Abstract
Adoption, use, and diffusion of Information Technology (IT) applications, together with their widespread success, are among the most popular topics in Information Systems (IS) research. However, the impact of the acquired understanding of those phenomena on IS practice is not discernible. In fact, IT adoption, use, and diffusion are subjects scarcely mentioned in what concerns the practices of IT/IS professionals. This article addresses the question of IT/IS practitioners’ awareness of models and theories regarding the adoption, use, and diffusion of IT applications and their success. It describes two surveys of IT/IS project managers that look into their knowledge on a selected set of models/theories widely addressed in IS research. The results show that these project managers are not aware of IT adoption, use, and diffusion models/theories. The article ends with a discussion that attempts to find justifications for that evidence and stresses out the need for further research focused on translating the extant theoretical models into actionable knowledge.
1. Introduction
Information Technology (IT)/Information Systems (IS) projects are difficult to manage [1] due to the complexity involved [2], and many of them result in failure [3,4]. Putting IT applications in place in companies is a challenging and complex task [5,6] that demands unique competencies from the IT/IS professionals involved [7,8]. Many of those competencies are related to fostering appropriate behavior in the persons that are expected to make use of IT applications.
The issue at stake is the adoption and use of IT applications, which for the past three decades has attracted considerable interest from the IS research community, resulting in the production and validation of several theories that have contributed to explaining the adoption and use of IT applications. Examples of such theories include the Technology Acceptance Model (TAM) [9,10] and the Unified Theory of Acceptance and Use of Technology (UTAUT) [11,12]. In these theories, the use of an IT application is the dependent variable, corresponding to the expected behavior of the persons whose working context has been (or is about to be) affected by the introduction of an IT artifact. The independent variables include a wide range of factors that have been recognized to influence the use behavior [13].Those theories were established upon theories from the social psychology realm that aim at explaining human behavior in general terms, such as the Theory of Reasoned Action (TRA) [14] or the Theory of Planned Behavior (TPB) [15]. On the one hand, the general construct of behavior was replaced by the use of IT application behavior, or use behavior for short. On the other hand, the determining factors have been refined and extended to fit them into different contexts of IT being implemented in companies.
Sometimes, especially when the use of the IT application is not mandatory, an interesting aspect to consider is how the use of the application spreads among the company’s personnel; or how IT applications disseminate among companies. This is a complementary phenomenon that fits within another research stream, Diffusion of Innovation (DOI) [16,17,18,19], that was also taken into account by IS researchers. Adoption of some type of technology is a key concept in DOI. Although it is not specific to the adoption of IT artifacts, it is quite easy to instantiate it to this type of technology.
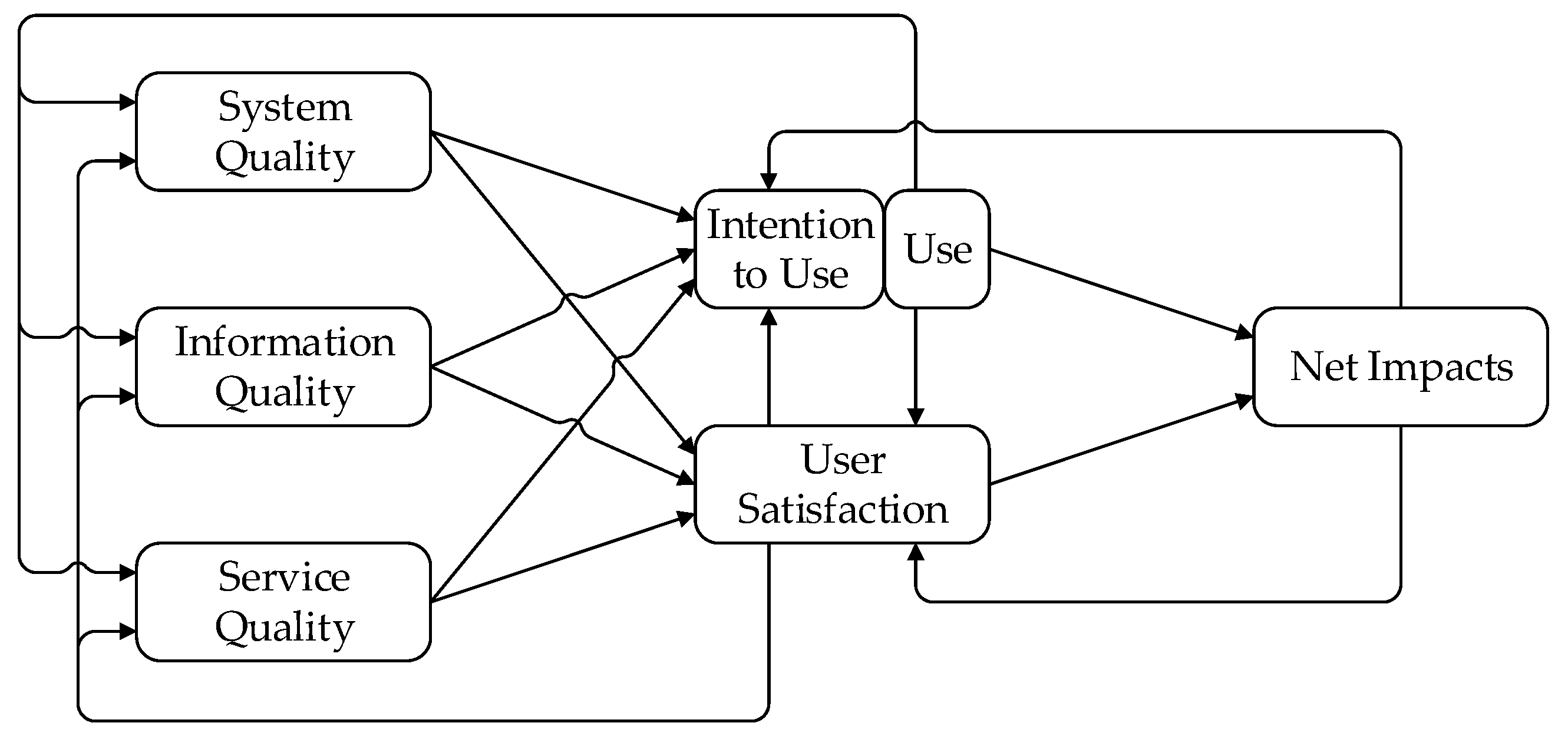
Adoption and use of IT applications are behavioral constructs central to the study of phenomena that involve bringing up IT artifacts into companies. In addition to being considered in the theories mentioned above, adoption and (consequent) use of an IT application are also part of the IS Success model [20,21,22]. This model plays a dual role: on the one hand, it constitutes a classification of success measures; on the other hand, it highlights that success measures are not independent of each other, and some of them are determinant to the achievement of others. The use of IT artifacts is at the center of the IS Success model. Use is influenced by measures related to service, system, and information quality, and, in parallel to user satisfaction, it influences the achievement of business benefits or impacts.
