S.O.V.O.R.A.: A Distributed Wireless Operating System
Abstract
1. Introduction
2. Wireless Distributed Systems
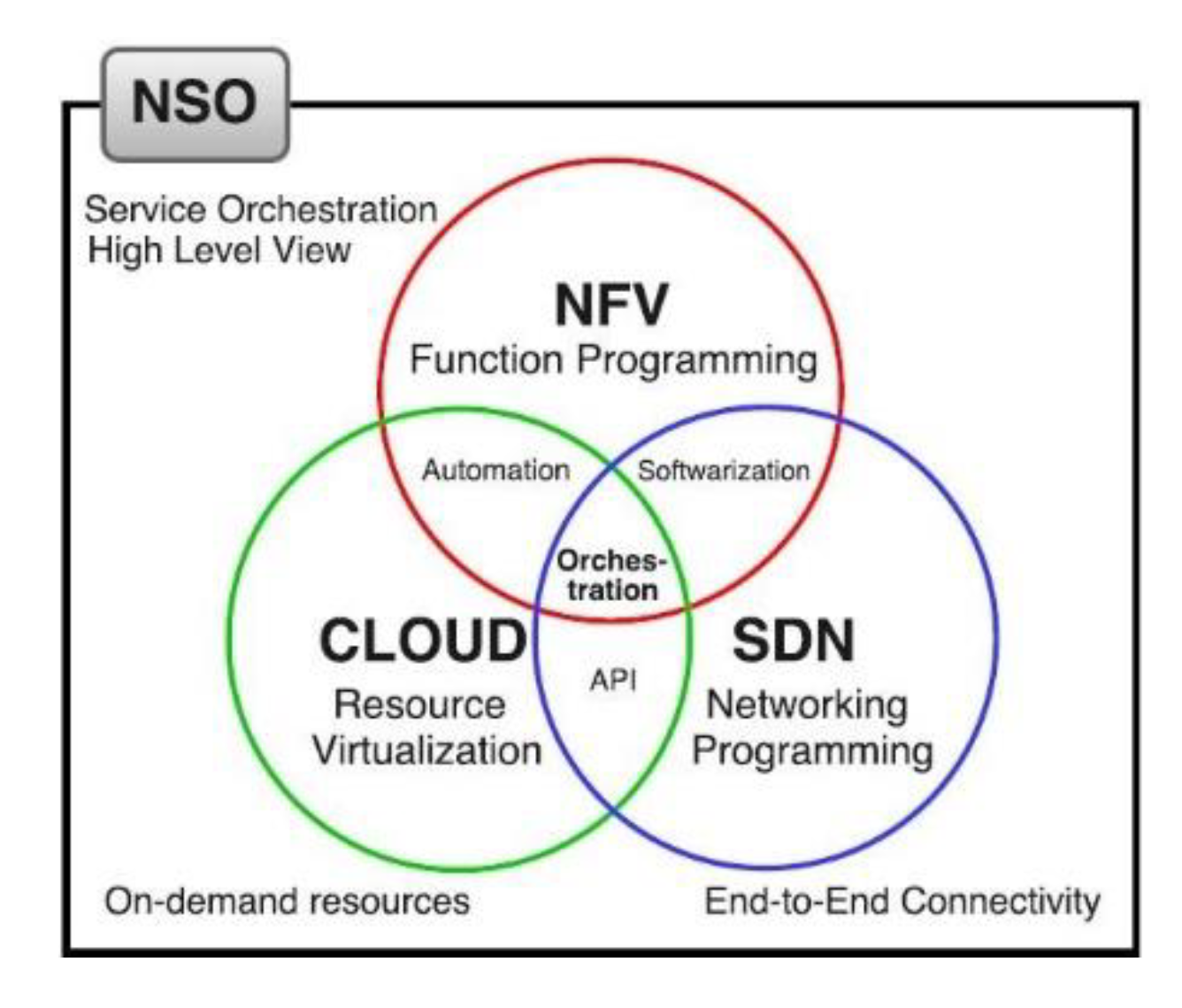
2.1. Network Management
2.2. Distributed Architectures
2.2.1. MANET Mobile Ad Hoc Network
2.2.2. Fog Computing
2.2.3. Operating Systems for Distributed Systems
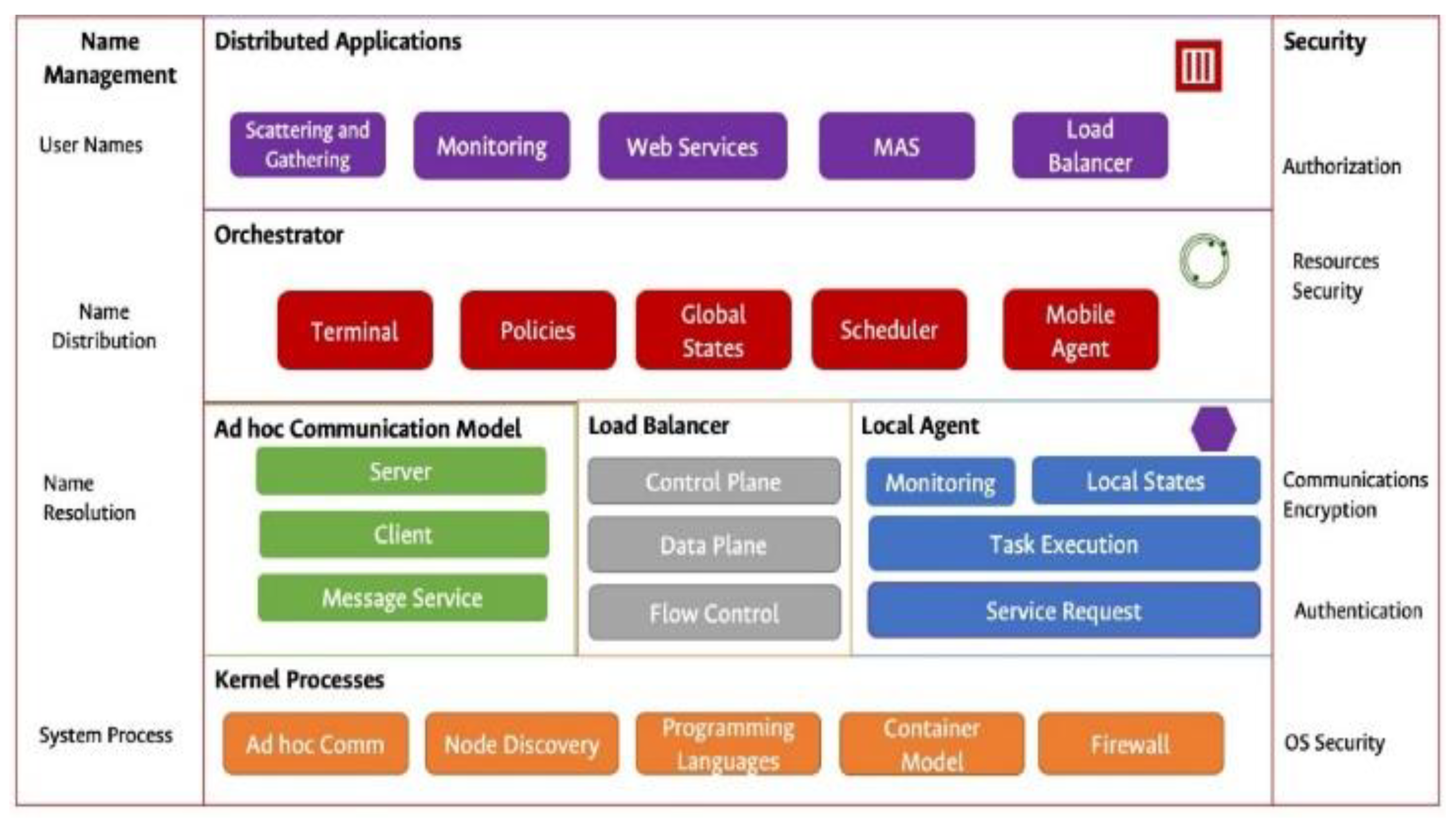
3. S.O.V.O.R.A. Wireless Distributed Systems
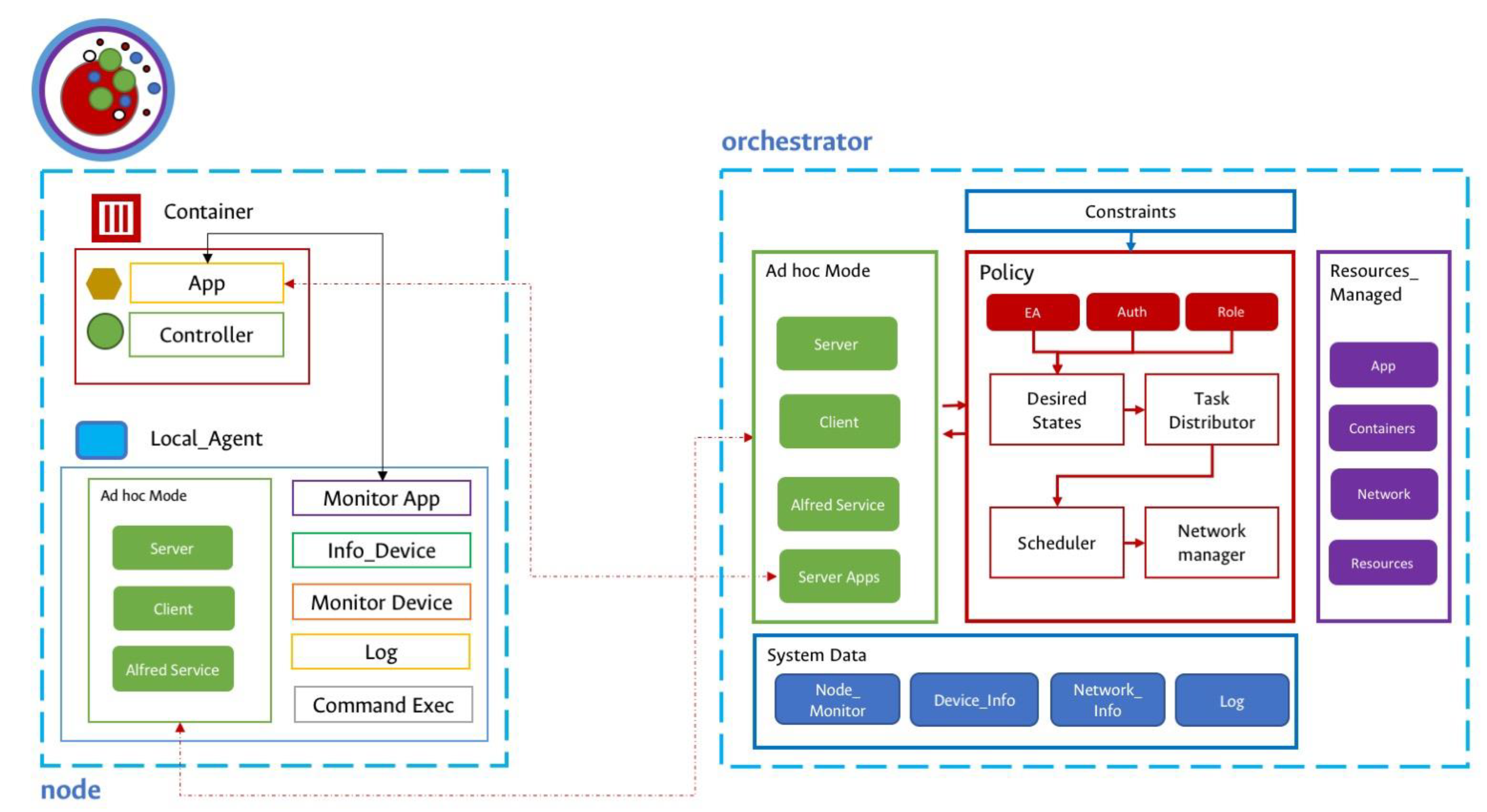
3.1. Architecture
- Nodo (Node): Represents the physical devices.
- GGlobal (Ggroup): Represents a gorup of physicial nodes on the same MANET.
- Group (Group): Represents a set of local agents.
- Local Agent (Agl): Represents an instance of local agent on the physical node. On each node can exist one or more instances of LA.
- Orchesrator (Orch): Represents a global controller the system. On each MANET cluster can exist one or more instances.
3.2. The Orchestrator
- Server: It is a microservice that create a server multi-thread for the communication between nodes and applications.
- Client: A microservice managed by the local agent that creates a multi-thread client to collect information about the node applications, send messages to deploy applications, and set the throughput and the resources consumption in each node.
- B.A.T.M.A.N. protocol: Proactive network protocol that works on ad hoc mode on IEEE 802.11 standard. The Protocol allows for communication between nodes and orchestrator due to the best route based on transmission quality factor. The communication is a multi hop on the cluster.
- Alfred Service: A microservice used as module to enable the node discovery service, on the network through B.A.T.M.A.N. protocol that allows signaling and to identify the orchestrator on the network.
- Server Apps: It is a microservice that receives the information or results from the applications and sends it to the user or destination node.
3.3. The Local Agent
- Ad hoc Mode: This module enables the communication between the LA and the OR to send and receive the commands or the log information with the Alfred service.
- Monitor App: A microservice that monitors the application performance. A controller links the LA to applications designed for use in the system.
- Information: A microservice that collects the local information such as computing resources (CPU, Memory, Storage, I/O) and applications state, and the LA sends it to the OR.
- Monitor Device: A microservice that shows the information in real-time executed as a thread.
- Log: A microservice that stores all logging information about resources, messages, network interface state, and local and global interactions in each node or instance.
