A Group-Based Energy-Efficient Dual Priority Scheduling for Real-Time Embedded Systems
Abstract
1. Introduction
- The GEDP scheduling algorithm is presented for isolating different types of tasks to avoid disruption and decreasing energy consumption through reducing context switches in a real-time embedded system.
- The WCRT model is improved based on considering context switches’ overhead, and the improved WCRT model can enhance the accuracy of WCRT.
- To verify the effectiveness of the GEDP, the context switches’ statistics methods and the tasks’ energy consumption analysis methods are discussed. Furthermore, a physical experiment is set up on the Linux 2.6.32.5 kernel, which is modified to support GEDP, and four benchmarks are taken as testing applications.
2. Related Work
3. GEDP Scheduling
3.1. Scheduling Model
- is a normal priority assignment for the tasks.
- is a threshold priority assignment for the tasks.
- is a mapping of tasks into processes.
3.2. GEDP Algorithm
- (1)
- Grouping rule of system tasks: If the priority of task satisfies conditions and , then the task is a system task. Add task into the system task group, denoted as .
- (2)
- Grouping rule of application tasks: If the priority of the task satisfies conditions and , then the task is an application task. Add task into the application task group, denoted as .
| Algorithm 1: GEDP algorithm. |
 |
4. Schedulability Analysis and Threshold Priority Assignment