In what concerns success, DeLone and McLean’s model is a milestone in the IS field. The publication of its first version [20] motivated a plethora of studies that scrutinized its components or attempted to enrich it (such as Seddon [23] and Wang [24]). Similar attraction can be found upon adoption and use. Proposed theories motivated IS researchers to further explore the phenomenon, replicate studies, and refine the theories to particular corporate circumstances and specific types of IT applications.
IT success, adoption, and use are undoubtedly issues of significant importance to corporate interventions involving the implantation of IT applications. This importance is well evidenced in research: the last decades have been fertile with studies addressing IS success, adoption, and use [13]. Thus, these aspects must be a key concern for those with responsibilities in managing the corresponding projects. At the present moment, we have reached a good level of understanding of the processes involving the adoption, use, and diffusion of IT applications and also, of their success. Considering the relevance of this understanding for practice in the IS field, it is expectable that IT/IS professionals are somehow aware of existing models and theories. First of all, it is expectable that theories on the adoption, use, and diffusion of IT applications and their success are well known and considered by practitioners in their projects, namely projects involving the implantation of IT applications in companies. Secondly, it is expectable that those theories have somehow been translated into methods and other work procedures to guide practitioners’ activities related to putting IT applications in place.
However, little is known on these subjects since research in this area has been focused almost exclusively on theoretical contributions. Aiming to fill the gap in the literature, this article addresses the first of these two aspects. It addresses the issue of IT/IS practitioners’ familiarity with models and theories on the adoption, use, and diffusion of IT applications and their success. It is expected that answers to this issue will provide evidence and support for further research on improving IS practice by translating the extant theoretical models into actionable knowledge.
The article starts with a brief background on these models and theories. Then it describes two surveys inquiring IT/IS project managers about what theories related to the adoption, use, diffusion, and success of IT applications they know and take into consideration in the context of projects carried out in the companies they are affiliated to. The article concludes by discussing the results and possible justifications for the identified state of affairs.
2. Background
Since IT plays a central role in today’s businesses, successfully bringing in new IT applications into companies is a crucial ability for the development of business capabilities [25,26,27]. For the past decades, the IS research community has been paying great attention to the success of IT applications and what influences such success [28,29,30]. Evidence of the considerable research effort on these topics is the number of research articles published in major outlets of the IS field.
In this section are described some of the most popular models and theories related to the adoption, use, and diffusion of IT applications and success models [13] that were considered in the two surveys carried out in the context of this research. It should be noted that the models/theories presented here do not exhaust the research results produced from the fertile area of IT adoption, use, diffusion, and their success, and other models and theories could have been considered (for more information, see, for instance, [13,31].)
2.1. Delone and Mclean IS Success Model
The DeLone and McLean’s IS Success model (Figure 1) was first proposed in 1992 [20] and was later revised [21,22], incorporating research results propounded by a multitude of researchers engaged in verifying, refining, and extending the initial model. The model serves a dual purpose: it provides a classification of success measures, and it shows how the measures influence each other.
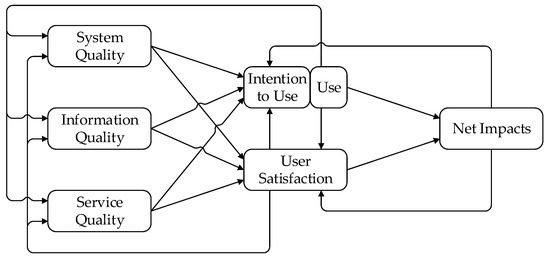
Figure 1.
DeLone and McLean IS Success model (version 3). Adapted from DeLone and McLean [22].
2.2. TAM—Technology Acceptance Model
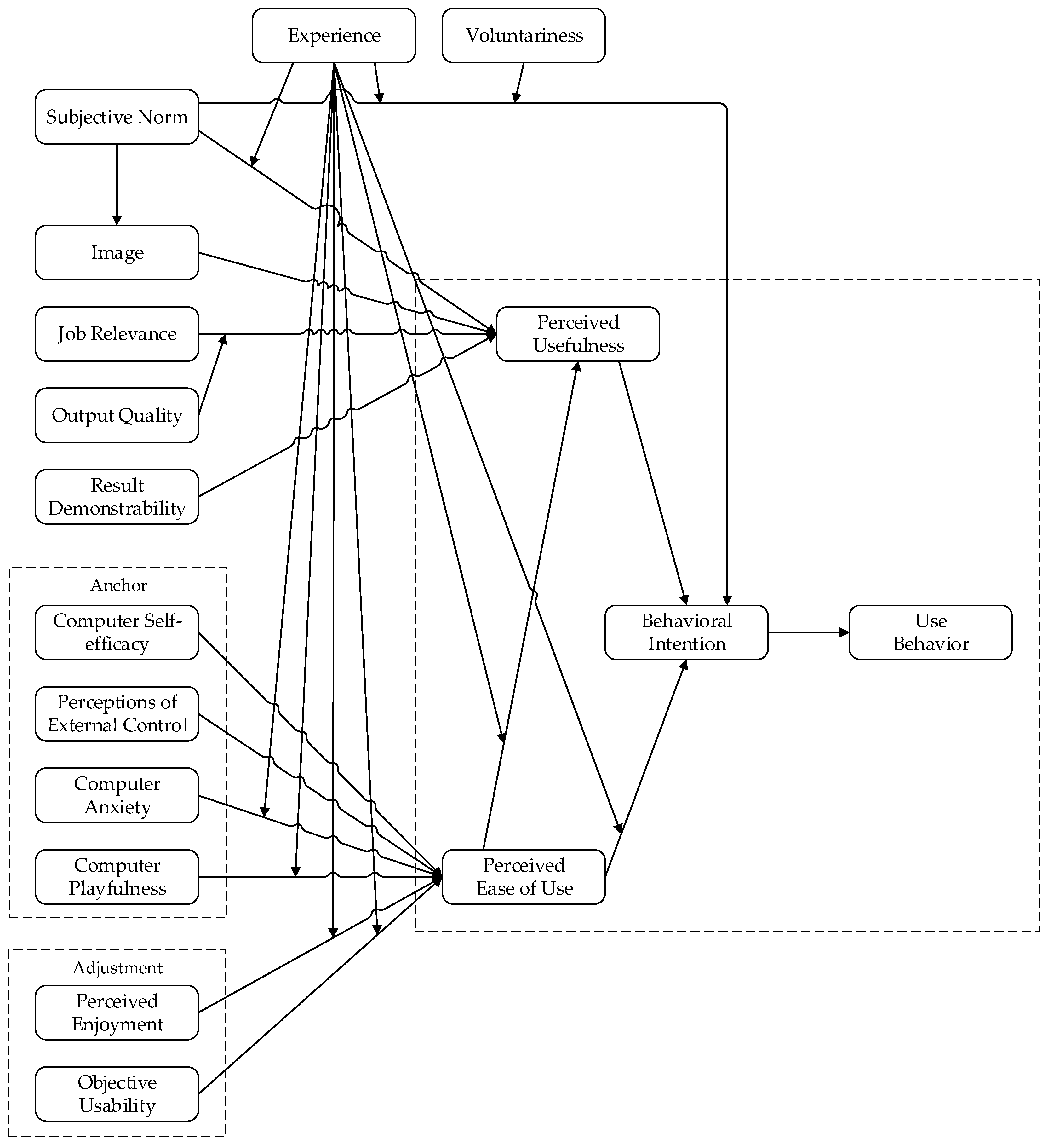
The Technology Acceptance Model was initially presented by Davis [9]. It builds upon the Theory of Reasoned Action (TRA) [14,32] and aims at explaining the initial use of IT applications [10]. TAM gained visibility within the IS research community in the late 1980s, after the publication of research work involving it [10]. The model evolved, and its current version is TAM 3 (Figure 2). It contemplates a comprehensive nomological network of the determinants of IT adoption and use by individuals [33].
