Robot Evacuation on a Line Assisted by a Bike
Abstract
1. Introduction
1.1. Model and Notation
1.2. Related Work
1.3. Outline and Results of the Paper
2. Preliminaries
| Algorithm 1: Zig-Zag Algorithm |
 |
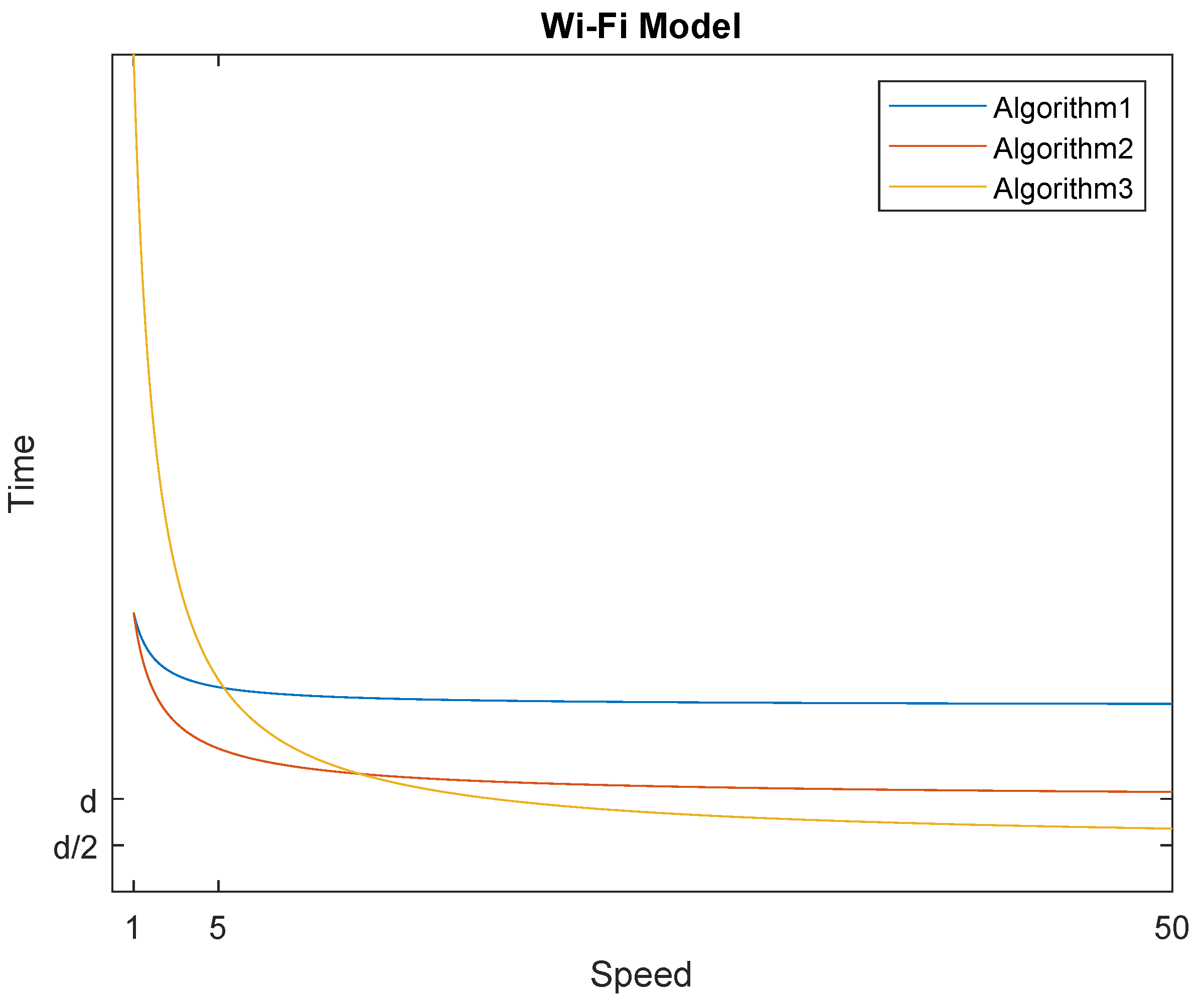
3. Evacuation in the Wireless (WiFi) Model
3.1. Opposite Direction with Max Speed
| Algorithm 2: (OppDirectionWithMaxSpeedWiFi) |
 |
3.2. Opposite Direction with Optimal Speed
| Algorithm 3: (OppDirectionWithOptimalSpeedWiFi) |
 |
3.3. Slower Imitates Faster
| Algorithm 4: (SlowerImitateFasterWiFi) |
 |
4. Evacuation in the Face-to-Face (F2F) Model
4.1. Slower Pursues Faster
| Algorithm 5: (SlowerPursueFasterF2F) |
 |
- Define to be the time needed by the biker to go to the exit from the point of intersection between the the biker and the hiker at then to return distance x to drop off the bike and subsequently go back to the exit. Thus can be defined as follows:
- Define to be the time needed by the hiker to go from the point of intersection between the hiker and the biker at to the exit while picking up the bike on its way. Thus can be defined as follows:
4.2. Slower Evacuation Close to Exit without Aid
| Algorithm 6: (SlowerEvacuationCloseToExitWithoutAidF2F) |
 |
4.3. Nearest Meeting to Exit
| Algorithm 7: (EvacuatingWithBikeF2F) |
 |
5. Lower Bounds
- If the hiker is located in the interval then the adversary places the exit at in which case by Theorem 7 the evacuation time will be at least .
