Efficient Security Scheme for Disaster Surveillance UAV Communication Networks
Abstract
1. Introduction
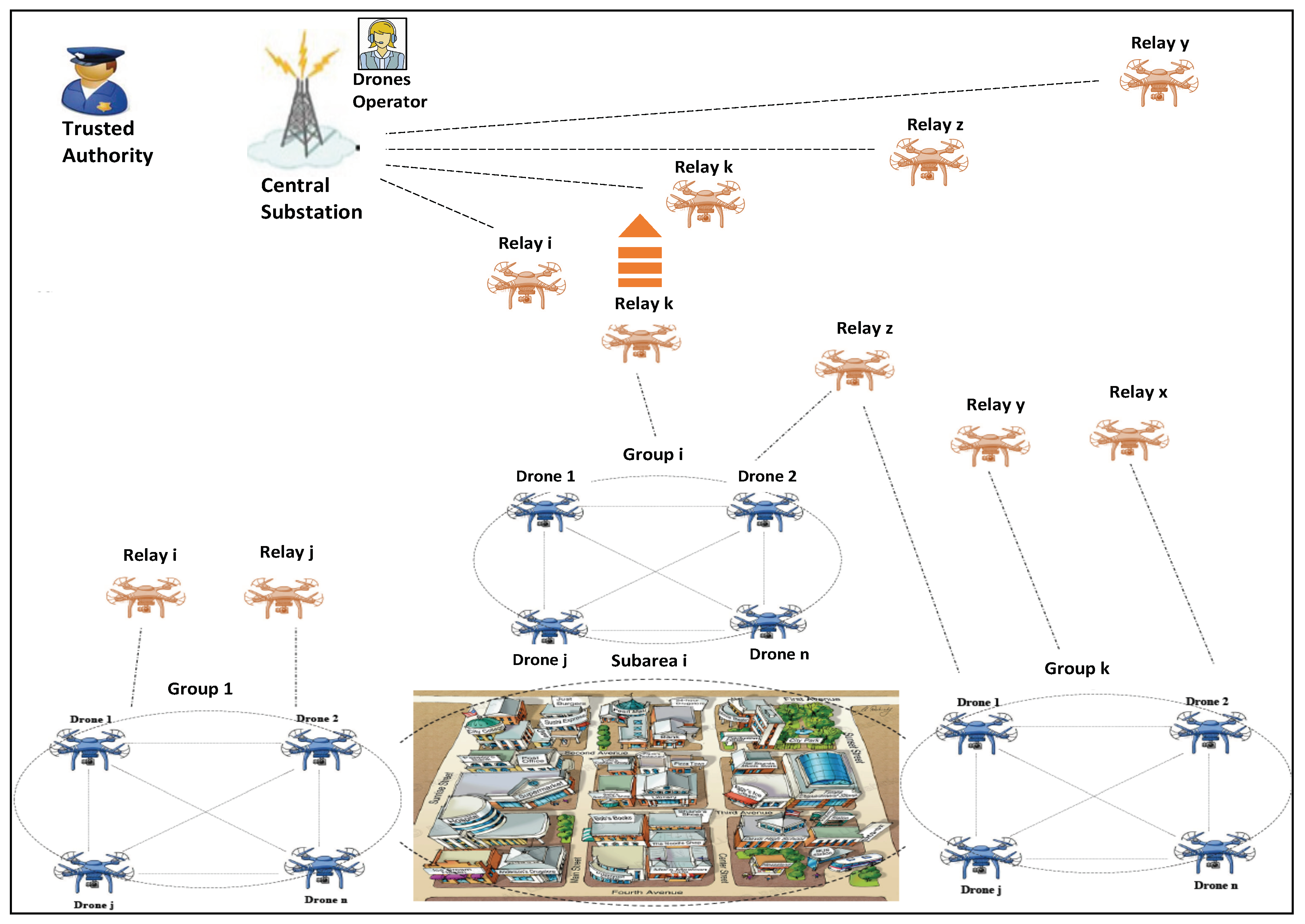
- Central ground substation (CS) which collects data from relaying drones.
- Clusters of drones participating in the same application that perform some kind of surveillance/sensing application.
- Cluster head drone(s) in each cluster have two main functions. Firstly, they keep administrative membership data for the cluster. Secondly, they collect sensed data perform data fusion, integrity and confidentiality. Due to a large distance between cluster head(s) and central substation (CS), cluster head(s) do not send data directly to it. Instead, cluster head(s) transmits the data to relay drones. Please note that it is also possible that each node in the cluster can communicate with the relay node and that a single or a few nodes keep administrative functions.
- Relay drones which need to leave the cluster and return to the ground station in order to re-charge the batteries. Relay drones collect the data from the cluster head and hand them over to the central substation.
2. Related Work
3. System Model
3.1. Network Model Using IEEE 802.11ah
3.2. UAV Application Model
3.3. Adversary Model
3.4. Security Requirements and Design Goals
4. Preliminaries of the Security Protocol
4.1. The Ring-LWE Encryption Scheme
4.1.1. The Ring-LWE Problem
4.1.2. Key Generation
4.1.3. Encryption
4.1.4. Decryption
5. The Proposed Security Scheme
5.1. Setup Phase
- Issuing Key ParametersTA provides the keying parameters for each party in the connection:TA issues a public/private key pair for ; as a private key and as public key, and then sends the key pair to via secure channel.TA assigns a set of unique secret IDs and secret session keys Ks and sends it securely to the . then provides a unique secret ID = and a secret session key K = for each drone, which uses to prove its identity to . While the is utilized during the round that the drone plays the cluster head role to organize the joining/leaving groups process:assigns these security parameters for the drones before releasing them to begin their missions ().
- Forming the GroupsThe whole disaster area is divided into subareas ; each subarea is monitored by certain number of air drones m that are arranged in k groups; the number of the groups in the subarea is varied according to the size and importance of the subarea. For instance, the city downtown usually is more crucial than uptown, as downtown is crowded by people and has most of the business and important buildings.Drones can join or leave the group at any time as they can fly to the group or fly back to the to recharge their batteries. When the drones are flying over the subarea to collect information about the subarea, forward messages from the earth, or take photos/videos; they are called Monitoring Drones. While the drones are flying back to the substation, they are working as Relaying Drones to forward the messages from the cluster heads to the base station . In other words, the monitoring drone is converted to a relaying drone once it leaves its group to recharge the battery.For each group , the assigns a different number of cluster heads for each reading round, where is varied for each group per reading round. For example, substation connects to four groups in the subarea ; each group has 20 drones. For group , substation chooses drones and to be two cluster heads for round 1; drones , , and to be three cluster heads for round 2; and so on. The chain of cluster heads for each group is assigned by the corresponding , i.e., the operator.The groups in the same subarea are using different frequency channels to reduce the interference with other groups’ connections.