- Command Exec: A microservice that receives the messages from the users or the OR to execute, stop, or exit some distributed application.
| Algorithm 1. Local Agent Algorithm. |
 |
3.4. Network
4. Experiment and Results
4.1. Proposed Testbed
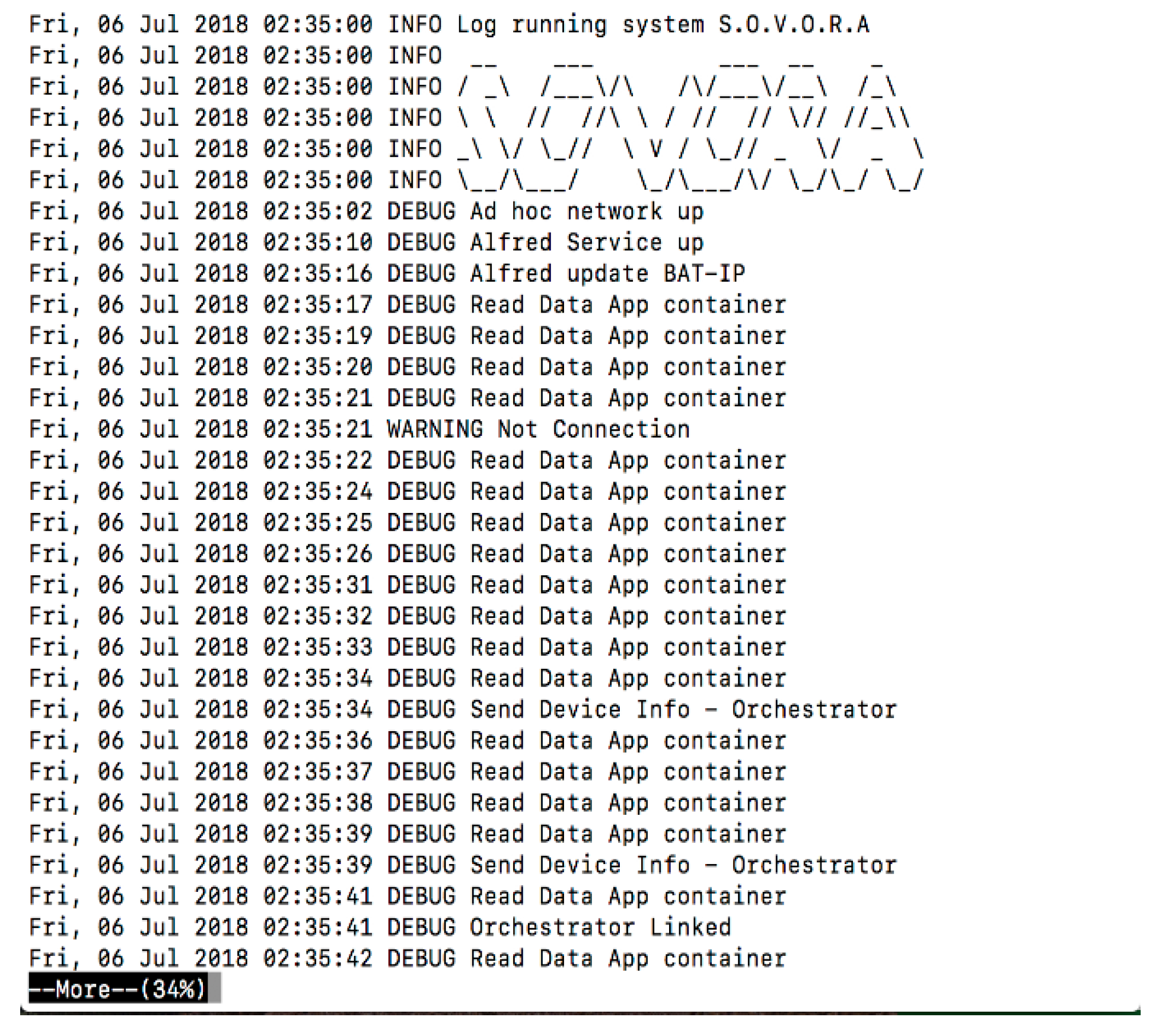
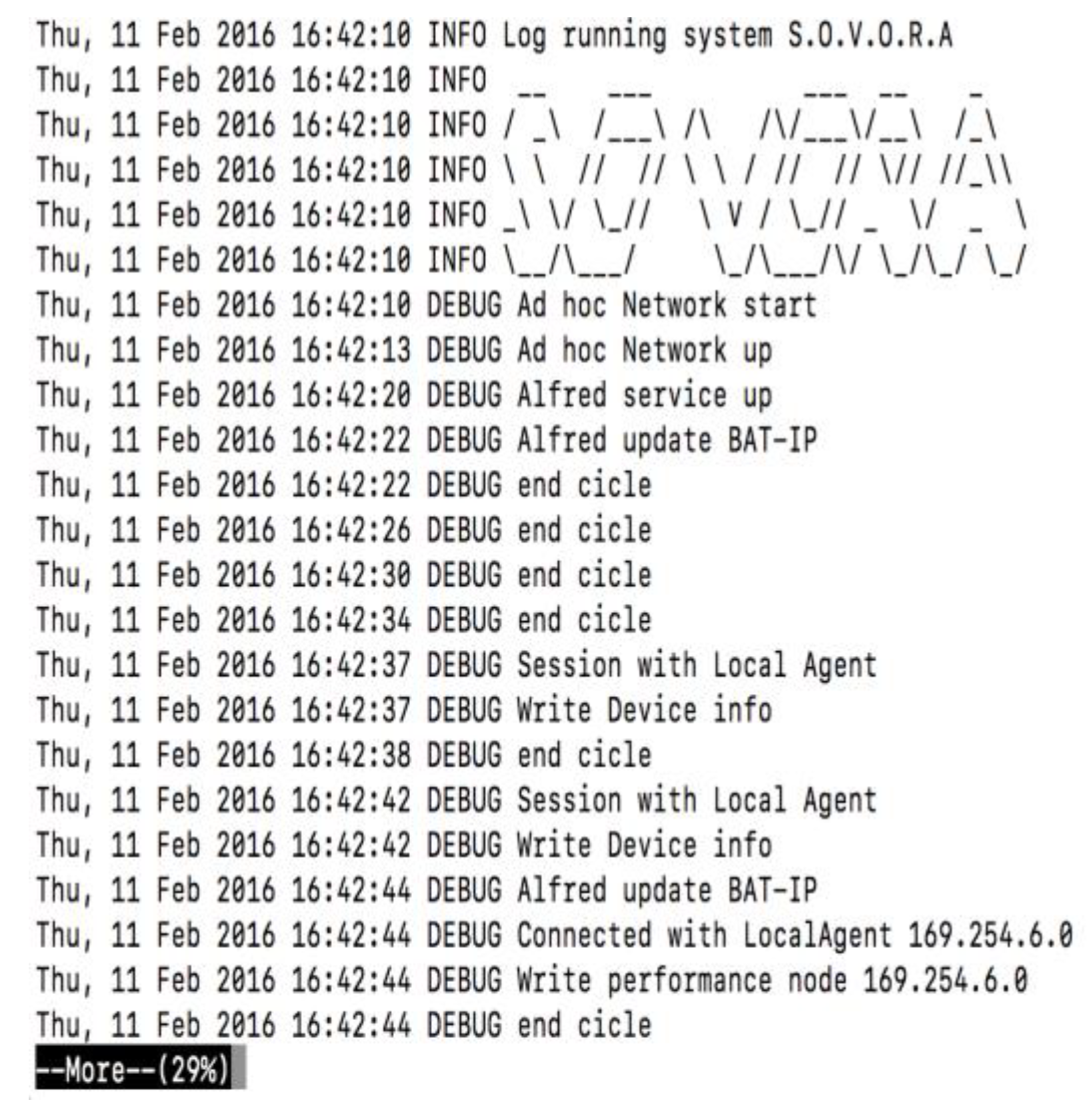
4.2. Logs and Events
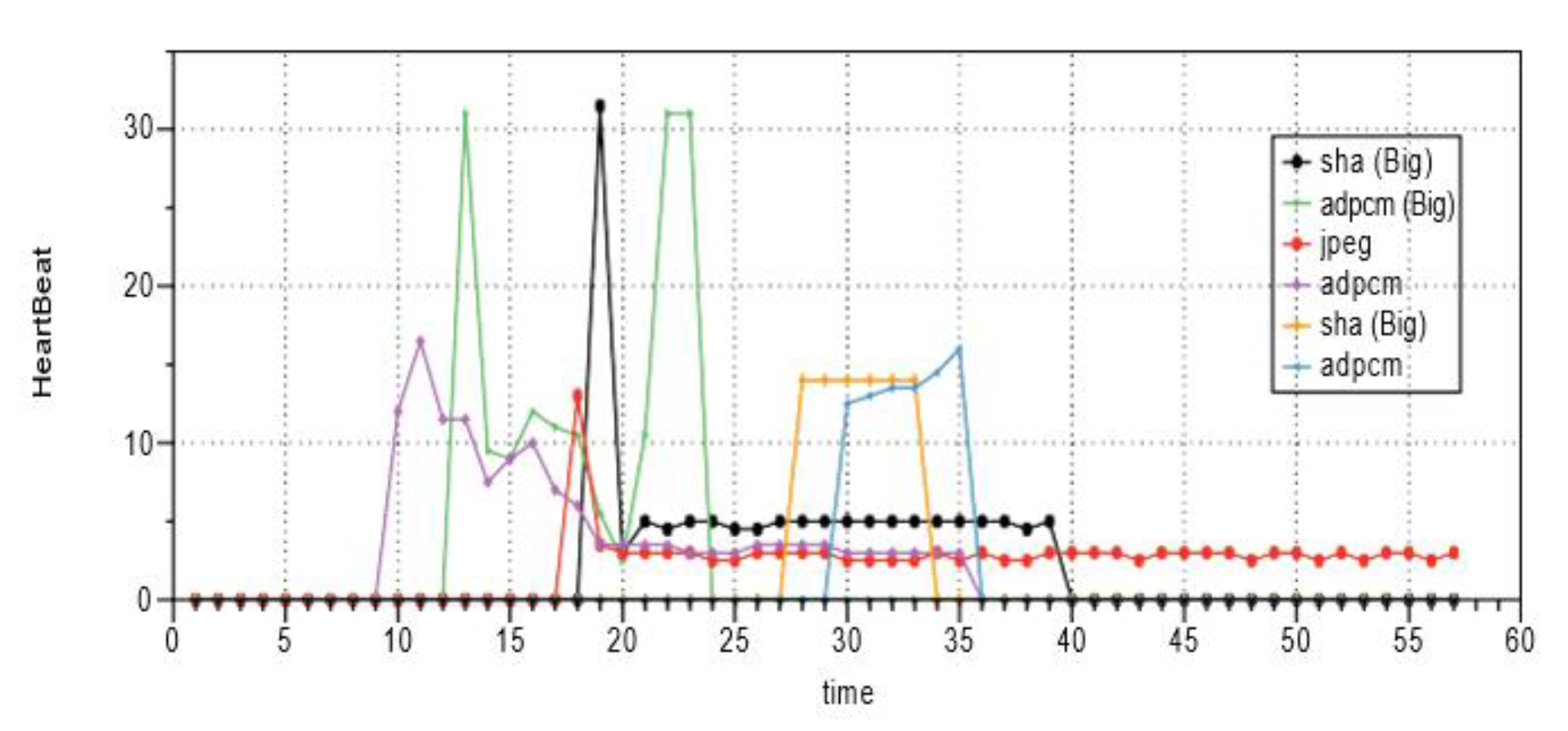
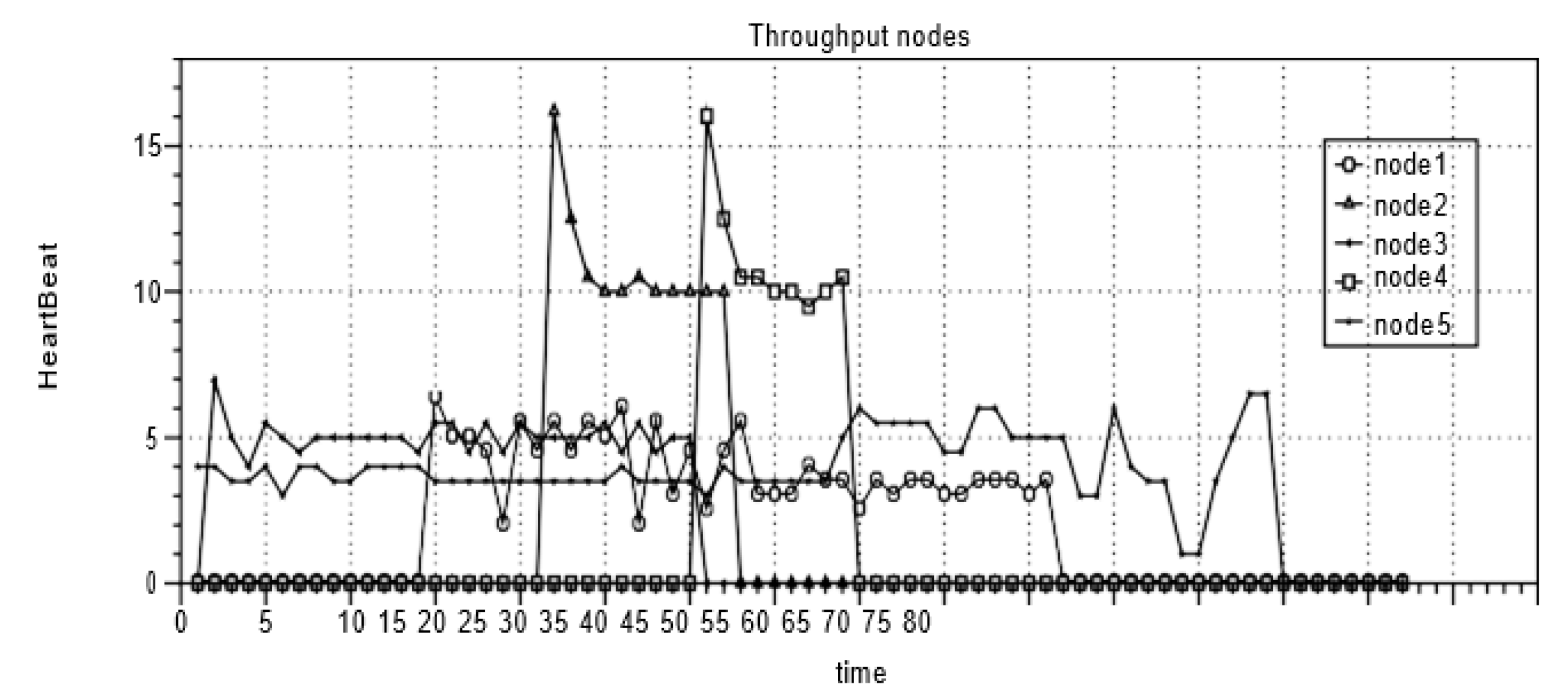
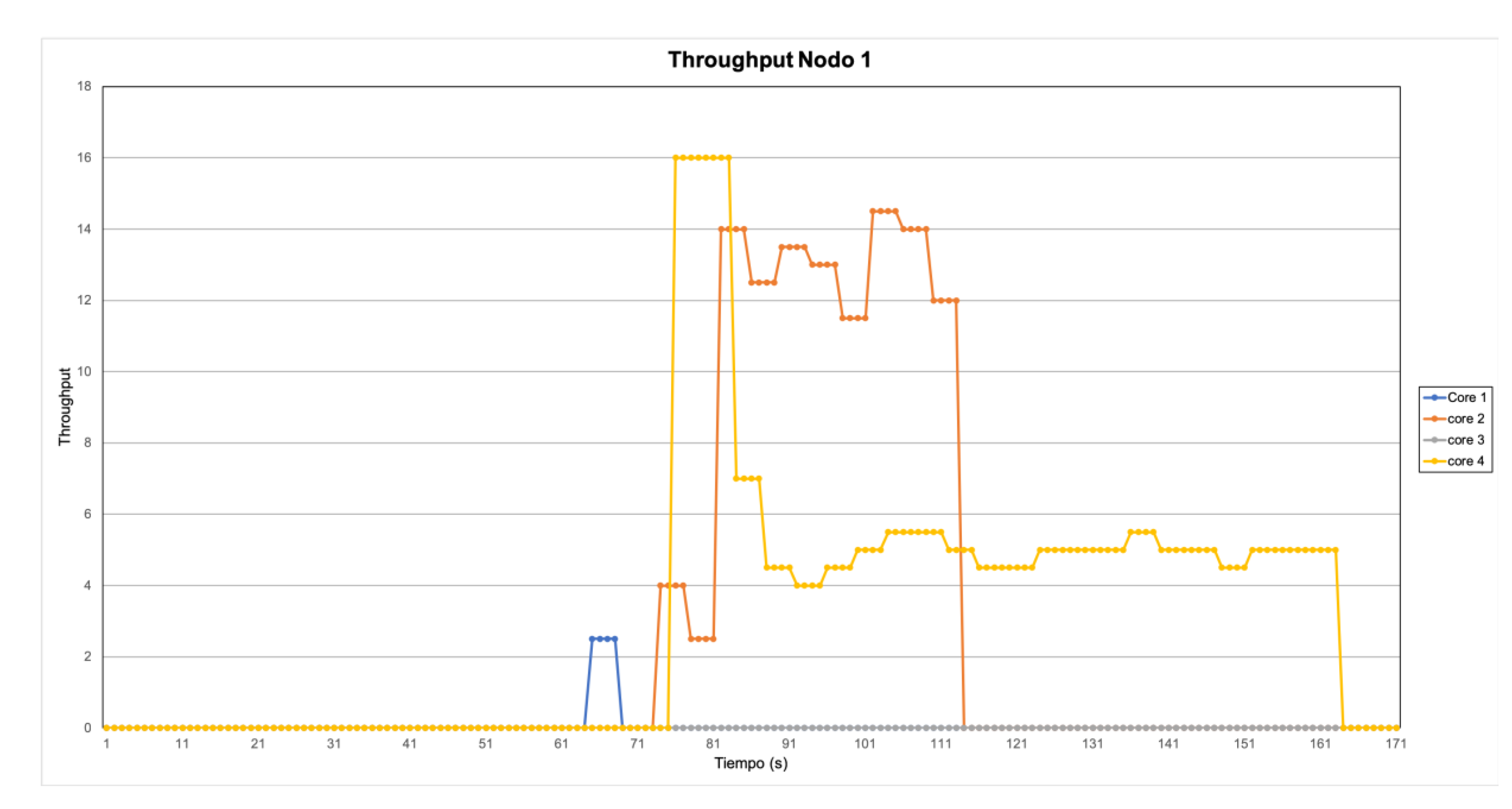
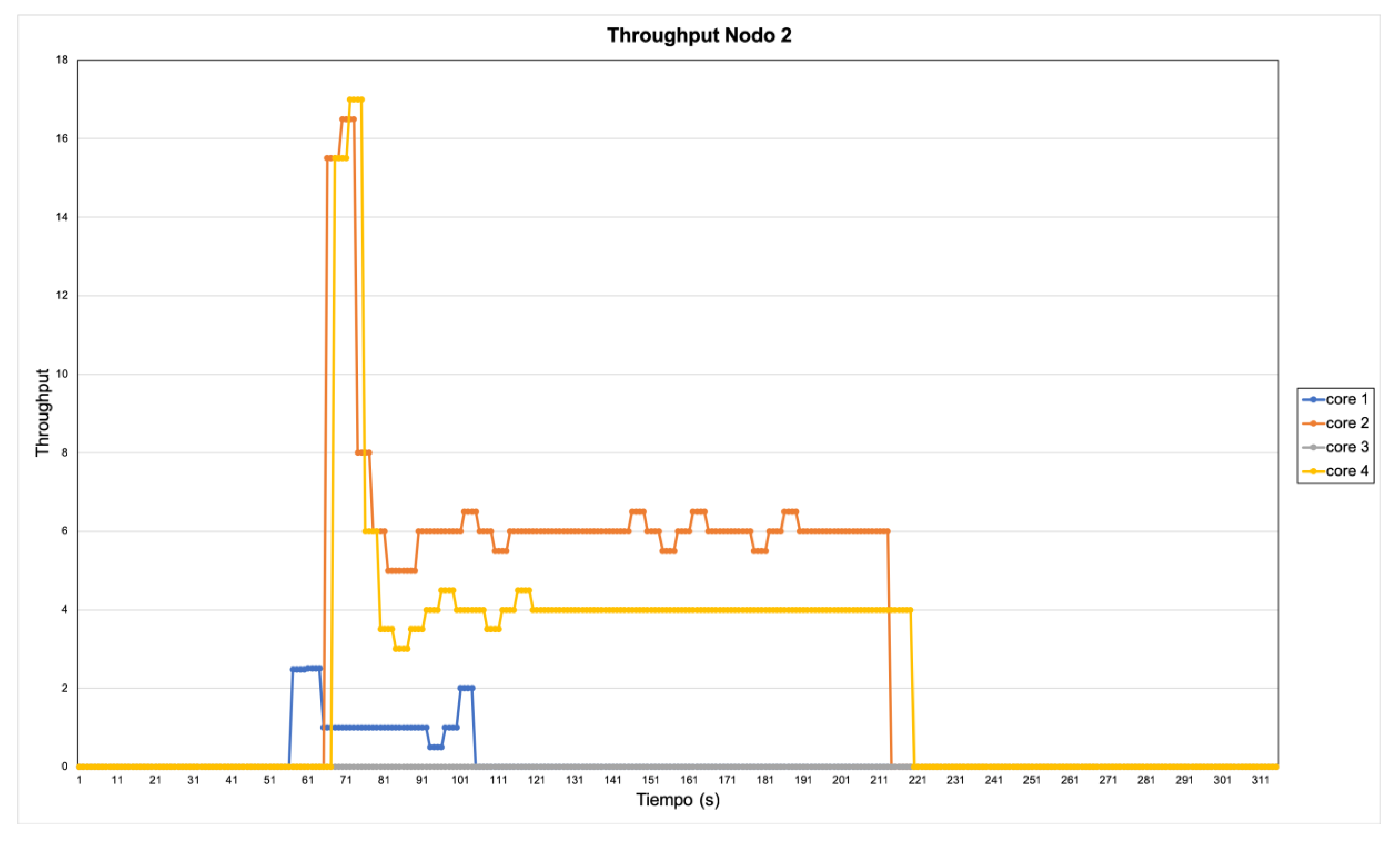
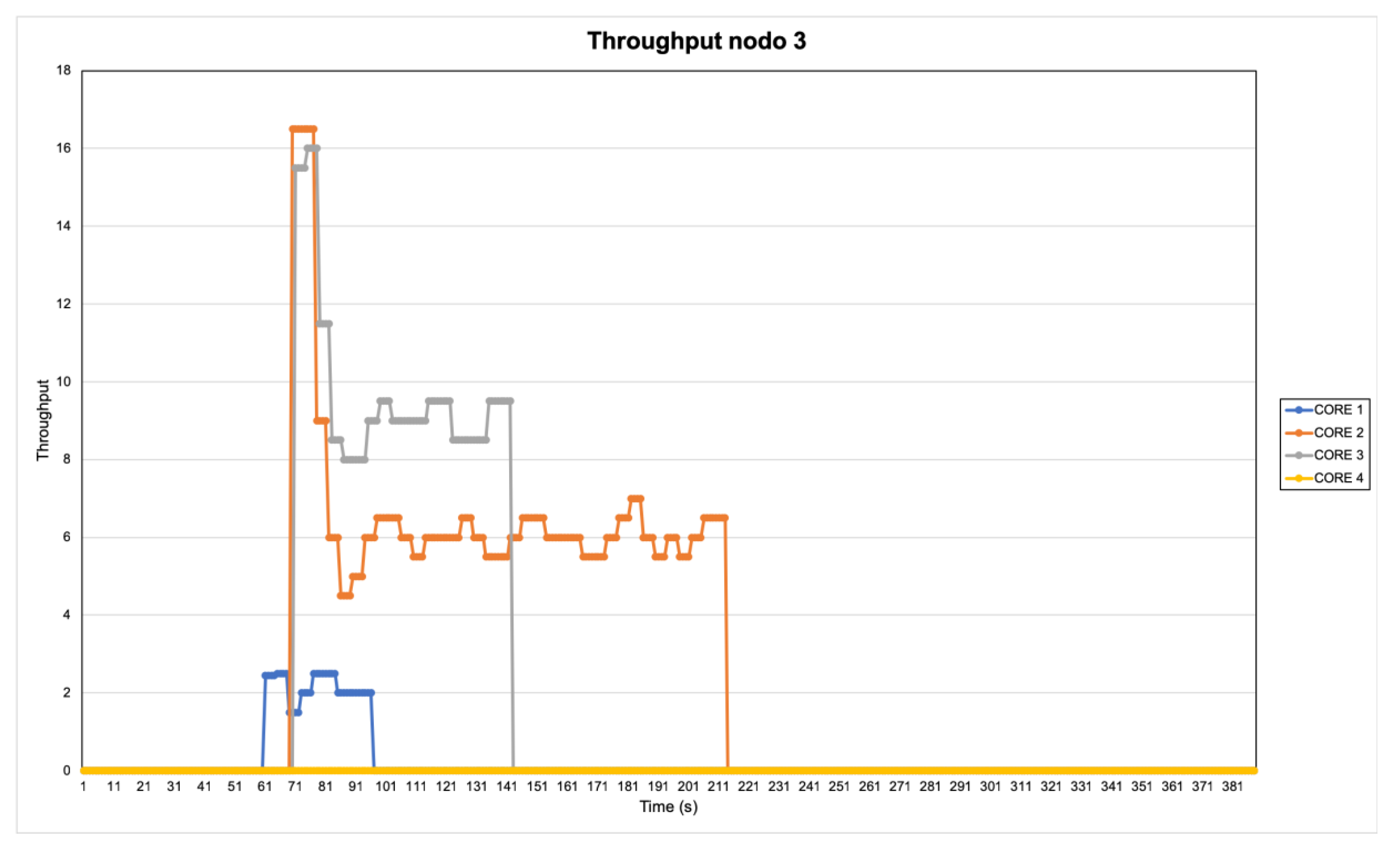
4.3. Experiment Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Fitzek, F.H.; Katz, M.D. Mobile Clouds: Exploiting Distributed Resources in Wireless, Mobile and Social Networks; John Wiley & Sons: Hoboken, NJ, USA, 2013. [Google Scholar]
- Dolui, K.; Datta, S.K. Comparison of Edge Computing Implementations: Fog Computing, Cloudlet and Mobile Edge Computing; Global Internet of Things Summit; IEEE: Dublin, Ireland, 2017; pp. 1–6. [Google Scholar]
- Ceballos, H.Z. Diseño de un Sub-Sistema de Cómputo Distribuido que permita implementar virtualización inalámbrica para gestionar recursos (Procesamiento, memoria, almacenamiento y dispositivos E/S) distribuidos en una Red Ad Hoc, mediante el modelo de pseudo Estado. Línea de Investigación: Computación Aplicada. Ph.D Thesis, Universidad Nacional de Colombia, Bogotá, Columbia, January 2018. [Google Scholar]
- Shahzadi, S.; Iqbal, M.; Dagiuklas, T.; Qayyum, Z.U. Multi-access edge computing: Open issues, challenges and future perspectives. J. Cloud Comput. 2017, 6, 30. [Google Scholar] [CrossRef]
