A Computation-Efficient Group Key Distribution Protocol Based on a New Secret Sharing Scheme
Abstract
1. Introduction
1.1. Contributions
- A new secret-sharing scheme is proposed. The corresponding polynomial degree of it is lower, which greatly simplifies the process of secret recovery. In addition, this scheme enables GC to construct an encrypted rekeying message when the secret shares of all authorized members have been determined, which avoids the transmission of secret shares.
- A simple and efficient node-coding method for a logical key tree is proposed and its update algorithm is given, which is the basis for implementing the new encryption and decryption scheme in the tree structure of LKH.
- A CEGKD that satisfies forward security and backward security is proposed, and its specific implementation is given. The number of polynomials to be constructed by GC is equal to the depth of the key tree, and the degree of polynomials is equal to the degree of the key tree.
1.2. Related Works
2. Preliminaries
2.1. Logical Key Hierarchy
2.2. Shamir Threshold Secret-Sharing Scheme
3. Our Proposed Protocol CEGKD
3.1. New Form of Secret Sharing Scheme
3.2. Group-Key Distribution Protocol
3.2.1. Key-Numbering Rule
- Number the group key as
- For other keys k, assuming that the parent node number of k is n, the number of k is d||n, where || represents string concatenation, and d is a binary string. If k is the first child of its parent node, then ; if k is the second child, then ; if k is the third child, then .
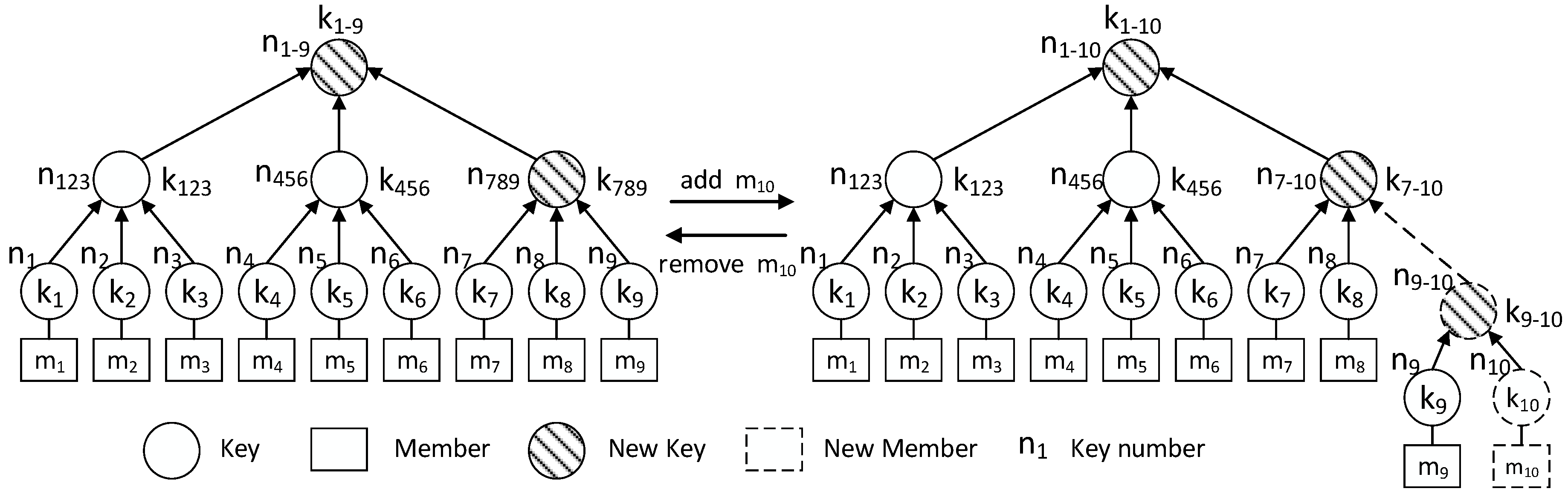
3.2.2. Joining a Group
- Align private key number to the right of . If =, and it is not the new member, update the private key number to , and set .
