Visualisation of Control Software for Cyber-Physical Systems
Abstract
1. Introduction
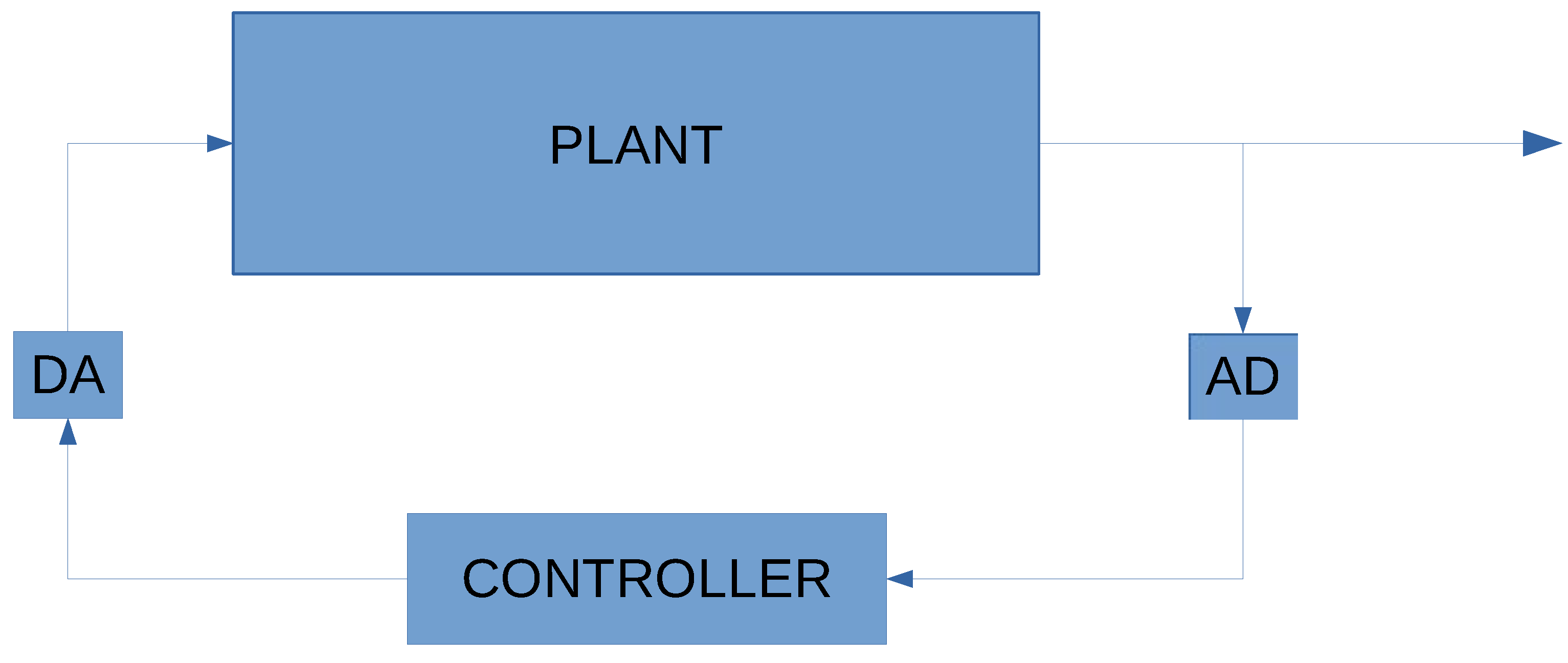
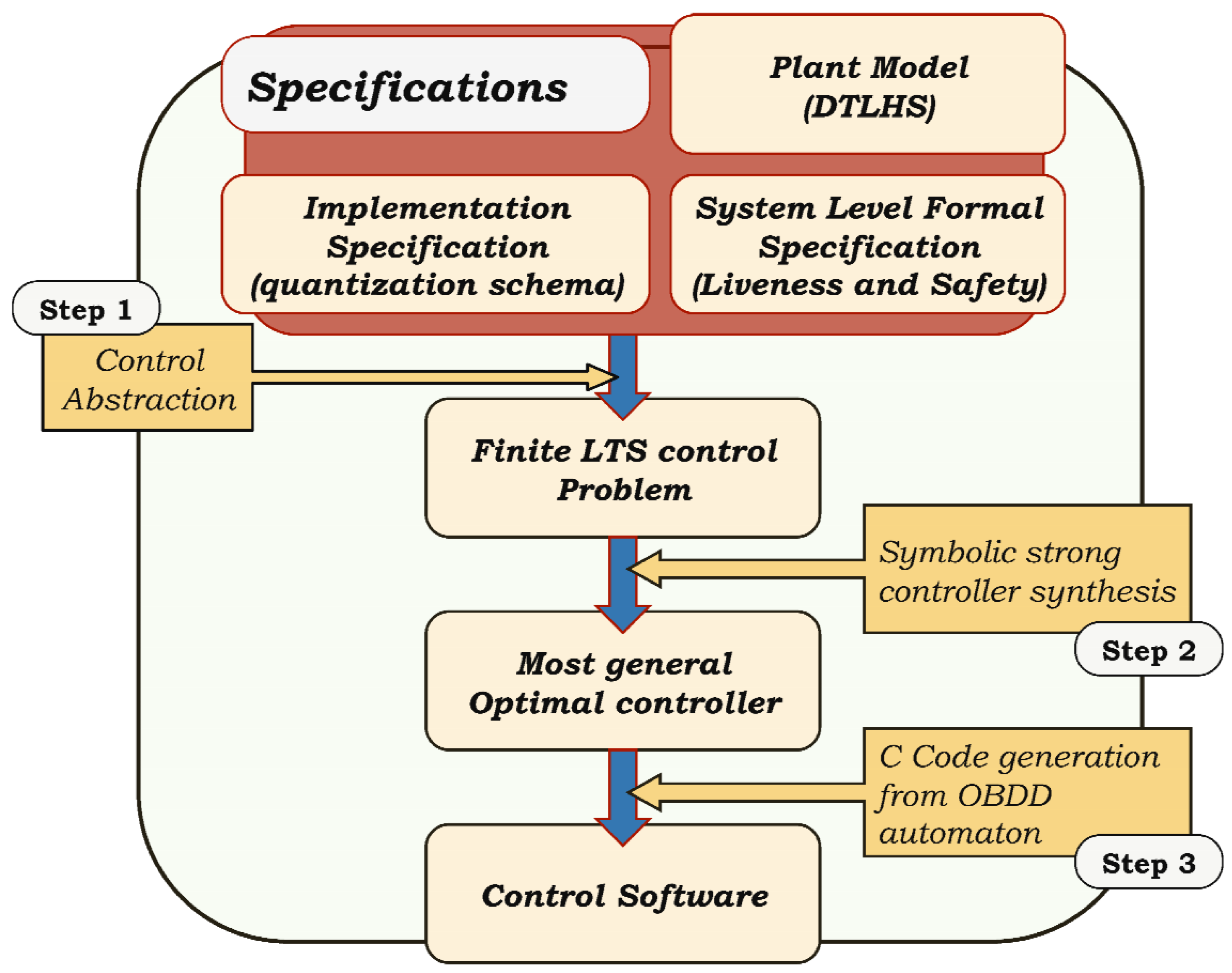
- A plant model, given as a Discrete Time Linear Hybrid System (DTLHS). Namely, such a model may be defined by continuous as well as discrete variables, provided that the dynamics is described by linear constraints;
- System level formal specifications, that describe functional requirements of the closed loop system (i.e., initial and goal regions);
- Implementation specifications, that describe non functional requirements of the control software, such as the number of bits used in the quantization process, the required worst case execution time, and so forth.