4.1. WCRT Analysis
- (1)
- The execution time of the task: The time overhead of voluntary context switches should be considered. Every time the task gives up the CPU, a voluntary context switch occurs;
- (2)
- Interference from other higher priority tasks: In this case, the time overhead of involuntary context switches should be considered. Each time a task is preempted, the preemption task will be switched first and then switches back to the current task. In this case, context switches occur twice.
- (3)
- Blocking from lower priority tasks caused by the threshold priority: If the lower priority task is running, the objective task cannot be preempted due to higher threshold priority, and this will result in blocking time.
4.2. Threshold Priority Assignment
| Algorithm 2: Threshold priority assignment. |
 |
4.3. Schedulability Analysis Tool
- Step 1:
- Enter the attributes of the task;
- Step 2:
- Click the “Add Task =>” button to add the task to the task list. If all tasks have been added, continue to Step 3; otherwise, repeat Step 1 to continue adding tasks;
- Step 3:
- If you are doing a non-threshold experiment, go to Step 4 directly. If you are doing a threshold experiment, check the “Open Threshold” check-box and click the “Comp Threshold =>” button to calculate the threshold priorities;
- Step 4:
- If the threshold calculation fails, click the “Clear” button to clear all the information and return to the first step to restart the operation; otherwise, click the “RUN” button to run all tasks;
