Blockchain and Machine Learning: A Critical Review on Security
Abstract
1. Introduction
2. Background
2.1. Security and Blockchain
2.2. Blockchain and the Importance of ML
3. Methods and Materials
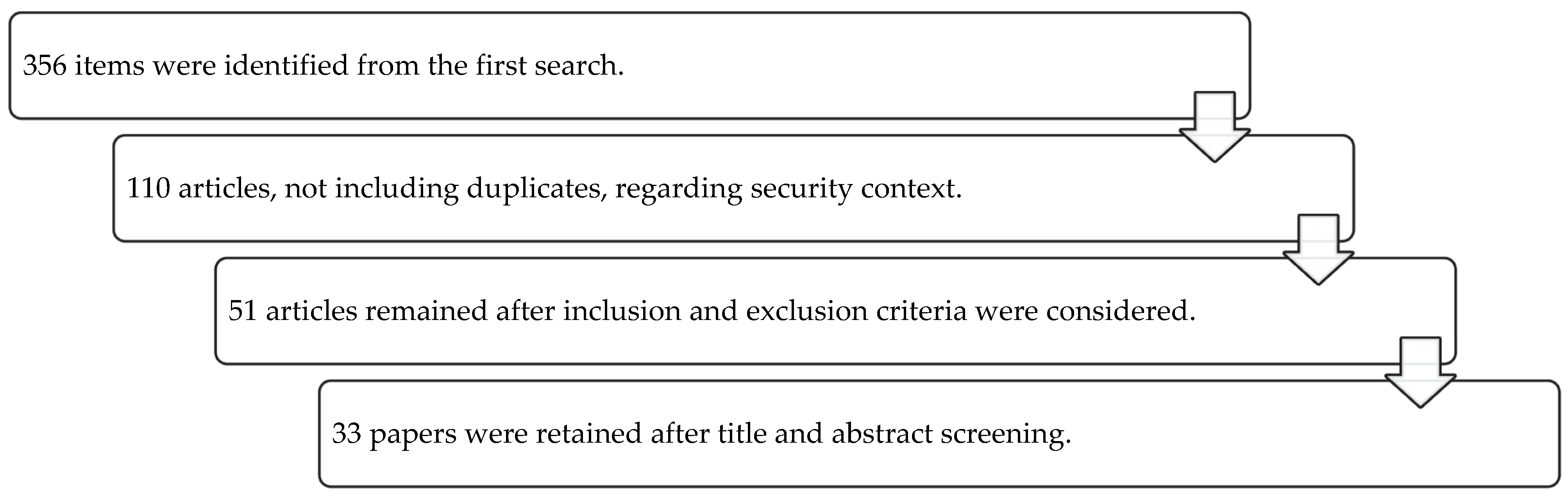
3.1. Research Method
- o
- “Machine Learning” AND “Blockchain” AND “Security”
- o
- “Machine Learning” AND “Blockchain” AND “Network Security”
- o
- “Machine Learning” AND “Blockchain” AND “Security of Data”
- o
- “Machine Learning” AND “Blockchain” AND “Cybersecurity”
- o
- “Machine Learning” AND “Blockchain” AND “Security and Privacy”
- o
- “Machine Learning” AND “Blockchain” AND “Privacy and Security”
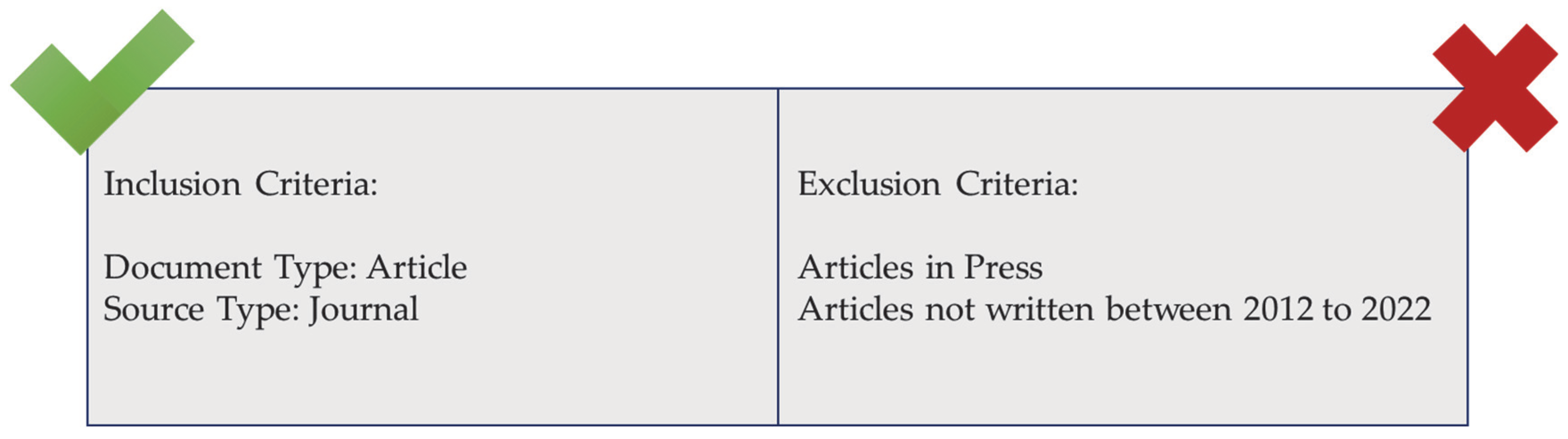
3.2. Exclusion and Inclusion
3.3. Study’s Objective
- o
- To understand the literature on ML and blockchain applications for security
- o
- To understand the significance of ML.
