Openness and Security Thinking Characteristics for IoT Ecosystems
Abstract
1. Introduction and Background
- First, we identify a set of openness and security thinking characteristics important for IoT ecosystems, (a) openness encompasses open architectures followed by a number of important aspects such as open standards, open data, open Application Programming Interfaces (APIs), open processes, and open source; (b) security thinking encompasses awareness, assessment and challenges that are needed to develop an IoT security mindset.
- Second, we propose a novel model which is conceptualized with the identified characteristics followed with several key aspects important to design and secure future IoT systems. Our conceptualized model emphasizes the human in the loop concept that would help to easily understand the emerging needs as design principles for IoT ecosystems in a more open and secure way.
- Finally, we show that novelty and risks concurrently target security in the IoT, and thus the importance of the three identified dimensions: awareness, assessment and challenges, together with a number of identified aspects uplifting continuous security thinking.
2. Motivation and Related Work
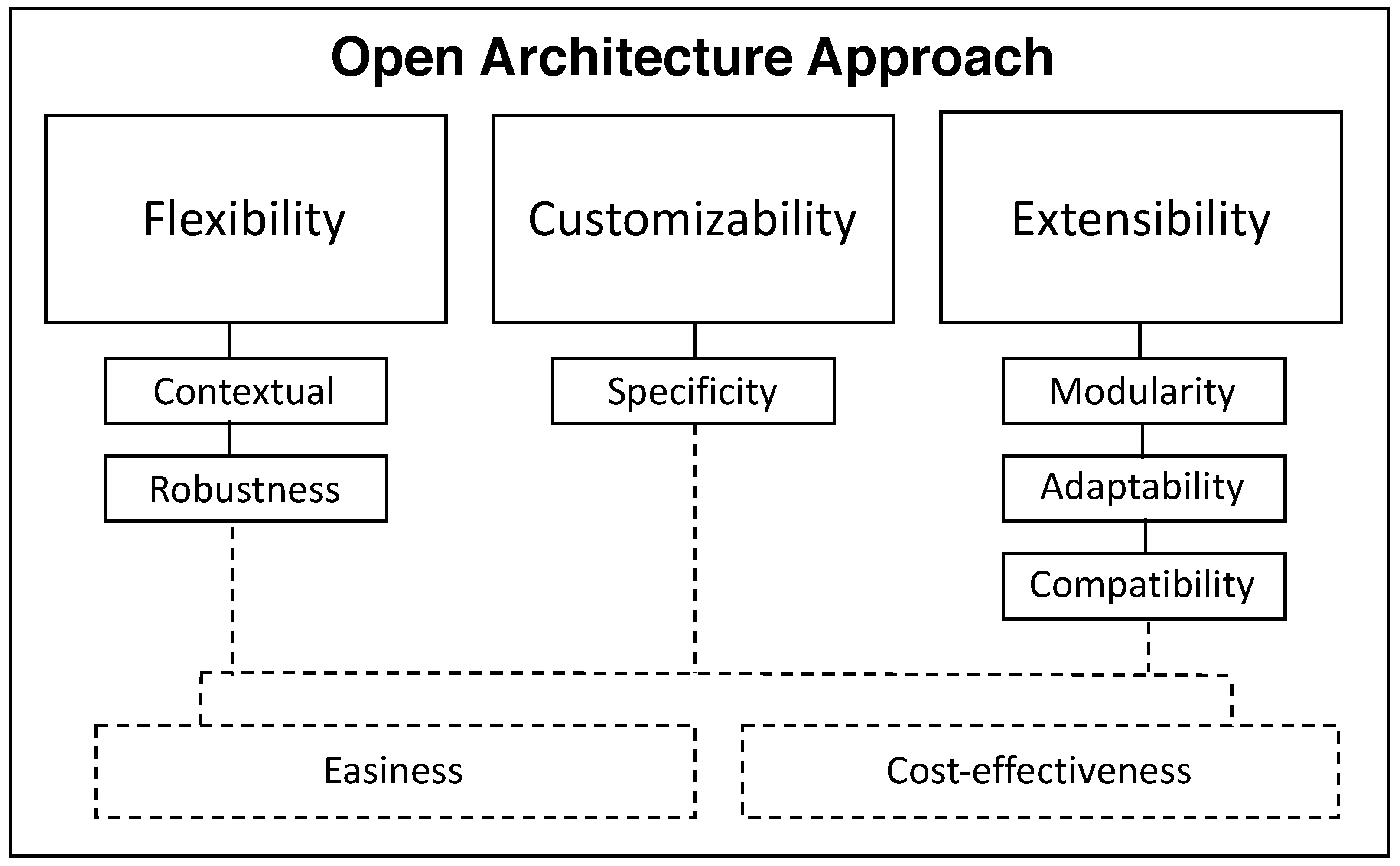
2.1. The Need for Openness of IoT as Design Principles
2.2. The Need for Security Thinking
3. Research Approach
4. Results and Discussion
4.1. Openness vs. Security
4.2. Continuous Security Thinking
5. Towards Openness and Security Thinking Model for IoT Ecosystems
| Aspects | Sources |
|---|---|
| Continuous Awareness | |
| Data management | Aggarwal et al. [40]; Benson et al. [41]; Kolias et al. [42] |
| Training and education | Stallings et al. [45]; Törngren et al. [37]; Izosimov and Törngren [44]; Dhillon et al. [27]; Harbers et al. [48]; Bugeja et al. [43]; All respondents |
| Designed-in security | Peisert [46]; Miorandi [59], Bugeja et al. [43] |
| People and team management | Wan and Zeng [49] |
| Contextual aspects | All respondents |
| Learn by observing | R5 |
| Legal framework and policy enforcement | Weber [14]; Hoepman [50]; Porras et al. [52] |