- If the hiker is located in the interval then the adversary places the exit at in which case again by Theorem 7 the evacuation time will be at least .
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Baeza Yates, R.; Culberson, J.; Rawlins, G. Searching in the plane. Inf. Comput. 1993, 106, 234–252. [Google Scholar] [CrossRef]
- Beck, A. On the linear search problem. Israel J. Math. 1964, 2, 221–228. [Google Scholar] [CrossRef]
- Bellman, R. An optimal search. SIAM Rev. 1963, 5, 274. [Google Scholar] [CrossRef]
- Kao, M.Y.; Reif, J.H.; Tate, S.R. Searching in an unknown environment: An optimal randomized algorithm for the cow-path problem. Inf. Comput. 1996, 131, 63–79. [Google Scholar] [CrossRef]
- Czyzowicz, J.; Kranakis, E.; Krizanc, D.; Narayanan, L.; Opatrny, J. Search on a Line with Faulty Robots. In Proceedings of the 2016 ACM Symposium on Principles of Distributed Computing, Chicago, IL, USA, 25–28 July 2016; pp. 405–414. [Google Scholar]
- Czyzowicz, J.; Georgiou, K.; Kranakis, E.; Krizanc, D.; Narayanan, L.; Opatrny, J.; Shende, S. Search on a Line by Byzantine Robots. arXiv 2016, arXiv:1611.08209. [Google Scholar]
- Czyzowicz, J.; Gasieniec, L.; Gorry, T.; Kranakis, E.; Martin, R.; Pajak, D. Evacuating Robots via Unknown Exit in a Disk. In Proceedings of the International Symposium on Distributed Computing, Austin, TX, USA, 12–15 October 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 122–136. [Google Scholar]
- Czyzowicz, J.; Georgiou, K.; Kranakis, E. Group Search and Evacuation. In Distributed Computing by Mobile Entities, Current Research in Moving and Computing; Springer: Cham, Switzerland, 2019; Volume 11340, pp. 335–370. [Google Scholar]
- Kranakis, E.; Santoro, N.; Sawchuk, C.; Krizanc, D. Mobile agent rendezvous in a ring. In Proceedings of the IEEE 23rd International Conference on Distributed Computing Systems, Providence, RI, USA, 19–22 May 2003; pp. 592–599. [Google Scholar]
- Czyzowicz, J.; Dobrev, S.; Kranakis, E.; Krizanc, D. The power of tokens: Rendezvous and symmetry detection for two mobile agents in a ring. In Proceedings of the International Conference on Current Trends in Theory and Practice of Computer Science, Nový Smokovec, Slovakia, 27–30 January 2019; Springer: Berlin/Heidelberg, Germany, 2008; pp. 234–246. [Google Scholar]
- Czyzowicz, J.; Dobrev, S.; Godon, M.; Kranakis, E.; Sakai, T.; Urrutia, J. Searching for a Non-adversarial, Uncooperative Agent on a Cycle. Theor. Comput. Sci. 2020, 806, 531–542. [Google Scholar] [CrossRef]
- Gasieniec, L.; Kijima, S.; Min, J. Searching with increasing speeds. In Proceedings of the International Symposium on Stabilizing, Safety, and Security of Distributed Systems, Tokyo, Japan, 4–7 November 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 126–138. [Google Scholar]
- Chrobak, M.; Gasieniec, L.; Gorry, T.; Martin, R. Group search on the line. In Proceedings of the International Conference on Current Trends in Theory and Practice of Informatics, Harrachov, Czech Republic, 27 July 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 164–176. [Google Scholar]
- Bampas, E.; Czyzowicz, J.; Gasieniec, L.; Ilcinkas, D.; Klasing, R.; Kociumaka, T.; Pajak, D. Linear search by a pair of distinct-speed robots. Algorithmica 2019, 81, 317–342. [Google Scholar] [CrossRef] [PubMed]