- o
- To understand the many solutions to these problems.
- o
- To understand the open issues, challenges, and future directions of research.
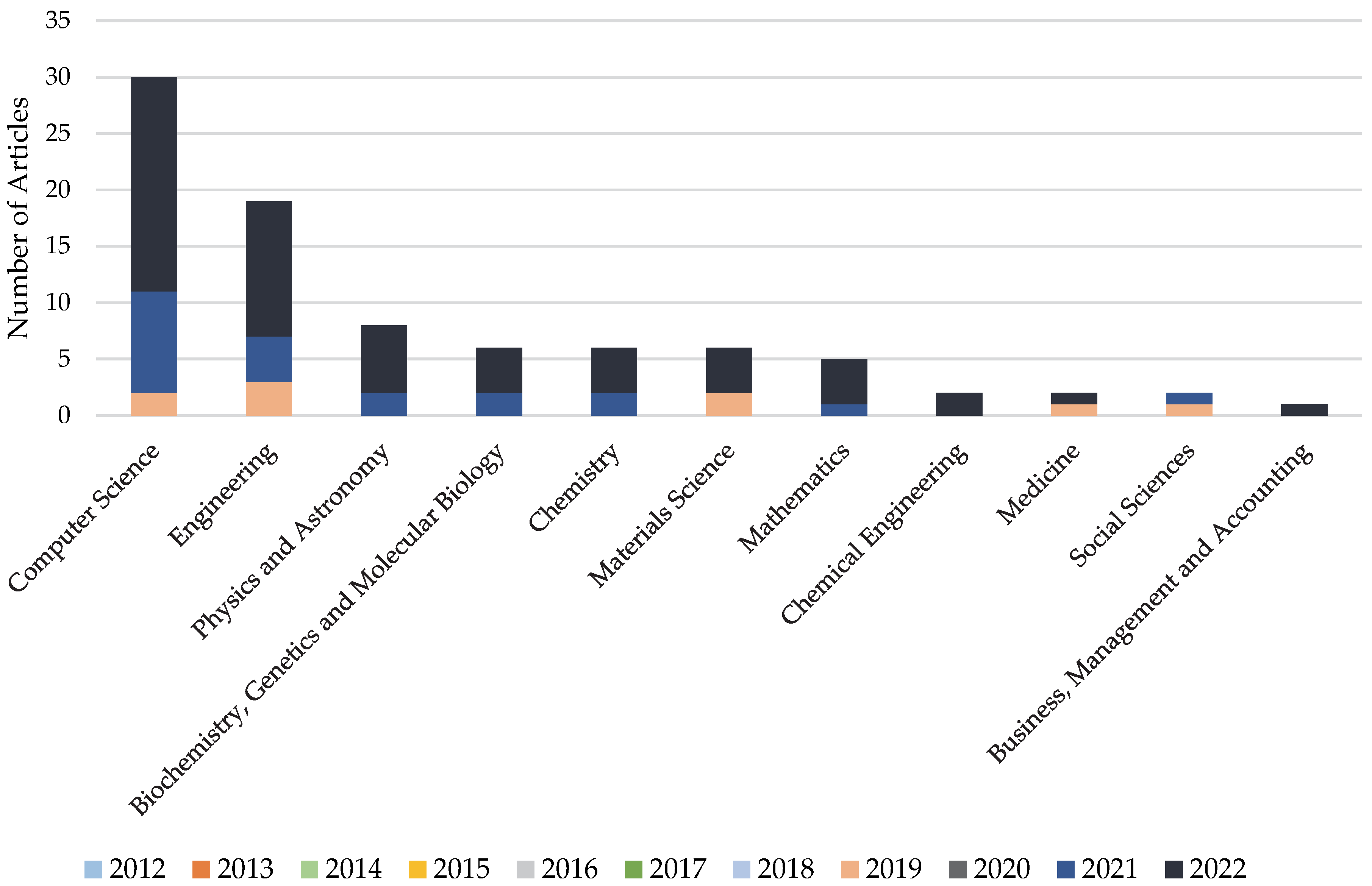
4. Current State of Scope
5. Discussion
5.1. Applications
5.2. Protocols
5.3. Algorithms
5.4. Security Analysis
6. Open Issues and Future Directions
- o
- Scalability: Blockchain technology is still comparatively sluggish and has difficulty processing large quantities of data. In addition to being computationally intensive, ML algorithms can make it difficult to process data swiftly and effectively.
