The Impact of Organizational Practices on the Information Security Management Performance
Abstract
:1. Introduction
- A model has been developed to evaluate the impact of organizational practices on information security management performance.
- Previous studies only focused on a few aspects of information security, but this study also highlights the importance of organizational procedures and the role of employees.
- To the best of our knowledge, this type of study has not been done yet in the UK. The proposed method was also validated through hypothesis testing.
- This study highlights that employees are often the source of unintentional data breaches, and their training in information security needs to be a priority.
2. Literature Review
3. Research Methodology
3.1. Information Security Knowledge Sharing
3.2. Information Security Education
3.3. Information Security Visibility
3.4. Information Security Training
3.5. Trust in an Organisation
4. Results
4.1. Exploratory Factor Analysis
4.2. Reliability Tests
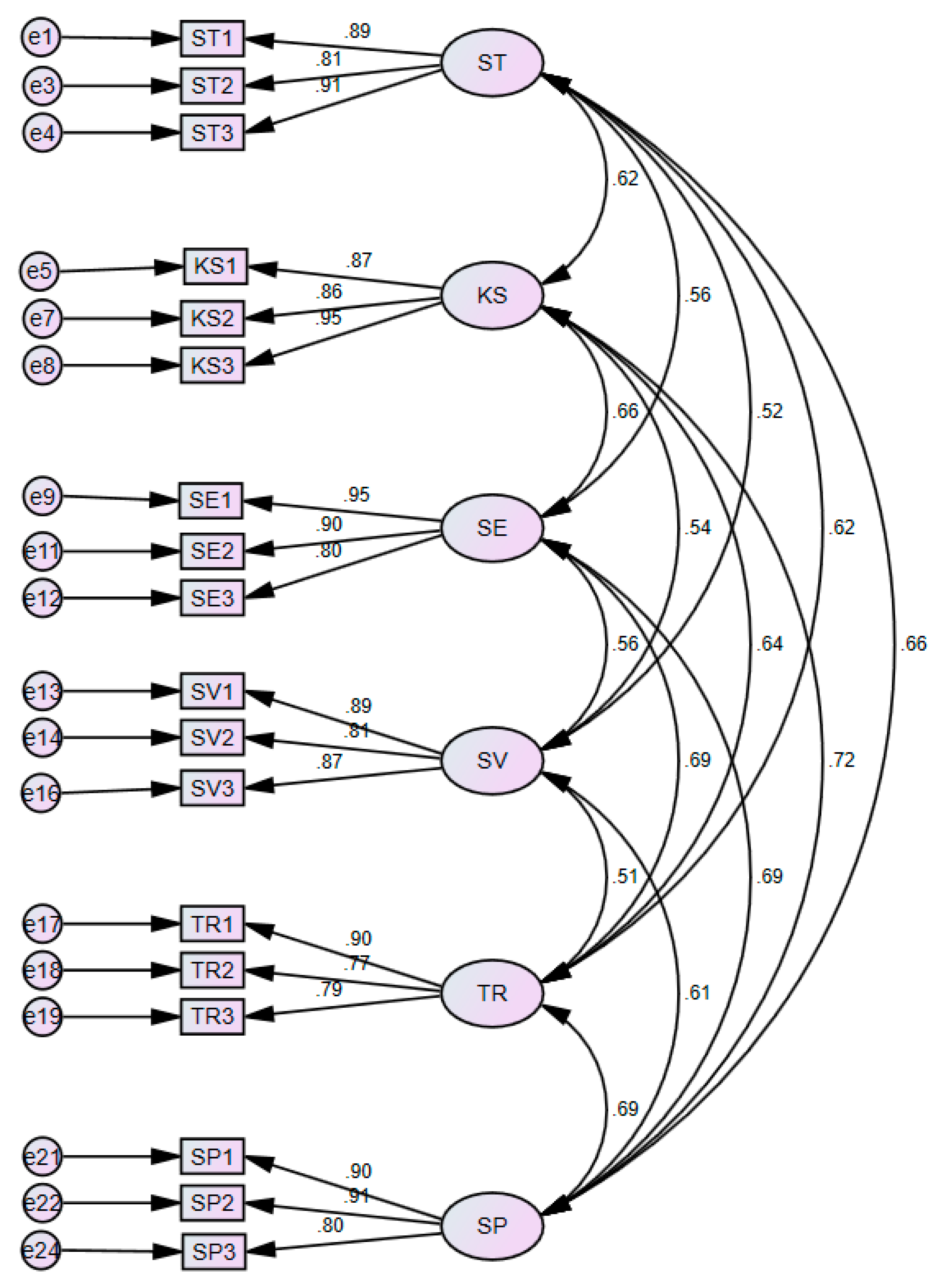
4.3. Confirmatory Factor Analysis
4.4. Reliability and Validity Tests
4.5. Structural Equation Model Path Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Diesch, R.; Pfaff, M.; Krcmar, H. A comprehensive model of information security factors for decision-makers. Comput. Secur. 2020, 92, 101747. [Google Scholar] [CrossRef]
- Doherty, N.F.; Tajuddin, S.T. Towards a user-centric theory of value-driven information security compliance. Inf. Technol. People 2018, 31, 348–367. [Google Scholar] [CrossRef]
- Fonseca-Herrera, O.A.; Rojas, A.E.; Florez, H. A Model of an Information Security Management System Based on NTC-ISO/IEC 27001 Standard. IAENG Int. J. Comput. Sci. 2021, 48, IJCS_48_2_01. [Google Scholar]
- Kobis, P. Human factor aspects in information security management in the traditional IT and cloud computing models. Oper. Res. Decis. 2021, 1, 61–76. [Google Scholar]
- Pérez-González, D.; Preciado, S.T.; Solana-Gonzalez, P. Organizational practices as antecedents of the information security management performance: An empirical investigation. Inf. Technol. People 2019, 32, 1262–1275. [Google Scholar] [CrossRef]
- Safa, N.S.; Von Solms, R. An information security knowledge sharing model in organizations. Comput. Hum. Behav. 2016, 57, 442–451. [Google Scholar] [CrossRef]
