A Digital Signature Model Using XAdES Standard as a Rest Service
Abstract
:1. Introduction
2. Background and Related Works
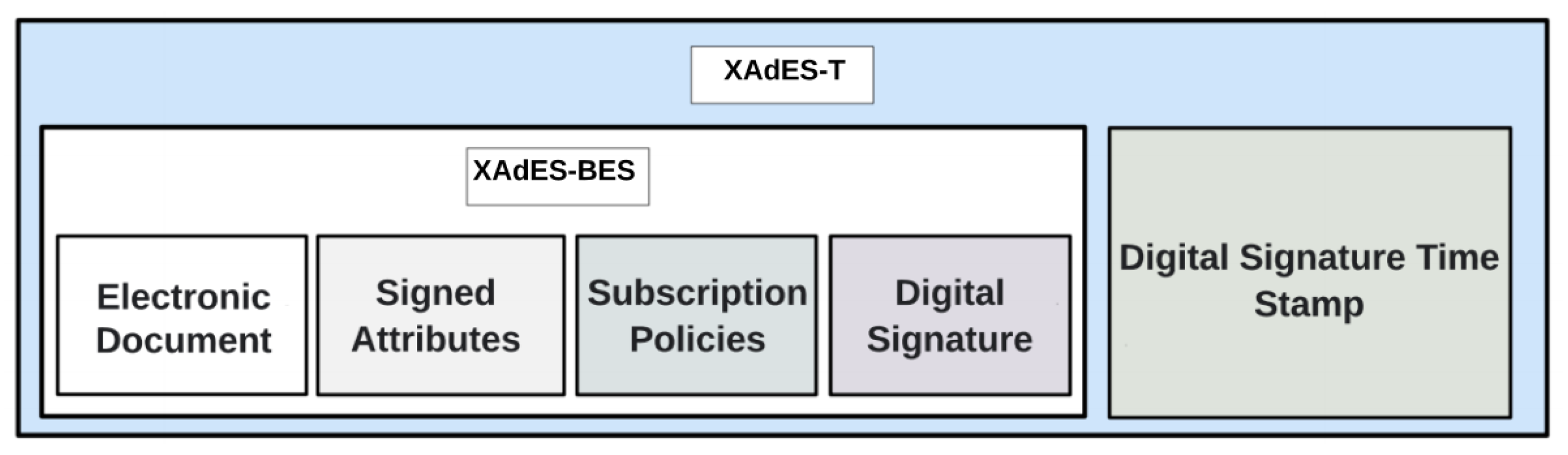
- XAdES-BES: it is basic way of signing documents in XML format, where authenticity and integrity of records are guaranteed; however, it does not offer the non-repudiation.
- XAdES-T: there is the addition of timestamp to the XAdES-BES basic signature, which ensures non-repudiation.
- XAdES-C: it adds dataset references to XAdES-T that support electronic signature validation. Information such as certification path reference, certificate status and revocation. This type of signature is important when you want to archive information externally.
- XAdES-X: builds on XAdES-C by adding timestamps to protect against risk of any keys used in the certificate chain or revocation status information that may be compromised.
- XAdES-X-L: added to XAdES-X providing more validation data, such as certificate revocation values, in case the revocation information is not stored in another external location.
- XAdES-A: builds on XAdES-X-L by adding a timestamp field for archiving signed documents.
