Supply Chain Disruption Risk Management with Blockchain: A Dynamic Literature Review
Abstract
1. Introduction
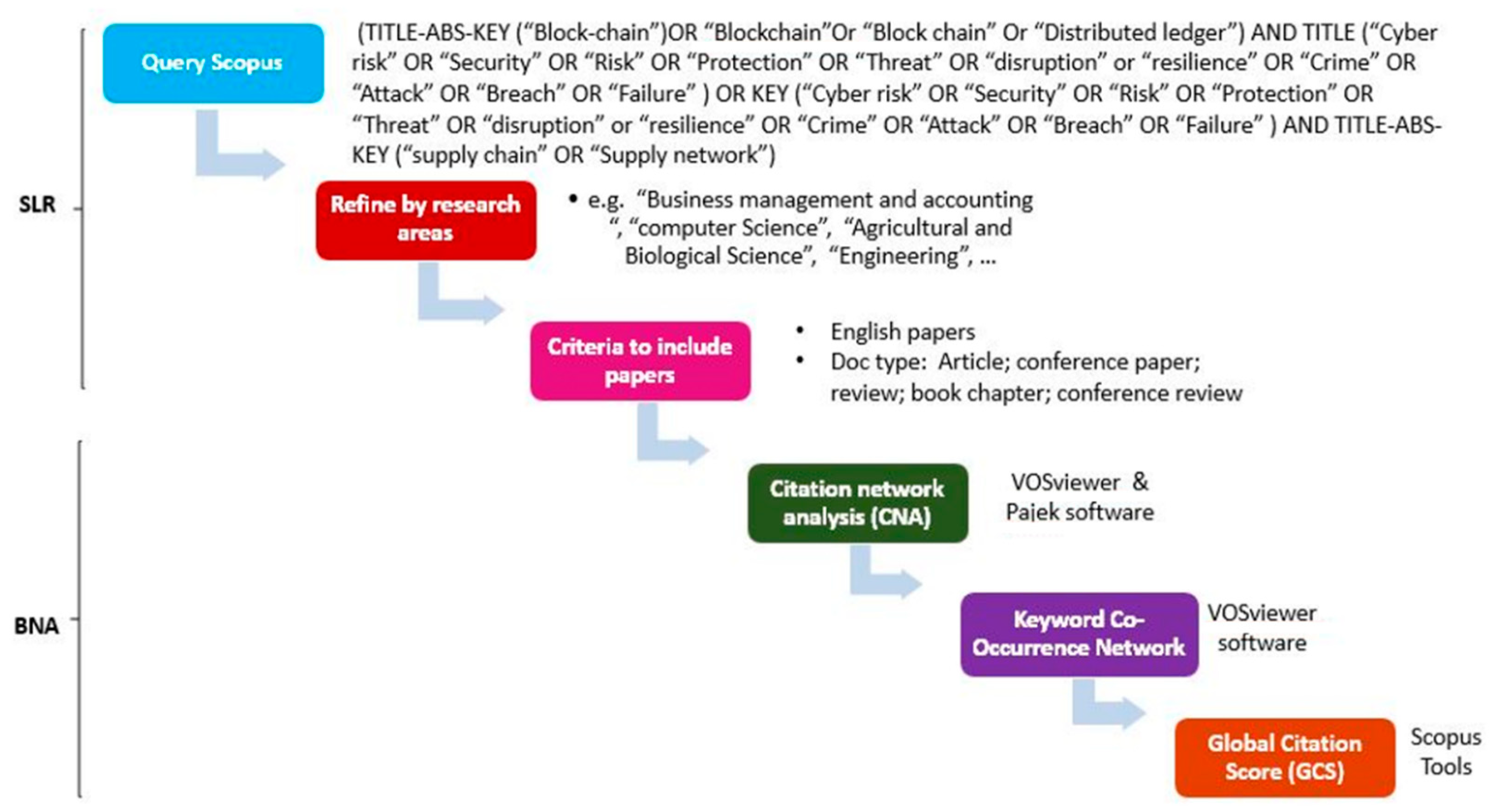
2. Materials and Methods
3. First Phase of SLNA Methodology: SLR
3.1. Scope of the Analysis
- RQ1: What are the latest blockchain applications focused on disruption risk management?
- RQ2: How is blockchain solutions used to identify potential disruption risks?