- Bittencourt, L.F.; Diaz-Montes, J.; Buyya, R.; Rana, O.F.; Parashar, M. Mobility-aware application scheduling in fog computing. IEEE Cloud Comput. 2017, 4, 26–35. [Google Scholar] [CrossRef]
- Datla, D.; Chen, X.; Tsou, T.; Raghunandan, S.; Hasan, S.S.; Reed, J.H.; Dietrich, C.B.; Bose, T.; Fette, B.; Kim, J.H. Wireless distributed computing: A survey of research challenges. IEEE Commun. Mag. 2012, 50, 144–152. [Google Scholar] [CrossRef]
- Gao, M.; Addis, B.; Bouet, M.; Secci, S. Optimal Orchestration of Virtual Network Functions. arXiv 2017, arXiv:1706.04762. [Google Scholar] [CrossRef]
- Giotis, K.; Kryftis, Y.; Maglaris, V. Policy-Based Orchestration of NFV Services in Software-Defined Networks. In Proceedings of the Conference Network Softwarization, London, UK, 13–17 April 2015; pp. 1–5. [Google Scholar]
- Sun, C.; Bi, J.; Zheng, Z.; Hu, H. HYPER: A Hybrid High-Performance Framework for Network Function Virtualization. IEEE J. Sel. Areas Commun. 2017, 35, 2490–2500. [Google Scholar] [CrossRef]
- Santoro, D.; Zozin, D.; Pizzolli, D.; De Pellegrini, F.; Cretti, S. Foggy: A Platform for Workload Orchestration in a Fog Computing Environment. In Proceedings of the Cloud Computing Technology and Science, Sydney, Australia, 11–13 December 2017; pp. 231–234. [Google Scholar]
- Asnaghi, A.; Ferroni, M.; Santambrogio, M. DockerCap: A Software-Level Power Capping Orchestrator for Docker Containers. In Proceedings of the Computational Science and Engineering/Embedded and Ubiquitous Computing, Paris, France, 24–26 August 2016; pp. 90–97. [Google Scholar]
- Hui, F.; Mohapatra, P. Experimental Characterization of Multi-Hop Communications in Vehicular ad Hoc Network. In Proceedings of the 2nd ACM international workshop on Vehicular ad Hoc Networks, Cologne, Germany, 2 September 2005; pp. 85–86. [Google Scholar]