Related Works
3. The Electronic Signature Law in Brazil
- Digital Degree_v1.00.xsd: defines the syntactic structure of the graduate’s XML.
- Academic Documentation Digital Degree Registration_v1.090.xsd: defines the syntactic structure of academic documentation for issuance and registration.
- Basic Types_v1.00.xsd: responsible for syntactic control of all types used in other files of this technical specification of the digital degree. It serves to guarantee the syntactic integrity of the fields used in the digital degree.
- Digital Degree Layout_v1.00.xsd: Responsible for syntactic control of the XML structure of the graduate.
- Academic Documentation Layout of Digital Degree Registration_v1.00: Responsible for syntactic control of the XML structure of academic documentation for issuance and registration.
- Xmldsig-core-schema_v1.1.xsd: responsible for syntactic control of the digital signature XML structure.
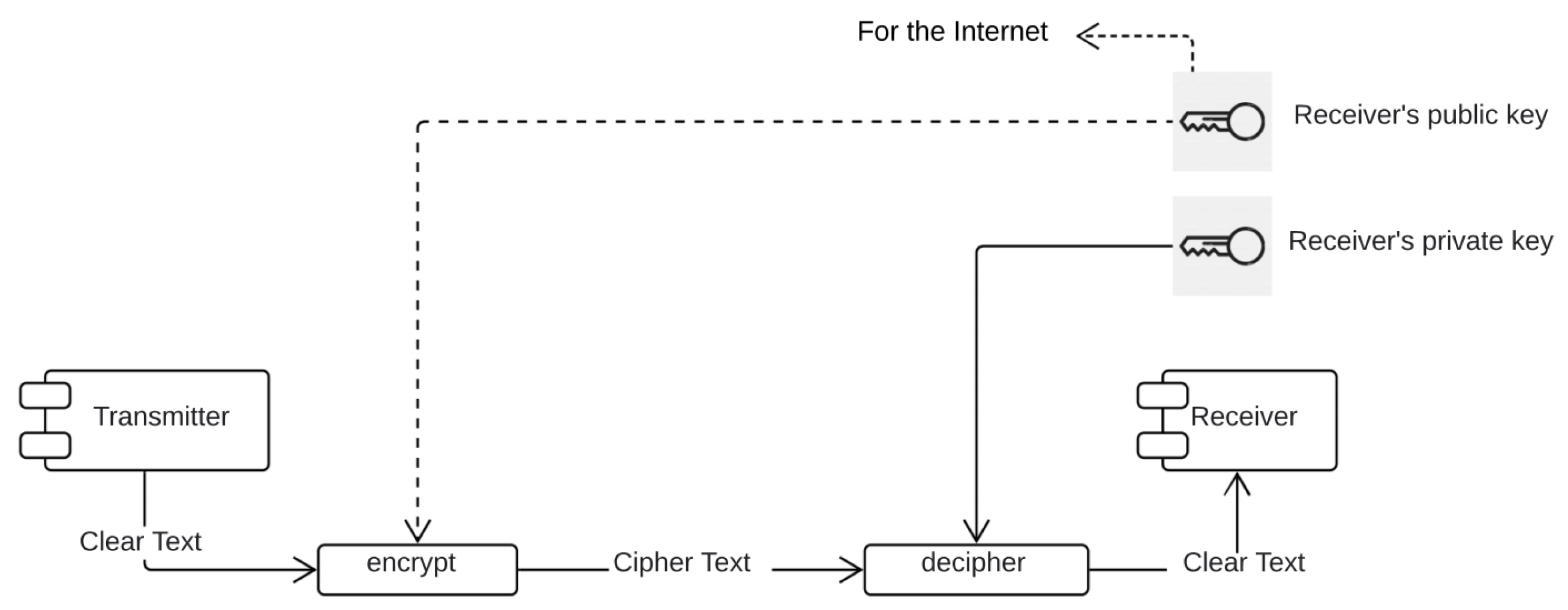
4. Digital Signature Requirements
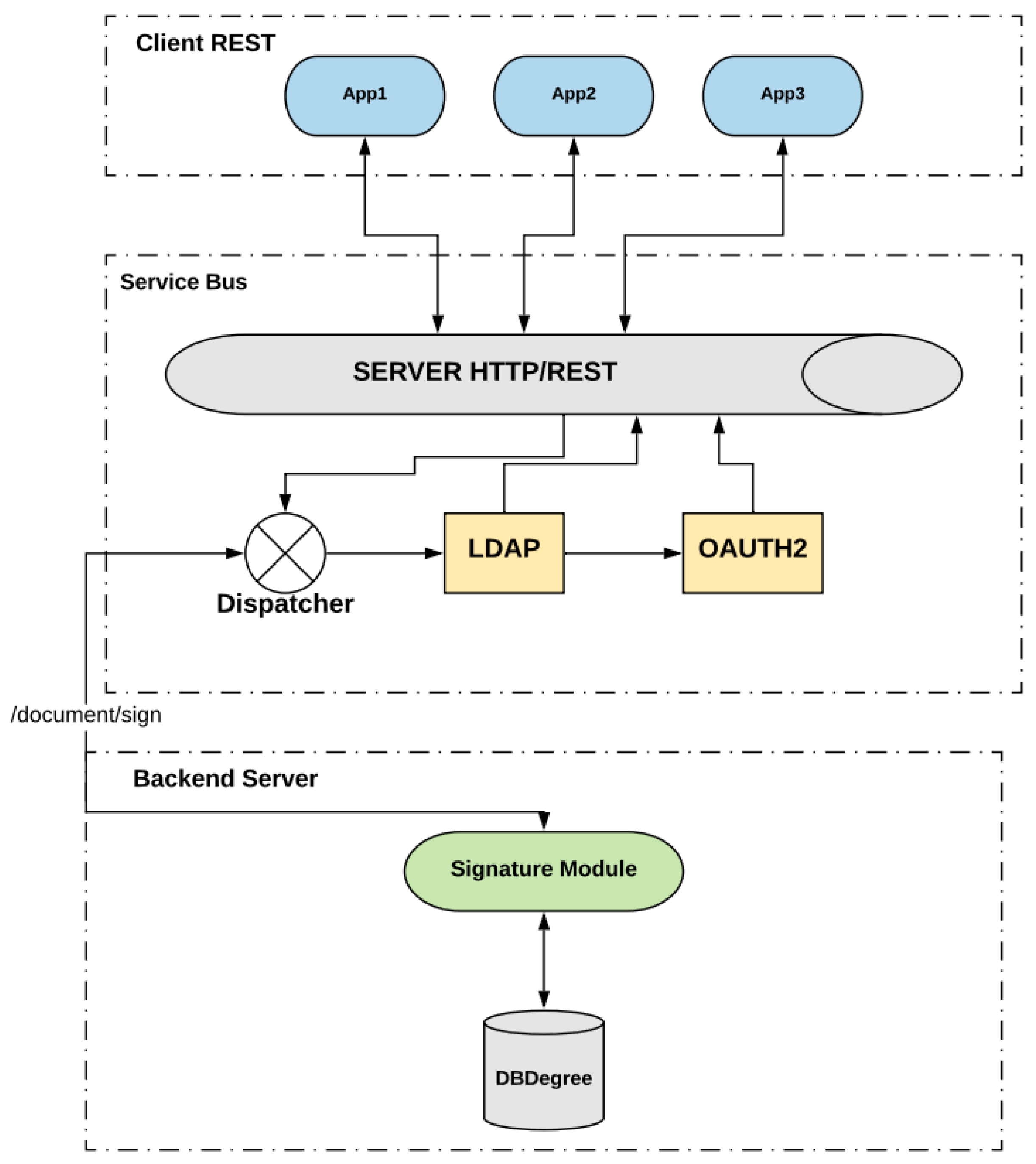
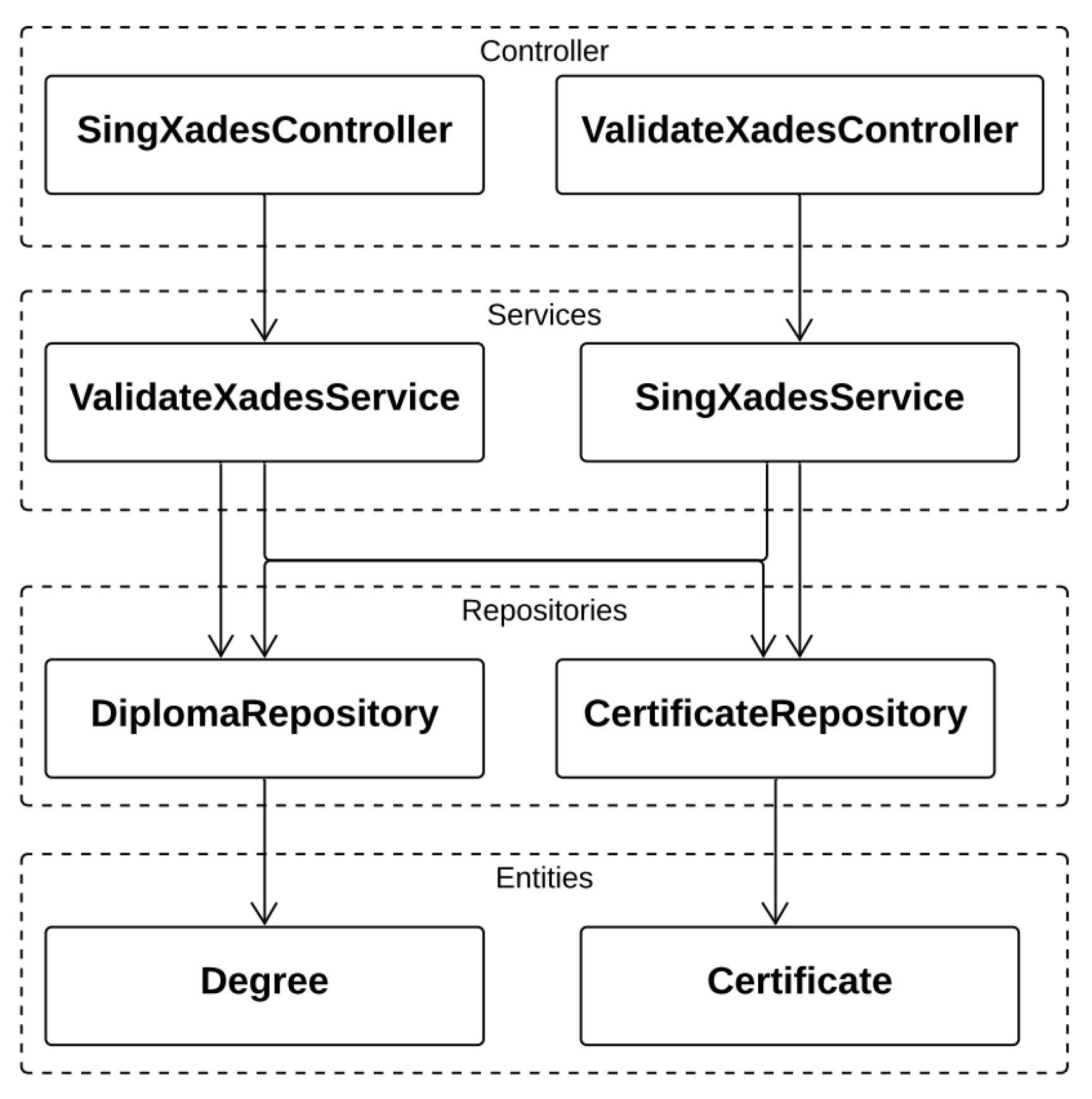