| Security as a process | Vogel and Varshney [19], Bugeja et al. [43]; R5 |
| Addressing the digital divide | R1; R6 |
| Keep secure always | All respondents |
| Plan for end-to-end security | R6; Bugeja et al. [43] |
| Ethical concerns | Kaleta et al. [47]; Dhillon et al. [27] |
| Continuous Assessment | |
| Identity management | Kounelis et al. [53]; Kumar et al. [54]; Dhillon et al. [27]; Sfar et al. [55] |
| Risk management | Izosimov and Törngren [44]; Choobineh et al. [56]; Peisert et al. [46]; Törngren et al. [37], Bugeja et al. [43]; R5, R6 |
| Security and privacy by design principles | Hoepman [50]; Harbers et al. [48], Bugeja et al. [43]; Cha et al. [57]; All respondents |
| Trust management | Sicari et al. [51]; Porras et al. [52]; Sfar et al. [55]; Vogel and Varshney [19]; R1; R2 |
| Auditing | Dhillon et al. [27]; Ali et al. [58]; R5; R6 |
| Compliance | Kajtazi et al. [29]; Dhillon et al. [27]; Moody et al. [28]; Ali et al. [58], Bugeja et al. [43] |
| Security toolbox | Bugeja et al. [43], Vogel and Varshney [19]; R5 |
| Data assessment | Bugeja et al. [43], Vogel and Varshney [19]; Cha et al. [57]; R1; R6 |
| Continuous Challenges | |
| Closed and proprietary | Benson et al. [41]; Kolias et al. [42]; Vogel and Gkouskos [6];Bugeja et al. [43]; |
| Standards (both technical and business level) | Kolias et al. [42]; Izosimov and Törngren [44], Bugeja et al. [43]; R2; R6 |
| IoT complexity | Harbers et al. [48]; Törngren et al. [37]; Bugeja et al. [43]; All respondents |
| IoT environment (resource) constraints | Porras et al. [52]; Agarwal and Dey [22]; Vogel and Varshney [19]; R1; R2; R6 |
| Heterogeneity and continuous updates | Wan and Zeng [49]; Agarwal and Dey [22], Vogel and Varshney [19]; R6 |
| Multiple verticals and Fragmentation | R1; R2 |
| Migration to public networks | R5 |
6. Study Limitations
7. Conclusions and Future Perspectives
Author Contributions
Funding
Conflicts of Interest
References
- Markit, I. The Internet of Things: A Movement, Not a Market. IHS Markit, 2017. Available online: https://cdn.ihs.com/www/pdf/IoT_ebook.pdf (accessed on 1 December 2020).
