Abstract
Information Technologies represent a primary instrument in all types of organizations. However, their use is not always well planned in the public sector. The research proposes a methodology to build a realistic action plan that improves the use of information technology and its governance in public organizations. We conduct a case study using semi-structured interviews to investigate the different views of 8 decision-makers regarding the use of IT and its governance. The findings were analyzed systematically and synthesized into a set of perspectives on the subject. An interference matrix reveals how each view interferes and receives positive and/or negative interference from the others. Based on the matrix, the methodology applies criteria to prioritize the perspectives with the highest potential to improve the use of IT and its governance. The final product of the methodology is an action plan aligned with the vision of the institution’s decision-makers. The plan requires little effort to improve the use of IT and its governance. Seventeen views related to the use of IT and its governance emerged from the interviews. Four views that do not cause or receive harmful interference from other perspectives were selected to guide the plan elaboration. The methodology proved to be efficient for creating an action plan adapted to the institutional reality. According to the managers, the action plan represents with high precision the most urgent needs of the organization, respecting its work capacity and available resources for a project to improve the use of IT and its governance.
Keywords:
qualitative research; case study; governance; information technology; public sector; university; Brazil; 5W1H; graph; matrix; covid-19; SMART objective; KPI 1. Introduction
The corporate use of Information Technology (IT) in the field of public administration usually evolves at a slow pace. This fact may have a significant impact on the quality of services and the lives of citizens. Thus, it is beneficial to investigate the causes of such inefficiency and define strategies to promote the evolution in the use of information technology scenarios in public organizations. Some works point out different challenges related to the use of IT and its governance in public sector organizations. An example of a challenge faced by public organizations is the lack of standards on IT decision-making policies. It is common to observe variations within the same institution. This fact makes it challenging to create an ITG framework to fulfill all decision-making strategies [1,2].
This work proposes a new methodology for constructing a macro action plan to promote more efficient IT’s use and governance (ITG) in organizations. The final product of the methodology is a macro action plan aligned with the vision of the organization’s decision-makers.
The work conducts a study in a Brazilian Federal University founded in the 1940s to demonstrate the practical application of the methodology. Although classified among the best of the Latin American universities, the Brazilian information technology governance committee assigned a low maturity level to the institution. The result has forced the institution to review its routine procedures for the development of ITG, making it a perfect laboratory for this research.
The methodology provides the necessary information for the development of a macro action plan to improve the ITG practices in the public university and generate a benchmark for similar organizations. The plan does not replace other institutional plans or projects but allows sharing knowledge amongst IT management teams.
The methodology considers the organization’s reality to stimulate perspectives that have a positive influence on the effective use of IT and that neutralize negative perspectives. The ITG should consider environment variables to improve organizational performance [3].
Moreover, the role of people in the organization is another point observed during the research development. The success of initiatives such as action plans for public organizations highly depends on the participation of government employees. Moreover, to acquire all benefits from ITG, organizations should take a holistic approach during the implementation of ITG programs [4]. Therefore, IT decisions must involve technology departments, top managers and other sectors in the organization [5].
The main focus of this work is the public sector. However, the authors understand that one can successfully apply the methodology to construct action plans to improve the use of IT and its governance in private companies. For instance, in financial service companies that use IT to gain competitive advantages [6], IT is part of the business organizations. IT is one of the critical components of its success [7]. IT is a powerful tool to ensure that financial and operational information is accurate, reliable, available and updated.
The term ITG appeared in the literature in 1991 and presented many definitions. According to the COBIT framework, IT governance is defined “as a structure of relationships and processes designed to direct and control the enterprise, so that it achieves its objectives by creating value, while ensuring the balance of risk in relation with the benefit of information technology and associated processes.”
According to the ISO 38500, corporate IT governance is any system for controlling the future use of IT. It involves assessing, monitoring and guiding IT’s use to support the organization in achieving its goals. It also includes any policies and strategies for the use of IT in the organization.
According to the IT Governance Institute, the board of directors and executives are responsible for the ITG. Moreover, ITG is an integral part of corporate governance and consists of organizational leadership structures that ensure that the organization’s IT maintains and evolves its strategy and objectives.
Superior government bodies of public organizations usually request the implementation of ITG as a set of actions to define an integrated IT policy and a decision-making system, an instrument to guarantee the control and the security of the information. Although there is no unique formula of how ITG should look, ITG mechanisms can contribute to organizational performance [8] and improve its level of maturity.
The definition “Specifying the decision rights and accountability framework to encourage desirable behavior in the use of IT” [9] (p. 64) is in line with the objectives of this study.
This paper answers the following research question: “how to build a governance action plan based on the organizations describe its use of IT?”
Based on the founds in the studies mentioned above, this paper highlights some essential points: (i) the topic is of interest to public companies that want to advance their IT governance and improve their performance; (ii) an open approach contributes to improving knowledge on issues related to ITG; (iii) due to the investigation’s subjective nature, the case study is an appropriate method for data collection; (iv) the low level of governance observed in Brazilian public organizations makes them suitable as a case since it may reveal many gaps related to good IT governance.
The document consists of this introduction, literature review, materials and methods, results, discussion, conclusions and limitations and further works.
2. Literature Review
The authors found primary and secondary studies that investigated the public and private sectors. Developing countries were the focus of some of these researches.
Some studies highlight the importance of adopting formal structures in ITG to implement IT value management [10]. However, even though some organizations recognize its importance. ITG is more a wish than a reality in many organizations [10]. The finds of the present paper reinforce their perception. Besides, a literature review points out that many organizations adopt frameworks to help them in ITG implementation. However, the literature available provides low scientific evidence to support the efficacy of such frameworks [11].
Bouayad, H. et al. defend the importance of ITG frameworks to handle IT’s dynamic contexts [12]. They developed a framework that offers the required agility to implement digital transformations. The study then suggests using an Analytic Hierarchy Process (AHP), a multicriteria decision analysis method, to help a decision-maker choose the best suitable ITG framework. The authors of this paper have a similar purpose but adopt the opposite strategy. It guides the construction of an ITG framework (macro action plan) to help decision-makers improve the ITG in their organizations. As the perception changes, so do the framework, affecting IT-related decisions.
Nielsen, M. highlights the strategic role of perceiving potential weaknesses and strengths through the participation of local authorities and informally consulting to implement a successful ITG plan [13]. Their work evaluated the global top Demark model regarding the digital transformation of the public sector.
Maes, K. et al. evaluate IT value management frameworks and models and conclude that organizations are still fighting to implement such IT value management practices [14]. According to them, IT value acquisition requires intense involvement of people. Their study reinforces this paper’s premise that people are fundamental to overcome the challenges and difficulties to increase the benefits of IT investments in organizations.
Indeed, the effective implementation of ITG highly depends on the particularities of each organization. Thus, the ITG plan that works for one organization is unlikely to be suitable for another. This fact makes it essential to build ITG on top of best practices available. The literature has several standard structures and evaluation methods to verify the impact and performance of IT that help in the implementation of IT governance. Larsen et al. [15] cite some related decision-making process (COBIT, ITIL, IT Governance Assessment), core business process (ITL, CMM/CMMI, SIX SIGMA) and support process (ASL, ISO 17799, PRINCE2, SOX). COBIT is a reference for good IT security and control practices. ITIL focuses on critical business processes and disciplines related to the delivery of high-quality services. IT Governance Assessment is a framework for evaluating IT governance performance. CMM/CMMI acts in the software development of organizations. SIX SIGMA aims to improve capacity and reduce defects in processes. ASL manages the development and maintenance of applications. ISO 17799 is a standard for information control and security. PRINCE2 organizes, manages and controls projects. SOX is a law that protects shareholders and society from accounting errors and illegal practices in organizations. There are other governance mechanisms used by organizations that can be remembered as COSO, ISO 20000, ISO 9000, ISO 31000, ISO BS7799, ISO 17799, PMI, SLA/SLM, BSC, IT BSC, BPM, SOA.
The lack of ITG maturity observed in the organization analyzed in this study is also the reality in other public organizations of developing countries, as stated in References [11,16]. Both works attributed to personal antecedents the lack of maturity and slowness for changes in such an organization. The theme exploited in References [16,17] is similar to the topic of this paper, analyzing the barriers to implement ITG in public sectors of developing countries.