1.1. Our Main Contributions
- For OBDD-based (i.e., symbolic) formal verification [16,17], our methodology could be easily adapted to visualise, for example, the reachable state space, which is represented with OBDDs. This is also possible for some explicit model checkers such as SPIN, which may represent the reachable state space as an OBDD-like data structure [18].
- In system-level formal verification [19,20,21,22,23,24,25,26,27,28,29], a simulation campaign is used to check if a system is correct, by relying on a simulator of the system itself. Furthermore, a simulation campaign compactly represents a set of input (test) traces for the system under verification, in a way which resembles the compaction provided by OBDDs. Hence, our methodology could be used to visualise the distribution of the test traces, as well as their coverage w.r.t. the state space of the system to be verified.
- Statistical model checking [30,31] refers to a series of simulation-based techniques that can be used to determine if the probability that a system satisfies a given property is sufficiently high or not (or to actually compute an approximation of such probability). Statistical model checking can be used in many and very diverse areas, for example, biological systems [32,33,34,35,36,37], smart grids [38,39,40] and communication protocols [41]. In such context, our approach may be extended so as to visualise the probability of a given property, by colouring the state space of the system under verification. The same idea may be applied to probabilistic model checking (see, e.g., [42,43]).
1.2. Paper Outline
2. Basic Definitions
2.1. Predicates
2.2. OBDD Representation for Boolean Functions
- is the root of the DAG ;
- assigns to each vertex v either a variable in (if v is an internal node) or the unique terminal node (otherwise), so that implies ;
- the terminal node v s.t. has no children (i.e., the set is empty). In the following, by abusing notation, we will denote with the terminal node itself;
- each internal node has exactly two children (i.e., the set has exactly two elements);
- are partial functions which distinguish the two successors of v as the then-child and the else-child. That is, represents the case in which is true (then-child) and represents the case in which is false (else-child). Both are partial since they are not defined on the terminal node ;
- is a partial function assigning to each internal node v a boolean value, meaning that the edge is complemented. Function is partial since it is not defined on the terminal node ;
- on each path from an internal node to the terminal node , the variables labeling each internal node must follow the same ordering . That is, is a bijective function and for all s.t. and , it must hold that for all .