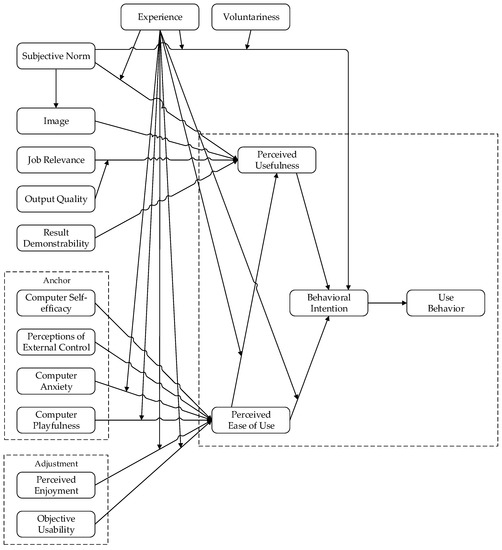
Figure 2.
Technology Acceptance Model (version 3). Adapted from Venkatesh and Bala [33].
2.3. UTAUT—Unified Theory of Acceptance and Use of Technology
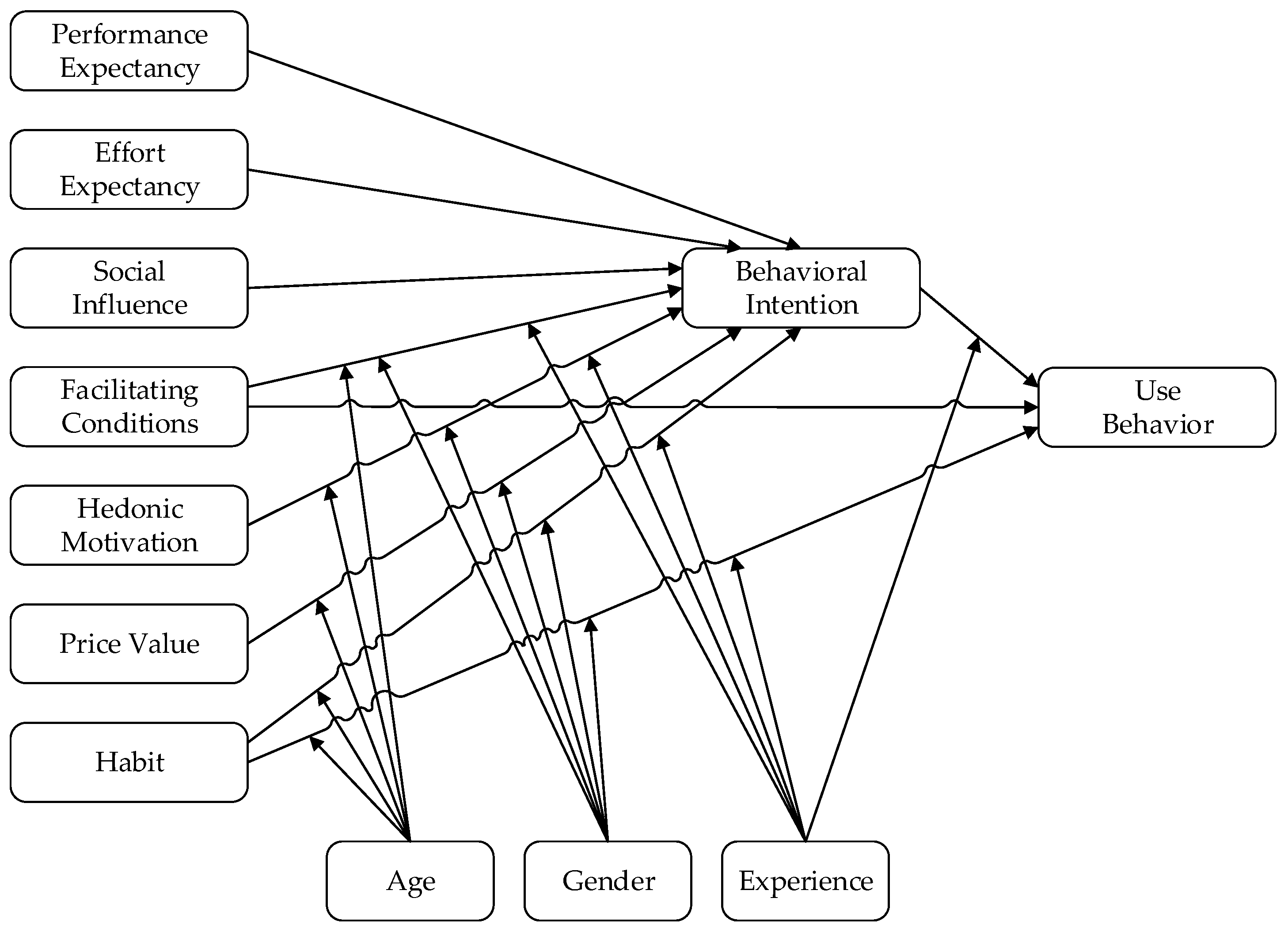
The Unified Theory of Acceptance and Use of Technology was formulated based on a combination of eight models previously considered in, or resulting from, research on IT acceptance [11], including: TRA [14,32]; TAM [9]; Motivational Model (MM) [34,35]; Theory of Planned Behavior (TPB) [15,36]; a model combining TAM and the Theory of Planned Behavior [37]; Model of PC Utilization (MPCU) [38]; Innovation Diffusion Theory (IDT) [39]; and Social Cognitive Theory (SCT) [40,41]. The current version is UTAUT 2 (Figure 3).
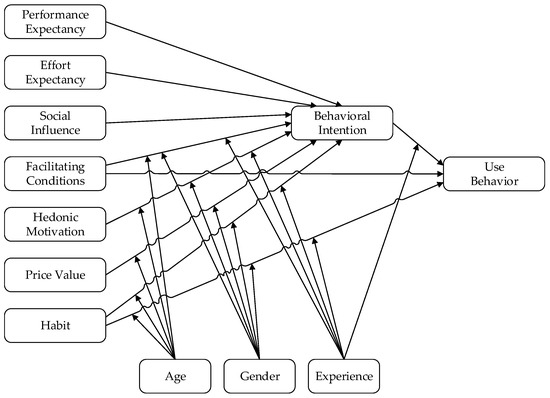
Figure 3.
Unified Theory of Acceptance and Use of Technology (version 2). Adapted from Venkatesh, et al. [12].
