A Study on Cyber Security Threats in a Shipboard Integrated Navigational System
Abstract
1. Introduction
2. The Integrated Navigational System
3. Implemented Safeguards
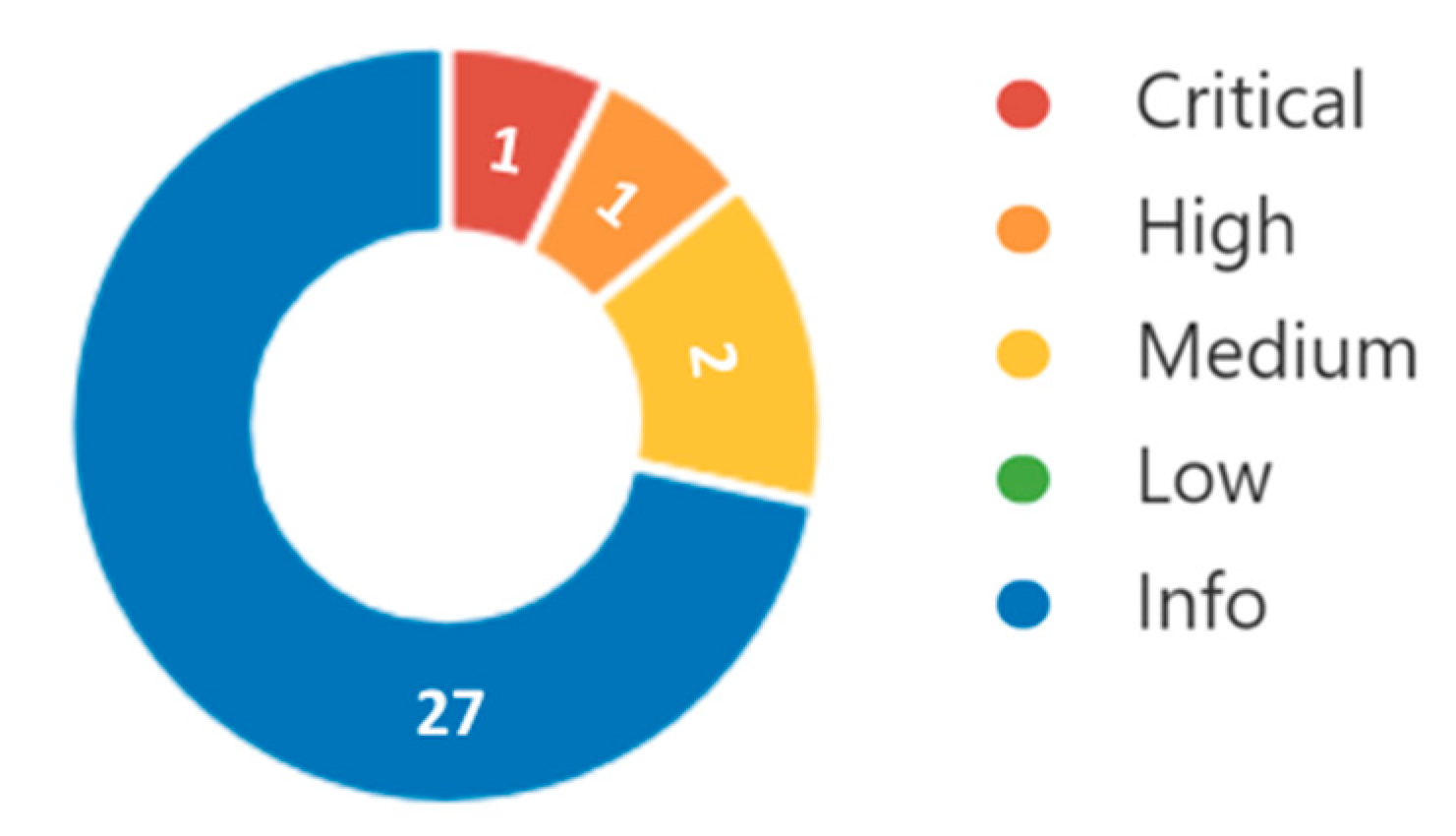
4. Cybersecurity Testing
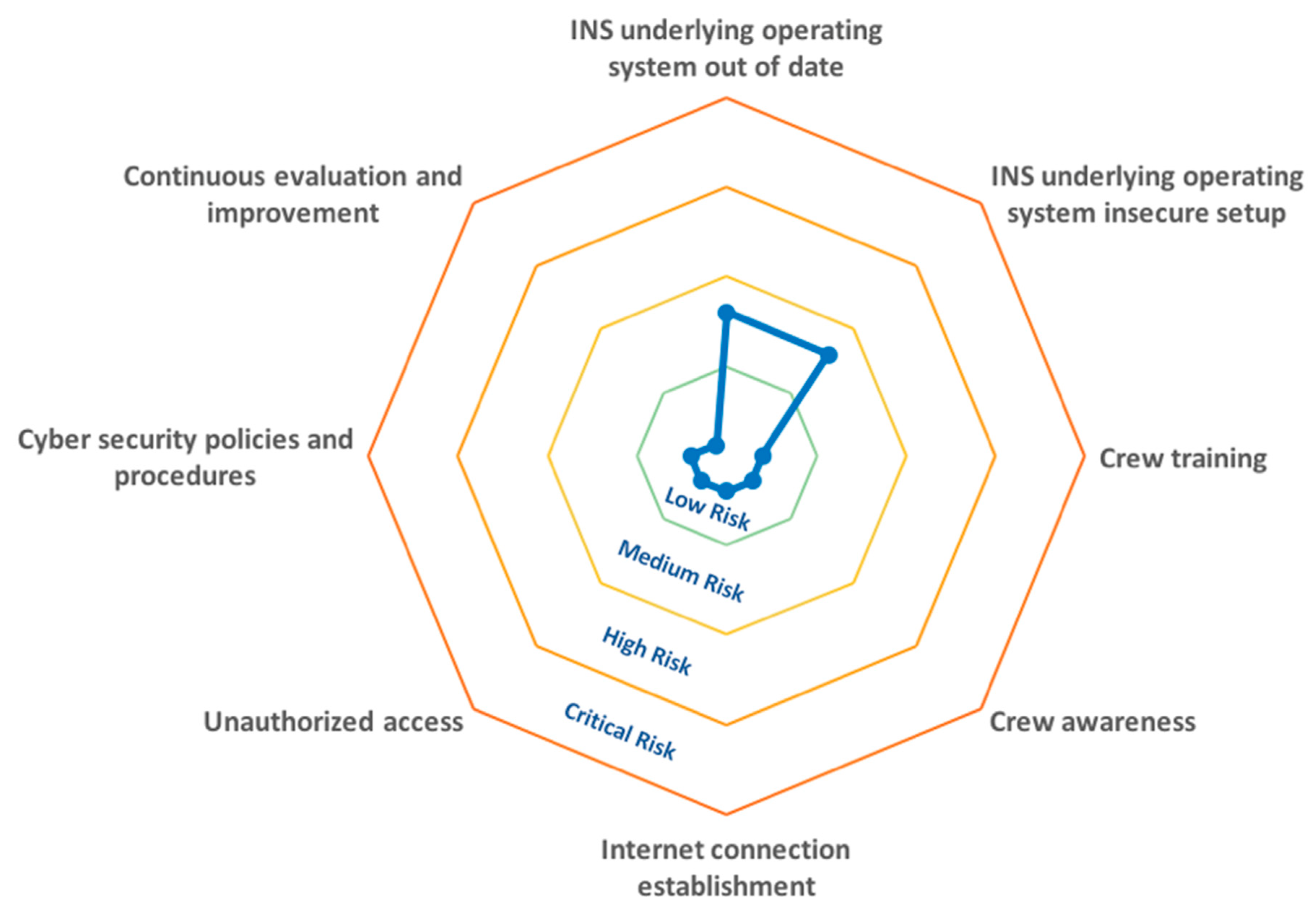
5. Risk Level Determination
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Svilicic, B.; Kamahara, J.; Rooks, M.; Yano, Y. Maritime Cyber Risk Management: An Experimental Ship Assessment. J. Navig. 2019, 72, 1108–1120. [Google Scholar] [CrossRef]
- Kaleem Awan, M.S.; Al Ghamdi, M.A. Understanding the Vulnerabilities in Digital Components of An Integrated Bridge System (IBS). J. Mar. Sci. Eng. 2019, 7, 350. [Google Scholar] [CrossRef]
- Tam, K.; Jones, K. MaCRA: A model-based framework for maritime cyber-risk assessment. WMU J. Mar. Affairs. 2019, 18, 129–163. [Google Scholar] [CrossRef]
- Chybowski, L.; Gawdzinska, K.; Laskowski, R. Assessing the Unreliability of Systems during the Early Operation Period of a Ship—A Case Study. J. Mar. Sci. Eng. 2019, 7, 213. [Google Scholar] [CrossRef]
- Tsimplis, M.; Papadas, S. Information Technology in Navigation: Problems in Legal Implementation and Liability. J. Navig. 2019, 72, 833–849. [Google Scholar] [CrossRef]
- Svilicic, B.; Kamahara, J.; Celic, J.; Bolmsten, J. Assessing Ship Cyber Risks: A Framework and Case Study of ECDIS Security. WMU J. Mar. Affairs 2019, in press. [Google Scholar] [CrossRef]
- Chen, Y.; Liu, Q.; Wan, C.; Li, Q.; Yuan, P. Identification and Analysis of Vulnerability in Traffic-Intensive Areas of Water Transportation Systems. J. Mar. Sci. Eng. 2019, 7, 174. [Google Scholar] [CrossRef]