- Akyildiz, I.F.; Wang, X.; Wang, W. Wireless Mesh Networks: A Survey. Comput. Netw. 2005, 4, 445–487. [Google Scholar]
- Akyildiz, I.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on fog computing: Architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog Computing: A Platform for Internet of Things and Analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Springer: Berlin/Heidelberg, Germany, 2014; pp. 169–186. [Google Scholar]
- Ning, H.; Li, Y.; Shi, F.; Yang, L.T. Heterogeneous edge computing open platforms and tools for internet of things. Future Gener. Comput. Syst. 2020, 106, 67–76. [Google Scholar] [CrossRef]
- Negash, B.; Rahmani, A.M.; Liljeberg, P.; Jantsch, A. Fog Computing Fundamentals in the Internet-of-Things. In Fog Computing in the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2018; pp. 3–13. [Google Scholar]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog computing: A taxonomy, survey and future directions. In Internet of Everything; Springer: Berlin/Heidelberg, Germany, 2018; pp. 103–130. [Google Scholar]
- Brogi, A.; Forti, S.; Ibrahim, A. How to Best Deploy YOUR FOG APPLICATIONS, Probably. In Proceedings of the International Conference Fog and Edge Computing, Valencia, Spain, 8–11 May 2017; pp. 105–114. [Google Scholar]
- Brogi, A.; Forti, S. QoS-Aware Deployment of IoT Applications Through the Fog. IEEE Internet Things J. 2017, 4, 1185–1192. [Google Scholar] [CrossRef]
- Sood, S.K. SNA based QoS and reliability in fog and cloud framework. World Wide Web. 2018, 6, 1601–1616. [Google Scholar] [CrossRef]