- Markit, I. The top trends of 2019: Powered by Transformative Technologies. IHS Markit, 2019. Available online: https://cdn.ihs.com/www/pdf/0119/IHS-Markit-2019-Trends-Report.pdf (accessed on 1 December 2020).
- Columbus, L. 2018 Roundup Of Internet Of Things Forecasts In addition, Market Estimates. Forbes, 13 December 2018. [Google Scholar]
- Zuboff, S. The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power, 1st ed.; PublicAffairs: New York, NY, USA, 2019. [Google Scholar]
- Bröring, A.; Schmid, S.; Schindhelm, C.K.; Khelil, A.; Käbisch, S.; Kramer, D.; Le Phuoc, D.; Mitic, J.; Anicic, D.; Teniente, E. Enabling IoT ecosystems through platform interoperability. IEEE Softw. 2017, 34, 54–61. [Google Scholar] [CrossRef]
- Vogel, B.; Gkouskos, D. An open architecture approach: Towards common design principles for an IoT architecture. In Proceedings of the 11th European Conference on Software Architecture: Companion Proceedings, Canterbury, UK, 11–15 September 2017; pp. 85–88. [Google Scholar] [CrossRef]
- Nikayin, F.; De Reuver, M. Governance of smart living service platforms: State-ofthe-art and the need for collective action. In Proceedings of the 3rd International Engineering Systems Symposium, Delft, The Netherlands, 18–20 June 2012. [Google Scholar]
- Samsung. The Internet of Things Needs Openness and Industry Collaboration to Succeed. Samsung, 27 October 2015. [Google Scholar]
- Schlagwein, D.; Conboy, K.; Feller, J.; Leimeister, J.M.; Morgan, L. “Openness” with and without Information Technology: A framework and a brief history. J. Inf. Technol. 2017, 32, 297–305. [Google Scholar] [CrossRef]
- Vogel, B.; Dong, Y.; Emruli, B.; Davidsson, P.; Spalazzese, R. What Is an Open IoT Platform? Insights from a Systematic Mapping Study. Future Internet 2020, 12, 73. [Google Scholar] [CrossRef]
- Wickström, J.; Westerlund, M.; Pulkkis, G. Rethinking IoT Security: A Protocol Based on Blockchain Smart Contracts for Secure and Automated IoT Deployments. arXiv 2020, arXiv:cs.CR/2007.02652. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things Security. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Wu, H.; Han, H.; Wang, X.; Sun, S. Research on Artificial Intelligence Enhancing Internet of Things Security: A Survey. IEEE Access 2020, 8, 153826–153848. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of things: New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Konstantina, S.; Zeynep, G.; Catherine, M.E.L. Organizational cloud security and control: A proactive approach. Inf. Technol. People 2019. [Google Scholar] [CrossRef]
- Mansfield-Devine, S. Open Source and the Internet of Things; Network Security; Elsevier: Amsterdam, The Netherlands, 2018; pp. 14–19. [Google Scholar]
- Lowry, P.B.; Dinev, T.; Willison, R. Why security and privacy research lies at the centre of the information systems (IS) artefact: Proposing a bold research agenda. Eur. J. Inf. Syst. 2017, 26, 546–563. [Google Scholar] [CrossRef]
- McDermott, C.D.; Isaacs, J.P.; Petrovski, A.V. Evaluating Awareness and Perception of Botnet Activity within Consumer Internet-of-Things (IoT) Networks. Informatics 2019, 6, 8. [Google Scholar] [CrossRef]
- Vogel, B.; Varshney, R. Towards Designing Open and Secure IoT Systems: Insights for Practitioners. In Proceedings of the 8th International Conference on the Internet of Things, Santa Barbara, CA, USA, 15–18 October 2018; ACM: New York, NY, USA, 2018; pp. 36:1–36:6. [Google Scholar] [CrossRef]
