Impact of Social Media Behavior on Privacy Information Security Based on Analytic Hierarchy Process
Abstract
:1. Introduction
2. Research Framework
2.1. Literature Review
2.1.1. Types of User’s Behavior
2.1.2. Types of Privacy
2.1.3. Facebook Case Study
2.2. Theoretical Underpinnings
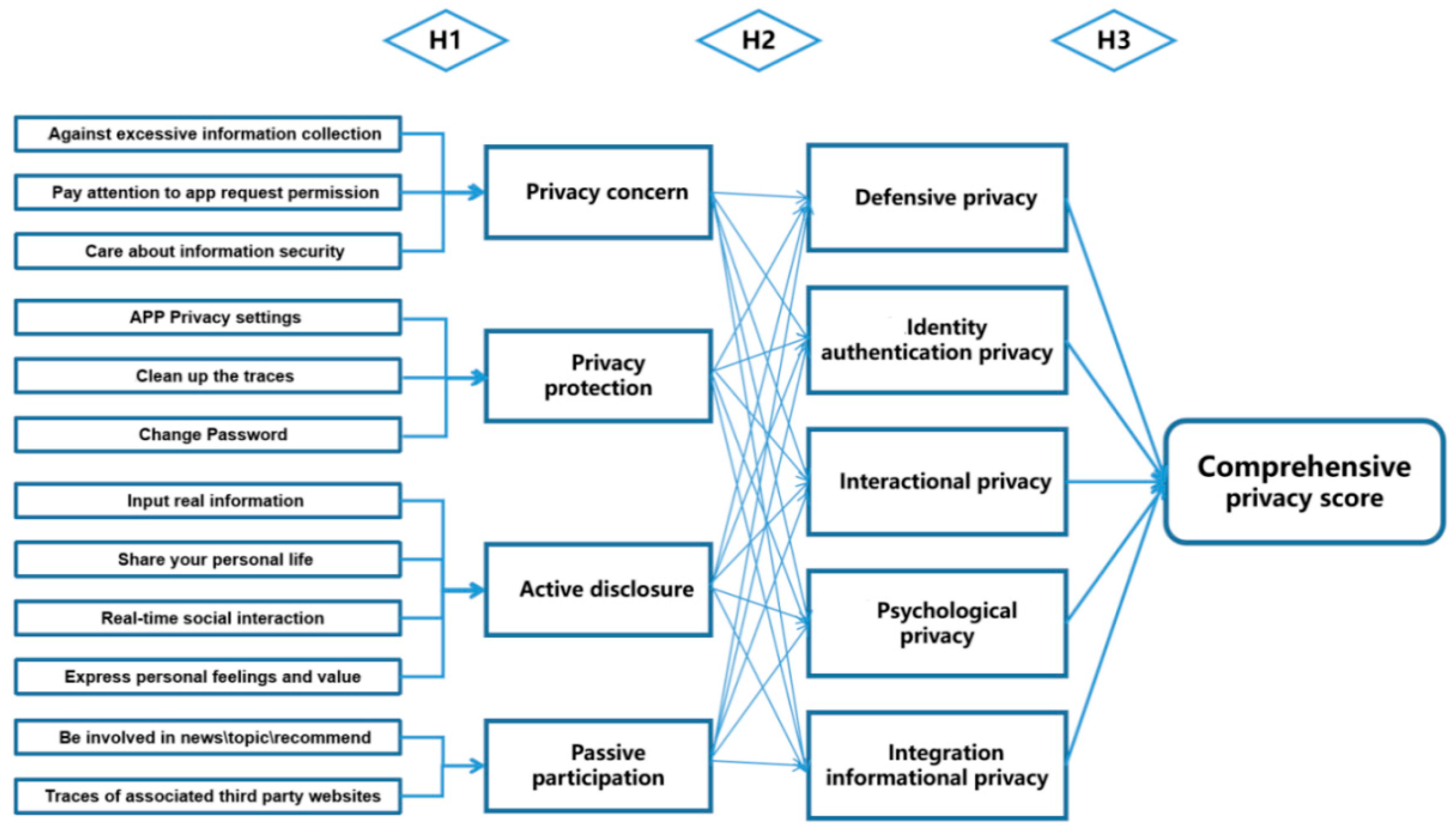
2.3. Research Model
2.4. Hypotheses Building
- H2a. Privacy Concern: H1a. Against excessive information collection; H1b. Pay attention to app request permission; H1c. Care about information security.