- o
- Interoperability: Due to numerous blockchain platforms and standards, it can be challenging to develop interoperable systems that are compatible with multiple platforms.
- o
- Privacy: Blockchain technology can produce a transparent and unchangeable ledger of transactions, which can raise privacy concerns. In addition to collecting vast quantities of data, ML algorithms can also raise privacy concerns.
7. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Sarker, I.H. Machine learning: Algorithms, real-world applications and research directions. SN Comput. Sci. 2021, 2, 160. [Google Scholar] [CrossRef]
- Taherdoost, H.; Madanchian, M. Artificial Intelligence and Knowledge Management: Impacts, Benefits, and Implementation. Computers 2023, 12, 72. [Google Scholar] [CrossRef]
- De Breuck, P.-P.; Hautier, G.; Rignanese, G.-M. Materials property prediction for limited datasets enabled by feature selection and joint learning with MODNet. NPJ Comput. Mater. 2021, 7, 83. [Google Scholar] [CrossRef]
- Vabalas, A.; Vabalas, A.; Gowen, E.; Poliakoff, E.; Casson, A.J. Machine learning algorithm validation with a limited sample size. PLoS ONE 2019, 14, e0224365. [Google Scholar] [CrossRef]
- Liu, B.; Liu, B.; Ding, M.; Shaham, S.; Rahayu, W.; Farokhi, F.; Lin, Z. When machine learning meets privacy: A survey and outlook. ACM Comput. Surv. (CSUR) 2021, 54, 31. [Google Scholar] [CrossRef]
- Daniel, F.; Daniel, F.; Kucherbaev, P.; Cappiello, C.; Benatallah, B.; Allahbakhsh, M. Quality control in crowdsourcing: A survey of quality attributes, assessment techniques, and assurance actions. ACM Comput. Surv. (CSUR) 2018, 51, 7. [Google Scholar] [CrossRef]
- Jordaney, R.; Jordaney, R.; Sharad, K.; Dash, S.K.; Wang, Z. Transcend: Detecting concept drift in malware classification models. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017. [Google Scholar]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Ye, C.; Li, G.; Cai, H.; Gu, Y.; Fukuda, A. Analysis of security in blockchain: Case study in 51%-attack detecting. In Proceedings of the 2018 5th International Conference on Dependable Systems and Their Applications (DSA), Dalian, China, 22–23 September 2018. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the Principles of Security and Trust: 6th International Conference, POST 2017, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2017, Uppsala, Sweden, 22–29 April 2017; Proceedings 6. Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 2-1. [Google Scholar]
- Taherdoost, H. Smart Contracts in Blockchain Technology: A Critical Review. Information 2023, 14, 117. [Google Scholar] [CrossRef]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Usman, M.; Jan, M.A.; He, X.; Chen, J. A survey on representation learning efforts in cybersecurity domain. ACM Comput. Surv. (CSUR) 2019, 52, 111. [Google Scholar] [CrossRef]
- Mahdavifar, S.; Ghorbani, A.A. Application of deep learning to cybersecurity: A survey. Neurocomputing 2019, 347, 149–176. [Google Scholar] [CrossRef]
- Kumble, G.P. Practical Artificial Intelligence and Blockchain: A Guide to Converging Blockchain and AI to Build Smart Applications for New Economies; Packt Publishing Ltd.: Birmingham, UK, 2020. [Google Scholar]
- Habib, G.; Sharma, S.; Ibrahim, S.; Ahmad, I.; Qureshi, S.; Ishfaq, M. Blockchain Technology: Benefits, Challenges, Applications, and Integration of Blockchain Technology with Cloud Computing. Future Internet 2022, 14, 341. [Google Scholar] [CrossRef]
- Craig, W.L.; Park, W.W.; Paulsson, J. International Chamber of Commerce Arbitration; Oceana Publications: New York, NY, USA, 1990; Volume 3. [Google Scholar]
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Cai, C.W. Disruption of financial intermediation by FinTech: A review on crowdfunding and blockchain. Account. Financ. 2018, 58, 965–992. [Google Scholar] [CrossRef]