2.3. Most General Optimal Controllers
2.4. Discrete Time Linear Hybrid Systems
Controllers and COBDDs
3. Other Related Work
4. Automatic Visualization of Control Software
| Algorithm 1 Visualizing a controller. |
|
| Algorithm 2 Visualizing a controller: Gnuplot body. |
|
4.1. Input and Output
- A DTLHS plant model ;
- A quantisation for . Such quantisation specifies (i) how many bits are used to discretize variables in X and in U and (ii) the bounds of variables in X and U;
- A subset of plant state variables s.t. . Variables in are those to be shown in the axes of the final 2D picture. If , then ;
- A QFC solution K to a control problem involving , represented as a COBDD s.t. .
4.2. Algorithm Details
4.2.1. Function CreateGnuplotBody
5. Experimental Results
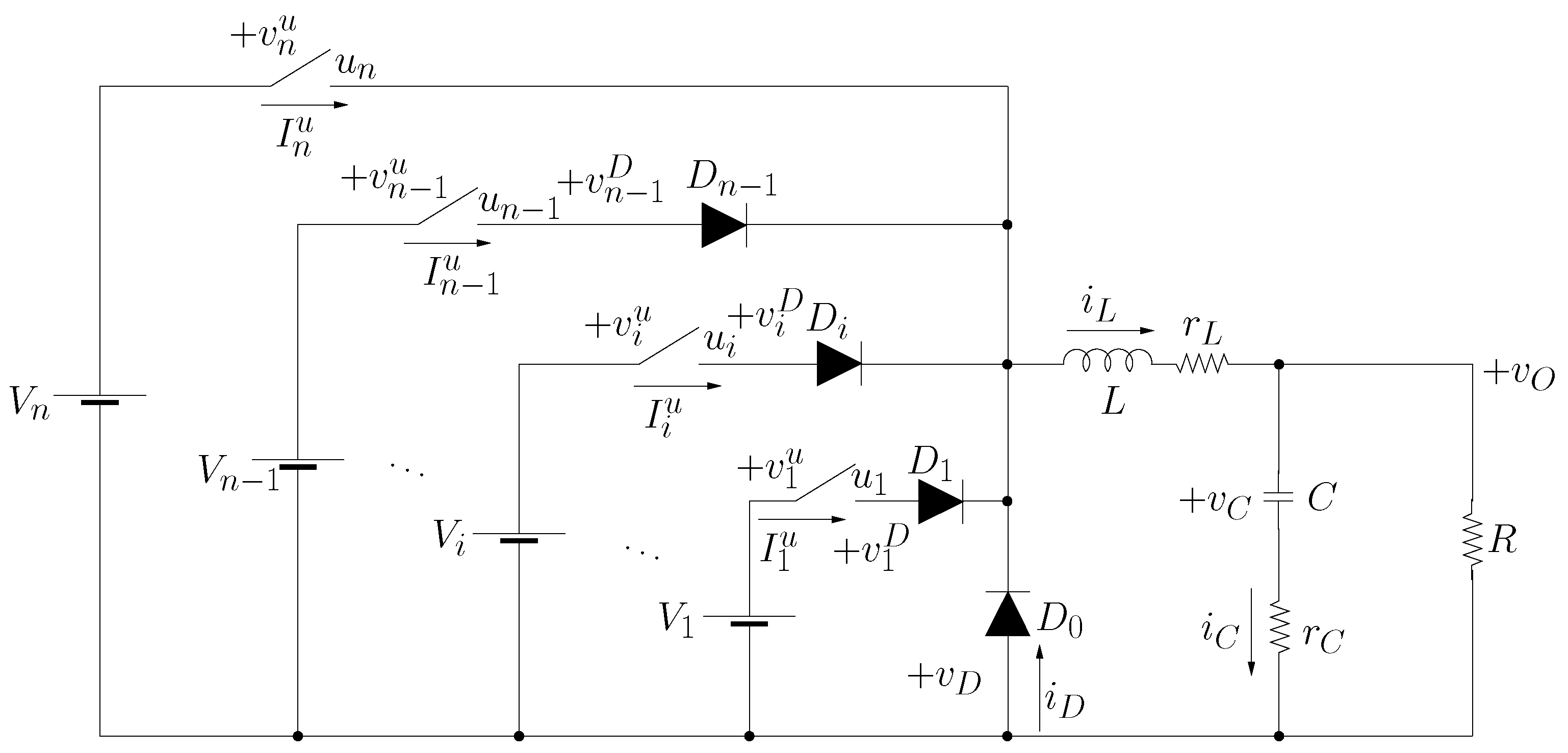
5.1. Experimental Settings: Case Study
5.2. Experimental Settings: Running KPS
5.3. KPS Performance
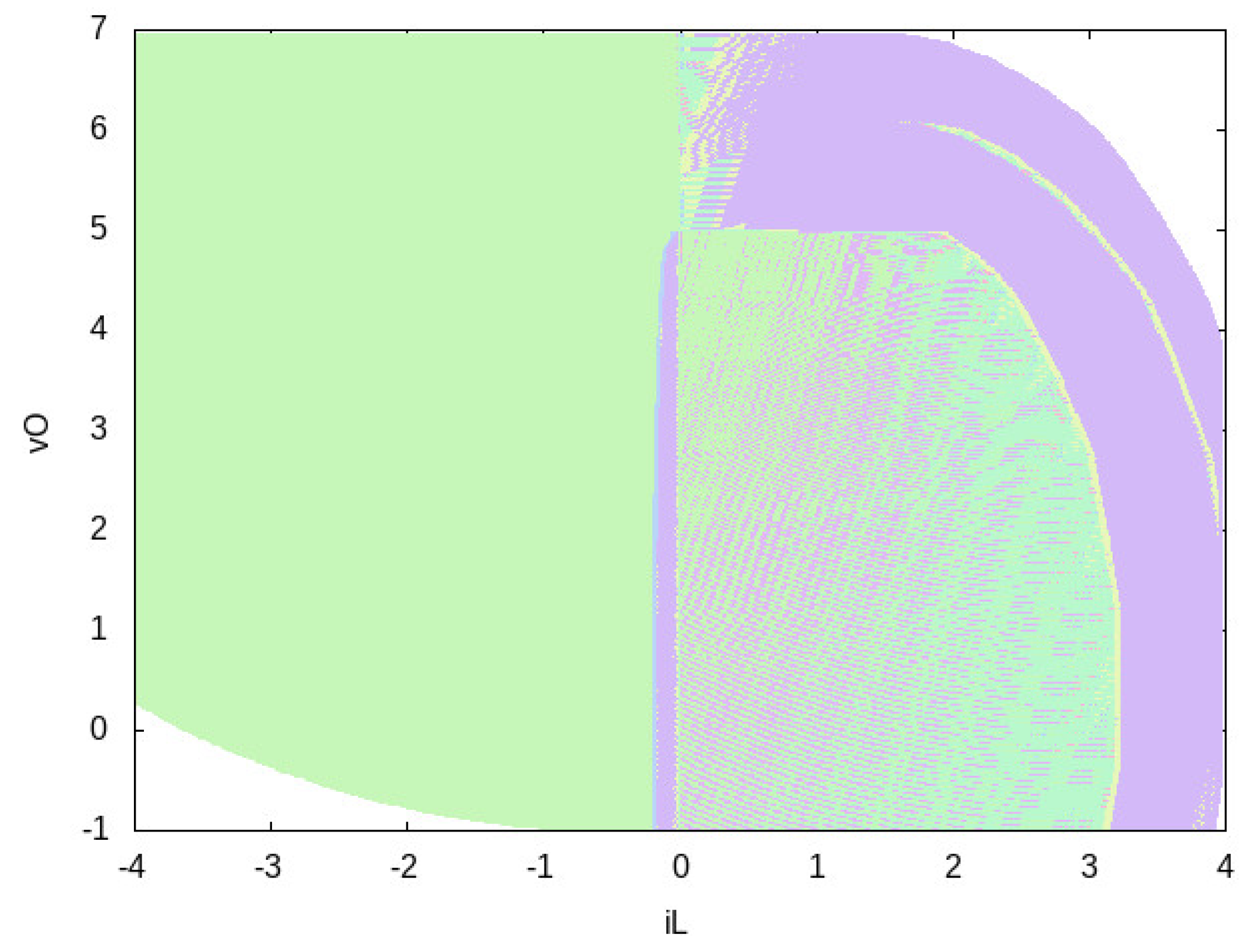
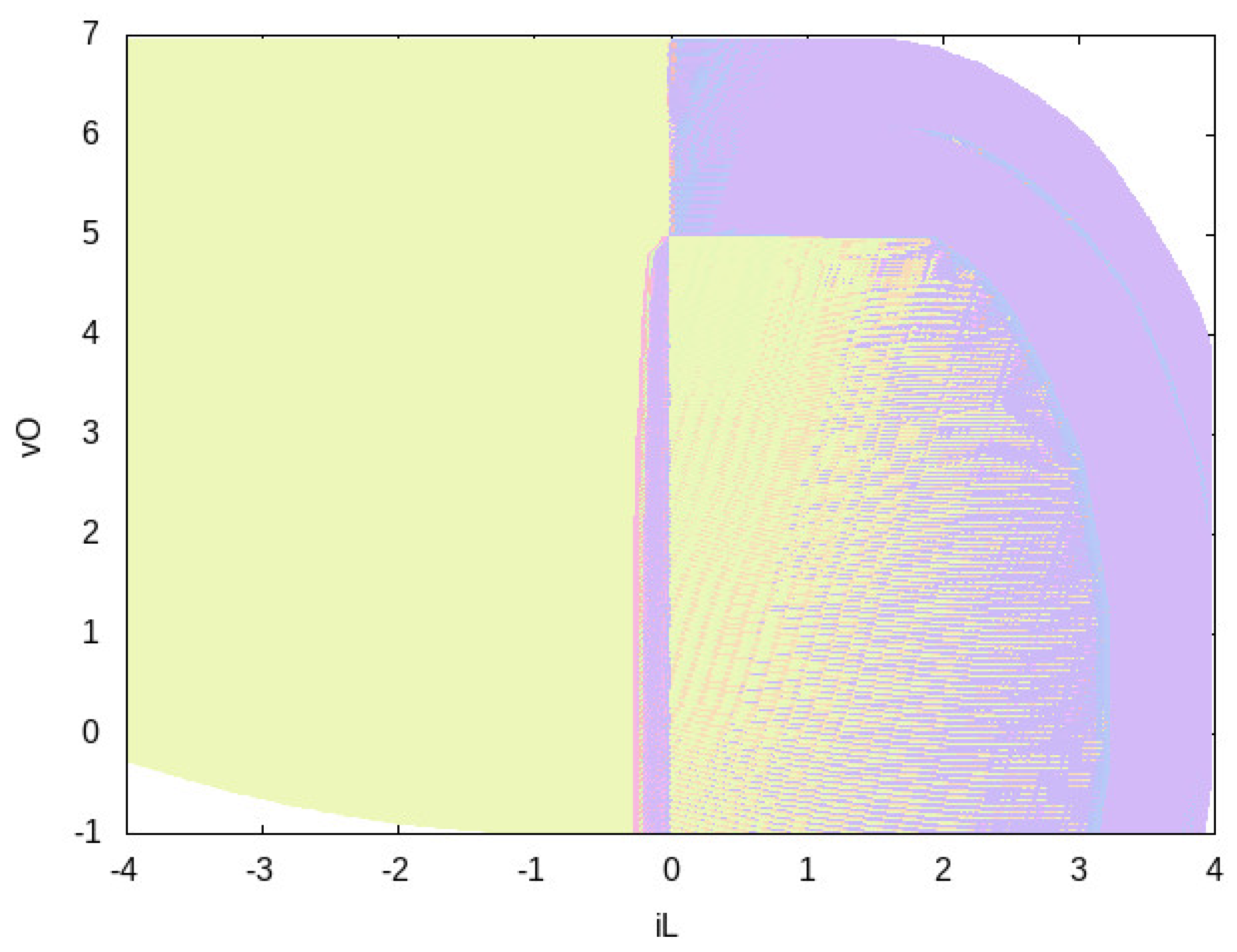
5.4. Controllers Qualitative Evaluation via Pictures
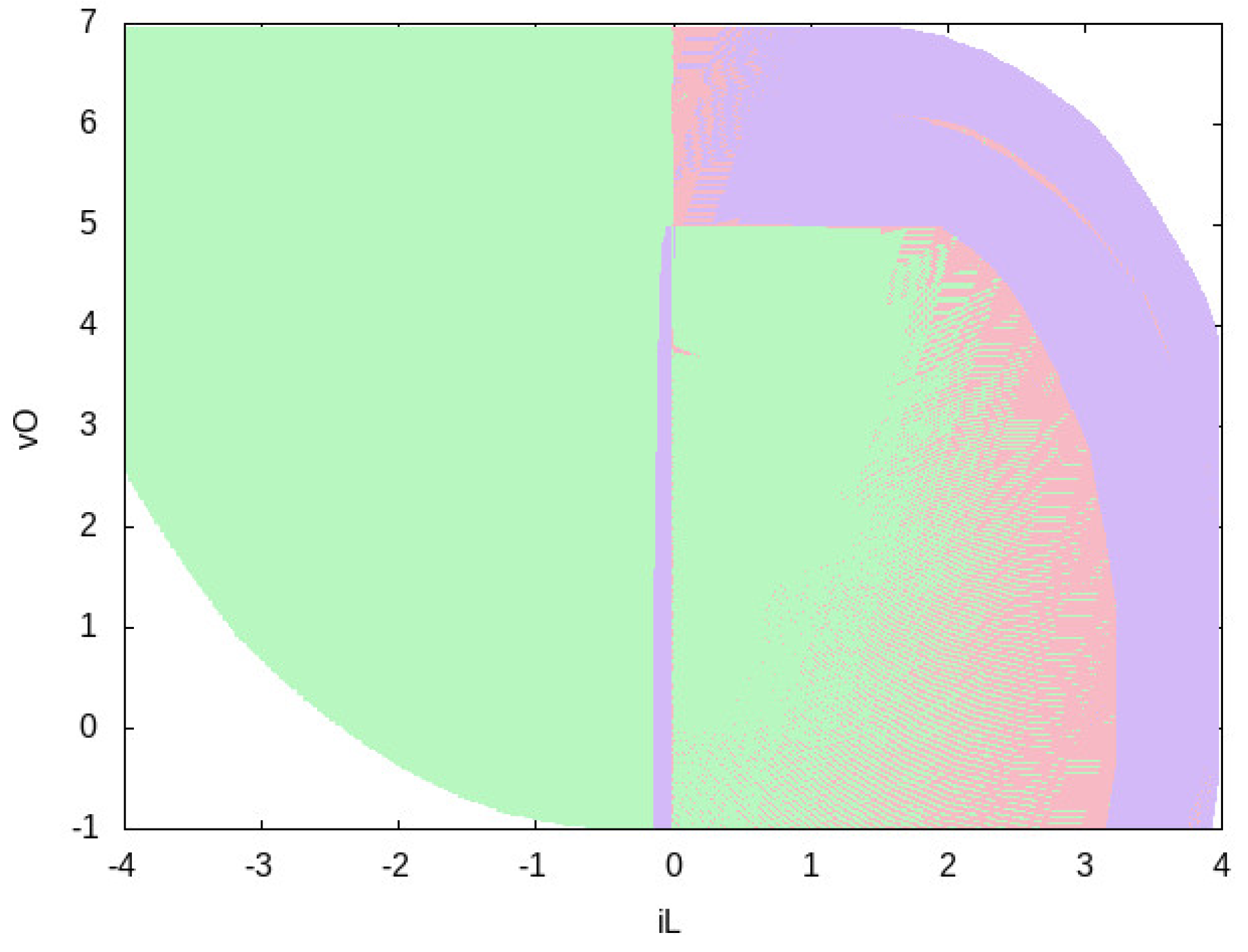
- Do cover a wide enough portion of the system state space? The answer is yes for all controllers , since the region for which any color is shown covers nearly all the system state space. Moreover, we may see that, increasing the number of actions (i.e., going from to ) the coverage increases.