- Hwang, I.; Kim, D.; Kim, T.; Kim, S. Why not comply with information security? An empirical approach for the causes of non-compliance. Online Inf. Rev. 2017. Available online: https://www.emerald.com/insight/content/doi/10.1108/OIR-11-2015-0358/full/html (accessed on 16 September 2021). [CrossRef]
- Miladinović, V.T. Development of Awareness and Competences of Employees in the Processes of Information Security Management System: Guidelines for practical application. JITA-J. Inf. Technol. Appl. 2020, 20, 87–95. [Google Scholar]
- Putra, I.M.M.; Mutijarsa, K. Designing Information Security Risk Management on Bali Regional Police Command Center Based on ISO 27005. In Proceedings of the 2021 3rd East Indonesia Conference on Computer and Information Technology (EIConCIT), Surabaya, Indonesia, 9–11 April 2021; pp. 14–19. [Google Scholar]
- Siponen, M.; Pahnila, S.; Mahmood, M.A. Compliance with information security policies: An empirical investigation. Computer 2010, 43, 64–71. [Google Scholar] [CrossRef]
- Marelli, L.; Lievevrouw, E.; Van Hoyweghen, I. Fit for purpose? The GDPR and the governance of European digital health. Policy Stud. 2020, 41, 447–467. [Google Scholar] [CrossRef]
- Ma, Q.; Schmidt, M.B.; Pearson, J.M. An Integrated Framework for Information Security Management. Rev. Bus. 2009, 30, 58–69. [Google Scholar]
- Rocha Flores, W.; Antonsen, E.; Ekstedt, M. Information security knowledge sharing in organizations: Investigating the effect of behavioral information security governance and national culture. Comput. Secur. 2014, 43, 90–110. [Google Scholar] [CrossRef] [Green Version]
- Parsons, K.; McCormac, A.; Butavicius, M.; Pattinson, M.; Jerram, C. Determining employee awareness using the human aspects of information security questionnaire (HAIS-Q). Comput. Secur. 2014, 42, 165–176. [Google Scholar] [CrossRef]
- Singh, A.N.; Gupta, M.; Ojha, A. Identifying factors of “organizational information security management”. J. Enterp. Inf. Manag. 2014, 27, 644–667. [Google Scholar] [CrossRef]
- Soomro, Z.A.; Shah, M.H.; Ahmed, J. Information security management needs more holistic approach: A literature review. Int. J. Inf. Manag. 2016, 36, 215–225. [Google Scholar] [CrossRef]
- Choi, S.; Martins, J.T.; Bernik, I. Information security: Listening to the perspective of organisational insiders. J. Inf. Sci. 2018, 44, 752–767. [Google Scholar] [CrossRef] [Green Version]
