Qualitative Risk Assessment of Cybersecurity and Development of Vulnerability Enhancement Plans in Consideration of Digitalized Ship
Abstract
1. Introduction
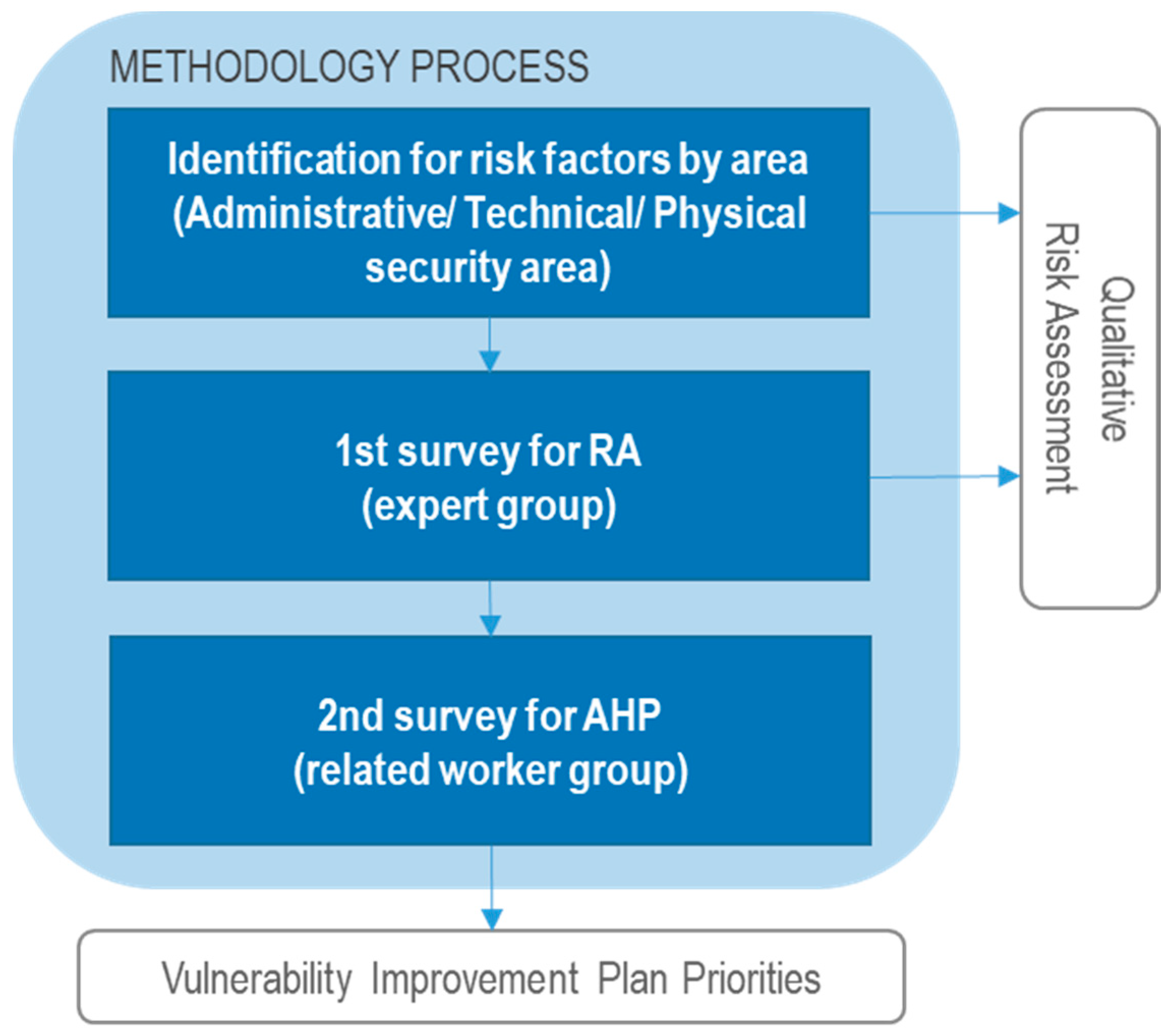
2. Methodology
2.1. Risk Factors and Risk Assessment
2.2. Analytic Hierarchy Process Analysis
3. Analysis Results
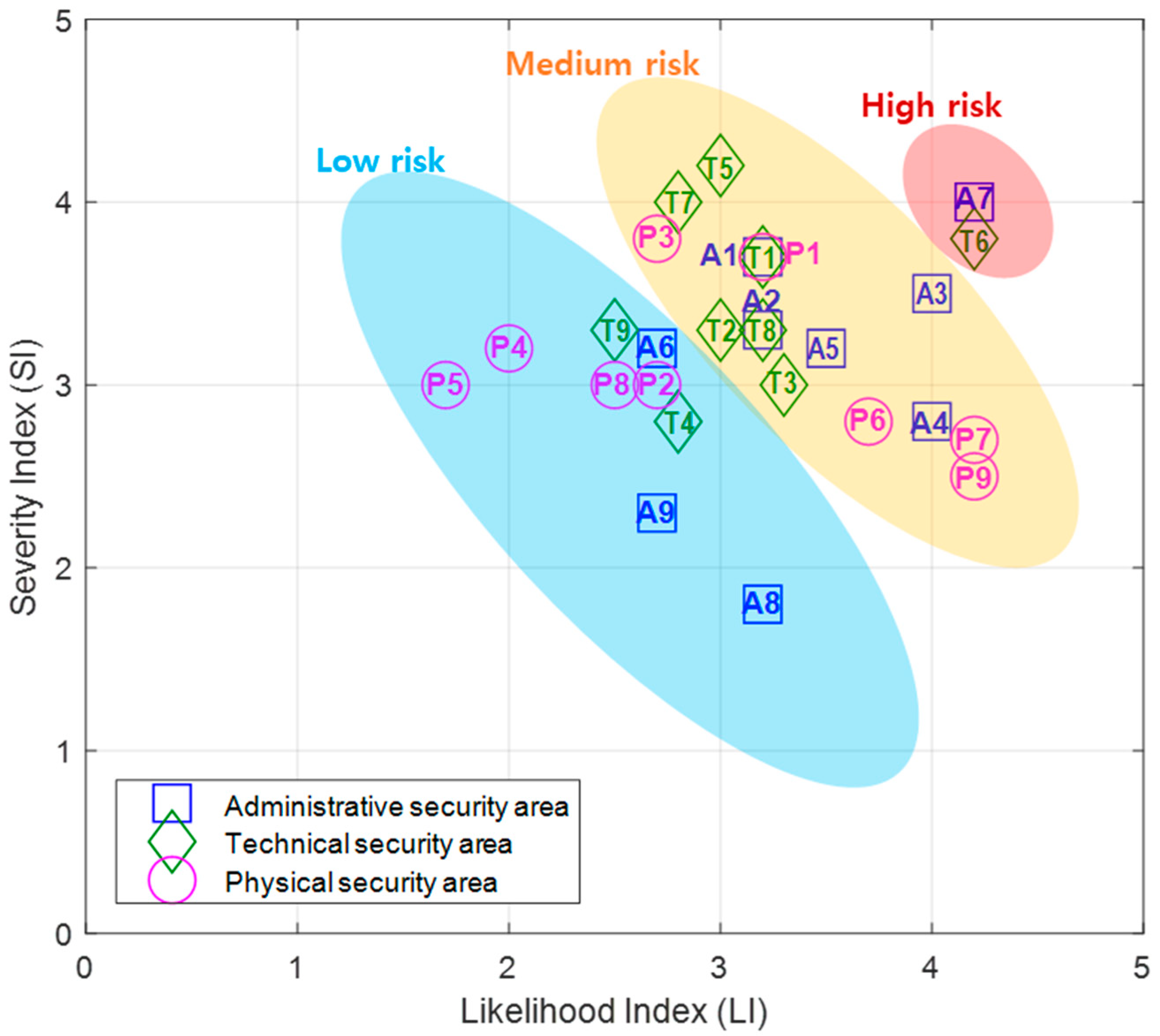
3.1. Risk Assessment Results
3.2. Vulnerability Improvement Priority
4. Discussion
4.1. Considerations and Limitations of the Study
4.2. Recommendations for Improvement Plans
5. Conclusions
- Increasing awareness of risks and educating staff about mitigation measures;
- Controlling access to cyber networks;
- Improving threat detection and blocking systems.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kessler, G.C.; Craiger, J.P.; Haass, J.C. A taxonomy framework for maritime cybersecurity: A demonstration using the automatic identification system. J. Trans. Nav. 2018, 12, 429–437. [Google Scholar] [CrossRef]
- Oikonomou, S. Maritime Cybersecurity Practices Scheme (Block Box). Master’s Thesis, School of Science Informatics and Computational Biomedicine, University of Thessaly, San Jose, CA, USA, 2019. [Google Scholar]
