network |
| GAN-RXA | Generative Adversarial Network-based Receiver Agnostic |
| GFSK | Gaussian Frequency-Shift Keying |
| GLFormer | Gated and sliding Local self-attention transFormer |
| GMSK | Gaussian Minimum Shift-Keying |
| GPU | Graphical Processing Unit |
| GRU | Gated Recurrent Unit |
| GT | Gabor Transform |
| HART | Highway Addressable Remote Transducer |
| ICMP | Internet Control Message Protocol |
| IIR | Infinite Impulse Response |
| InfoGANs | Information maximized Generative Adversarial Networks |
| IoT | Internet of Things |
| IoV | Internet of Vehicles |
| IoBT | Internet of Battlefield Things |
| IoMT | Internet of Military Things |
| IIoT | Industrial Internet of Things |
| IQ | In-phase and Quadrature |
| IQI | IQ Imbalance |
| ISM | Industrial, Scientific, and Medical |
| ISR | Intentional Structure Removal |
| ITD | Intrinsic Time-scale Decomposition |
| JCAECNN | Joint CAE and CNN |
| kNN | k-Nearest Neighbors |
| LAI | Linear Approximation Interpolation |
| LMMD | Local Maximum Mean Discrepancy |
| LO | Local Oscillator |
| LoS | Line-of-Sight |
| LSTM | Long Short-Term Memory |
| LTE | Long-Term Evolution |
| LTS | Long Training Symbol |
| MAC | Media Access Control |
| MANET | Mobile Ad hoc NETwork |
| MDA | Multiple Discriminant Analysis |
| MDA/ML | Multiple Discriminant Analysis/Maximum Likelihood |
| MIMO | Multiple Input Multiple Output |
| MLP | Multi-Layer Perceptron |
| MMSE | Minimum Mean Squared Error |
| N–M | Nelder–Mead |
| NN | Neural Network |
| OFDM | Orthogonal Frequency-Division Multiplexing |
| OOK | On-Off Keying |
| OQPSK | Offset Quadrature Phase-Shift Keying |
| ORACLE | Optimized Radio clAssification through Convolutional neuraL nEtworks |
| ORANs | Open Radio Access Networks |
| OSTBC | Orthogonal Space-Time Block Code |
| PA | Power Amplifier |
| PAM | Pulse Amplitude Modulation |
| PARADIS | Passive RAdiometric Device Identification System |
| PBA | Per Batch Accuracy |
| PCA | Principal Component Analysis |
| PGD | Projected Gradient Descent |
| PHY | Physical |
| PLA | Physical Layer Authentication |
| PLL | Phase-Locked Loop |
| PLS | Physical Layer Security |
| PMF | Probability Mass Function |
| POWDER | Platform for Open Wireless Data-driven Experimental Research |
| PSA | Per Slice Accuracy |
| PSK | Phase Shift-Keying |
| PTA | Per-Transmission Accuracy |
| QAM | Quadrature Amplitude Modulation |
| QoS | Quality of Service |
| QPSK | Quadrature Phase Shift-Keying |
| RECAP | Radiometric signature Exploitation Countering using |
| Adversarial machine learning-based Protocol | |
| ResNN | Residual Neural Network |
| RF | Radio Frequency |
| RFF | Radio Frequency Fingerprint |
| RFFE | Radio Frequency Fingerprint Embedding |
| RF-DNA | Radio Frequency-Distinct, Native, Attributes |
| RNN | Recurrent Neural Network |
| SC | Suppressed Carrier |
| SDR | Software-Defined Radio |
| SD-RXA | Statistical Distance-based Receiver Agnostic |
| SEI | Specific Emitter Identification |
| SepBN-DANN | Separated Batch Normalization-Deep Adversarial Neural Network |
| SFEBLN | Signal Feature Embedded Broad Learning Network |
| SIB | Square Integral Bispectrum |
| SigMF | Signal Metadata Format |
| SNR | Signal-to-Noise Ratio |
| STS | Short Training Symbol |
| STBC | Space-Time Block Code |
| STFT | Short-Time Fourier Transform |
| SSB | Single Side-Band |
| SVM | Support Vector Machines |
| SWaP-C | Size, Weight, and Power-Cost |
| SYNC | Synchronization |
| TeRFF | Temperature-aware Radio Frequency Fingerprinting |
| TF | Time-Frequency |
| USRP | Universal Software Radio Peripheral |
| VCP | Voltage Controlled Oscillator |
| VMD | Variational Mode Decomposition |
| WANET | Wireless Ad hoc NETwork |
| WBFM | Wide-Band Frequency Modulation |
| WC | Without Carrier |
| Wi-Fi | Wireless-Fidelity |
| WLAN | Wireless Local Area Network |
| ZSL | Zero-Shot Learning |
References
- Department of Defense (DoD), United States. DoD Policy Recommendations for the Internet of Things (IoT). 2016. Available online: https://www.hsdl.org/?view&did=799676 (accessed on 14 June 2018).
- Gartner Research. Gartner Says 6.4 Billion Connected “Things” Will Be in Use in 2016, Up 30 Percent from 2015. 2015. Available online: https://www.gartner.com/en/newsroom/press-releases/2015-11-10-gartner-says-6-billion-connected-things-will-be-in-use-in-2016-up-30-percent-from-2015#:~:text=Gartner%2C%20Inc.,will%20get%20connected%20every%20day (accessed on 15 June 2018).
- Juniper Research. ‘Internet of Things’ Connected Devices to Triple by 2021, Reaching Over 46 Billion Units. 2016. Available online: https://www.juniperresearch.com/press/internet-of-things-connected-devices-triple-2021 (accessed on 23 July 2021).
- Statista. Internet of Things (IoT) Connected Devices Installed Base Worldwide from 2015 to 2025 (in Billions). 2019. Available online: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed on 12 May 2020).
- Rawlinson, K. Hp Study Reveals 70 Percent of Internet of Things Devices Vulnerable to Attack. [Online]. 2014. Available online: https://www8.hp.com/us/en/hp-news/press-release.html?id=1744676 (accessed on 12 May 2020).
- Ray, I.; Kar, D.M.; Peterson, J.; Goeringer, S. Device identity and trust in IoT-sphere forsaking cryptography. In Proceedings of the 2019 IEEE 5th International Conference on Collaboration and Internet Computing (CIC), Los Angeles, CA, USA, 12–14 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 204–213. [Google Scholar]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Larson, S. A Smart Fish Tank Left a Casino Vulnerable to Hackers. 2017. Available online: https://money.cnn.com/2017/07/19/technology/fish-tank-hack-darktrace/index.html#:~:text=Most%20people%20know%20about%20phishing,report%20from%20security%20firm%20Darktrace (accessed on 13 December 2021).
- Wright, J.; Cache, J. Hacking Exposed Wireless: Wireless Security Secrets & Solutions; McGraw-Hill Education Group: Washington, DC, USA, 2015. [Google Scholar]
- Stanislav, M.; Beardsley, T. Hacking IoT: A Case Study on Baby Monitor Exposures and Vulnerabilities; Rapid7 Report; Rapid7 Inc.: Boston, MA, USA, 2015. [Google Scholar]
- Wright, J. KillerBee: Practical ZigBee Exploitation Framework or “Wireless Hacking and the Kinetic World”. 2018. Available online: https://www.willhackforsushi.com/presentations/toorcon11-wright.pdf (accessed on 13 December 2021).
- Shipley, P.; Gooler, R. Insteon: False Security and Deceptive Documentation; DEF CON: Springfield, IL, USA, 2015; Volunme 23. [Google Scholar]
- Shipley, P. Tools for Insteon RF. GitHub. 2015. Available online: https://github.com/evilpete/insteonrf (accessed on 14 December 2021).
- Krebs, B. Mirai IoT Botnet Co-Authors Plead Guilty-Krebs on Security. Krebs on Security. 2017. Available online: https://krebsonsecurity.com/2017/12/mirai-iot-botnet-co-authors-plead-guilty/#:~:text=For%20the%20click%20fraud%20conspiracy,a)(5)(A) (accessed on 9 January 2022).
- Simon, S.; Selyukh, A. Internet of Things’ Hacking Attack Led to Widespread Outage of Popular Websites. National Public Radio (NPR). 2016. Available online: https://www.npr.org/2016/10/22/498954197/internet-outage-update-internet-of-things-hacking-attack-led-to-outage-of-popula (accessed on 10 January 2022).