- Moody, G.D.; Siponen, M.; Pahnila, S. Toward a unified model of information security policy compliance. MIS Q. 2018, 42, 285–311. [Google Scholar] [CrossRef]
- Hwang, I.; Cha, O. Examining technostress creators and role stress as potential threats to employees’ information security compliance. Comput. Hum. Behav. 2018, 81, 282–293. [Google Scholar] [CrossRef]
- Shaukat, K.; Alam, T.M.; Luo, S.; Shabbir, S.; Hameed, I.A.; Li, J.; Abbas, S.K.; Javed, U. A review of time-series anomaly detection techniques: A step to future perspectives. In Proceedings of the Future of Information and Communication Conference, Vancouver, BC, Canada, 29–30 April 2021; pp. 865–877. [Google Scholar]
- Shaukat, K.; Luo, S.; Chen, S.; Liu, D. Cyber Threat Detection Using Machine Learning Techniques: A Performance Evaluation Perspective. In Proceedings of the 2020 International Conference on Cyber Warfare and Security (ICCWS), Islamabad, Pakistan, 20–21 October 2020; pp. 1–6. [Google Scholar]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Chen, S.; Liu, D.; Li, J. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 2020, 13, 2509. [Google Scholar] [CrossRef]
- Mamonov, S.; Benbunan-Fich, R. The impact of information security threat awareness on privacy-protective behaviors. Comput. Hum. Behav. 2018, 83, 32–44. [Google Scholar] [CrossRef]
- Willison, R.; Warkentin, M. Beyond deterrence: An expanded view of employee computer abuse. MIS Q. 2013, 37, 1–20. [Google Scholar] [CrossRef] [Green Version]
- Peikari, H.R.; Ramayah, T.; Shah, M.H.; Lo, M.C. Patients’ perception of the information security management in health centers: The role of organizational and human factors. BMC Med Inform. Decis. Mak. 2018, 18, 102. [Google Scholar] [CrossRef] [PubMed]
- Bentler, P.M. Comparative fit indexes in structural models. Psychol. Bull. 1990, 107, 238. [Google Scholar] [CrossRef] [PubMed]
- Bentler, P.M.; Bonett, D.G. Significance tests and goodness of fit in the analysis of covariance structures. Psychol. Bull. 1980, 88, 588. [Google Scholar] [CrossRef]
- Bollen, K.A. Structural Equations with latent Variables; John Wiley & Sons: New York, NY, USA, 1989; p. 210. Available online: https://www.wiley.com/en-ca/Structural+Equations+with+Latent+Variables-p-9780471011712 (accessed on 16 September 2021).
- Qu, X. Multivariate Data Analysis; Taylor & Francis: London, UK, 2007; Available online: https://www.tandfonline.com/doi/abs/10.1198/tech.2007.s455 (accessed on 16 September 2021).