- Do cover the most important portion of the system state space? Again, the answer is yes for all controllers . Namely, in the DC-DC buck converter case study the most important part is the starting point and the goal region (delimited by A and V). In all four cases, it is clear that such regions are covered.
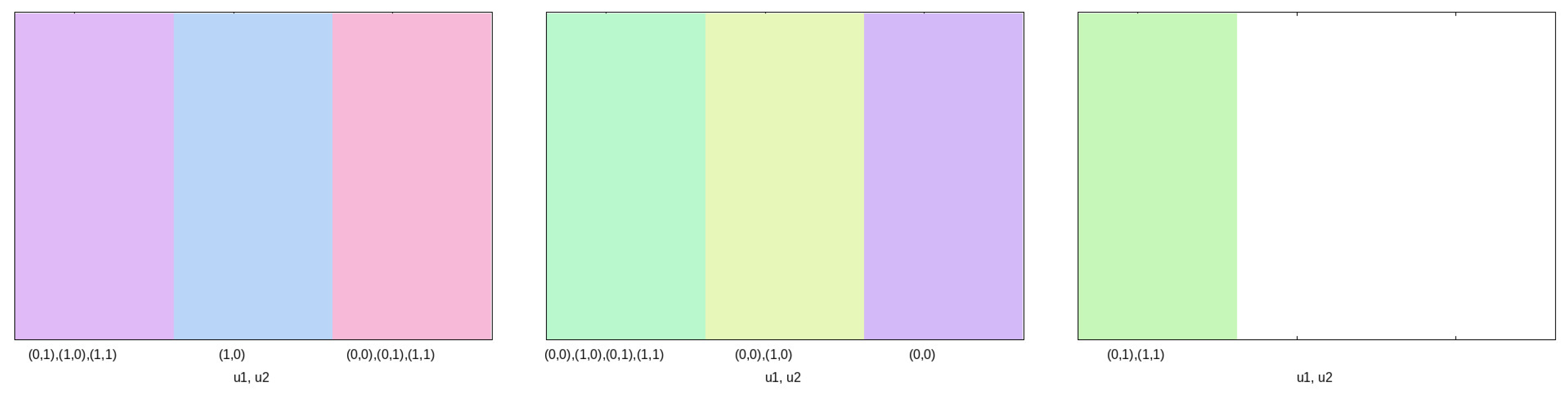
- Which actions are enabled by in a given portion of the system space? If we focus on the whole covered state space, we have the following. From Figure 5 we may immediately see that all possible actions sets are used by . On the other hand, from Figure 7 we immediately conclude that only 7 actions sets out of (excluding the empty actions set) are indeed enabled in . Note that, in order to retain readability, colors legend pictures always have at most 3 colors. If more than actions sets are used by the given controller, then pictures for colors legend are used. This results in 1 picture for and in 3 pictures for . For space reasons, we do not show colors legends for and . Namely, uses 25 actions set (out of 255), resulting in 9 files for colors legend, whilst uses 83 actions sets (out of 65,535), resulting in 28 files for colors legend.
- Is there an actions set which is used more than the other actions sets? We have that the most used actions sets are for and for . By considering the missing colors legend pictures, analogous results may be obtained for and .
- Which is the distribution of action sets on the state space? Let us focus, e.g., on Figure 4. We have a huge portion on the left part of the picture which is colored in green, which corresponds to action u1 = 1 (see Figure 5). This may be interepreted as follows: for negative values of (provided that is not too small w.r.t. ), the only action enabled by the controller is always to close the switch (see Figure 3). As a further example, if A and V, then there are some states for which u1 = 1 (switch closed, green color in Figure 5) and some other for which it is ok to perform any action (either close or open the switch is ok, pink color in Figure 5).
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AD | Analog-to-Digital |
| BLIF | Berkeley Logic Interchange Format |
| COBDD | Complemented edges OBDD |
| CUDD | Colorado University Decision Diagram |
| DA | Digital-to-Analog |
| DAG | Directed Acyclic Graph |
| DFS | Depth-First Search |
| DTLHS | Discrete Time Linear Hybrid System |
| EPS | Encapsulated Postscript |
| FDRI | Fault Detection, Isolation and Recovery |
| HSV | Hue Saturation Value |
| JPEG | Joint Photographic Experts Group |
| KPS | Kontroller Picture Synthesizer |
| LTS | Labeled Transition System |
| MGO | Most General Optimal controller |
| MILP | Mixed Integer Linear Programming |
| OBDD | Ordered Binary Decision Diagram |
| QFC | Quantized Feedback Control |
| QKS | Quantized feedback Kontrol Synthesizer |
| RGB | Red Green Blue |
| SBCS | Software Based Control Systems |
References
- Lee, E.A.; Seshia, S.A. Introduction to Embedded Systems, A Cyber-Physical Systems Approach; MIT Press: Cambridge, MA, USA, 2017. [Google Scholar]
- Bartocci, E.; Deshmukh, J.; Donzé, A.; Fainekos, G.; Maler, O.; Ničković, D.; Sankaranarayanan, S. Specification-based monitoring of cyber-physical systems: A survey on theory, tools and applications. In Lecture Notes in Computer Science (including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2018; pp. 135–175. [Google Scholar] [CrossRef]
- Gawand, H.L.; Bhattacharjee, A.; Roy, K. Online Monitoring of a Cyber Physical System Against Control Aware Cyber Attacks. Procedia Comput. Sci. 2015, 70, 238–244. [Google Scholar] [CrossRef]
- Henzinger, T.A.; Sifakis, J. The Embedded Systems Design Challenge. In Proceedings of the International Symposium on Formal Methods, Hamilton, ON, Canada, 21–27 August 2006; pp. 1–15. [Google Scholar]
- Henzinger, T.; Ho, P.H.; Wong-Toi, H. HyTech: A Model Checker for Hybrid Systems. STTT 1997, 1, 110–122. [Google Scholar] [CrossRef]
- Frehse, G. PHAVer: Algorithmic verification of hybrid systems past HyTech. Int. J. Softw. Tools Technol. Transf. 2008, 10, 263–279. [Google Scholar] [CrossRef]
- Wong-Toi, H. The synthesis of controllers for linear hybrid automata. In Proceedings of the CDC, San Diego, CA, USA, 10–12 December 1997; Volume 5, pp. 4607–4612. [Google Scholar] [CrossRef]
- Tomlin, C.; Lygeros, J.; Sastry, S. Computing Controllers for Nonlinear Hybrid Systems. In Proceedings of the HSCC, Berg en Dal, The Netherlands, 29–31 March 1999; pp. 238–255. [Google Scholar]
