Automated GDPR Contract Compliance Verification Using Knowledge Graphs
Abstract
1. Introduction
- 1.
- A scalable tool for managing semantic-based contracts within smart city and insurance use cases;
- 2.
- Our tool implements a KG-based approach for GDPR-compliant CCV;
- 3.
- An ontology and KG for contracts that can be reused in various cases and domains.
2. Related Work
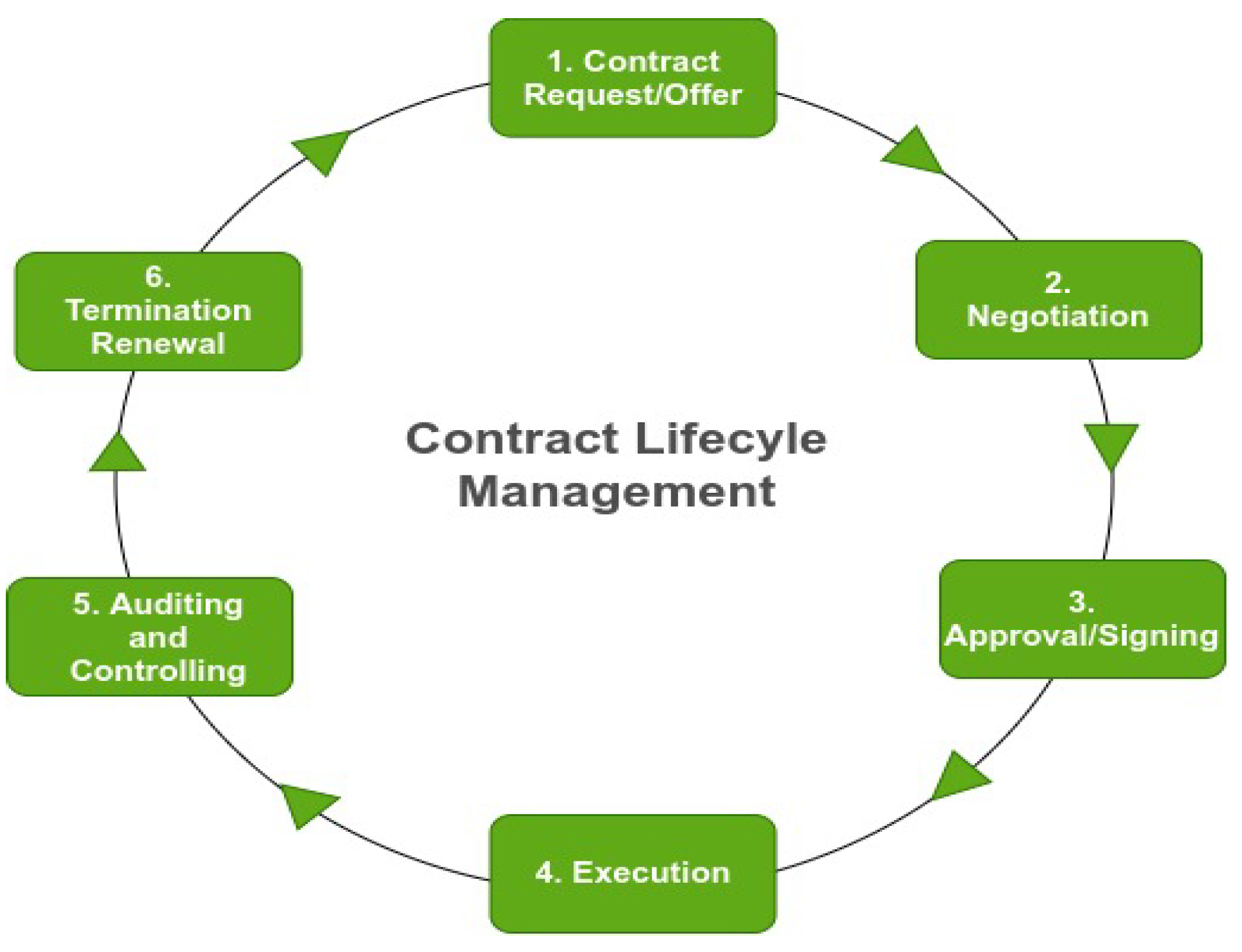
2.1. Contract Management
2.2. Semantic Modelling
2.3. Compliance Verification
3. Approach
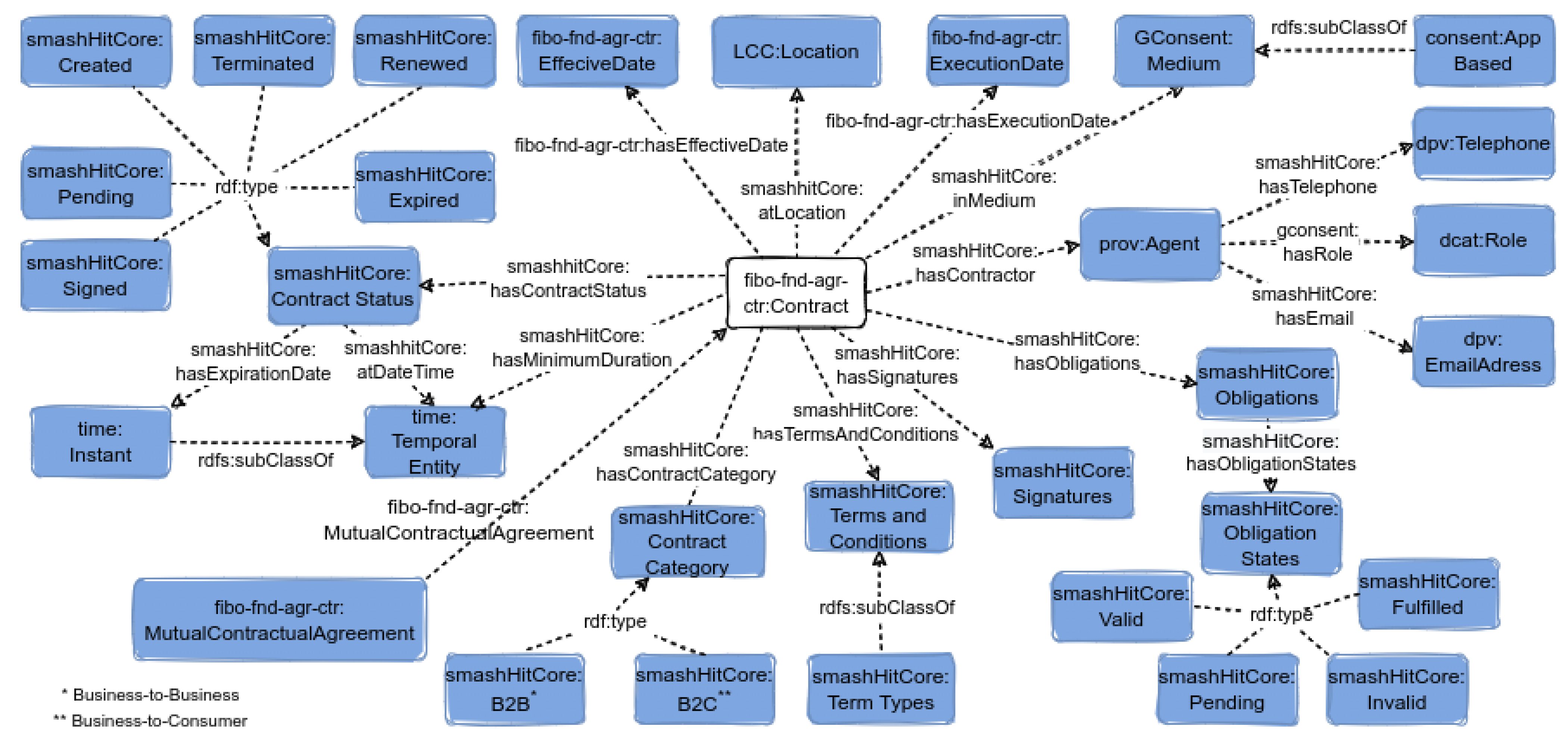
3.1. Semantic-Based Contract Model
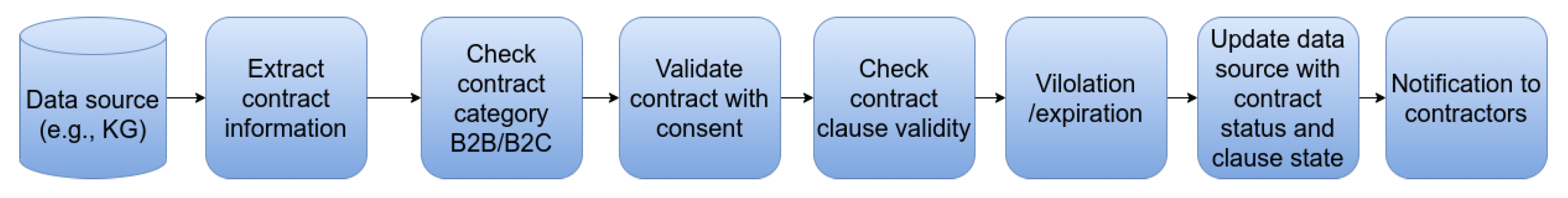
3.2. CCV
3.3. CCV Scenarios
3.3.1. B2C or B2B Contracts
3.3.2. Consent-Based Compliance Verification on B2C Contracts
3.3.3. Consent-Based Compliance Verification on B2B Contracts
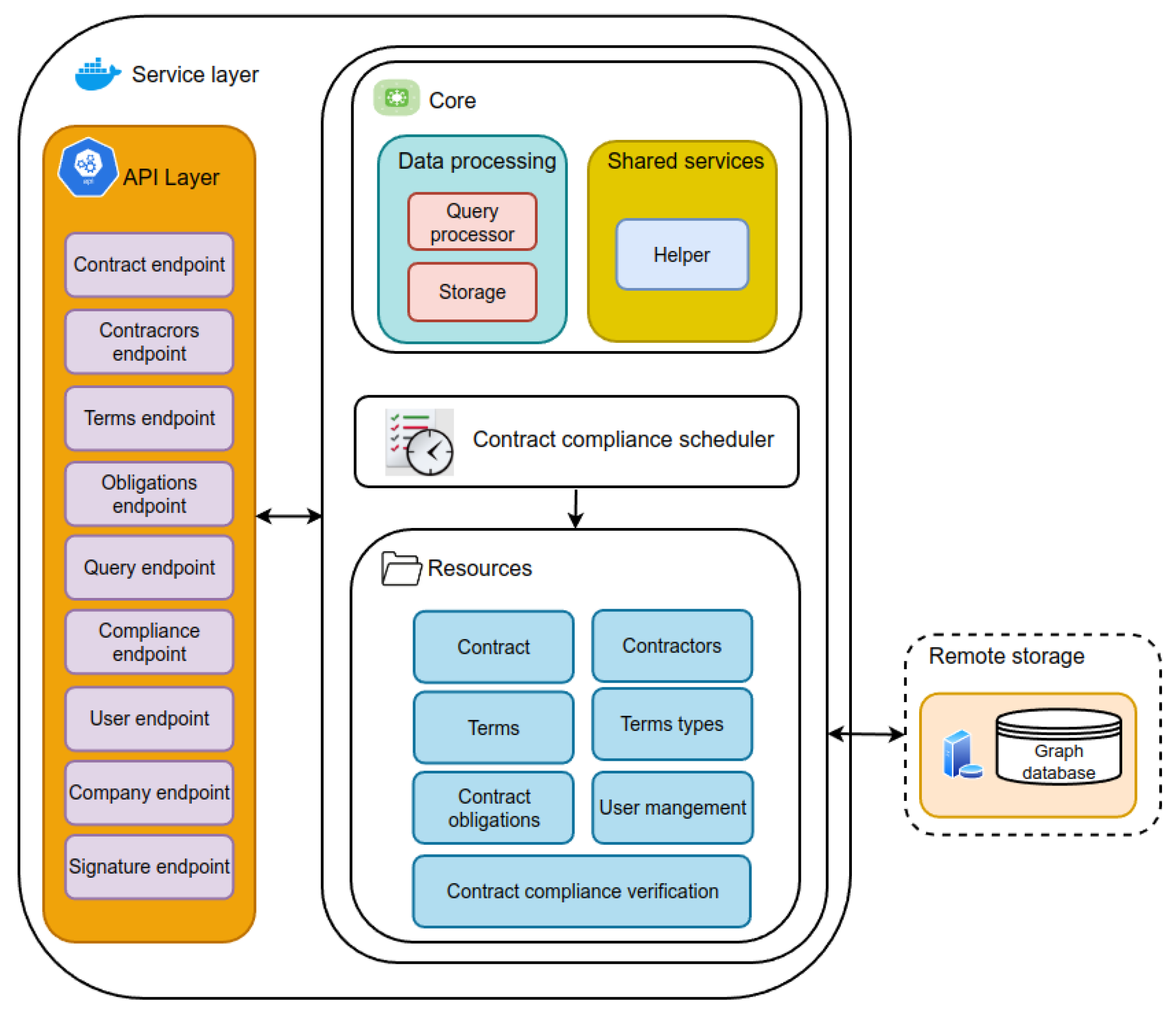
4. Architectural Design and Implementation
4.1. CCV Architectural Design
4.1.1. Core
4.1.2. API Layer
4.1.3. Resources
4.1.4. Remote Storage
4.1.5. Contract Compliance Scheduler
4.1.6. Contract REST API
4.2. Implementation
4.2.1. The Implementation of TOMs
Data Encryption
Protection against External Influences on Systems and Services
Documentation of Data Syntax
Reduction in Non-Required Attributes of Data Subjects
Role Concepts with Graduated Access Rights Based on Identity Management and a Secure Authentication Process
- 1.
- Systematises data protection requirements in the form of protection goals;
- 2.
- Systematically derives generic measures from protection goals, supplemented by a catalogue of reference measures;
- 3.
- Systematises the identification of risks in order to determine protection requirements of the data subjects resulting from the processing; and
- 4.
- Offers a procedure model for modelling, implementation, and continuous control and testing of processing activities.