- Talbot, C.M.; Temple, M.A.; Carbino, T.J.; Betances, J.A. Detecting rogue attacks on commercial wireless Insteon home automation systems. Comput. Secur. 2018, 74, 296–307. [Google Scholar] [CrossRef]
- Sa, K.; Lang, D.; Wang, C.; Bai, Y. Specific emitter identification techniques for the internet of things. IEEE Access 2019, 8, 1644–1652. [Google Scholar] [CrossRef]
- Reising, D.; Cancelleri, J.; Loveless, T.D.; Kandah, F.; Skjellum, A. Radio identity verification-based IoT security using RF-DNA fingerprints and SVM. IEEE Internet Things J. 2020, 8, 8356–8371. [Google Scholar] [CrossRef]
- Langley, L.E. Specific emitter identification (SEI) and classical parameter fusion technology. In Proceedings of the WESCON’93, San Francisco, CA, USA, 28–30 September 1993; IEEE: Piscataway, NJ, USA, 1993; pp. 377–381. [Google Scholar]
- Terry, I. Networked Specific Emitter Identification in Fleet Battle Experiment Juliet. 2003. Available online: https://apps.dtic.mil/sti/citations/ADA415972 (accessed on 22 August 2023).
- Defence R&D Canada—Ottawa. Interferometric Intrapulse Radar Receiver for Specific Emitter Identification and Direction-Finding. Fact Sheet REW 224 2007, 224. [Google Scholar]
- Dudczyk, J.; Kawalec, A. Specific emitter identification based on graphical representation of the distribution of radar signal parameters. Bull. Pol. Acad. Sci. Tech. Sci. 2015, 63, 391–396. [Google Scholar] [CrossRef]
- Matuszewski, J. Specific emitter identification. In Proceedings of the 2008 International Radar Symposium, Wroclaw, Poland, 21–23 May 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 1–4. [Google Scholar]
- Toonstra, J.; Kinsner, W. Transient analysis and genetic algorithms for classification. In Proceedings of the IEEE WESCANEX 95, Communications, Power, and Computing, Conference Proceedings, Winnipeg, MB, Canada, 15–16 May 1995; IEEE: Piscataway, NJ, USA, 1995; Volume 2, pp. 432–437. [Google Scholar]
- Ureten, O.; Serinken, N. Detection of radio transmitter turn-on transients. Electron. Lett. 1999, 35, 1996–1997. [Google Scholar] [CrossRef]
- Ureten, O.; Serinken, N. Bayesian detection of Wi-Fi transmitter RF fingerprints. Electron. Lett. 2005, 41, 373–374. [Google Scholar] [CrossRef]
- Ureten, O.; Serinken, N. Wireless security through RF fingerprinting. Can. J. Electr. Comput. Eng. 2007, 32, 27–33. [Google Scholar] [CrossRef]
- Jana, S.; Kasera, S.K. On fast and accurate detection of unauthorized wireless access points using clock skews. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, San Francisco, CA, USA, 14–19 September 2008; pp. 104–115. [Google Scholar]
- Suski, W.C., II; Temple, M.A.; Mendenhall, M.J.; Mills, R.F. Radio frequency fingerprinting commercial communication devices to enhance electronic security. Int. J. Electron. Secur. Digit. Forensics 2008, 1, 301–322. [Google Scholar]
- Suski, W.C., II; Temple, M.A.; Mendenhall, M.J.; Mills, R.F. Using spectral fingerprints to improve wireless network security. In Proceedings of the IEEE GLOBECOM 2008-2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 1–5. [Google Scholar]
- Danev, B.; Capkun, S. Transient-based identification of wireless sensor nodes. In Proceedings of the 2009 International Conference on Information Processing in Sensor Networks, San Francisco, CA, USA, 13–16 April 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 25–36. [Google Scholar]
- Klein, R.; Temple, M.A.; Mendenhall, M.J.; Reising, D.R. Sensitivity analysis of burst detection and RF fingerprinting classification performance. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 1–5. [Google Scholar]
- Klein, R.W.; Temple, M.A.; Mendenhall, M.J. Application of wavelet-based RF fingerprinting to enhance wireless network security. J. Commun. Netw. 2009, 11, 544–555. [Google Scholar] [CrossRef]
- Liu, M.W.; Doherty, J.F. Specific emitter identification using nonlinear device estimation. In Proceedings of the 2008 IEEE Sarnoff Symposium, Princeton, NJ, USA, 28–30 April 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 1–5. [Google Scholar]
- Liu, M.W.; Doherty, J.F. Nonlinearity estimation for specific emitter identification in multipath channels. IEEE Trans. Inf. Forensics Secur. 2011, 6, 1076–1085. [Google Scholar]
- Kennedy, I.O.; Kuzminskiy, A.M. RF fingerprint detection in a wireless multipath channel. In Proceedings of the 2010 7th International Symposium on Wireless Communication Systems, York, UK, 19–22 September 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 820–823. [Google Scholar]
- Reising, D.R.; Temple, M.A.; Mendenhall, M.J. Improving intra-cellular security using air monitoring with RF fingerprints. In Proceedings of the 2010 IEEE Wireless Communication and Networking Conference, Beijing, China, 25–27 June 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 1–6. [Google Scholar]
- Reising, D.R.; Temple, M.A.; Mendenhall, M.J. Improved wireless security for GMSK-based devices using RF fingerprinting. Int. J. Electron. Secur. Digit. Forensics 2010, 3, 41–59. [Google Scholar] [CrossRef]
- Reising, D.; Prentice, D.; Temple, M. An FPGA Implementation of Real-Time RF-DNA Fingerprinting for RFINT Applications. In Proceedings of the IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 7–10 November 2011. [Google Scholar]
- Reising, D.R.; Temple, M.A.; Oxley, M.E. Gabor-based RF-DNA fingerprinting for classifying 802.16 e WiMAX mobile subscribers. In Proceedings of the 2012 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 30 January–2 February 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 7–13. [Google Scholar]
- Reising, D.R.; Temple, M.A.; Jackson, J.A. Authorized and rogue device discrimination using dimensionally reduced RF-DNA fingerprints. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1180–1192. [Google Scholar] [CrossRef]
- Williams, M.D.; Temple, M.A.; Reising, D.R. Augmenting bit-level network security using physical layer RF-DNA fingerprinting. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 1–6. [Google Scholar]
- Takahashi, D.; Xiao, Y.; Zhang, Y.; Chatzimisios, P.; Chen, H.H. IEEE 802.11 user fingerprinting and its applications for intrusion detection. Comput. Math. Appl. 2010, 60, 307–318. [Google Scholar] [CrossRef]
- Tekbaş, Ö.; Üreten, O.; Serinken, N. Improvement of transmitter identification system for low SNR transients. Electron. Lett. 2004, 40, 182–183. [Google Scholar] [CrossRef]
- Ellis, K.; Serinken, N. Characteristics of radio transmitter fingerprints. Radio Sci. 2001, 36, 585–597. [Google Scholar] [CrossRef]
- Soliman, S.S.; Hsue, S.Z. Signal classification using statistical moments. IEEE Trans. Commun. 1992, 40, 908–916. [Google Scholar] [CrossRef]
- Azzouz, E.; Nandi, A.K. Automatic Modulation Recognition of Communication Signals; Springer Science & Business Media: New York, NY, USA, 2013. [Google Scholar]
- Wheeler, C.G.; Reising, D.R. Assessment of the impact of CFO on RF-DNA fingerprint classification performance. In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Silicon Valley, CA, USA, 26–29 January 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 110–114. [Google Scholar]
- Pan, Y.; Yang, S.; Peng, H.; Li, T.; Wang, W. Specific Emitter Identification Based on Deep Residual Networks. IEEE Access 2019, 7, 54425–54434. [Google Scholar] [CrossRef]
- Fadul, M.K.; Reising, D.R.; Loveless, T.D.; Ofoli, A.R. RF-DNA fingerprint classification of OFDM signals using a Rayleigh fading channel model. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–19 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar]