The macro action plan constructed through the methodology proposed in this paper has the same objectives as [16,18], a set of recommendations to improve the quality of ITG.
Barrera, S.M.B. et al. studied the relationship between effective ITG, ITG relevant knowledge and how they influence innovation products and processes [19]. Results demonstrated that ITG has a positive and significant influence on innovation products and processes. They state that it is necessary to maintain a global culture of practices that help achieve ITG. The methodology to construct an action macro plan proposed in this paper contributes to improving the global ITG culture. Therefore, it can potentialize the positive influence of ITG on innovative products and processes.
Silva, N. et al. present a survey on the use of the best practices of ITG [20]. The work also seeks to understand the level of alignment these companies maintain between strategic planning and ITG.
Alonso, A. et al. propose and validate an IT artifact designed to guide IT managers in the task of handling IT demands [21].
Kizito, M. et al. relate the transdisciplinarity between ITG and digitalization in healthcare [22]. In times of pandemic, due to the coronavirus, there is an exponential growth in the benefits that the proper use of IT can bring to society.
Veerankutty, F. argues that ITG can highlight the added value that IT can bring to organizations [23]. The paper points out that the growth in the digitalization of public sector services in developing countries has led public agencies to offer more effective and efficient public services.
Ajayi, A. et al. conducted empirical research to understand the current status of ITG in public higher education institutions of countries [24]. Borges, C. et al. defined a plan for IT contracting in Brazilian public higher education institutions [25]. Delport, M. et al. sought to identify problems in the implementation of ITG across Africa, addressing process complexity [26]. Ngoma, M. et al. evaluated the ITG status in the public sector of South Africa [27]. Mamboko, P. et al. analyzed the status of ITG in local authorities in Zimbabwe [28]. Qassimi, A. et al. discussed the application of ITG in a public organization, particularly in a governmental organization of a developing country [2]. Some works expose critical challenges for ITG and demonstrate how intelligent systems can help face these challenges [29,30]. A public university in Malaysia served as a scenario for these studies.
The authors of this work conducted a systematic mapping to identify the perspectives most cited in the literature available on the theme ITG in public organizations. Studies [2,24,25,26,27,28,29,30] are among those selected in the mapping. The mapping demonstrated that public organizations of developing countries cite perspectives similar to those found in this paper. However, they attribute different levels of importance to each perspective. Table 1 presents the IT governance practices mentioned in the studies selected in the mapping.

Table 1.
Level of importance that articles from the systematic mapping attribute to each perspective.
Section 5 presents a comparison between the results of the mapping and the findings of this study.
3. Materials and Methods
The first stage of this research seeks to understand of a Brazilian Federal University’s challenges to implement good practices in the use of IT. The descriptive study in the institution aims at understanding the current scenario regarding IT use and its governance through an interpretation of human, managerial and organizational perspectives.
3.1. Institution Studied and Sample
The public university evaluated has more than 40,000 members, including students, researchers, lecturers and administrative staff. According to Brazilian regulatory bodies, this university presents an unacceptable level of governance. Such regulatory bodies carry out surveys that address IT governance and management practices. The result is a map indicating the maturity level of each Brazilian public institution. This institution has presented undesired maturity levels since the survey conducted in 2012. This fact makes the institution an excellent scenario for the case study.
The authors requested indications from the IT Director of the university to select the managers for the interview. Based on the information provided by the IT Director, the authors defined the following criteria to select the interviewees. The sample must include: (i) members from the most influential sectors in the university organizational structure, which includes the Dean, Dean’s Assistants, Heads of Administration Units, Heads of Academic Units; (ii) at least 30% of managers of each category of influential sectors; (iii) at least one manager with IT-related duties of each influential sector; (iv) managers with different profiles (age, employment time and qualification). Table 2 presents the sample distribution. It shows the number of managers per position in the institution and the corresponding number/percentage of interviewees who took part in the interview. Likewise, it exhibits the same information for managers playing roles associated with IT.

Table 2.
Sample distribution per category of manager.
3.2. Method and Design of the Research
The study seeks describe how managers of public institutions use IT in their daily routines. The description addresses human, managerial and organizational perspectives that affect IT’s use and its governance. Human perspectives include the opinions, ideas, routines and actions of staff members. Managerial and organizational perspectives observe features of different hierarchical levels. We use the case study as method. Observing these weaknesses/strengths, managers have essential information for constructing a macro action plan to promote the efficient use of IT. Figure 1 shows the design of this research.
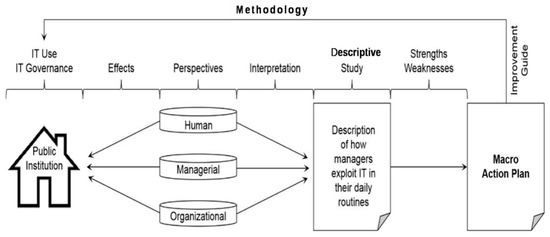
Figure 1.
Design of the research.
The perspectives are intrinsically dynamic and context-dependent, allowing several interpretations. This study shows one interpretation of the perspectives. Since it is dynamic and non-linear, the plan has several starting points and allows incremental evolution and customization.
3.3. Collection Instrument and Data Collection
The study used a qualitative source of data collection by performing supervised semi-structured interviews to obtain information. Semi-structured interviews are a useful instrument for collecting the necessary information to point out the strengths and weaknesses of such perspectives. A semi-structured interview was adopted as a data collection instrument because its script includes a combination of questions with a flexible structure, which can be addressed with no pre-defined order [31].
The semi-structured interview can also explore intangible factors such as personal beliefs, ideas, values, judgments and actions of participants through open and broad questions. The questions should not reveal the interviewer’s opinion. They must lead the interviewee to describe and reflect on their experiences and bring information outside the discussion script [32]. In addition to personal questions, the interview script includes general questions about the use of IT in each interviewee’s sector.
The interview script considers the styles, typologies and characteristics of a good question, according to References [31,33], as cited in Reference [31] (p. 96). It adapts items found in Reference [34]. Moreover, the script observes ITG documents, methodologies and practices recommended by competent bodies and institutes, such as those provided by Reference [35]. Eventually, the interview script follows complementary guidelines for publications such as those provided in Reference [36]. Appendix A presents the guide for researchers (interview script).
The interviews adopted the following steps: (i) validate the data collection instrument through a pilot study. Three professionals involved in top IT management participated in the pilot study, two from the institution and one from another public agency; (ii) adjust the interview script according to the evaluations of the pilot study; (iii) select the managers to participate in the interview: the study selected 8 (eight) managers, which is a representative sample of the population (see Table 2); (iv) schedule meetings with the managers; (v) two authors conducted the interviews from February 22 to 13 June 2017. Only the interviewee and the two authors participated in each meeting. Each interview took 41 minutes on average. The actual duration varied according to the interviewee required to respond to the answers. (vi) transcript the interviewee’s speech audio into a document structured by one interviewer author writer and reviewed by the other. The manual transcription process was valuable for the research. It allowed a more accurate interpretation of the data; (vii) analyze the documents, codify using the software MAXQDA12 and classify the information into perspectives that represent strengths and weaknesses associated with the IT evolution.
3.4. Analysis of Collected Data
The freedom each interviewee had to talk about the importance of the use of IT required an in-depth analysis of collected data. This work adopts a bottom-up analysis procedure with similar mechanisms to the Grounded Theory [37,38] to facilitate the primary data analysis. However, the study did not fully apply the Grounded Theory protocol. The study developed only methodical gathering and analysis of data but did not build theories. The analysis initiates by studying the transcription of the interviews. The aim is to create a coding system with the perspectives related to the use of IT in the organization. Before assigning a code to a given sentence is necessary to evaluate its similarities and differences concerning other codes [39]. Figure 2 illustrates the coding and categorization process.