- H2b. Privacy Protection: H1d. APP Privacy settings; H1e. Clean up the traces; H1f. Change Password.
- H2c. Active disclosure: H1g. Input real information; H1h. Share your personal life; H1i. Real-time social interaction. H1j. Express personal feelings and value.
- H2d. Passive participation: H1k. News and information disclosure; H1l. Traces of associated third party websites.
- H3a. Defensive privacy—It mainly describes the following aspects of privacy: virtual territory/accessibility.
- H3b. Identity authentication privacy—It mainly describes the following aspects of privacy: factual/personal/Bodily/Biological.
- H3c. Interactional privacy—It mainly describes the following aspects of privacy: Communication/comment/share.
- H3d. Psychological privacy—It mainly describes the following aspects of privacy: emotion/decision/value/knowledge.
- H3e. Integration informational privacy—It mainly describes the following aspects of privacy: Proprietary/preference/Commercial history and traces.
3. Results
3.1. Descriptive Statistical Analysis
3.2. Analytic Hierarchy Process
3.2.1. Determine the Measurement Table
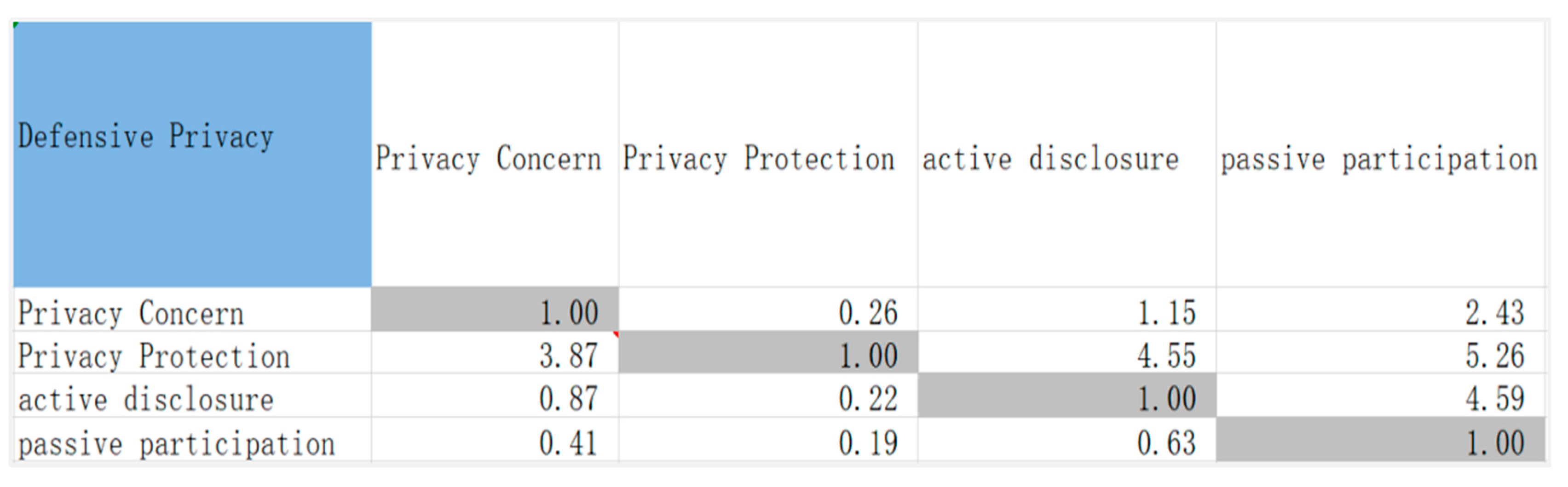
3.2.2. Construct Judgment Matrix
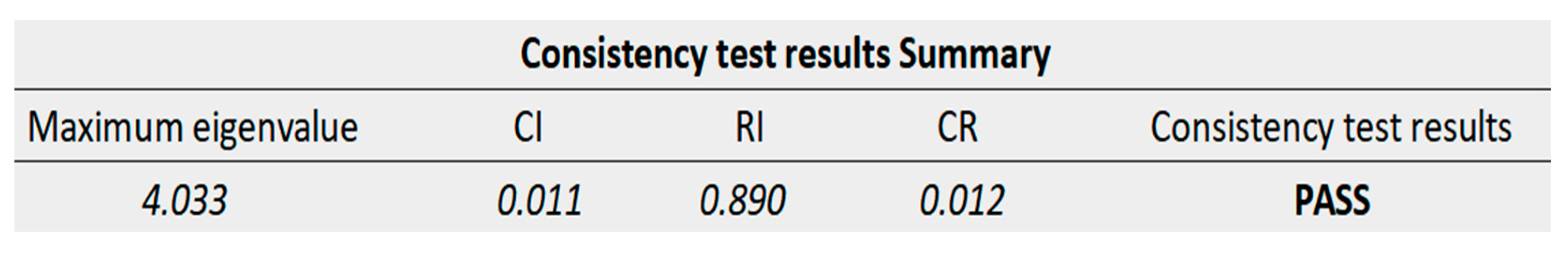
3.2.3. Consistency Test
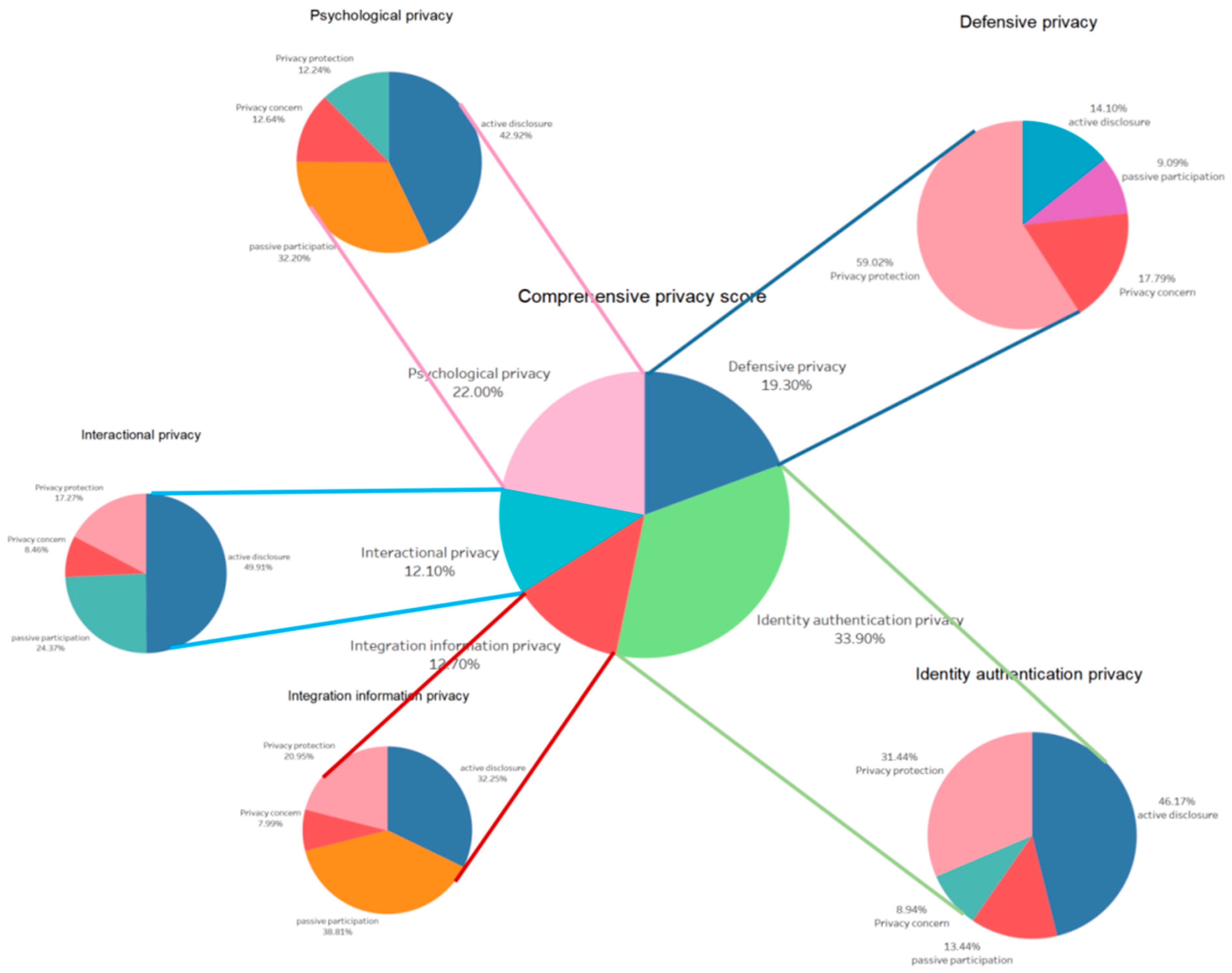
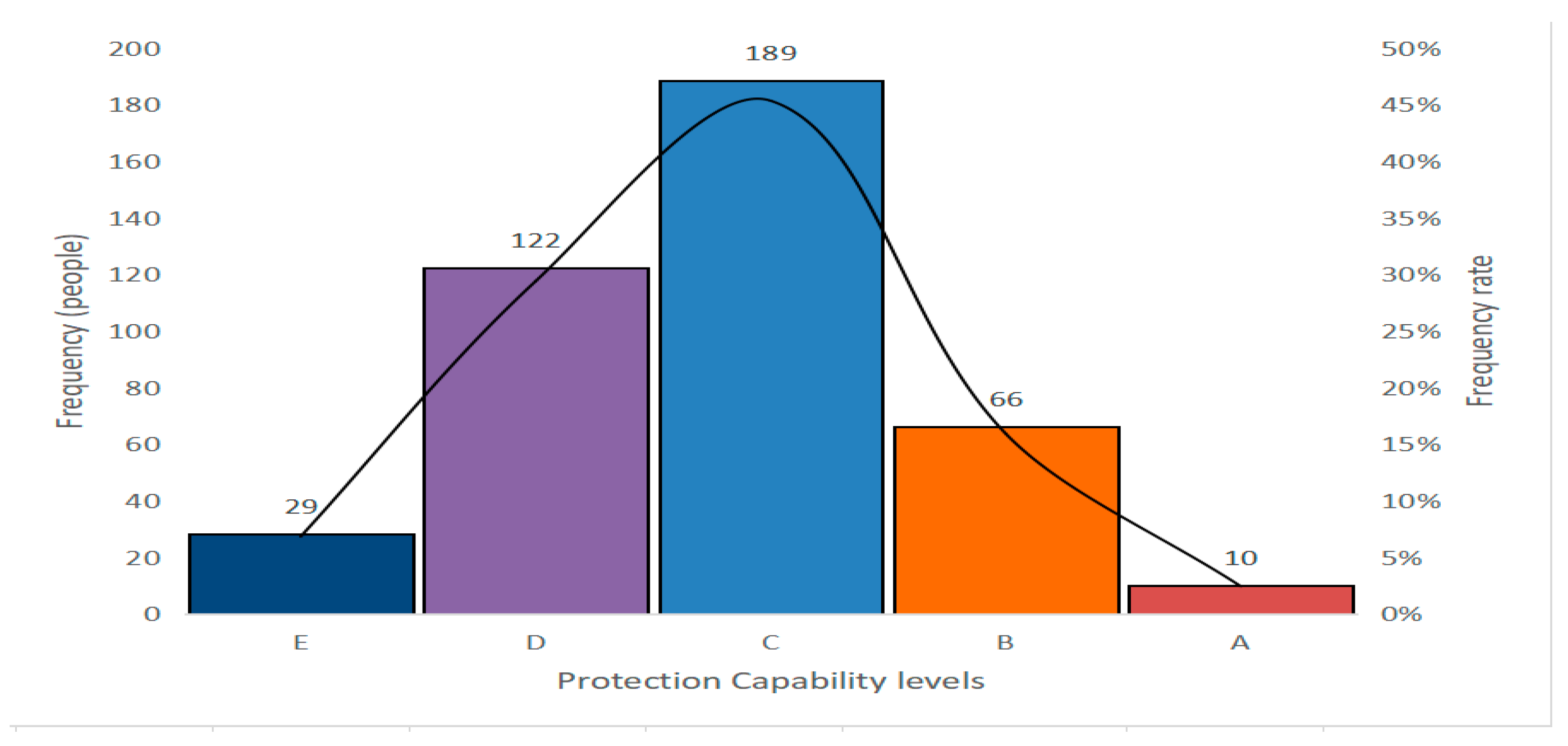