- Step 5:
- Enter the task name, and click the “START” button to capture the statistical information when the task is running;
- Step 6:
- Click the “START” button to capture the tasks running information in the system. Repeat Step 5 and Step 6 to get the running information of the tasks at different times.
5. Results and Discussion
5.1. Experiment Setup
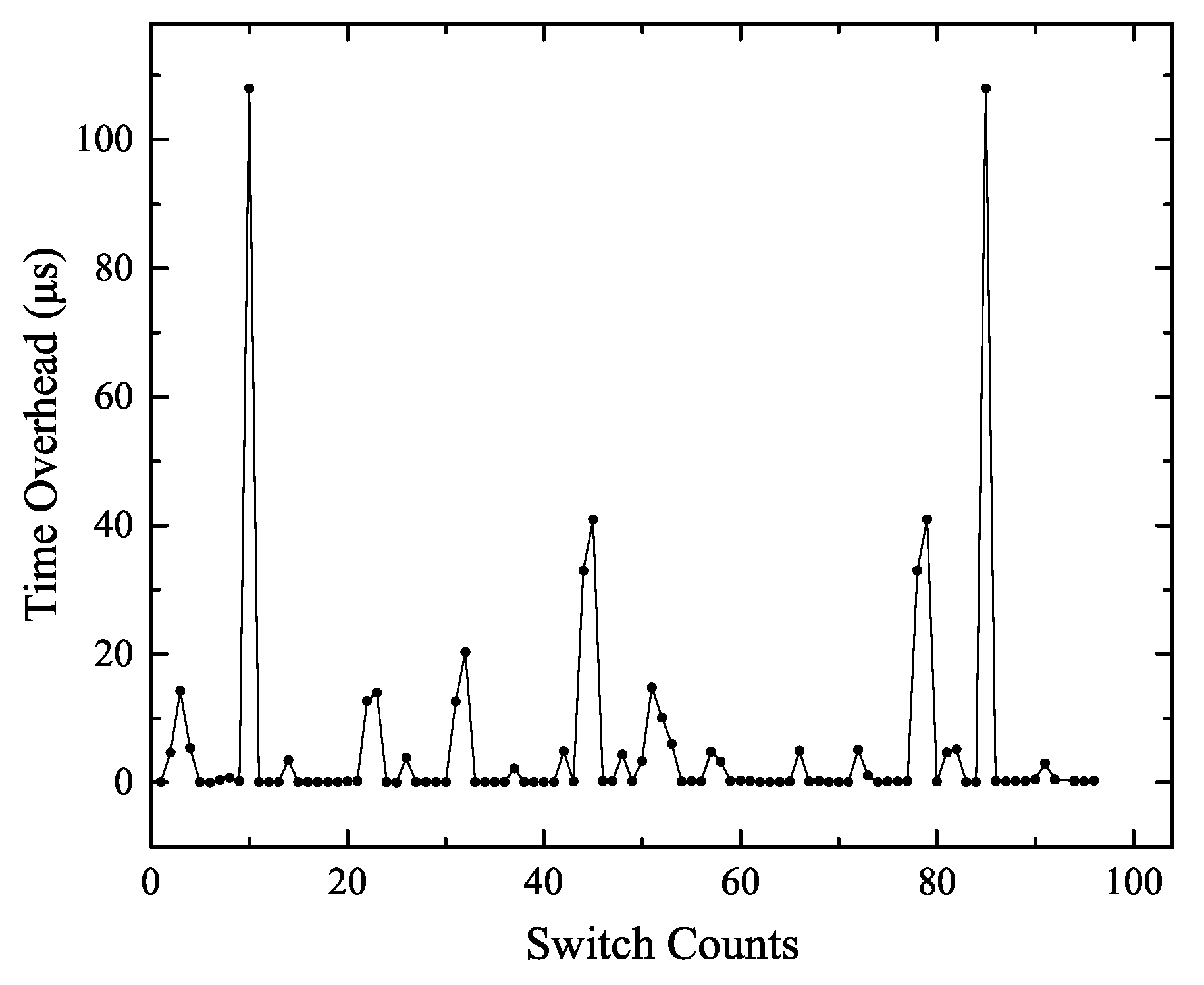
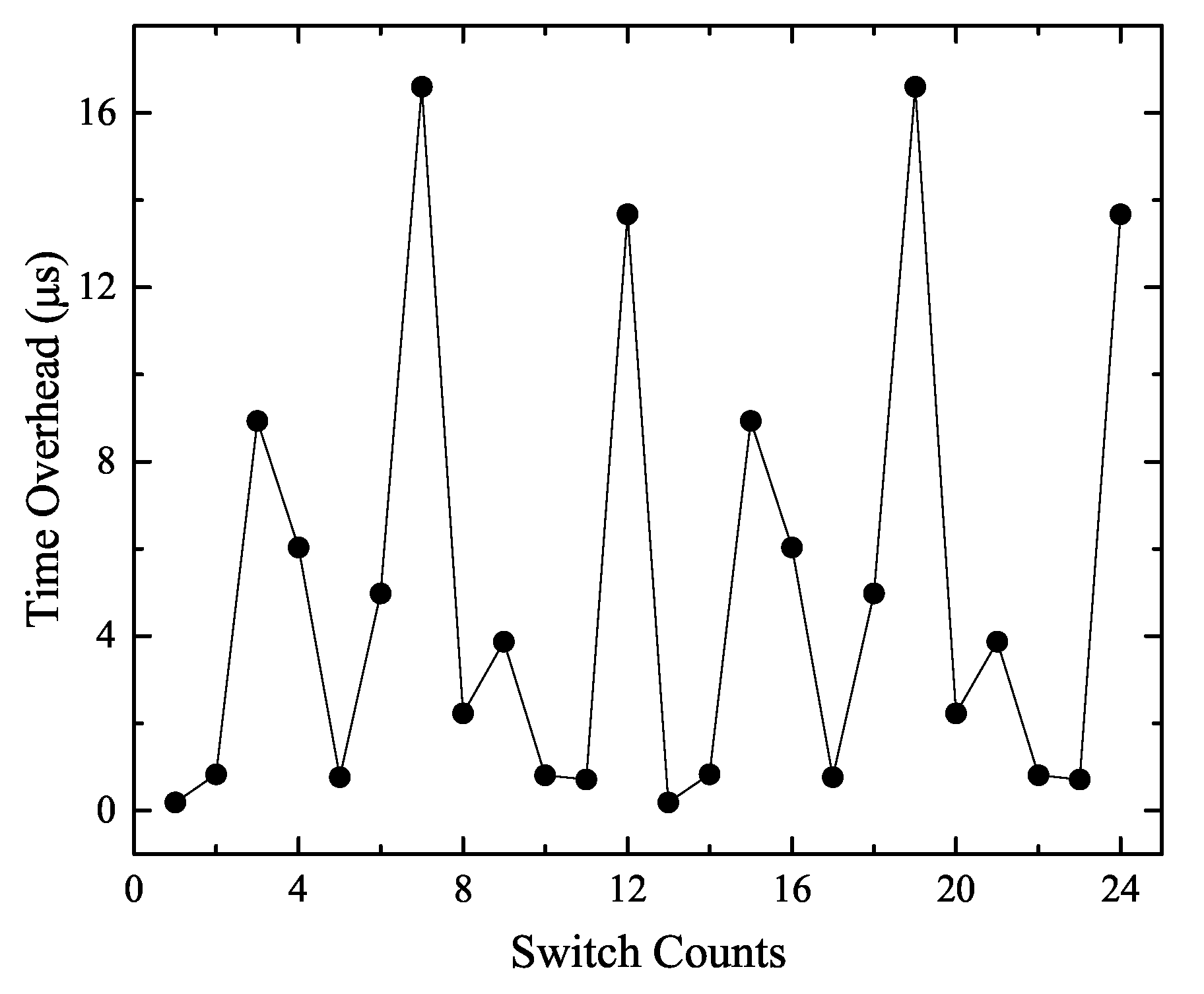
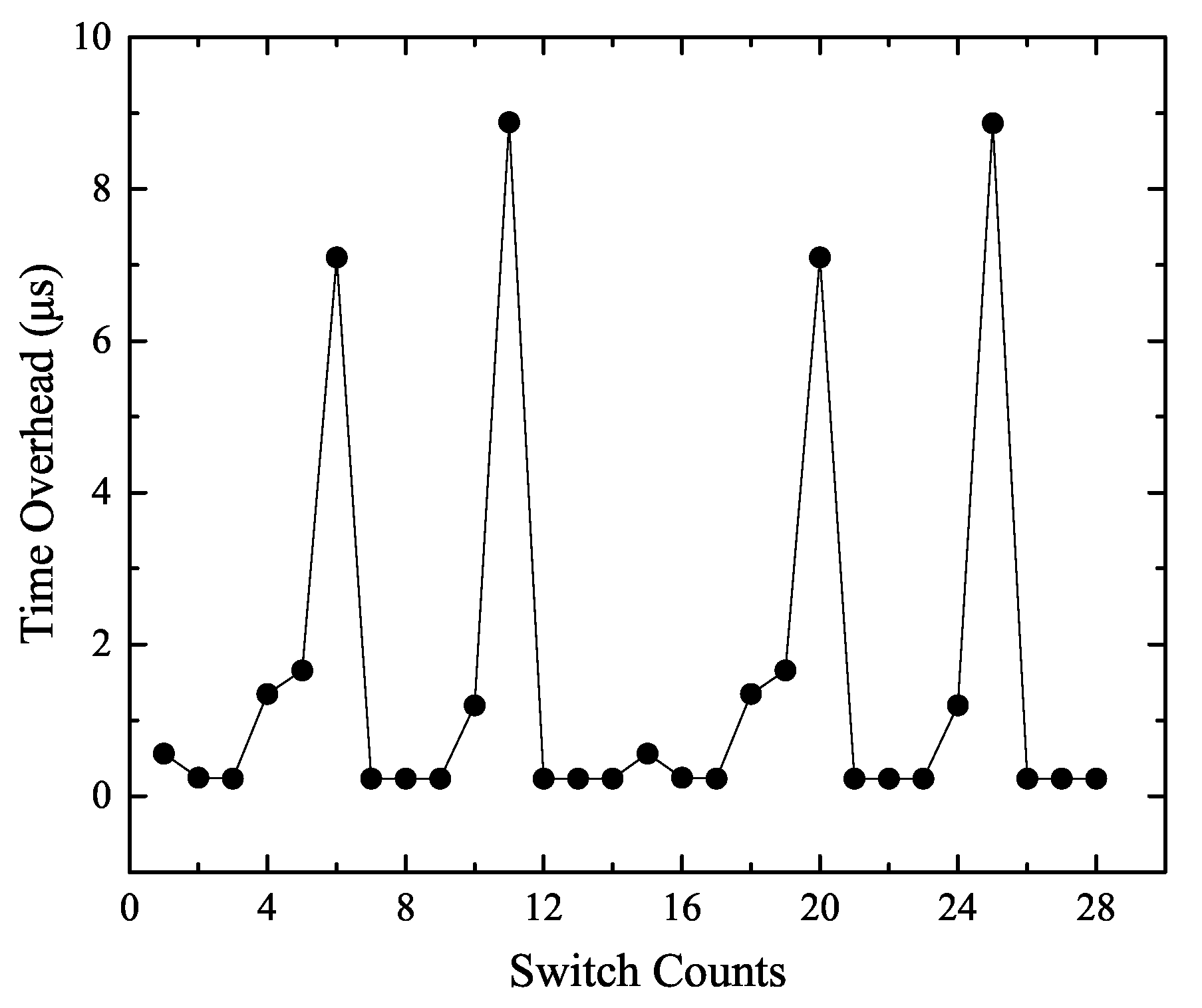
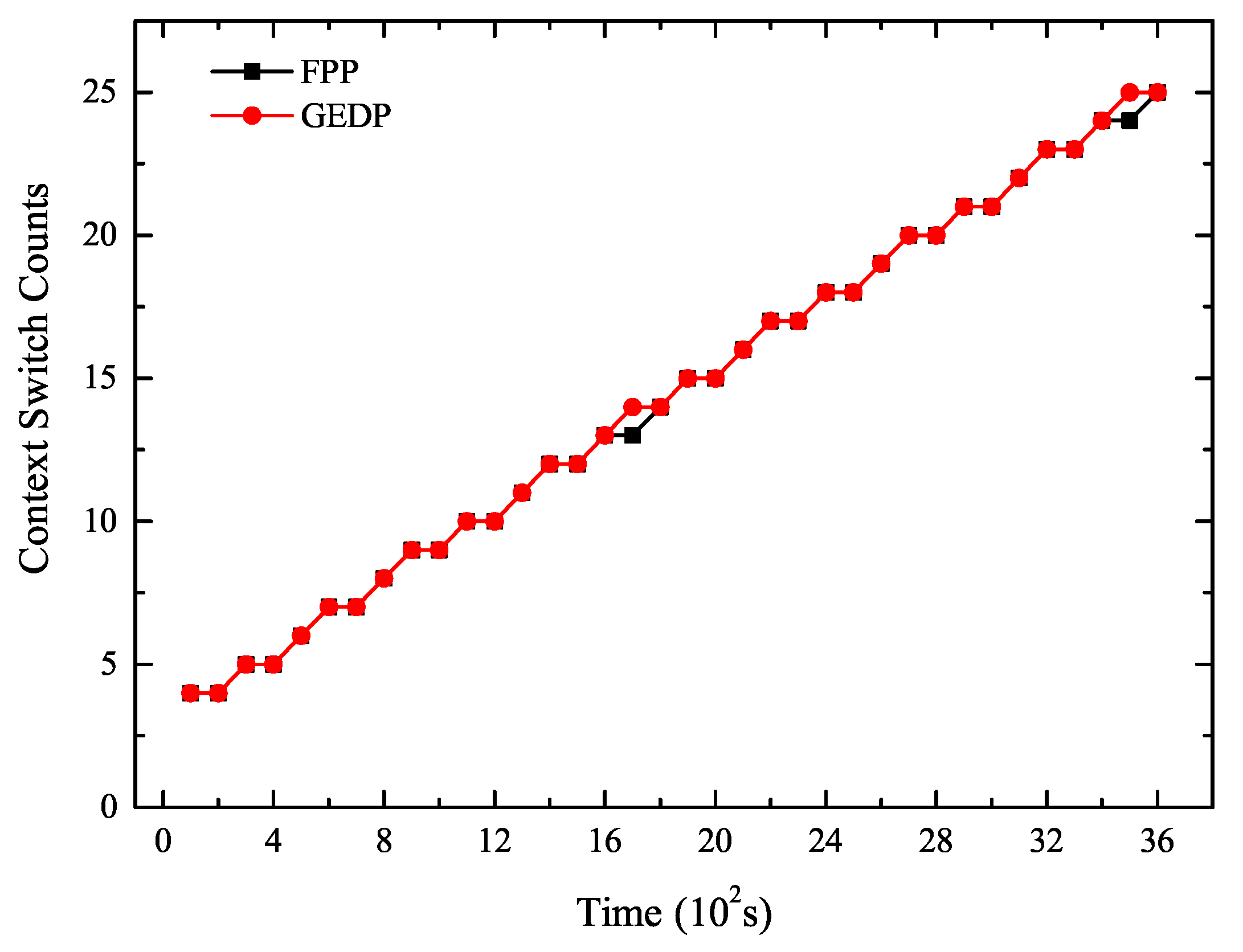
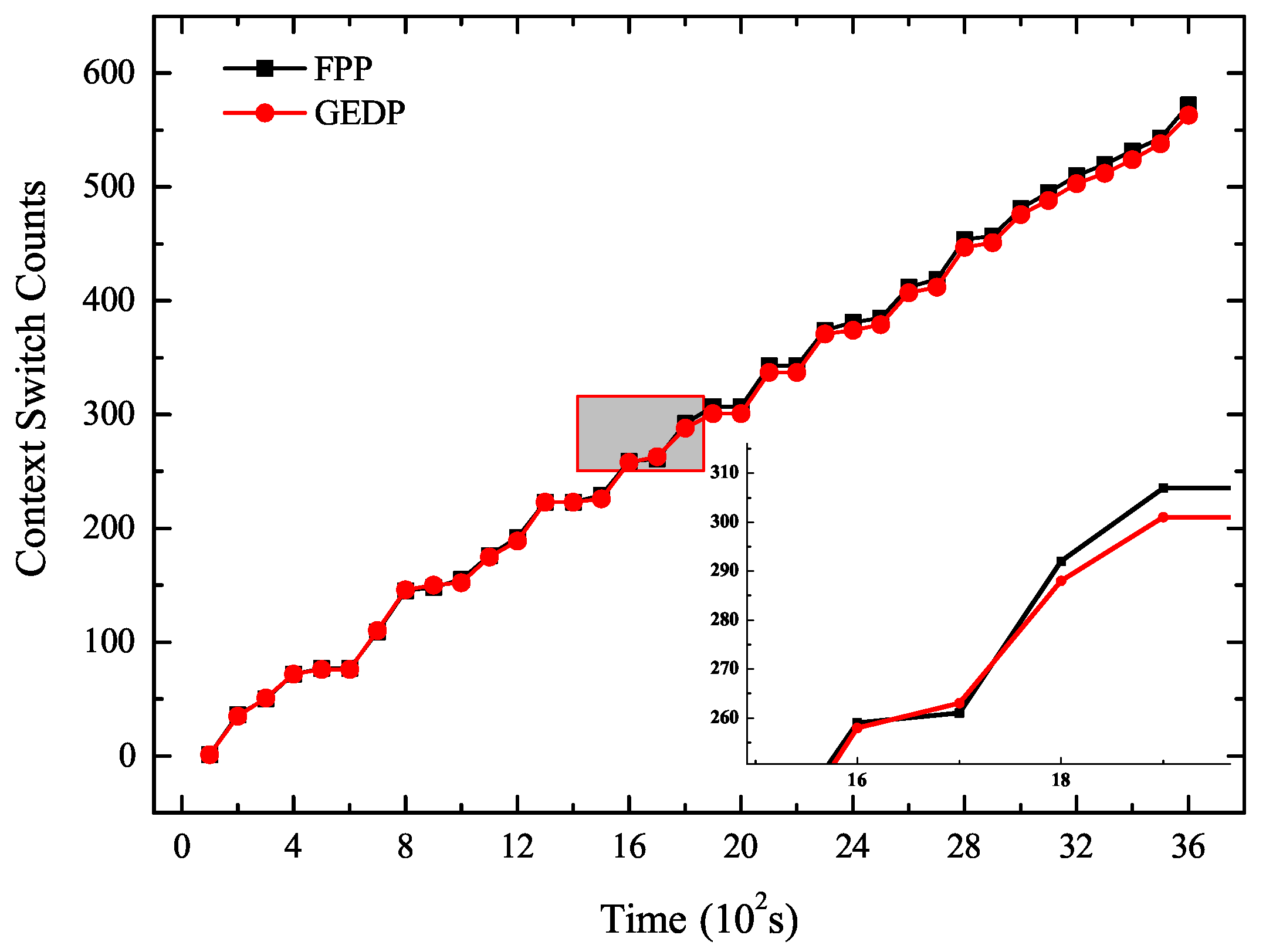
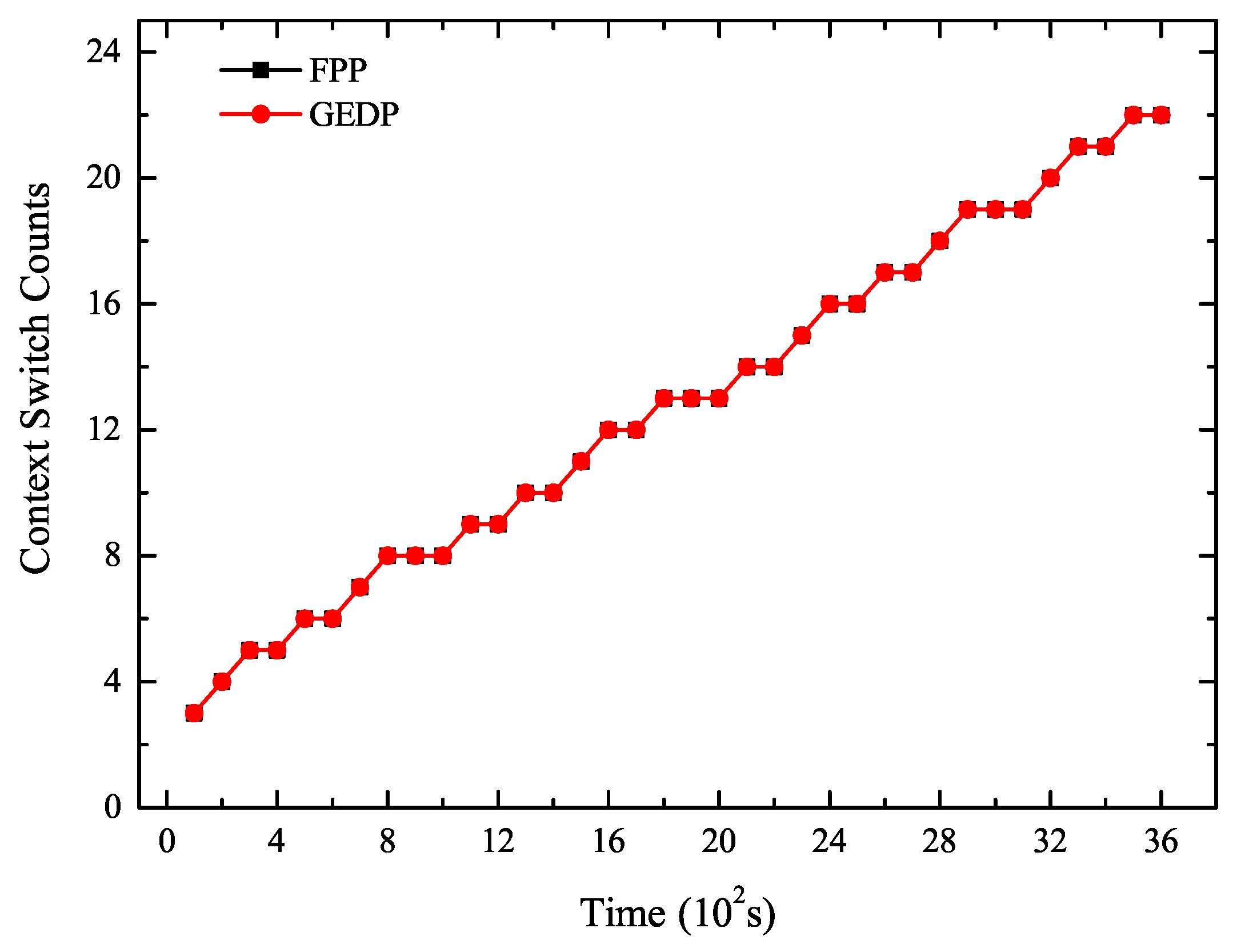
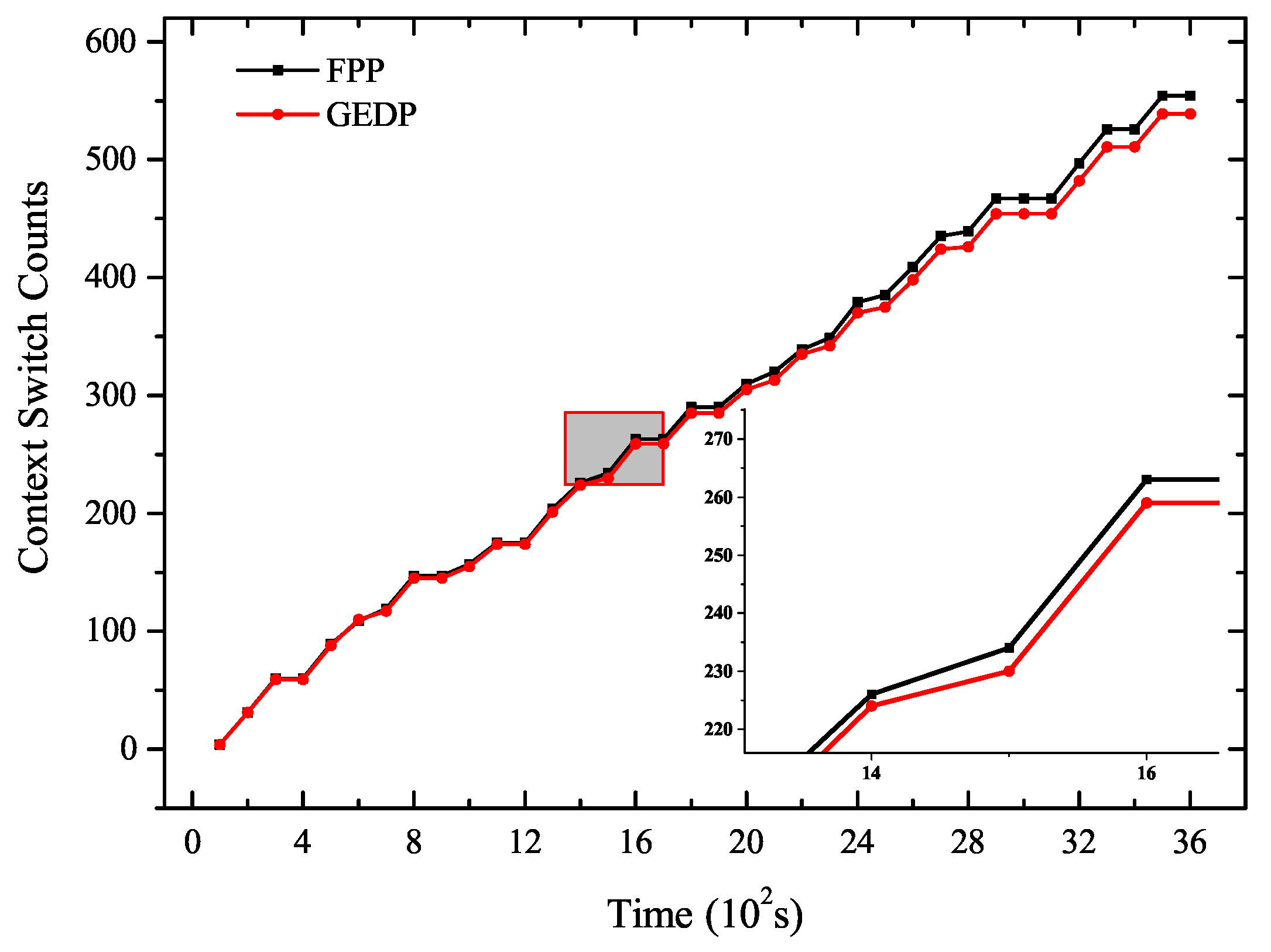
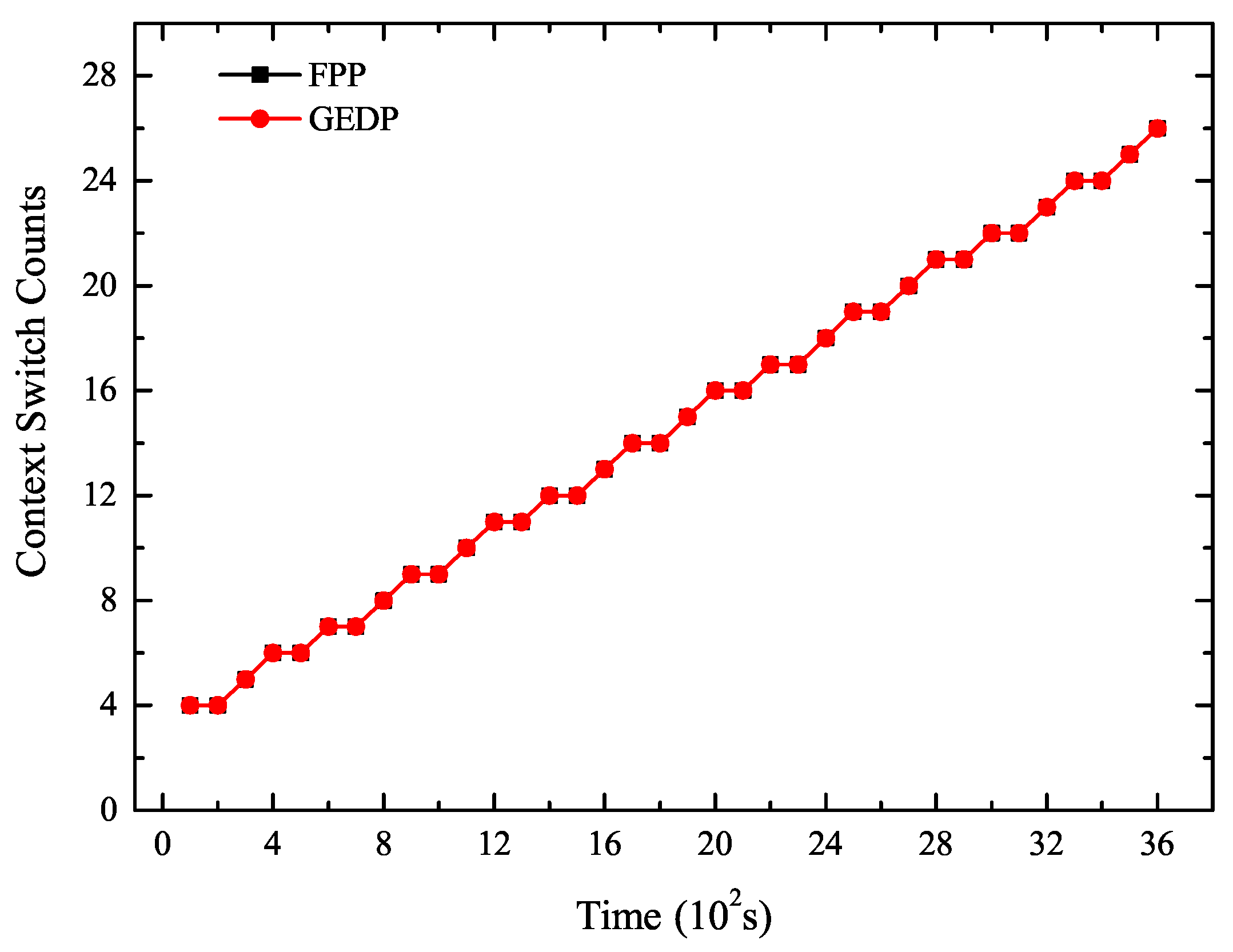