4.2.2. System Setup for Evaluation
4.2.3. Automated GDPR CCV Tool Implementation
API Layer
Data Processing
Contract Compliance Scheduler
Resources
Security
5. Evaluation
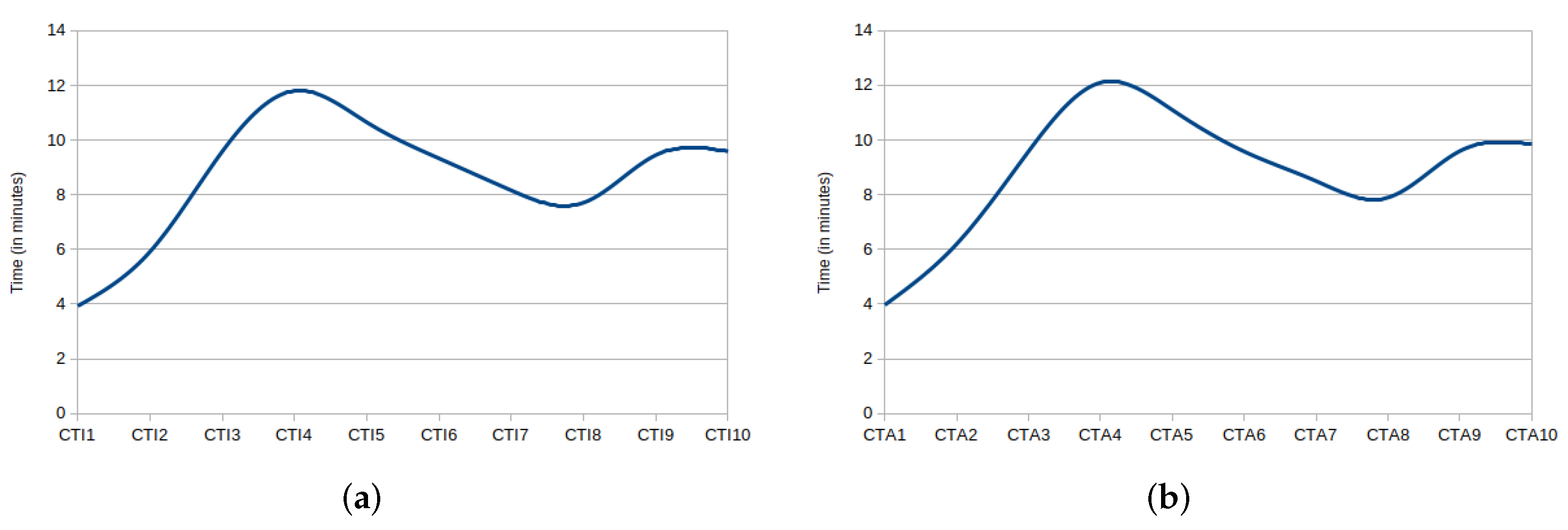
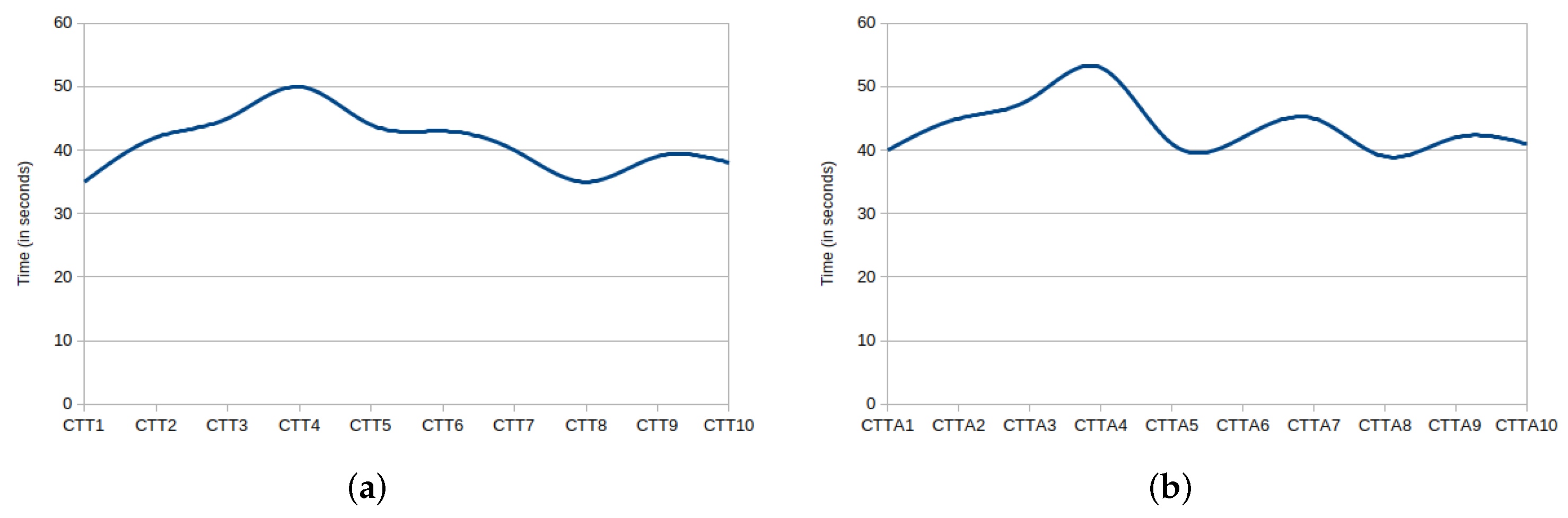
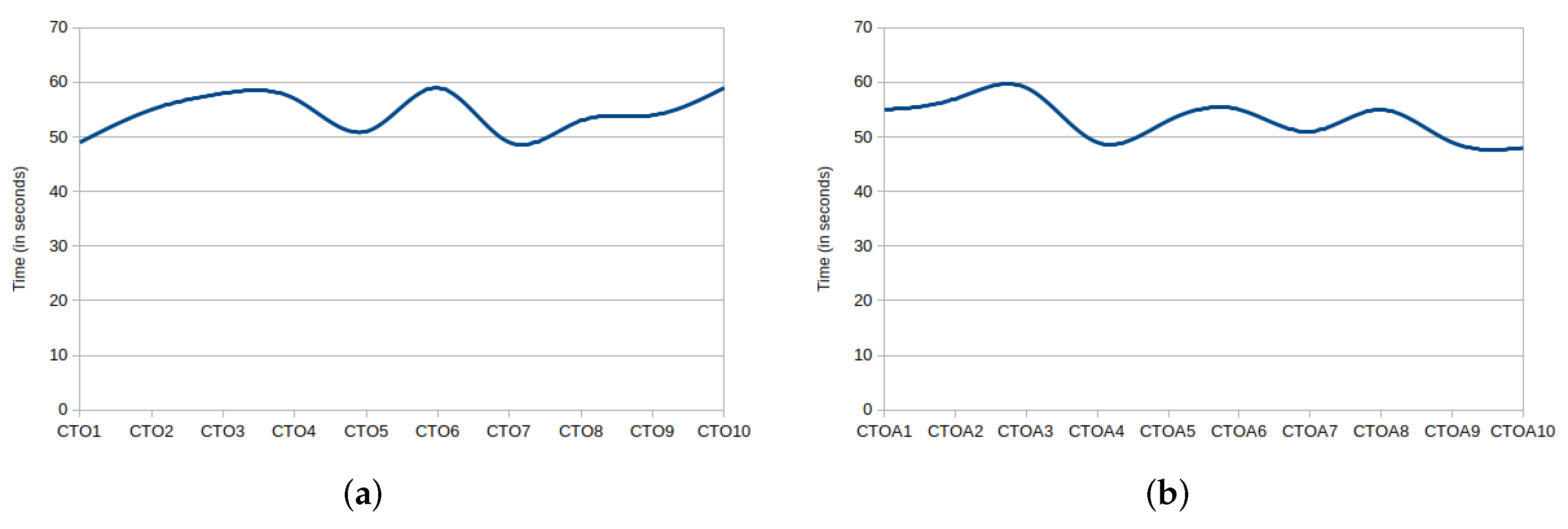
5.1. CCV Performance Evaluation
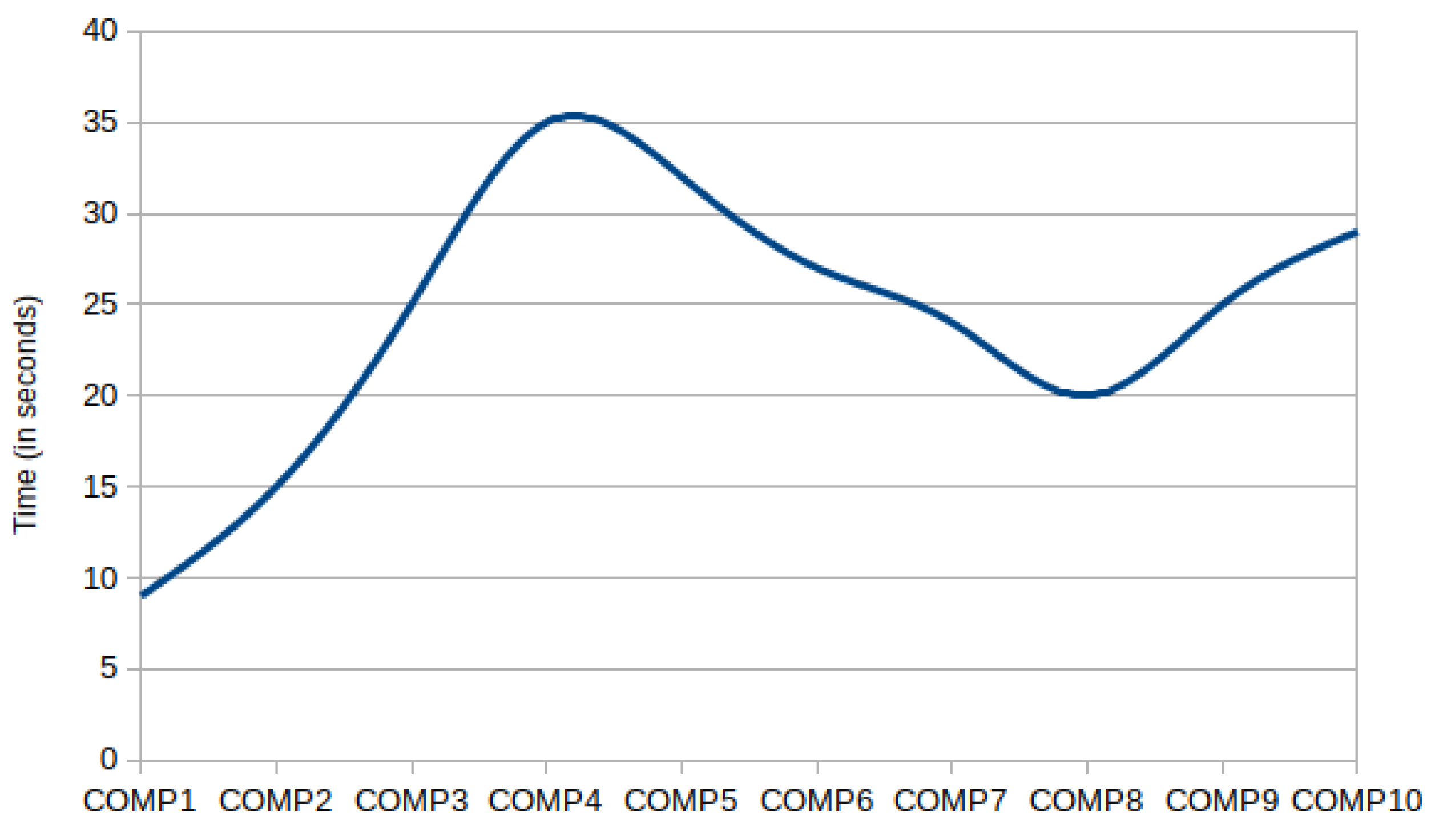
5.2. TOMs Evaluation
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
Semantic Models Prefix
References
- General Data Protection Regulation (GDPR). Available online: https://gdpr.eu/what-is-gdpr/ (accessed on 20 July 2022).
- Li, M.; Samavi, R. DSAP: Data Sharing Agreement Privacy Ontology. SWAT4LS, 2018. Ph.D. Thesis, McMaster University, Hamilton, ON, Canada, 2018. [Google Scholar] [CrossRef]
- European Parliament and Council. Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of Such Data, and REPEALING DIRective 95/46/EC (General Data Protection Regulation). Off. J. Eur. Union 2016, L119. Available online: https://eur-lex.europa.eu/eli/reg/2016/679/oj (accessed on 5 March 2022).
- Habib, H.; Li, M.; Young, E.; Cranor, L. “Okay, whatever”: An evaluation of cookie consent interfaces. In Proceedings of the 2022 CHI Conference on Human Factors in Computing Systems, CHI ’22, New Orleans, LA, USA, 29 April–5 May 2022; Association for Computing Machinery: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- European Data Protection Board. Available online: https://edpb.europa.eu/edpb_en (accessed on 26 July 2022).