- You, B.; Zhang, Y.; Cheng, L.C. Review on cybersecurity risk assessment and evaluation and their approaches on maritime transportation. In Proceedings of the 30th Annual Conference of International Chinese Transportation Professionals Association, Houston, TX, USA, 19–21 May 2017; pp. 429–437. [Google Scholar]
- AON. 2018 Cybersecurity Predictions: A Shift to Managing Cyber as an Enterprise Risk, 2018 ed.; Aon Cyber Solutions: London, UK, 2018. [Google Scholar]
- CISCO. 2018 Annual Cybersecurity Report, 2018 ed.; CISCO: San Jose, CA, USA, 2018. [Google Scholar]
- COMODO. Comodo cybersecurity Q1 2018 Report, 2018 ed.; COMODO Threat Research Labs: Clifton, NJ, USA, 2018. [Google Scholar]
- FIRE-EYE. M-Trends 2018, 2018 ed.; FireEye: Milpitas, CA, USA, 2018. [Google Scholar]
- Kessler, G.C. Cybersecurity in the maritime domain. In Proceedings of the Marine Safety & Security Council; US Department of Homeland Security: Washington, DC, USA; US Coast Guard: Arlington, VA, USA, 2019; Volume 76, pp. 34–39. [Google Scholar]
- PWC. Revitalizing Privacy and Trust in a Data-Driven World: Key Findings from The Global State of Information Security Survey 2018, 2018 ed.; PwC: London, UK, 2018. [Google Scholar]
- WIPRO. State of Cybersecurity Report 2018: Foresight for the Global Cybersecurity Community, 2018 ed.; WIPRO: Bengaluru, India, 2018. [Google Scholar]
- G-CAPTAIN. Clarkson Plc Reveals Details of 2017 Cybersecurity Incident. Available online: https://gcaptain.com/clarkson-plc-reveals-details-of-2017-cyber-security-incident/ (accessed on 19 June 2019).
- Park, C.; Shi, W.; Zhang, W.; Kontovas, C.; Chang, C.H. Cybersecurity in the maritime industry: A literature review. In Proceedings of the International Association of Maritime Universities (IAMU) Conference, Tokyo, Japan, 30 October–1 November 2019. [Google Scholar]
- SAFETY-AT-SEA. Shipping Must Confront Onboard Systems’ Cyber Vulnerabilities. Available online: https://safetyatsea.net/news/2017/shipping-must-confront-onboard-systems-cyber-vulnerabilities/ (accessed on 19 June 2019).
- SAFETY-AT-SEA. Cyber Attack Hits COSCO Shipping. Available online: https://safetyatsea.net/news/2018/cyber-attack-hits-cosco-shipping/ (accessed on 19 June 2019).