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A Survey on Machine Learning Techniques for Cyber Security in the Last Decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
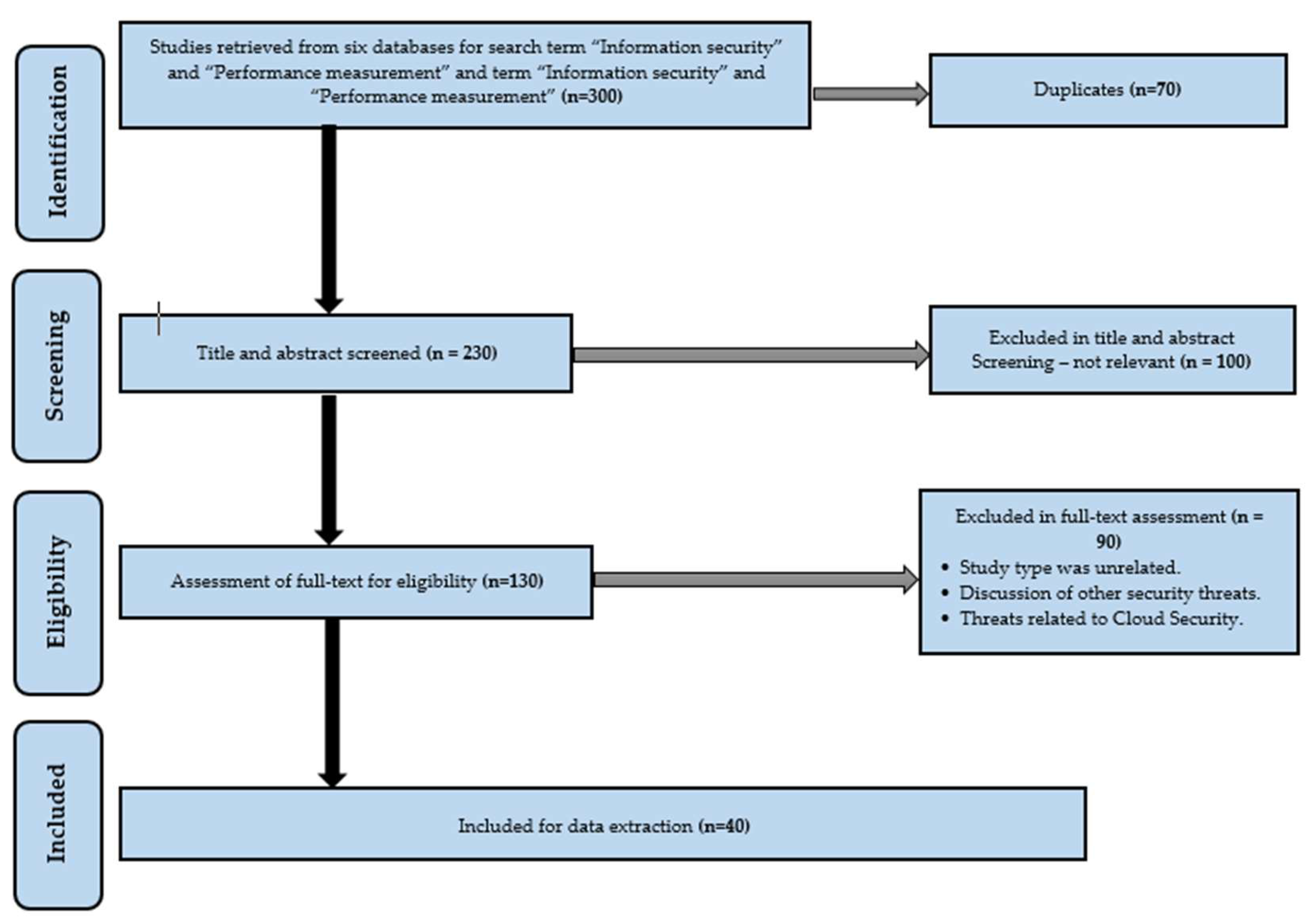


| References | Objective | Limitations |
|---|---|---|
| Ma et al. [13] | An ISM-based framework was developed for conceptualized decision-making. | It is observed that their framework consists of four principles but didn’t explain how information security policy will be implemented. What are the parameters to establish the objectives of information security? |
| Flores et al. [14] | This study investigated the impact of the establishment of information security governance factors incorporates based on culture. | Only behavioural and cultural factors are included for the establishment of information security knowledge sharing in organizations. |
| Parsons et al. [15] | Developed a questionnaire based on human aspects to measure the vulnerabilities for human-based information security. | The impact of interventional, individual, and organizational factors on information security management also need to be determined. |
| Singh et al. [16] | Developed a hybrid method to determine the factors related to information security management. | A small number of factors were considered related to information security management. |
| Safa and Solms [17] | Integrated several methods using human behaviour to determine the information security knowledge sharing development in various organizations. | The sample size is small and limited techniques were employed for data collection. |
| Soomro et al. [18] | Conducted a systemic literature review to investigate the management’s roles in information security management to improve productivity. | A limited number of papers are included for the survey, and management perspective was not mentioned. |
| Hwang et al. [19] | Investigated the relationship between organizational security factors and non-compliance causes of individuals. | Only two non-compliance factors were determined. Employees actual behaviours in the context of information security need to be incorporated. |
| Choi et al. [20] | Investigated the relationship between information security and organizational insiders. | The impact of organisational citizenship behaviour needs to be evaluated in detail. |