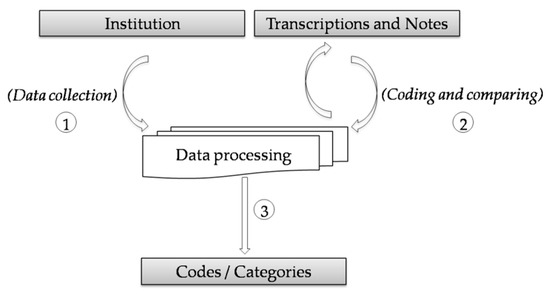
Figure 2.
Coding and categorization process.
After data collection (1), the coding and comparing phase takes place (2). It uses the tool MAXQDA12 to automate this process. It adopts the following set of steps:
- Inclusion of the eight documents (one document per interviewee) with the transcriptions; the notes helped in understanding the interviewees’ thoughts on the use of IT item
- Code generation for each interview according to the subjects or themes associated with the use of IT and the manager (the left-hand side of Figure 3 shows the system captured by the MAXQDA12 tool)
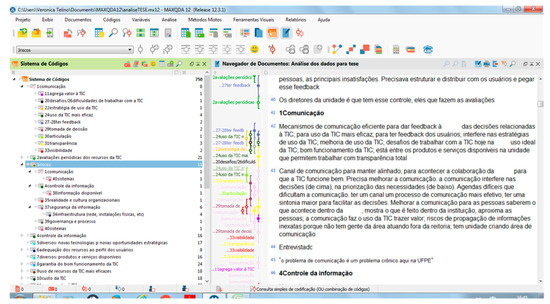 Figure 3. Coding system and compiled document produced through MAXQDA12.
Figure 3. Coding system and compiled document produced through MAXQDA12. - The eight documents are then compiled into a single report (right-hand side of Figure 3), using the codes as an aggregation key
- Codes are maintained and combined into categories according to the analysis and meaning of results (Code System). In MAXQDA12, categories are called codes
The coding phase produced 43 perspectives related to the use of IT (the left-hand side of Figure 3 shows the system captured by the MAXQDA12 tool).
4. Results
Figure 4 classifies these 43 perspectives as primary and secondary and related and unrelated. Primary perspectives are those that were stimulated by questions formulated during the interviews. On the other hand, secondary perspectives originated from spontaneous statements provided by the interviewees. This study assumes primary and secondary perspectives to have the same level of importance. Moreover, some perspectives originated from declarations that are comments and opinions unrelated to other perspectives. While others emerged from statements that connect two or more perspectives of an associated idea. Therefore, unrelated perspectives do not interfere in other perspectives and related perspectives can have a positive or negative effect on other perspectives. Two perspectives present a relationship if at least one respondent claims that one interferes positively or negatively with another. For example: IT governance is essential in controlling IT; training reduces diversity between departments and users. If the respondents do not mention any interference between two activities, they are unrelated.
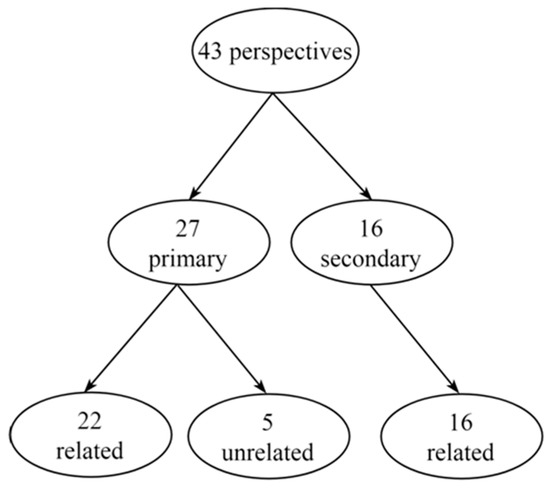
Figure 4.
Classification of the 43 perspectives.
4.1. Perspectives
As illustrated in Figure 4, this study identified 27 primary perspectives (22 are related perspectives and 5 are unrelated perspectives) and 16 secondary perspectives (all of them are related perspectives). The result is a description of how managers exploit IT in their daily routines. The data point out the strengths and weaknesses associated with IT’s use and governance in the organization.
Table 3 gives an overview of the search findings that can be useful to the construction of the action macro plan. It shows the 38 related perspectives evaluated at the University and the number of interferences directly associated with each one. For instance, the perspective Reality receives positive direct interference (Strength+ Is Affected) of 10 perspectives but causes no positive direct interference (Strength+ Affect) on other perspectives. Moreover, Reality causes negative direct interference (Weakness Affect) on 23 perspectives and receives negative direct interference (Weakness Is Affected) of 1 perspective.

Table 3.
Perspectives and interferences.
Notice that some perspectives are variations on a similar topic. The researchers used this strategy in their qualitative study to get consistent responses.
The analysis includes positive and negative interferences. The former represents forces toward the evolution of IT and its governance. On the other hand, negative interferences force in the opposite direction. Eventually, each perspective may affect or be affected by other perspectives. The final configuration forms the basis to create the macro plan. However, it is important to stress that the institution is a live organism and the arrangement may change, depending on the moment the study is conducted.
Those perspectives explicitly stated in the interviewing questions are marked with asterisks. The remaining perspectives emerged spontaneously in the answers. Notice that the term governance did not appear in the questionnaire to avoid bias or limit the responses of managers that have no formal knowledge on the subject. Besides, the interviews seek to evaluate if the managers would naturally associate the term with the use of IT.
No interviewee treated the problem of data privacy. Nor when talking about control and security of information. The survey data collection took place in 2017 and, in Brazil, Law 13.709/18 or the General Law of Personal Data Protection (LGPD), although sanctioned in 2018, has not yet entered into force. The LGPD expansion process may accelerate due to the publication of Decree no. 10,474, of 26 August 2020, in the Federal Official Gazette on 27 August 2020, which creates the structure and positions of the National Data Protection Authority (https://www.in.gov.br/web/dou/-/decreto-n-10.474-de-26-de-agosto-de-2020-274389226). Regarding the implementation of LGPD in the Institution, the Board of Directors approved in June 2020 a working group formed by 13 servers that meet weekly. The working group should submit the LGPD implementation process to the Board of Directors for approval by December 2021.
The number of direct interferences indicated in Table 3 represents the importance assigned to each perspective in the Brazilian university.
4.2. Interference Matrix
In order to offer a clear view of the interference network presented in Table 2, Figure 5 and Figure 6 present the example of the diversity perspective, demonstrating how it affects or is affected by other perspectives.
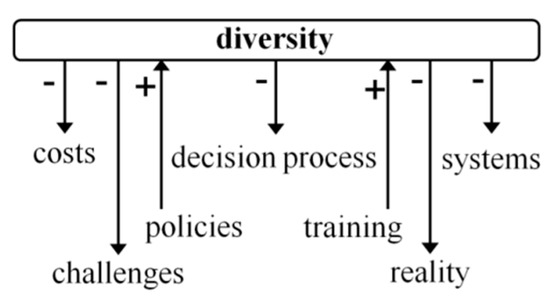
Figure 5.
Diversity graph.
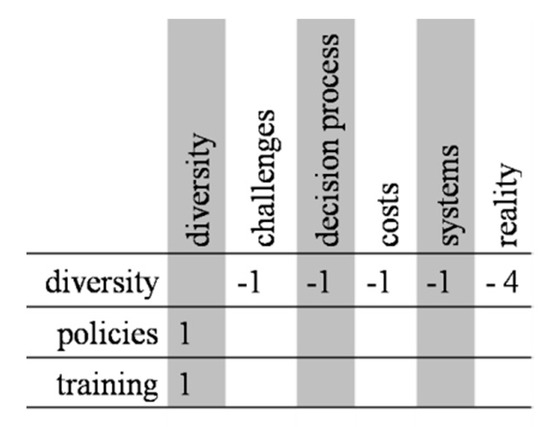
Figure 6.
Diversity matrix.
The large number of perspectives extracted from the study make the description of IT’s use and governance in an institution a systemic and complicated process. As an attempt to reduce this complexity, this work adopts an interference matrix to demonstrate the relationship amongst the categorized perspectives. The interference matrix includes the 38 perspectives identified. After that, researchers applied the criteria to select some perspectives and define a scenario.
