Identifying Influential Nodes in Complex Networks Based on Local Effective Distance
Abstract
1. Introduction
2. Related Work
3. The KDEC Method
3.1. Preliminaries
3.2. The KDEC Model
3.3. The KDEC Algorithm
| Algorithm 1: KDEC. |
| Input: ; 1: network G with N nodes and E edges; Output: traverse the nodes;
|
3.4. Time Complexity
4. Experimental Evaluation
4.1. Real-World Network Data Sets
4.2. Algorithm Description
4.3. Evaluate Metric
4.3.1. SIR Model
4.3.2. Kendall Correlation Coefficient
4.4. Evaluation Analysis
4.4.1. Efficiency Analysis
4.4.2. Infectivity Analysis
4.4.3. Kendall Coefficient Analysis
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Erdös, P.; Rényi, A. Publication of the Mathematical Institute of the Hungarian Academy of Sciences. 1960. Available online: http://www.scirp.org/(S(351jmbntvnsjt1aadkposzje))/reference/ReferencesPapers.aspx?ReferenceID=1448571 (accessed on 8 October 2019).
- Barrat, A.; Barthelemy, M.; Vespignani, A. Dynamical Processes on Complex Networks; Cambridge University Press: New York, NY, USA, 2008. [Google Scholar]
- Dorogovtsev, S.N.; Goltsev, A.V.; Mendes, J.F. Critical phenomena in complex networks. Rev. Mod. Phys. 2008, 80, 1275. [Google Scholar] [CrossRef]
- Raven, B. The Bases of Social Power; University of Michigan: Oxford, UK, 1959; pp. 150–167. [Google Scholar]
- Zhou, T.; Liu, J.G.; Bai, W.J. Behaviors of susceptible-infected epidemics on scale-free networks with identical infectivity. Phys. Rev. 2006, 74, 056109. [Google Scholar] [CrossRef]
- Pastorsatorras, R.; Vespignani, A. Epidemic Spreading in Scale-Free Networks. Phys. Rev. Lett. 2000, 86, 3200–3203. [Google Scholar] [CrossRef]
- Shah, D.; Zaman, T.R. Detecting sources of computer viruses in networks: Theory and experiment. In Proceedings of the 2010 ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems, New York, NY, USA, 14–18 June 2010. [Google Scholar]
- Tao, L.; Liu, X.; Li, H. An Immune-Based Model for Computer Virus Detection. Lect. Notes Comput. Sci. 2005, 3810, 59–71. [Google Scholar]
- Doer, B.; Fouz, M.; Friedrich, T. Why rumors spread so quickly in social networks. Commun. ACM 2012, 55, 70. [Google Scholar] [CrossRef]
- Moreno, Y.; Nekovee, M.; Pacheco, A.F. Dynamics of rumor spreading in complex networks. Phys. Rev. 2004, 69, 066130. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H. A Survey on Smart Grid Communication Infrastructures: Motivations, Requirements and Challenges. IEEE Commun. Surv. Tutor. 2013, 15, 5–20. [Google Scholar] [CrossRef]