- Fadul, M.; Reising, D.; Loveless, T.D.; Ofoli, A. Preprint: Using RF-DNA Fingerprints To Classify OFDM Transmitters Under Rayleigh Fading Conditions. arXiv 2020, arXiv:2005.04184. [Google Scholar]
- Fadul, M.; Reising, D.; Sartipi, M. Identification of OFDM-based Radio sunder Rayleigh Fading using RF-DNA and Deep Learning. IEEE Access 2020, 7, 17100–17113. [Google Scholar]
- Dubendorfer, C.K.; Ramsey, B.W.; Temple, M.A. An RF-DNA verification process for ZigBee networks. In Proceedings of the MILCOM 2012–2012 IEEE Military Communications Conference, Orlando, FL, USA, 29 October–1 November 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 1–6. [Google Scholar]
- Baldini, G.; Steri, G. A Survey of Techniques for the Identification of Mobile Phones Using the Physical Fingerprints of the Built-In Components. IEEE Commun. Surv. Tutor. 2017, 19, 1761–1789. [Google Scholar] [CrossRef]
- Baldini, G.; Gentile, C.; Giuliani, R.; Steri, G. Comparison of Techniques for Radiometric Identification based on Deep Convolutional Neural Networks. Electron. Lett. 2019, 55, 90–92. [Google Scholar] [CrossRef]
- Baldini, G.; Giuliani, R. An Assessment of the Impact of Wireless Interferences on IoT Emitter Identification using Time Frequency Representations and CNN. In Proceedings of the Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019. [Google Scholar] [CrossRef]
- Restuccia, F.; D’Oro, S.; Al-Shawabka, A.; Belgiovine, M.; Angioloni, L.; Ioannidis, S.; Chowdhury, K.; Melodia, T. DeepRadioID: Real-time channel-resilient optimization of deep learning-based radio fingerprinting algorithms. In Proceedings of the Twentieth ACM International Symposium on Mobile Ad Hoc Networking and Computing, Shanghai, China, 26–29 July 2019; pp. 51–60. [Google Scholar]
- Wong, L.; Headley, W.; Andrews, S.; Gerdes, R.; Michaels, A. Clustering Learned CNN Features from Raw I/Q Data for Emitter Identification. In Proceedings of the IEEE Military Communications Conf (MILCOM), Los Angeles, CA, USA, 29–31 October 2018. [Google Scholar] [CrossRef]
- Jafari, H.; Omotere, O.; Adesina, D.; Wu, H.; Qian, L. IoT Devices Fingerprinting Using Deep Learning. In Proceedings of the IEEE Military Communications Conf (MILCOM), Los Angeles, CA, USA, 29–31 October 2018. [Google Scholar] [CrossRef]
- Bassey, J.; Li, X.; Qian, L. Device Authentication Codes based on RF Fingerprinting using Deep Learning. arXiv Electr. Eng. Syst. Sci. Signal Process. 2020, 8, 1–17. [Google Scholar] [CrossRef]
- Chen, X.; Hao, X. Feature Reduction Method for Cognition and Classification of IoT Devices Based on Artificial Intelligence. IEEE Access 2019, 7, 103291–103298. [Google Scholar] [CrossRef]
- O’Shea, T.; Roy, T.; Clancy, T. Over-the-Air Deep Learning Based Radio Signal Classification. IEEE J. Sel. Top. Signal Process. 2018, 12, 168–179. [Google Scholar] [CrossRef]
- Youssef, K.; Bouchard, L.; Haigh, K.; Silovsky, J.; Thapa, B.; Valk, C. Machine Learning Approach to RF Transmitter Identification. IEEE J. Radio Freq. Identif. 2018, 2, 197–205. [Google Scholar] [CrossRef]
- Wilson, A.J.; Reising, D.R.; Loveless, T.D. Integration of matched filtering within the RF-DNA fingerprinting process. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Hall, J.; Barbeau, M.; Kranakis, E. Detection of transient in radio frequency fingerprinting using signal phase. Wirel. Opt. Commun. 2003, 9, 13. [Google Scholar]
- Hall, M. Correlation-based Feature Selection for Discrete and Numeric Class Machine Learning. In Proceedings of the 17th International Conference on Machine Learning (ICML-2000), Silicon Valley, CA, USA, 29 June–2 July 2000; pp. 359–366. [Google Scholar]
- Hall, J.; Barbeau, M.; Kranakis, E. Radio frequency fingerprinting for intrusion detection in wireless networks. IEEE Trans. Defendable Secur. Comput. 2005, 12, 1–35. [Google Scholar]
- Merchant, K.; Revay, S.; Stantchev, G.; Nousain, B. Deep Learning for RF Device Fingerprinting in Cognitive Communication Networks. IEEE J. Sel. Top. Sig. Proc. 2018, 12, 160–167. [Google Scholar] [CrossRef]
- Polak, A.; Goeckel, D. RF Fingerprinting of Users Who Actively Mask Their Identities with Artificial Distortion. In Proceedings of the 2011 Conference Record of the Forty Fifth Asilomar Conference on Signals, Systems and Computers (ASILOMAR), Pacific Grove, CA, USA, 6–9 November 2011. [Google Scholar]
- Polak, A.; Goeckel, D. Wireless Device Identification Based on RF Oscillator Imperfections. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2492–2501. [Google Scholar] [CrossRef]
- Polak, A.; Dolatshahi, S.; Goeckel, D. Identifying Wireless Users via Transmitter Imperfections. IEEE J. Sel. Areas Commun. 2011, 29, 1469–1479. [Google Scholar] [CrossRef]
- Polak, A.; Goeckel, D. Identification of Wireless Devices of Users Who Actively Fake Their RF Fingerprints With Artificial Data Distortion. IEEE Trans. Wirel. Commun. 2015, 14, 5889–5899. [Google Scholar] [CrossRef]
- Dolatshahi, S.; Polak, A.; Goeckel, D. Identification of wireless users via power amplifier imperfections. In Proceedings of the 2010 Conference Record of the Forty Fourth Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 7–10 November 2010. [Google Scholar]
- Yu, J.; Hu, A.; Li, G.; Peng, L. A Robust RF Fingerprinting Approach Using Multisampling Convolutional Neural Network. IEEE Internet Things J. 2019, 6, 6786–6799. [Google Scholar] [CrossRef]
- Guyue, L.; Jiabao, Y.; Xing, Y.; Hu, A. Location-Invariant Physical Layer Identification Approach for WiFi Devices. IEEE Access 2019, 7, 106974–106986. [Google Scholar] [CrossRef]
- Liang, J.; Huang, Z.; Li, Z. Method of Empirical Mode Decomposition in Specific Emitter Identification. Wirel. Pers. Commun. 2017, 96, 1–15. [Google Scholar] [CrossRef]
- Smith, L.; Smith, N.; Hopkins, J.; Rayborn, D.; Ball, J.; Tang, B.; Young, M. Classifying WiFi Physical Fingerprints using Complex Deep Learning. In Automatic Target Recognition XXX; International Society for Optics and Photonics, SPIE: Cardiff, UK, 2020; Volume 11394, p. 113940J. [Google Scholar]
- Kandah, F.; Cancelleri, J.; Reising, D.; Altarawneh, A.; Skjellum, A. A Hardware-Software Co-design Approach to Identity, Trust, and Resilience for IoT/CPS at Scale. In Proceedings of the International Conference on Internet of Things (iThings), Atlanta, GA, USA, 14–17 July 2019. [Google Scholar]
- Harmer, P.K.; Temple, M.A.; Buckner, M.A.; Farquhar, E. 4G Security Using Physical Layer RF-DNA with DE-Optimized LFS Classification. J. Commun. 2011, 6, 671–681. [Google Scholar] [CrossRef]
- Harmer, P.K.; Reising, D.R.; Temple, M.A. Classifier selection for physical layer security augmentation in cognitive radio networks. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 2846–2851. [Google Scholar]
- Wang, X.; Hao, P.; Hanzo, L. Physical-layer Authentication for Wireless Security Enhancement: Current Challenges and Future Developments. IEEE Commun. Mag. 2016, 54, 152–158. [Google Scholar] [CrossRef]
- Xu, Q.; Zheng, R.; Saad, W.; Han, Z. Device fingerprinting in wireless networks: Challenges and opportunities. IEEE Commun. Surv. Tutor. 2015, 18, 94–104. [Google Scholar] [CrossRef]
- Gerdes, R.; Daniels, T.; Phd, M.; Russell, S. Device Identification via Analog Signal Fingerprinting: A Matched Filter Approach. Available online: https://www.researchgate.net/publication/221655376_Device_Identification_via_Analog_Signal_Fingerprinting_A_Matched_Filter_Approach (accessed on 22 August 2023).