- Nan, Y.; Li, W.; Bao, W.; Delicato, F.C.; Pires, P.F.; Zomaya, A.Y. A dynamic tradeoff data processing framework for delay-sensitive applications in Cloud of Things systems. J. Parallel Distrib. Comput. 2018, 112, 53–66. [Google Scholar] [CrossRef]
- Santos, J.; Wauters, T.; Volckaert, B.; De Turck, F. Fog Computing: Enabling the Management and Orchestration of Smart City Applications in 5G Networks. Entropy 2017, 20, 4. [Google Scholar] [CrossRef] [PubMed]
- De Sousa, N.F.S.; Perez, D.A.L.; Rosa, R.V.; Santos, M.A.; Rothenberg, C.E. Network Service Orchestration: A Survey. arXiv 2018, arXiv:1803.06596v4. [Google Scholar] [CrossRef]
- He, S.; Shin, H.S.; Xu, S.; Tsourdos, A. Distributed estimation over a low-cost sensor network: A review of state-of-the-art. Inf. Fusion 2020, 54, 21–43. [Google Scholar] [CrossRef]
- Zikria, Y.B.; Kim, S.W.; Hahm, O.; Afzal, M.K.; Aalsalem, M.Y. Internet of Things (IoT) Operating Systems Management: Opportunities, Challenges, and Solution. Sensors 2019, 8, 1793. [Google Scholar] [CrossRef]
- Baccelli, E.; Gündog˘an, C.; Hahm, O.; Kietzmann, P.; Lenders, M.S.; Petersen, H.; Schleiser, K.; Schmidt, T.C.; Wählisch, M. RIOT: An open source operating system for low-end embedded devices in the IoT. IEEE Internet Things J. 2018, 5, 4428–4440. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N.; Jawhar, I.; Mahmoud, S. CoTWare: A Cloud of Things Middleware. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), Atlanta, GA, USA, 5–8 June 2017; pp. 214–219. [Google Scholar]
- Ullah, R.; Rehman, M.A.U.; Kim, B.S. Design and implementation of an open source framework and prototype for named data networking-based edge cloud computing system. IEEE Access 2019, 7, 57741–57759. [Google Scholar] [CrossRef]