3.2. Locating Studies
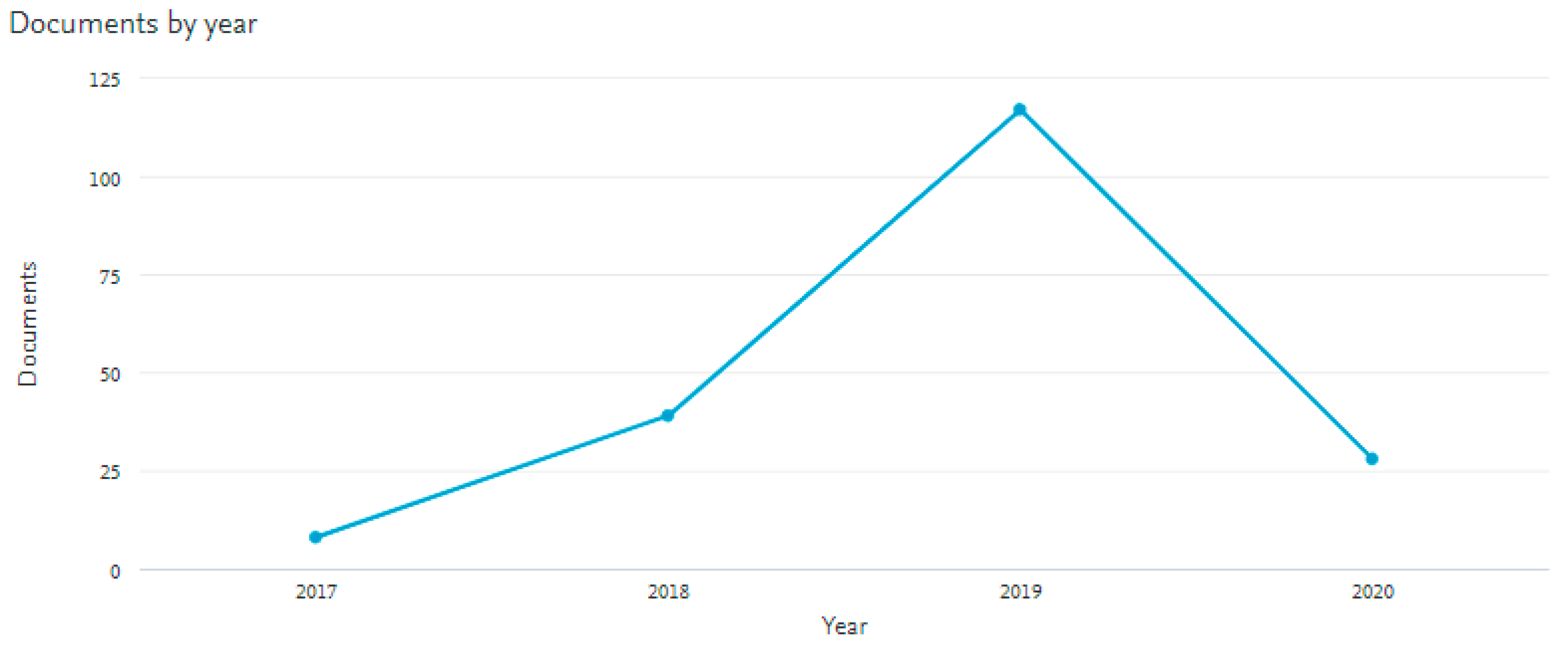
3.3. Study Selection and Evaluation
4. Second Phase of SLNA Methodology: BNA
5. Results
5.1. Citation Network Analysis (CNA)
5.1.1. The Biggest Connected Component
5.1.2. The Louvain Communities’ Analysis
Community A—Disruption Risk Management by Blockchain
Community C—A Digital Record of Every Transaction and Interaction
Community D—Integration of Blockchain with IoT to Solve Privacy and Security Vulnerabilities
Community E—Transparency and Traceability in Information Exchange by Blockchain Technology
Community F—Anti-Counterfeiting by Blockchain
Community G—Information Privacy by Blockchain
Community H—Safety and Security Aspects of the Blockchain
5.1.3. Main Path Analysis
5.1.4. General Comments on the Connected Components’ Analyses
5.2. Global Citation Score Analysis
5.3. Co-Occurrence Analysis of Author Keywords
5.3.1. Cluster 1: Digitalization for Improved Supply Chain Resilience
5.3.2. Cluster 2: Employing Blockchain Technology with Smart Contracts in Supply Chain Management
5.3.3. Cluster 3: Traceability Database Systems to Ensure Food Safety and Security
5.3.4. Cluster 4: Blockchain’s Benefits in Strengthening Cybersecurity and Cryptography
5.3.5. Cluster 5: Privacy and Security Challenges and Blockchain Solutions
5.3.6. Cluster 6: Security of Smart Contracts in Ethereum Platforms
5.3.7. Cluster 7: Monitoring Counterfeited Products in the Supply Chain
6. Discussion of Findings and Future Research Directions
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Chen, T.M.; Abu-Nimeh, S. Lessons from Stuxnet. Computer 2011. [Google Scholar] [CrossRef]
- Boyes, H. Cybersecurity and Cyber-Resilient Supply Chains. Technol. Innov. Manag. Rev. 2015. [Google Scholar] [CrossRef]
- Deloitte. The Future of Cyber Survey 2019 Cyber Everywhere. Succeed Anywhere; Deloitte: London, UK, 2019; pp. 1–32. [Google Scholar]
- Raab, M.; Griffin-Cryan, B. Digital Transformation of Supply Chains: Creating Value—When Digital Meets Physical; Capgemini Consulting: Paris, France, 2011. [Google Scholar]
- Aceto, B. Blockchain e Dintorini. 2019. Retrieved 22 May 2019. Available online: http://tendenzeonline.info/articoli/2019/05/08/blockchain-edintorini (accessed on 5 February 2021).