- Joo, K.; Choi, W.; Lee, D.H. Hold the door! fingerprinting your car key to prevent keyless entry car theft. arXiv 2020, arXiv:2003.13251. [Google Scholar]
- Riyaz, S.; Sankhe, K.; Ioannidis, S.; Chowdhury, K. Deep Learning Convolutional Neural Networks for Radio Identification. IEEE Commun. Mag. 2018, 56, 146–152. [Google Scholar] [CrossRef]
- O’Shea, T.; Hoydis, J. An Introduction to Deep Learning for the Physical Layer. IEEE Trans. Cogn. Commun. Netw. 2017, 3, 563–575. [Google Scholar] [CrossRef]
- Mendis, G.; Wei, J.; Madanayake, A. Deep Learning Based Radio-Signal Identification With Hardware Design. IEEE Trans. Aerosp. Electron. Syst. 2019, 55, 2516–2531. [Google Scholar] [CrossRef]
- Brik, V.; Banerjee, S.; Gruteser, M.; Oh, S. Wireless device identification with radiometric signatures. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, San Francisco, CA, USA, 14–19 September 2008; pp. 116–127. [Google Scholar]
- Jain, A.K.; Hong, L.; Pankanti, S.; Bolle, R. An identity-authentication system using fingerprints. Proc. IEEE 1997, 85, 1365–1388. [Google Scholar] [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-layer security of 5G wireless networks for IoT: Challenges and opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Bai, L.; Zhu, L.; Liu, J.; Choi, J.; Zhang, W. Physical layer authentication in wireless communication networks: A survey. J. Commun. Inf. Netw. 2020, 5, 237–264. [Google Scholar] [CrossRef]
- Soltanieh, N.; Norouzi, Y.; Yang, Y.; Karmakar, N.C. A Review of Radio Frequency Fingerprinting Techniques. IEEE J. Radio Freq. Identif. 2020, 4, 222–233. [Google Scholar] [CrossRef]
- Xie, N.; Li, Z.; Tan, H. A survey of physical-layer authentication in wireless communications. IEEE Commun. Surv. Tutor. 2020, 23, 282–310. [Google Scholar] [CrossRef]
- Jagannath, A.; Jagannath, J.; Kumar, P.S.P.V. A comprehensive survey on radio frequency (rf) fingerprinting: Traditional approaches, deep learning, and open challenges. arXiv 2022, arXiv:2201.00680. [Google Scholar] [CrossRef]
- Parmaksiz, H.; Karakuzu, C. A Review of Recent Developments on Secure Authentication Using RF Fingerprints Techniques. Sak. Univ. J. Comput. Inf. Sci. 2022, 5, 278–303. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, J.; Li, J.; Niu, S.; Song, H. Machine learning for the detection and identification of Internet of Things devices: A survey. IEEE Internet Things J. 2021, 9, 298–320. [Google Scholar] [CrossRef]
- Clarke, R.H. A statistical theory of mobile-radio reception. Bell Syst. Tech. J. 1968, 47, 957–1000. [Google Scholar] [CrossRef]
- Danev, B.; Luecken, H.; Capkun, S.; El Defrawy, K. Attacks on physical-layer identification. In Proceedings of the Third ACM Conference on Wireless Network Security, Hoboken, NJ, USA, 22–24 March 2010; pp. 89–98. [Google Scholar]
- Fadul, M.; Reising, D.; Loveless, T.D.; Ofoli, A. Nelder-mead simplex channel estimation for the RF-DNA fingerprinting of OFDM transmitters under Rayleigh fading conditions. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2381–2396. [Google Scholar] [CrossRef]
- Reising, D.R.; Weerasena, L.P.; Loveless, T.D.; Sartipi, M. Improving RF-DNA Fingerprinting Performance in an Indoor Multipath Environment Using Semi-Supervised Learning. arXiv 2023, arXiv:2304.00648. [Google Scholar]
- Tyler, J.; Fadul, M.; Reising, D.; Kandah, F. An Analysis of Signal Energy Impacts and Threats to Deep Learning Based SEI. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022. [Google Scholar]
- Peggs, C.S.; Jackson, T.S.; Tittlebaugh, A.N.; Olp, T.G.; Tyler, J.H.; Reising, D.R.; Loveless, T.D. Preamble-based RF-DNA Fingerprinting Under Varying Temperatures. In Proceedings of the 2023 12th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 6–10 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–8. [Google Scholar]
- Tyler, J.H.; Fadul, M.K.; Reising, D.R.; Liang, Y. Assessing the Presence of Intentional Waveform Structure In Preamble-based SEI. In Proceedings of the GLOBECOM 2022–2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 4129–4135. [Google Scholar] [CrossRef]
- Tyler, J.H.; Reising, D.R.; Kandah, F.I.; Kaplanoglu, E.; Fadul, M.M.K. Physical Layer-Based IoT Security: An Investigation Into Improving Preamble-Based SEI Performance When Using Multiple Waveform Collections. IEEE Access 2022, 10, 133601–133616. [Google Scholar] [CrossRef]
- Taha, M.A.; Fadul, M.K.; Tyler, J.H.; Reising, D.R.; Loveless, T.D. An assessment of entropy-based data reduction for SEI within IoT applications. In Proceedings of the MILCOM 2022–2022 IEEE Military Communications Conference (MILCOM), Rockville, MD, USA, 28 November–2 December 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 385–392. [Google Scholar]
- Fadul, M.; Reising, D.; Weerasena, L. An Investigation into the Impacts of Deep Learning-based Re-sampling on Specific Emitter Identification Performance. arXiv 2022, arXiv:2305.03853. [Google Scholar]
- Tyler, J.; Fadul, M.; Hilling, M.; Reising, D.; Loveless, D. Assessing Adversarial Replay and Deep Learning-Driven Attacks on Specific Emitter Identification-based Security Approaches. arXiv 2023, arXiv:2308.03579. [Google Scholar]
- Brandes, T.S.; Kuzdeba, S.; McClelland, J.; Bomberger, N.; Radlbeck, A. RF waveform synthesis guided by deep reinforcement learning. In Proceedings of the 2020 IEEE International Workshop on Information Forensics and Security (WIFS), New York, NY, USA, 6–11 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Wang, W.; Gan, L. Radio Frequency Fingerprinting Improved by Statistical Noise Reduction. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 1444–1452. [Google Scholar] [CrossRef]
- Han, H.; Cui, L.; Li, W.; Huang, L.; Cai, Y.; Cai, J.; Zhang, Y. Radio Frequency Fingerprint Based Wireless Transmitter Identification Against Malicious Attacker: An Adversarial Learning Approach. In Proceedings of the 2020 International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 21–23 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 310–315. [Google Scholar]
- Yuan, Y.; Huang, Z.; Wu, H.; Wang, X. Specific emitter identification based on Hilbert–Huang transform-based time–frequency–energy distribution features. IET Commun. 2014, 8, 2404–2412. [Google Scholar] [CrossRef]
- Guo, S.; Akhtar, S.; Mella, A. A method for radar model identification using time-domain transient signals. IEEE Trans. Aerosp. Electron. Syst. 2021, 57, 3132–3149. [Google Scholar] [CrossRef]
- Chen, N.; Hu, A.; Fu, H. LoRa radio frequency fingerprint identification based on frequency offset characteristics and optimized LoRaWAN access technology. In Proceedings of the 2021 IEEE 5th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 March 2021; IEEE: Piscataway, NJ, USA, 2021; Volume 5, pp. 1801–1807. [Google Scholar]
- Gu, X.; Wu, W.; Guo, N.; He, W.; Song, A.; Yang, M.; Ling, Z.; Luo, J. TeRFF: Temperature-aware Radio Frequency Fingerprinting for Smartphones. In Proceedings of the 2022 19th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Stockholm, Sweden, 20–23 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 127–135. [Google Scholar]
- Chen, Y.; Chen, X.; Lei, Y. Emitter Identification of Digital Modulation Transmitter Based on Nonlinearity and Modulation Distortion of Power Amplifier. Sensors 2021, 21, 4362. [Google Scholar] [CrossRef]
- Liting, S.; Xiang, W.; Huang, Z. Unintentional modulation evaluation in time domain and frequency domain. Chin. J. Aeronaut. 2022, 35, 376–389. [Google Scholar]
- Zhang, J.; Woods, R.; Sandell, M.; Valkama, M.; Marshall, A.; Cavallaro, J. Radio Frequency Fingerprint Identification for Narrowband Systems, Modelling and Classification. IEEE Trans. Inf. Forensics Secur. 2021, 16, 3974–3987. [Google Scholar] [CrossRef]
- Hou, W.; Wang, X.; Chouinard, J.Y.; Refaey, A. Physical layer authentication for mobile systems with time-varying carrier frequency offsets. IEEE Trans. Commun. 2014, 62, 1658–1667. [Google Scholar] [CrossRef]
- Robyns, P.; Marin, E.; Lamotte, W.; Quax, P.; Singelée, D.; Preneel, B. Physical-layer fingerprinting of LoRa devices using supervised and zero-shot learning. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Boston, MA, USA, 18–20 July 2017; pp. 58–63. [Google Scholar]
- Hao, P.; Wang, X.; Behnad, A. Relay authentication by exploiting I/Q imbalance in amplify-and-forward system. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 613–618. [Google Scholar]