- Programming the DronesAt , the drones’ operator prepares each drone for its assigned task. The object is assigned for each drone; includes which subarea the drone has to scan, at what level it will fly, which group to enroll, and what mission to accomplish, such as taking photos/videos for the subarea, connecting with and forwarding the messages from the earth, or transferring first aid medical equipment. In addition, the operator determines when that specific drone works as a cluster head of its group. Consequently, the drone’s path is pre-planned, i.e., the drones are tracked by GPS, so that, if a drone is redirected from the specified path, a suspicious action alarm is declared. For instance, the operator assigns for the drone .The operator sets two fingerprints’ features [32] for each drone; these features extract characteristics from transmitted signals from the wireless devices and their environments to generate non-forgeable signatures. The first feature is a Location Feature to guarantee that the drones stick to their paths. For instance, the drone mission is to join group at the subarea to take photos. Thus, the location feature for is to be within the subarea. If it moves outside , this means that it is controlled by a malicious adversary or a malfunction. Then, the operator does not depend on the ’s information. The second feature, which is the Data Feature , is utilized to detect the compromised drones. The operator assigns a certain protocol that the drone should follow before encrypting the collected data; if the drone does not apply that protocol, it is declared as a compromised node. The data feature could be a specific padding data that were added in certain bits, repeating the data in the packet in a pre-determined sequence, or adding the drone’s ID in different location. For example, the operator assigns a certain padding data for to add in specific bits in the message before encryption:In addition, the features are changed every time that the drone returns to the station for recharging its battery, i.e., the drone has a new mission in a different subarea and assigned other new features.
5.2. Surveillance UAV Network Operation Phase
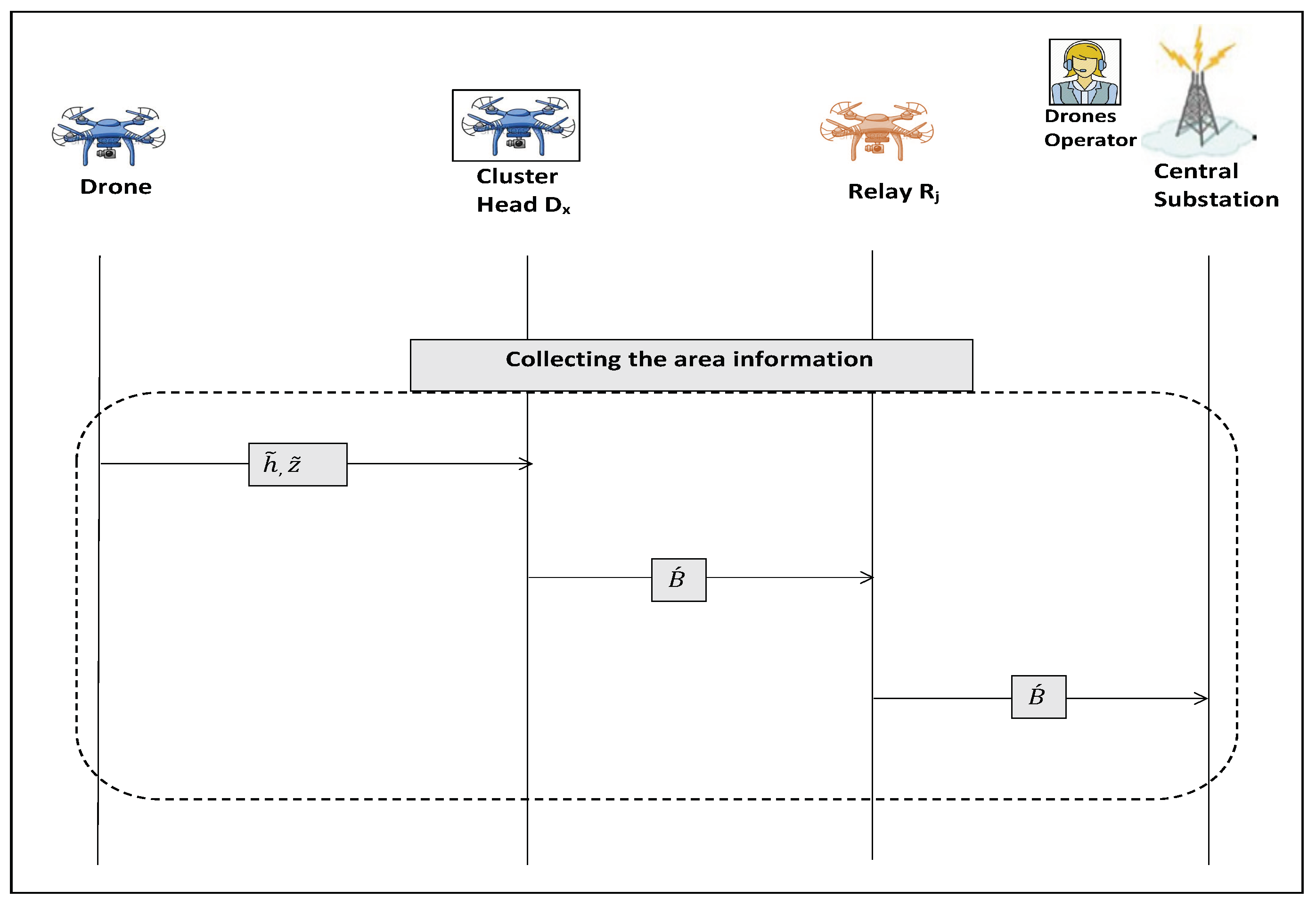
5.2.1. Collecting the Area Information Procedure
- Collecting the Area InformationAt the beginning of the reading round, each drone in the group scans its subarea , collects the required information, concatenates its secret ID to the collected data and inserting the data feature , and then encrypts the result by the public key :The message is encoded to a polynomial . Error polynomials are generated from . Next, computeThe encrypted message equalsThen, sends its message to the current cluster heads of the group; assume that there are two cluster heads and for the current readings round:Each cluster head and concatenates all the received messages of the group:where i is the number of drones enrolled in the group during the current reading round.Then, and encrypt B by their session keys and :before forwarding the result messages to the via different relay drones R:where the relays and are drones flying towards the .