- Kshetri, N. Blockchain’s roles in strengthening cybersecurity and protecting privacy. Telecommun. Policy 2017, 41, 1027–1038. [Google Scholar] [CrossRef]
- Swan, M. Climate Change 2013—The Physical Science Basis. In Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Newton, MA, USA, 2015. [Google Scholar] [CrossRef]
- Ghadge, A.; Weiß, M.; Caldwell, N.D.; Wilding, R. Managing cyber risk in supply chains: A review and research agenda. Supply Chain Manag. 2019. [Google Scholar] [CrossRef]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2019. [Google Scholar] [CrossRef]
- Strozzi, F.; Colicchia, C.; Creazza, A.; Noè, C. Literature review on the “Smart Factory” concept using bibliometric tools. Int. J. Prod. Res. 2017, 55, 6572–6591. [Google Scholar] [CrossRef]
- Zhao, G.; Liu, S.; Lopez, C.; Lu, H.; Elgueta, S.; Chen, H.; Boshkoska, B.M. Blockchain technology in agri-food value chain management: A synthesis of applications, challenges and future research directions. Comput. Ind. 2019, 109, 83–99. [Google Scholar] [CrossRef]
- Etemadi, N.; Borbon, Y.G.; Strozzi, F. Blockchain technology for cybersecurity applications in the food supply chain: A systematic literature review. In Proceedings of the XXIV Summer School “Francesco Turco”—Industrial Systems Engineering, Bergamo, Italy, 9–11 September 2020. [Google Scholar]
- Denyer, D.; Tranfield, D. Producing a Systematic Review. In The SAGE Handbook of Organizational Research Methods; 2009; Available online: https://psycnet.apa.org/record/2010-00924-039 (accessed on 5 February 2021).
- Van Eck, N.J.; Waltman, L. How to normalize cooccurrence data? An analysis of some well-known similarity measures. J. Am. Soc. Inf. Sci. Technol. 2009. [Google Scholar] [CrossRef]
- De Nooy, W.; Mrvar, A.; Batagelj, V. Exploratory Social Network Analysis with Pajek. Connections 2011. [Google Scholar] [CrossRef]
- Colicchia, C.; Strozzi, F. Supply chain risk management: A new methodology for a systematic literature review. Supply Chain Manag. 2012. [Google Scholar] [CrossRef]
- Falagas, M.E.; Pitsouni, E.I.; Malietzis, G.A.; Pappas, G. Comparison of PubMed, Scopus, Web of Science, and Google Scholar: Strengths and weaknesses. FASEB J. 2008. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 5 February 2021).
- Kamada, T.; Kawai, S. An algorithm for drawing general undirected graphs. Inf. Process. Lett. 1989. [Google Scholar] [CrossRef]
- Blondel, V.D.; Guillaume, J.L.; Lambiotte, R.; Lefebvre, E. Fast unfolding of communities in large networks. J. Stat. Mech. Theory Exp. 2008. [Google Scholar] [CrossRef]
- Lucio-Arias, D.; Leydesdorff, L. Main-path analysis and path-dependent transitions in HistCiteTM-based historiograms. J. Am. Soc. Inf. Sci. Technol. 2008. [Google Scholar] [CrossRef]
- Liu, J.S.; Lu, L.Y.Y. An Integrated Approach for Main Path Analysis: Development of the Hirsch Index as an Example. J. Am. Soc. Inf. Sci. Technol. 2012, 63, 528–542. [Google Scholar] [CrossRef]
- Ivanov, D.; Dolgui, A.; Das, A.; Sokolov, B. Digital Supply Chain Twins: Managing the Ripple Effect, Resilience, and Disruption Risks by Data-Driven Optimization, Simulation, and Visibility. Int. Ser. Oper. Res. Manag. Sci. 2019. [Google Scholar] [CrossRef]
- Ivanov, D. Revealing interfaces of supply chain resilience and sustainability: A simulation study. Int. J. Prod. Res. 2018, 56, 3507–3523. [Google Scholar] [CrossRef]
- Ivanov, D.; Dolgui, A.; Sokolov, B. The impact of digital technology and Industry 4.0 on the ripple effect and supply chain risk analytics. Int. J. Prod. Res. 2019. [Google Scholar] [CrossRef]
- Manupati, V.K.; Schoenherr, T.; Ramkumar, M.; Wagner, S.M.; Pabba, S.K.; Inder Raj Singh, R. A blockchain-based approach for a multi-echelon sustainable supply chain. Int. J. Prod. Res. 2020. [Google Scholar] [CrossRef]
- Dubey, R.; Gunasekaran, A.; Bryde, D.J.; Dwivedi, Y.K.; Papadopoulos, T. Blockchain technology for enhancing swift-trust, collaboration and resilience within a humanitarian supply chain setting. Int. J. Prod. Res. 2020, 58, 3381–3398. [Google Scholar] [CrossRef]
- Kshetri, N. Can Blockchain Strengthen the Internet of Things? IT Prof. 2017. [Google Scholar] [CrossRef]
- Cui, Y.; Idota, H. Improving supply chain resilience with establishing a decentralized information sharing mechanism. ACM Int. Conf. Proc. Ser. 2018. [Google Scholar] [CrossRef]
- Agrell, P.J.; Lindroth, R.; Norrman, A. Risk, information and incentives in telecom supply chains. Int. J. Prod. Econ. 2004. [Google Scholar] [CrossRef]