2.4. DOI—Diffusion of Innovation Theory
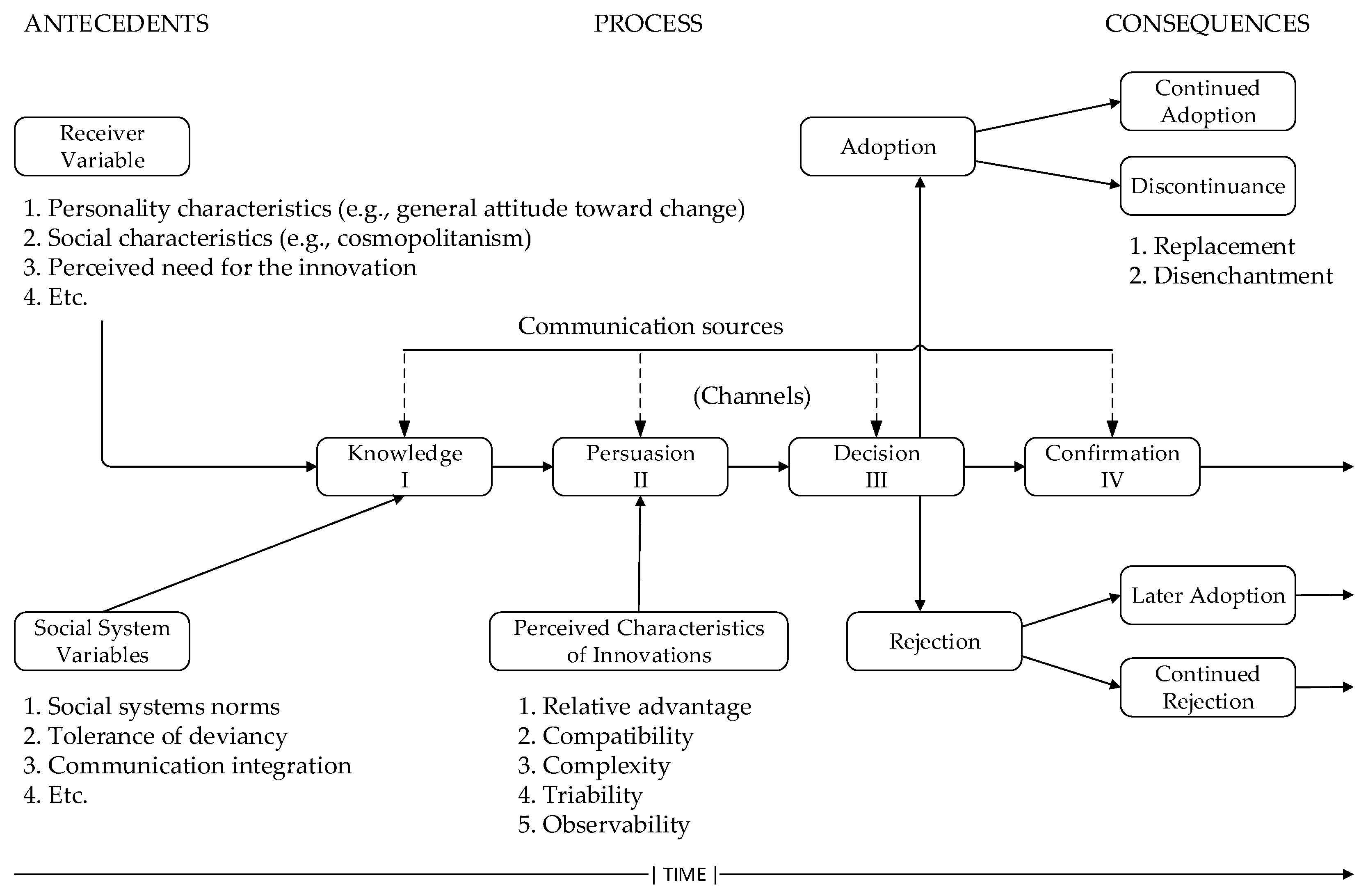
The Diffusion of Innovation Theory (Figure 4) was established in sociology and popularized by Rogers [16,17,18,19], who synthesized a large number of studies in the field of diffusion originating from several different areas, such as anthropology, education, sociology, rural sociology, industrial sociology, and medical sociology. The resulting theory addresses the adoption of innovations among individuals and organizations [16]. Adoption or rejection of new technology is the aspect of the theory that corresponds to relevant behavior—the use of some technology.
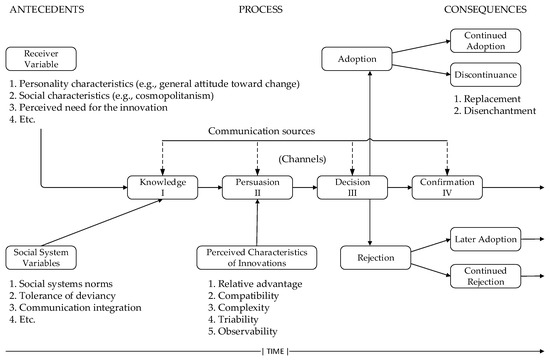
Figure 4.
Model of Stages in the Innovation-Decision Process. Adapted from Rogers [18].
3. Method
The research design is depicted in Figure 5. Considering the extant research on the adoption, use, and diffusion of IT applications and their success, for the past decades, it is expectable that outcomes of this research have impacted the practices of IT/IS professionals. Two primary research questions can therefore be asked related to this issue: How familiar are IT/IS practitioners with these theories/models? What theories/models are being used by IT/IS practitioners in projects involving the implantation of IT applications?

Figure 5.
Research Design.
These questions oriented awareness of the problem and the literature review, enabling to characterize the research gap. To obtain empirical evidence to answer these questions, a first questionnaire-based survey (Exploratory Survey 1) was carried out. To strengthen the results of the first survey, it was decided to conduct a second survey (Exploratory Survey 2) on a different sample, followed by the analysis and discussion, which consisted in reflecting on the concerns that arose from the obtained results. From this reflection, important research avenues were then identified. Both the surveys and the respective research instruments and samples are described next.
3.1. Survey Instrument (Questionnaire)
The survey instrument (a questionnaire) included several support questions regarding the participants’ demographics and their companies, and one single question related to the purpose of this study. This question was differently formulated in the two surveys in order to achieve a greater range of possible answers. In one survey, the question queried the knowledge/awareness of the participants regarding the models/theories, as follows: “Please indicate which of the following models you have heard about before (please indicate all that apply): Delone and Mclean IS Success model; TAM; UTAUT; DOI; Other.” In the other survey, the question queried the awareness/consideration/use of the models/theories in projects: “Please indicate which of the following models you are aware of or are considered/used in your projects (please indicate all that apply): Delone and Mclean IS Success model; TAM; UTAUT; DOI; Other.” We decided to limit the list of models/theories to those mentioned in the question. However, participants were given the opportunity to indicate other theories/models that were considered/used in their professional practice under option “Other” in the questionnaire. The context validity of the questionnaires was examined prior to conducting the surveys. Two IS and project management professors and two IT project managers were requested to pilot-testing the questionnaires. Their feedback led to a few minor refinements.