- Mazo, M.; Davitian, A.; Tabuada, P. PESSOA: A Tool for Embedded Controller Synthesis. In International Conference on Computer Aided Verification (CAV), Proceedings of the 22nd International Conference, CAV 2010, Edinburgh, UK, 15–19 July 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 566–569. [Google Scholar]
- Mari, F.; Melatti, I.; Salvo, I.; Tronci, E. Model Based Synthesis of Control Software from System Level Formal Specifications. ACM TOSEM 2014, 23, 1–42. [Google Scholar] [CrossRef]
- Alimguzhin, V.; Mari, F.; Melatti, I.; Salvo, I.; Tronci, E. A Map-Reduce Parallel Approach to Automatic Synthesis of Control Software. In Proceedings of the International SPIN Symposium on Model Checking of Software (SPIN 2013), Stony Brook, NY, USA, 8–9 July 2013; Springer: Berlin/Heidelberg, Germany, 2013; Volume 7976, pp. 43–60. [Google Scholar] [CrossRef]
- Janert, P.K. Gnuplot in Action: Understanding Data with Graphs; Manning Publications Co.: Greenwich, CT, USA, 2009. [Google Scholar]
- Clarke, E.M.; Grumberg, O.; Peled, D.A. Model Checking; The MIT Press: Cambridge, MA, USA, 1999. [Google Scholar]
- Sirjani, M.; Lee, E.A.; Khamespanah, E. Verification of Cyberphysical Systems. Mathematics 2020, 8, 1068. [Google Scholar] [CrossRef]
- Sirjani, M.; Lee, E.A.; Khamespanah, E. Model Checking Software in Cyberphysical Systems. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020; pp. 1017–1026. [Google Scholar] [CrossRef]
- Burch, J.R.; Clarke, E.M.; McMillan, K.L.; Dill, D.L.; Hwang, L.J. Symbolic model checking: 1020 states and beyond. Inf. Comput. 1992, 98, 142–170. [Google Scholar] [CrossRef]
- Cimatti, A.; Corvino, R.; Lazzaro, A.; Narasamdya, I.; Rizzo, T.; Roveri, M.; Sanseviero, A.; Tchaltsev, A. Formal Verification and Validation of ERTMS Industrial Railway Train Spacing System. In International Conference on Computer Aided Verification (CAV), Proceedings of the 24th International Conference, CAV 2012, Berkeley, CA, USA, 7–13 July 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 378–393. [Google Scholar]
- Holzmann, G.; Puri, A. A Minimized Automaton Representation of Reachable States. Int. J. Softw. Tools Technol. Transf. (STTT) 1999, 2, 270–278. [Google Scholar] [CrossRef][Green Version]
- Zuliani, P.; Platzer, A.; Clarke, E. Bayesian Statistical Model Checking with Application to Stateflow/Simulink Verification; Formal Methods in System Design; Springer: Berlin/Heidelberg, Germany, 2010; Volume 43, pp. 243–252. [Google Scholar] [CrossRef]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Merli, F.; Tronci, E. System Level Formal Verification via Model Checking Driven Simulation. In Proceedings of the CAV 2013, Saint Petersburg, Russia, 13–19 July 2013; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8044, pp. 296–312. [Google Scholar] [CrossRef]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Tronci, E. System Level Formal Verification via Distributed Multi-Core Hardware in the Loop Simulation. In Proceedings of the PDP 2014, Torino, Italy, 12–14 February 2014; pp. 734–742. [Google Scholar] [CrossRef]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Tronci, E. Anytime System Level Verification via Random Exhaustive Hardware In The Loop Simulation. In Proceedings of the DSD 2014, Verona, Italy, 27–29 August 2014; pp. 236–245. [Google Scholar]
- Camilli, M. Formal Verification Problems in a Big Data World: Towards a Mighty Synergy. In Companion Proceedings of the 36th International Conference on Software Engineering; ICSE Companion 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 638–641. [Google Scholar] [CrossRef]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Tronci, E. SyLVaaS: System Level Formal Verification as a Service. In Proceedings of the 23rd Euromicro International Conference on Parallel, Distributed and Network-Based Computing (PDP), Turku, Finland, 4–6 March 2015; pp. 476–483. [Google Scholar]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Tronci, E. Anytime System Level Verification via Parallel Random Exhaustive Hardware in the Loop Simulation. Microprocess Microsyst. 2016, 41, 12–28. [Google Scholar] [CrossRef][Green Version]
- Duggirala, P.S.; Mitra, S.; Viswanathan, M.; Potok, M. C2E2: A Verification Tool for Stateflow Models. In Tools and Algorithms for the Construction and Analysis of Systems; Baier, C., Tinelli, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 68–82. [Google Scholar]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Tronci, E. SyLVaaS: System Level Formal Verification as a Service. Fundam. Inform. 2016, 149, 101–132. [Google Scholar] [CrossRef]
- Zutshi, A.; Sankaranarayanan, S.; Deshmukh, J.V.; Jin, X. Symbolic-Numeric Reachability Analysis of Closed-Loop Control Software. In Proceedings of the 19th International Conference on Hybrid Systems: Computation and Control, Vienna, Austria, 12–14 April 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 135–144. [Google Scholar] [CrossRef]