- Xing, G.; Shen, M.; Liu, H. Frequency offset and I/Q imbalance compensation for direct-conversion receivers. IEEE Trans. Wirel. Commun. 2005, 4, 673–680. [Google Scholar] [CrossRef]
- Jian, T.; Rendon, B.; Ojuba, E.; Soltani, N.; Wang, Z.; Sankhe, K.; Gritsenko, A.; Dy, J.; Chowdhury, K.; Ioannidis, S. Deep Learning for RF Fingerprinting: A Massive Experimental Study. IEEE Internet Things Mag. 2020, 3, 50–57. [Google Scholar] [CrossRef]
- Robinson, J.; Kuzdeba, S.; Stankowicz, J.; Carmack, J. Dilated Causal Convolutional Model For RF Fingerprinting. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 0157–0162. [Google Scholar] [CrossRef]
- Morin, C.; Cardoso, L.S.; Hoydis, J.; Gorce, J.M.; Vial, T. Transmitter classification with supervised deep learning. In Proceedings of the Cognitive Radio-Oriented Wireless Networks: 14th EAI International Conference, CrownCom 2019, Poznan, Poland, 11–12 June 2019; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2019; pp. 73–86. [Google Scholar]
- Behura, S.; Kedia, S.; Hiremath, S.M.; Patra, S.K. WiST ID—Deep Learning-Based Large Scale Wireless Standard Technology Identification. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 1365–1377. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, B.; Zhang, J.; Yang, N.; Wei, G.; Guo, D. Specific Emitter Identification Based on Deep Adversarial Domain Adaptation. In Proceedings of the 2021 4th International Conference on Information Communication and Signal Processing (ICICSP), Shanghai, China, 24–26 September 2021; pp. 104–109. [Google Scholar] [CrossRef]
- Gong, J.; Xu, X.; Qin, Y.; Dong, W. A Generative Adversarial Network Based Framework for Specific Emitter Characterization and Identification. In Proceedings of the 2019 11th International Conference on Wireless Communications and Signal Processing (WCSP), Xi’an, China, 23–25 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Gong, J.; Xu, X.; Lei, Y. Unsupervised Specific Emitter Identification Method Using Radio-Frequency Fingerprint Embedded InfoGAN. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2898–2913. [Google Scholar] [CrossRef]
- Basha, N.; Hamdaoui, B.; Sivanesan, K.; Guizani, M. Channel-Resilient Deep-Learning-Driven Device Fingerprinting through Multiple Data Streams. IEEE Open J. Commun. Soc. 2023, 4, 118–133. [Google Scholar] [CrossRef]
- Xing, Y.; Hu, A.; Zhang, J.; Peng, L.; Wang, X. Design of A Channel Robust Radio Frequency Fingerprint Identification Scheme. IEEE Internet Things J. 2022, 10, 6946–6959. [Google Scholar] [CrossRef]
- Yuan, H.; Yan, Y.; Bao, Z.; Xu, C.; Gu, J.; Wang, J. Multipath Canceled RF Fingerprinting for Wireless OFDM Devices Based on Hammerstein System Parameter Separation. IEEE Can. J. Electr. Comput. Eng. 2022, 45, 401–408. [Google Scholar] [CrossRef]
- Yang, L.; Camtepe, S.; Gao, Y.; Liu, V.; Jayalath, D. On the Use of Power Amplifier Nonlinearity Quotient to Improve Radio Frequency Fingerprint Identification in Time-Varying Channels. arXiv 2023, arXiv:2302.13724. [Google Scholar]
- Brown, C.N.; Mattei, E.; Draganov, A. ChaRRNets: Channel robust representation networks for RF fingerprinting. arXiv 2021, arXiv:2105.03568. [Google Scholar]
- Breen, J.; Buffmire, A.; Duerig, J.; Dutt, K.; Eide, E.; Hibler, M.; Johnson, D.; Kasera, S.K.; Lewis, E.; Maas, D.; et al. POWDER: Platform for Open Wireless Data-driven Experimental Research. In Proceedings of the 14th International Workshop on Wireless Network Testbeds, Experimental Evaluation and Characterization (WiNTECH), London, UK, 21 September 2020. [Google Scholar] [CrossRef]
- Rehman, S.; Sowerby, K.; Alam, S.; Ardekani, I. Radio frequency fingerprinting and its challenges. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 496–497. [Google Scholar]
- Wang, T.; Fang, K.; Wei, W.; Tian, J.; Pan, Y.; Li, J. Microcontroller Unit Chip Temperature Fingerprint Informed Machine Learning for IIoT Intrusion Detection. IEEE Trans. Ind. Inform. 2022, 19, 2219–2227. [Google Scholar] [CrossRef]
- Yilmaz, Ö.; Yazici, M. The Effect of Ambient Temperature On Device Classification Based On Radio Frequency Fingerprint Recognition. Sak. Univ. J. Comput. Inf. Sci. 2022, 5, 233–245. [Google Scholar] [CrossRef]
- Frerking, M. Crystal Oscillator Design and Temperature Compensation; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Shi, Y.; Davaslioglu, K.; Sagduyu, Y.E. Generative adversarial network for wireless signal spoofing. In Proceedings of the ACM Workshop on Wireless Security and Machine Learning, Miami, FL, USA, 15–17 May 2019; pp. 55–60. [Google Scholar]
- Shi, Y.; Davaslioglu, K.; Sagduyu, Y.E. Generative adversarial network in the air: Deep adversarial learning for wireless signal spoofing. IEEE Trans. Cogn. Commun. Netw. 2020, 7, 294–303. [Google Scholar] [CrossRef]
- Restuccia, F.; D’Oro, S.; Al-Shawabka, A.; Rendon, B.C.; Chowdhury, K.; Ioannidis, S.; Melodia, T. Hacking the waveform: Generalized wireless adversarial deep learning. arXiv 2020, arXiv:2005.02270. [Google Scholar]
- Lalouani, W.; Younis, M.; Baroudi, U. Countering radiometric signature exploitation using adversarial machine learning based protocol switching. Comput. Commun. 2021, 174, 109–121. [Google Scholar] [CrossRef]
- Abanto-Leon, L.F.; Bäuml, A.; Sim, G.H.; Hollick, M.; Asadi, A. Stay connected, leave no trace: Enhancing security and privacy in wifi via obfuscating radiometric fingerprints. Proc. ACM Meas. Anal. Comput. Syst. 2020, 4, 1–31. [Google Scholar] [CrossRef]
- Karunaratne, S.; Krijestorac, E.; Cabric, D. Penetrating RF fingerprinting-based authentication with a generative adversarial attack. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–6. [Google Scholar]
- Nikoofard, A.; Givehchian, H.; Bhaskar, N.; Schulman, A.; Bharadia, D.; Mercier, P.P. Protecting Bluetooth User Privacy through Obfuscation of Carrier Frequency Offset. IEEE Trans. Circuits Syst. II Express Briefs 2022, 70, 541–545. [Google Scholar] [CrossRef]
- Sun, L.; Ke, D.; Wang, X.; Huang, Z.; Huang, K. Robustness of Deep Learning-Based Specific Emitter Identification under Adversarial Attacks. Remote Sens. 2022, 14, 4996. [Google Scholar] [CrossRef]
- Ke, D.; Huang, Z.; Wang, X.; Sun, L. Application of adversarial examples in communication modulation classification. In Proceedings of the 2019 International Conference on Data Mining Workshops (ICDMW), Beijing, China, 8–11 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 877–882. [Google Scholar]
- Goodfellow, I.J.; Shlens, J.; Szegedy, C. Explaining and harnessing adversarial examples. arXiv 2014, arXiv:1412.6572. [Google Scholar]
- Madry, A.; Makelov, A.; Schmidt, L.; Tsipras, D.; Vladu, A. Towards deep learning models resistant to adversarial attacks. arXiv 2017, arXiv:1706.06083. [Google Scholar]
- Carlini, N.; Wagner, D. Towards evaluating the robustness of neural networks. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 39–57. [Google Scholar]
- Defense Advances Research Projects Agency (DARPA). Spectrum Collaboration Challenge—Using AI to Unlock the True Potential of the RF Spectrum. 2017. Available online: https://archive.darpa.mil/sc2/ (accessed on 12 March 2018).
- Defense Advances Research Projects Agency (DARPA). Radio Frequency Machine Learning Systems. 2019. Available online: https://www.darpa.mil/program/radio-frequency-machine-learning-systems (accessed on 14 September 2019).
- Yang, Y.; Hu, A.; Yu, J.; Li, G.; Zhang, Z. Radio frequency fingerprint identification based on stream differential constellation trace figures. Phys. Commun. 2021, 49, 101458. [Google Scholar] [CrossRef]
- Al-Shawabka, A.; Restuccia, F.; D’Oro, S.; Jian, T.; Costa Rendon, B.; Soltani, N.; Dy, J.; Ioannidis, S.; Chowdhury, K.; Melodia, T. Exposing the Fingerprint: Dissecting the Impact of the Wireless Channel on Radio Fingerprinting. In Proceedings of the IEEE INFOCOM 2020–IEEE Conference on Computer Communications, Virtual Event, 16–19 November 2020; pp. 646–655. [Google Scholar] [CrossRef]
- Hamdaoui, B.; Basha, N.; Sivanesan, K. Deep Learning-Enabled Zero-Touch Device Identification: Mitigating the Impact of Channel Variability Through MIMO Diversity. IEEE Commun. Mag. 2023, 61, 80–85. [Google Scholar] [CrossRef]
- Downey, J.; Hilburn, B.; O’Shea, T.; West, N. In the Future, AIs—Not Humans—Will Design Our Wireless Signals. Available online: https://spectrum.ieee.org/in-the-future-aisnot-humanswill-design-our-wireless-signals (accessed on 30 April 2020).