| Moody et al. [21] | Compared eleven theories related to the behavioural perspective of information system security. | The proposed model was not proved practically nor empirically. |
| Pérez-González et al. [5] | Investigated the impact of organizational security practices on information security management performance. | The results cannot be mapped worldwide because the employed data was only collected from Spain since economic and technological development disparity exists worldwide. |
| Kobis [12] | Classified the major organizational threats in the way of information management processes. | This research lacks human factors (management level) on information security management. |
| Fonseca-Herrera et al. [6] | Proposed a framework for information security management to protect the data from outsiders, hackers, and unauthorized individuals. | The threats related to management individuals are not incorporated well. |
| Component 1 | Factor Loadings | Eigenvalue | % Variance |
|---|---|---|---|
| SV1 | 0.837 | 9.596 | 53.311 |
| SV2 | 0.788 | ||
| SV3 | 0.869 | ||
| Component 2 | Factor Loadings | Eigenvalue | % Variance |
| ST1 | 0.798 | 1.399 | 7.771 |
| ST2 | 0.807 | ||
| ST3 | 0.846 | ||
| Component 3 | Factor Loadings | Eigenvalue | % Variance |
| SE1 | 0.756 | 1.305 | 7.251 |
| SE2 | 0.795 | ||
| SE3 | 0.843 | ||
| Component 4 | Factor Loadings | Eigenvalue | % Variance |
| KS1 | 0.819 | 1.043 | 5.793 |
| KS2 | 0.731 | ||
| KS3 | 0.804 | ||
| Component 5 | Factor Loadings | Eigenvalue | % Variance |
| TR1 | 0.773 | 0.908 | 5.046 |
| TR2 | 0.751 | ||
| TR3 | 0.777 | ||
| Component 6 | Factor Loadings | Eigenvalue | % Variance |
| SP1 | 0.769 | 0.835 | 4.638 |
| SP2 | 0.731 | ||
| SP3 | 0.762 | ||
| Total percentage of variance: 83.812 | |||
| Component | Items | Cronbach’s Alpha | No of Items |
|---|---|---|---|
| 1 | SV1, SV2, SV3 | 0.890 | 3 |
| 2 | ST1, ST2, ST3 | 0.900 | 3 |
| 3 | SE1, SE2, SE3 | 0.915 | 3 |
| 4 | KS1, KS2, KS3 | 0.919 | 3 |
| 5 | TR1, TR2, TR3 | 0.857 | 3 |
| 6 | SP1, SP2, SP3 | 0.902 | 3 |
| Estimate | SE | CR | P | |||
|---|---|---|---|---|---|---|
| ST | <--> | KS | 0.683 | 0.115 | 5.913 | *** |
| ST | <--> | SE | 0.659 | 0.117 | 5.632 | *** |
| ST | <--> | SV | 0.590 | 0.113 | 5.228 | *** |
| ST | <--> | TR | 0.759 | 0.128 | 5.912 | *** |
| ST | <--> | SP | 0.658 | 0.106 | 6.211 | *** |
| KS | <--> | SE | 0.792 | 0.125 | 6.359 | *** |
| KS | <--> | SV | 0.612 | 0.115 | 5.338 | *** |
| KS | <--> | TR | 0.793 | 0.131 | 6.044 | *** |