- Kajtazi, M.; Vogel, B.; Bugeja, J.; Varshney, R. State-of-the-Art in Security Thinking for the Internet of Things (IoT). In Proceedings of the 13th Pre-ICIS Workshop on Information Security and Privacy, San Francisco, CA, USA, 13 December 2018; Volume 5. [Google Scholar]
- Weiser, M. The computer for the 21 stcentury. Sci. Am. 1991, 265, 94–104. [Google Scholar] [CrossRef]
- Agarwal, Y.; Dey, A.K. Toward Building a Safe, Secure, and Easy-to-Use Internet of Things Infrastructure. Computer 2016, 49, 88–91. [Google Scholar] [CrossRef]
- Caporuscio, M.; Ghezzi, C. Engineering Future Internet applications: The Prime approach. J. Syst. Softw. 2015, 106, 9–27. [Google Scholar] [CrossRef]
- Vogel, B. Towards Open Architecture System. In Proceedings of the 2013 9th Joint Meeting on Foundations of Software Engineering, ESEC/FSE 2013, Saint Petersburg, Russia, August 18–26 2013; ACM: New York, NY, USA, 2013; pp. 731–734. [Google Scholar] [CrossRef]
- Vogel, B.; Kurti, A.; Mikkonen, T.; Milrad, M. Towards an Open Architecture Model for Web and Mobile Software: Characteristics and Validity Properties. In Proceedings of the 2014 IEEE 38th Annual Computer Software and Applications Conference, Vasteras, Sweden, 21–25 July 2014; pp. 476–485. [Google Scholar] [CrossRef]
- Sicker, D.C.; Lookabaugh, T. VoIP Security: Not an Afterthought. Queue 2004, 2, 56–64. [Google Scholar] [CrossRef]
- Dhillon, G.; Carter, L.; Abed, J.; Sandhu, R. Defining Objectives For Securing The Internet of Things: A Value-Focused Thinking Approach. WISP Proc. 2016, 3. [Google Scholar]
- Moody, G.; Siponen, M.T.; Pahnila, S. Toward a Unified Model of Information Security Policy Compliance. MIS Q. 2018, 42, 285. [Google Scholar] [CrossRef]
- Kajtazi, M.; Cavusoglu, H.; Benbasat, I.; Haftor, D. Escalation of commitment as an antecedent to noncompliance with information security policy. Inf. Comput. Secur. 2018, 26, 171–193. [Google Scholar] [CrossRef]
- Varshney, R. Towards Designing Open Secure IoT System—Insights for Practitioners. Master’s Thesis, Malmo University, Malmo, Sweden, 2018. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. Understanding the Internet of Things: Definition, potentials, and societal role of a fast evolving paradigm. Ad Hoc Netw. 2017, 56, 122–140. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A Vision, Architectural Elements, and Future Directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Preventis, A.; Stravoskoufos, K.; Sotiriadis, S.; Petrakis, E.G.M. IoT-A and FIWARE: Bridging the Barriers Between the Cloud and IoT Systems Design and Implementation. In Proceedings of the 6th International Conference on Cloud Computing and Services Science, CLOSER 2016, Rome, Italy, 23–25 April 2016; SCITEPRESS—Science and Technology Publications, Lda: Setubal, Portugal, 2016; Volume 1–2, pp. 146–153. [Google Scholar] [CrossRef]
- Aly, M.; Khomh, F.; Guéhéneuc, Y.; Washizaki, H.; Yacout, S. Is Fragmentation a Threat to the Success of the Internet of Things? IEEE Internet Things J. 2019, 6, 472–487. [Google Scholar] [CrossRef]
- Petersen, H.; Baccelli, E.; Wählisch, M. Interoperable Services on Constrained Devices in the Internet of Things. 2014. Available online: https://www.w3.org/2014/02/wot/papers/baccelli.pdf (accessed on 1 December 2020).