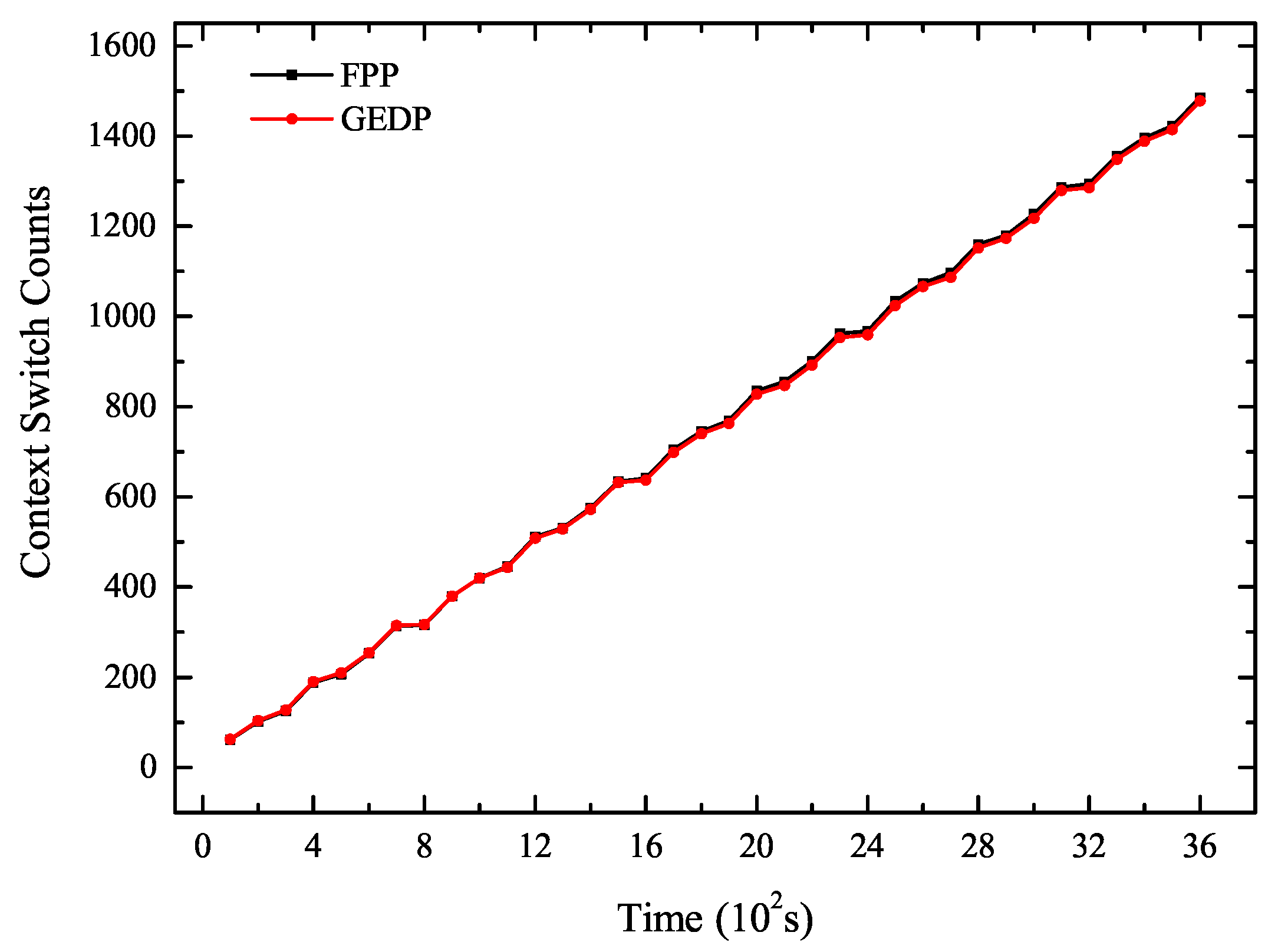
5.2. Experiment 1: The Number of Context Switches Analysis
5.3. Experiment 2: System Energy Consumption Analysis
- (1)
- Compared with FPP, the GEDP reduced energy consumption by 5910.98 J and reduced context switches 385 times. The energy consumption and the number of context switching under the GEDP were significantly reduced compared to FPP. This showed that GEDP was efficient to reduce context switches to optimize the system energy consumption.
- (2)
- The savings of energy consumption tended to increase as the number of context switches decreased. This was because the GEDP reduced more context switches, thus producing cumulative effects on saving energy.