- Liu, J.; Lin, J.; Guo, Q.; Zhou, T. Locating influential nodes via dynamics-sensitive centrality. Sci. Rep. 2016, 6, 21380. [Google Scholar] [CrossRef]
- Brockmann, D.; Helbing, D. The hidden geometry of complex, network—Driven contagion phenomena. Science 2013, 342, 1337–1342. [Google Scholar] [CrossRef]
- Fei, L.; Zhang, Q.; Deng, Y. Identifying influential nodes in complex networks based on the inverse—Square law. Phys. Stat. Mech. Appl. 2018, 512, 1044–1059. [Google Scholar] [CrossRef]
- Ma, L.; Ma, C.; Zhang, H.; Wang, B. Identifying influential spreaders in complex networks based on gravity formula. Phys. Stat. Mech. Appl. 2016, 451, 205–212. [Google Scholar] [CrossRef]
- Helbing, D. Globally networked risks and how to respond. Nature 2013, 497, 51–59. [Google Scholar] [CrossRef]
- Gao, C.; Lan, X.; Zhang, X.; Deng, Y. A bio-inspired methodology of identifying influential nodes in complex networks. PLoS ONE 2013, 8, e66732. [Google Scholar] [CrossRef]
- Ttcher, L.; Woolley-Meza, O.; Goles, E. Connectivity disruption sparks explosive epidemic spreading. Phys. Rev. 2016, 93, 042315. [Google Scholar]
- Gao, L.; Song, J.; Nie, F.; Zou, F.; Sebe, N.; Shen, H.T. Graph-without-Cut: An ideal graph learning for image segmentation. In Proceedings of the Thirtieth Aaai Conference on Artificial Intelligence, Phoenix, AZ, USA, 12–17 February 2016. [Google Scholar]
- Song, J.; Gao, L.; Zou, F.; Yan, Y.; Sebea, N. Deep and fast: Deep learning hashing with semi-supervised graph construction. Image Vis. Comput. 2016, 55, 101–108. [Google Scholar] [CrossRef]
- Lv, L.; Chen, D.; Ren, X.L.; Zhang, Q.M.; Zhang, Y.C.; Zhou, T. Vital nodes identification in complex networks. Phys. Rep. 2016, 650, 1–63. [Google Scholar]
- Bonacich, P. Factoring and weighting approaches to status scores and clique identification. J. Math. Cal Sociol. 1972, 2, 113–120. [Google Scholar] [CrossRef]
- Kitsak, M.; Gallos, L.K.; Havlin, S.; Liljeros, F.; Muchnik, L.; Stanley, H.E.; Makse, H.A. Identification of influential spreaders in complex networks. Nat. Phys. 2010, 6, 888. [Google Scholar] [CrossRef]
- Zhao, S.X.; Rousseau, R.; Ye, F.Y. h-Degree as a basic measure in weighted networks. J. Inf. 2011, 5, 668–677. [Google Scholar] [CrossRef]
- Hage, P.; Harary, F. Eccentricity and centrality in networks. Soc. Netw. 1995, 17, 57–63. [Google Scholar] [CrossRef]
- Sabidussi, G. The centrality index of a graph. Psychometrika 1966, 31, 581–603. [Google Scholar] [CrossRef] [PubMed]