- Verifying the Collected InformationWhen receives all the messages , where n is the number of the groups in the subarea (notice that each group sends two messages from two different cluster heads), it first decrypts and de-concatenates each message in . For example, the messages that were sent by the cluster heads and in the group are decrypted and then the resulted B is concatenated as:For each message , decrypts:using the inverse NTT. Then, the original message is recovered using a decoder.checks the drone’s features: if the drone is flying within its assigned location ; in addition, checks the presence of the inserted .Then, it verifies the validity of before accepting the message as an accurate reading.then compares between the received data from different drones (that assigned for the same task) and accepts the information from the majority; all drones of the groups in the subarea are expected to send similar readings to . Figure 3 shows the main procedure for collecting the subarea information. Figure 3 demonstrates the Collecting the Area Information procedure.
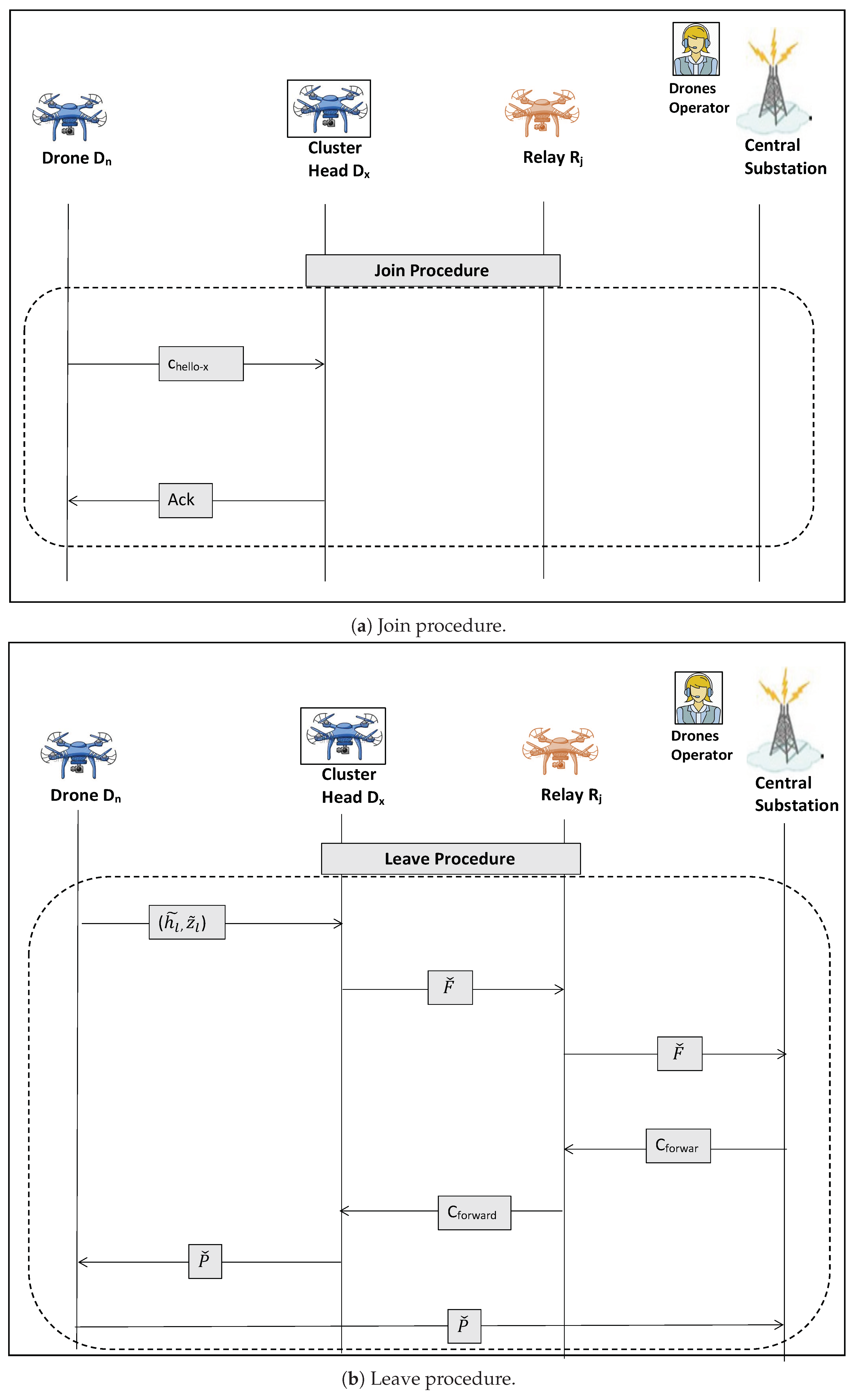
5.2.2. Join/Leave Procedures
- Join Process:When a new drone is sent from to join a specific group, the operator provides by the session keys and of the current cluster heads and . Then, encrypts two hello messages using and ; notice that the hello messages include timestamps and random nonce to prevent the replay attacks:Then, the drone forwards them to and :The cluster heads reply to by acknowledgment messages encrypted by their session keys. Figure 4a shows the join procedures.