- (3)
- For given benchmarks, the experiment results showed that GEDP provided gains (0.6% energy consumption and 1% context switches) over the previous scheduling FPP. It proved that reducing the number of context switches could decrease system energy consumption. However, affected by the physical experiment environment and different task attributes, different benchmarks may have different gains. We plan to study the relationship between benchmarks and gains in future work.
- (4)
- According to the results for total system energy consumption and context switches in Table 4, we could calculate that the average energy overhead of a context switch was about 15 J. The context switches’ energy overhead was related to memory accesses in saving/restoring the task context, as well as due to the additional cache misses resulting from a context switch. The context switch energy overhead was not constant.
6. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Norouzi, R.; Kosari, A.; Sabour, M.H. Real time estimation of impaired aircraft flight envelope using feedforward neural networks. Aerosp. Sci. Technol. 2019, 90, 434–451. [Google Scholar] [CrossRef]
- Kato, S.; Tokunaga, S.; Maruyama, Y.; Maeda, S.; Hirabayashi, M.; Kitsukawa, Y.; Monrroy, A.; Ando, T.; Fujii, Y.; Azumi, T. Autoware on board: Enabling autonomous vehicles with embedded systems. In Proceedings of the ACM/IEEE 9th International Conference on Cyber-Physical Systems, Porto, Portugal, 11–13 April 2018; pp. 287–296. [Google Scholar]
- Ikura, M.; Miyashita, L.; Ishikawa, M. Real-time Landing Gear Control System Based on Adaptive 3D Sensing for Safe Landing of UAV. In Proceedings of the IEEE/SICE International Symposium on System Integration (SII), Honolulu, HI, USA, 12–15 January 2020; pp. 759–764. [Google Scholar]
- Malewski, M.; Cowell, D.M.J.; Freear, S. Review of battery powered embedded systems design for mission-critical low-power applications. Int. J. Electr. 2018, 105, 893–909. [Google Scholar] [CrossRef]
- Xu, H.; Li, R.; Pan, C.; Keqin, L. Minimizing energy consumption with reliability goal on heterogeneous embedded systems. J. Parallel Distrib. Comput. 2019, 127, 44–57. [Google Scholar] [CrossRef]
- Tzilis, S.; Trancoso, P.; Sourdis, I. Energy-Efficient Runtime Management of Heterogeneous Multicores using Online Projection. ACM Trans. Archit. Code Optim. (TACO) 2019, 15, 1–26. [Google Scholar] [CrossRef]
- Wägemann, P.; Dietrich, C.; Distler, T.; Ulbrich, P.; Schroder-Preikschat, W. Whole-system worst-case energy-consumption analysis for energy-constrained real-time systems. In Proceedings of the Leibniz International Proceedings in Informatics, Barcelona, Spain, 3–6 June 2018; pp. 24–36. [Google Scholar]
- Li, J.; Shu, L.C.; Chen, J.J.; Li, G. Energy-efficient scheduling in nonpreemptive systems with real-time constraints. IEEE Trans. Syst. Man Cybern. Syst. 2012, 43, 332–344. [Google Scholar] [CrossRef]
- Dick, R.P.; Lakshminarayana, G.; Raghunathan, A.; Jha, N.K. Analysis of power dissipation in embedded systems using real-time operating systems. IEEE Trans. Computer-Aided Des. Integr. Circuit Syst. 2003, 22, 615–627. [Google Scholar] [CrossRef]
- Kada, B.; Kalla, H. An Efficient Fault-Tolerant Scheduling Approach with Energy Minimization for Hard Real-Time Embedded Systems. Cybern. Inf. Technol. 2019, 19, 45–60. [Google Scholar] [CrossRef]
- Carvalho, S.A.L.; Cunha, D.C.; Silva-Filho, A.G. Autonomous power management in mobile devices using dynamic frequency scaling and reinforcement learning for energy minimization. Microprocess. Microsyst. 2019, 64, 205–220. [Google Scholar] [CrossRef]
- Ahmed, I.; Zhao, S.; Trescases, O.; Betz, V. Automatic application-specific calibration to enable dynamic voltage scaling in FPGAs. IEEE Trans. Computer-Aided Des. Integr. Circ. Syst. 2018, 37, 3095–3108. [Google Scholar] [CrossRef]
- Zhou, M.; Cheng, L.; Antonio, M.; Wang, X.; Bing, Z.; Ali Nasseri, M.; Huang, K.; Knoll, A. Peak Temperature Minimization for Hard Real-Time Systems Using DVS and DPM. J. Circuits Syst. Comp. 2019, 28, 1950102. [Google Scholar] [CrossRef]
- Khan, H.; Bashir, Q.; Hashmi, M.U. Scheduling based energy optimization technique in multiprocessor embedded systems. In Proceedings of the International Conference on Engineering and Emerging Technologies, Edinburgh, UK, 16–19 July 2019; pp. 1–8. [Google Scholar]
- Zuniga, A.F.; Turner, M.F.; Rasky, D. Building an Economical and Sustainable Lunar Infrastructure to Enable Lunar Industrialization. In Proceedings of the AIAA SPACE and Astronautics Forum and Exposition, Orlando, FL, USA, 12–14 September 2017; p. 5148. [Google Scholar]
- Luhua, X.; Xianfeng, C.; Yuan, X. The Operations of China’s First Lunar Rover. In Proceedings of the SpaceOps 2012 Conference, Stockholm, Sweden, 11–15 June 2012; pp. 1–8. [Google Scholar]
- Wang, Y.; Saksena, M. Scheduling fixed-priority tasks with preemption threshold. In Proceedings of the Sixth International Conference on Real-Time Computing Systems and Applications, Hong Kong, China, 13–15 December 1999; pp. 328–335. [Google Scholar]
- Hosseinimotlagh, S.; Khunjush, F.; Hosseinimotlagh, S. A cooperative two-tier energy-aware scheduling for real-time tasks in computing clouds. In Proceedings of the 22nd Euromicro International Conference on Parallel, Distributed, and Network-Based Processing, Turin, Italy, 12–14 February 2014; pp. 178–182. [Google Scholar]