3.2.4. Model Analysis Result
3.3. User Behavior Empirical Analysis
3.3.1. User Behavior Evaluation Model
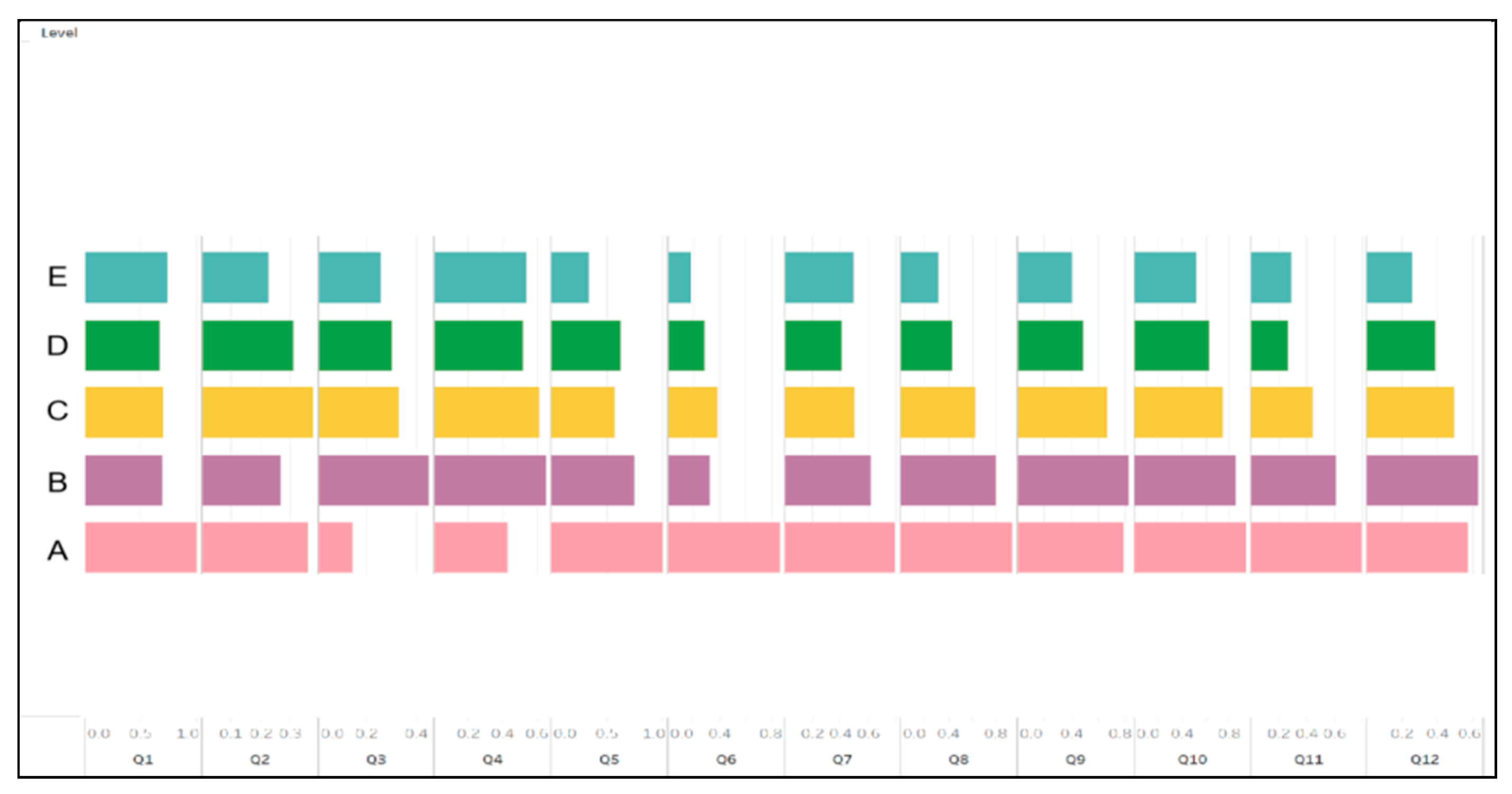
3.3.2. Survey Result Analysis
4. Discussion
5. Conclusions
6. Limitations and Improvements
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kenton, W.; Mansa, J. Understanding Social Networking. Available online: https://www.investopedia.com/terms/s/social-networking.asp (accessed on 10 November 2020).