- Svilicic, B.; Brčić, D.; Žuškin, S.; Kalebić, D. Raising Awareness on Cyber Security of ECDIS. TransNav Int. J. Mar. Navig. Safety Sea Trans. 2019, 13, 231–236. [Google Scholar] [CrossRef]
- Lee, E.; Mokashi, A.J.; Moon, S.Y.; Kim, G. The Maturity of Automatic Identification Systems (AIS) and Its Implications for Innovation. J. Mar. Sci. Eng. 2019, 7, 287. [Google Scholar] [CrossRef]
- Hareide, O.S.; Jøsok, Ø.; Lund, M.S.; Ostnes, R.; Helkala, K. Enhancing Navigator Competence by Demonstrating Maritime Cyber Security. J. Navig. 2018, 71, 1025–1039. [Google Scholar] [CrossRef]
- Zăgan, R.; Raicu, G.; Pazara, R.H.; Enache, S. Realities in Maritime Domain Regarding Cyber Security Concept. Adv. Eng. Forum 2018, 27, 221–228. [Google Scholar] [CrossRef]
- Dobryakova, L.A.; Lemieszewski, L.S.; Ochin, E.F. GNSS spoofing detection using static or rotating single-antenna of a static or moving victim. IEEE Access 2018, 6, 79074–79081. [Google Scholar] [CrossRef]
- Polatidis, N.; Pavlidis, M.; Mouratidis, H. Cyber-attack path discovery in a dynamic supply chain maritime risk management system. Comput. Stand. Interfaces 2018, 56, 74–82. [Google Scholar] [CrossRef]
- Kalogeraki, E.; Apostolou, D.; Polemi, N.; Papastergiou, S. Knowledge management methodology for identifying threats in maritime/ logistics supply chains. Knowl. Manag. Res. Pract. 2018, 16, 508–524. [Google Scholar] [CrossRef]
- Lund, M.S.; Gulland, J.E.; Hareide, O.S.; Jøsok, O.; Carlsson Weum, K.O. Integrity of Integrated Navigation Systems. In Proceedings of the IEEE International Workshop on Cyber-Physical Systems Security, Beijing, China, 30 May–1 June 2018. [Google Scholar]
- Lewis, S.; Maynard, L.; Chow, C.E.; Akos, D. Secure GPS Data for Critical Infrastructure and Key Resources: Cross-Layered Integrity Processing and Alerting Service. Navig. J. Inst. Navig. 2018, 65, 389–403. [Google Scholar] [CrossRef]