- Katz, L. A new status index derived from sociometric analysis. Psychometrika 1953, 18, 39–43. [Google Scholar] [CrossRef]
- Freeman, L.C. Centrality in social networks conceptual clarification. Soc. Netw. 1978, 1, 215–239. [Google Scholar] [CrossRef]
- Yan, G.; Zhou, T.; Hu, B.; Fu, Z.; Wang, B. Efficient routing on complex networks. Phys. Rev. 2006, 73, 046108. [Google Scholar] [CrossRef] [PubMed]
- Zeng, A.; Zhang, C. Ranking spreaders by decomposing complex networks. Phys. Lett. 2013, 377, 1031–1035. [Google Scholar] [CrossRef]
- Estrada, E.; Rodriguez–Velazquez, J.A. Subgraph centrality in complex networks. Phys. Rev. 2005, 71, 056103. [Google Scholar] [CrossRef]
- Poulin, R.; Boily, M.C.; Masse, B.R. Dynamical systems to define centrality in social networks. Soc. Netw. 2000, 22, 187–220. [Google Scholar] [CrossRef]
- Brin, S.; Page, L. The anatomy of a large–scale hypertextual web search engine. Comput. Netw. ISDN Syst. 1998, 30, 107–117. [Google Scholar] [CrossRef]
- Lv, L.; Zhang, Y.; Yeung, C.H.; Zhou, T. Leaders in social networks, the delicious case. PLoS ONE 2011, 6, e21202. [Google Scholar]
- Kleinberg, J.M. Authoritative sources in a hyperlinked environment. J. ACM 1999, 46, 604–632. [Google Scholar] [CrossRef]
- Chen, D.B.; Gao, H.; Lv, L.; Zhou, T. Identifying influential nodes in largescale directed networks: The role 410 of clustering. PLoS ONE 2013, 8, e77455. [Google Scholar]
- Barabasi, A.; Albert, R. Emergence of scaling in random networks. Science 1999, 286, 509–512. [Google Scholar] [CrossRef] [PubMed]
- Kang, B.; Chhipi-Shrestha, G.; Deng, Y.; Hewageb, K.; Sadiq, R. Stable strategies analysis based on the utility of Z-number in the evolutionary games. Appl. Math. Comput. 2018, 324, 202–217. [Google Scholar] [CrossRef]
- Christakis, N.A.; Fowler, J.H. Social contagion theory: Examining dynamic social networks and human behavior. Stat. Med. 2013, 32, 556–577. [Google Scholar] [CrossRef] [PubMed]
- Yu, Z.; Shao, J.; Yang, Q.; Sun, Z. Profitleader: Identifying leaders in networks with profit capacity. World Wide Web 2019, 22, 533–553. [Google Scholar] [CrossRef]
- Hu, Y.; Ji, S.; Feng, L.; Jin, Y. Quantify and maximise global viral influence through local network information. arXiv 2015, arXiv:1509.03484. [Google Scholar]
- Anderson, R.M.; Anderson, B.; May, R.M. Infectious Diseases of Humans: Dynamics and Control; Oxford University Press: New York, NY, USA, 1991. [Google Scholar]
- Kendall, M.G. A new measure of rank correlation. Biometrika 1938, 30, 81–93. [Google Scholar] [CrossRef]