- Stephen, R.; Alex, A. Alex, A. A review on blockchain security. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2018. [Google Scholar]
- Hong, H.; Sun, Z. A secure peer to peer multiparty transaction scheme based on blockchain. Peer-to-Peer Netw. Appl. 2021, 14, 1106–1117. [Google Scholar] [CrossRef]
- Anderson, R. Security Engineering: A Guide to Building Dependable Distributed Systems; John Wiley & Sons: Hoboken, NJ, USA, 2020. [Google Scholar]
- Xinyi, Y.; Yi, Z.; He, Y. Technical characteristics and model of blockchain. In Proceedings of the 2018 10th international Conference on Communication Software and Networks (ICCSN), Chengdu, China, 6–9 July 2018. [Google Scholar]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A survey of blockchain technology applied to smart cities: Research issues and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Gai, K.; Guo, J.; Zhu, L.; Yu, S. Blockchain meets cloud computing: A survey. IEEE Commun. Surv. Tutor. 2020, 22, 2009–2030. [Google Scholar] [CrossRef]
- Wang, W.; Huang, H.; Zhang, L.; Su, C. Secure and efficient mutual authentication protocol for smart grid under blockchain. Peer-to-Peer Netw. Appl. 2021, 14, 2681–2693. [Google Scholar] [CrossRef]
- Wang, W.; Huang, H.; Zhang, L.; Han, Z.; Qiu, C.; Su, C. BlockSLAP: Blockchain-based secure and lightweight authentication protocol for smart grid. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021. [Google Scholar]
- Taherdoost, H. A critical review of blockchain acceptance models—Blockchain technology adoption frameworks and applications. Computers 2022, 11, 24. [Google Scholar] [CrossRef]
- Kulkarni, N.; Pise, R.; Patil, S. A Deep Dive into Blockchain Consensus Algorithms, in Blockchain for Smart Systems; Chapman and Hall/CRC: Boca Raton, FL, USA, 2022; pp. 67–82. [Google Scholar]
- Sayadi, S.; Rejeb, S.B.; Choukair, Z. Blockchain challenges and security schemes: A survey. In Proceedings of the 2018 Seventh International Conference on Communications and Networking (ComNet), Hammamet, Tunisia, 1–3 November 2018. [Google Scholar]
- Göbel, J.; Keeler, H.P.; Krzesinski, A.E.; Taylor, P.G. Bitcoin blockchain dynamics: The selfish-mine strategy in the presence of propagation delay. Perform. Eval. 2016, 104, 23–41. [Google Scholar] [CrossRef]
- Tosh, D.K.; Shetty, S.; Liang, X.; Kamhoua, C.A.; Kwiat, K.A.; Njilla, L. Security implications of blockchain cloud with analysis of block withholding attack. In Proceedings of the 2017 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID), Madrid, Spain, 14–17 May 2017. [Google Scholar]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A provably secure proof-of-stake blockchain protocol. In Proceedings of the Advances in Cryptology—CRYPTO 2017: 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Proceedings, Part I.. Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.; Alshamari, M.; Cao, Y. A survey on blockchain technology: Evolution, architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Singh, S.; Hosen, A.S.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed IoT network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Taherdoost, H. Blockchain Technology and Artificial Intelligence Together: A Critical Review on Applications. Appl. Sci. 2022, 12, 12948. [Google Scholar] [CrossRef]
- Mayo, M. Frameworks for approaching the machine learning process. KDnuggets, 19 October 2018. [Google Scholar]
- Balusamy, B.; Chilamkurti, N.; Beena, L.A.; Poongodi, T. Blockchain and Machine Learning for e-Healthcare Systems. The Institution of Engineering and Technology. 2021. Available online: https://www.amazon.ca/Blockchain-Machine-Learning-Healthcare-Systems/dp/1839531142 (accessed on 1 May 2023).