- Davis, R.I.; Burns, A. Priority assignment for global fixed priority pre-emptive scheduling in multiprocessor real-time systems. In Proceedings of the 30th IEEE Real-Time Systems Symposium, Washington, DC, USA, 1–4 December 2009; pp. 398–409. [Google Scholar]
- Zhu, D.; Melhem, R.; Mossé, D. The effects of energy management on reliability in real-time embedded systems. In Proceedings of the IEEE/ACM International conference on Computer-aided design, San Jose, CA, USA, 7–11 November 2004; pp. 35–40. [Google Scholar]
- Deepaksubramanyan, B.S.; Nunez, A. Analysis of subthreshold leakage reduction in CMOS digital circuits. In Proceedings of the 50th Midwest Symposium on Circuits and Systems, Montreal, QC, Canada, 5–8 August 2007; pp. 1400–1404. [Google Scholar]
- Fataniya, B.; Patel, M. Survey on different method to improve performance of the round robin scheduling algorithm. Int. J. Res. Sci. Eng. Technol. 2018, 6, 69–77. [Google Scholar]
- Ouni, B.; Belleudy, C.; Senn, E. Accurate energy characterization of OS services in embedded systems. EURASIP J. Embedded Syst. 2012, 2012, 1–16. [Google Scholar] [CrossRef]
- Liu, F.; Guo, F.; Solihin, Y.; Kim, S.; Eker, A. Characterizing and modeling the behavior of context switch misses. In Proceedings of the 17th International Conference on Parallel Architectures and Compilation Techniques, Toronto, ON, Canada, 25–29 October 2008; pp. 91–101. [Google Scholar]
- David, F.M.; Carlyle, J.C.; Campbell, R.H. Context switch overheads for Linux on ARM platforms. In Proceedings of the Workshop on Experimental Computer Science, San Diego, CA, USA, 25–26 June 2007; pp. 1–7. [Google Scholar]
- Acquaviva, A.; Benini, L.; Riccó, B. Energy characterization of embedded real-time operating systems. In Compilers and Operating Systems for Low Power; Springer: Cham, Switzerland, 2003; pp. 53–73. [Google Scholar]
- Behera, H.S.; Mohanty, R.; Nayak, D. A New Proposed Dynamic Quantum with Re-Adjusted Round Robin Scheduling Algorithm and Its Performance Analysis. arXiv 2011, arXiv:1103.3831. [Google Scholar] [CrossRef]
- Raveendran, B.K.; Prasad, K.D.; Balasubramaniam, S.; Gurunarayanan, S. Variants of priority scheduling algorithms for reducing context-switches in real-time systems. In Proceedings of the 8th International Conference on Distributed Computing and Networking, Guwahati, India, 27–30 December 2006; pp. 466–478. [Google Scholar]
- Wang, Y.; Saksena, M. Scheduling Fixed-Priority Tasks with Preemption Threshold An Attractive Technology? Montreal: Concordia University. 1999. Available online: http://www.cs.utah.edu/~regehr/reading/open_papers/wang_saksena_attractive.pdf (accessed on 10 January 2020).
- John Burkardt. C Software. Available online: https://people.sc.fsu.edu/~jburkardt/c_src/ (accessed on 12 January 2020).




| Tasks | ||||||
|---|---|---|---|---|---|---|
| 6 | 32 | 17 | 10 | 17 | 18 | |
| 4 | 48 | 32 | 21 | 12 | 17 | |
| 2 | 48 | 8 | 20 | 8 | 13 | |
| 5 | 40 | 17 | 43 | 6 | 11 |
| Tasks | ||||||
|---|---|---|---|---|---|---|
| Linpack_bench | 34 | 165 | 160 | 53 | 53 | 155 |
| Memory_test | 60 | 245 | 243 | 70 | 53 | 241 |
| Whetstone | 26 | 190 | 185 | 62 | 45 | 181 |
| Mxm | 59 | 160 | 100 | 45 | 45 | 86 |
| Times | Linpack_bench | Memory_test | Whetstone | Mxm | ||||
|---|---|---|---|---|---|---|---|---|
| FPP | GEDP | FPP | GEDP | FPP | GEDP | FPP | GEDP | |
| T1 | 798 | 803 | 592 | 582 | 580 | 569 | 1496 | 1509 |
| T2 | 802 | 793 | 594 | 579 | 576 | 561 | 1511 | 1504 |
| T3 | 807 | 801 | 587 | 576 | 567 | 566 | 1532 | 1501 |
| T4 | 797 | 797 | 600 | 578 | 565 | 576 | 1531 | 1522 |
| T5 | 804 | 806 | 594 | 588 | 559 | 565 | 1539 | 1509 |
| T6 | 801 | 822 | 576 | 573 | 569 | 527 | 1518 | 1524 |
| T7 | 814 | 803 | 585 | 576 | 561 | 521 | 1533 | 1539 |
| T8 | 812 | 804 | 592 | 579 | 587 | 570 | 1592 | 1545 |
| T9 | 802 | 804 | 582 | 580 | 575 | 570 | 1538 | 1530 |
| T10 | 796 | 800 | 592 | 586 | 571 | 528 | 1522 | 1527 |
| Sampling | Context Switches | Energy Consumption (J) | ||
|---|---|---|---|---|
| FPP | GEDP | FPP | GEDP | |
| S0 | 1029 | 1026 | 30,278 | 30,222 |
| S4 | 1056 | 1047 | 30,042 | 30,280 |
| S8 | 1049 | 1047 | 26,082 | 25,763 |
| S12 | 1074 | 1079 | 26,143 | 25,958 |
| S16 | 1054 | 1045 | 26,101 | 25,837 |
| S20 | 1087 | 1069 | 26,336 | 26,209 |
| S24 | 1094 | 1085 | 26,295 | 26,100 |
| S28 | 1095 | 1098 | 26,788 | 26,454 |
| S32 | 1072 | 1058 | 26,223 | 25,797 |
| S36 | 1100 | 1073 | 26,624 | 25,949 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ge, Y.; Liu, R. A Group-Based Energy-Efficient Dual Priority Scheduling for Real-Time Embedded Systems. Information 2020, 11, 191. https://doi.org/10.3390/info11040191
Ge Y, Liu R. A Group-Based Energy-Efficient Dual Priority Scheduling for Real-Time Embedded Systems. Information. 2020; 11(4):191. https://doi.org/10.3390/info11040191
Chicago/Turabian StyleGe, Yongqi, and Rui Liu. 2020. "A Group-Based Energy-Efficient Dual Priority Scheduling for Real-Time Embedded Systems" Information 11, no. 4: 191. https://doi.org/10.3390/info11040191
APA StyleGe, Y., & Liu, R. (2020). A Group-Based Energy-Efficient Dual Priority Scheduling for Real-Time Embedded Systems. Information, 11(4), 191. https://doi.org/10.3390/info11040191