- Gao, Z.; Xu, L.; Chen, L.; Zhao, X.; Lu, Y.; Shi, W. CoC: A Unified Distributed Ledger Based Supply Chain Management System. J. Comput. Sci. Technol. 2018. [Google Scholar] [CrossRef]
- Xiong, F.; Xiao, R.; Ren, W.; Zheng, R.; Jiang, J. A key protection scheme based on secret sharing for blockchain-based construction supply chain system. IEEE Access 2019. [Google Scholar] [CrossRef]
- Kim, H.Y.; Suh, T.; Xu, L.; Shi, W. FPGA based decentralized ledger for enterprise applications. In Proceedings of the ICBC 2019—IEEE International Conference on Blockchain and Cryptocurrency 2019, Seoul, Korea, 14–17 May 2019. [Google Scholar] [CrossRef]
- Zhang, H.; Nakamura, T.; Sakurai, K. Security and trust issues on digital supply chain. In Proceedings of the IEEE 17th International Conference on Dependable, Autonomic and Secure Computing, IEEE 17th International Conference on Pervasive Intelligence and Computing, IEEE 5th International Conference on Cloud and Big Data Computing, 4th Cyber Scienc, Fukuoka, Japan, 5–8 August 2019. [Google Scholar] [CrossRef]
- Choi, T.M. Blockchain-technology-supported platforms for diamond authentication and certification in luxury supply chains. Transp. Res. Part E Logist. Transp. Rev. 2019. [Google Scholar] [CrossRef]
- Min, H. Blockchain technology for enhancing supply chain resilience. Bus. Horiz. 2019, 62, 35–45. [Google Scholar] [CrossRef]
- Choi, T.M.; Wen, X.; Sun, X.; Chung, S.H. The mean-variance approach for global supply chain risk analysis with air logistics in the blockchain technology era. Transp. Res. Part E Logist. Transp. Rev. 2019. [Google Scholar] [CrossRef]
- Cai, S.; Xu, M.; Zhang, L. Automatic information disclosure with value chains based on blockchain technology. In Proceedings of the 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference, ITAIC, Chongqing, China, 24–26 May 2019. [Google Scholar] [CrossRef]
- Zhai, S.; Yang, Y.; Li, J.; Qiu, C.; Zhao, J. Research on the Application of Cryptography on the Blockchain. J. Phys. Conf. Ser. 2019, 1168. [Google Scholar] [CrossRef]
- Jiang, N.; Wang, W.; Wu, J.; Wang, J. Traceable Method for Personal Information Registration Based on Blockchain. IEEE Access 2020, 8, 52700–52712. [Google Scholar] [CrossRef]
- Choi, T.M.; Feng, L.; Li, R. Information disclosure structure in supply chains with rental service platforms in the blockchain technology era. Int. J. Prod. Econ. 2020. [Google Scholar] [CrossRef]
- Montecchi, M.; Plangger, K.; Etter, M. It’s real, trust me! Establishing supply chain provenance using blockchain. Bus. Horiz. 2019. [Google Scholar] [CrossRef]
- Feng, H.; Wang, X.; Duan, Y.; Zhang, J.; Zhang, X. Applying blockchain technology to improve agri-food traceability: A review of development methods, benefits and challenges. J. Clean. Prod. 2020. [Google Scholar] [CrossRef]
- Azzi, R.; Chamoun, R.K.; Sokhn, M. The power of a blockchain-based supply chain. Comput. Ind. Eng. 2019, 135, 582–592. [Google Scholar] [CrossRef]
- Mondal, S.; Wijewardena, K.P.; Karuppuswami, S.; Kriti, N.; Kumar, D.; Chahal, P. Blockchain inspired RFID-based information architecture for food supply chain. IEEE Internet Things J. 2019. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Das Bit, S. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Tse, D.; Zhang, B.; Yang, Y.; Cheng, C.; Mu, H. Blockchain application in food supply information security. In Proceedings of the IEEE International Conference on Industrial Engineering and Engineering Management, Bangkok, Thailand, 16–19 December 2018. [Google Scholar] [CrossRef]
- Treiblmaier, H. The impact of the blockchain on the supply chain: A theory-based research framework and a call for action. Supply Chain Manag. 2018. [Google Scholar] [CrossRef]
- Malik, S.; Kanhere, S.S.; Jurdak, R. ProductChain: Scalable blockchain framework to support provenance in supply chains. In Proceedings of the NCA 2018—2018 IEEE 17th International Symposium on Network Computing and Applications 2018, Cambridge, MA, USA, 1–3 November 2018. [Google Scholar] [CrossRef]
- Peña, M.; Llivisaca, J.; Siguenza-Guzman, L. Blockchain and Its Potential Applications in Food Supply Chain Management in Ecuador. Adv. Intell. Syst. Comput. 2020. [Google Scholar] [CrossRef]