- The Contractual Necessity Basis for Processing Personal Data in the Context of Online Services. Available online: https://edpb.europa.eu/sites/default/files/consultation/edpb_draft_guidelines-art_6-1-b-final_public_consultation_version_en.pdf (accessed on 25 July 2022).
- Li, H.; Yu, L.; He, W. The Impact of GDPR on Global Technology Development. J. Glob. Inf. Technol. Manag. 2019, 22, 1–6. [Google Scholar] [CrossRef]
- Kurteva, A.; Chhetri, T.R.; Pandit, H.J.; Fensel, A. Consent through the lens of semantics: State of the art survey and best practices. Semant. Web 2021, 1–27. [Google Scholar] [CrossRef]
- Breach of Contract. Available online: http://jec.unm.edu/education/online-training/contract-law-tutorial/breach-of-contract (accessed on 10 July 2022).
- The smashHit EU H2020 Project. Available online: https://smashhit.eu/ (accessed on 20 July 2022).
- Hunhevicz, J.J.; Motie, M.; Hall, D.M. Digital building twins and blockchain for performance-based (smart) contracts. Autom. Constr. 2022, 133, 103981. [Google Scholar] [CrossRef]
- Liu, L.; Tsai, W.T.; Bhuiyan, M.Z.A.; Peng, H.; Liu, M. Blockchain-enabled fraud discovery through abnormal smart contract detection on Ethereum. Future Gener. Comput. Syst. 2022, 128, 158–166. [Google Scholar] [CrossRef]
- Semantic Agreement. Available online: https://joinup.ec.europa.eu/taxonomy/term/http_e_f_fdata_ceuropa_ceu_fdr8_fSemanticAgreement (accessed on 20 July 2022).