- Shapiro, L.R.; Maras, M.-H.; Velotti, L.; Pickman, S.; Wei, H.-L.; Till, R. Trojan horse risks in the maritime transportation systems sector. J. Trans. Secur. 2018, 8, 1–19. [Google Scholar] [CrossRef]
- Kessler, G.C.; Craiger, J.P.; Haass, J.C. A Taxonomy Framework for Maritime Cybersecurity: A Demonstration Using the Automatic Identification System. Trans. Nav. Int. J. Mar. Navig. Safety Sea Trans. 2018, 12, 429–437. [Google Scholar] [CrossRef]
- Lee, Y.C.; Park, S.K.; Lee, W.K.; Kang, J. Improving cyber security awareness in maritime transport: A way forward. J. Korean Soc. Mar. Eng. 2017, 41, 738–745. [Google Scholar] [CrossRef]
- Borkowski, P. Presentation algorithm of possible collision solutions in a navigational decision support system. Sci. J. Marit. Univ. Szczec. 2014, 38, 20–26. [Google Scholar]
- Svilicic, B.; Rudan, I.; Frančić, V.; Mohović, Đ. Towards a Cyber Secure Shipboard Radar. J. Navig. 2019, in press. [Google Scholar] [CrossRef]
- International Maritime Organization. Guidelines on Maritime Cyber Risk Management, MSC-FAL.1/Circ.3; IMO: London, UK, 2017. [Google Scholar]
- International Maritime Organization. Maritime Cyber Risk Management in Safety Management Systems, MSC 98/23/Add.1; IMO: London, UK, 2017. [Google Scholar]
- International Electrotechnical Commission. Maritime Navigation and Radiocommunication Equipment and Systems-Cybersecurity-General Requirements, Methods of Testing and Required Test Results. IEC 63154 ED1; IEC: Geneva, Switzerland, 2019. [Google Scholar]
- Vu, V.D.; Lützhöft, M.; Emad, G.R. Frequency of use—the First Step Toward Human-Centred Interfaces for Marine Navigation Systems. J. Navig. 2019, 72, 1089–1107. [Google Scholar] [CrossRef]