3.2. Characteristics of the Respondents
Both surveys were carried out among IT/IS project managers with experience in projects involving the implantation of IT in companies, since they are typically in charge of IT/IS projects. The first survey was carried out following the ‘snowballing’ technique for sampling. In this type of sampling, a set of initially identified respondents are invited to suggest other participants [42,43]. We started with a set of 10 IT/IS project managers from several companies whose contacts we had. The IT/IS project managers were individually invited by e-mail to complete an online questionnaire. Additionally, they were asked to spread the questionnaire to their contacts. A total of 74 valid responses were then obtained. In the second survey, an e-mail message with an invitation to participate in the survey and a link to an online questionnaire was sent to project managers from 500 IT companies. A similar message was sent via LinkedIn to select IT/IS project managers who were members of IT/IS Project Management groups. A total of 193 valid responses were obtained. Table 1 summarizes the participants’ demographics and their companies in the two surveys.

Table 1.
Profiles of respondents and companies.
Most of the respondents are senior IT/IS project managers: a vast majority (>90%) is over 30 years old, and more than 40% has more than 10 years of experience in project management. Respondents came from organizations of diverse sizes and industries. The majority of the respondents (>75%) work in companies with an international presence. Respondents also reported the type of projects they participated in, which mainly include package (e.g., ERP systems) implantation, systems’ enhancement, consultancy, and business analysis assignments, customized software development, systems migration, and infrastructure implementation.
4. Results and Discussion
Figure 6 depicts the obtained results. It shows that IT/IS practitioners are not aware of the models/theories. In fact, it shows that practitioners are practically ignoring such theoretical framework. The graphic shown in Figure 6 can be considered of little help since it is almost void. However, we decided to include it to emphasize the dramatic reality it does evidence.

Figure 6.
Awareness of IT adoption models/theories in projects (results compiled from the two surveys).
To enable respondents to mention other models/theories, the questionnaire included the option “Other” (an open question). In this case, 25 respondents (15%) used this option. Five of them (3%) mentioned “I do not know any,” while 14 (8.4%) made references to Benefits Management, and the remaining mentioned non-related subjects, such as SCRUM. Benefits Management can be described as a model for supporting IT/IS professionals in establishing and achieving the business benefits expected from the implantation of IT applications in companies. It is possible to establish a correspondence between these “benefits” and the “net benefits” of the DeLone and McLean’s success model (version 2) [21]. However, the Benefits Management model (or approach) does not consider behavioral aspects related to the adoption and use of IT applications.
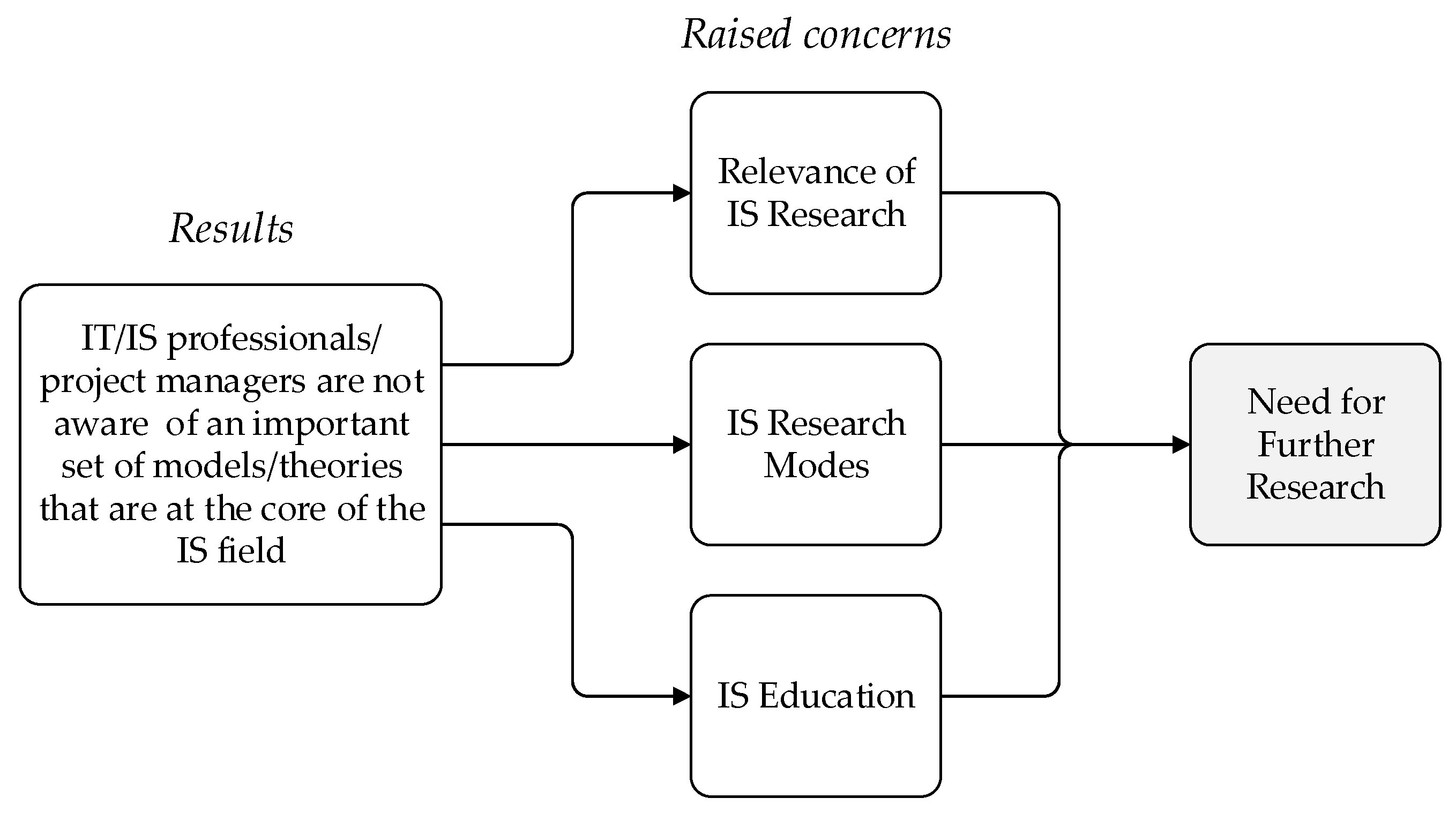
The results of the study show that IT/IS professionals are not cognizant of an important set of models/theories that are at the core of the IS field. Perhaps even more serious, the study suggests that IT/IS project managers are simply not aware of the existence of these models/theories. Even considering the limited sample of project managers surveyed, the surveys’ results are worrying, since IS leadership and proficiency are critical to promoting the success of IS projects [44]. It is hard to admit that senior IT/IS project managers could possibly ignore theories that are key to understanding prime phenomena in their area of interest. These results raise several concerns related to the status of the IS field, as depicted in Figure 7, which demand further research, as discussed next.