- Mancini, T.; Mari, F.; Massini, A.; Melatti, I.; Salvo, I.; Tronci, E. On Minimising the Maximum Expected Verification Time. Inf. Proc. Lett. 2017, 122, 8–16. [Google Scholar] [CrossRef][Green Version]
- Grosu, R.; Smolka, S.A. Monte Carlo Model Checking. In Tools and Algorithms for the Construction and Analysis of Systems; Halbwachs, N., Zuck, L.D., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 271–286. [Google Scholar]
- Legay, A.; Lukina, A.; Traonouez, L.M.; Yang, J.; Smolka, S.A.; Grosu, R. Statistical Model Checking. In Computing and Software Science: State of the Art and Perspectives; Springer International Publishing: Cham, Switzerland, 2019; pp. 478–504. [Google Scholar] [CrossRef]
- Tronci, E.; Mancini, T.; Salvo, I.; Sinisi, S.; Mari, F.; Melatti, I.; Massini, A.; Davi’, F.; Dierkes, T.; Ehrig, R.; et al. Patient-Specific Models from Inter-Patient Biological Models and Clinical Records. In Proceedings of the FMCAD 2014, Lausanne, Switzerland, 21–24 October 2014; pp. 207–214. [Google Scholar] [CrossRef]
- Mancini, T.; Tronci, E.; Salvo, I.; Mari, F.; Massini, A.; Melatti, I. Computing Biological Model Parameters by Parallel Statistical Model Checking. In Proceedings of the IWBBIO 2015, Granada, Spain, 15–17 April 2015; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9044, pp. 542–554. [Google Scholar] [CrossRef]
- Rieger, T.R.; Allen, R.J.; Bystricky, L.; Chen, Y.; Colopy, G.W.; Cui, Y.; Gonzalez, A.; Liu, Y.; White, R.D.; Everett, R.A.; et al. Improving the Generation and Selection of Virtual Populations in Quantitative Systems Pharmacology Models. bioRxiv 2018. [Google Scholar] [CrossRef]
- Schmiester, L.; Schälte, Y.; Froehlich, F.; Hasenauer, J.; Weindl, D. Efficient parameterization of large-scale dynamic models based on relative measurements. Bioinformatics (Oxf. Engl.) 2019, 36, 594–602. [Google Scholar] [CrossRef]
- Sinisi, S.; Alimguzhin, V.; Mancini, T.; Tronci, E.; Leeners, B. Complete populations of virtual patients for in silico clinical trials. Bioinformatics 2020, 36, 5465–5472. [Google Scholar]
- Maggioli, F.; Mancini, T.; Tronci, E. SBML2Modelica: Integrating Biochemical Models within Open-Standard Simulation Ecosystems. Bioinformatics 2020, 36, 2165–2172. [Google Scholar] [CrossRef] [PubMed]
- Mancini, T.; Mari, F.; Melatti, I.; Salvo, I.; Tronci, E.; Gruber, J.; Hayes, B.; Prodanovic, M.; Elmegaard, L. Demand-Aware Price Policy Synthesis and Verification Services for Smart Grids. In Proceedings of the SmartGridComm 2014, Venice, Italy, 3–6 November 2014; pp. 794–799. [Google Scholar] [CrossRef]
- Lee, C.K.; Chaudhuri, N.R.; Chaudhuri, B.; Hui, S.Y.R. Droop Control of Distributed Electric Springs for Stabilizing Future Power Grid. IEEE Trans. Smart Grid 2013, 4, 1558–1566. [Google Scholar] [CrossRef]
- Mancini, T.; Mari, F.; Melatti, I.; Salvo, I.; Tronci, E.; Gruber, J.; Hayes, B.; Elmegaard, L. Parallel Statistical Model Checking for Safety Verification in Smart Grids. In Proceedings of the SmartGridComm 2018, Aalborg, Denmark, 29–31 October 2018. [Google Scholar] [CrossRef]
- Basu, A.; Bensalem, S.; Bozga, M.; Delahaye, B.; Legay, A.; Sifakis, E. Verification of an AFDX Infrastructure Using Simulations and Probabilities; Runtime Verification; Barringer, H., Falcone, Y., Finkbeiner, B., Havelund, K., Lee, I., Pace, G., Roşu, G., Sokolsky, O., Tillmann, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 330–344. [Google Scholar]
- Kwiatkowska, M.; Norman, G.; Parker, D. PRISM 4.0: Verification of Probabilistic Real-Time Systems; Gopalakrishnan, G., Qadeer, S., Eds.; Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2011; pp. 585–591. [Google Scholar]
- Norman, G.; Parker, D. Quantitative Verification: Formal Guarantees for Timeliness, Reliability and Performance; Leese, R., Melham, T., Eds.; Technical Report; The London Mathematical Society and the Smith Institute: Oxford, UK, 2014. [Google Scholar]
- Brace, K.S.; Rudell, R.L.; Bryant, R.E. Efficient Implementation of a BDD Package. In Proceedings of the 27th ACM/IEEE Design Automation Conference (DAC), Orlando, FL, USA, 24–28 June 1990; pp. 40–45. [Google Scholar]
- Minato, S.; Ishiura, N.; Yajima, S. Shared Binary Decision Diagram with Attributed Edges for Efficient Boolean function Manipulation. In Proceedings of the 27th ACM/IEEE Design Automation Conference (DAC), Orlando, FL, USA, 24–28 June 1990; pp. 52–57. [Google Scholar]
- CUDD Web Page. Available online: http://web.mit.edu/sage/export/tmp/y/usr/share/doc/polybori/cudd/cuddIntro.html (accessed on 21 April 2021).