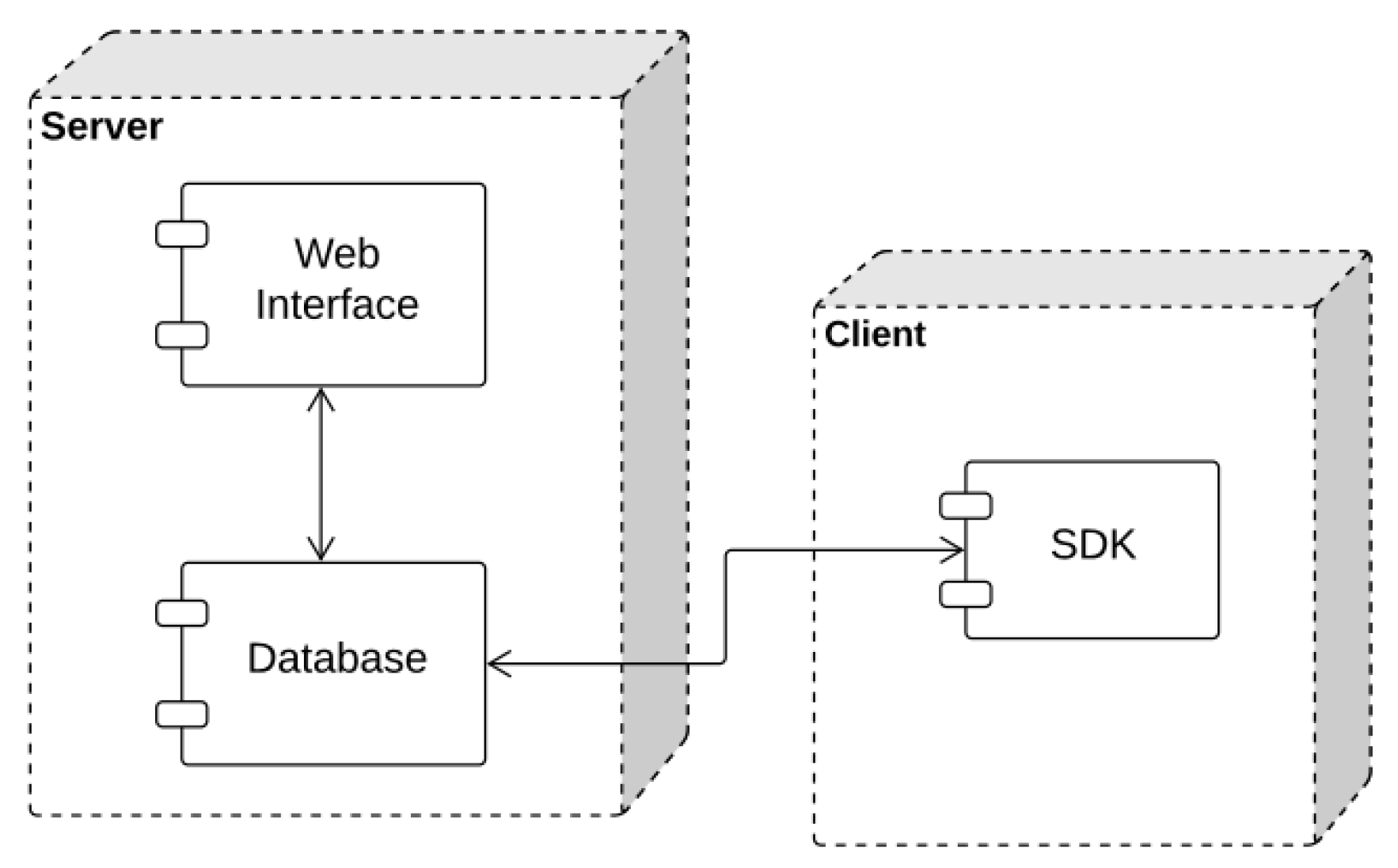
5. Digital Signature Model
- XadesController Signature: It is the initial class that has the communication interface with the service bus. The signXades method is the main method for signing in the XAdES standard. As a parameter, the degrees are compressed in zip format, the certificate password and the idPerson are sent to search the certificate.
- ValidateXadesController: It is the initial class that makes the communication interface for the validity of a signed degree. The main method is the validate method, which checks if the signed degree complies with the MEC standard, as the xsd format for degree validation.
- SignatureXadesService: It is the service class that actually has the function of signing each document that is inside the digital degree signature zip file. The main method of this class is the sign method, which makes the signature of a degree using the XAdES standard. There are two auxiliary methods, one to save the signed degree into the database and another to fetch the certificate saved by the sdk in the database to perform the signature.