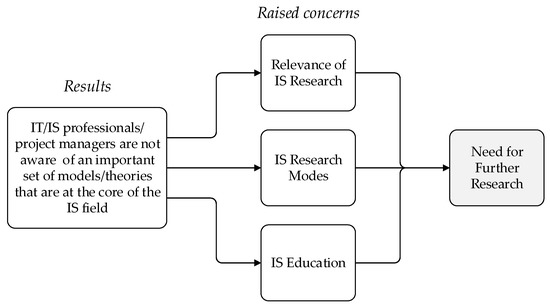
Figure 7.
Concerns arising from IT/IS professionals’/project managers’ lack of awareness of IT adoption models/theories in projects.
A first concern is related to the relevance of IS research: “Is it the case that the current understanding of the adoption, use, and diffusion of IT applications and their success is irrelevant for practical purposes?” We do not think that this question has a positive answer. However, the answer might depend on what is considered to be a central IT/IS professional activity. A traditional perspective views the development of IT applications (often referred to as IS development) as a core IT/IS professional activity. If this is the case, then the crucial professional actions are concerned with identifying the requirements for IT application or its design. Adoption and use are relevant, as they provide the rationale both for accurate identification of requirements (to ensure the usefulness of the IT application) and the design of an adequate interface (to assure the IT application’s ease of use). However, this perspective does not take into consideration behavior issues that are associated with the change that the implantation of an IT application in a business setting will demand.
In an era where many ready-to-use IT enterprise applications are available, the key concerns shift from identification requirements and interface design to managing the inescapable change that such implantation of IT enterprise applications will bring up. Being aware of the factors that determine adoption, use, and diffusion is of utmost importance to IT/IS professionals that have to manage such change. They will launch initiatives, issue policies, and carry out a wide range of deeds that address those factors and aim at achieving the success of the IT application being implanted. This means not only achieving adoption and use of the IT application, but also achieving the expected benefits for the company. Therefore, irrelevance does not seem to account for the results of our surveys.
A second concern is related to IS research modes. Most often, IS research (addressing adoption, use, and diffusion of IT applications) takes the form of basic research. It typically involves empirical research that approaches the relevant phenomena, aiming at establishing causal or association relationships that are capable of explaining and/or predicting IT adoption, use, and diffusion. Other forms of research (addressing IT adoption, use, and diffusion) are not so common and could include: a) Research that aims at translating the understanding achieved through basic research into actionable knowledge. This type of research leads to the establishment of means-to-end relationships or methods (prescriptive models) that can guide IT/IS professionals in their activity; b) Research that studies the practices of IT/IS professionals, aiming at both identifying the actions they launch to promote adoption and use of IT applications and establishing the success of such actions. This type of research leads to the establishment of grounded technological rules [45] whose logic takes the following form: “To achieve Y in situation Z, perform action X.”
The first mode of research can be described as applied research or translational research. It departs from existing theory and aims at applying/translating it into knowledge for action. A common designation for the outcome would be “method” or “technique,” as they correspond to ways of working. This form of research focuses on the production of the method/technique—i.e., an artifact [46]—whose concept has to be proven. Applied research in IS is usually viewed as integrating the design research stream, leading to the production of artifacts which, in this case, are not computer-based artifacts but methods/techniques. The second mode of research corresponds to practice research (sometimes also referred to as clinical research), as it involves studying the actual professional practices of specialists in certain domains. This research mode does not aim at producing new methods or techniques, but it enables establishing the effectiveness of the methods, techniques, and practices deployed by the professionals.
Having made a distinction between complementary modes of doing research, we can ask: “Does IS research related to the adoption, use, and diffusion of IT applications and their success embrace a wide range of research modes, or is it mainly focused on basic research?” Taking into consideration the literature published in IS major journals, it is clear that the majority of research follows the basic research mode, aiming at establishing, revising, refining, and extending the adoption and use of models/theories. Grover and Lyytinen [47] wonder why so much research focuses on basically the same questions over and over again (e.g., variations on TAM). Their answer is that there is a “mid-range script” that is relatively easy to apply through surveys and generates innocuous results that are somewhat obvious and are often difficult to argue with, as they were generated by sound methods. It is, therefore, fair to claim that the adoption, use, and diffusion of IT applications research stream in IS requires a widened perspective to allow moving from the understanding of the phenomena to ways of intervening in processes involving adoption, use, and diffusion of IT.
A third concern relates to IS education: “Do IS programs, at the bachelor and/or master’s level, address the models/theories of adoption, use, and diffusion of IT applications and their success?” A preliminary answer to this question can be found in the existing IS curricula recommendations.
Current curricula recommendations in IS (IS 2020 [48] and MSIS 2016 [49]) follow a less prescriptive approach than their previous versions (IS 2010 [50] and MSIS 2006 [51]). Instead of suggesting specific courses, core or electives that should be included in the programs, they present the required competencies for a graduate. Competencies combine knowledge, skills, and dispositions/attitudes related to a task. Looking for references to models/theories of adoption, use, and diffusion of IT applications and their success involves analyzing such competencies, looking into the tasks they are associated to, and the knowledge involved.
IS 2020 [48] encompasses six competency realms: Foundations of Information Systems; Data/Information Management; Technology and Security; (Applications) Development; Organizational Domain; and Integration. The competency realms are then subdivided into required competency areas. Several competency areas are candidates to encompass the application of the models/theories of adoption, use, and diffusion of IT applications and their success:
- Competency 8 of the Foundations realm—“Demonstrate an ability to solve basic computational and design problems using IS development with appropriate methodologies, software tools and innovative methods for improving processes and organizational change” (emphasis added)—suggests the relevance of the models/theories that we are interested in. However, they are not mentioned in the knowledge involved in the competency [48], p. 101.
- The Technology and Security competency realm does not seem to be the place to find references to the models/theories. However, in one of the competencies included in the Emerging Technologies competency area—Competency 4: Investigate technologies through a theoretical lens—it is possible to find the following pair knowledge element/Skill level: Appropriate theories related to technology implementation and use/5—Evaluate [48], p. 120. In addition, Competency 6—“Identify the impact of technologies on society and business” includes the pair: Business impact of technology/5—Evaluate [48], p. 121.
- The description of the (Applications) Development realm mentions that an “IS perspective on application development” includes “sociological and psychological components that constitute user and organizational acceptance and satisfaction” [48], p. 55. However, the two required competency areas of this realm—Systems Analysis and Design and Application Development and Programming—emphasize aspects related to the construction of software. While recognizing the increased deployment of digital technologies, concerns regarding the implantation of these technologies are absent in these competency realms.
- The Digital Innovation Competency Area within the Organizational Domain Competency Realm includes competency under the following description: “Competency 7: Practically demonstrate the investigation and application of new innovation.” It includes the pair: Evaluation criteria for a successful application/5—Evaluate [48], p. 166.
- The Business Process Management Competency Area within the Organizational Domain Competency Realm includes competency under the following description: “Competency 6: Use process improvement methods and implement TO-BE processes by eliminating the bottlenecks, enhancing, and innovating the AS-IS process.” It includes the pair: Change management and implementation/3—Apply [48], p. 169.