- Leave Procedure:The drone , which needs to leave for battery recharging, embeds a recharge request in its previous reading message , encrypts it to and sends the result to the current cluster heads of the group and ; they include the message in the current total aggregated message F, encrypt F to before forwarding to .The then sends a forward request to the group heads and ; this request asks them to forward the future aggregated messages of the group via the returning drone , which becomes the relay . The forward requests are encrypted by the cluster heads session keys and :The forward request messages reach the cluster heads via the previously returning relays, e.g., and .Then, and aggregate the group readings in one message P and send their encrypted group messages to the relay drone :stores until it enters the ’s range and then forwards them to . Figure 4b shows the leave procedures:
6. Security Analysis
6.1. Information Integrity
6.1.1. Compromised Drones
6.1.2. Intercepted Messages
6.2. Information Availability
6.3. Confidentiality
7. Performance Evaluation
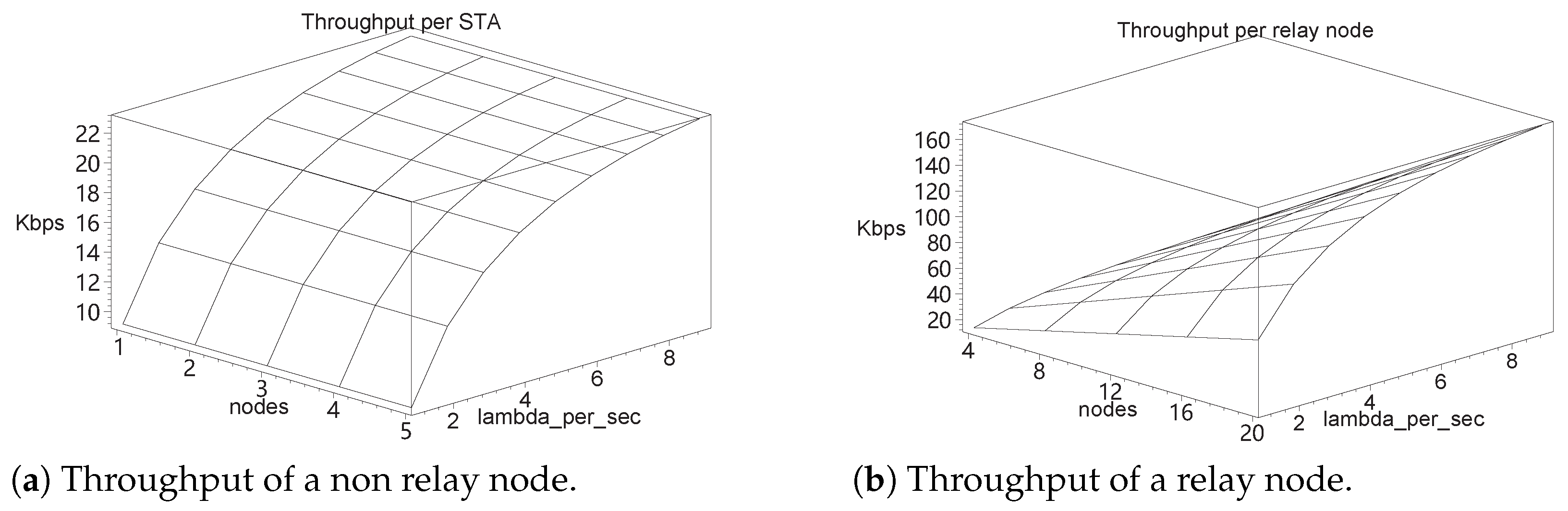
7.1. Network Performance
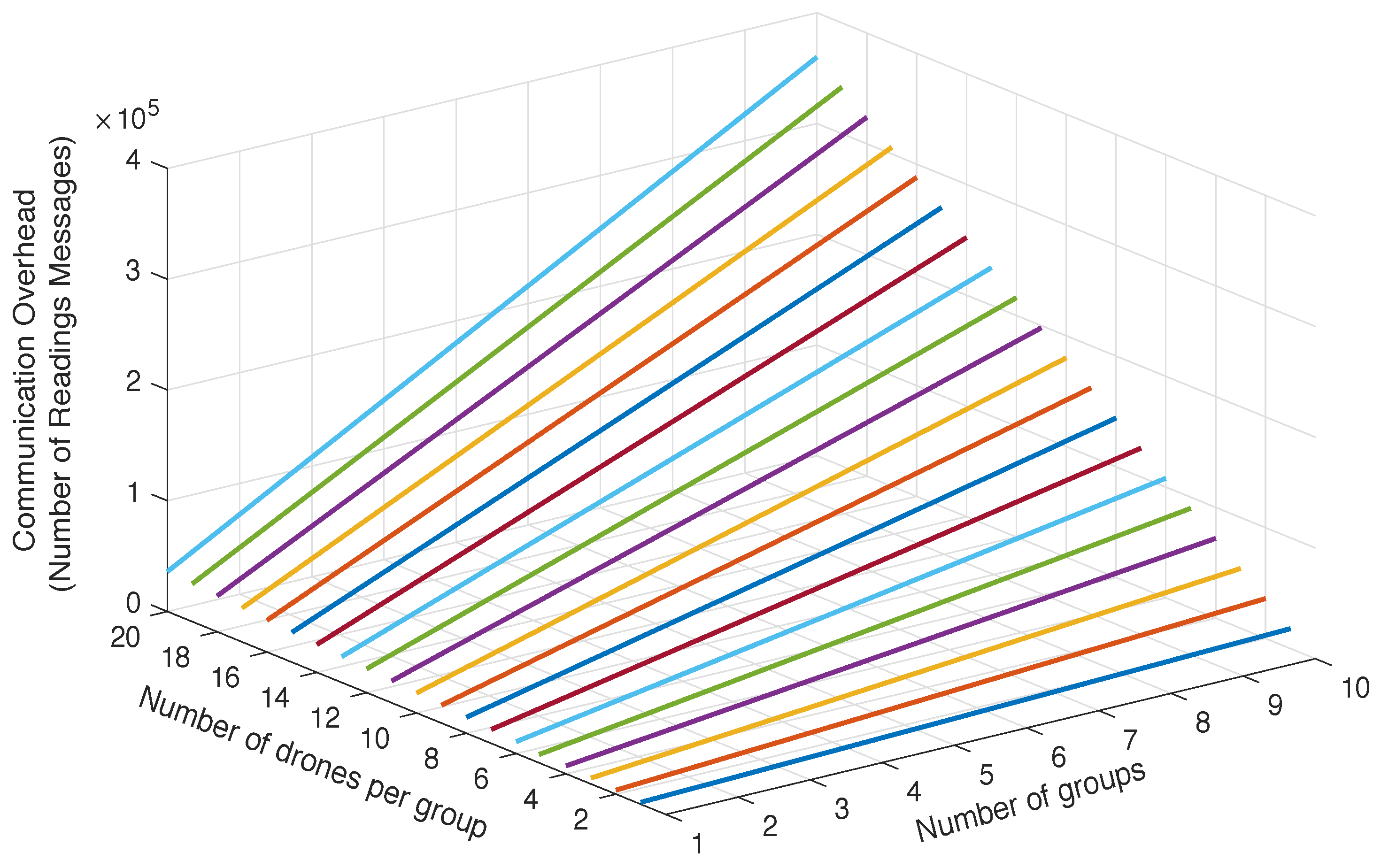
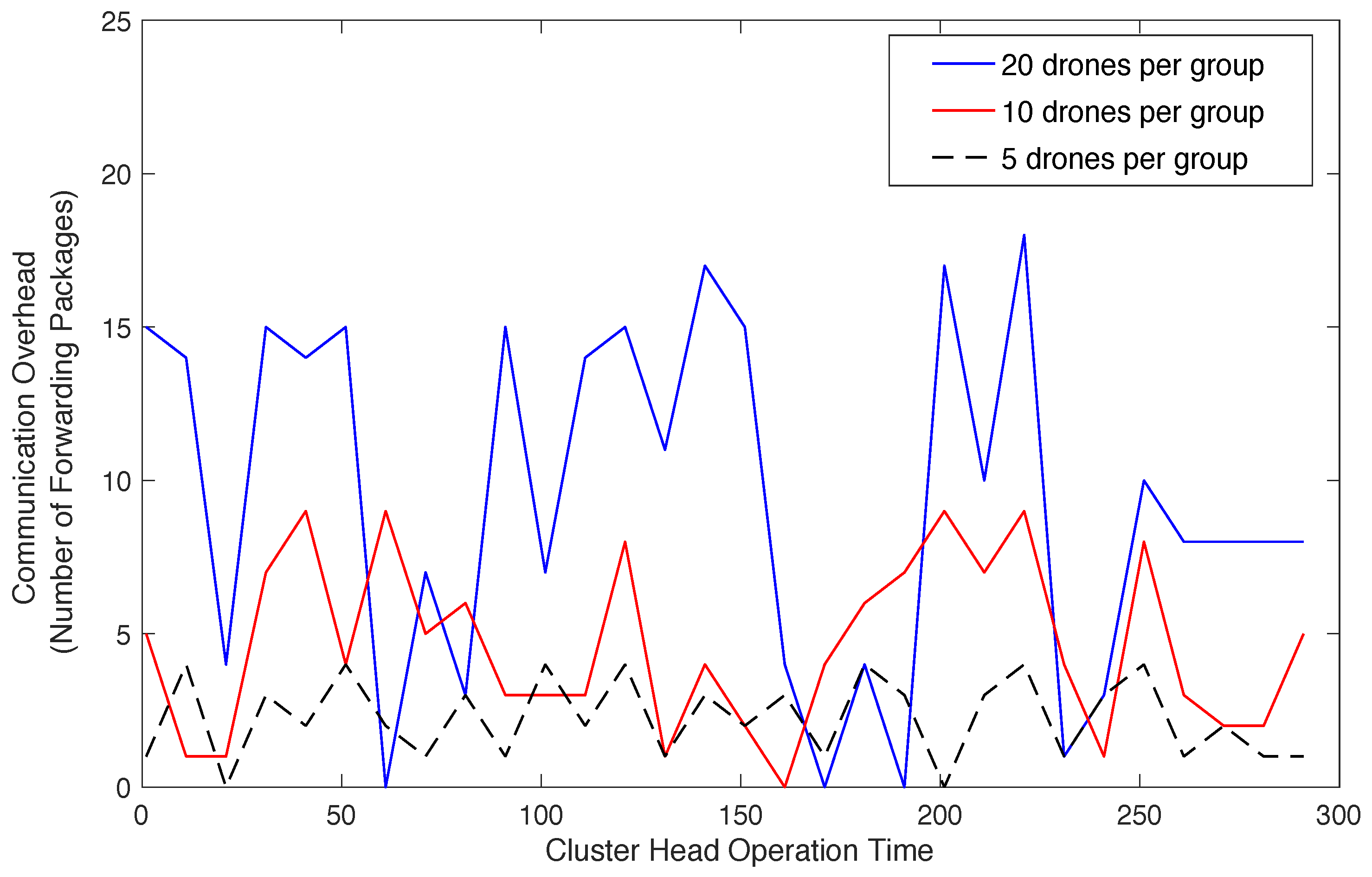
7.2. Communication Complexity
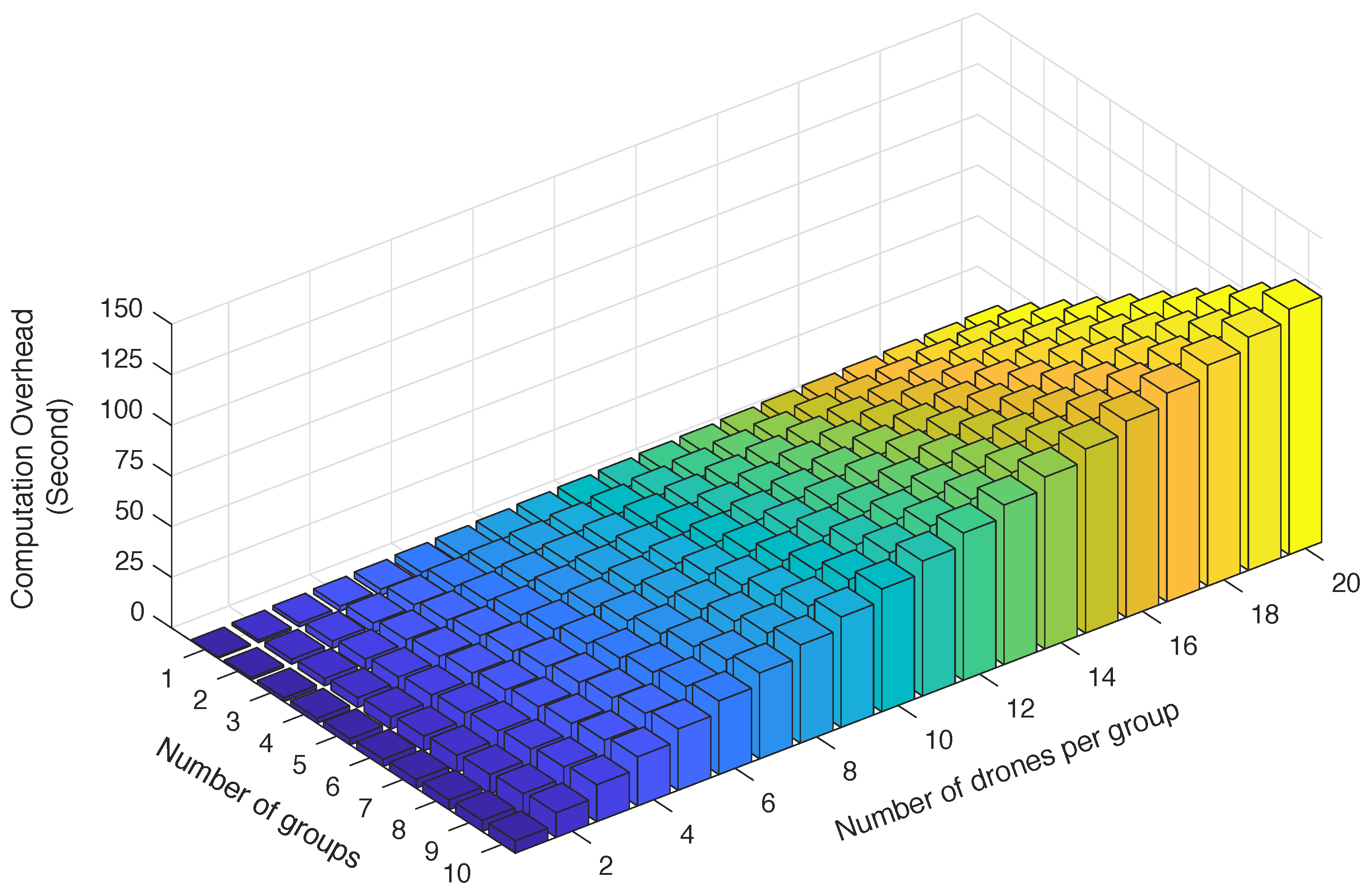
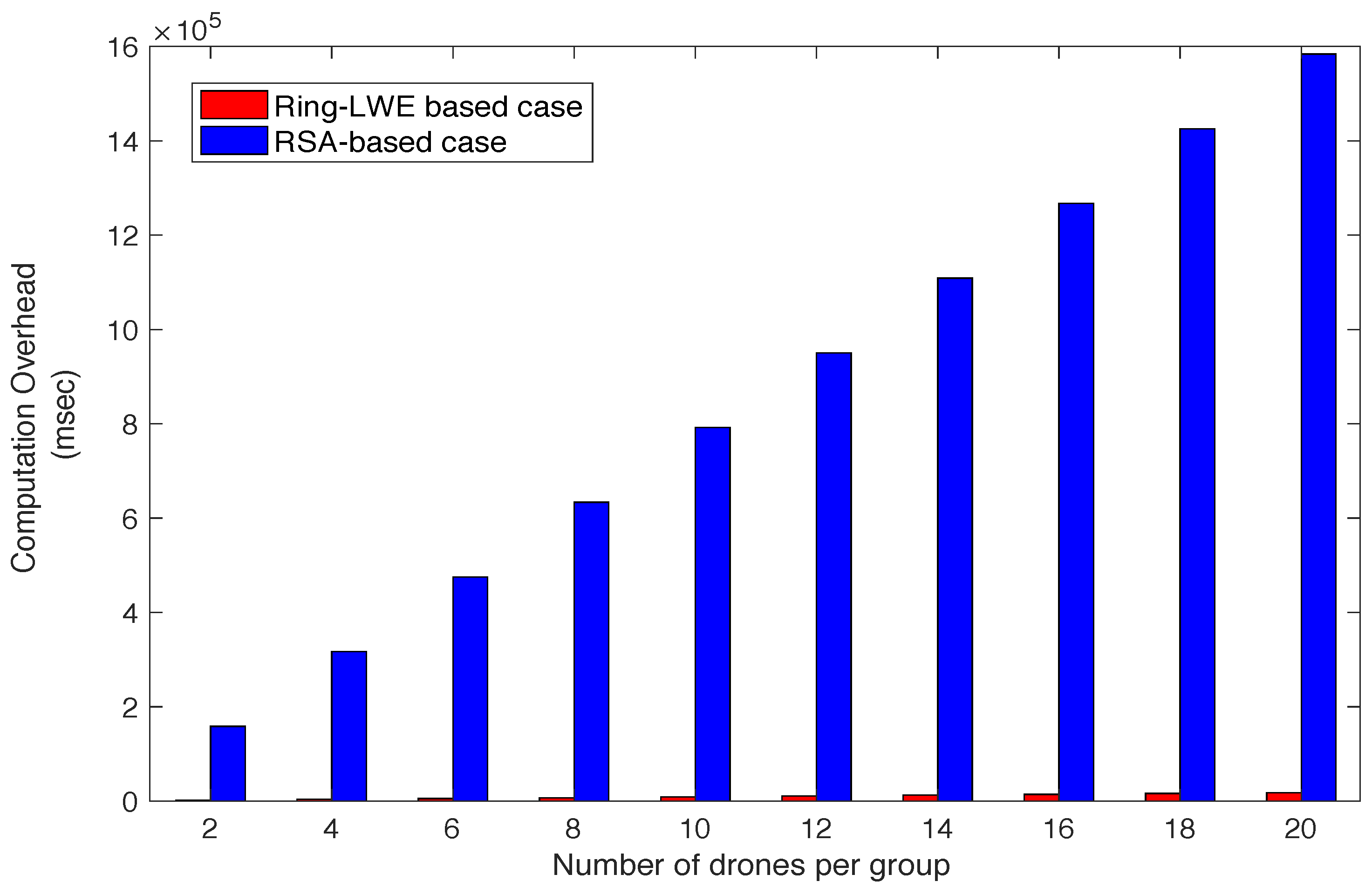
7.3. Computation Complexity
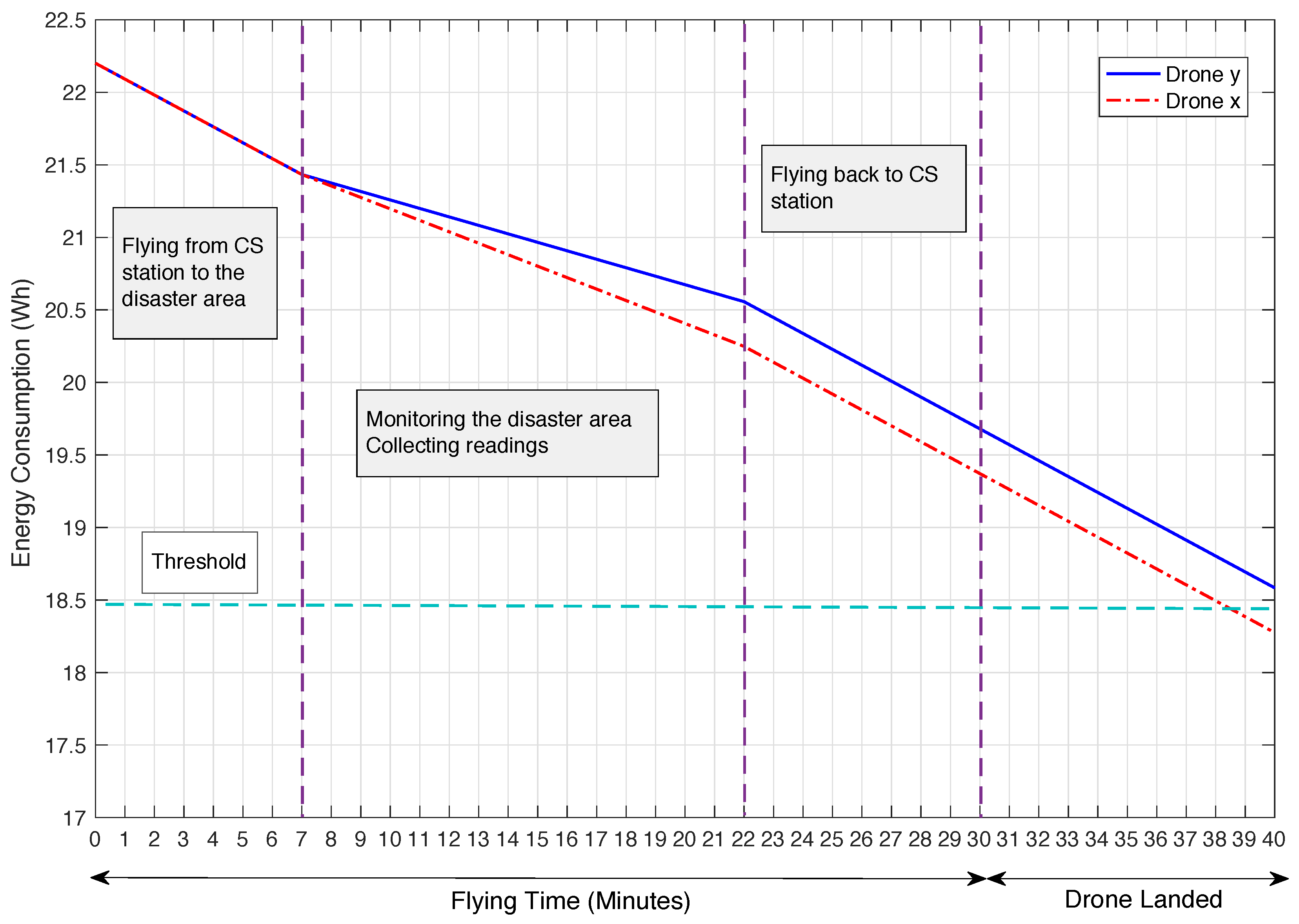
7.4. Energy Consumption Estimation
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of Important Issues in UAV Communication Networks. IEEE Commun. Surv. Tutor. 2016, 18, 1123–1152. [Google Scholar] [CrossRef]
- Frew, E.; Brown, T. Airborne Communication Networks for Small Unmanned Aircraft Systems. Proc. IEEE 2008, 96, 2008–2027. [Google Scholar] [CrossRef]
- Silva, M.R.; Souza, E.S.; Alsina, P.J.; Francisco, H.C.; Medeiros, A.A.D.; Nogueira, M.B.; de Alburquerque, G.G.L.A.; Dantas, J.B.D. Communication Network Architecture Specification for Multi-UAV System Applied to Scanning Rocket Impact Area First Results. In Proceedings of the 2017 Latin American Robotics Symposium (LARS) and 2017 Brazilian Symposium on Robotics (SBR), Curitiba, Brazil, 8–11 November 2017. [Google Scholar]