- Kumari, A.; Tanwar, S.; Tyagi, S.; Kumar, N. Verification and validation techniques for streaming big data analytics in internet of things environment. IET Netw. 2019, 8, 155–163. [Google Scholar] [CrossRef]
- Gaur, R.; Prakash, S.; Kumar, S.; Abhishek, K.; Msahli, M.; Wahid, A. A Machine-Learning–Blockchain-Based Authentication Using Smart Contracts for an IoHT System. Sensors 2022, 22, 9074. [Google Scholar] [CrossRef]
- Mrabet, H.; Alhomoud, A.; Jemai, A.; Trentesaux, D. A Secured Industrial Internet-of-Things Architecture Based on Blockchain Technology and Machine Learning for Sensor Access Control Systems in Smart Manufacturing. Appl. Sci. 2022, 12, 4641. [Google Scholar] [CrossRef]
- Hamodi, Y.I.; Aljanabi, Y.I.; Majeed, A.A.; Jihad, K.H.; Qader, B.A. Detect and Mitigate Blockchain-Based DDoS Attacks Using Machine Learning and Smart Contracts. Informatica 2022, 46, 55–62. [Google Scholar]
- Shahbazi, Z.; Byun, Y.C. Blockchain-Based Event Detection and Trust Verification Using Natural Language Processing and Machine Learning. IEEE Access 2022, 10, 5790–5800. [Google Scholar]
- Zhou, Q.; Zheng, K.; Zhang, K.; Hou, L.; Wang, X. Vulnerability Analysis of Smart Contract for Blockchain-Based IoT Applications: A Machine Learning Approach. IEEE Internet Things J. 2022, 9, 24695–24707. [Google Scholar] [CrossRef]
- Al-Qarafi, A.; Alrowais, F.; Alotaibi, S.S.; Nemri, N.; Al-Wesabi, F.N.; Al Duhayyim, M.; Marzouk, R.; Othman, M.; Al-Shabi, M. Optimal Machine Learning Based Privacy Preserving Blockchain Assisted Internet of Things with Smart Cities Environment. Appl. Sci. 2022, 12, 5893. [Google Scholar] [CrossRef]
- Tian, Y.; Tian, Y.; Li, T.; Xiong, J.; Bhuiyan, M.Z.A.; Ma, J.; Peng, C. A Blockchain-Based Machine Learning Framework for Edge Services in IIoT. IEEE Trans. Ind. Inform. 2022, 18, 1918–1929. [Google Scholar] [CrossRef]
- Yu, Y.; Chen, R.; Li, H.; Li, Y.; Tian, A. Toward data security in edge intelligent IIoT. IEEE Netw. 2019, 33, 20–26. [Google Scholar] [CrossRef]
- Liu, X.; Xie, L.; Wang, Y.; Zou, J.; Xiong, J.; Ying, Z.; Vasilakos, A.V. Privacy and security issues in deep learning: A survey. IEEE Access 2020, 9, 4566–4593. [Google Scholar] [CrossRef]
- Hasan, N.; Chaudhary, K.; Alam, M. A novel blockchain federated safety-as-a-service scheme for industrial IoT using machine learning. Multimed. Tools Appl. 2022, 81, 36751–36780. [Google Scholar] [CrossRef]
- Aldughayfiq, B.; Sampalli, S. Patients’, pharmacists’, and prescribers’ attitude toward using blockchain and machine learning in a proposed ePrescription system: Online survey. JAMIA Open 2022, 5, ooab115. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Srivastava, G.; Gupta, G.P.; Tripathi, R.; Gadekallu, T.R.; Xiong, N.N. PPSF: A Privacy-Preserving and Secure Framework Using Blockchain-Based Machine-Learning for IoT-Driven Smart Cities. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2326–2341. [Google Scholar] [CrossRef]
- Khan, M.A.; Khan, M.A.; Abbas, S.; Rehman, A.; Saeed, Y.; Zeb, A.; Uddin, M.I.; Nasser, N.; Ali, A. A Machine Learning Approach for Blockchain-Based Smart Home Networks Security. IEEE Netw. 2021, 35, 223–229. [Google Scholar] [CrossRef]