Although it is possible to find reference to “theories related to technology implementation and use,” this is carried out in the context of Emerging Technologies. Other competencies reveal that IS 2020 [48] encompasses concerns with the development of IT applications (software development) and several other aspects related to the use of technology in organizations (improving processes; organizational change; the impact of technologies on society and business; digital innovation). However, the implantation (deployment, organizational implementation) of IT applications is not made explicit.
It is interesting to note that the IS 2010 model [50] included a course—Systems Analysis and Design—that covered the “organizational implementation of a new information system” [50], p. 52, although nothing in the learning outcomes or the course discussion suggested coverage of topics related to IT adoption, use, and diffusion.
At the master’s level, the MSIS 2016 [49] model provides a list of 88 competency categories distributed by nine competency areas. Sample competencies are indicated for each competency category. “Promote the adoption and use of the new application” is an example of competency within competency category 88—Deploying a new system to organizational use—that fits in the competency area of Systems Development and Deployment (SDAD) [49], p. 91. There is an obvious association between this competency—Promote the adoption and use of the new application—and IT adoption, use, and diffusion area. Although no guidelines are provided, it is reasonable to assume that this competency builds upon IT adoption, use, and that diffusion models/theories use them as risk factors for a successful deployment of IT applications, and address ways of dealing with those risks.
On the other hand, these themes can (and should) also be explored in information systems project management teaching. Project management curricula should prepare students for specific competencies and the professional work environment they will encounter upon graduation [52]. For instance, IT adoption subjects are fundamental in IS projects when defining and implementing transition plans and business implementation plans [53]. Let us wait and see whether a new generation of IT/IS professionals/project managers are aware of the applicability of IT adoption, use, and diffusion models/theories.
5. Conclusions
The results of our study suggest that IT/IS professionals/project managers are not aware of an important set of models/theories that are at the core of the IS field, including the IS Success model [20,21,22], the Technology Acceptance Model [9,10], the Unified Theory of Acceptance and Use of Technology [11,12], and the Diffusion of Innovation Theory [16,17,18,19]. Even considering the limited sample of project managers surveyed, these results are worrying. Our contribution is twofold. First, our study raises attention to a reality that urgently calls for applied research or translational research, so that the valuable results obtained at a theoretical level can be used to improve IS practice. Second, it stresses the importance of addressing the models/theories of adoption, use, and diffusion of IT applications in IT/IS project management programs.
We recognize that the study presented in this article has limited scope. However, education, training, and experience of most IT/IS project managers surveyed have put them in contact with well-established project management practices. Nonetheless, these practices fail to explicitly address IT adoption, use, and diffusion issues. Maybe a theory is needed to guide the translation, adoption, and use in practice of the learnings from adoption and use theories.
Author Contributions
Conceptualization, J.V. and J.Á.C.; Methodology, J.V. and J.Á.C.; Validation, J.V. and J.Á.C.; Formal analysis, J.V. and J.Á.C.; Investigation, J.V., J.Á.C., T.S., and J.P.; Data curation, J.V., T.S., and J.P.; Writing—original draft preparation, J.V. and J.Á.C.; Writing—review and editing, J.V. and J.Á.C.; Supervision, J.V.; Funding acquisition, J.V. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to thank MDPI Information Editorial Office for all the support.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Tam, C.; Moura, E.J.D.C.; Oliveira, T.; Varajão, J. The factors influencing the success of on-going agile software development projects. Int. J. Proj. Manag. 2020, 38, 165–176. [Google Scholar] [CrossRef]
- Hafseld, K.H.J.; Hussein, B.; Rauzy, A.B. An attempt to understand complexity in a government digital transformation project. Int. J. Inf. Syst. Proj. Manag. 2021, 9, 70–91. [Google Scholar]
- Owens, D.; Merhout, J.W.; Khazanchi, D. Project management assurance in agile projects: Research in progress. In Proceedings of the Thirteenth Midwest Association for Information Systems Conference, Saint Louis, MO, USA, 17–18 May 2018. [Google Scholar]
- Iriarte, C.; Bayona, S. It projects success factors: A literature review. Int. J. Inf. Syst. Proj. Manag. Rev. 2020, 8, 49–78. [Google Scholar]
- Morcov, S.; Pintelon, L.; Kusters, R. Definitions, characteristics and measures of IT project complexity—A systematic literature review. Int. J. Inf. Syst. Proj. Manag. 2020, 8, 5–21. [Google Scholar]
- Janssens, G.L.S.G.; Kusters, R.J.; Martin, H.H. Expecting the unexpected during ERP implementations: A complexity view. Int. J. Inf. Syst. Proj. Manag. 2020, 8, 68–82. [Google Scholar]
- Varajão, J.; Silva, H.; Pejic-Bach, M. Key competences of information systems project managers. Int. J. Inf. Technol. Proj. Manag. 2019, 10, 73–90. [Google Scholar] [CrossRef] [Green Version]
- Sampaio, S.; Wu, Q.; Cormican, K.; Varajão, J. Reach for the sky: Analysis of behavioral competencies linked to project success. Int. J. Manag. Proj. Bus. 2021, 15, 192–215. [Google Scholar] [CrossRef]
- Davis, F.D. A Technology Acceptance Model for Empirically Testing New End-User Information Systems: Theory and Results. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 1986. [Google Scholar]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. User acceptance of computer technology: A comparison of two theoretical models. Manag. Sci. 1989, 35, 982–1003. [Google Scholar] [CrossRef] [Green Version]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User acceptance of information technology: Toward a unified view. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef] [Green Version]
- Venkatesh, V.; Thong, J.Y.L.; Xu, X. Consumer acceptance and use of information technology: Extending the unified theory of acceptance and use of technology. MIS Q. 2012, 36, 157–178. [Google Scholar] [CrossRef] [Green Version]
- Varajão, J.; Silva, T.; Trigo, A. ISRI—Information systems research constructs and indicators: A web tool for information systems researchers. J. Inf. Sci. Theory Pract. 2021, 9, 54–67. [Google Scholar]
- Fishbein, M.; Ajzen, I. Belief, Attitude, Intention, and Behavior: An Introduction to Theory and Research; Addison-Wesley Pub. Co: Boston, MA, USA, 1975. [Google Scholar]