- Ryan, T.; Xenos, S. Who uses Facebook? An investigation into the relationship between the Big Five, shyness, narcissism, loneliness, and Facebook usage. Comput. Hum. Behav. 2011, 27, 1658–1664. [Google Scholar] [CrossRef]
- Wang, X.; Sun, X. Evaluation of personal Privacy Disclosure Prevention Ability based on Mobile Social Network. Mod. Inf. Technol. 2019, 3, 144–147. [Google Scholar]
- Fuchs, C. An Alternative View of Privacy on Facebook. Information 2011, 2, 140–165. Available online: https://www.mdpi.com/2078-2489/2/1/140/htm (accessed on 7 November 2020). [CrossRef] [Green Version]
- Tavani, H.T. Informational privacy: Concepts, theories, and controversies. In The Handbook of Information and Computer Ethics; Fuchs, C., Ed.; Rivier University: Nashua, NH, USA, 2008; pp. 131–164. [Google Scholar]
- Gu, L. Integrated privacy: A new type of privacy in the era of big data. Nanjing Soc. Sci. 2020, 4, 106–111+122. [Google Scholar] [CrossRef]
- Clement, J. Facebook: Number of Users Worldwide. Available online: https://www.statista.com/statistics/490424/number-of-worldwide-facebook-users/ (accessed on 7 November 2020).
- Smith, K. 53 Incredible Facebook Statistics and Facts. Available online: https://www.brandwatch.com/blog/facebook-statistics/ (accessed on 7 November 2020).
- Nyoni, P.; Velempini, M. Privacy and user awareness on Facebook. South Afr. J. Sci. 2018, 114, 1–5. Available online: https://www.sajs.co.za/article/view/5165 (accessed on 7 November 2020). [CrossRef]
- Wang, N.; Xu, H.; Grossklags, J. Third-party apps on Facebook: Privacy and the illusion of control. In Proceedings of the 5th ACM Symposium on Computer Human Interaction for Management of Information Technology, New York, NY, USA, 4 December 2011; Available online: http://docplayer.net/17187683-Third-party-apps-on-facebook-privacy-and-the-illusion-of-control.html (accessed on 7 November 2020).
- Liu, Y.; Gummadi, K.P.; Krishnamurthy, B.; Mislove, A. Analyzing Facebook Privacy Settings: User Expectations vs. Reality. In Proceedings of the 2011 ACM SIGCOMM Conference on Internet Measurement Conference, New York, NY, USA, 2 November 2011; Available online: https://scinapse.io/papers/2118994807 (accessed on 7 November 2020).
- Bumgarner, B.A. You Have Been Poked: Exploring the Uses and Gratifications of Facebook among Emerging Adults. Available online: https://firstmonday.org/article/view/2026/1897 (accessed on 7 November 2020).
- Wang, A.; Zhang, A.; Xu, Y. Privacy in Online Social Networks. In Proceedings of the Thirty Second International Conference on Information Systems, Shanghai, China, 4–7 December 2011. [Google Scholar]
- Callahan, M. Big Brother 2.0: 160,000 Facebook Pages Are Hacked a Day. Available online: https://nypost.com/2015/03/01/big-brother-2-0-160000-facebook-pages-are-hacked-a-day/ (accessed on 13 November 2020).