The perspectives that produce interference in other perspectives appear in the matrix lines, while the columns represent the perspectives that receive interference from other perspectives. Positive numbers express positive interference and negative numbers have the opposite interpretation. Blank cells indicate a lack of a direct relationship between the pairs of perspectives. Whenever an interviewee mentions a relationship between a pair of perspectives, the authors add 1 to the corresponding cell value, for positive interferences or −1 for negative interferences. Therefore, each cell’s value represents the number of times interviewees indicated a positive or negative interference between two perspectives. (For the sake of simplicity, authors omitted blank lines and columns). For instance, notice the absence of a relationship between ITG and other perspectives, which may indicate a low ITG maturity level in the organization. Figure 7 presents the global view of the relationship between perspectives in Table 3 through an interference matrix. If one respondent cites a positive interference and another respondent a negative for the same pair of perspectives, the methodology suggests returning to the respondents to seek consensus. It is important to note that such a situation did not occur in this study.
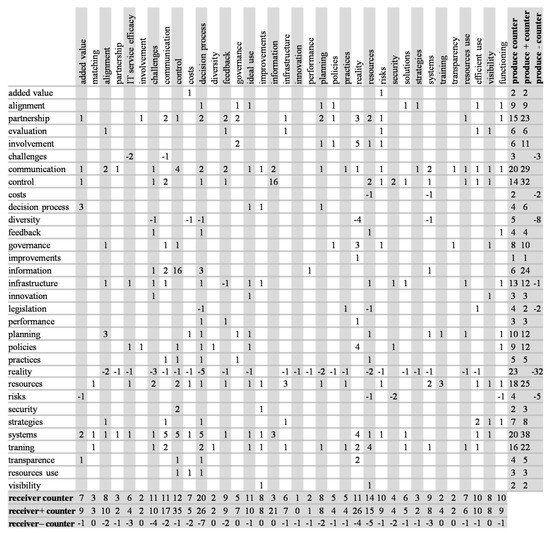
Figure 7.
Interference Matrix.
4.3. Avaliação das Perspectives
The last three columns and the last three lines of Figure 7 summarize the importance that each perspective has for the organization. Authors calculate each value in these columns and lines through the following formulae:
where n is the number of columns in the interference matrix;
where m is the number of lines in the interference matrix. Authors consider:
if interference exists between the pair of perspectives;
otherwise.
where n is the number of columns in the interference matrix;
where m is the number of lines in the interference matrix. Authors consider:
if a positive interference exists between a pair of perspectives;
otherwise.
if a negative interference exists between a pair of perspectives;
otherwise.
interference(perspectivei, perspectivej) = 1,
interference(perspectivei, perspectivej) = 0,
positive(perspectivei, perspectivej, value) = value,
positive(perspectivei, perspectivej, value) = 0,
negative(perspectivei, perspectivej, value) = 0,
For the sake of a proper understanding of the interference matrix, the study looks at the perspective partnership, which produces a positive interference in 15 perspectives. Moreover, the interviewees mentioned partnership 23 times during the case study. These numbers provide indications that the institution puts a great deal of importance on the perspective of partnership.
The higher the degree of interferences associated with a perspective, the higher are the chances of including the perspective in the action macro plan. The plan must create actions to stimulate positive interferences and neutralize negative interferences. These actions provide the necessary support to the appropriate use of IT in the institution.
4.4. Seleção das Perspectives
The methodology suggests using variables to produce counter, produce+ counter, produce counter, receive counter, receive+ counter and receive counter to guide the selection of the perspectives to be included in the macro action plan. The selection criterion follows a prioritization procedure, which may widely vary from one organization to another. In this study the authors adopted the following inclusion criterion:
Criterion: include the perspective of line i (Figure 7) in the macro action plan if [c1∨c2∨c3], where:
and #c is the total number of perspectives in lines of the matrix, #+c is the total number of non-blank cells in column produce+ counter and #-c is the total number of nonblank cells in column produce- counter.
Notice that in this study’s particular case, the researchers used only the values of the columns to produce counter, produce+ counter and produce- counter to define the selection criterion. Table 4 calculates c1, c2 and c3.

Table 4.
Values of c1, c2 and c3.
Table 5 shows the application of the selection criterion using the data from the matrix and indicates the perspectives that fulfilled the criterion. The perspective reality presents a high degree of negative interference. Indeed, it is four times higher than the second perspective in the produce- counter column. Therefore, despite having selected it for the macro action plan, to avoid biasing, the authors did not include reality negative interference values in the formulae to calculate the selection criterion.

Table 5.
Application of the criterion to select perspectives for the macro action plan using data from matrix.
4.5. Base Scenario to Construct the Macro Action Plan
Thirteen positive (Strength+) and four negatives (Weakness-) perspectives meet at least one inclusion criterion. It might be costly to implement all perspectives at once. Thus, it is essential to define a scenario to allow an incremental implementation of selected perspectives. For instance, in this study, the authors prioritize perspectives that require less effort to implement. Moreover, the authors assumed that a perspective that does not receive or produce negative influence could have its positive impact potentialized by the positive influence it receives from other perspectives. Based on this premise, the base scenario includes four perspectives that respect the premise: involvement, governance, information and training. After implementing these central perspectives, one can consider implementing secondary perspectives that have a higher number of connections with the four fundamental perspectives, then moving to tertiary perspectives. Figure 8 shows the base scenario for this study. The scenario only includes perspectives with a direct relationship to the four central perspectives. Therefore, the macro action plan takes into account only positive relations. Notice that the context may change requiring the construction of a different scenario. It all depends on the organization itself.
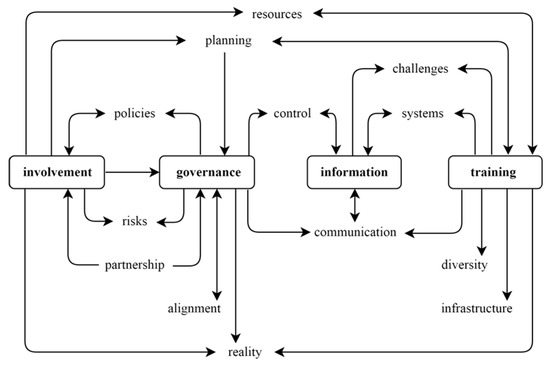
Figure 8.
Base Scenario to Construct the Macro Action Plan.
4.6. The Macro Action Plan
Notice that the plan does not replace institutional planning or projects. Their actions include the brainstorming resulting from interviewees’ statements, the available literature on IT governance in public institutions and the researchers’ interpretations of this theme. The methodology suggests an incremental and continuous strategy to implement the measures pointed out in the action macro plan, starting with the central perspectives. The researchers adapted the technique 5W1H to create the plan. 5W1H is the acronym for What, When, Who, Why, Where and How. The researchers apply the technique to create a checklist of actions to improve IT’s use and governance. The method includes the following:
- When: when it will be executed?
- Where: where to execute the action?
- Who: who will execute it?
- What: what action will take place?
- Why: why perform the action?
- How: how to conduct the execution of each action?
The actions in the “giti13” (Governance, Involvement, Training and Information, with 13 perspectives) plan represent a stimulus network oriented to the evolution of IT’s use and governance. For instance, to increase team involvement, managers should create action to improve resource management, IT planning, IT policies, risk management, reality and organizational culture and IT governance. Likewise, to improve IT governance, managers should develop actions that contribute to information available, alignment of IT and institution needs, risk management, defense of IT policies and reality and organization culture. Managers should develop actions to neutralize negative effects when it comes to perspectives with the potential to create negative interferences. The interviews and the literature on IT governance in public institutions guided the choice of the actions in the plan. Figure 9 details part of the giti13 plan.
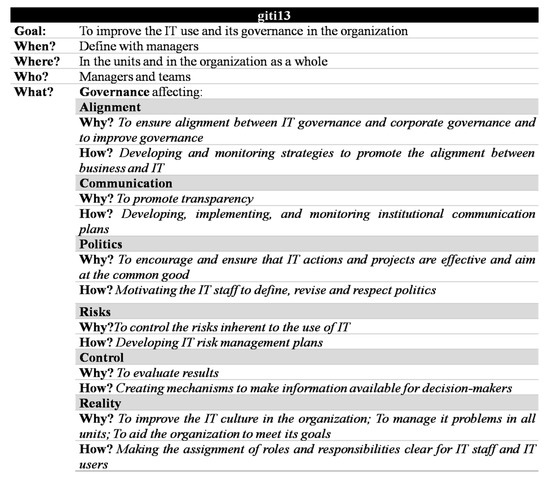
Figure 9.