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Processes 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Rogers, E.M. Diffusion of Innovations, 1st ed.; Free Press of Glencoe: New York, NY, USA, 1962. [Google Scholar]
- Rogers, E.M. Diffusion of Innovations, 3rd ed.; Free Press: New York, NY, USA, 1983. [Google Scholar]
- Rogers, E.M. Diffusion of Innovations, 4th ed.; Free Press: New York, NY, USA, 1995. [Google Scholar]
- Rogers, E.M. Diffusion of Innovations, 5th ed.; Free Press: New York, NY, USA, 2003. [Google Scholar]
- DeLone, W.H.; McLean, E.R. Information systems success: The quest for the dependent variable. Inf. Syst. Res. 1992, 3, 60–95. [Google Scholar] [CrossRef] [Green Version]
- DeLone, W.H.; McLean, E.R. The DeLone and McLean model of information systems success: A ten-year update. J. Manag. Inf. Syst. 2003, 19, 9–30. [Google Scholar]
- DeLone, W.H.; McLean, E.R. Information systems success measurement. Found. Trends® Inf. Syst. 2016, 2, 1–116. [Google Scholar] [CrossRef]
- Seddon, P.B. A respecification and extension of the DeLone and McLean model of IS success. Inf. Syst. Res. 1997, 8, 240–253. [Google Scholar] [CrossRef]
- Wang, Y.S. Assessing e-commerce systems success: A respecification and validation of the DeLone and McLean model of IS success. Inf. Syst. J. 2008, 18, 529–557. [Google Scholar] [CrossRef]
- Patnayakuni, R.; Ruppel, C.P. A socio-technical approach to improving the systems development process. Inf. Syst. Front. 2010, 12, 219–234. [Google Scholar] [CrossRef]
- Varajão, J.; Trigo, A. Evaluation of IS project success in InfSysMakers: An exploratory case study. In Proceedings of the 37th International Conference on Information Systems (ICIS 2016), Dublin, Ireland, 11–14 December 2016; pp. 1–10. [Google Scholar]
- Kääriäinen, J.; Kuusisto, O.; Pussinen, P.; Saarela, M.; Saari, L.; Hänninen, K. Applying the positioning phase of the digital transformation model in practice for smes: Toward systematic development of digitalization. Int. J. Inf. Syst. Proj. Manag. 2020, 8, 24–43. [Google Scholar]
- Pereira, J.; Varajão, J.; Takagi, N. Evaluation of information systems project success—Insights from practitioners. Inf. Syst. Manag. 2021, 2021, 1–18. [Google Scholar] [CrossRef]
- Bezdrob, M.; Brkić, S.; Gram, M. The pivotal factors of it projects’ success—Insights for the case of organizations from the federation of Bosnia and Herzegovina. Int. J. Inf. Syst. Proj. Manag. 2020, 8, 23–41. [Google Scholar]
- Hefley, W.E.; Bottion, M. Skills of junior project management professionals and project success achieved by them. Int. J. Inf. Syst. Proj. Manag. 2021, 9, 56–75. [Google Scholar]
- Varajão, J.; Silva, T. ISRI—Information Systems Research Indicators 2017–2021. Available online: https://isri.sciencesphere.org/ (accessed on 15 December 2021).
- Ajzen, I.; Fishbein, M. Understanding Attitudes and Predicting Social Behavior; Prentice-Hall: Englewood Cliffs, NJ, USA, 1980. [Google Scholar]
- Venkatesh, V.; Bala, H. Technology acceptance model 3 and a research agenda on interventions. Decis. Sci. 2008, 39, 273–315. [Google Scholar] [CrossRef] [Green Version]
- Davis, F.D.; Bagozzi, R.P.; Warshaw, P.R. Extrinsic and intrinsic motivation to use computers in the workplace. J. Appl. Soc. Psychol. 1992, 22, 1111–1132. [Google Scholar] [CrossRef]
- Vallerand, R.J. Toward a hierarchical model of intrinsic and extrinsic motivation. Adv. Exp. Soc. Psychol. 1997, 29, 71–360. [Google Scholar]
- Ajzen, I. From intentions to actions: A theory of planned behavior. In Action Control; Springer: Berlin/Heidelberg, Germany, 1985; pp. 11–39. [Google Scholar]
- Taylor, S.; Todd, P. Assessing IT usage: The role of prior experience. MIS Q. 1995, 19, 561–568. [Google Scholar] [CrossRef] [Green Version]
- Thompson, R.L.; Higgins, C.A.; Howell, J.M. Personal computing: Toward a conceptual model of utilization. MIS Q. 1991, 15, 125–142. [Google Scholar] [CrossRef]
- Moore, G.C.; Benbasat, I. Development of an instrument to measure the perceptions of adopting an information technology innovation. Inf. Syst. Res. 1991, 2, 192–222. [Google Scholar] [CrossRef] [Green Version]
- Bandura, A. Social Foundations of Thought and Action: A Social Cognitive Theory; Prentice-Hall, Inc.: Hoboken, NJ, USA, 1986. [Google Scholar]
- Compeau, D.; Higgins, C. Computer self-efficacy: Development of a measure and initial test. MIS Q. 1995, 19, 189–210. [Google Scholar] [CrossRef] [Green Version]
- Harrell, M.C.; Bradley, M.A. Data Collection Methods. Semi-Structured Interviews And Focus Groups; RAND National Defense Research Institute: Santa Monica, CA, USA, 2009. [Google Scholar]
- Rea, L.M.; Parker, R.A. Designing and Conducting Survey Research: A Comprehensive Guide; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar]
- Tripathi, A.; Khazanchi, D. IS/T leadership: A comprehensive review of published research. In Proceedings of the 24th Americas Conference on Information Systems 2018: Digital Disruption, AMCIS 2018, New Orleans, LA, USA, 16–18 August 2018. [Google Scholar]
- Van Aken, J.E. Management research based on the paradigm of the design sciences: The quest for field-tested and grounded technological rules. J. Manag. Stud. 2004, 41, 219–246. [Google Scholar] [CrossRef]
- March, S.T.; Smith, G.F. Design and natural science research on information technology. Decis. Support Syst. 1995, 15, 251–266. [Google Scholar] [CrossRef]
- Grover, V.; Lyytinen, K. New state of play in information systems research: The push to the edges. MIS Q. Manag. Inf. Syst. 2015, 39, 271–296. [Google Scholar] [CrossRef]
- Association for Computing Machinery (ACM); Association for Information Systems (AIS). IS2020: A Competency Model for Undergraduate Programs in Information Systems; The Joint ACM/AIS IS2020 Task Force; ACM: New York, NY, USA; AIS: Atlanta, GA, USA, 2021; Available online: https://www.acm.org/binaries/content/assets/education/curricula-recommendations/is2020.pdf (accessed on 18 December 2021).
- Topi, H.; Karsten, H.; Brown, S.A.; Carvalho, J.A.; Donnellan, B.; Shen, J.; Tan, B.C.Y.; Thouin, M.F. MSIS 2016 global competency model for graduate degree programs in information systems. Commun. Assoc. Inf. Syst. 2017, 40, 18. [Google Scholar] [CrossRef]
- Topi, H.; Vlalcich, J.S.; Wright, R.Y.; Kaiser, K.M.; Nunamaker, J.F.J.R.; Sipior, J.C.; de Vreede, G.J. IS 2010: Curriculum guidelines for undergraduate degree programs in information systems. Commun. Assoc. Inf. Syst. 2010, 26, 18. [Google Scholar] [CrossRef] [Green Version]
- Gorgone, J.T.; Gray, P.; Stohr, E.A.; Valacich, J.S.; Wigand, R.T. MSIS 2006: Model Curriculum and Guidelines for Graduate Degree Programs in Information Systems. Commun. Assoc. Inf. Syst. 2006, 17, 1–58. [Google Scholar] [CrossRef]
- Task for on PM Curricula, PM Curriculum and Resources; Project Management Institute: Newtown Square, PA, USA, 2015.
- European Commission. PM² Project Management Methodology (Guide 3.0.1); European Commission: Brussels, Luxembourg, 2021. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).