- ValityXadesService: It is the service class that uses xsds files to validate the degree signed in the MEC standard. The method validateDegree is the main method that informs whether the degree is valid or not according to the standard specified in xsd.
- DegreeRepository: It is the class that saves the signed degree in the database and joins the saved degree to the signed idPerson and the idPerson of the degree student.
- CertificateRepository: Retrieves the certificate from idPerson to sign a batch of degrees.
- Certificate: It is an entity that has all database parameters. It is all the data that will be retrieved in the certificate table.
- Degree: It is the entity that sets all the parameters to save a degree. All data will be saved in the degree table.
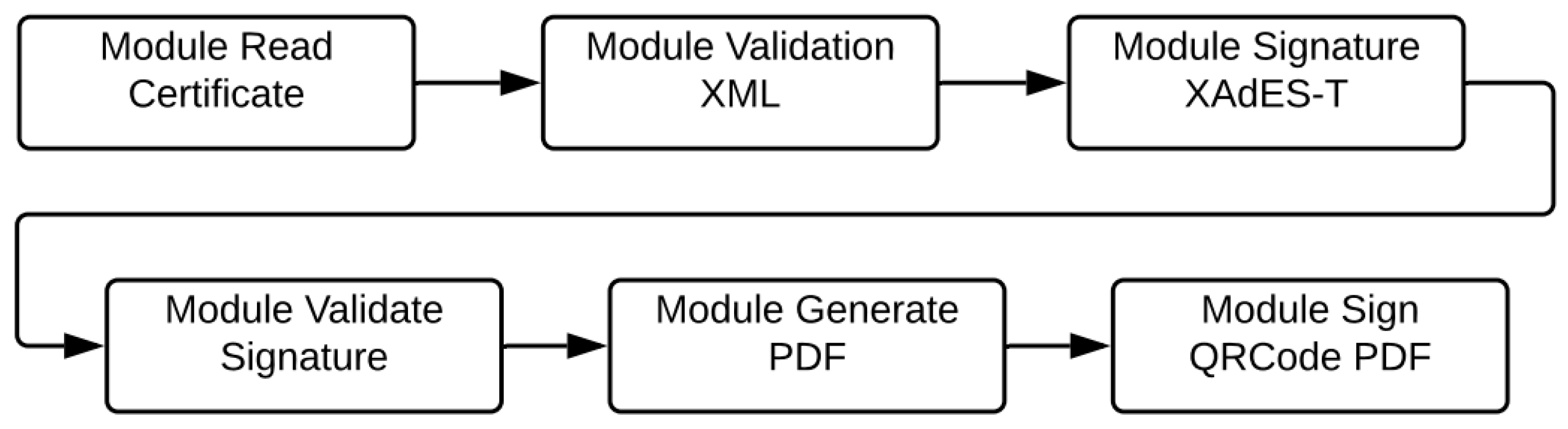
- The digital signature of the degrees must be made with the A1 or A3 format.
- After reading the certificate, it is necessary to generate the XML according to the XSDs provided by the MEC website digital degree (accessed on 20 February 2021).
- After reading and validating with the XSDs provided by MEC, the signature is made with the XAdES-T standard.
- It is necessary to provide a module for the external digital signature.
- After signing the degree in XML format, it is necessary to generate the degree in visual format in PDF format.
- A QRCode is generated to ensure the integrity of the degree in visual format.
- Both the degree signed in XML format and the other in visual format, in PDF format must be made available to the student by digital means, being accessible at any time.
6. Tests and Discussion
6.1. Guarantee of Better Security in the Signed Degree
6.2. European Standard for Signing Digital (Europass)
- Aggregate Subscription: It is a kind of subscription that receives n different subscriptions from n different users, and it is possible to summarize all these subscriptions in a single short subscription. This summary ensures that the n users signed the document. The advantage of this technique is that the computing power for signature storage and verification is greatly reduced. This technique is recommended in locations with low bandwidth and limited storage space [36].
- Ring Signing: This scheme assumes a public key for all users and a private key for each user. This kind of signature is used on documents that need traceability and that need long-term protection. This approach eliminates the needing of a third party to validate the signature on the signed document was made [36].
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Educação, Ministério da Educação: Portaria no 554, de 11 de Março de 2019. 2019. Available online: http://www.in.gov.br/materia/-/asset_publisher/Kujrw0TZC2Mb/content/id/66544171/do1-2019-03-12-portaria-n-554-de-11-de-marco-de-2019-66543842 (accessed on 2 May 2021).
- UnB Diploma, UnB Diploma. Sistema de Emissão de Diplomas Digitais. 2018. Available online: http://servicos.unb.br/diploma (accessed on 2 April 2021).
- Normativa, I. Instrução Normativa no 1, de 15 de Dezembro de 2020. 2020. Available online: http://portal.mec.gov.br/diplomadigital/arquivos/in_01_15122020.pdf (accessed on 2 May 2021).
- ICP-BRASIL, D.A. PadrõEs E Algoritmos CriptográFicos. 2019. Available online: https://www.gov.br/iti/pt-br/centrais-deconteudo/doc-icp-01-01-v-4-2-padroes-e-algoritmos-criptograficos-da-icp-brasil-copy-pdf (accessed on 13 July 2021).
- Klavos, N.; Stallings, W. Book Review. In Cryptography and Network Security: Principles and Practice, 6th ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2013; 752p, Volume 23, pp. 49–50. ISBN 13: 978-0133354690. [Google Scholar]
- Forouzan, B.; Catherine, C.; Sophia, C.F. Introduction to Data Communications and Networking; McGraw-Hill, Inc.: New York, NY, USA, 2012. [Google Scholar]
- ETSI. 101 903 Xml Advanced Electronic Signatures (xades), v1. 3.2. European Telecommunications Standards Institute. 2010. Available online: https://www.etsi.org/deliver/etsi_ts/101900_101999/101903/01.04.02_60/ts_101903v010402p.pdf (accessed on 1 June 2021).
- Brzica, H.; Boris, H.; Hrvoje, S. Long-Term Preservation of Validity of Electronically Signed Records. In Future 2013. November 2013. Available online: http://darhiv.ffzg.unizg.hr/id/eprint/8291/ (accessed on 6 January 2021).