- Yi, H. Securing instant messaging based on blockchain with machine learning. Saf. Sci. 2019, 120, 6–13. [Google Scholar] [CrossRef]
- Zhang, R.; Song, M.; Li, T.; Yu, Z.; Dai, Y.; Liu, X.; Wang, G. Democratic learning: Hardware/software co-design for lightweight blockchain-secured on-device machine learning. J. Syst. Archit. 2021, 118, 102205. [Google Scholar] [CrossRef]
- Benjamin Franklin, I.; Jerald, M.P.A.; Bhuvaneswari, R. Machine Learning-Based Trust Management in Cloud Using Blockchain Technology. SN Comput. Sci. 2022, 3, 429. [Google Scholar] [CrossRef]
- Priyadharshini, K.; Canessane, R.A. Light chain consensus reinforcement machine learning: An effective blockchain model for Internet of Things using for its advancement and challenges. Comput. Intell. 2021, 37, 1651–1672. [Google Scholar] [CrossRef]
- Vairagade, R.S.; Brahmananda, S.H. Enabling machine learning-based side-chaining for improving QoS in blockchain-powered IoT networks. Trans. Emerg. Telecommun. Technol. 2022, 33, e4433. [Google Scholar] [CrossRef]
- Vargas, H.; Lozano-Garzon, C.; Montoya, G.A.; Donoso, Y. Detection of security attacks in industrial IoT networks: A blockchain and machine learning approach. Electronics 2021, 10, 2662. [Google Scholar] [CrossRef]
- Choudhary, S.; Dorle, S. A quality of service-aware high-security architecture design for software-defined network powered vehicular ad-hoc networks using machine learning-based blockchain routing. Concurr. Comput. Pract. Exp. 2022, 34, e6993. [Google Scholar] [CrossRef]
- Pon, P.; Kavitha, V. Blockchain based cloud service security architecture with distributed machine learning for smart device traffic record transaction. Concurr. Comput. Pract. Exp. 2022, 34, e683. [Google Scholar] [CrossRef]
- Nasir, M.U.; Nasir, M.U.; Khan, S.; Mehmood, S.; Khan, M.A.; Zubair, M.; Hwang, S.O. Network Meddling Detection Using Machine Learning Empowered with Blockchain Technology. Sensors 2022, 22, 6755. [Google Scholar] [CrossRef]
- Unal, D.; Hammoudeh, M.; Khan, M.A.; Abuarqoub, A.; Epiphaniou, G.; Hamila, R. Integration of federated machine learning and blockchain for the provision of secure big data analytics for Internet of Things. Comput. Secur. 2021, 109, 102393. [Google Scholar] [CrossRef]
- Shahin, R.; Sabri, K.E. A Secure IoT Framework Based on Blockchain and Machine Learning. Int. J. Comput. Digit. Syst. 2022, 11, 671–683. [Google Scholar] [CrossRef]
- Jamil, F.; Kahng, H.K.; Kim, S.; Kim, D.H. Towards secure fitness framework based on IoT-enabled blockchain network integrated with machine learning algorithms. Sensors 2021, 21, 1640. [Google Scholar] [CrossRef] [PubMed]
- Kim, H.; Kim, S.H.; Hwang, J.Y.; Seo, C. Efficient privacy-preserving machine learning for blockchain network. IEEE Access 2019, 7, 136481–136495. [Google Scholar] [CrossRef]
- Shahbazi, Z.; Byun, Y.C. Integration of blockchain, IoT and machine learning for multistage quality control and enhancing security in smart manufacturing. Sensors 2021, 21, 1467. [Google Scholar] [CrossRef] [PubMed]