- Facebook Faces $5 Billion Fine Over Privacy Violations. 2019. Available online: https://www.dw.com/en/facebook-faces-5-billion-fine-over-privacy-violations/a-49575702 (accessed on 13 November 2020).




| Types of User Behavior | Variables in Twelve User Behaviors | Mean | SD | Description |
|---|---|---|---|---|
| Privacy Concern | Against excessive information collection | 5.67 | 1.43 | The degree of over-collection of information on social media |
| Pay attention to app request permission | 2.23 | 1.39 | The degree that users pay attention to app request permission and read privacy policy statement | |
| Care about information security | 6.56 | 0.86 | The importance of information security | |
| Privacy Protection | App privacy settings | 4.04 | 1.52 | The degree of application privacy settings can help reduce privacy leaks |
| Clean up the traces | 3.49 | 1.63 | The extent to which clean up the traces on social media can help reduce privacy disclosures | |
| Change password | 3.32 | 1.71 | The extent to which social media passwords are regularly changed can help reduce privacy disclosures | |
| Active Disclosure | Input real information | 5.74 | 1.19 | The extent to which use real information increase privacy disclosures |
| Share your personal life | 5.47 | 1.18 | The extent to which share personal life increase privacy disclosures | |
| Real-time social interaction | 4.72 | 1.55 | The extent to which real-time social interaction has privacy disclosures risk | |
| Express personal feelings and value | 4.51 | 1.56 | The extent to which express personal feelings and value increase privacy disclosures | |
| Passive Participation | Be involved in news/ topic/ recommend | 5.1 | 1.69 | The degree of users that being involved in news/ topic/ recommend |
| Traces of associated third party websites | 5.14 | 1.44 | Due to traces of associated third party websites, users received recommended information from social media |
| Four Types of User Behaviour | Mean | Description |
|---|---|---|
| Lack of Privacy Concern | 4.82 | The extent to which privacy concern can help reduce privacy disclosures |
| Lack of Privacy Protection | 3.62 | The extent to which privacy protection can help reduce privacy disclosures |
| Active Disclosure | 5.11 | The extent to which use active disclosure increase privacy disclosures |
| Passive Participation | 5.12 | The degree of users that involved in passive participation and that increase privacy disclosures |
| Score | Means | Score | Means |
|---|---|---|---|
| 1 | The same | / | / |
| 3 | A bit more important | Reciprocal 1/3 | A bit less important |
| 5 | More important | Reciprocal 1/5 | Less important |
| 7 | Extremely important | Reciprocal 1/7 | Extremely unimportant |
| 2, 4, 6, 8 | Median on both sides | Reciprocal ½, ¼ | Median on both side |
| Grade | 0–10 | 10–20 | 20–30 | 30–40 | 40–50 | 50–60 | 60–70 | 70–80 | 80–90 | 90–100 |
| Interval | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Tse, W.K.; Kwok, P.Y.; Chiu, Y.H. Impact of Social Media Behavior on Privacy Information Security Based on Analytic Hierarchy Process. Information 2022, 13, 280. https://doi.org/10.3390/info13060280
Liu Y, Tse WK, Kwok PY, Chiu YH. Impact of Social Media Behavior on Privacy Information Security Based on Analytic Hierarchy Process. Information. 2022; 13(6):280. https://doi.org/10.3390/info13060280
Chicago/Turabian StyleLiu, Yuxuan, Woon Kwan Tse, Pui Yu Kwok, and Yu Hin Chiu. 2022. "Impact of Social Media Behavior on Privacy Information Security Based on Analytic Hierarchy Process" Information 13, no. 6: 280. https://doi.org/10.3390/info13060280
APA StyleLiu, Y., Tse, W. K., Kwok, P. Y., & Chiu, Y. H. (2022). Impact of Social Media Behavior on Privacy Information Security Based on Analytic Hierarchy Process. Information, 13(6), 280. https://doi.org/10.3390/info13060280