The giti13 Macro Action Plan.
The description of the Macro Action Plan is available at https://bit.ly/2JHuHsq. The studies selected in the systematic mapping developed in this research do not present performance indicators to monitor objectives. To help those interested in controlling the execution of the plan, we present examples of Key Performance Indicator (KPIs) and objectives for the perspectives in Figure 9 in Appendix B.
4.7. The Methodology
Figure 10 summarizes the methodology proposed to construct the macro action plan, which is the main contribution of this work.
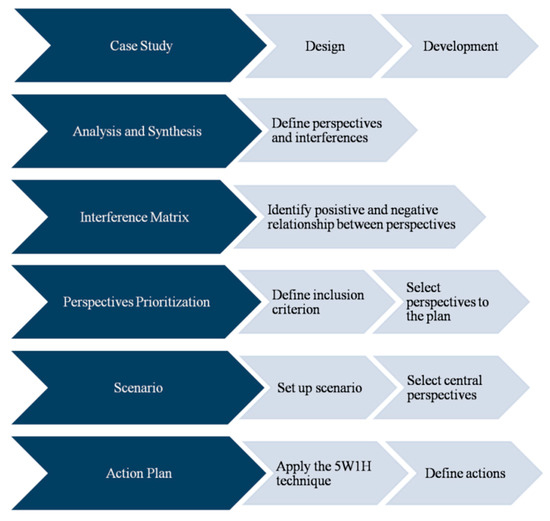
Figure 10.
Methodology to Construct the Macro Action Plan.
5. Discussion
Public organizations worldwide present low levels of IT governance. As indicated in Reference [23], inadequate governance practices contribute to the underutilization of technologies in this sector. Therefore, public companies are investing in creating strategic plans to improve IT governance. However, there are few studies on this subject [10,14,16,17,18]. Moreover, studies available in the literature offer little support to guide the organizations with this task according to References [2,24,25,26,27,28,29,30]. Such studies advocate procedures based on international norms that are too generic and do not recognize each organization’s particularities. The known international practices are complex, making them hard to adopt in organization [17,18].
This research contributes to overcoming this challenge. As the proposed methodology adopts primary sources, it creates a plan that considers the organization’s context. Thus, the plan is capable of highlighting facts and information relevant to increase IT governance maturity. The methodology allows for assessing the IT governance issues and recommend viable actions to mitigate problems.
As suggested in Reference [40], the proposed methodology is flexible and requires the collaboration of stakeholders associated with the institution. The macro action plan does not dictate an implementation process. Instead, it takes into account the systemic nature of the institution. It is dynamic and emphasizes the perspective of different agents in the organization. One can perform the plan’s actions at any time, prioritize actions or even interrupt/ignore actions in the plan. However, the methodology can help design the implementation process by constructing a base scenario, which exposes the perspectives that require less effort to produce relevant results.
This work conducted a case study at a Brazilian public university. Eight managers participated in the interview performed to collect the institution’s perception of IT use and its governance. Only 37.5% of the respondents are familiar with formal IT governance practices. This fact reflects our interest in capturing a global view of IT use and its governance, rather than producing a plan based only on expert opinion. The following discussion is the result of comparing the case study carried out in this work (Table 3) with the data observed in the systematic mapping carried out by the authors of this article (Table 1): (i) the university evaluated in this article does not present knowledge management among the perspectives addressed by the interviewees. In contrast, 33% of the articles in the systematic mapping cite the perspective. This fact is surprising, as knowledge management is an essential practice to improve the quality of decision making; (ii) the mapping refers to the service level management perspective but the interviewees make an indirect and fragmented reference to this perspective, revealing an implicit desire not yet systematized by managers; (iii) both studies overlooked the perspectives of ethics and culture of compliance. This fact alone deserves an in-depth study to understand this point; (iv) the study revealed that the institution values little frameworks and standards like COBIT and ITIL frameworks compared to the mapping results which cite EA Framework, PMI, ISO 9000, MTEF, ITIL, PRINCE2, King III, COBIT, ISO/IEC, ISO 17799, ISO 27000 and Framework Local. Although they were encouraged to talk about the subject (question E6 of the guide for researchers (interview script)—Appendix A), the interviewees’ responses were short and generic.
Based on the founds in the studies [2,24,25,26,27,28,29,30], the authors of this paper observed that the topic is of interest to public companies that want to advance their IT governance and improve their performance; that an open approach contributes to improving knowledge on issues related to ITG; that, due to the subjective nature of the investigation, the case study is an appropriate method for data collection; and that the low level of governance observed in Brazilian public organizations makes them an appropriate as a case, since many gaps related to the good IT governance can be found. The case study demonstrated that the methodology could be an instrument to stimulate reflection on the current reality and what would be the desirable use of IT in the institution. Regardless of the specifics of the study, the meetings led the interviewees to realize the importance of their participation in IT’s evolution. As a continuation of the research, the authors are developing a computational tool to support the methodology for creating a macro action plan. The idea is to steer the governance manager during the application of the methodology through a semi-automatic procedure. For instance, the tool will assist in creating the interference matrix, applying a criterion to select perspectives for the macro action plan and generating the final macro plan. The creation of appropriate computational tools in proposals such as this is crucial because they support organizations’ strategic decision making.
The authors are also conducting new case studies to evaluate the methodology in a public organization from the judiciary sector. Moreover, reusing the macro action plan is an essential possibility that the authors intend to evaluate. Institutions with similar characteristics might customize the plan, replicate it or use it as a reference to create their action plans. Authors of this paper have the intention of evaluating the degree of reuse the plan can reach when applied to similar organizations. One can combine successive applications of the plan into a larger volume of data to solve more complex organizational problems. The study [41] agrees with the use of combined data to serve more significant purposes.
The completion of this work occurred when the World Health Organization declared COVID-19 Pandemic. This fact raises questions about the impact caused by behavioral changes in the use of IT at the university studied. Thus, the authors contacted participants to understand the coronavirus’s impact on the use of IT in the institution. A new rector took office at the end of 2019. A result, only two respondents have held the same position since the original collection. The first author of this paper sent an email to the 2 participants asking, “What changes did the COVID-19 pandemic cause for IT’s use in the institution?” The testimonies of the 2 participants are in Appendix C of this document.
6. Conclusions
This work proposes a methodology to construct a macro action plan to improve IT’s use and governance. The starting point of the methodology is the statements of people involved with the research problem. Stakeholder involvement in improving the use of IT is essential [22]. The interpretation of these statements generates a set of perspectives that can have positive or negative interference on other perspectives related to IT’s use and governance. The result is an interference matrix that makes explicit the relationship between the main perspectives cited in the interviewee’s statements. The number of perspectives in the matrix may be very high. Thus, the methodology recommends the definition of a criterion to select the most relevant perspectives. These perspectives are the most cited by respondents. They require less effort to implemented by organizations. Moreover, the perspective neither receives nor produces negative influence in other perspectives. Thus, it could have its positive impact potentialized by the positive influence it receives from other perspectives. The macro plan consists of a set of actions associated with these perspectives. Some actions motivate good IT’s use and governance. Others work to neutralize bad influences on this objective.
6.1. Actions Recommended
Examples of actions recommended in the case study are as follows: (i) policies to reduce conflicts of interest in the organization, aiming at the common good; (ii) alignment between an organization’s strategic plan and IT activities; (iii) improving the control and availability of the information in the organization, to recover it democratically, quickly and safely; (iv) implementing an effective communication process that promotes transparency and avoids conflicts; (v) increasing IT budgets; (vi) strengthening the IT governance area; (vii) providing better support to IT to guarantee a good service to its users and departments; (viii) creating and maintaining risk management plans, the ideal way to manage uncertainties; (ix) reviewing the IT organizational culture to increase the involvement of an organization’s community in IT decisions (x) strengthening the IT governance area.