- From right to left, compare and the SN of each two bits to obtain the same number in succession. Once the difference is found, the process is terminated. Denote the result as . For the new member, the result is set to .
- Calculate new key according to the following formula:
- Replace the -th key stored by the member with .
- Reduce the value of I by 1 and repeat Steps 2 to 5 until is obtained.
3.2.3. Leaving a Group
4. Security and Efficiency Analysis
4.1. Security Analysis
- and obtained from RM;
- key and key number on the path before leaving; and
- all key numbers inferred from key number rules.
- and obtained from RM;
- key and key number on the path before leaving; and
- all key numbers inferred from key number rules.
4.2. Efficiency Analysis
4.2.1. Computation Cost
4.2.2. Communication Cost
4.2.3. Storage Cost
5. Experiments
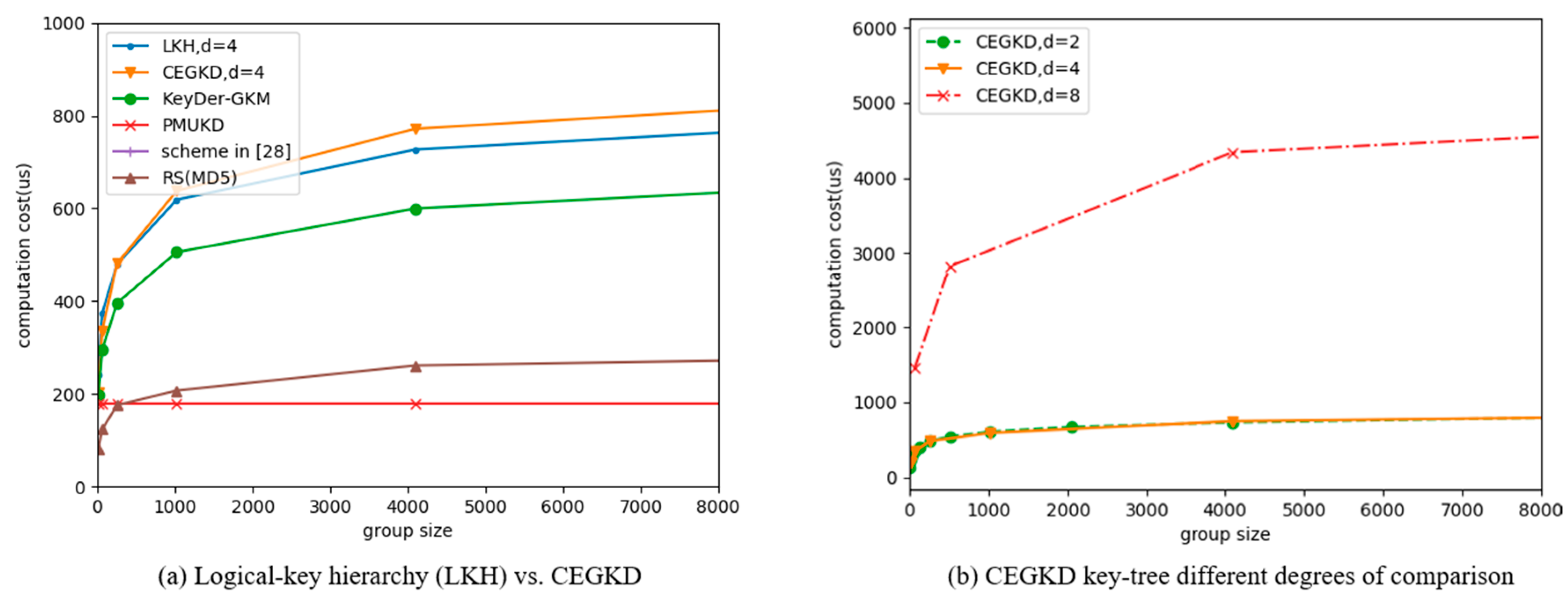
5.1. Computation Cost
- (1)
- GC computation cost. In addition to the computation cost analyzed in the Section 4, GC computation cost also comes from operations such as generating key tree nodes and traversing the key tree. As can be seen from Figure 2, except that the computation cost of PMUKD scheme is constant, the cost of other methods is logarithmic to the group size. Under the same key-tree degree, the computation cost of the LKH scheme is close to that of the CEGKD scheme. For the CEGKD scheme, the bigger the degree of the key tree, the higher the GC computation cost is.