- Riahi, A.; Natalizio, E.; Challal, Y.; Mitton, N.; Iera, A. A systemic and cognitive approach for IoT security. In Proceedings of the 2014 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 3–6 February 2014; pp. 183–188. [Google Scholar] [CrossRef]
- Törngren, M.; Bensalem, S.; McDermid, J.; Passerone, R.; Sangiovanni-Vincentelli, A.; Schätz, B. Education and Training Challenges in the Era of Cyber-Physical Systems: Beyond Traditional Engineering. In Proceedings of the WESE’15: Workshop on Embedded and Cyber-Physical Systems Education, Amsterdam, The Netherlands, 4–9 October 2015; ACM: New York, NY, USA, 2015; pp. 8:1–8:5. [Google Scholar] [CrossRef]
- Dhillon, G.; Backhouse, J. Current directions in IS security research: Towards socio-organizational perspectives. Inf. Syst. J. 2001, 11, 127–154. [Google Scholar] [CrossRef]
- Simmonds, A.J.; Sandilands, P.; van Ekert, L. An Ontology for Network Security Attacks; AACC; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Aggarwal, C.C.; Ashish, N.; Sheth, A. The Internet of Things: A Survey from the Data-Centric Perspective. In Managing and Mining Sensor Data; Aggarwal, C.C., Ed.; Springer: Boston, MA, USA, 2013; pp. 383–428. [Google Scholar] [CrossRef]
- Benson, K.; Fracchia, C.; Wang, G.; Zhu, Q.; Almomen, S.; Cohn, J.; D’arcy, L.; Hoffman, D.; Makai, M.; Stamatakis, J.; et al. SCALE: Safe community awareness and alerting leveraging the internet of things. IEEE Commun. Mag. 2015, 53, 27–34. [Google Scholar] [CrossRef]
- Kolias, C.; Stavrou, A.; Voas, J.; Bojanova, I.; Kuhn, R. Learning Internet-of-Things Security “Hands-On”. IEEE Secur. Priv. 2016, 14, 37–46. [Google Scholar] [CrossRef]
- Bugeja, J.; Vogel, B.; Jacobsson, A.; Varshney, R. IoTSM: An End-to-end Security Model for IoT Ecosystems. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 267–272. [Google Scholar] [CrossRef]
- Izosimov, V.; Törngren, M. Security Evaluation of Cyber-Physical Systems in Society- Critical Internet of Things. In Proceedings of the TRUDEVICE—6th Conference on Trustworthy Manufacturing and Utilization of Secure Devices, Barcelona, Spain, 14–16 November 2016. [Google Scholar]
- Stallings, W.; Brown, L. Computer Security: Principles and Practice, 3rd ed.; Pearson: Hoboken, NJ, USA, 2015. [Google Scholar]
- Peisert, S.; Margulies, J.; Nicol, D.M.; Khurana, H.; Sawall, C. Designed-in Security for Cyber-Physical Systems. IEEE Secur. Priv. 2014, 12, 9–12. [Google Scholar] [CrossRef]
- Kaleta, J.; Thackston, R.; Ojagbule, O. Exploring User Privacy Based on Human Behavior with Internet of Things Devices at Home (Formative Research). SAIS 2018 Proc. 2018, 6. Available online: https://aisel.aisnet.org/cgi/viewcontent.cgi?article=1021&context=sais2018 (accessed on 1 December 2020).