- Crampton, J. Applying Hierarchical and Role-Based Access Control to Xml Documents. In Proceedings of the 2004 Workshop on Secure Web Service, SWS ’04, Fairfax, VA, USA, 29 October 2004; Association for Computing Machinery: New York, NY, USA, 2004; pp. 37–46, ISBN 158113973X. [Google Scholar] [CrossRef]
- Engelbertz, N.; Vladislav, M.; Juraj, S.; David, H.; Nurul-lah, E.; Jörg, S. Security analysis of xades validation in the CEF digital signature services (DSS). In Proceedings of the Open Identity Summit 2019, OID 2019, Garmisch-Partenkirchen, Germany, 28–29 March 2019; Roßnagel, H., Sven, W., Detlef, H., Eds.; GI. Bonn: Bonn, Germany, 2019; Volume P-293 de LNI, pp. 95–106. Available online: https://dl.gi.de/handle/20.500.12116/20997 (accessed on 6 March 2020).
- Lepiane, C.D.; Pereira, F.L.; Pieri, G.; Martins, D.; Martina, J.E.; Rabelo, M.L. Digital degree certificates for higher education in brazil: A technical policy specification. In Proceedings of the ACM Symposium on Document Engineering 2019, Berlin, Germany, 23–26 September 2019; Schimmler, S., Uwe, M.B., Eds.; Association for Computing Machinery: New York, NY, USA, 2019; pp. 7:1–7:10. Available online: https://dl.acm.org/doi/abs/10.1145/3342558.3345398 (accessed on 14 March 2021).
- de Oliveira Fernandes, E.; Lima, J.L. Estudo da Tecnologia Blockchain para Aplicação na EmissãO, Arquivamento e Validação de Diplomas de Graduação em Formato Digital. Anais do Simpósio de Tecnologia da Informação e da Semana de Iniciação Científica do Curso de Sistemas de Informação (ISSN em Fase de Registro). 2019, pp. 36–40. Available online: https://www.anais.ueg.br/index.php/sti_sic/article/view/13988 (accessed on 14 April 2020).
- Ibarz, J.C. Bringing json signatures to etsi ades framework: Meet jades signatures. Comput. Stand. Interfaces 2020, 71, 103434. Available online: https://www.sciencedirect.com/science/article/abs/pii/S0920548919300960 (accessed on 21 February 2021). [CrossRef]
- Indriyawati, H.; Winarti, T.; Vydia, V. Web-based document certification system with advanced encryption standard digital signature. Indones. J. Electr. Eng. Comput. Sci. 2021, 516–521. [Google Scholar] [CrossRef]
- Europass Framework for Digitally Signed Credentials. 2018. Available online: https://ec.europa.eu/futurium/en/system/files/ged/europass_background-info_framework-digitally-signed-credentials.pdf (accessed on 10 April 2021).
- Yarygina, T.; Bagge, A.H. Overcoming security challenges in microservice architectures. In Proceedings of the 2018 IEEE Symposium on Service-Oriented System Engineering (SOSE), Bamberg, Germany, 26–29 March 2018; pp. 11–20. Available online: https://ieeexplore.ieee.org/abstract/document/8359144 (accessed on 8 February 2021).
- Educação, Ministério da Educação: Portaria no 330, de 05 de abril de 2018. 2018. Available online: http://www.in.gov.br/materia/-/asset_publisher/Kujrw0TZC2Mb/content/id/9365055/do1-2018-04-06-portaria-n-330-de-5-de-abril-de-2018-9365051 (accessed on 17 April 2021).
- Diploma Digital. 2020. Available online: http://portal.mec.gov.br/diplomadigital/ (accessed on 10 May 2021).
- DE, Geração e Verificação: Requisitos Mínimos para Geração e Verificação de Assinaturas Digitais na icp-Brasil doc-icp-15.01 versão 2.0. ICP-Brasil, 2010. xii. Available online: https://www.gov.br/iti/pt-br/centrais-de-conteudo/doc-icp-15-01-v-2-0-pdf (accessed on 2 May 2021).
- Bartel, M.; Boyer, J.; Fox, B.; LaMacchia, B.; Simon, E. Xml Signature Syntax and Processing Version 1.1. Signature 2013 6, 1. Available online: https://www.w3.org/TR/xmldsig-core1/ (accessed on 10 February 2021).
- Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R.; Polk, W.T. Internet x. 509 Public Key Infrastructure Certificate and Certificate Revocation List (crl) Profile. IETF. RFC 2008, 5280, 1–151. Available online: https://datatracker.ietf.org/doc/html/rfc5280 (accessed on 13 March 2021).
- Marcilio, D.; Bonifácio, R.; Monteiro, E.; Canedo, E.; Luz, W.; Pinto, G. Are static analysis violations really fixed? A closer look at realistic usage of sonarqube. In Proceedings of the 2019 IEEE/ACM 27th International Conference on Program Comprehension (ICPC), Montreal, QC, Canada, 25–26 May 2019; pp. 209–219. Available online: https://ieeexplore.ieee.org/abstract/document/8813272 (accessed on 9 April 2021).
- Marchand-Melsom, A.; Nguyen Mai, D.B. Automatic repair of OWASP top 10 security vulnerabilities: A survey. In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering Workshops, Seoul, Korea, 27 June–19 July 2020; pp. 23–30. Available online: https://dl.acm.org/doi/abs/10.1145/3387940.3392200 (accessed on 27 January 2021).
- Riadi, I.; Pradana, A.R. Vulnerability Analysis of E-Voting Application Using Open Web Application Security Project (Owpasp) Framework. 2019. Available online: https://pdfs.semanticscholar.org/2be6/83e9e959ca6746a9134a236deb4b603c04cd.pdf (accessed on 15 July 2021).
- Mishra, S.; Majed, A.A.; Sunil, K.S. Impact of Security Standards and Policies on the Credibility of E-Government. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 1–12. Available online: https://link.springer.com/article/10.1007/s12652-020-02767-5 (accessed on 12 January 2021).
- Sudaryono, S.; Aini, Q.; Lutfiani, N.; Hanafi, F.; Rahardja, U. Application of blockchain technology for ilearning student assessment. IJCCS Indones. J. Comput. Cybern. Syst. 2020, 14, 209–218. Available online: https://journal.ugm.ac.id/ijccs/article/view/53109 (accessed on 18 January 2021). [CrossRef]
- Panachev, A.; Shcherbitsky, V.; Medvedev, M.A. Application of blockchain technologies and game approach in the educational process of universities. AIP Conf. Proc. 2021, 2333, 100004. Available online: https://aip.scitation.org/doi/abs/10.1063/5.0042076 (accessed on 18 March 2021).