6.2. Limitations
This research encountered some limitations: (i) as the studies selected in the systematic mapping [2,24,25,26,27,28,29,30] point out the public sector does not have a governance model to use as a reference; (ii) the set of perspectives obtained in this study is neither complete nor stable, as people change their minds over time; (iii) the study planning and data collection in qualitative studies are time-consuming and complex tasks that depend on other people’s schedules; (iv) it is not possible to treat the actions related to the perspectives at the same depth level, as each interviewee expresses his or her opinion with different levels of detail. Indeed, some interviewees provided little information about one perspective, while another contributed with detailed explanations about it; (v) it was not easy to design the instruments for data collection and deal with the empiricism related to the open collection process and the volume of information obtained; (vi) in some situations, it was necessary to return to the interviewee to request clarification on some responses; (vii) during the interviews, there was a constant concern to keep participants willing to collaborate, to avoid manipulation and bias in the statements.
7. Further Works
Recent studies show the interest of researchers in the IT governance theme and the relevance in developing more related research. Strategic alignment remains a valued practice. Sanchez and Bayona-Oré develop a systematic literature review to identify the critical factors that interfere with strategic alignment between business and IT [42]. Marchão et al. show the importance of alignment between the management and governance of the organization and the IT area. They highlight the importance of implementing IT management practices that are included in ITIL and COBIT [43]. The execution of plan actions related to alignment or an adaptation of the methodology to create plans that implement alignment may be a suggestion for future work. In Appendix B we exemplify goal and indicator related to alignment that can contribute in implementations. Wautelet identifies deficiencies in IT governance professional frameworks and structures its research around the 3 basic pillars of IT governance that are to evaluate, direct and monitor [44]. Chang et al. aim to strengthen research on IT governance through an investigation of risk factors in the context of IoT (Internet of Things) [45]. Koltay’s study allows us to note the proximity of data governance to information and technology governance [46]. Guo et al. discuss privacy in the context of self-governance and social networks [47]. From the perspective of ISO/IEC 27002:2013, Solana-González et al. found that practices related to privacy and protection of personal identifiable information play the least role in the decision-making process related to improvements in information security requirements in organizations [48]. The scarcity of work on privacy and IT governance and evidence such as that found in Solana-González et al.’s research signals for future studies. For example, investigate how to achieve greater integration between IT security and governance standards. Other suggestions for future work are as follows: (i) replication of the case study in other public institutions; (ii) studies on the diversity existing in large public bodies; (iii) use of empirical information obtained by other researchers. The description and systematization of the findings may help similar studies; (iv) creating a computational tool to guide the application of the proposed methodology. The idea is to guide the manager during the application of the methodology through a semi-automatic procedure. For example, the tool can help create the interference matrix, apply a criterion to select perspectives for the macro action plan and generate the final macro plan.
Author Contributions
The work presented here was carried out in collaboration between all authors. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Guide for researchers (questions asked to the interviewees):
- (A)
- Initial preparations
- Introduce yourself;
- Thank for the availability to participate in the interview;
- Ask for permission to record. If the interviewee does not allow recording, transcribe the entire conversation manually.
- (B)
- General clarifications (the researchers inform the interviewees)
- “The purpose of this research is to describe the use of IT by public bodies in their daily work”;
- “We will adopt the concept of IT to indicate the entire infrastructure for the storage, control and security of information circulating in the institution”;
- “We will take all measures to prevent third parties from identifying the interviewees’ statements”;
- “Your participation is voluntary. You can stop participating in the survey at any time. Do you agree to participate?”
- (C)
- General stages of the interview process
- First phase: the interviewee will answer the questions and the questionnaire;
- Second phase (scheduling a new meeting-optional): opportunity for the interviewee to remember something important that was not mentioned in the initial conversation.
- (D)
- Questions about the interviewees’ background, experiences and behavior (allow the researcher to understand how the interviewees’ experiences can interfere with the interviewee’s current choices and behavior)
- What is your formal education?
- How long have you worked at this institution?
- How long have you worked in this department?
- What is your current position at the institution?
- How many members participate in the team that works directly with IT in your department?
- What other departments at the institution collaborate with your department to promote the proper use of IT?
- How does your department collaborate with the institution’s central administration to promote the proper use of IT?
- Who makes IT-related decisions in your department?
- How do employees in your department report their views on IT decisions?
- If employees in your department do not report their views on IT decisions, how could you encourage such behavior?
- How often would you like to receive feedback from employees about IT decisions?
- When the institution makes IT-related decisions, how do you present your opinion on those decisions?
- Suppose you want to give your feedback to the institution. How would you do that?
- What are the difficulties related to the use of IT faced by your department?
- How would you address problems related to the use of IT in your department?
- What do you do when IT is unavailable in your department?
- How does your department manage IT performance?
- How does your department plan the development of IT?
- How would you control the cost of IT in your department?
- How to use IT resources more effectively?
- How does your department ensure the proper use of IT?
- What IT products and services are available for your department?
- Analyze if the IT resources used in your department are adequate for the users’ profile?
- Do you explore new technologies to generate new strategic opportunities?
- What are the information control requirements in your department?
- Daily, how do you address IT-related risks?
- Do you perform periodic assessments of the IT resources employed in your department?
- How would you assess the IT resources employed in your department?
- (E)
- Questions about the interviewee’s beliefs and opinions
- What would you do to make the use of IT more effective in your department?
- What would you do to make the use of IT more effective at the institution?
- Regarding the IT demands of your department, how do you evaluate the service provided by the institution?
- How do you think your department takes strategic decisions about using IT?
- What do you think of these strategies?
- There are some methodologies and practices related to the use of IT in the literature. How do you think the institution should adopt them?
- Name the difficulties in making IT-related decisions in your department.
- Cite the current challenges in working with IT at the institution.
- Cite the current challenges of working with IT in your department.
- What are the advantages of implementing proper IT management and control (governance) practices within the institution?
- What would you suggest to the institution to improve the use of IT in your department?
- Describe the ideal use for IT today within the institution.
- Describe the ideal use for IT today within your department.
- How do you feel about the use of IT within the institution?
- How would you rate the evolution of institution departments concerning IT decision making?
- How is IT aligned with your department’s needs?
- How do you think using IT can bring value to your department?
Appendix B
SMART objective and KPI:
The methodology suggests the use of the SMART method proposed by Peter Drucker. Drucker’s SMART Method is useful to verify if an objective is valid. The SMART acronym to checks if the objective is S (specific), M (measurable), A (attainable), R (relevant or realist) and T (time-related). The introduction of these parameters in the research can awaken involved about the importance of concentrating efforts to obtain improvements in the use of IT.
The methodology recommends defining a SMART objective for actions from each perspective affected by governance and corresponding KPI to assess the objective’s achievement.