- Chen, T.; Xiao, Y.; Zhao, X.; Gao, T.; Xu, Z. 4G UAV Communication System and Hovering Height Optimization for Public Safety. In Proceedings of the 2017 IEEE 19th International Conference on e-Health Networking, Applications and Services (Healthcom), Dalian, China, 12–15 October 2017. [Google Scholar]
- Arnold, S.; Montgomery, G.; Gopal, R.; Losada, D. Validation of high-speed broadband satellite communications on airborne platforms. In Proceedings of the Military Communications Conference (MILCOM), San Jose, CA, USA, 31 October–3 November 2010. [Google Scholar]
- Nintanavongsa, P.; Pitimon, I. Impact of Sensor Mobility on UAV-based Smart Farm Communications. In Proceedings of the 2017 International Electrical Engineering Congress (iEECON), Pattaya, Thailand, 8–10 March 2017. [Google Scholar]
- Chakareski, J. Aerial UAV-IoT Sensing for Ubiquitous Immersive Communication and Virtual Human Teleportation. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017. [Google Scholar]
- Ali, M.Z.; Misic, J.; Misic, V.B. Efficiency of Restricted Access Window Scheme of IEEE 802.11ah under Non-ideal Channel Condition. In Proceedings of the 2018 IEEE International Conference on Green Computing and Communications (GreenCom-2018), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar]
- Ali, M.Z.; Misic, J.; Misic, V.B. Differentiated QoS to Heterogeneous IoT Nodes in IEEE 802.11ah RAW Mechanism. In Proceedings of the IEEE Globecom 2018, Abu Dhabi, UAE, 9–13 December 2018. [Google Scholar]
- Zhu, Y.; Huang, Q.; Li, J.; Wu, D. Design and evaluation of airborne communication networks. In Proceedings of the 2015 Seventh International Conference on Ubiquitous and Future Networks, Sapporo, Japan, 7–10 July 2015. [Google Scholar]
- Guo, W.; Devine, C.; Wang, S. Performance Analysis of Micro Unmanned Airborne Communication Relays for Cellular Networks. In Proceedings of the International Symposium on Communication Systems, Networks & Digital Sign (CSNDSP), Manchester, UK, 23–25 July 2014. [Google Scholar]
- Kumbhar, A.; Güvenc, I.; Singh, S.; Tuncer, A. Exploiting LTE-Advanced HetNets and FeICIC for UAV-assisted Public Safety Communications. IEEE Access 2018, 6, 783–796. [Google Scholar] [CrossRef]