- Liang, X.; Xu, S. Student performance protection based on blockchain technology. J. Phys. Conf. Ser. 2021, 1748, 022006. Available online: https://iopscience.iop.org/article/10.1088/1742-6596/1748/2/022006/meta (accessed on 20 March 2021). [CrossRef]
- Meng, N.; Shunxiang, Z. University Education Resource Sharing Based on Blockchain and Ipfs. In Big Data Analytics for Cyber-Physical System in Smart City; Atiquzzaman, M., Neil, Y., Zheng, X., Eds.; Springer: Singapore, 2021; pp. 1808–1813. ISBN 978-981-33-4572-0. Available online: https://link.springer.com/chapter/10.1007/978-981-33-4572-0_270 (accessed on 15 November 2020).
- Palma, L.M.; Vigil, M.A.; Pereira, F.L.; Martina, J.E. Blockchain and smart contracts for higher education registry in brazil. Int. J. Netw. Manag. 2019, 29, e2061. Available online: https://onlinelibrary.wiley.com/doi/full/10.1002/nem.2061 (accessed on 8 November 2020). [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. 2019, 52, 1–34. Available online: https://dl.acm.org/doi/abs/10.1145/3316481 (accessed on 22 January 2021). [CrossRef] [Green Version]
- Costa, R.; Faustino, D.; Lemos, G.; Queiroga, A.; Djohnnatha, C.; Alves, F.; Lira, J.; Pires, M. Uso não financeiro de blockchain: Um estudo de caso sobre o registro, autenticação e preservação de documentos digitais acadêmicos. In Anais do I Workshop em Blockchain: Teoria, Tecnologias e Aplicações; Sociedade Brasileira de Computação: Porto Alegre, Brazil, 2018; Available online: https://sol.sbc.org.br/index.php/wblockchain/article/view/2356 (accessed on 23 March 2021).