- SAFETY4SEA. Lessons to be Learned from Recent Cyber Incidents. Available online: https://safety4sea.com/cm-lessons-to-be-learned-from-recent-cyber-incidents/ (accessed on 19 June 2019).
- THREAT-POST. Gold Galleon Hacking Group Plunders Shipping Industry. Available online: https://threatpost.com/gold-galleon-hacking-group-plunders-shipping-industry/131203/ (accessed on 19 June 2019).
- WORLD-MARITIME-NEWS. Hackers Access BW Group’s IT Systems. Available online: https://worldmaritimenews.com/archives/232434/hackers-access-bw-groups-it-systems-countermeasures-undertaken/ (accessed on 19 June 2019).
- ZDNET. Port of San Diego Suffers Cyber-Attack. Available online: https://www.zdnet.com/article/port-of-san-diego-suffers-cyber-attack-second-port-in-a-week-after-barcelona/ (accessed on 19 June 2019).
- SAFETY4SEA. Maersk Line: Surviving from a Cyber Attack. Available online: https://safety4sea.com/cm-maersk-line-surviving-from-a-cyber-attack/ (accessed on 19 June 2019).
- GMF; MARSH; IUMI. Global Maritime Issues Monitor, 2018 ed.; Global Maritime Forum Foundation: Copenhagen, Denmark, 2018. [Google Scholar]
- ALLIANZ. Safety and Shipping Review 2019: An Annual Review of Trends and Developments in Shipping Losses and Safety, 2019 ed.; Allianz Global Corporate & Specialty: Munich, Germany, 2019. [Google Scholar]
- CYBERCRIME-MAGAZINE. Cybercrime to Cost the World $10.5 Trillion Annually by 2025. Available online: https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/ (accessed on 9 December 2020).
- Kavallieratos, G.; Katsikas, S. Managing cyber security risks of the cyber-enabled ship. J. Mar. Sci. Eng. 2020, 8, 768. [Google Scholar] [CrossRef]
- Tam, K.; Jones, K. Maritime cyber-security policy: The scope and impact of evolving technology on international shipping. J. Cyber Policy 2018, 3, 147–164. [Google Scholar] [CrossRef]
- Rodseth, O.; Burmeister, H. Risk assessment for an unmanned merchant ship. J. TransNav 2015, 9, 147–164. [Google Scholar] [CrossRef]
- Chang, C.; Kontovas, C.; Yu, Q.; Yang, Z. Risk assessment of the operations of maritime autonomous surface ships. Reliab. Eng. Syst. Saf. 2021, 207, 1–11. [Google Scholar] [CrossRef]
- Svilicic, B.; Rudan, I.; Jugovic, A.; Zec, D. A study on cyber security threats in a shipboard Integrated Navigational System. J. Mar. Sci. Eng. 2019, 7, 364. [Google Scholar] [CrossRef]
- Awan, M.; Ghamdi, M. Understanding the vulnerabilities in digital components of an Integrated Bridge System (IBS). J. Mar. Sci. Eng. 2019, 7, 350. [Google Scholar] [CrossRef]
- Kang, N.S. Analysis of on-board ship cybersecurity. J. Kor. Soc. Mar. Eng. 2018, 42, 463–471. [Google Scholar] [CrossRef]
- BIMCO; CLIA; ICS; INTERCARGO; INTERMANAGER; INTERTANKO; IUMI; OCIMF; WSC. The Guidelines on Cyber Security Onboard Ships, 3rd ed.; INTERCARGO: London, UK, 2018. [Google Scholar]
- Miron, W.; Muita, K. Cybersecurity capability maturity models for providers for critical infrastructure. Technol. Innov. Manag. Rev. 2014, 4, 33–39. [Google Scholar] [CrossRef]
- Kang, J.M.; Hwang, H.U.; Lee, J.M.; Yun, Y.T.; Bae, B.C.; Jung, S.Y. A study on national cyber capability assessment methodology. J. Kor. Inst. Info. Secur. Cryptol. 2012, 22, 1039–1055. [Google Scholar]
- Bae, S.; Park, S.; Kim, S.J. A study on the development for the national cybersecurity capability assessment criteria. J. Kor. Inst. Info. Secur. Cryptol. 2015, 25, 1293–1314. [Google Scholar] [CrossRef]