- Li, H.; Gupta, K.; Wang, C.; Ghose, N.; Wang, B. RadioNet: Robust Deep-Learning Based Radio Fingerprinting. In Proceedings of the 2022 IEEE Conference on Communications and Network Security (CNS), Austin, TX, USA, 3–5 October 2022; pp. 190–198. [Google Scholar] [CrossRef]
- Smith, L.; Smith, N.; Rayborn, D.; Tang, B.; Ball, J.E.; Young, M. Identifying unlabeled WiFi devices with zero-shot learning. In Automatic Target Recognition XXX; SPIE: Cardiff, UK, 2020; Volume 11394, pp. 129–137. [Google Scholar]
- Reus-Muns, G.; Jaisinghani, D.; Sankhe, K.; Chowdhury, K.R. Trust in 5G open RANs through machine learning: RF fingerprinting on the POWDER PAWR platform. In Proceedings of the GLOBECOM 2020–2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- O’shea, T.J.; West, N. Radio machine learning dataset generation with gnu radio. In Proceedings of the GNU Radio Conference, Boulder, CO, USA, 12–16 September 2016; Volume 1. [Google Scholar]
- Sankhe, K.; Belgiovine, M.; Zhou, F.; Riyaz, S.; Ioannidis, S.; Chowdhury, K. ORACLE: Optimized Radio clAssification through Convolutional neuraL nEtworks. In Proceedings of the IEEE INFOCOM 2019–IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 370–378. [Google Scholar] [CrossRef]
- Hanna, S.; Karunaratne, S.; Cabric, D. WiSig: A large-scale WiFi signal dataset for receiver and channel agnostic RF fingerprinting. IEEE Access 2022, 10, 22808–22818. [Google Scholar] [CrossRef]
- Jian, T.; Gong, Y.; Zhan, Z.; Shi, R.; Soltani, N.; Wang, Z.; Dy, J.; Chowdhury, K.; Wang, Y.; Ioannidis, S. Radio frequency fingerprinting on the edge. IEEE Trans. Mob. Comput. 2021, 21, 4078–4093. [Google Scholar] [CrossRef]
- Lin, D.; Wu, W. RF Fingerprint-Identification-Based Reliable Resource Allocation in an Internet of Battle Things. IEEE Internet Things J. 2022, 9, 21111–21120. [Google Scholar] [CrossRef]
- Xu, Z.; Han, G.; Liu, L.; Zhu, H.; Peng, J. A Lightweight Specific Emitter Identification Model for IIoT Devices Based on Adaptive Broad Learning. IEEE Trans. Ind. Inform. 2022, 19, 7066–7075. [Google Scholar] [CrossRef]
- Zhang, Y.; Peng, Y.; Sun, J.; Gui, G.; Lin, Y.; Mao, S. GPU-Free Specific Emitter Identification Using Signal Feature Embedded Broad Learning. IEEE Internet Things J. 2023, 10, 13028–13039. [Google Scholar] [CrossRef]
- Kuzdeba, S.; Robinson, J.; Carmack, J.; Couto, D. Systems View to Designing RF Fingerprinting for Real-World Operations. In Proceedings of the 2022 ACM Workshop on Wireless Security and Machine Learning, San Antonio, TX, USA, 19 May 2022; pp. 33–38. [Google Scholar]
- Deng, P.; Hong, S.; Qi, J.; Wang, L.; Sun, H. A Lightweight Transformer-Based Approach of Specific Emitter Identification for the Automatic Identification System. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2303–2317. [Google Scholar] [CrossRef]
- Nguyen, D.D.N.; Sood, K.; Xiang, Y.; Gao, L.; Chi, L.; Yu, S. Towards IoT Node Authentication Mechanism in Next Generation Networks. IEEE Internet Things J. 2023, 10, 13333–13341. [Google Scholar] [CrossRef]
- Zhang, T.; Ye, S.; Zhang, K.; Tang, J.; Wen, W.; Fardad, M.; Wang, Y. A systematic dnn weight pruning framework using alternating direction method of multipliers. In Proceedings of the European Conference on Computer Vision (ECCV), Munich, Germany, 8 September 2018; pp. 184–199. [Google Scholar]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Ya, T.; Yun, L.; Haoran, Z.; Zhang, J.; Yu, W.; Guan, G.; Shiwen, M. Large-scale real-world radio signal recognition with deep learning. Chin. J. Aeronaut. 2022, 35, 35–48. [Google Scholar]
- Zhang, S.; Zhang, Y.; Sun, J.; Gui, G.; Lin, Y.; Gacanin, H.; Adachi, F. A real-world radio frequency signal dataset based on LTE system and variable channels. arXiv 2022, arXiv:2205.12577. [Google Scholar]
- Zhang, Y.; Peng, Y.; Adebisi, B.; Gui, G.; Gacanin, H.; Sari, H. Specific Emitter Identification Based on Radio Frequency Fingerprint Using Multi-Scale Network. In Proceedings of the 2022 IEEE 96th Vehicular Technology Conference (VTC2022-Fall), London, UK, 26–29 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–5. [Google Scholar]
- Krug, S.; O’Nils, M. IoT Communication Introduced Limitations for High Sampling Rate Applications. In Proceedings of the GI/ITG KuVS Fachgespräch Sensornetze–FGSN 2018, Braunschweig, Germany, 12 October 2018. [Google Scholar]
- Long, J.D.; Temple, M.A.; Rondeau, C.M. Discriminating WirelessHART Communication Devices Using Sub-Nyquist Stimulated Responses. Electronics 2023, 12, 1973. [Google Scholar] [CrossRef]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention is all you need. Adv. Neural Inf. Process. Syst. 2017, 30, 6000–6010. [Google Scholar]
- Shen, G.; Zhang, J.; Marshall, A.; Woods, R.; Cavallaro, J.; Chen, L. Towards Receiver-Agnostic and Collaborative Radio Frequency Fingerprint Identification. arXiv 2022, arXiv:2207.02999. [Google Scholar]
- Qian, Y.; Qi, J.; Kuai, X.; Han, G.; Sun, H.; Hong, S. Specific emitter identification based on multi-level sparse representation in automatic identification system. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2872–2884. [Google Scholar] [CrossRef]
- Liu, Z.; Lin, Y.; Cao, Y.; Hu, H.; Wei, Y.; Zhang, Z.; Lin, S.; Guo, B. Swin transformer: Hierarchical vision transformer using shifted windows. In Proceedings of the IEEE/CVF International Conference on Computer Vision, Cambridge, MA, USA, 17 August 2021; pp. 10012–10022. [Google Scholar]
- Wu, H.; Xiao, B.; Codella, N.; Liu, M.; Dai, X.; Yuan, L.; Zhang, L. Cvt: Introducing convolutions to vision transformers. In Proceedings of the IEEE/CVF International Conference on Computer Vision, Cambridge, MA, USA, 17 August 2021; pp. 22–31. [Google Scholar]
- Merchant, K.; Nousain, B. Toward receiver-agnostic RF fingerprint verification. In Proceedings of the 2019 IEEE Globecom Workshops (GC Wkshps), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- He, B.; Wang, F. Cooperative specific emitter identification via multiple distorted receivers. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3791–3806. [Google Scholar] [CrossRef]
- Huang, K.; Jiang, B.; Yang, J.; Wang, J.; Hu, P.; Li, Y.; Shao, K.; Zhao, D. Cross-receiver specific emitter identification based on a deep adversarial neural network with separated batch normalization. In Proceedings of the Third International Conference on Computer Science and Communication Technology (ICCSCT 2022), Shanghai, China, 24–26 September 2021; SPIE: Cardiff, UK, 2022; Volume 12506, pp. 1659–1663. [Google Scholar]
- Zhao, T.; Sarkar, S.; Krijestorac, E.; Cabric, D. GAN-RXA: A Practical Scalable Solution to Receiver-Agnostic Transmitter Fingerprinting. arXiv 2023, arXiv:2303.14312. [Google Scholar]
- Zha, X.; Li, T.; Qiu, Z.; Li, F. Cross-Receiver Radio Frequency Fingerprint Identification Based on Contrastive Learning and Subdomain Adaptation. IEEE Signal Process. Lett. 2023, 30, 70–74. [Google Scholar] [CrossRef]
- Tatarek, T.; Kronenberger, J.; Handmann, U. Functionality, Advantages and Limits of the Tesla Autopilot. 2017. Available online: https://www.handmann.net/pdf/IR-TatHanEtAl2017.pdf (accessed on 20 April 2023).