| KS | <--> | SP | 0.728 | 0.111 | 6.560 | *** |
| SE | <--> | SV | 0.686 | 0.121 | 5.644 | *** |
| SE | <--> | TR | 0.917 | 0.140 | 6.559 | *** |
| SE | <--> | SP | 0.749 | 0.113 | 6.611 | *** |
| SV | <--> | TR | 0.642 | 0.126 | 5.076 | *** |
| SV | <--> | SP | 0.628 | 0.107 | 5.867 | *** |
| TR | <--> | SP | 0.777 | 0.121 | 6.424 | *** |
| Name of Parameter | Value |
|---|---|
| The goodness of fit index | 0.925 |
| Comparative fit index | 0.996 |
| Root mean square error of approximation (RMSEA) | 0.022 |
| CR Value | AVE | |
|---|---|---|
| ST | 0.903 | 0.757 |
| KS | 0.923 | 0.801 |
| SE | 0.916 | 0.786 |
| SV | 0.892 | 0.735 |
| TR | 0.862 | 0.676 |
| SP | 0.904 | 0.759 |
| ST | KS | SE | SV | TR | SP | |
|---|---|---|---|---|---|---|
| ST | 0.870 | |||||
| KS | 0.616 | 0.895 | ||||
| SE | 0.555 | 0.66 | 0.886 | |||
| SV | 0.523 | 0.536 | 0.561 | 0.857 | ||
| TR | 0.62 | 0.64 | 0.692 | 0.509 | 0.822 | |
| SP | 0.657 | 0.719 | 0.691 | 0.609 | 0.694 | 0.871 |
| Estimate | SE | CR | P | |||
|---|---|---|---|---|---|---|
| TR | <--- | ST | 0.366 | 0.093 | 3.930 | *** |
| TR | <--- | KS | 0.432 | 0.093 | 4.638 | *** |
| SP | <--- | SV | 0.131 | 0.059 | 2.227 | 0.026 |
| SP | <--- | SE | 0.141 | 0.063 | 2.257 | 0.024 |
| SP | <--- | KS | 0.220 | 0.077 | 2.865 | 0.004 |
| SP | <--- | ST | 0.144 | 0.069 | 2.082 | 0.037 |
| SP | <--- | TR | 0.156 | 0.070 | 2.228 | 0.026 |
| Name of the Parameter | Value |
|---|---|
| Goodness of fit index | 0.914 |
| Comparative fit index | 0.988 |
| Root mean square error of approximation | 0.037 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alzahrani, L.; Seth, K.P. The Impact of Organizational Practices on the Information Security Management Performance. Information 2021, 12, 398. https://doi.org/10.3390/info12100398
Alzahrani L, Seth KP. The Impact of Organizational Practices on the Information Security Management Performance. Information. 2021; 12(10):398. https://doi.org/10.3390/info12100398
Chicago/Turabian StyleAlzahrani, Latifa, and Kavita Panwar Seth. 2021. "The Impact of Organizational Practices on the Information Security Management Performance" Information 12, no. 10: 398. https://doi.org/10.3390/info12100398
APA StyleAlzahrani, L., & Seth, K. P. (2021). The Impact of Organizational Practices on the Information Security Management Performance. Information, 12(10), 398. https://doi.org/10.3390/info12100398