- IMO. Provisional Agenda for the 99th Session of the Maritime Safety Committee to Be Held from 16–25 May 2018; MSC.99/1; International Maritime Organization: London, UK, 2017. [Google Scholar]
- IMO. Regulatory Scoping Exercise for the use of Maritime Autonomous Surface Ships (MASS); MSC.99/5; International Maritime Organization: London, UK, 2017. [Google Scholar]
- IMO. Maritime Cyber Risk Management in Safety Management Systems; MSC.428(98) Resolution; International Maritime Organization: London, UK, 2017. [Google Scholar]
- Hopcraft, R.; Martin, K.M. Effective maritime cybersecurity regulation—The case for a cyber code. J. Indian Ocean Reg. 2018, 14, 354–366. [Google Scholar] [CrossRef]
- IMO. Guidelines on Maritime Cyber Risk Management; MSC-FAL.1/Circ.3 Annex; International Maritime Organization: London, UK, 2017. [Google Scholar]
- IMO. International Safety Management (ISM) Code with Guidelines for Its Implementation, 5th ed.; International Maritime Organization: London, UK, 2018. [Google Scholar]
- ISO/IEC. International Standard 27001: Information Technology—Security Techniques—Information Security Management Systems—Requirements; 2013 Standard; International Organization for Standardization: Geneva, Switzerland, 2013. [Google Scholar]
- NIST. Framework for Improving Critical Infrastructure Cybersecurity, 1.1 version; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar]
- IMO. Interim Guidelines for MASS Trials; MSC.1/Circ.1604; International Maritime Organization: London, UK, 2019. [Google Scholar]
- Bernasconi, M.; Choirat, C.; Seri, R. The analytic hierarchy process and the theory of measurement. Manag. Sci. 2010, 56, 699–711. [Google Scholar] [CrossRef][Green Version]
- Saaty, T.L. The Analytic Hierarchy Process: Planning, Priority Setting, Resources Allocation; McGraw-Hill: London, UK, 1980. [Google Scholar]
- Saaty, T.L. How to make a decision: The analytic hierarchy process. Eur. J. Oper. Res. 1990, 48, 9–26. [Google Scholar] [CrossRef]
- Taherdoost, H. Decision making using the analytic hierarchy process (AHP): A step by step approach. Econ. Manag. Syst. 2017, 2, 244–246. [Google Scholar]
- BV. Rules on Cybersecurity for the Classification of Marine Units, 2018 ed.; Bureau Veritas: Paris, France, 2018. [Google Scholar]
- DEUTSCHE-FLAGGE. ISM Cybersecurity. Available online: https://www.deutsche-flagge.de/de/redaktion/dokumente/ism-rundschreiben/circ2018_4_2.pdf (accessed on 19 June 2019).
- IALA. Risk Management, IALA Guideline 1018, 3rd ed.; International Association of Marine Aids to Navigation and Lighthouse Authorities: Saint-Germain-en-Laye, France, 2013. [Google Scholar]
- IEC. Risk Management—Risk Assessment Techniques; IEC 21010:2009 Standard; International Electrotechnical Commission: Geneva, Switzerland, 2009. [Google Scholar]
- KR. Guidelines of Maritime Cybersecurity, 1.0 version; Korean Register: Busan, South Korea, 2017. [Google Scholar]
- Han, S.H. A practical approaches to decrease the consistency index in AHP. In Proceedings of the 5th SCIS & ISIS 2014, Kitakyushu, Japan, 3–6 December 2014; pp. 867–872. [Google Scholar]
- Lee, J.G. A Study on Decision Factor of Residential Environments of NEW STAY Using the AHP. Master’s Thesis, Graduate School of Real Estate Studies, Konkuk University, Seoul, Korea, 2015. [Google Scholar]
- KASS. Project Detail. KASS (Korea Autonomous Surface Ship) Project. Available online: http://kassproject.org/en/info/projectdetail.php (accessed on 12 May 2021).