- Dubrowsky, A. Transformação Digital nas InstituiçõEs Privadas de Ensinosuperior Brasileiras: Proposta para Autenticação de Diplomas Digitais de Graduação por Meio de Blockchain. Fundação Getúlio Vargas. 2019. Available online: http://bibliotecadigital.fgv.br/dspace;/bitstream/handle/10438/27717/DISSERTACAO_ALEXANDER_DUBROWSKY_VF.pdf (accessed on 17 March 2021).
- AN Digital Política de PreservaçãO Digital. 2016. Available online: http://www.siga.arquivonacional.gov.br/images/an_digital/and_politica_preservacao_digital_v2.pdf (accessed on 25 March 2021).
- Stančić, H. Long-Term Preservation of Digital Signatures. Em Tehnični in Vsebinski Problemi Klasičnega in Elektronskega Arhiviranja. 2016. Available online: https://www.researchgate.net/profile/Hrvoje-Stancic/publication/301364818_Long-term_Preservation_of_Digital_Signatures/links/5e05edd44585159aa49d8b2d/Long-term-Preservation-of-Digital-Signatures.pdf (accessed on 23 March 2021).
- Fang, W.; Chen, W.; Zhang, W.; Pei, J.; Gao, W.; Wang, G. Digital signature scheme for information non-repudiation in blockchain: A state of the art review. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 56. Available online: https://jwcn-eurasipjournals.springeropen.com/articles/10.1186/s13638-020-01665-w (accessed on 12 April 2021). [CrossRef] [Green Version]
- Drescher, D. Protecting the Data Store; Apress: Berkeley, CA, USA, 2017; pp. 135–143. Available online: https://link.springer.com/chapter/10.1007/978-1-4842-2604-9_16 (accessed on 12 January 2021).