- Pandit, H.J.; O’Sullivan, D.; Lewis, D. Towards knowledge-based systems for GDPR compliance. In Proceedings of the International Semantic Web Conference (ISWC), Monterey, CA, USA, 8–12 October 2018. [Google Scholar] [CrossRef]
- Fensel, D.; Şimşek, U.; Angele, K.; Huaman, E.; Kärle, E.; Panasiuk, O.; Toma, I.; Umbrich, J.; Wahler, A. Knowledge Graphs; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
- Hogan, A.; Blomqvist, E.; Cochez, M.; d’Amato, C.; Melo, G.d.; Gutierrez, C.; Kirrane, S.; Gayo, J.E.L.; Navigli, R.; Neumaier, S.; et al. Knowledge Graphs. Synth. Lect. Data, Semant. Knowl. 2021, 12, 1–257. [Google Scholar] [CrossRef]
- Voss, W.G. Data protection issues for smart contracts. In Smart Contracts: Technological, Business and Legal Perspectives; Corrales, M., Fenwick, M., Wrbka, S., Eds.; Hart Publishing: London, UK; Bloomsbury: London, UK, 2021; Available online: https://www.bloomsburycollections.com/book/smart-contracts-technological-business-and-legal-perspectives/ (accessed on 15 June 2022). [CrossRef]
- Jusic, A. Dealing with tensions between the blockchain and the GDPR. The LegalTech Book: The Legal Technology Handbook for Investors, Entrepreneurs and FinTech Visionaries; FINTECH Circle Ltd.: London, UK, 2020; pp. 83–86. [Google Scholar] [CrossRef]
- Smart Contract. Available online: https://corporatefinanceinstitute.com/resources/knowledge/deals/smart-contracts/ (accessed on 20 July 2022).
- Jusic, A. Privacy between Regulation and Technology: GDPR and the Blockchain. Int. Univ. Sarajevo (IUS) Law J. 2022, 1, 47–59. Available online: https://ssrn.com/abstract=4049371 (accessed on 21 July 2022).
- Chhetri, T.R.; Kurteva, A.; Adigun, J.G.; Fensel, A. Knowledge Graph Based Hard Drive Failure Prediction. Sensors 2022, 22, 985. [Google Scholar] [CrossRef]
- Breitfuss, A.; Errou, K.; Kurteva, A.; Fensel, A. Representing emotions with knowledge graphs for movie recommendations. Future Gener. Comput. Syst. 2021, 125, 715–725. [Google Scholar] [CrossRef]
- Sermet, Y.; Demir, I. A Semantic Web Framework for Automated Smart Assistants: A Case Study for Public Health. Big Data Cogn. Comput. 2021, 5, 57. [Google Scholar] [CrossRef]
- Chhetri, T.R.; Kurteva, A.; DeLong, R.J.; Hilscher, R.; Korte, K.; Fensel, A. Data Protection by Design Tool for Automated GDPR Compliance Verification Based on Semantically Modeled Informed Consent. Sensors 2022, 22, 2763. [Google Scholar] [CrossRef]
- Longo, A.; Zappatore, M.; Bochicchio, M.A. Service level aware—Contract management. In Proceedings of the 2015 IEEE International Conference on Services Computing, New York, NY, USA, 27 June–2 July 2015; pp. 499–506. [Google Scholar] [CrossRef]
- Keller, A.; Ludwig, H. The WSLA Framework: Specifying and Monitoring Service Level Agreements for Web Services. J. Netw. Syst. Manag. 2003, 11, 57–81. [Google Scholar] [CrossRef]
- NoSQL. Available online: https://www.ontotext.com/knowledgehub/fundamentals/nosql-graph-database/ (accessed on 20 July 2022).
- Guo, L.; Liu, Q.; Shi, K.; Gao, Y.; Luo, J.; Chen, J. A Blockchain-Driven Electronic Contract Management System for Commodity Procurement in Electronic Power Industry. IEEE Access 2021, 9, 9473–9480. [Google Scholar] [CrossRef]
- Voronova, O. Development of contract management system for network companies under economy digitalization. E3S Web Conf. EDP Sci. 2020, 164, 09018. [Google Scholar] [CrossRef]
- Schmidt, R.N.; House, M.; Rodriguez, O.O. Journey into Dnv Hospital Accreditation and the Implementation of an Electronic Contract Management System (Ecms). J. Bus. Educ. Leadersh. 2019, 9, 67–75. Available online: http://asbbs.org/files/2019/JBEL_Vol9_Fall_2019.pdf#page=67 (accessed on 15 July 2022).
- Simić, S.; Marković, M.; Gostojić, S. Smart contract and blockchain based contract management system. In Proceedings of the 7th Conference on the Engineering of Computer Based Systems, ECBS 2021, Novi Sad, Serbia, 26–27 May 2021; Association for Computing Machinery: New York, NY, USA, 2021. [Google Scholar] [CrossRef]
- Zou, J.; Wang, Y.; Lin, K.J. A formal service contract model for accountable SaaS and Cloud Services. In Proceedings of the 2010 IEEE International Conference on Services Computing, Miami, FL, USA, 5–10 July 2010; pp. 73–80. [Google Scholar] [CrossRef]
- Perrin, O.; Godart, C. An approach to implement contracts as trusted intermediaries. In Proceedings of the First IEEE International Workshop on Electronic Contracting, San Diego, CA, USA, 6 July 2004; pp. 71–78. [Google Scholar] [CrossRef]
- Kabilan, V.; Johannesson, P. Semantic representation of contract knowledge using multi tier ontology. In Proceedings of the First International Conference on Semantic Web and Databases, SWDB’03, Berlin, Germany, 7–8 September 2003; CEUR-WS.org: Aachen, DEU, 2003; pp. 378–397. [Google Scholar] [CrossRef]
- De Cesare, S.; Geerts, G.L. Toward a perdurantist ontology of contracts. In Proceedings of the International Conference on Advanced Information Systems Engineering, Gdańsk, Poland, 25–26 June 2012; Springer: Cham, Switzerland, 2012; pp. 85–96. [Google Scholar] [CrossRef]
- Petrova, G.G.; Tuzovsky, A.F.; Aksenova, N.V. Application of the Financial Industry Business Ontology (FIBO) for development of a financial organization ontology. J. Phys. Conf. Ser. 2017, 803, 12116. [Google Scholar] [CrossRef]
- Matthias, G. The Impact of the Gdpr on Third-Party Contracts in the Cloud Service Industry (Tilburg University, 2019). Available online: http://arno.uvt.nl/show.cgi?fid=149355 (accessed on 20 July 2022).
- Doe, S. Practical Privacy: Report from the GDPR World. Leg. Inf. Manag. 2018, 18, 76–79. [Google Scholar] [CrossRef]
- Ferrari, V. EU Blockchain Observatory and Forum Workshop on GDPR, Data Policy and Compliance. Soc. Sci. Res. Netw. (SSRN) Electron. J. 2018, 8. [Google Scholar] [CrossRef]
- Strano, M.; Molina-Jimenez, C.; Shrivastava, S. Implementing a rule-based contract compliance checker. In Proceedings of the 9th IFIP WG 6.1 Conference on e-Business, e-Services and e-Society, I3E 2009, Nancy, France, 23–25 September 2009; Godart, C., Gronau, N., Sharma, S., Canals, G., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 96–111. [Google Scholar] [CrossRef]
- Mamadolimova, A.; Ambiah, N.; Lukose, D. Modeling Islamic finance knowledge for contract compliance in Islamic banking. In Proceedings of the International Conference on Knowledge-Based and Intelligent Information and Engineering Systems, Kaiserslautern, Germany, 12–14 September 2011; Springer: Cham, Switzerland, 2011; pp. 346–355. [Google Scholar] [CrossRef]
- Pantlin, N.; Wiseman, C.; Everett, M. Supply chain arrangements: The ABC to GDPR compliance—A spotlight on emerging market practice in supplier contracts in light of the GDPR. Comput. Law Secur. Rev. 2018, 34, 881–885. [Google Scholar] [CrossRef]
- Barati, M.; Rana, O. Tracking GDPR Compliance in Cloud-Based Service Delivery. IEEE Trans. Serv. Comput. 2022, 15, 1498–1511. [Google Scholar] [CrossRef]
- Cambronero, M.E.; Llana, L.; Pace, G.J. Timed contract compliance under event timing uncertainty. In Proceedings of the Legal Knowledge and Information Systems: JURIX 2017: The Thirtieth Annual Conference JURIX, Luxembourg, 13–15 December 2017; pp. 33–38. [Google Scholar] [CrossRef]
- The smashHitCore Ontology. Available online: https://gitlab.atb-bremen.de/smashhit/semantic-model/-/blob/master/smashHitCore.owl (accessed on 5 March 2022).