- Benomar, Z.; Longo, F.; Merlino, G.; Puliafito, A. Enabling Container-Based Fog Computing with Openstack. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA, 14–17 July 2019; pp. 1049–1056. [Google Scholar]
- Struhár, V.; Behnam, M.; Ashjaei, M.; Papadopoulos, A.V. Real-Time Containers: A Survey. In Proceedings of the 2nd Workshop on Fog Computing and the IoT (Fog-IoT 2020). Schloss Dagstuhl-Leibniz-Zentrum für Informatik, Sydney, Australia, 21 April 2020. [Google Scholar]
- Li, J.; Jin, J.; Yuan, D.; Zhang, H. Virtual fog: A virtualization enabled fog computing framework for Internet of Things. IEEE Internet Things J. 2017, 5, 121–131. [Google Scholar] [CrossRef]
- Haddad, S.; Kordon, F.; Pautet, L.; Petrucci, L. Distibuted Systems: Design and Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 2013. [Google Scholar]
- Lynch, N.A. Distributed Algzorithms; Elsevier: Amsterdam, The Netherlands, 1996. [Google Scholar]
- Neumann, A.; Aichele, C.; Lindner, M.; Wunderlich, S. Better approach to mobile ad-hoc networking (BATMAN). IETF Draft 2008, 1–24. Available online: https://tools.ietf.org/pdf/draft-wunderlich-openmesh-manet-routing-00.pdf (accessed on 8 December 2020).
- Mesh, P. ALFRED. Available online: https://www.open-mesh.org/projects/alfred/wiki (accessed on 8 December 2020).
- Guthaus, M.R.; Ringenberg, J.S.; Ernst, D.; Austin, T.M.; Mudge, T.; Brown, R.B. MiBench: A Free, Commercially Representative Embedded Benchmark Suite. In Proceedings of the International Workshop on Workload Characterization, Austin, TX, USA, 2 December 2001; pp. 3–14. [Google Scholar]
- Odroid, U.K. Smart Power 2. Available online: https://odroid.com/dokuwiki/doku.php?id=en:acc:smartpower2 (accessed on 8 December 2020).