- Jawhar, K. Bike Assisted Linear Search and Evacuation. Master’s Thesis, School of Computer Science, Carleton University, Ottawa, ON, Canada, 2020. [Google Scholar]
- Jawhar, K.; Kranakis, E. Bike Assisted Evacuation on a Line. In Proceedings of the SOFSEM (47th International Conference on Current Trends in Theory and Practice of Computer Science), Bozen-Bolzano, Italy, 25–28 January 2021; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Shaheen, S.A.; Guzman, S.; Zhang, H. Bikesharing in Europe, the Americas, and Asia: Past, present, and future. Transp. Res. Rec. 2010, 2143, 159–167. [Google Scholar] [CrossRef]
- Chen, B.; Pinelli, F.; Sinn, M.; Botea, A.; Calabrese, F. Uncertainty in urban mobility: Predicting waiting times for shared bicycles and parking lots. In Proceedings of the 16th International IEEE Conference on Intelligent Transportation Systems (ITSC 2013), The Hague, The Netherlands, 6–9 October 2013; pp. 53–58. [Google Scholar]
- Li, Z.; Zhang, J.; Gan, J.; Lu, P.; Gao, Z.; Kong, W. Large-scale trip planning for bike-sharing systems. Pervasive Mob. Comput. 2019, 54, 16–28. [Google Scholar] [CrossRef]
- O’Mahony, E.; Shmoys, D.B. Data analysis and optimization for (citi) bike sharing. In Proceedings of the Twenty-Ninth AAAI Conference on Artificial Intelligence, Austin, TX, USA, 25–30 January 2015. [Google Scholar]
- Pfrommer, J.; Warrington, J.; Schildbach, G.; Morari, M. Dynamic vehicle redistribution and online price incentives in shared mobility systems. IEEE Trans. Intell. Transp. Syst. 2014, 15, 1567–1578. [Google Scholar] [CrossRef]
- Singla, A.; Santoni, M.; Bartók, G.; Mukerji, P.; Meenen, M.; Krause, A. Incentivizing users for balancing bike sharing systems. In Proceedings of the Twenty-Ninth AAAI Conference on Artificial Intelligence, Austin, TX, USA, 25–30 January 2015. [Google Scholar]
- Yang, Z.; Hu, J.; Shu, Y.; Cheng, P.; Chen, J.; Moscibroda, T. Mobility modeling and prediction in bike-sharing systems. In Proceedings of the 14th Annual International Conference on Mobile Systems, Applications, and Services, Singapore, 26–30 June 2016; pp. 165–178. [Google Scholar]
- Czyzowicz, J.; Georgiou, K.; Killick, R.; Kranakis, E.; Krizanc, D.; Narayanan, L.; Opatrny, J.; Pankratov, D. The Bike Sharing Problem. arXiv 2020, arXiv:2006.13241. [Google Scholar]

| Algorithm | Theorem | Evacuation Time |
|---|---|---|
| Algorithm 2 (WiFi) | Theorem 1 | |
| Algorithm 3 (WiFi) | Theorem 2 | |
| Algorithm 4 (WiFi) | Theorem 3 | |
| Algorithm 5 (F2F) | Theorem 4 | |
| Algorithm 6 (F2F) | Theorem 5 | |
| Algorithm 7 (F2F) | Theorem 6 | if |
| if |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jawhar, K.; Kranakis, E. Robot Evacuation on a Line Assisted by a Bike. Information 2021, 12, 28. https://doi.org/10.3390/info12010028
Jawhar K, Kranakis E. Robot Evacuation on a Line Assisted by a Bike. Information. 2021; 12(1):28. https://doi.org/10.3390/info12010028
Chicago/Turabian StyleJawhar, Khaled, and Evangelos Kranakis. 2021. "Robot Evacuation on a Line Assisted by a Bike" Information 12, no. 1: 28. https://doi.org/10.3390/info12010028
APA StyleJawhar, K., & Kranakis, E. (2021). Robot Evacuation on a Line Assisted by a Bike. Information, 12(1), 28. https://doi.org/10.3390/info12010028