- Moreno, Y.; Pastor-Satorras, R.; Vespignani, A. Epidemic outbreaks in complex heterogeneous networks. Eur. Phys. J. 2002, 26, 521–529. [Google Scholar] [CrossRef]
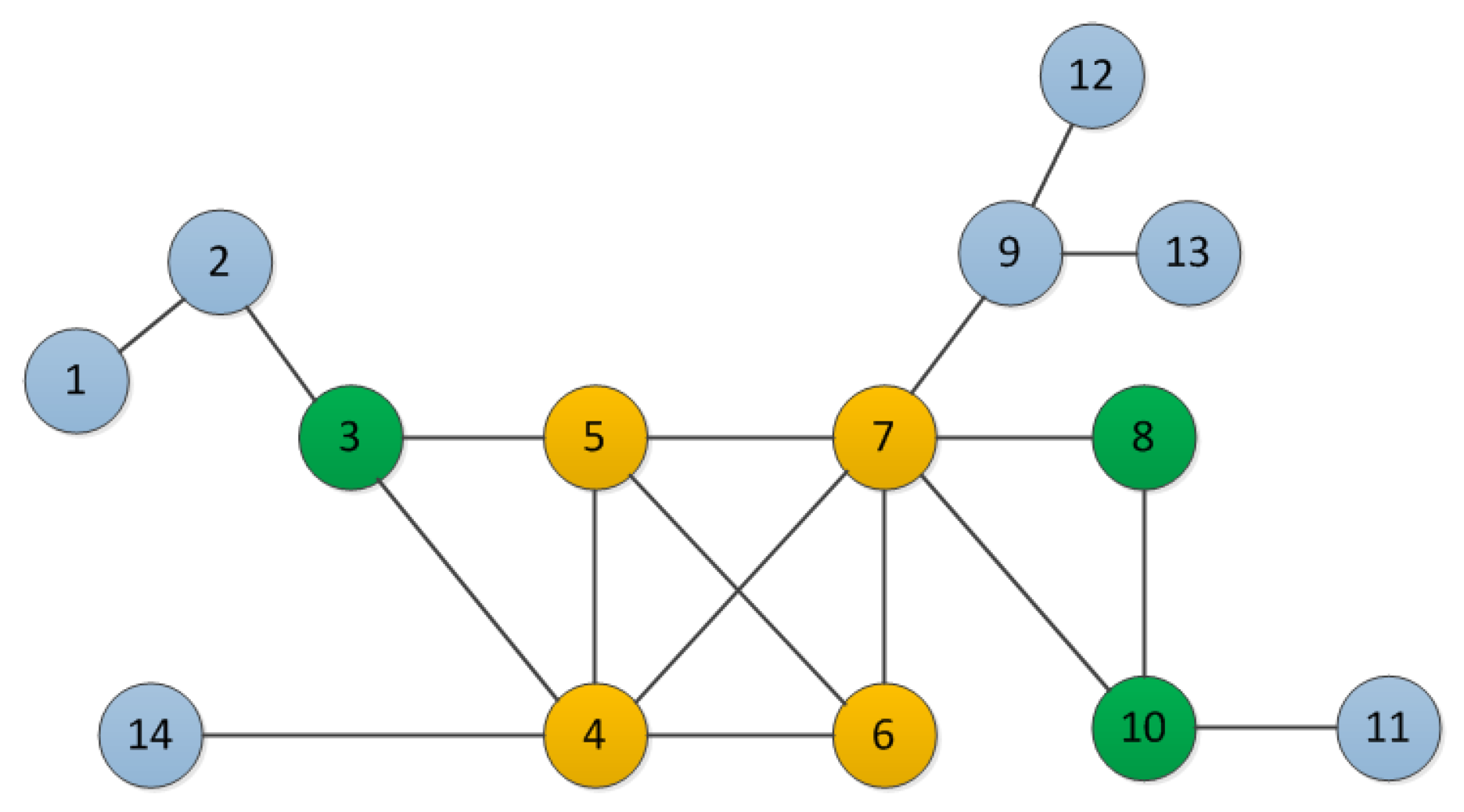



| node | 1 | 2 | 3 | 4 | 5 | 14 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| K-shell | 1 | 1 | 2 | 3 | 3 | 1 | 3 | 3 | 2 | 1 | 2 | 2 | 1 | 1 |
| Degree | 1 | 2 | 3 | 5 | 4 | 1 | 3 | 6 | 2 | 3 | 3 | 1 | 1 | 1 |
| node | 7 | 4 | 5 | 6 | 3 | 10 | 8 | 9 | 2 | 14 | 11 | 13 | 12 | 1 |
| Rank | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| Data Sets | |||||
|---|---|---|---|---|---|
| Arenas-email | 1133 | 5451 | 9.62 | 71 | 0.2202 |
| Friendship | 1858 | 12,534 | 5.76 | 85 | 0.167 |
| As2000010 | 6474 | 12,572 | 3.883 | 1458 | 0.252 |
| Bio-dmela | 7393 | 25,569 | 6.916 | 17 | 0.5706 |
| Web-spam | 4767 | 37,375 | 15.681 | 477 | 0.2859 |
| Ca-astroph | 18,771 | 198,050 | 21.34 | 236 | 0.677 |
| Rank | CC | EC | Hits | H-index | PR | PL | KDEC | KDEC Value | SIR | SIR Value |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 7 | 7 | 7 | 4 | 7 | 7 | 7 | 28.7212 | 7 | 2.907 |
| 2 | 4 | 4 | 4 | 5 | 4 | 4 | 4 | 21.1858 | 4 | 2.494 |
| 3 | 5 | 5 | 5 | 6 | 9 | 5 | 5 | 16.6559 | 5 | 2.455 |
| 4 | 9 | 6 | 6 | 7 | 5 | 9 | 6 | 11.7006 | 6 | 2.31 |
| 5 | 3 | 9 | 3 | 3 | 10 | 10 | 3 | 6.9794 | 3 | 2.03 |
| 6 | 6 | 10 | 9 | 8 | 3 | 3 | 10 | 5.3482 | 10 | 1.93 |
| 7 | 10 | 3 | 10 | 10 | 6 | 6 | 8 | 3.4368 | 9 | 1.852 |
| 8 | 2 | 8 | 8 | 2 | 2 | 2 | 9 | 2.5331 | 8 | 1.843 |
| 9 | 1 | 14 | 14 | 9 | 1 | 1 | 2 | 0.9289 | 2 | 1.54 |
| 10 | 14 | 13 | 2 | 1 | 13 | 11 | 14 | 0.6624 | 14 | 1.468 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, J.; Wang, B.; Sheng, J.; Dai, J.; Hu, J.; Chen, L. Identifying Influential Nodes in Complex Networks Based on Local Effective Distance. Information 2019, 10, 311. https://doi.org/10.3390/info10100311
Zhang J, Wang B, Sheng J, Dai J, Hu J, Chen L. Identifying Influential Nodes in Complex Networks Based on Local Effective Distance. Information. 2019; 10(10):311. https://doi.org/10.3390/info10100311
Chicago/Turabian StyleZhang, Junkai, Bin Wang, Jinfang Sheng, Jinying Dai, Jie Hu, and Long Chen. 2019. "Identifying Influential Nodes in Complex Networks Based on Local Effective Distance" Information 10, no. 10: 311. https://doi.org/10.3390/info10100311
APA StyleZhang, J., Wang, B., Sheng, J., Dai, J., Hu, J., & Chen, L. (2019). Identifying Influential Nodes in Complex Networks Based on Local Effective Distance. Information, 10(10), 311. https://doi.org/10.3390/info10100311