Alignment
- SMART objective: define the actions of the IT’s annual strategic plans, checking the actions scheduled every six months; the head of each IT’s sector is responsible for monitoring the objective
- KPI: number of open problems in the checklist
- Metric: Number of open problems = 0
- Specific: yes
- Measurable: yes (counting the number of open problems)
- Attainable: yes (by controlling the execution of the strategic plan)
- Relevant: yes (to ensure the execution of the IT´s annual strategic plan)
- Time-related: yes (one year)
Communication
- SMART objective: train 50 people (departments A, B, C and D) per month in the use of digital platforms for one year; the head of each department is responsible for monitoring the objective
- KPI: people trained in the use of digital platforms
- Metric: number of people × number of months × number of years = 50 × 12 × 1 = 600
- Specific: yes
- Measurable: yes (counting the number of training)
- Attainable: yes (by offering high-quality training)
- Relevant: yes (to promote visibility to the products and services provided by the IT sectors)
- Time-related: yes (one year)
Politics
- SMART objective: promote campaigns to publicize the importance of respecting IT policies for one year; the head of each department is responsible for monitoring the objective
- KPI: respected politics
- Metric: number of violations of IT politics = 0
- Specific: yes
- Measurable: yes (counting the number of violations of IT policies)
- Attainable: partially (the campaigns can reduce the number of violations of IT policies but it is unlikely that no employee neglects an IT policy)
- Relevant: yes (to promote ethical practices in the use of IT)
- Time-related: yes (one year)
Risks
- SMART objective: design a risk management plan for remote work for the pandemic period through a task force with 10 IT people, within ten days; the leader of the task force is responsible for monitoring the objective
- KPI: risk management plan completed
- Metric: time to elaborate the plan ≤ ten days
- Specific: yes
- Measurable: yes (counting the number of days to deliver the plan)
- Attainable: yes (the organization created a task force with ten experts)
- Relevant: yes (to maintain the organizations working during the Coronavirus pandemic)
- Time-related: yes (the plan must be ready within ten days)
Control
- SMART objective: make 100% of the information required for decision-making within 2 h; decision-makers are responsible for monitoring the objective
- KPI:100% of the information available within 2 h
- Metric: percentage of information available within 2 h = 100%
- Specific: yes
- Measurable: yes (counting the percentage of the information available within 2 h)
- Attainable: yes (by investing in data science-related technologies)
- Relevant: yes (to take right decisions)
- Time-related: yes (the information must be available within two hours)
Reality
- SMART objective: eliminating conflicts between IT staff and IT users, clarifying roles and responsibilities of each one through monthly group dynamics with ten people (representatives of sectors A, B, C and D), mediated by two professionals with the necessary competence, for one year; a member of the IT staff is responsible for monitoring the objective
- KPI: number of participants in the dynamic groups
- Metric: number of participants necessary competence, for number of months necessary competence, for number of years = 10 × 12 × 1 = 120 participants and number of conflict = 0
- Specific: yes
- Measurable: yes (counting the number of conflicts)
- Attainable: partially (there are many variables involved and some depend on aspects not fully controlled by the action)
- Relevant: yes (to promote the well-being of IT staff and IT users)
- Time-related: yes (one year)
Appendix C
A Universidade e a COVID-19 Pandemic:
An interviewee who has no training in IT responded: “IT at the University now plays a central role in both administrative and academic actions. From an administrative point of view, meetings are no longer face-to-face and have become remote with different platforms. The university must contract institutional systems that can guarantee access and security of information. From an academic point of view, remote pedagogical approaches are necessary and the reality of everyday life in the classroom is initially replaced by 100% remote interventions, with the prospect of adopting a hybrid model (face-to-face/remote)). This aspect is more complicated, as it involves the training of teachers and students to access the platforms. Besides, students in a situation of social vulnerability will require strong State intervention to support them.”
The interviewee with formal education in the technological area replied: “With regard to IT in the Institution and in universities in general, I believe that the Covid-19 pandemic impacts on several aspects:
- From the point of view of development professionals and even IT support, there is a need to be more prepared for remote work, since there is unpredictability in relation to live working conditions. It is necessary that they have more access to mobile equipment (notebooks) that can be used at work and at home and/or that conditions are given so that they have equipment and adequate connectivity in their homes. The opportunity to work remotely is also an important factor for the quality of life of professionals, so one should explore hybrid work mechanisms (face-to-face/remote) at least for part of the team, depending on the activity and considering the preference of the professional, when possible
- From an infrastructure point of view, the use of more virtual servers, in the cloud, should be evaluated.
- From the point of view of infrastructure for teachers and other professionals, equipment and mobile infrastructure should also be prioritized whenever possible, with the purchase of devices such as notebooks or ensuring remote secure access to equipment installed at the university.
- From the students’ point of view, especially in relation to those in a vulnerable situation, there is a need for loan and management mechanisms for more equipment under some level of responsibility of the university. Or support the acquisition of equipment and communication infrastructure by these students.
- More investment is needed in VPN (Virtual Private Network) and security solutions, given the increase in remote access. In addition, it is necessary to invest in backup solutions and guarantee that university data is protected and safe, even with the expansion of remote access. Avoid risk that the data is not only on mobile devices, external or that have no control/management of the university
- In general, there is an increase in responsibilities for the university’s IT, because in addition to supporting the existing infrastructure within its physical facilities, there is a significant increase in the need for infrastructure and support for remote access for servers and students, which will increase the workload. IT managers must plan the acquisition and use of new software or remote support procedures. Including to help maintain physical distance, in the most critical moment.”
The advent of the pandemic raised the level of relevance of this study. Organizations in different segments depend more than ever on information technology. Public organizations that make good use of IT and its governance can offer better quality services to citizens.
References
- Wilkin, C.; Campbell, J. Corporate governance of IT: A case study in an Australian government department. In Proceedings of the 14th Pacific Asia Conference on Information Systems, Taipei, Taiwan, 9–12 July 2010. [Google Scholar]
- Qassimi, N.A.; Rusu, L. IT governance in a public organization in a developing country: A case study of a governmental organization. Procedia Comput. Sci. 2015, 64, 450–456. [Google Scholar] [CrossRef][Green Version]
- Turel, O.; Liu, P.; Bart, C. Board-level information technology governance effects on organizational performance: The roles of strategic alignment and authoritarian governance style. Inf. Syst. Manag. 2017, 34, 117–136. [Google Scholar] [CrossRef]
- Nunes, D.; Rosa, I.; Silva, M.M. Improving IT strategic plan for the Portuguese public administration. In Proceedings of the 15th International Conference on Business Informatics, Vienna, Austria, 15–18 July 2013. [Google Scholar]
- De Haes, S.; Huygh, T.; Joshi, A.; Caluwe, L. National corporate governance codes and IT governance transparency in annual reports. J. Glob. Inf. Manag. 2019, 27, 91–118. [Google Scholar] [CrossRef]
- Safari, M.R.; Jiang, Q. The theory and practice of IT governance maturity and strategies alignment: Evidence from banking industry. J. Glob. Inf. Manag. 2018, 26, 127–146. [Google Scholar] [CrossRef]
- Levstek, A.; Hovelja, T.; Pucihar, A. IT governance mechanisms and contingency factors: Towards an adaptive IT governance model. J. Manag. Inf. Hum. Resour. 2018, 51, 286–310. [Google Scholar] [CrossRef]
- Vugec, D.S.; Spremić, M.; Bach, M.P. IT governance adoption in banking and insurance sector: Longitudinal case study of COBIT use. Int. J. Qual. Res. 2017, 11, 691–716. [Google Scholar] [CrossRef]
- Weill, P.; Ross, J.W. IT Governance: How Top Performers Manage IT Decision Rights for Superior Results. Book Review. Int. J. Electron. Gov. Res. 2005, 1, 63–67. Available online: https://www.researchgate.net/publication/236973378_IT_Governance_How_Top_Performers_Manage_IT_Decision_Rights_for_Superior_Results (accessed on 18 August 2019).