- MGL. Maritime Safety Act. MGL (Ministry of Government Legislation). Available online: https://elaw.klri.re.kr/kor_service/lawView.do?hseq=49260&lang=ENG/ (accessed on 9 December 2020).
- MGL. Enforcement Decree of the Maritime Safety Act. MGL (Ministry of Government Legislation). Available online: https://elaw.klri.re.kr/kor_service/lawView.do?hseq=53293&lang=ENG/ (accessed on 9 December 2020).
- IMO. The International Ship and Port Facility Security (ISPS) Code, 2003 ed.; International Maritime Organization: London, UK, 2003. [Google Scholar]
- IMO. Measures to Enhance Maritime Security—Cyber Risk Management in Safety Management Systems; MSC 101/4/4; International Maritime Organization: London, UK, 2019. [Google Scholar]
- MGL. International Ship and Port Facility Security Act. MGL (Ministry of Government Legislation). Available online: https://elaw.klri.re.kr/kor_service/lawView.do?hseq=51649&lang=ENG/ (accessed on 9 December 2020).
- MGL. Enforcement Decree of the International Ship and Port Facility Security Act. MGL (Ministry of Government Legislation). Available online: https://elaw.klri.re.kr/kor_service/lawView.do?hseq=49955&lang=ENG/ (accessed on 9 December 2020).


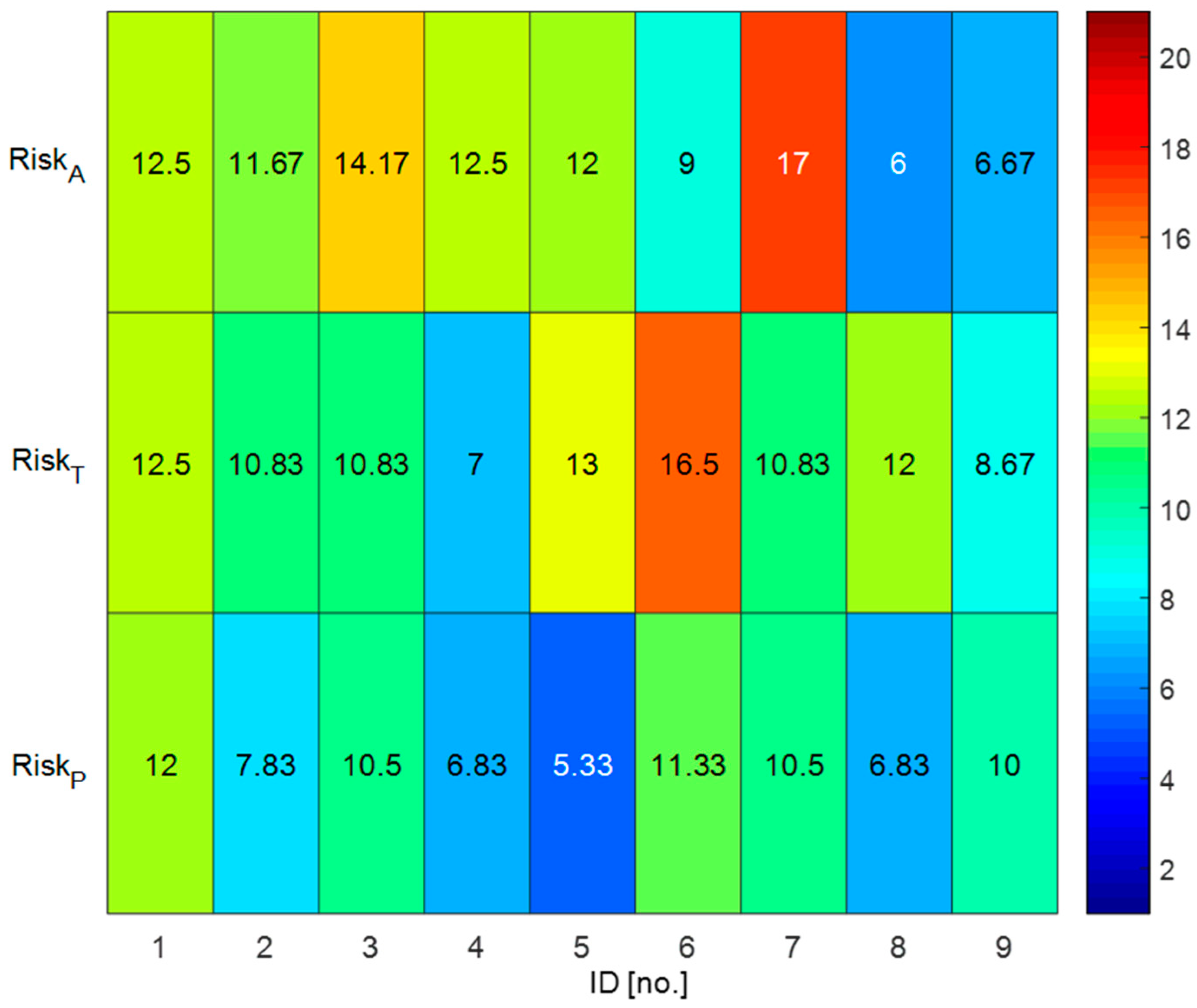
| Security Areas | Risk Factors * in Case of Control Failure | Identification Code (ID) |
|---|---|---|
| Administrative Security | 1. Raise awareness on information protection and conduct education targeting staff on board as well as on land | A1 |
| 2. Access limitation of visitors (port-related officials, technicians, agents, etc.) | A2 | |
| 3. Upgrade hardware (H/W) and software (S/W), and S/W maintenance | A3 | |
| 4. Update anti-virus and malware prevention S/W tools | A4 | |
| 5. System of regulating remote access | A5 | |
| 6. Access to information is only allowed to authorized staff | A6 | |
| 7. Control the use of portable media (USB, portable PC, etc.) | A7 | |
| 8. Policy for discarding equipment including data | A8 | |
| 9. Establish contingency plans for cyberattacks | A9 | |
| Technical Security | 1. Limitation and control of network port, protocol, and service | T1 |
| 2. Configure network equipment such as firewall, router, and switch | T2 | |
| 3. Detect, block, and warn of cyberattacks through the system | T3 | |
| 4. Data encryption by utilizing a virtual private network (VPN) | T4 | |