- (2)
- Computation cost of group members. After receiving the rekeying message, the group members in the CEGKD scheme obtain the updated key by modulo operation and hash operation over finite field GF(q), which is faster than the AES decryption algorithm in the LKH scheme. In addition, group members can precalculate the powers of numbers in polynomials, which also makes the CEGKD scheme more efficient on the group-member side. As can be seen from Figure 3, although the computation costs of all schemes except PMUKD are logarithmically related to the number of group members; the computation cost of the CEGKD scheme on the group-member side is much lower than that of the LKH scheme and the others’. The larger the communication-group size is, the greater the computation-efficiency advantage of CEGKD at the member side. Although the computation cost of PMUKD scheme is constant, the computation cost of CEGKD on the group member side is still the smallest among all schemes within the foreseeable range of group size. For the CEGKD scheme, the bigger the degree of the key tree is, the lower the computation cost of the group members.
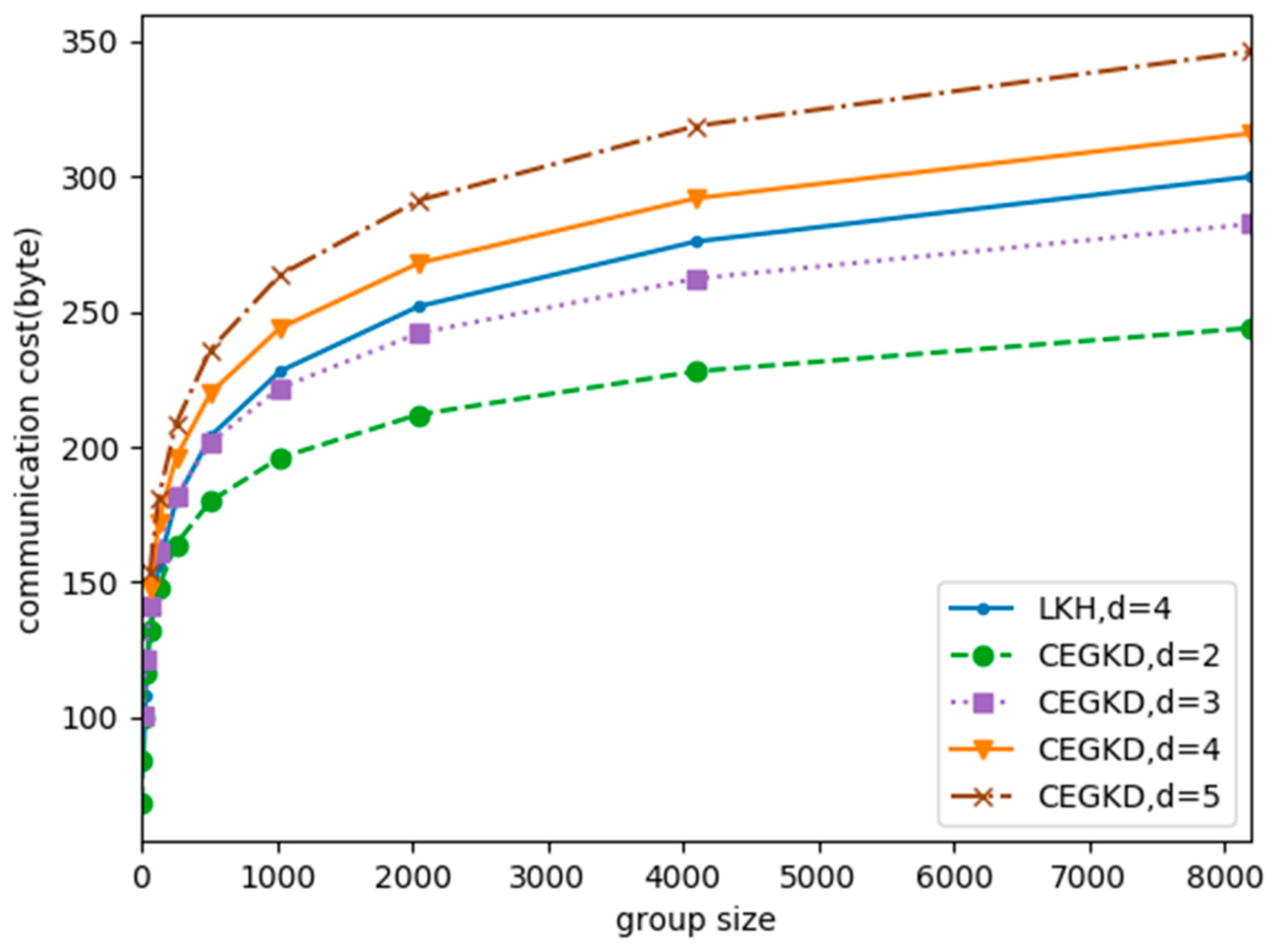
5.2. Communication Cost
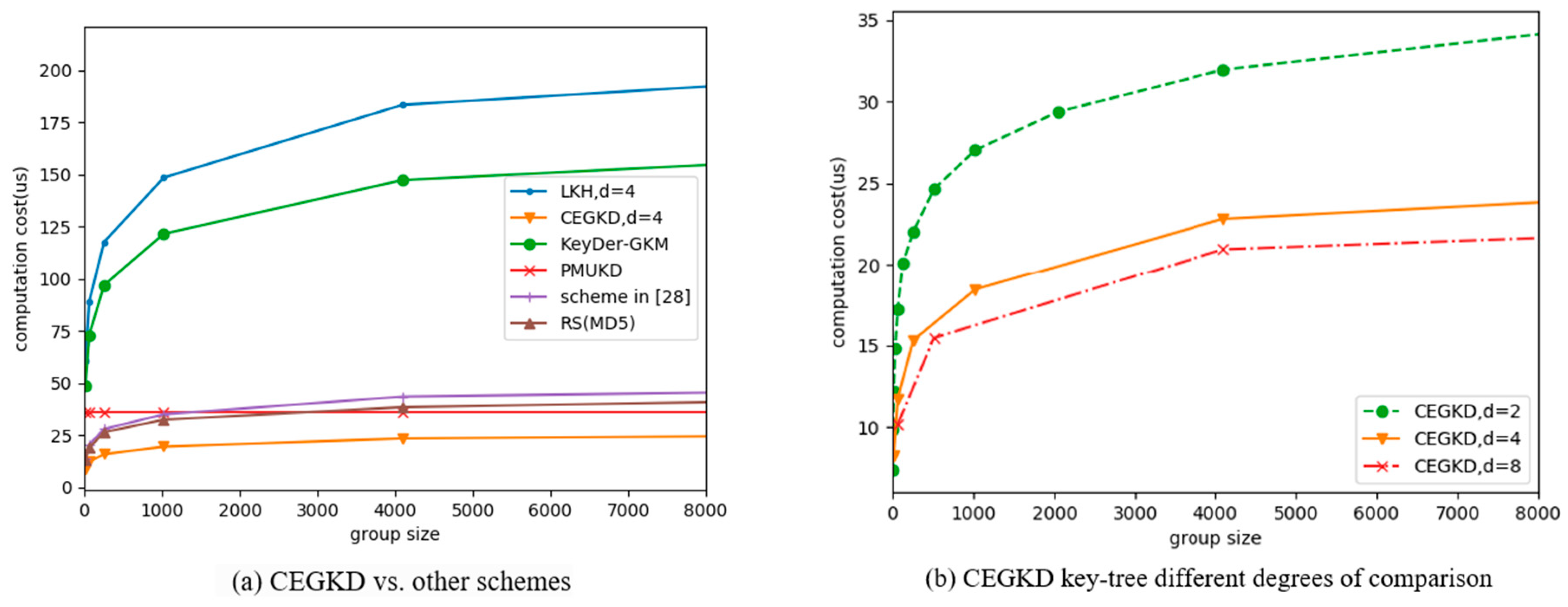
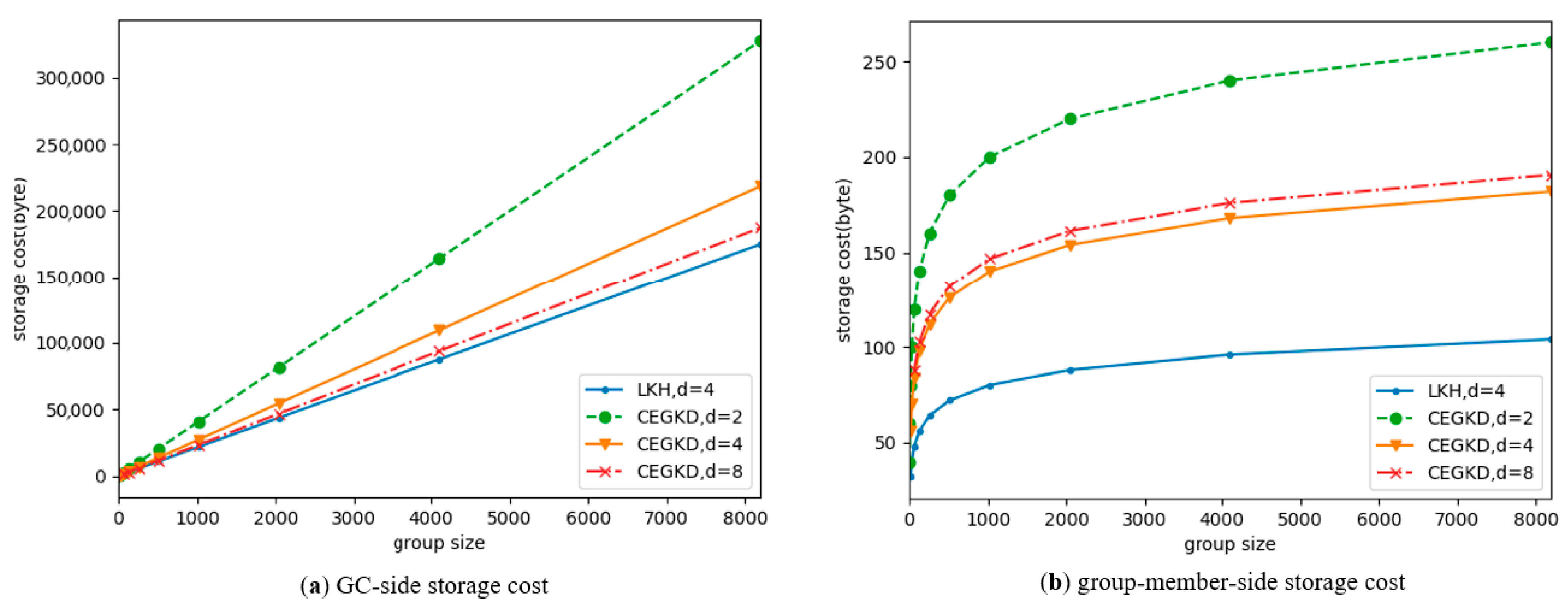
5.3. Storage Cost
- (1)
- GC-side storage cost. As can be seen from Figure 5, as the size of the communication group increases, storage-cost increases of the two schemes are both linear with member size. GC storage cost under the CEGKD scheme is slightly larger than the value under the LKH scheme. For the CEGKD scheme, the greater the degree of the key tree is, the smaller the GC storage overhead.
- (2)
- Group-member-side storage cost. As can be seen from Figure 5, the storage costs of the two schemes are both logarithmically related to member size. The storage cost of group members under the CEGKD scheme is greater than that of LKH scheme because the precomputation results of the powers of the key numbers are both to be stored.