- Shahbazi, Z.; Byun, Y.C. Blockchain and machine learning for intelligent multiple factor-based ride-hailing services. Comput. Mater. Contin. 2022, 70, 4429–4446. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. TP2SF: A Trustworthy Privacy-Preserving Secured Framework for sustainable smart cities by leveraging blockchain and machine learning. J. Syst. Archit. 2021, 115, 101954. [Google Scholar] [CrossRef]
- Agrawal, S.; Kumar, S. MLSMBQS: Design of a Machine Learning Based Split & Merge Blockchain Model for QoS-Aware Secure IoT Deployments. Int. J. Image Graph. Signal Process. 2022, 14, 58–71. [Google Scholar] [CrossRef]
- Wang, H.; Wang, Y.; Cao, Z.; Li, Z.; Xiong, G. An overview of blockchain security analysis. In Proceedings of the Cyber Security: 15th International Annual Conference, CNCERT 2018, Beijing, China, 14–16 August 2018; Revised Selected Papers 15. Springer: Singapore, 2019. [Google Scholar]
- Du, R.; Gao, Y.; Liu, C. Fine-grained Web Service Trust Detection: A Joint Method of Machine Learning and Blockchain. J. Web Eng. 2022, 21, 1519–1542. [Google Scholar] [CrossRef]
- Ashfaq, T.; Ashfaq, T.; Khalid, M.I.; Ali, G.; Affendi, M.E.; Iqbal, J.; Hussain, S.; Ullah, S.S.; Yahaya, A.S.; Khalid, R.; et al. An Efficient and Secure Energy Trading Approach with Machine Learning Technique and Consortium Blockchain. Sensors 2022, 22, 7263. [Google Scholar] [CrossRef]
- Ashfaq, T.; Khalid, R.; Yahaya, A.S.; Aslam, S.; Azar, A.T.; Alsafari, S.; Hameed, I.A. A Machine Learning and Blockchain Based Efficient Fraud Detection Mechanism. Sensors 2022, 22, 7162. [Google Scholar] [CrossRef]
- Sajid, M.B.E.; Ullah, S.; Javaid, N.; Ullah, I.; Qamar, A.M.; Zaman, F. Exploiting Machine Learning to Detect Malicious Nodes in Intelligent Sensor-Based Systems Using Blockchain. Wirel. Commun. Mob. Comput. 2022, 2022, 7386049. [Google Scholar] [CrossRef]
- Xiong, W.; Xiong, L. Smart Contract Based Data Trading Mode Using Blockchain and Machine Learning. IEEE Access 2019, 7, 102331–102344. [Google Scholar] [CrossRef]
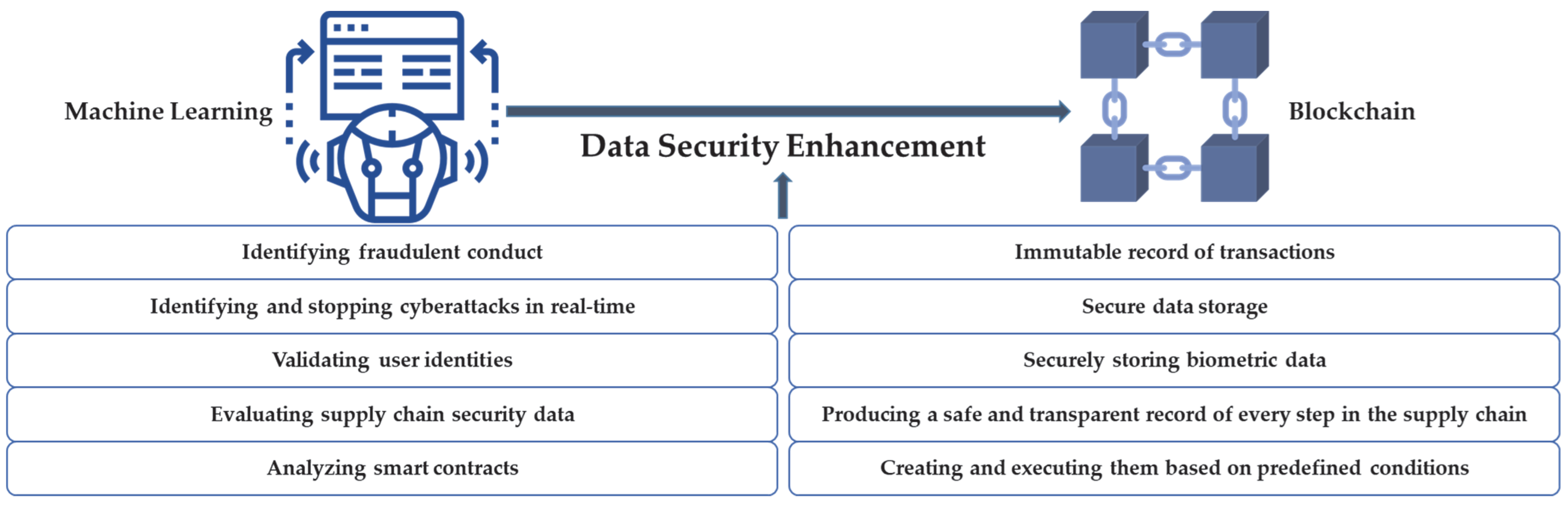
| Application | Advantages | Challenges | References |
|---|---|---|---|
| Industrial automation security | Cryptographic protection of data and immutability | Functionality requires minor enhancements, and post-implementation user research is required. | [51,52] |
| Smart cities powered by IoT | Superior performance, security, and privacy preservation | verifiability, privacy, transparency, scalability, and Centralization | [53] |
| Secure communication in IoT | resource efficiency and decentralized privacy protection | The computational and temporal intensity of existing methods | [54] |
| Instant messaging | Anomaly detection, integrity verification, privacy protection, and message authentication | Implementation obstacles include verifiability, transparency, scalability, and centralization. | [55] |
| Protocol | Advantages | Applications | References |
|---|---|---|---|
| DemL | Cost-effective trust in an environment devoid of trust and protection against privacy leakage and model contamination | AI learning | [56] |
| BaaS | Superior level of defense against Byzantine attacks | Cloud computing | [57] |
| LCC-RML | Scalability, latency, and security are enhanced without compromising the decentralized system. | IoT systems | [58,59] |