- Irwin, K.; Yu, T.; Winsborough, W.H. On the modeling and analysis of obligations. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 134–143. [Google Scholar] [CrossRef]
- Resource Description Framework (RDF) Sparql Query. Available online: https://www.w3.org/TR/rdf-sparql-query/ (accessed on 1 June 2022).
- Dragoni, N.; Giallorenzo, S.; Lafuente, A.L.; Mazzara, M.; Montesi, F.; Mustafin, R.; Safina, L. Microservices: Yesterday, today, and tomorrow. In Present and Ulterior Software Engineering; Springer: Cham, Switzerland, 2017; pp. 195–216. [Google Scholar] [CrossRef]
- Ontotext GraphDB. Available online: https://www.ontotext.com/products/graphdb/ (accessed on 1 June 2022).
- Flask-apscheduler. Available online: https://viniciuschiele.github.io/flask-apscheduler/ (accessed on 1 June 2022).
- Contract Compliance Verification GitHub Repository. Available online: https://github.com/AmarTauqeer/Contract/tree/master/backend/ (accessed on 1 June 2022).
- Swagger API Documentation. Available online: https://swagger.io/solutions/api-documentation/ (accessed on 1 June 2022).
- Ízdemir, F.; Ídemiş Ízger, Z. Rivest-Shamir-Adleman algorithm. In Partially Homomorphic Encryption; Springer: Cham, Switzerland, 2021; pp. 37–41. [Google Scholar] [CrossRef]
- Selent, D. Advanced encryption standard. Rivier Acad. J. 2010, 6, 1–14. Available online: https://www2.rivier.edu/journal/roaj-fall-2010/j455-selent-aes.pdf (accessed on 25 June 2022).
- Van Rossum, G.; Warsaw, B.; Coghlan, N. PEP 8–style guide for python code. Python. org 2001, 1565, 28. Available online: http://cnl.sogang.ac.kr/cnlab/lectures/programming/python/PEP8_Style_Guide.pdf, (accessed on 18 June 2022).
- JSON Web Tokens (JWT). Available online: https://www.json.org/json-en.html (accessed on 20 June 2022).
- Conference of the Independent Data Protection Supervisory Authorities of the Federation and the Länder. The Standard Data Protection Model—A Method for Data Protection Advising and Controlling on the Basis of Uniform Protection Goals, Version 2.0b. 2020. Available online: https://www.datenschutzzentrum.de/uploads/sdm/SDM-Methodology_V2.0b.pdf (accessed on 20 July 2022).
- Python. Available online: https://www.python.org/ (accessed on 8 June 2022).
- Flask. Available online: https://flask.palletsprojects.com/en/2.0.x/ (accessed on 8 June 2022).
- Flask-RESTful. Available online: https://flask-restful.readthedocs.io/en/latest/ (accessed on 8 June 2022).
- Flask-SQLAlchemy. Available online: https://flask-sqlalchemy.palletsprojects.com/en/2.x/ (accessed on 8 June 2022).
- Flask-Apispec: Auto-Documenting REST APIs for Flask. Available online: https://flask-apispec.readthedocs.io/en/latest/ (accessed on 8 June 2022).
- PyCryptodome. Available online: https://www.pycryptodome.org/en/latest/src/introduction.html (accessed on 8 June 2022).
- SPARQL Endpoint Interface to Python. Available online: https://sparqlwrapper.readthedocs.io/en/latest/ (accessed on 8 June 2022).
- Docker. Available online: https://www.docker.com/ (accessed on 8 June 2022).
- PyJWT. Available online: https://pyjwt.readthedocs.io/en/stable/ (accessed on 8 June 2022).
- Marshmallow: Simplified Object Serialisation. Available online: https://marshmallow.readthedocs.io/en/stable/index.html (accessed on 4 April 2022).
- Federal Information Processing Standards Publication (FIPS), P. 197. Advanced Encryption Standard (AES), National Institute of Standards and Technology, US Department of Commerce. Available online: https://nvlpubs.nist.gov/nistpubs/fips/nist.fips.197.pdf (accessed on 20 July 2022).
- Garg, N.; Yadav, P. Comparison of asymmetric algorithms in cryptography. J. Comput. Sci. Mob. Comput. (IJCSMC) 2014, 3, 1190–1196. Available online: https://www.ijcsmc.com/docs/papers/April2014/V3I4201499a73.pdf (accessed on 17 July 2022).
- Unit Testing Framework. Available online: https://docs.python.org/3/library/unittest.html (accessed on 16 June 2022).
- Pellegrini, T.; Mireles, V.; Steyskal, S.; Panasiuk, O.; Fensel, A.; Kirrane, S. Automated rights clearance using semantic web technologies: The DALICC framework. In Semantic Applications: Methodology, Technology, Corporate Use; Hoppe, T., Humm, B., Reibold, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2018; pp. 203–218. [Google Scholar] [CrossRef]
- Licence Clearance Tool Description and Documentation. Available online: https://wiki.ni4os.eu/index.php/LicenseClearanceTool-DescriptionandDocumentation (accessed on 16 June 2022).