5.4. Analysis
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Dejan, V.; Andrea, T.; Savo, D.; Khirallah, C. Random Linear Network Coding for 5G Mobile Video Delivery. Information 2018, 9, 72. [Google Scholar]
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of Internet of Vehicles. Chin. Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Akpakwu, G.; Silva, B.; Hancke, G.P.; Abu-Mahfouz, A.M. A Survey on 5G Networks for the Internet of Things: Communication Technologies and Challenges. IEEE Access 2017, 5, 3619–3647. [Google Scholar] [CrossRef]
- Wong, C.K.; Gouda, M.; Lam, S.S. Secure group communications using key graphs. IEEE/ACM Trans. Netw. 2000, 8, 16–30. [Google Scholar] [CrossRef]
- Challal, Y.; Seba, H. Group Key Management Protocols: A Novel Taxonomy. Int. Sch. Sci. Res. Innov. 2008, 2, 3620–3633. [Google Scholar]
- Zhu, S.; Jajodia, S. Scalable Group Key Management for Secure Multicast: A Taxonomy and New Directions. In Network Security; Springer: New York, NY, USA, 2010. [Google Scholar]
- Zhou, Z.; Huang, D. An Optimal Key Distribution Scheme for Secure Multicast Group Communication. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- Waldvogel, M.; Caronni, G.; Sun, D.; Weiler, N.; Plattner, B. The VersaKey framework: Versatile group key management. IEEE J. Sel. Areas Commun. 1998, 17, 1614–1631. [Google Scholar] [CrossRef]
- Harn, L.; Lin, C. Authenticated Group Key Transfer Protocol Based on Secret Sharing. IEEE Trans. Comput. 2010, 59, 842–846. [Google Scholar] [CrossRef]
- Penrig, A.; Song, D.; Tygar, J.D. ELK, a new protocol for efficient large-group key distribution. In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 14–16 May 2002. [Google Scholar]
- Rafaeli, S.; Mathy, L.; Hutchison, D. LKH+2: An improvement on the LKH+ algorithm for removal operations. Arkiv För Matematik. 1971, 9, 171–180. [Google Scholar]
- Wallner, D.M.; Harder, E.J.; Agee, R.C. Key Management for Multicast: Issues and Architectures; The Internet Society: Reston, VA, USA, 1999. [Google Scholar] [CrossRef]
- Wong, C.K.; Lam, S.S. Keystone: A group key management service. In Proceedings of the International Conference on Telecommunications, Acapulco, Mexico, 20–25 May 2000. [Google Scholar]
- Sherman, A.T.; Mcgrew, D.A. Key Establishment in Large Dynamic Groups Using One-Way Function Trees. IEEE Trans. Softw. Eng. 2003, 29, 444–458. [Google Scholar] [CrossRef]
- Li, X.S.; Yang, Y.R.; Gouda, M.G.; Lam, S.S. Batch rekeying for secure group communications. In Proceedings of the International Conference on World Wide Web, Hong Kong, China, 1–5 May 2008. [Google Scholar]
- Xu, L.; Member, S.; Huang, C. Computation Efficient Multicast Key Distribution. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 577–587. [Google Scholar]
- Liu, X.; Huang, J.; Gao, X. A Probabilistically Weakly Secure Network Coding Scheme in Multipath Routing for WSNs. Sensors 2017, 17, 1133. [Google Scholar]
- Yoneyama, K.; Yoshida, R.; Kawahara, Y.; Kobayashi, T.; Fuji, H.; Yamamoto, T. Multi-cast Key Distribution: Scalable, Dynamic and Provably Secure Construction. In Proceedings of the International Conference on Provable Security, Nanjing, China, 10–11 November 2016; Springer: Basel, Switzerland, 2016. [Google Scholar]
- Chen, Y.R.; Tzeng, W.G. Group key management with efficient rekey mechanism: A Semi-Stateful approach for out-of-Synchronized members. Comput. Commun. 2016, 98, 31–42. [Google Scholar] [CrossRef]
- Shamir, A. How to Share a Secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Blakley, G.R. Safeguarding cryptographic keys. In Proceedings of the AFIPS, New York, NY, USA, 4–7 June 1979. [Google Scholar]