| TMLVD | Adequate detection tools for identifying particular security flaws | Smart contracts | [46] |
| KNN | A practical method for locating and containing intrusions in an IoT network | IoT device networks | [60] |
| Delay-Aware, Energy-Aware, Throughput-Aware, and PDR-Aware Underlying Protocol | Reduced energy consumption and E2E latency, enhanced network throughput | VANET | [61] |
| SEC-LearningChain | Secure data transactions and effective service for sharing data | P2P network | [62] |
| SVM | Enhancing the protection of trained models, network communications, and transaction data | Runtime and beforehand security in ML | [63] |
| Federated ML with fuzzy data and Blockchain | Protecting the integrity of trained models, preventing model poisoning, identifying anomalies, and secures IoT systems | Secure and private big data analytics services | [64] |
| ML Algorithms Used | Objective | References |
|---|---|---|
| Naive Bayes, AdaBoost, KNN, DT, Random Forest, LR | Safely storing IoT data while preserving its availability and integrity | [65] |
| KNN, SVM, LR, DT | Securing IoT fitness gadgets | [66] |
| DML | Operating a learning model without data centralization | [67] |
| XGBoost, KNN | Multistage quality control | [68] |
| ML DT, XGBoost | Enhancing the safety of passenger transaction data and reducing waiting time | [69] |
| XGBoost | Providing the TP2SF for smart cities | [70] |
| System | Method | Outcome | Limitation | References |
|---|---|---|---|---|
| ML Technique and Consortium Blockchain | Oyente | Enhancing the security and confidentiality of transactions | Using their recommended model in a real-world setting without comparing it to other charge schemes with the same characteristics. | [74] |
| ML and Blockchain | Oyente | The suggested method detects transaction fraud correctly. | Is susceptible to the adversary’s attack | [75] |
| Exploiting ML in Intelligent Sensor-Based Systems Using Blockchain | Oyente | The smart contract is resilient against flaws. | When a function is run, it prevents the execution of other functions. | [76] |
| Data Trade Mode Based on Smart Contracts Utilizing Blockchain and ML | Not mentioned | Addressing the issue of the data trading center’s inability to keep data in the conventional data trading mode, to preserve the data owner’s rights and interests and support the growth of data trading. | The remedy to the issue of data resale is to sign a non-resale contract, although signing a contract cannot remove the problem of data resale. | [77] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Taherdoost, H. Blockchain and Machine Learning: A Critical Review on Security. Information 2023, 14, 295. https://doi.org/10.3390/info14050295
Taherdoost H. Blockchain and Machine Learning: A Critical Review on Security. Information. 2023; 14(5):295. https://doi.org/10.3390/info14050295
Chicago/Turabian StyleTaherdoost, Hamed. 2023. "Blockchain and Machine Learning: A Critical Review on Security" Information 14, no. 5: 295. https://doi.org/10.3390/info14050295
APA StyleTaherdoost, H. (2023). Blockchain and Machine Learning: A Critical Review on Security. Information, 14(5), 295. https://doi.org/10.3390/info14050295