- Toyoda, K.; Mathiopoulos, P.T.; Sasase, I.; Ohtsuki, T. A Novel Blockchain-Based Product Ownership Management System (POMS) for Anti-Counterfeits in the Post Supply Chain. IEEE Access 2017. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Traceability of counterfeit medicine supply chain through Blockchain. In Proceedings of the 2019 11th International Conference on Communication Systems and Networks, COMSNETS 2019, Bangalore, India, 7–11 January 2019. [Google Scholar] [CrossRef]
- Pham, H.L.; Tran, T.H.; Nakashima, Y. Practical Anti-Counterfeit Medicine Management System Based on Blockchain Technology. In Proceedings of the TIMES-iCON 2019—2019 4th Technology Innovation Management and Engineering Science International Conference, Bangkok, Thailand, 11–13 December 2019. [Google Scholar] [CrossRef]
- Negka, L.; Gketsios, G.; Anagnostopoulos, N.A.; Spathoulas, G.; Kakarountas, A.; Katzenbeisser, S. Employing blockchain and physical unclonable functions for counterfeit IoT devices detection. ACM Int. Conf. Proc. Ser. 2019. [Google Scholar] [CrossRef]
- Sidorov, M.; Ong, M.T.; Sridharan, R.V.; Nakamura, J.; Ohmura, R.; Khor, J.H. Ultralightweight mutual authentication RFID protocol for blockchain enabled supply chains. IEEE Access 2019. [Google Scholar] [CrossRef]
- Wen, Q.; Gao, Y.; Chen, Z.; Wu, D. A blockchain-based data sharing scheme in the supply chain by IIoT. In Proceedings of the 2019 IEEE International Conference on Industrial Cyber Physical Systems, ICPS 2019, Taipei, Taiwan, 6–9 May 2019. [Google Scholar] [CrossRef]
- Zheng, K.; Zhang, Z.; Chen, Y.; Wu, J. Blockchain adoption for information sharing: Risk decision-making in spacecraft supply chain. Enterp. Inf. Syst. 2019. [Google Scholar] [CrossRef]
- Liu, L.; Li, F.; Qi, E. Research on Risk Avoidance and Coordination of Supply Chain Subject Based on Blockchain Technology. Sustainability 2019, 11, 2182. [Google Scholar] [CrossRef]
- Meng, W.; Tischhauser, E.W.; Wang, Q.; Wang, Y.; Han, J. When intrusion detection meets blockchain technology: A review. IEEE Access 2018. [Google Scholar] [CrossRef]
- Engelenburg, S.; van Janssen, M.; Klievink, B. Design of a software architecture supporting business-to-government information sharing to improve public safety and security: Combining business rules, Events and blockchain technology. J. Intell. Inf. Syst. 2019. [Google Scholar] [CrossRef]
- Cui, Y.; Idota, H.; Ota, M. Improving Supply Chain Resilience with a Hybrid System Architecture. Commun. Comput. Inf. Sci. 2019. [Google Scholar] [CrossRef]
- Kulkarni, A.; Hazari, N.A.; Niamat, M. A Blockchain Technology Approach for the Security and Trust of the IC Supply Chain. In Proceedings of the IEEE National Aerospace Electronics Conference, NAECON, 2019, Dayton, OH, USA, 15–19 July 2019. [Google Scholar] [CrossRef]
- Liang, X.; Shetty, S.; Tosh, D.; Ji, Y.; Li, D. Towards a reliable and accountable cyber supply chain in energy delivery system using blockchain. In Proceedings of the Lecture Notes of the Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering, LNICST, Osaka, Japan, 28–29 February 2018. [Google Scholar] [CrossRef]
- Kshetri, N. 1 Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inf. Manag. 2018, 39, 80–89. [Google Scholar] [CrossRef]
- Queiroz, M.M.; Wamba, S.F. Blockchain adoption challenges in supply chain: An empirical investigation of the main drivers in India and the USA. Int. J. Inf. Manag. 2019, 46, 70–82. [Google Scholar] [CrossRef]
- Liu, Z.; Li, Z. A blockchain-based framework of cross-border e-commerce supply chain. Int. J. Inf. Manag. 2020, 52, 102059. [Google Scholar] [CrossRef]
- Tian, F. A supply chain traceability system for food safety based on HACCP, blockchain & Internet of things. In Proceedings of the 14th International Conference on Services Systems and Services Management, ICSSSM 2017—Proceedings, Dalian, China, 16–18 June 2017. [Google Scholar] [CrossRef]
- Habib, M.A.; Sardar, M.B.; Jabbar, S.; Faisal, C.N.; Mahmood, N.; Ahmad, M. Blockchain-based Supply Chain for the Automation of Transaction Process: Case Study based Validation. In Proceedings of the 2020 International Conference on Engineering and Emerging Technologies, ICEET 2020, Tokyo, Japan, 22–23 February 2020. [Google Scholar] [CrossRef]
- Ahmed, S.; Islam, M.E.; Hosen, M.T.; Hasan, M.H. BlockChain based fertilizer distribution system: Bangladesh perspective. ACM Int. Conf. Proc. Ser. 2020. [Google Scholar] [CrossRef]
- The World Health Organization (WHO). Situation Report—18. 7 February 2020. Available online: https://www.who.int/docs/default-source/coronaviruse/transcripts/transcript-coronavirus-press-conference-full-07feb2020-final.pdf?sfvrsn=3beba1c0_2 (accessed on 5 February 2021).