- Laih, C.S.; Lee, J.Y.; Harn, L. A new threshold scheme and its application in designing the conference key distribution cryptosystem. Inf. Process. Lett. 1989, 32, 95–99. [Google Scholar] [CrossRef]
- Just, M.; Kranakis, E.; Krizanc, D.; van Oorschot, P. On key distribution via true broadcasting. In Proceedings of the ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 2–4 November 1994. [Google Scholar]
- Sun, Y.; Trappe, W.; Liu, K.R. Network-Aware Security for Group Communications; Springer: New York, NY, USA, 2008. [Google Scholar]
- Lin, J. Efficient Group Key Management Protocol with One-Way Key Derivation. In Proceedings of the IEEE Conference on Local Computer Networks Anniversary, Sydney, Australia, 17 November 2005. [Google Scholar]
- Wuu, L.C.; Hung, C.H.; Kuo, W.C. Group Key Management based on (2, 2) Secret Sharing. KSII Trans. Internet Inf. Syst. 2014, 8, 1144–1156. [Google Scholar]
- Ganesan, V.C.; Periyakaruppan, A.; Lavanya, R. Cost-effective polynomial-based multicast–unicast key distribution framework for secure group communication in IPv6 multicast networks. IET Inf. Secur. 2016, 10, 252–261. [Google Scholar] [CrossRef]
- Mahmood, Z.; Ning, H.; Ghafoor, A. A Polynomial Subset-Based Efficient Multi-Party Key Management System for Lightweight Device Networks. Sensors 2017, 17, 670. [Google Scholar] [CrossRef] [PubMed]
- Li, C.H.; Pieprzyk, J. Conference Key Agreement from Secret Sharing. In Proceedings of the Australasian Conference on Information Security and Privacy; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1587, pp. 64–76. [Google Scholar]
- Werner, W. Polynomial interpolation: Lagrange versus Newton. Math. Comput. 1984, 43, 205–217. [Google Scholar] [CrossRef]
| Cost | Member Join | Member Left |
|---|---|---|
| Group controller (GC) | ||
| Group member |
| Operations | GC | Group Member |
|---|---|---|
| Modular addition | + 1 | |
| Modular subtraction | ||
| Modular multiplication | + 1 | |
| Modular division | 0 | |
| Hash operations |
| Cost | Member Join | Member Left |
| Storage cost | GC | Group Member |
| Time (μs) | CEGKD | PMUKD [27] | RS(MD5) [16] | Scheme in [26] | KeyDer-GKM [19] | LKH [4] |
|---|---|---|---|---|---|---|
| GC | 894 | 178 | 294 | 14963 | 706 | 840 |
| member | 26 | 36 | 45 | 49 | 170 | 211 |
| Change | Computation Cost | Communication Cost | Storage Cost |
|---|---|---|---|
| GC | Increase by about 3% | Increase by 16 bytes | Increase by 25% |
| Member | Decrease by more than 87.7% | Increase by 75% |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiao, R.; Ouyang, H.; Lin, Y.; Luo, Y.; Li, G.; Jiang, Z.; Zheng, Q. A Computation-Efficient Group Key Distribution Protocol Based on a New Secret Sharing Scheme. Information 2019, 10, 175. https://doi.org/10.3390/info10050175
Jiao R, Ouyang H, Lin Y, Luo Y, Li G, Jiang Z, Zheng Q. A Computation-Efficient Group Key Distribution Protocol Based on a New Secret Sharing Scheme. Information. 2019; 10(5):175. https://doi.org/10.3390/info10050175
Chicago/Turabian StyleJiao, Runhai, Hong Ouyang, Yukun Lin, Yaoming Luo, Gang Li, Zaiyu Jiang, and Qian Zheng. 2019. "A Computation-Efficient Group Key Distribution Protocol Based on a New Secret Sharing Scheme" Information 10, no. 5: 175. https://doi.org/10.3390/info10050175
APA StyleJiao, R., Ouyang, H., Lin, Y., Luo, Y., Li, G., Jiang, Z., & Zheng, Q. (2019). A Computation-Efficient Group Key Distribution Protocol Based on a New Secret Sharing Scheme. Information, 10(5), 175. https://doi.org/10.3390/info10050175