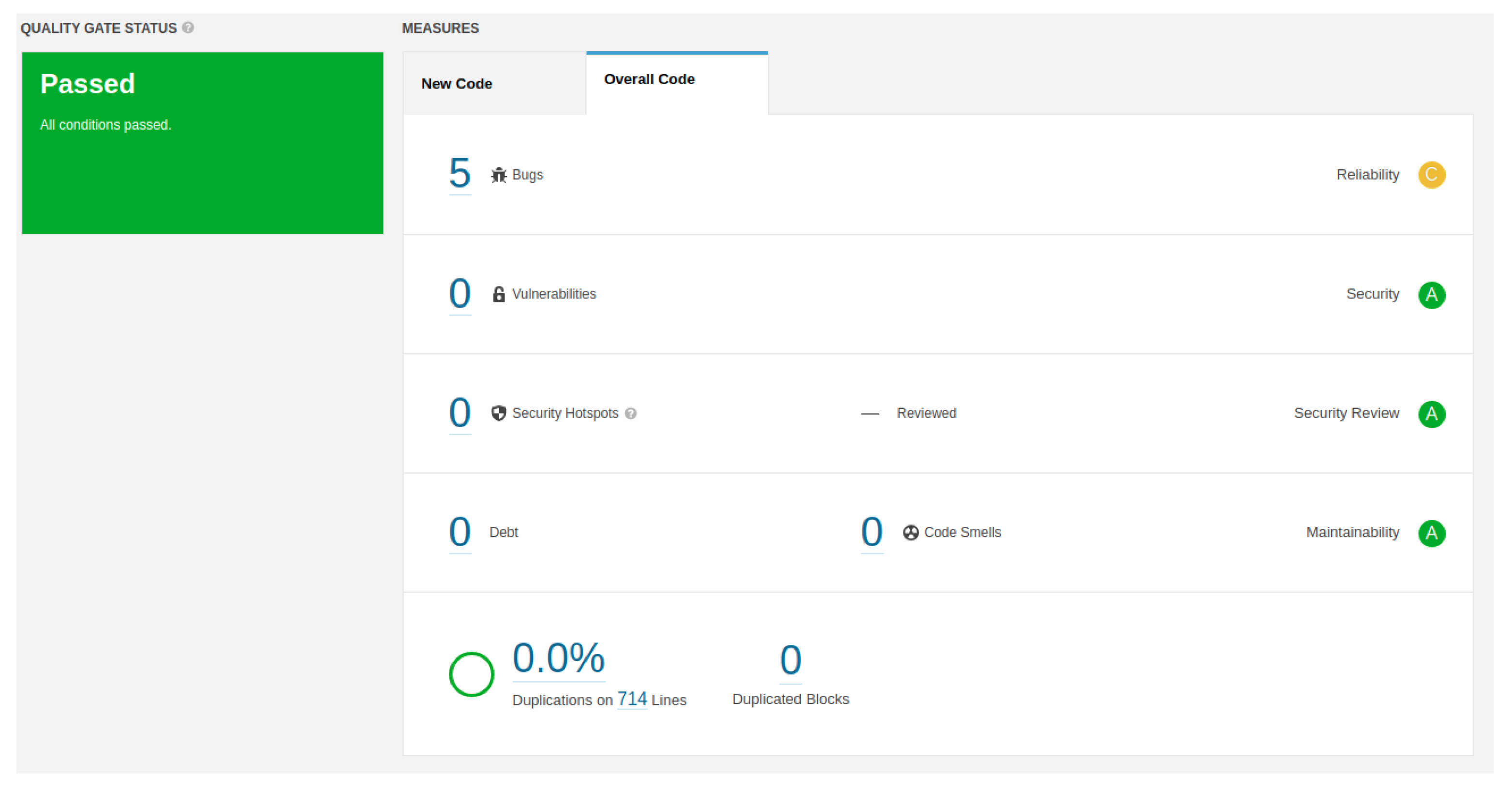

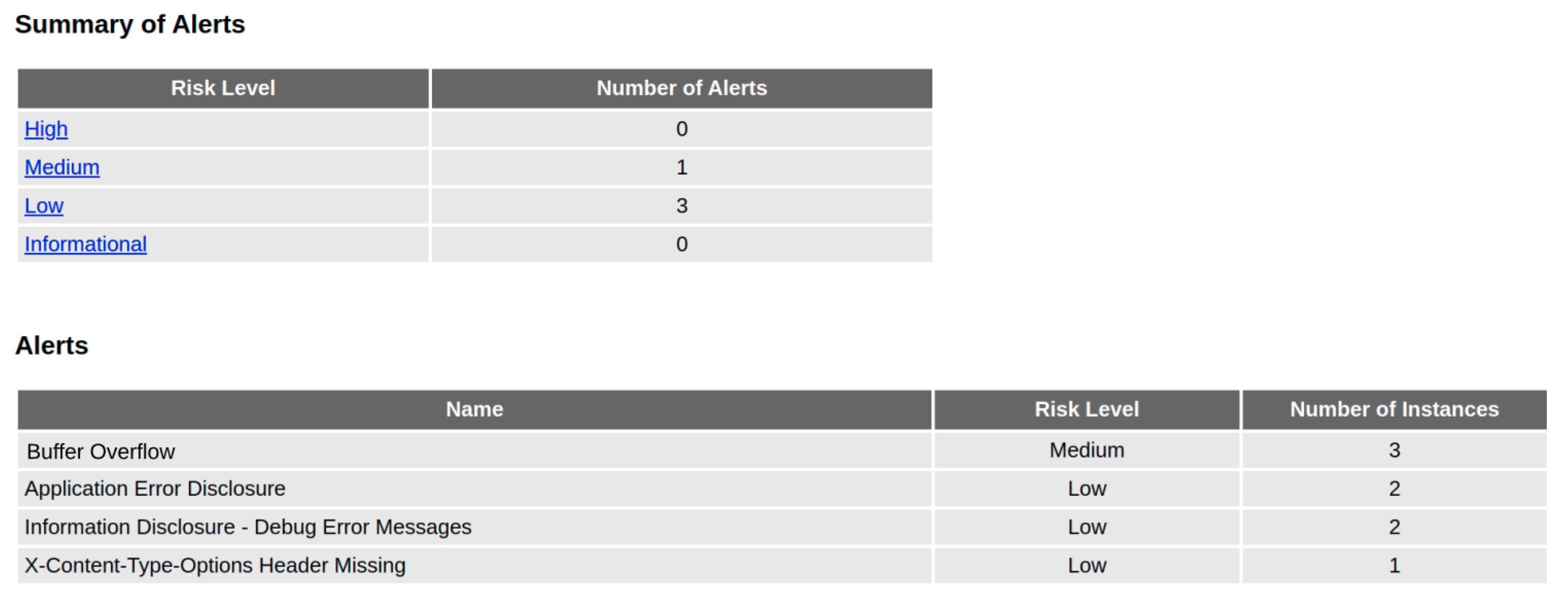

| Requirements | Expected Value | Value Obtained |
|---|---|---|
| Code Quality | 0.0% | 0.0% |
| High Alerts | 0 | 0 |
| Medium Alerts | 1 | 3 |
| Low Alerts | 7 | 4 |
| Error Instances | 50 | 390 |
| Performance | 12 min | 6 min and 25 s |
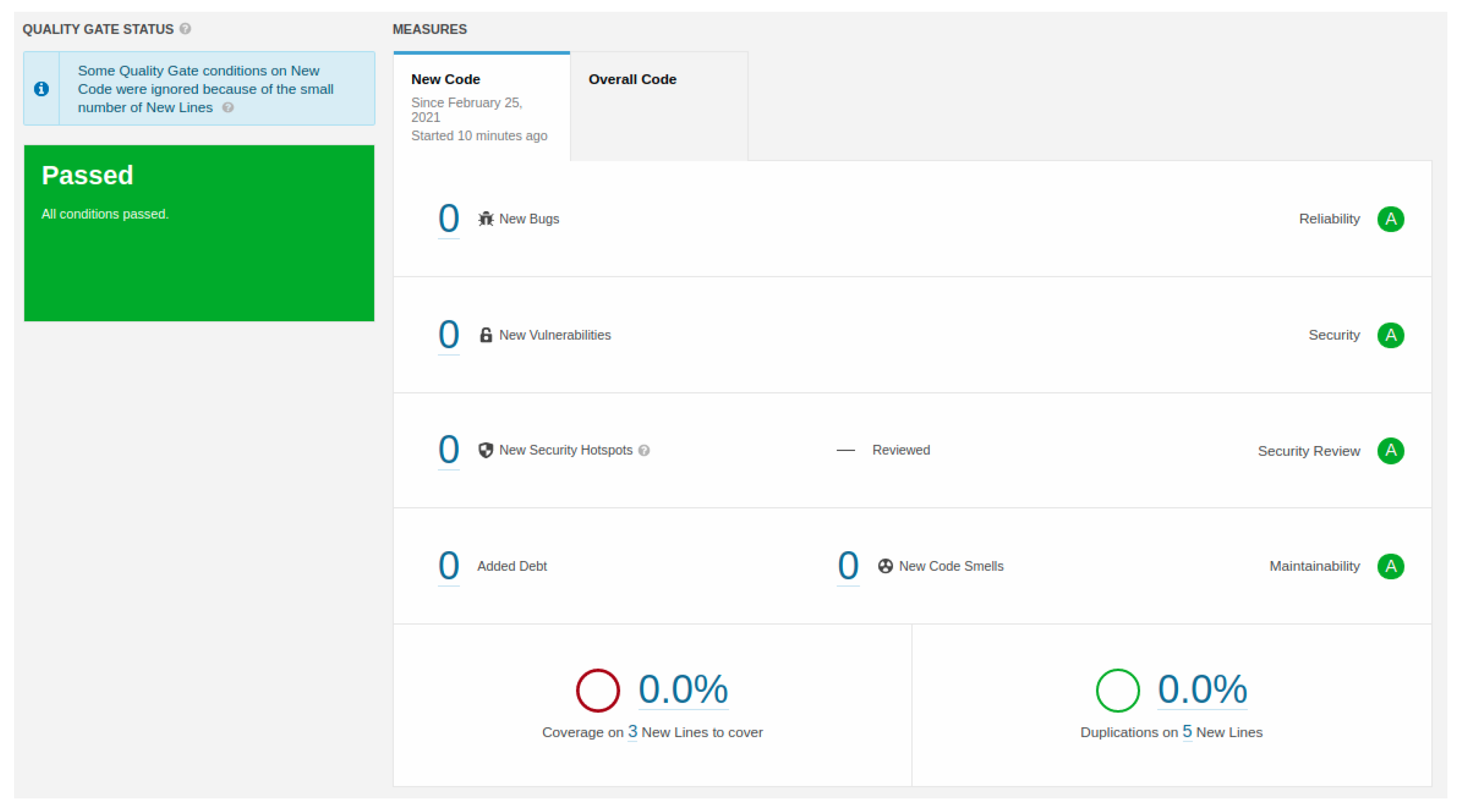
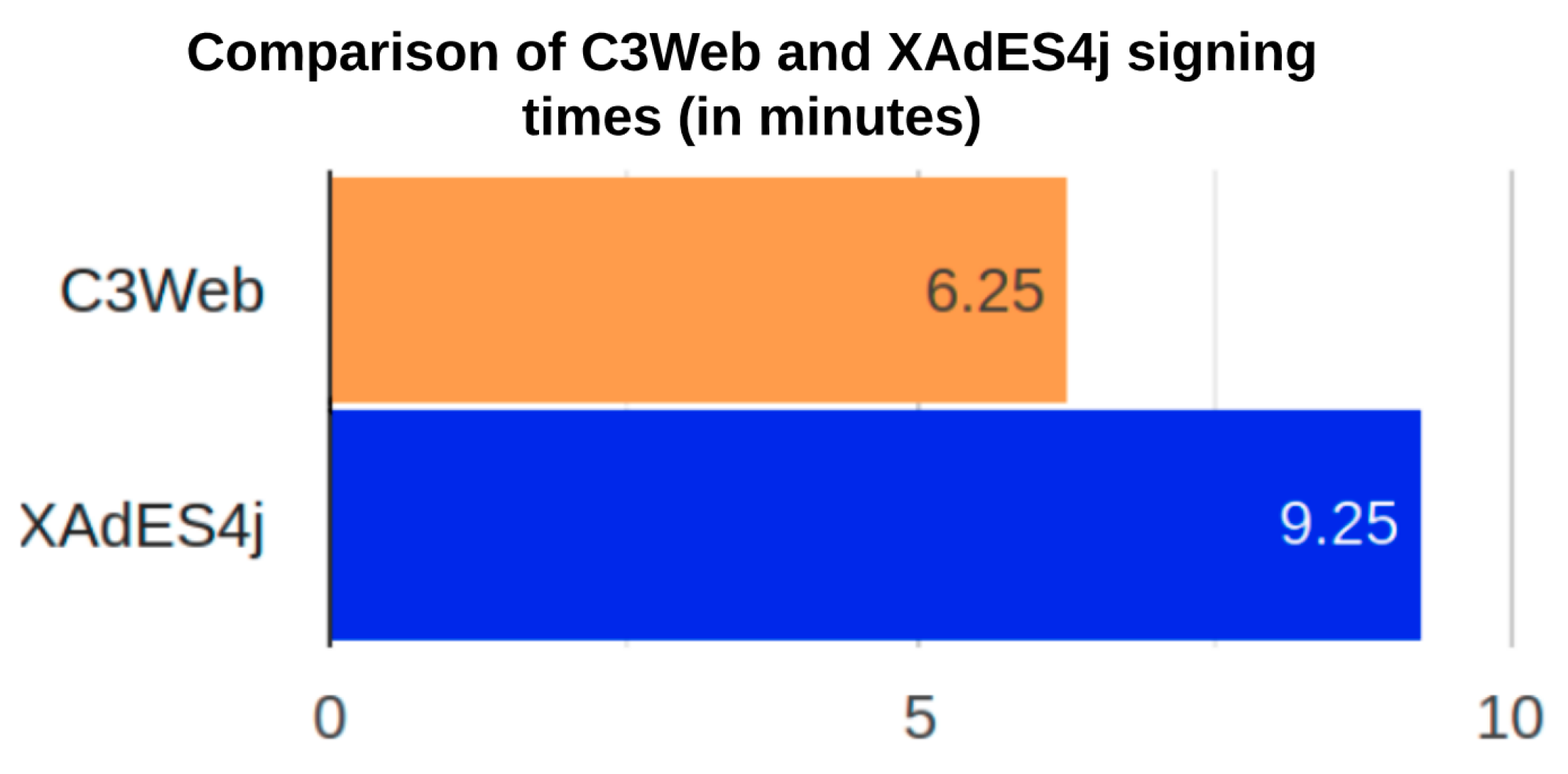
| Requirements | Expected Value | Value Obtained |
|---|---|---|
| Code Quality | 0.0% | 0.0% |
| High Alerts | 0 | 0 |
| Medium Alerts | 1 | 3 |
| Low Alerts | 3 | 4 |
| Error Instances | 50 | 8 |
| Performance 12 min | 9 min and 25 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ribeiro, R.C.; de Almeida, M.G.; Canedo, E.D. A Digital Signature Model Using XAdES Standard as a Rest Service. Information 2021, 12, 289. https://doi.org/10.3390/info12080289
Ribeiro RC, de Almeida MG, Canedo ED. A Digital Signature Model Using XAdES Standard as a Rest Service. Information. 2021; 12(8):289. https://doi.org/10.3390/info12080289
Chicago/Turabian StyleRibeiro, Renato Carauta, Murilo Góes de Almeida, and Edna Dias Canedo. 2021. "A Digital Signature Model Using XAdES Standard as a Rest Service" Information 12, no. 8: 289. https://doi.org/10.3390/info12080289
APA StyleRibeiro, R. C., de Almeida, M. G., & Canedo, E. D. (2021). A Digital Signature Model Using XAdES Standard as a Rest Service. Information, 12(8), 289. https://doi.org/10.3390/info12080289