- Ministry of Commerce, People’s Republic of China. Online Press Conference on 10 February 2020. In Chinese. Available online: http://www.mofcom.gov.cn/article/i/jyjl/l/202002/20200202936313.shtml (accessed on 5 February 2021).
- Knoke, D.; Yang, S. Social Network Analysis, 2nd ed.; Sage Publications: Szende Oaks, CA, USA, 2019. [Google Scholar]
- Ding, Y.; Chowdhury, G.G.; Foo, S. Bibliometric cartography of information retrieval research by using co-word analysis. Inf. Process. Manag. 2001. [Google Scholar] [CrossRef]
- Ivanov, D.; Sokolov, B.; Solovyeva, I.; Dolgui, A.; Jie, F. Dynamic recovery policies for time-critical supply chains under conditions of ripple effect. Int. J. Prod. Res. 2016, 54, 7245–7258. [Google Scholar] [CrossRef]
- Hosseini, S.; Ivanov, D.; Dolgui, A. Review of quantitative methods for supply chain resilience analysis. Transp. Res. Part E Logist. Transp. Rev. 2019. [Google Scholar] [CrossRef]
- Holland, M.; Nigischer, C.; Stjepandic, J. Copyright protection in additive manufacturing with blockchain approach. Adv. Transdiscipl. Eng. 2017. [Google Scholar] [CrossRef]
- Queiroz, M.M.; Ivanov, D.; Dolgui, A.; Wamba, S.F. Impacts of epidemic outbreaks on supply chains: Mapping a research agenda amid the COVID-19 pandemic through a structured literature review. Ann. Oper. Res. 2020. [Google Scholar] [CrossRef] [PubMed]
- Global Blockchain Business Council. Global Blockchain Business Council (GBBC) Announces Release of Annual Report. Medium 2018. Available online: https://www.google.com.hk/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwi5o4ji3tLuAhUTy4sBHTBaCYgQFjAAegQIAhAC&url=https%3A%2F%2Fgbbc.medium.com%2Fglobal-blockchain-business-council-gbbc-announces-release-of-annual-report-f7f1fd533db6&usg=AOvVaw3mnlHq8VHHum8e30QpTh79 (accessed on 5 February 2021).
- Naidu, V.; Mudliar, K.; Naik, A.; Bhavathankar, P. A Fully Observable Supply Chain Management System Using Block Chain and IOT’. In Proceedings of the 2018 3rd International Conference for Convergence in Technology, I2CT 2018, Pune, India, 6–7 April 2018. [Google Scholar] [CrossRef]
- Di Francesco Maesa, D.; Mori, P. Blockchain 3.0 applications survey. J. Parallel Distrib. Comput. 2020. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Blanco-Novoa, O.; Froiz-Míguez, I.; Fraga-Lamas, P. Towards an Autonomous Industry 4.0 Warehouse: A UAV and Blockchain-Based System for Inventory and Traceability Applications in Big Data-Driven Supply Chain Management. Sensors 2019, 19, 2394. [Google Scholar] [CrossRef]
- Galvez, J.F.; Mejuto, J.C.; Simal-Gandara, J. Future challenges on the use of blockchain for food traceability analysis. Trends Anal. Chem. 2018. [Google Scholar] [CrossRef]
- Mao, D.; Wang, F.; Hao, Z.; Li, H. Credit evaluation system based on blockchain for multiple stakeholders in the food supply chain. Int. J. Env. Res. Public Health 2018, 15, 1627. [Google Scholar] [CrossRef] [PubMed]
- Aung, M.M.; Chang, Y.S. Traceability in a food supply chain: Safety and quality perspectives. Food Control 2014. [Google Scholar] [CrossRef]
- Yiannas, F. A New Era of Food Transparency Powered by Blockchain. Innov. Technol. Gov. Glob. 2018. [Google Scholar] [CrossRef]
- Shaikh, S.; Butala, M.; Butala, R.; Creado, M. AgroVita using Blockchain. In Proceedings of the 2019 IEEE 5th International Conference for Convergence in Technology, I2CT 2019, Bombay, India, 29–31 March 2019. [Google Scholar] [CrossRef]
- Kayikci, Y.; Subramanian, N.; Dora, M.; Bhatia, M.S. Food supply chain in the era of Industry 4.0: Blockchain technology implementation opportunities and impediments from the perspective of people, process, performance, and technology. Prod. Plan. Control 2020, 1–21. [Google Scholar] [CrossRef]
- Mylrea, M.; Gourisetti, S.N.G. Blockchain for Supply Chain Cybersecurity, Optimization and Compliance. In Proceedings of the Resilience Week 2018, RWS 2018, Denver, CO, USA, 20–23 August 2018. [Google Scholar] [CrossRef]
- Rot, A.; Blaicke, B. Blockchain’s Future Role in Cybersecurity. Analysis of Defensive and Offensive Potential Leveraging Blockchain-Based Platforms. In Proceedings of the 2019 9th International Conference on Advanced Computer Information Technologies, ACIT 2019—Proceedings, Ceske Budejovice, Czech Republic, 5–7 June 2019. [Google Scholar] [CrossRef]