- Harbers, M.; Bargh, M.S.; Pool, R.; Berkel, J.V.; van den Braak, S.W.; Choenni, S. A Conceptual Framework for Addressing IoT Threats: Challenges in Meeting Challenges; HICSS: Hilton Waikoloa Village, HI, USA, 2018. [Google Scholar]
- Wan, J.; Zeng, M. Research on Key Success Factors Model for Innovation Application of Internet of Things with Grounded Theory. WHICEB 2015 Proc. 2015, 38. [Google Scholar]
- Hoepman, J.H. Privacy Design Strategies. In ICT Systems Security and Privacy Protection; Cuppens-Boulahia, N., Cuppens, F., Jajodia, S., Abou El Kalam, A., Sans, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; pp. 446–459. [Google Scholar]
- Sicaria, S.; Rizzardia, A.; Griecob, L.A.; Coen-porisinia, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Porras, J.; Pänkäläinen, J.; Knutas, A.; Khakurel, J. Security In The Internet Of Things—A Systematic Mapping Study; HICSS: Hilton Waikoloa Village, HI, USA, 2018. [Google Scholar]
- Kounelis, I.; Baldini, G.; Neisse, R.; Steri, G.; Tallacchini, M.; Guimaraes Pereira, A. Building Trust in the Human? Internet of Things Relationship. IEEE Technol. Soc. Mag. 2014, 33, 73–80. [Google Scholar] [CrossRef]
- Kumar, S.A.; Vealey, T.; Srivastava, H. Security in Internet of Things: Challenges, Solutions and Future Directions. In Proceedings of the 2016 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 5772–5781. [Google Scholar]
- Sfar, A.R.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Choobineh, J.; Dhillon, G.; Grimaila, M.R.; Ulmer, J.R. Management of Information Security: Challenges and Research Directions. Commun. Assoc. Inf. Syst. 2007, 20, 57. [Google Scholar] [CrossRef]
- Cha, S.; Hsu, T.; Xiang, Y.; Yeh, K. Privacy Enhancing Technologies in the Internet of Things: Perspectives and Challenges. IEEE Internet Things J. 2019, 6, 2159–2187. [Google Scholar] [CrossRef]
- Ali, I.; Sabir, S.; Ullah, Z. Internet of Things Security, Device Authentication and Access Control: A Review. arXiv 2019, arXiv:abs/1901.07309. [Google Scholar]
- Miorandi, D.; Sicari, S.; Pellegrini, F.D.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]

| Respondent | Role | IoT Domains |
|---|---|---|
| R1 | Security Architect | Mobile Communications |
| R2 | Senior Architect | IoT Solutions |
| R3 | Technology Leader | Industry Automation |
| R4 | Technology Expert | Home Security |
| R5 | Security Coach | Home Surveillance |
| R6 | Security Expert | Data Security |
| IoT |
|---|
| Q1. What is your job role in your organization? |
| Q2. What does Internet of Things mean to you? |
| Q3. What are the properties associated with smart things? |
| Q4. Are you aware of any general constraints in Internet of Things? |
| Security Awareness |
| Q5. What are your views on security of Internet of Things? |
| Q6. What are your views on privacy of Internet of Things? |
| Q7. What are the challenges or constraints in using existing security measures on Internet of Things? |
| Designing Open and Secure IoT Systems |
| Q8. How openness affects IoT (Flexibility, Customizability, and Extensibility)? |
| Q9. What do you think considering security and privacy while designing IoT solutions is critical? |
| Q10. Are you aware of any existing security mechanisms within your organization that can address challenges in Internet of Things? What measures can you suggest? |
| Q11. Do you want to make any last statement for IoT community and developers? |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vogel, B.; Kajtazi, M.; Bugeja, J.; Varshney, R. Openness and Security Thinking Characteristics for IoT Ecosystems. Information 2020, 11, 564. https://doi.org/10.3390/info11120564
Vogel B, Kajtazi M, Bugeja J, Varshney R. Openness and Security Thinking Characteristics for IoT Ecosystems. Information. 2020; 11(12):564. https://doi.org/10.3390/info11120564
Chicago/Turabian StyleVogel, Bahtijar, Miranda Kajtazi, Joseph Bugeja, and Rimpu Varshney. 2020. "Openness and Security Thinking Characteristics for IoT Ecosystems" Information 11, no. 12: 564. https://doi.org/10.3390/info11120564
APA StyleVogel, B., Kajtazi, M., Bugeja, J., & Varshney, R. (2020). Openness and Security Thinking Characteristics for IoT Ecosystems. Information, 11(12), 564. https://doi.org/10.3390/info11120564