- Scherer, J.; Rinner, B. Short and Full Horizon Motion Planning for Persistent multi-UAV Surveillance with Energy and Communication Constraints. In Proceedings of the 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS 2017), Vancouver, BC, Canada, 24–28 September 2017. [Google Scholar]
- He, H.; Zhang, S.; Zeng, Y.; Zhang, R. Joint Altitude and Beam-width Optimization for UAV-Enabled Multiuser Communications. IEEE Commun. Lett. 2018, 22, 344–347. [Google Scholar] [CrossRef]
- Ladosz, P.; Oh, H.; Chen, W. Prediction of Air-to-Ground Communication Strength for Relay UAV Trajectory Planner in Urban Environments. In Proceedings of the 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Vancouver, BC, Canada, 24–28 September 2017. [Google Scholar]
- Huo, Y.; Dong, X.; Lu, T.; Xu, W.; Yuen, M. Distributed and Multi-layer UAV Network for the Next-generation Wireless Communication. arXiv Preprint, 2018; arXiv:1805.01534. [Google Scholar]
- Lin, X.; Yajnanarayana, V.; Muruganathan, S.; Gao, S.; Asplund, H.; Maattanen, H.; Bergström, M.; Euler, S.; Wang, Y. The sky is not the limit: LTE for unmanned aerial vehicles. IEEE Commun. Mag. 2018, 56, 204–210. [Google Scholar] [CrossRef]
- Xu, X.; Zeng, Y.; Guan, Y.; Zhang, R. Overcoming endurance issue: UAV-enabled communications with proactive caching. IEEE J. Sel. Areas Commun. 2018, 36, 1231–1244. [Google Scholar] [CrossRef]
- Sharma, V.; Jayakody, D.; Srinivasan, K. On the Positioning Likelihood of UAVs in 5G Networks. Phys. Commun. 2018, 31, 1–9. [Google Scholar] [CrossRef]
- Yap, K.M.; Eu, K.S.; Low, J.M. Investigating Wireless Network Interferences of Autonomous Drones with Camera Based Positioning Control System. In Proceedings of the 2016 International Computer Symposium (ICS), Chiayi, Taiwan, 15–17 December 2016; pp. 369–373. [Google Scholar]
- Kagawa, T.; Ono, F.; Shan, L.; Takizawa, K.; Miura, E.; Li, H.; Kojima, F.; Kato, S. A study on latency-guaranteed multi-hop wireless communication system for control of robots and drones. In Proceedings of the 2017 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017; pp. 417–421. [Google Scholar]
- Biswas, S.; Misic, J.; Misic, V.B. DDoS Attack on WAVE-enabled VANET Through Synchronization. In Proceedings of the IEEE Globecom 2012, Anaheim, CA, USA, 3–7 December 2012. [Google Scholar]