- Cimatti, A.; Roveri, M.; Traverso, P. Strong Planning in Non-Deterministic Domains Via Model Checking. In Proceedings of the Fourth International Conference on Artificial Intelligence Planning SystemsJune (AIPS’98), Pittsburgh, PA, USA, 8–10 June 1998; pp. 36–43. [Google Scholar]
- Fu, M.; Xie, L. The sector bound approach to quantized feedback control. IEEE Trans. Autom. Control 2005, 50, 1698–1711. [Google Scholar] [CrossRef]
- Mari, F.; Melatti, I.; Salvo, I.; Tronci, E. Control Software Visualization. In Proceedings of the Second International Conference on Advanced Communications and Computation (INFOCOMP), Venice, Italy, 21–26 October 2012. [Google Scholar]
- Girard, A. Synthesis using approximately bisimilar abstractions: Time-optimal control problems. In Proceedings of the IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010; pp. 5893–5898. [Google Scholar] [CrossRef]
- Mazo, M.J.; Tabuada, P. Symbolic approximate time-optimal control. Syst. Control Lett. 2011, 60, 256–263. [Google Scholar] [CrossRef]
- Girard, A.; Pola, G.; Tabuada, P. Approximately Bisimilar Symbolic Models for Incrementally Stable Switched Systems. IEEE Trans. Autom. Control 2010, 55, 116–126. [Google Scholar] [CrossRef]
- De Gleizer, G.A.; Mazo, M., Jr. Towards Traffic Bisimulation of Linear Periodic Event-Triggered Controllers. IEEE Control Syst. Lett. 2020, 5, 25–30. [Google Scholar] [CrossRef]
- Zamani, M.; Mazo, M., Jr.; Khaled, M.; Abate, A. Symbolic abstractions of networked control systems. IEEE Trans. Control. Netw. Syst. 2017, 5, 1622–1634. [Google Scholar] [CrossRef]
- Kehrer, J.; Hauser, H. Visualization and Visual Analysis of Multifaceted Scientific Data: A Survey. IEEE Trans. Vis. Comput. Graph. 2013, 19, 495–513. [Google Scholar] [CrossRef]
- O’Donoghue, S.I.; Gavin, A.C.; Gehlenborg, N.; Goodsell, D.S.; Hériché, J.K.; Nielsen, C.B.; North, C.; Olson, A.J.; Procter, J.B.; Shattuck, D.W.; et al. Visualizing biological data—Now and in the future. Nat. Methods 2010, 7, S2–S4. [Google Scholar] [CrossRef]
- Won, J.H.; Jeon, Y.; Rosenberg, J.K.; Yoon, S.; Rubin, G.D.; Napel, S. Uncluttered Single-Image Visualization of Vascular Structures Using GPU and Integer Programming. IEEE Trans. Vis. Comput. Graph. 2013, 19, 81–93. [Google Scholar] [CrossRef]
- O’Connor, S.; Waite, M.; Duce, D.; O’Donnell, A.; Ronquillo, C. Data visualization in health care: The Florence effect. J. Adv. Nurs. 2020, 76, 1488–1490. [Google Scholar] [CrossRef] [PubMed]
- Smith, C.M.; Kozlakidis, Z.; Frampton, D.; Nastouli, E.; Coen, P.G.; Pillay, D.; Hayward, A. Development of a novel application for visualising infectious diseases in hospital settings. Lancet 2017, 390, S84. [Google Scholar] [CrossRef]
- Linsen, L.; Hagen, H.; Hamann, B. Visualization in Medicine and Life Sciences; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Wiemker, R.; Klinder, T.; Bergtholdt, M.; Meetz, K.; Carlsen, I.C.; Bulow, T. A Radial Structure Tensor and Its Use for Shape-Encoding Medical Visualization of Tubular and Nodular Structures. IEEE Trans. Vis. Comput. Graph. 2013, 19, 353–366. [Google Scholar] [CrossRef] [PubMed]
- Frey, S.; Sadlo, F.; Ertl, T. Visualization of Temporal Similarity in Field Data. IEEE Trans. Vis. Comput. Graph. 2012, 18, 2023–2032. [Google Scholar] [CrossRef] [PubMed]
- Ferstl, F.; Kanzler, M.; Rautenhaus, M.; Westermann, R. Time-Hierarchical Clustering and Visualization of Weather Forecast Ensembles. IEEE Trans. Vis. Comput. Graph. 2017, 23, 831–840. [Google Scholar] [CrossRef]
- Dinkla, K.; Strobelt, H.; Genest, B.; Reiling, S.; Borowsky, M.; Pfister, H. Screenit: Visual Analysis of Cellular Screens. IEEE Trans. Vis. Comput. Graph. 2017, 23, 591–600. [Google Scholar] [CrossRef]
- Liu, D.; Weng, D.; Li, Y.; Bao, J.; Zheng, Y.; Qu, H.; Wu, Y. SmartAdP: Visual Analytics of Large-scale Taxi Trajectories for Selecting Billboard Locations. IEEE Trans. Vis. Comput. Graph. 2017, 23, 1–10. [Google Scholar] [CrossRef]
- Campadelli, P.; Posenato, R.; Schettini, R. An algorithm for the selection of high-contrast color sets. Color Res. Appl. 1999, 24, 132–138. [Google Scholar] [CrossRef]
- Carter, R.C.; Carter, E.C. High-contrast sets of colors. Appl. Opt. 1982, 21, 2936–2939. [Google Scholar] [CrossRef] [PubMed]
- Joblove, G.H.; Greenberg, D. Color Spaces for Computer Graphics. In Proceedings of the 5th Annual Conference on Computer Graphics and Interactive Techniques, Atlanta, GA, USA, 23–25 August 1978; Association for Computing Machinery: New York, NY, USA, 1978; pp. 20–25. [Google Scholar] [CrossRef]
- Agoston, M.K. Computer Graphics and Geometric Modeling: Implementation and Algorithms; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar]
- Rodriguez, M.; Fernandez-Miaja, P.; Rodriguez, A.; Sebastian, J. A Multiple-Input Digitally Controlled Buck Converter for Envelope Tracking Applications in Radiofrequency Power Amplifiers. IEEE Trans. Pow. El. 2010, 25, 369–381. [Google Scholar] [CrossRef]
- So, W.C.; Tse, C.; Lee, Y.S. Development of a fuzzy logic controller for DC/DC converters: Design, computer simulation, and experimental evaluation. IEEE Trans. Power Electron. 1996, 11, 24–32. [Google Scholar] [CrossRef]
- Kim, W.; Gupta, M.S.; Wei, G.Y.; Brooks, D.M. Enabling On-Chip Switching Regulators for Multi-Core Processors Using Current Staggering. Available online: https://www.semanticscholar.org/paper/Enabling-On-Chip-Switching-Regulators-for-using-Kim-Gupta/7dc7fbaeb3e1f85e1e9738345c22bc4c4abcd8f5 (accessed on 21 April 2021).


| a | CPU(P) | CPU(G) | |||
|---|---|---|---|---|---|
| 1 | 9.15e+00 | 3.25e+02 | 6.17e+03 | 2.46e+01 | 5.19e+03 |
| 2 | 1.00e+01 | 1.47e+03 | 1.29e+04 | 2.91e+01 | 1.09e+04 |
| 3 | 1.06e+01 | 2.43e+03 | 1.67e+04 | 2.91e+01 | 1.39e+04 |
| 4 | 1.10e+01 | 3.58e+03 | 2.02e+04 | 3.16e+01 | 1.68e+04 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Melatti, I.; Mari, F.; Salvo, I.; Tronci, E. Visualisation of Control Software for Cyber-Physical Systems. Information 2021, 12, 178. https://doi.org/10.3390/info12050178
Melatti I, Mari F, Salvo I, Tronci E. Visualisation of Control Software for Cyber-Physical Systems. Information. 2021; 12(5):178. https://doi.org/10.3390/info12050178
Chicago/Turabian StyleMelatti, Igor, Federico Mari, Ivano Salvo, and Enrico Tronci. 2021. "Visualisation of Control Software for Cyber-Physical Systems" Information 12, no. 5: 178. https://doi.org/10.3390/info12050178
APA StyleMelatti, I., Mari, F., Salvo, I., & Tronci, E. (2021). Visualisation of Control Software for Cyber-Physical Systems. Information, 12(5), 178. https://doi.org/10.3390/info12050178