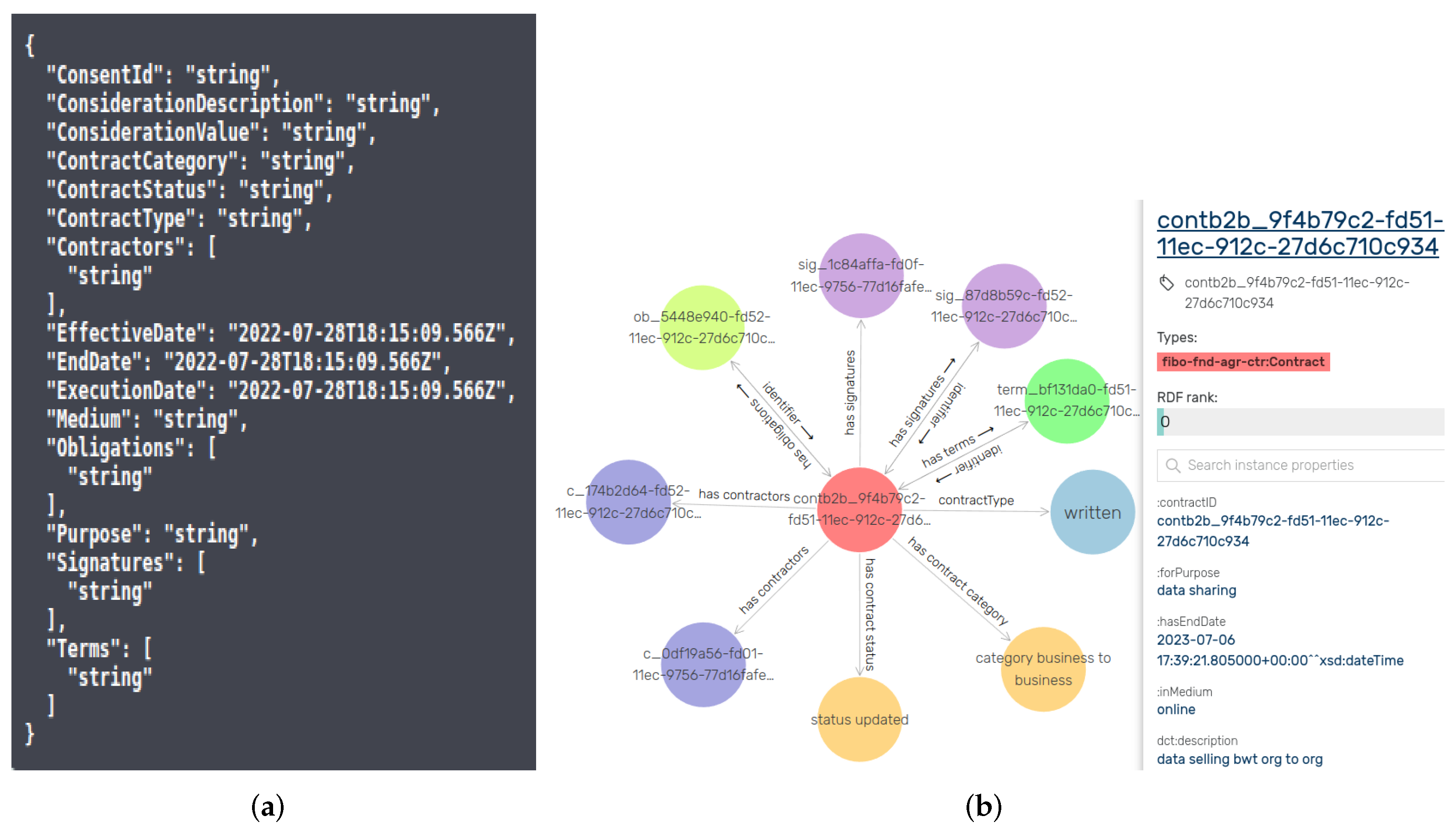

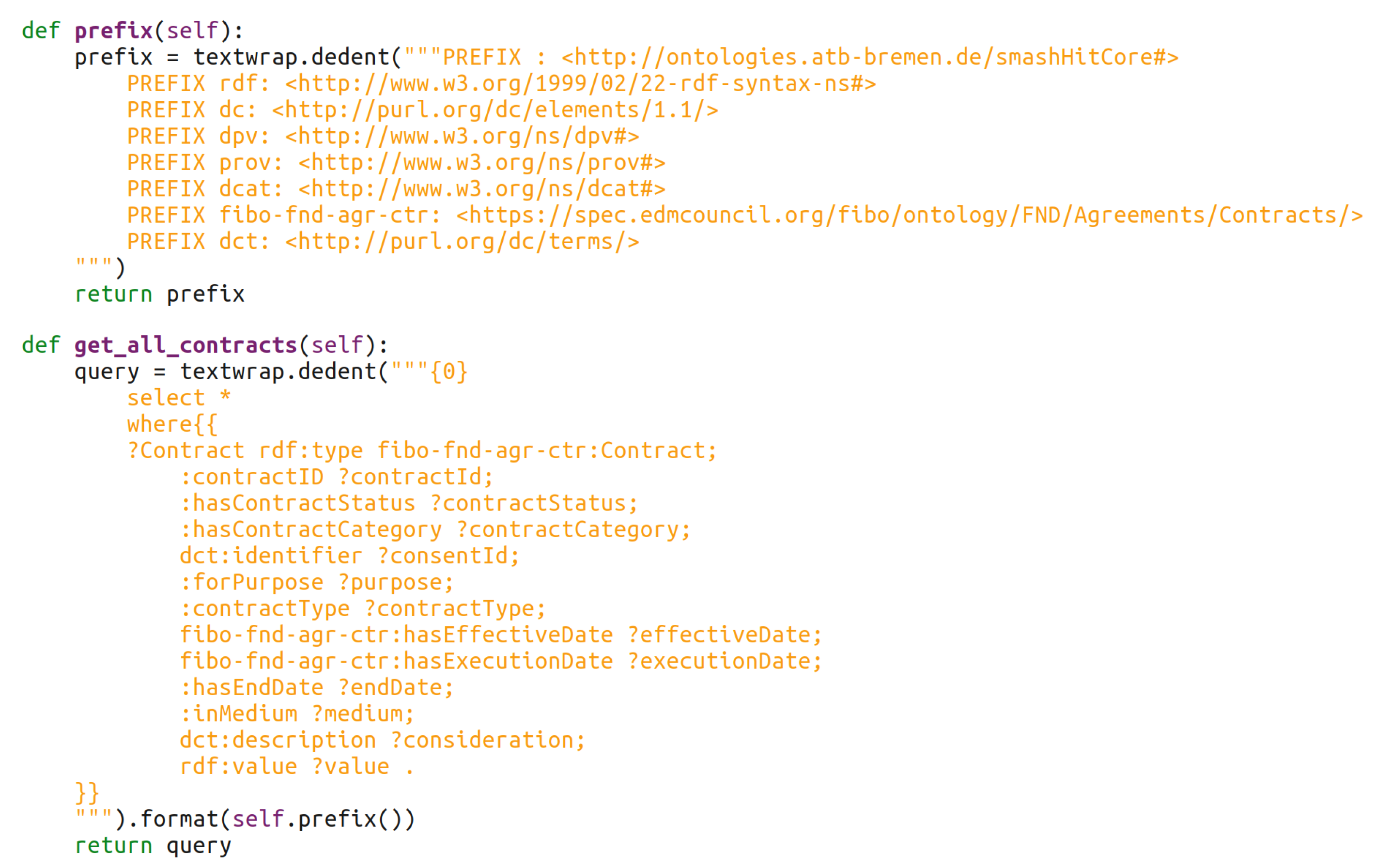

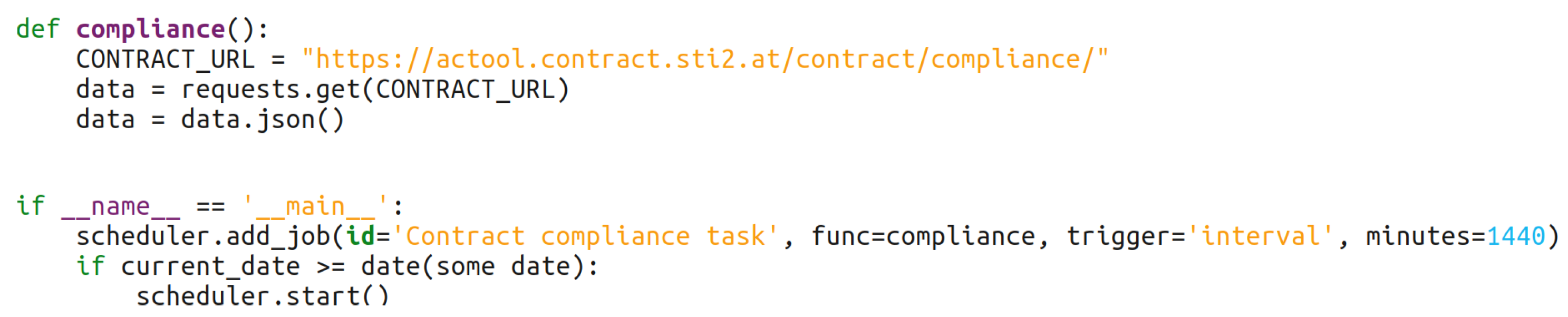
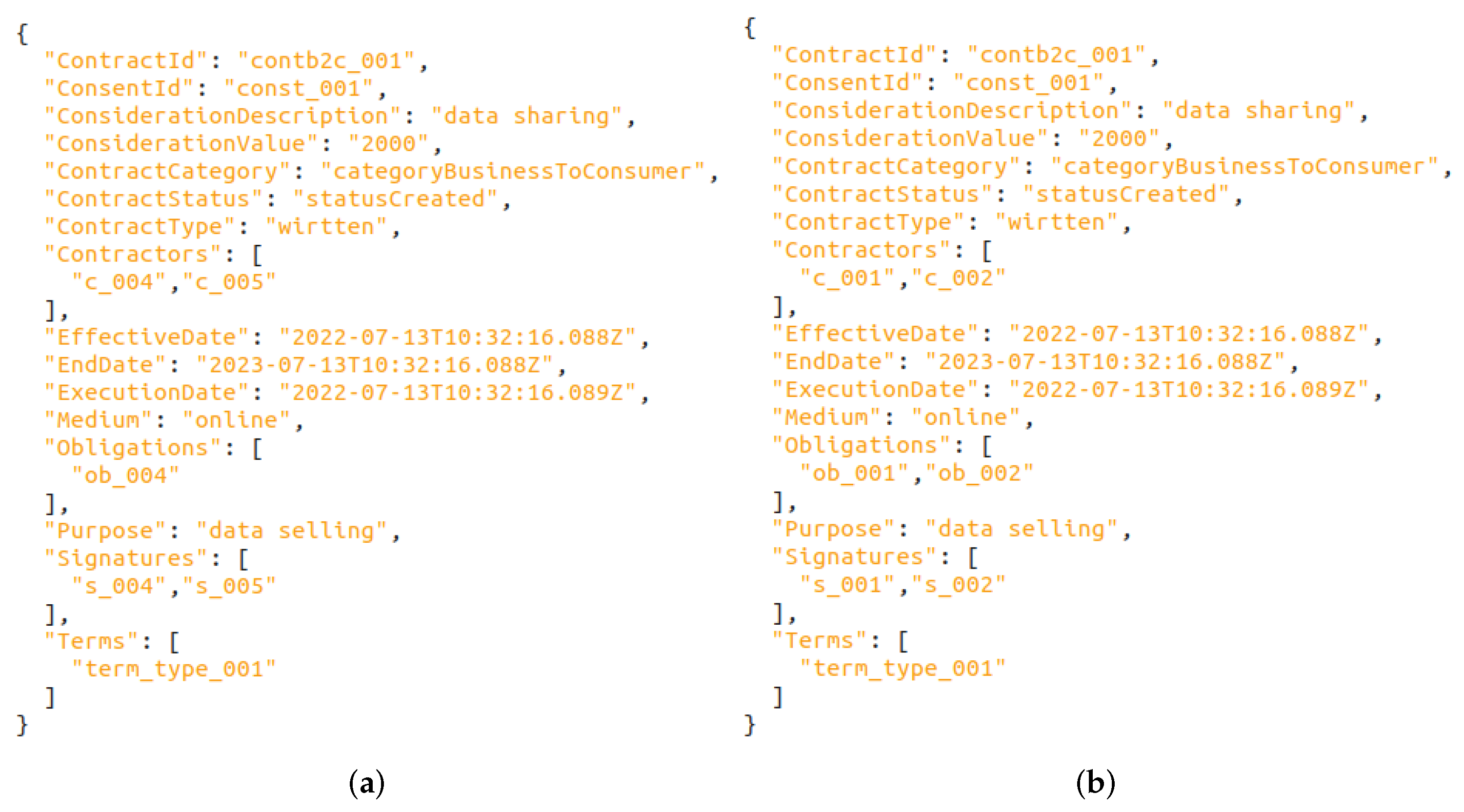

| Software (or Libraries) | Version |
|---|---|
| Python [58] | 3.8 |
| Flask [59] | 1.1.2 |
| Flask-RESTful [60] | 0.3.8 |
| Flask-SQLAlchemy [61] | 2.5.1 |
| Python Requests | 2.25.1 |
| Flask Apispec [62] | 0.11.0 |
| Pycryptodome [63] | 3.10.1 |
| SPARQLWrapper [64] | 1.8.5 |
| Docker ([65] Community Edition) | 20.X |
| SQLite | 2.6 |
| GraphDB free edition [49] | 9.4.1 |
| Protégé | 5.5.0 |
| Pyjwt [66] | 1.7.1 |
| ID | Contract Basic Information (Time in Minutes) | Contractual Parties (Time in Minutes) | Contractual Term (Time in Minutes) | Contractual Clauses (Time in Minutes) | Contractor Signatures (Time in Minutes) | Total (Time in Minutes) |
|---|---|---|---|---|---|---|
| 1 | 1.00 | 0:50 | 0.16 | 0.44 | 0.16 | 3.55 |
| 2 | 1.05 | 1:55 | 0.32 | 1.58 | 0.30 | 5.54 |
| 3 | 1.20 | 2:00 | 1.50 | 3.50 | 0.35 | 9.34 |
| 4 | 1.30 | 1:58 | 2.50 | 4.50 | 0.40 | 11.48 |
| 5 | 1.40 | 2:00 | 1.50 | 3.52 | 0.37 | 10.39 |
| 6 | 1.20 | 1:57 | 1.48 | 3.40 | 0.35 | 9.33 |