| 5. Wireless access control with encrypted keys | T5 | |
| 6. Install anti-malicious code software and regularly install patch files | T6 | |
| 7. Hardware and software security configuration (system access limit excluding administrator) | T7 | |
| 8. Protect emails and web browsers | T8 | |
| 9. Support data backup and recovery | T9 | |
| Physical Security | 1. Set up physical security area and access control | P1 |
| 2. Design and apply physical security for office, working space, and facility | P2 | |
| 3. Access control and information system isolation of unauthorized users | P3 | |
| 4. Secure continuous availability and confidentiality from the cut-off of power supply and support facilities | P4 | |
| 5. Protect power supply and communication cables supporting data transmission and information facilities from being damaged | P5 | |
| 6. Ban on carrying any equipment, information, and software outside without prior approval | P6 | |
| 7. In case of reuse and discarding of equipment including storage media, remove data and licensed S/W and confirm the removal | P7 | |
| 8. Protect user information and check the management of unused equipment | P8 | |
| 9. Desk organization policy for documents and portable storage media | P9 |
| Survey | Working Area | Respondents (No.) | Percentage (%) |
|---|---|---|---|
| 1st Survey for RA (Expert Group) | Cybersecurity Certification | 6 | - |
| 2nd Survey for AHP (Workers in Related Agencies) | Policy | 15 | 11.8 |
| Shipping | 20 | 15.7 | |
| Maritime Affairs | 33 | 26.0 | |
| Information and Communication | 24 | 18.9 | |
| Security Management | 6 | 4.7 | |
| Etc. | 29 | 22.8 | |
| Total | 127 * (Online: 41, Field: 76) | 100.0 (** Effective Response Rate: 28.2) |
| Index | Likelihood | Severity | RA | Risk Level | Color |
|---|---|---|---|---|---|
| 5 4 3 2 1 | Very Likely Likely Moderate Unlikely Very Unlikely | Very Severe Severe Moderate Not Severe Very not Severe | 21–25 16–20 11–15 6–10 1–5 | Very High Risk High Risk Medium Risk Low Risk Very Low Risk |  |
| Security Areas (Level-1) | Assessment Items (Level-2) | |
|---|---|---|
| I | Administrative Security | 1. Raise awareness on information protection and conduct education targeting staff on board as well as on land 2. Control the use of portable media (USB, portable PC, etc.) 3. Upgrade H/W and S/W, and software maintenance 4. Establish contingency plans for cyberattacks |