- Soori, M.; Arezoo, B.; Dastres, R. Artificial Intelligence, Machine Learning and Deep Learning in Advanced Robotics, A Review. Cogn. Robot. 2023, 3, 54–70. [Google Scholar] [CrossRef]
- Shen, G.; Zhang, J.; Marshall, A.; Cavallaro, J.R. Towards scalable and channel-robust radio frequency fingerprint identification for LoRa. IEEE Trans. Inf. Forensics Secur. 2022, 17, 774–787. [Google Scholar] [CrossRef]
- Chen, X.; He, K. Exploring simple siamese representation learning. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, Nashville, TN, USA, 20–25 June 2021; pp. 15750–15758. [Google Scholar]
- Zhu, Y.; Zhuang, F.; Wang, J.; Ke, G.; Chen, J.; Bian, J.; Xiong, H.; He, Q. Deep subdomain adaptation network for image classification. IEEE Trans. Neural Netw. Learn. Syst. 2020, 32, 1713–1722. [Google Scholar] [CrossRef]
- Ma, H.; Qiu, H.; Gao, Y.; Zhang, Z.; Abuadbba, A.; Fu, A.; Al-Sarawi, S.; Abbott, D. Quantization backdoors to deep learning models. arXiv 2021, arXiv:2108.09187. [Google Scholar]
- Capotondi, A.; Rusci, M.; Fariselli, M.; Benini, L. CMix-NN: Mixed low-precision CNN library for memory-constrained edge devices. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 871–875. [Google Scholar] [CrossRef]
- Alom, M.Z.; Moody, A.T.; Maruyama, N.; Van Essen, B.C.; Taha, T.M. Effective quantization approaches for recurrent neural networks. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–8. [Google Scholar]
- Kaushal, N.; Kaushal, P. Human identification and fingerprints: A review. J. Biomet. Biostat. 2011, 2, 2. [Google Scholar] [CrossRef]
- Henke, C. A Comprehensive Guide to IoT Protocols. Emnify 2022. Available online: https://www.emnify.com/iot-glossary/guide-iot-protocols (accessed on 24 April 2022).
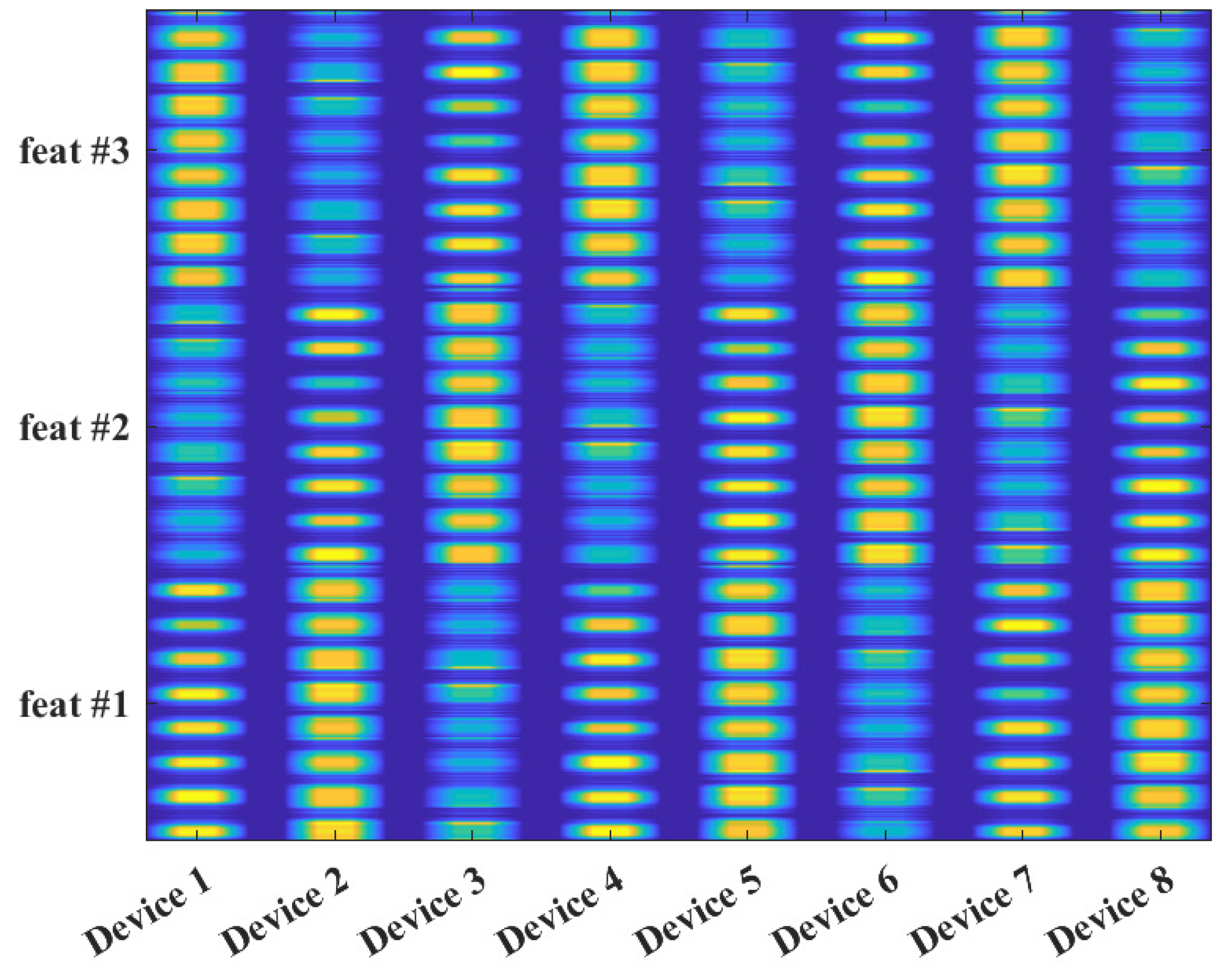

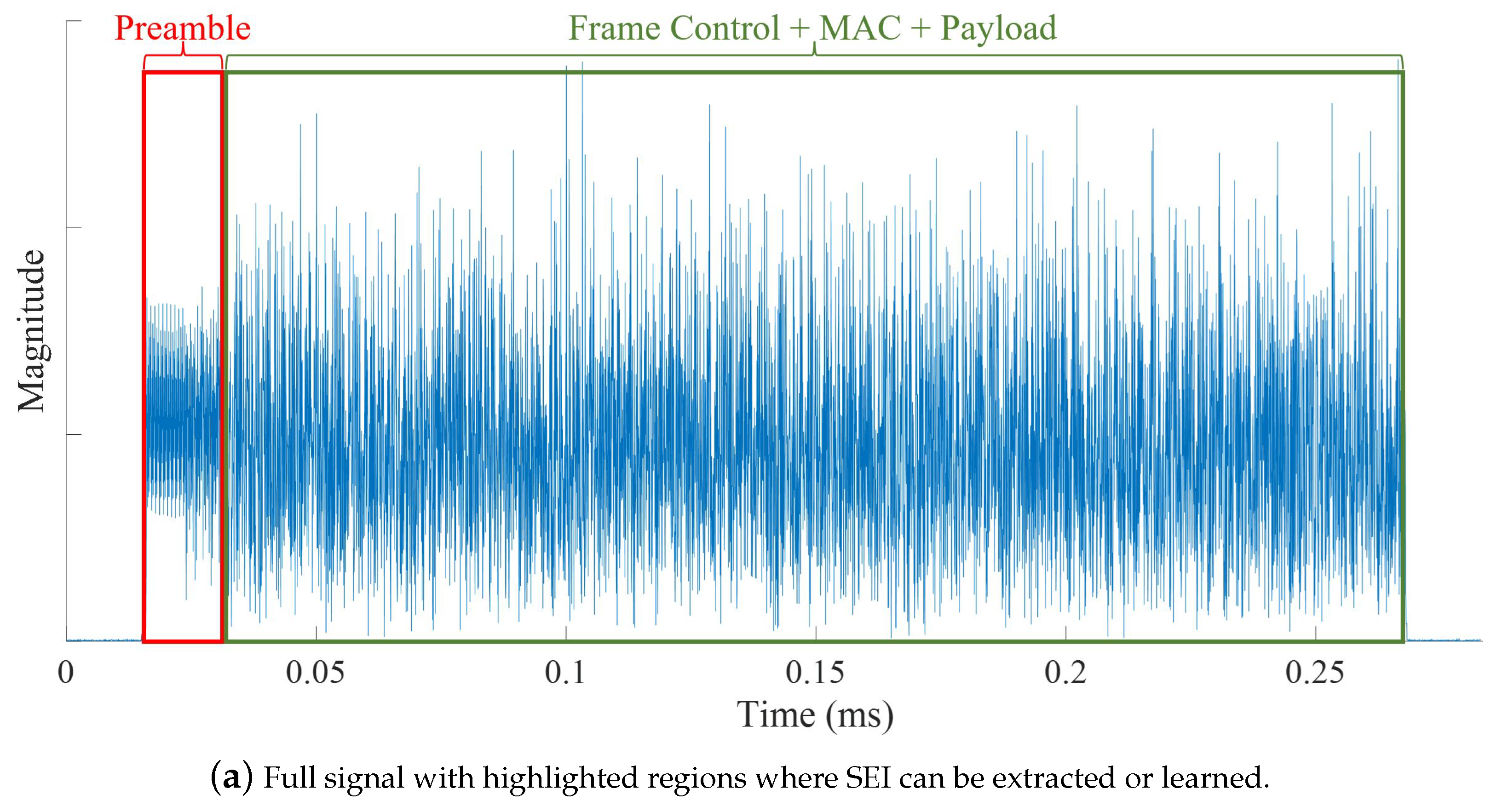
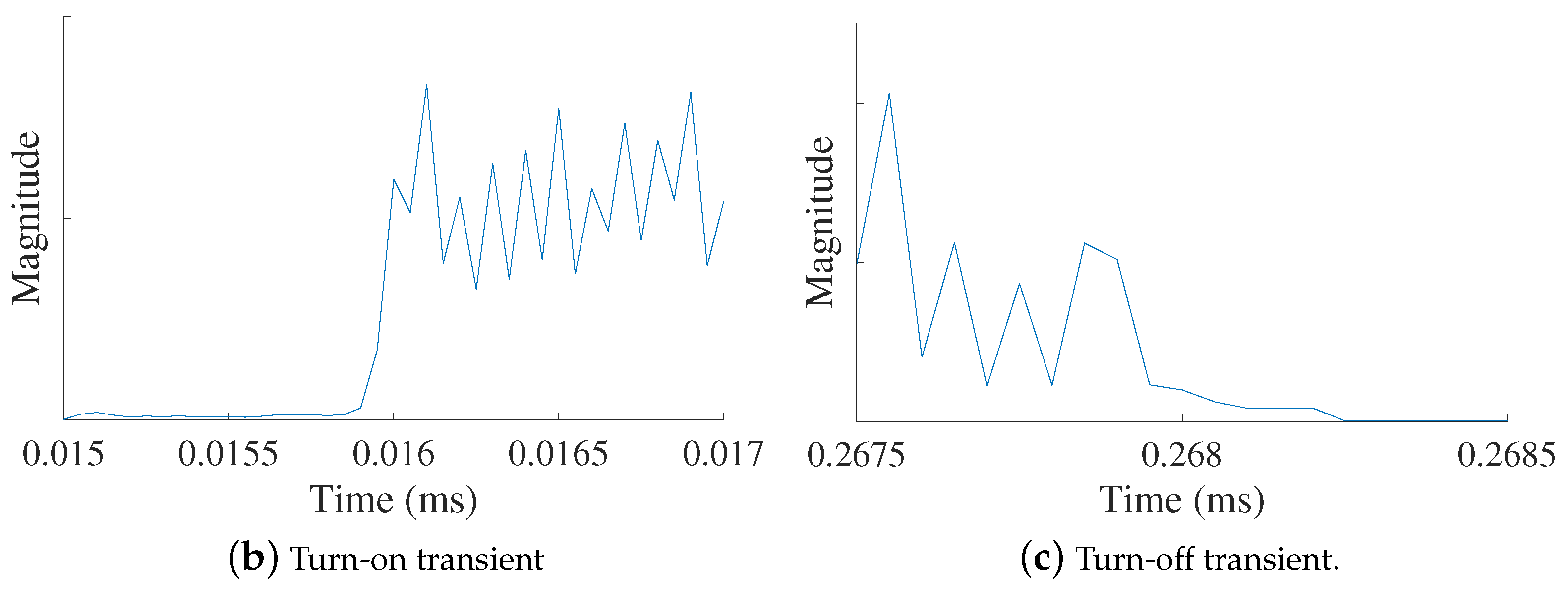
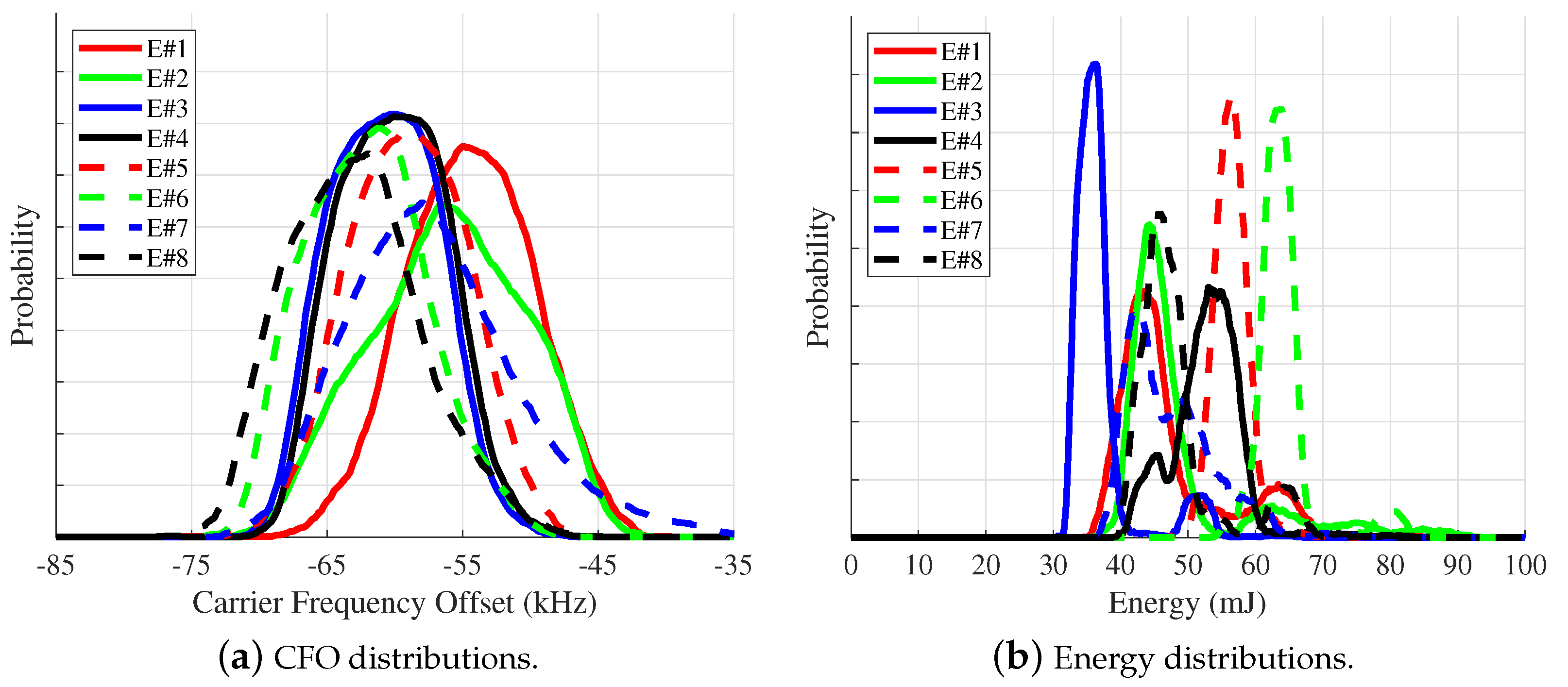