- Altawy, R.; Youssef, A. Security, privacy, and safety aspects of civilian drones: A survey. ACM Trans. Cyber-Phys. Syst. 2017, 1, 7. [Google Scholar] [CrossRef]
- Liu, C.; Quek, T.; Lee, J. Secure UAV Communication in the Presence of Active Eavesdropper. In Proceedings of the 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 11–13 October 2017. [Google Scholar]
- Rubin, S.; Grefe, W.; Bouabana-Tebibel, T.; Chen, S.; Shyu, M.; Simonsen, K. Cyber-Secure UAV Communications using Heuristically Inferred Stochastic Grammars and Hard Real-Time Adaptive Waveform Synthesis and Evolution. In Proceedings of the 2017 IEEE International Conference on Information Reuse and Integration (IRI), San Diego, CA, USA, 4–6 August 2017. [Google Scholar]
- Sharma, V.; Kumar, R.; Srinivasan, K.; Jayakody, D. Coagulation Attacks over Networked UAVs: Concept, Challenges, and Research Aspects. Int. J. Eng. Technol. 2018, 7, 183–187. [Google Scholar]
- Sharma, V.; Jayakody, D.; You, I.; Kumar, R.; Li, J. Secure and Efficient Context-Aware Localization of Drones in Urban Scenarios. IEEE Commun. Mag. 2018, 56, 120–128. [Google Scholar] [CrossRef]
- Regev, O. The Learning with Errors Problem (Invited Survey). In Proceedings of the IEEE Conference on Computational Complexity, Cambridge, MA, USA, 9–11 June 2010. [Google Scholar]
- Ducas, L.; Durmus, A. Ring-LWE in polynomial rings. In Proceedings of the 15th International Conference on Practice and Theory in Public Key Cryptography, Darmstadt, Germany, 21–23 May 2012; pp. 34–51. [Google Scholar]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On ideal lattices and learning with errors over rings. J. ACM 2013, 60, 43. [Google Scholar] [CrossRef]
- Roy, S.; Vercauteren, F.; Mentens, N.; Chen, D.; Verbauwhede, I. Compact Ring-LWE Cryptoprocessor. In Proceedings of the 16th International Workshop on Cryptographic Hardware and Embedded Systems—CHES 2014, Busan, Korea, 23–26 September 2014; pp. 371–391. [Google Scholar]
- Xu, Q.; Zheng, R.; Saad, W.; Han, Z. Device Fingerprinting in Wireless Networks: Challenges and Opportunities. IEEE Commun. Surv. Tutor. 2016, 18, 94–104. [Google Scholar] [CrossRef]