| 7 | 1.30 | 2:00 | 1.20 | 2.40 | 0.40 | 8.16 |
| 8 | 1.10 | 1:58 | 1.30 | 2.30 | 0.35 | 7.42 |
| 9 | 1.25 | 2:00 | 1.40 | 3.45 | 0.37 | 9.45 |
| 10 | 1.35 | 1:55 | 1.58 | 3.25 | 0.42 | 9.34 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tauqeer, A.; Kurteva, A.; Chhetri, T.R.; Ahmeti, A.; Fensel, A. Automated GDPR Contract Compliance Verification Using Knowledge Graphs. Information 2022, 13, 447. https://doi.org/10.3390/info13100447
Tauqeer A, Kurteva A, Chhetri TR, Ahmeti A, Fensel A. Automated GDPR Contract Compliance Verification Using Knowledge Graphs. Information. 2022; 13(10):447. https://doi.org/10.3390/info13100447
Chicago/Turabian StyleTauqeer, Amar, Anelia Kurteva, Tek Raj Chhetri, Albin Ahmeti, and Anna Fensel. 2022. "Automated GDPR Contract Compliance Verification Using Knowledge Graphs" Information 13, no. 10: 447. https://doi.org/10.3390/info13100447
APA StyleTauqeer, A., Kurteva, A., Chhetri, T. R., Ahmeti, A., & Fensel, A. (2022). Automated GDPR Contract Compliance Verification Using Knowledge Graphs. Information, 13(10), 447. https://doi.org/10.3390/info13100447