| Survey | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| This Paper | [54] | [90] | [91] | [92] | [93] | [94] | [95] | [96] | |
| Year | 2023 | 2017 | 2019 | 2020 | 2020 | 2021 | 2022 | 2022 | 2022 |
| IoT Motivated | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Handcrafted SEI | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| DL-based SEI | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Operating conditions | ✓ | ✓ | |||||||
| Threats to SEI | ✓ | ✓ | |||||||
| SEI at scale | ✓ | ||||||||
| IoT limitations | ✓ | ✓ | |||||||
| Citation | Consideration | ||
|---|---|---|---|
| Computational Resources | DL Training | Data | |
| [163] | ✓ | ✓ | |
| [164] | ✓ | ||
| [165] | ✓ | ||
| [166] | ✓ | ✓ | |
| [167] | ✓ | ✓ | |
| [105] | ✓ | ✓ | ✓ |
| [106] | ✓ | ✓ | ✓ |
| [168] | ✓ | ✓ | |
| [169] | ✓ | ✓ | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tyler, J.H.; Fadul, M.K.M.; Reising, D.R. Considerations, Advances, and Challenges Associated with the Use of Specific Emitter Identification in the Security of Internet of Things Deployments: A Survey. Information 2023, 14, 479. https://doi.org/10.3390/info14090479
Tyler JH, Fadul MKM, Reising DR. Considerations, Advances, and Challenges Associated with the Use of Specific Emitter Identification in the Security of Internet of Things Deployments: A Survey. Information. 2023; 14(9):479. https://doi.org/10.3390/info14090479
Chicago/Turabian StyleTyler, Joshua H., Mohamed K. M. Fadul, and Donald R. Reising. 2023. "Considerations, Advances, and Challenges Associated with the Use of Specific Emitter Identification in the Security of Internet of Things Deployments: A Survey" Information 14, no. 9: 479. https://doi.org/10.3390/info14090479
APA StyleTyler, J. H., Fadul, M. K. M., & Reising, D. R. (2023). Considerations, Advances, and Challenges Associated with the Use of Specific Emitter Identification in the Security of Internet of Things Deployments: A Survey. Information, 14(9), 479. https://doi.org/10.3390/info14090479