- De Clercq, R.; Roy, S.; Vercauteren, F.; Verbauwhede, I. Efficient software implementation of ring-LWE encryption. In Proceedings of the 2015 Design, Automation, and Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2015. [Google Scholar]


| Information Integrity |
|
| Information Availability |
|
| Confidentiality |
|
| Parameters | Numerical Values |
|---|---|
| Duration of Time slot, | 52 |
| Bit error rate (BER) | bits/s |
| Minimum physical (PHY) layer header | |
| Arbitration inter frame space (AIFSN) | 2 |
| Data rate | 650 Kbps |
| MAC service data unit (MSDU) length | 256 octets |
| Short Inter-frame space (SIFS) duration | 160 |
| MAC header length | 14 bytes |
| PS-Poll | |
| PS-Poll-ACK | |
| Block acknowledgment (BA) | |
| Maximum retry limit, R | 7 |
| Max. number of antennas in AP, | 1 |
| Number of antennas in STA | 1 |
| Bandwidth | 4 MHz |
| OFDM symbol duration | 40 |
| Number of bits in an OFDM symbol | 54 |
| Modulation and Coding scheme, MCS | 0 |
| Beacon interval, BI | 1 s |
| RAW slot | 200 ms |
| Minimum contention window size | 31 |
| Transaction opportunity (TXOP) limit | 2 packets |
| Idle mode energy consumption | J |
| Receive mode energy consumption | J |
| Transmit mode energy consumption | J |
| Drone Type | Communication Overhead | |
|---|---|---|
| Per Round | Total | |
| Monitoring | 2 | 1800 |
| Relay | 0 | 1 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdallah, A.; Ali, M.Z.; Mišić, J.; Mišić, V.B. Efficient Security Scheme for Disaster Surveillance UAV Communication Networks. Information 2019, 10, 43. https://doi.org/10.3390/info10020043
Abdallah A, Ali MZ, Mišić J, Mišić VB. Efficient Security Scheme for Disaster Surveillance UAV Communication Networks. Information. 2019; 10(2):43. https://doi.org/10.3390/info10020043
Chicago/Turabian StyleAbdallah, Asmaa, M. Zulfiker Ali, Jelena Mišić, and Vojislav B. Mišić. 2019. "Efficient Security Scheme for Disaster Surveillance UAV Communication Networks" Information 10, no. 2: 43. https://doi.org/10.3390/info10020043
APA StyleAbdallah, A., Ali, M. Z., Mišić, J., & Mišić, V. B. (2019). Efficient Security Scheme for Disaster Surveillance UAV Communication Networks. Information, 10(2), 43. https://doi.org/10.3390/info10020043