- Wang, S.; Zhu, S.; Zhang, Y. Blockchain-based Mutual Authentication Security Protocol for Distributed RFID Systems. IEEE Symp. Comput. Commun. 2018. [Google Scholar] [CrossRef]
- Makhdoom, I.; Zhou, I.; Abolhasan, M.; Lipman, J.; Ni, W. PrivySharing: A blockchain-based framework for privacy-preserving and secure data sharing in smart cities. Comput. Secur. 2020. [Google Scholar] [CrossRef]
- Hemalatha, K.; Hema, K.; Deepika, V. Utilization of blockchain technology to overthrow the challenges in healthcare industry. Adv. Intell. Syst. Comput. 2020. [Google Scholar] [CrossRef]
- Sahoo, M.; Singhar, S.S.; Sahoo, S.S. A blockchain based model to eliminate drug counterfeiting. Adv. Intell. Syst. Comput. 2020. [Google Scholar] [CrossRef]
- Abuidris, Y.; Kumar, R.; Wenyong, W. A survey of blockchain based on e-voting systems. ACM Int. Conf. Proc. Ser. 2019. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Panda, S.S.; Satapathy, U.; Jena, D.; Gountia, D. Trustworthy Management in Decentralized IoT Application using Blockchain. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies, ICCCNT 2019, Kanpur, India, 6–8 July 2019. [Google Scholar] [CrossRef]
- Badr, N.G. Blockchain or distributed ledger technology what is in it for the healthcare industry? In Proceedings of the IC3K 2019—Proceedings of the 11th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management, Vienna, Austria, 9–11 November 2019. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Mann, S.; Potdar, V.; Gajavilli, R.S.; Chandan, A. Blockchain technology for supply chain traceability, transparency and data provenance. ACM Int. Conf. Proc. Ser. 2018. [Google Scholar] [CrossRef]
- Huang, Y.; Bian, Y.; Li, R.; Zhao, J.L.; Shi, P. Smart contract security: A software lifecycle perspective. IEEE Access 2019. [Google Scholar] [CrossRef]
- Bartoletti, M.; Pompianu, L. An Empirical analysis of smart contracts: Platforms, applications, and design patterns. In Proceedings of the International Conference on Financial Cryptography and Data Security, Sliema, Malta, 3–7 April 2017. [Google Scholar] [CrossRef]
- Wohrer, M.; Zdun, U. Smart contracts: Security patterns in the ethereum ecosystem and solidity. In Proceedings of the 2018 IEEE 1st International Workshop on Blockchain Oriented Software Engineering, IWBOSE 2018—Proceedings, Campobasso, Italy, 1 November 2018. [Google Scholar] [CrossRef]
- Clack, C.D. Smart Contract Templates: Legal semantics and code validation. J. Digit. Bank. 2018, 2, 338–352. [Google Scholar]
- Abdellatif, T.; Brousmiche, K.L. Formal Verification of Smart Contracts Based on Users and Blockchain Behaviors Models. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security, NTMS 2018—Proceedings, Paris, France, 26–28 February 2018. [Google Scholar] [CrossRef]
- Grishchenko, I.; Maffei, M.; Schneidewind, C. A semantic framework for the security analysis of ethereum smart contracts. In Principles of Security and Trust, Proceedings of the 7th International Conference, POST 2018, Held as Part of the European Joint Conferences on Theory and Practice of Software, ETAPS 2018, Thessaloniki, Greece, 16–19 April 2018; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2018. [Google Scholar] [CrossRef]
- Hildenbrandt, E.; Saxena, M.; Zhu, X.; Rodrigues, N.; Daian, P.; Guth, D.; Rosu, G. KEVM: A complete formal semantics of the ethereum virtual machine. In Proceedings of the IEEE Computer Security Foundations Symposium, Cernayla-Ville, France, 9–12 July 2018; pp. 204–217. [Google Scholar] [CrossRef]
- Breidenbach, L.; Daian, P.; Tramèr, F.; Juels, A. Enter the Hydra: Towards principled bug bounties and exploit-resistant smart contracts. In Proceedings of the 27th USENIX Security Symposium, Berkeley, CA, USA, 12 August 2018. [Google Scholar]
- Nikolić, I.; Kolluri, A.; Sergey, I.; Saxena, P.; Hobor, A. Finding the greedy, prodigal, and suicidal contracts at scale. ACM Int. Conf. Proc. Ser. 2018. [Google Scholar] [CrossRef]
- Ema.europa.eu. COVID-19: Beware of Falsified Medicines from Unregistered Websites. 2020. Available online: https://www.ema.europa.eu/en/news/covid-19-beware-falsified-medicines-unregistered-website (accessed on 21 May 2020).