| II | Technical Security | 1. Limitation and control of network port, protocol, and service 2. Detect, block, and warn of cyberattacks through the system 3. Wireless access control with encrypted keys 4. Support data backup and recovery |
| III | Physical Security | 1. Set up physical security area and access control 2. Ban on carrying any equipment, information, and software outside without prior approval 3. Secure continuous availability and confidentiality from the cut-off of power supply and support facilities 4. In case of reuse and discarding of equipment including storage media, remove data and licensed S/W and confirm the removal |
| Category (Weighting) | Security Area | Vulnerabilities | Score | Rank |
|---|---|---|---|---|
| I (0.363) | Administrative Security | I-1 | 0.128 | 1 |
| I-2 | 0.096 | 4 | ||
| I-3 | 0.081 | 6 | ||
| I-4 | 0.049 | 11 | ||
| II (0.377) | Technical Security | II-1 | 0.122 | 2 |
| II-2 | 0.12 | 3 | ||
| II-3 | 0.066 | 10 | ||
| II-4 | 0.069 | 9 | ||
| III (0.281) | Physical Security | III-1 | 0.088 | 5 |
| III-2 | 0.07 | 7 | ||
| III-3 | 0.069 | 8 | ||
| III-4 | 0.042 | 12 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yoo, Y.; Park, H.-S. Qualitative Risk Assessment of Cybersecurity and Development of Vulnerability Enhancement Plans in Consideration of Digitalized Ship. J. Mar. Sci. Eng. 2021, 9, 565. https://doi.org/10.3390/jmse9060565
Yoo Y, Park H-S. Qualitative Risk Assessment of Cybersecurity and Development of Vulnerability Enhancement Plans in Consideration of Digitalized Ship. Journal of Marine Science and Engineering. 2021; 9(6):565. https://doi.org/10.3390/jmse9060565
Chicago/Turabian StyleYoo, Yunja, and Han-Seon Park. 2021. "Qualitative Risk Assessment of Cybersecurity and Development of Vulnerability Enhancement Plans in Consideration of Digitalized Ship" Journal of Marine Science and Engineering 9, no. 6: 565. https://doi.org/10.3390/jmse9060565
APA StyleYoo, Y., & Park, H.-S. (2021). Qualitative Risk Assessment of Cybersecurity and Development of Vulnerability Enhancement Plans in Consideration of Digitalized Ship. Journal of Marine Science and Engineering, 9(6), 565. https://doi.org/10.3390/jmse9060565