- Willson, P.; Pollard, C. Exploring IT governance in theory and practice in a large multi-national organisation in Australia. Inf. Syst. Manag. 2009, 26, 98–109. [Google Scholar] [CrossRef]
- Pereira, R.; da Silva, M.M. A literature review: IT governance guidelines and areas. In Proceedings of the 6th International Conference on Theory and Practice of Electronic Governance, Albany, NY, USA, 22–25 October 2012. [Google Scholar]
- Bouayad, H.; Benabbou, L.; Berrado, A. An analytic hierarchy process-based approach for information technology governance framework selection. In Proceedings of the 12th International Conference on Intelligent Systems: Theories and Applications, EMI Rabat, Marocco, 24–25 October 2018. [Google Scholar]
- Nielsen, M.M. Governance lessons from Denmark’s digital transformation. In Proceedings of the 20th Annual International Conference on Digital Government Research, Dubai, UAE, 18–20 June 2019. [Google Scholar]
- Maes, K.; De Haes, S.; Van Grembergen, W. How IT enabled investments bring value to the business: A literature review. In Proceedings of the 44th Hawaii International Conference on System Sciences, Kauai, HI, USA, 4–7 January 2011. [Google Scholar]
- Larsen, M.H.; Pedersen, M.K.; Viborg Andersen, K. IT Governance: Reviewing 17 IT governance tools and analysing the case of novozymes A/S. In Proceedings of the 39th Hawaii International Conference on System Sciences, Kauai, HI, USA, 4–7 January 2006. [Google Scholar] [CrossRef]
- Janahi, L.; Griffiths, M.; Al-Ammal, H. A conceptual model for IT governance in public sectors. In Proceedings of the 4th International Conference on Future Generation Communication Technologies, Bedfordshire Luton, UK, 29–31 July 2015. [Google Scholar]
- Othman, M.F.I.; Chan, T. Barriers to formal IT governance practice—Insights from a qualitative study. In Proceedings of the 46th Hawaii International Conference on System Sciences, Maui, Wailea, HI, USA, 7–10 January 2013. [Google Scholar]
- Bartens, Y.; De Haes, S.; Lamoen, Y.; Schulte, F.; Voss, S. On the way to a minimum baseline in IT governance: Using expert views for selective implementation of COBIT 5. In Proceedings of the 48th Hawaii International Conference on System Sciences, Kauai, HI, USA, 5–8 January 2015. [Google Scholar]
- Barrera, S.M.B.; Kim, K.; Yoon, H.; Hwang, J. IT governance effectiveness and its influence on innovation product and process. In Proceedings of the Portland International Conference for Management of Engineering and Technology, Honolulu, HI, USA, 3–6 January 2018. [Google Scholar]
- Da Silva, C.J.N.; Ribeiro, Q.A.D.S.; Soares, M.S.; Nascimento, R.P.C. ICT governance: A view of adoption of best practices in enterprises of Sergipe state. In Proceedings of the XV Brazilian Symposium on Information Systems, Aracaju, Brazil, 20–24 May 2019. [Google Scholar]
- Alonso, I.A.; Verdún, J.C.; Caro, E.T. Description of the structure of the IT demand management process framework. Int. J. Inf. Manag. 2017, 37, 1461–1473. [Google Scholar] [CrossRef]
- Kizito, M. Transdisciplinarity and information systems: IT governance in the digitalisation of healthcare. Proceedings 2017, 1, 175. [Google Scholar] [CrossRef]
- Veerankutty, F.; Ramayah, T.; Ali, N.A. Information technology governance on audit technology performance among malaysian public sector auditors. Soc. Sci. 2018, 7, 124. [Google Scholar] [CrossRef]
- Ajayi, B.A.; Hussin, H. IT governance from practitioners’ perspective: Sharing the experience of a Malaysian university. J. Theor. Appl. Inf. Technol. 2016, 88, 219–230. [Google Scholar]
- Borges, G.C.; Simao, J.B.; Miani, R.S. Exploratory analysis of ICT best practices for Brazilian federal universities. In Proceedings of the 35th Conference of the Chilean Computer Science Society, Valparaíso, Chile, 10–14 October 2016. [Google Scholar]
- Delport, P.M.J.; Von Solms, R.; Gerber, M. Towards corporate governance of ICT in local government. In Proceedings of the 11th International School of Tanganyika-Africa Week Conference, Durban, South Africa, 11–13 May 2016. [Google Scholar]
- Ngoma, M.; Erasmus, W. Maturity of IT governance in the South African public sector. In Proceedings of the 25th International Association for Management of Technology Conference Technology—Future Thinking, Orlando, FL, USA, 15–19 May 2016. [Google Scholar]
- Mamboko, P.; Zhou, M.; Tsokota, T.; Mhaka, C. IT governance: Status and level of implementation in Zimbabwean urban local authorities. Eur. J. Bus. Manag. 2015, 7, 173–179. Available online: https://iiste.org/Journals/index.php/EJBM/article/viewFile/18891/19361 (accessed on 18 August 2019).
- Ahlan, A.R.; Arshad, Y.; Ajayi, B.A. IT governance in a Malaysian public institute of higher learning and intelligent decision-making support system solution. Intell. Syst. Ref. Libr. 2014, 55, 19–33. [Google Scholar] [CrossRef]
- Arshad, Y.; Ahlan, A.R.; Ajayi, B.A. Intelligent IT governance decision-making support framework for a developing country’s public university. Intell. Decis. Technol. 2014, 8, 131–146. [Google Scholar] [CrossRef]
- Merriam, S.B. Qualitative Research: A Guide to Design and Implementation; Revised and expanded from Qualitative research and case study applications in education; Jossey-Bass: San Francisco, CA, USA, 2009. [Google Scholar]
- Charmaz, K. A Construção da Teoria Fundamentada: Guia Prático Para Análise Qualitativa; Tradução de Joice Elias Costa.Artmed: Porto Alegre, Brasil, 2009. [Google Scholar]
- Patton, M.Q. Qualitative Research and Evaluation Method; Sage: Thousand Oaks, CA, USA, 2002. [Google Scholar]
- Stray, V.; Sjøberg, D.I.K.; Dybå, T. The daily stand-up meeting: A grounded theory study. J. Syst. Softw. 2016, 114, 101–124. [Google Scholar] [CrossRef]
- Information Technology Secretariat of the Ministry of Planning, Budget and Management. Guia de Governança de Tecnologia da Informação e Comunicação do Sistema de Administração dos Recursos de Tecnologia da Informação, 1st ed.; STI/MPOG: Brasilia, Brazil, 2015. Available online: http://sisp.gov.br/govtic/wiki/download/file/GuiaGovTIC (accessed on 18 August 2019).
- Information Systems Audit and Control Association. Cobit 5: A Business Framework for the Governance and Management of Enterprise IT, 1st ed.; ISACA: Rolling Meadows, IL, USA, 2012; Available online: http://www.isaca.org/COBIT/Documents/COBIT-5-Introduction.pdf (accessed on 18 August 2019).
- Glaser, B.G. Basics of Grounded Theory Analysis: Emergence vs. Forcing; Sociology Press: Mill Valley, CA, USA, 1992. [Google Scholar]
- Goulding, C. Grounded theory: The missing methodology on the interpretive agenda. Qual. Mark. Res. 1998, 1, 50–57. [Google Scholar] [CrossRef]
- Santos, R.E.S.; Silva, F.Q.B.; Magalhães, C.V.C.; Monteiro, C.V.F. Building a theory of job rotation in software engineering from an instrumental case study. In Proceedings of the 38th International Conference on Software Engineering, Austin, TX, USA, 14–22 May 2016. [Google Scholar]
- Peterson, R.R. Integration Strategies and Tactics for Information Technology Governance.; Idea Group Publishing: Hershey, PA, USA, 2003; pp. 37–80. [Google Scholar]
- Janssen, M.; Helbig, N. Innovating and changing the policy-cycle: Policy-makers be prepared! Gov. Inf. Q. 2018, 35, 99–105. [Google Scholar] [CrossRef]
- Sanchez, X.; Bayona-Oré, S. Strategic alignment between business and information technology in companies. In Proceedings of the 15th Iberian Conference on Information Systems and Technologies, Sevilla, Spain, 24–27 June 2020. [Google Scholar] [CrossRef]
- Marchão, J.; Reis, L.; Martins, P.V. Business areas and processes alignment in ICT framework. In Proceedings of the 15th Iberian Conference on Information Systems and Technologies, Sevilla, Spain, 24–27 June 2020. [Google Scholar] [CrossRef]
- Wautelet, Y. Using the RUP/UML business use case model for service development governance: A business and IT alignment based approach. In Proceedings of the 22nd Conference on Business Informatics, Antwerp, Belgium, 22–24 June 2020. [Google Scholar] [CrossRef]
- Chang, S.-l.; Chang, L.-M.; Liao, J.-C. Risk factors of enterprise internal control under the internet of things governance: A qualitative research approach. Inf. Manag. 2020, 57, 1–18. [Google Scholar] [CrossRef]
- Koltay, T. Quality of Open Research Data: Values, Convergences and Governance. Information 2020, 11, 175. [Google Scholar] [CrossRef]
- Guo, G.; Zhu, Y.; Yu, R.; Chu, W.C.-C.; Ma, D. A Privacy-preserving Framework with Self-governanceand Permission Delegation in Online Social Networks. IEEE Access 2020. [Google Scholar] [CrossRef]
- Solana-González, P.; Vanti, A.A.; Fontana, K.H.S. Multicriteria analysis of the compliance for the improvement of information security. J. Inf. Syst. Technol. Manag. 2019, 16. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).