- Raj, R.; Rai, N.; Agarwal, S. Anticounterfeiting in Pharmaceutical Supply Chain by establishing Proof of Ownership. In Proceedings of the IEEE Region 10 Annual International Conference, Proceedings/TENCON, Osaka, Japan, 16–19 November 2019. [Google Scholar] [CrossRef]
- Chitre, M.; Sapkal, S.; Adhikari, A.; Mulla, S. Monitoring Counterfeit Drugs using CounterChain. In Proceedings of the 2019 6th IEEE International Conference on Advances in Computing, Communication and Control, ICAC3 2019, Mumbai, India, 20–21 December 2019. [Google Scholar] [CrossRef]
- Wang, K.; Liu, M.; Jiang, X.; Yang, C.; Zhang, H. A Novel Vehicle Blockchain Model Based on Hyperledger Fabric for Vehicle Supply Chain Management. Commun. Comput. Inf. Sci. 2020. [Google Scholar] [CrossRef]
- Scott, B.; Loonam, J.; Kumar, V. Exploring the rise of blockhain technology: Towards distributed collaborative organizations. Strateg. Chang. 2017. [Google Scholar] [CrossRef]





| Authors | Topic | Main Issues | Contribution |
|---|---|---|---|
| [6,28] | Integration of blockchain and the Internet of things (IoT) |
|
|
| [63,64] | Use of blockchain for supply chain securityblockchain-enabled supply chain activities |
|
|
| [44] | Adoption, benefits, and challenges |
|
|
| [46] | Blockchain solutions for IoT and IIoT |
|
|
| [65] | Adoption, drivers, and challenges |
|
|
| [66] | Cross-border e-commerce supply chain and traceability |
|
|
| [67] | Food supply chain and traceability |
|
|
| [68,69] | Automation of the transaction process |
|
|
| [23,25] | Digital technologies and resilient supply chain |
|
|
| [26] | Sustainability and traceability |
|
|
| [27] | Humanitarian logistics and supply chain |
|
|
| Title | Author | Source | Year | GCS | Main Path | Louvain Community |
|---|---|---|---|---|---|---|
| Can Blockchain Strengthen the Internet of Things? | [28] | IT Professional | 2017 | 213 | YES | G |
| Blockchain’s roles in meeting key supply chain management objectives | [64] | International Journal of Information Management | 2018 | 175 | YES | B |
| A supply chain traceability system for food safety based on HACCP, blockchain and the Internet of things | [67] | 14th International Conference on Services Systems and Services Management, ICSSSM 2017—Proceedings | 2017 | 120 | YES | A |
| Blockchain’s roles in strengthening cybersecurity and protecting privacy | [6] | Telecommunications Policy | 2017 | 110 | YES | H |
| When intrusion detection meets blockchain technology: A review | [59] | IEEE Access | 2018 | 108 | NO | H |
| A Novel Blockchain-Based Product Ownership Management System (POMS) for Anti-Counterfeits in the Post Supply Chain | [51] | IEEE Access | 2017 | 98 | NO | F |
| The impact of digital technology and Industry 4.0 on the ripple effect and supply chain risk analytics | [25] | International Journal of Production Research | 2019 | 81 | YES | A |
| Blockchain adoption challenges in the supply chain: An empirical investigation of the main drivers in India and the USA | [65] | International Journal of Information Management | 2019 | 54 | YES | A |
| Blockchain application in food supply information security | [47] | IEEE International Conference on Industrial Engineering and Engineering Management | 2018 | 51 | NO | E |
| The impact of the blockchain on the supply chain: a theory-based research framework and a call for action | [48] | Supply Chain Management | 2018 | 41 | NO | E |
| Main Subjects | Keywords |
|---|---|
| Cluster 1: Digitalization for improved supply chain resilience | Additive manufacturing; blockchain technology; cryptocurrency; industry 4.0; RFID; supply chain resilience; supply chain risk management |
| Cluster 2: Employing blockchain technology with smart contracts in supply chain management | Blockchain; IoT; risk management; smart contracts; supply chain management |
| Cluster 3: Traceability database systems to ensure food safety and security | Distribute ledger technology; food safety; food security; food supply chain; traceability |
| Cluster 4: Blockchain’s roles in strengthening cybersecurity | cloud computing; cryptography; cybersecurity; Internet of things |
| Cluster 5: Privacy and security challenges and blockchain solutions | Blockchain; distributed ledger; privacy; security |
| Cluster 6: Security of smart contracts in Ethereum platforms | Ethereum; smart contract |
| Cluster 7: Monitoring counterfeited products in the supply chain | Counterfeit; supply chain |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Etemadi, N.; Borbon-Galvez, Y.; Strozzi, F.; Etemadi, T. Supply Chain Disruption Risk Management with Blockchain: A Dynamic Literature Review. Information 2021, 12, 70. https://doi.org/10.3390/info12020070
Etemadi N, Borbon-Galvez Y, Strozzi F, Etemadi T. Supply Chain Disruption Risk Management with Blockchain: A Dynamic Literature Review. Information. 2021; 12(2):70. https://doi.org/10.3390/info12020070
Chicago/Turabian StyleEtemadi, Niloofar, Yari Borbon-Galvez, Fernanda Strozzi, and Tahereh Etemadi. 2021. "Supply Chain Disruption Risk Management with Blockchain: A Dynamic Literature Review" Information 12, no. 2: 70. https://doi.org/10.3390/info12020070
APA StyleEtemadi, N., Borbon-Galvez, Y., Strozzi, F., & Etemadi, T. (2021). Supply Chain Disruption Risk Management with Blockchain: A Dynamic Literature Review. Information, 12(2), 70. https://doi.org/10.3390/info12020070