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm (extended version). Retrieved July 2016, 20, 2018. [Google Scholar]







| Local Agent | |
| is_alive()[options-node, ip] | Verify the nodes on line and linked with SOVORA |
| node()[options-node,ip] | show information about the node resources, IP and UUID |
| process()[options-node,ip] | Show the process running on execution time on local node |
| Orchestrator | |
| sstatus [options][ip, port] | Shows the system status |
| nstatus [options][ip, port] | Show the MANET status |
| SOVORA | |
| server [options][ip, port] | Create a multi thread server on specific node |
| global()[options-ssid] | Shows the node member on the MANET cluster |
| org()[options-ssid] | Shows the network organization |
| gglobal()[options-nodes] | Create a communication group between local agents |
| disk()[options-app] | Provision disk space |
| cpu()[options-app] | Provision a thread |
| mem()[options-app] | Provision distributed memory |
| io()[options-app] | Provision I/O devices connection |
| pidg()[options-nodes] | Shows the process on all systems nodes |
| dprocess()[options-node,ip] | Create a process on specific node |
| mess()[options] | Create a broadcast message |
| clock()[options] | Set the systems clock |
| Device | Architecture | Processor Fam. | Chip | Cores | Arm_Freq (MHz) | Gpu_Freq (MHz) | Mem (MB) | Wifi_Chip |
|---|---|---|---|---|---|---|---|---|
| RPi 3 | ARM | ARM Cortex-53 | Broadcom BCM2837 | 4 | 1200 | 400 | 1024 | CypressCYW43438 |
| RPi zero w | ARM | ARM11 | Broadcom BCM2835 | 1 | 1000 | 400 | 512 | CypressCYW43438 |
| Rpi 2 | ARM | ARM-Cortex-A7 | Broadcom BCM2836 | 4 | 900 | 250 | 1024 | External |
| Odroid | ARM | ARMV8 | Samsung Exynos5422 | 8 | 2000 | 533–295 | 2048 | External |
| Application | Algorithm | Resources |
|---|---|---|
| Security | SHA | CPU, Mem, Bandwidth |
| Image Processing | JPEG | CPU, Mem, Bandwidth |
| Audio | ADPCM | CPU, Mem, Bandwidth |
| Image Processing | SUSAN | CPU, Mem, Bandwidth |
| RPi_3batctl | 14 MB Rpi_Zero | 14 MB Odroid |
|---|---|---|
| %CPU | 100.00 | 100.00 |
| Time (s) | 10.19 | 10.54 |
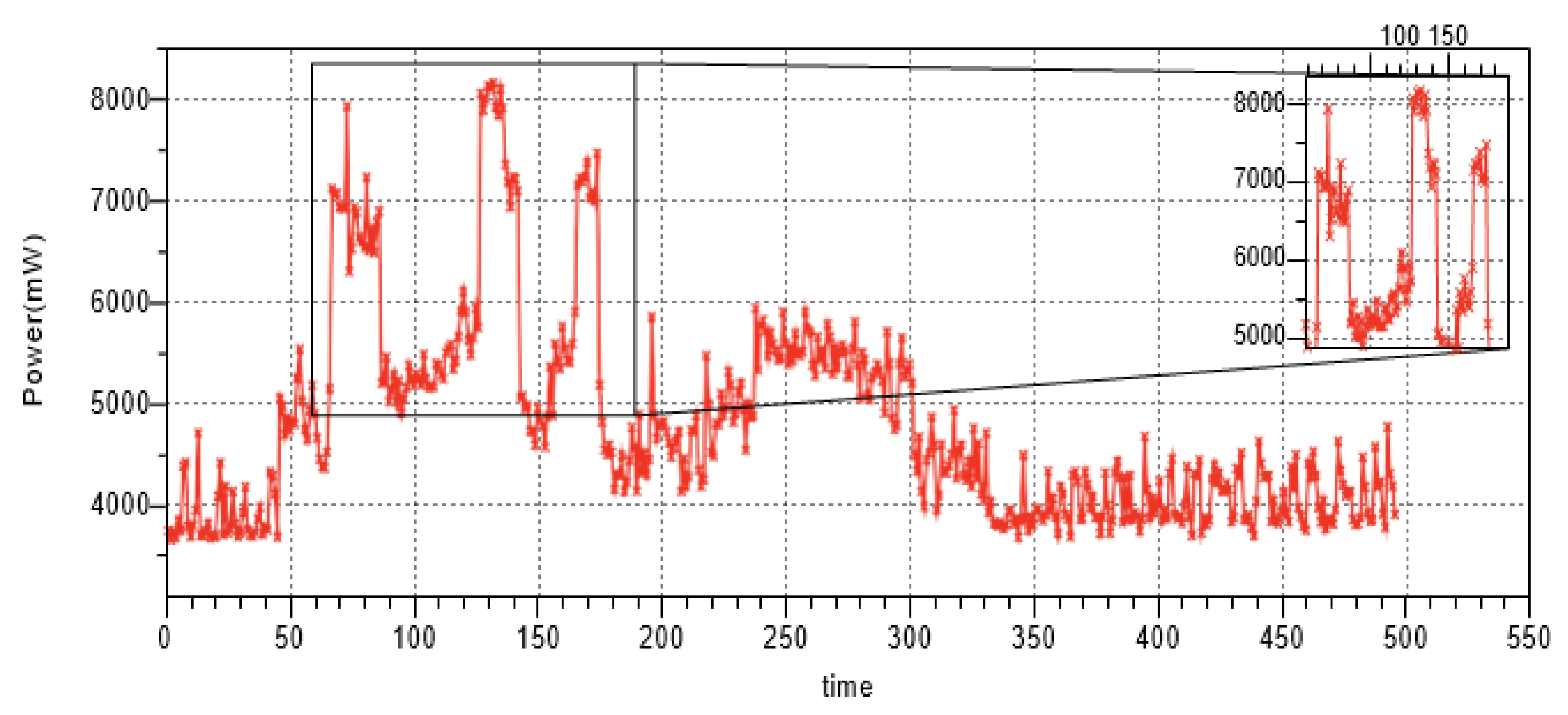
| Power (mW) | 2211.88 | 2230 |
| Energy (J) | 2211.88 | 2230 |
| Throughput (MB/s) | 0.8893 | 1.7 |
| MB Send | 7.605 | 18.5 |
| POWER + WIFI RPi 3 | ||||
|---|---|---|---|---|
| APP | IDLE | 50%THR_MIN | 75%THR_MAX | THR_MAX |
| SHA | 1689.95 | 1839.75 | 1938.41 | 1991.14 |
| ADPCM | 1689.95 | 1856.52 | 1906.49 | 1995.51 |
| SUSAN | 1689.95 | 1850.2 | 1902.81 | 1942.54 |
| JPEG | 1689.95 | 1852.39 | 1905.52 | 1929.54 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ceballos, H.Z.; Triviño, J.E.O. S.O.V.O.R.A.: A Distributed Wireless Operating System. Information 2020, 11, 581. https://doi.org/10.3390/info11120581
Ceballos HZ, Triviño JEO. S.O.V.O.R.A.: A Distributed Wireless Operating System. Information. 2020; 11(12):581. https://doi.org/10.3390/info11120581
Chicago/Turabian StyleCeballos, Henry Zárate, and Jorge Eduardo Ortiz Triviño. 2020. "S.O.V.O.R.A.: A Distributed Wireless Operating System" Information 11, no. 12: 581. https://doi.org/10.3390/info11120581
APA StyleCeballos, H. Z., & Triviño, J. E. O. (2020). S.O.V.O.R.A.: A Distributed Wireless Operating System. Information, 11(12), 581. https://doi.org/10.3390/info11120581