- International Maritime Organization. Adoption of the Revised Performance Standards for Integrated Navigation Systems (INS), Resolution MSC.252(83); IMO: London, UK, 2007. [Google Scholar]
- International Maritime Organization. ECDIS—Guidance for Good Practice, Resolution MSC.1/Circ.1503/Rev.1; IMO: London, UK, 2017. [Google Scholar]
- International Maritime Organization. Adoption of the Revised Performance Standards for Radar Equipment, Resolution MSC.192(79); IMO: London, UK, 2004. [Google Scholar]
- Tenable, Tenable Products: Nessus Professional. Available online: https://www.tenable.com/products/nessus/nessus-professional (accessed on 1 September 2019).
- Svilicic, B.; Celic, J.; Kamahara, J.; Bolmsten, J. A Framework for Cyber Security Risk Assessment of Ships. In Proceedings of the 19th International Association of Maritime Universities (IAMU) Conference, Barcelona, Spain, 17–19 October 2018; pp. 21–28. [Google Scholar]
- Microsoft, Microsoft Security Bulletin MS17-010 -Critical. Available online: https://technet.microsoft.com/library/security/MS17-010 (accessed on 1 September 2019).
- Swiss Government Computer Emergency Response Team, Notes About the NotPetya Ransomware. Available online: https://www.govcert.admin.ch/blog/32/notes-about-the-notpetya-ransomware# (accessed on 1 September 2019).
- United States Computer Emergency Readiness Team, Alert (TA17-181A) Petya Ransomware. Available online: https://www.us-cert.gov/ncas/alerts/TA17-181A (accessed on 1 September 2019).
- Microsoft, Microsoft: Search Product Lifecycle. Available online: https://support.microsoft.com/en-us/lifecycle (accessed on 1 September 2019).

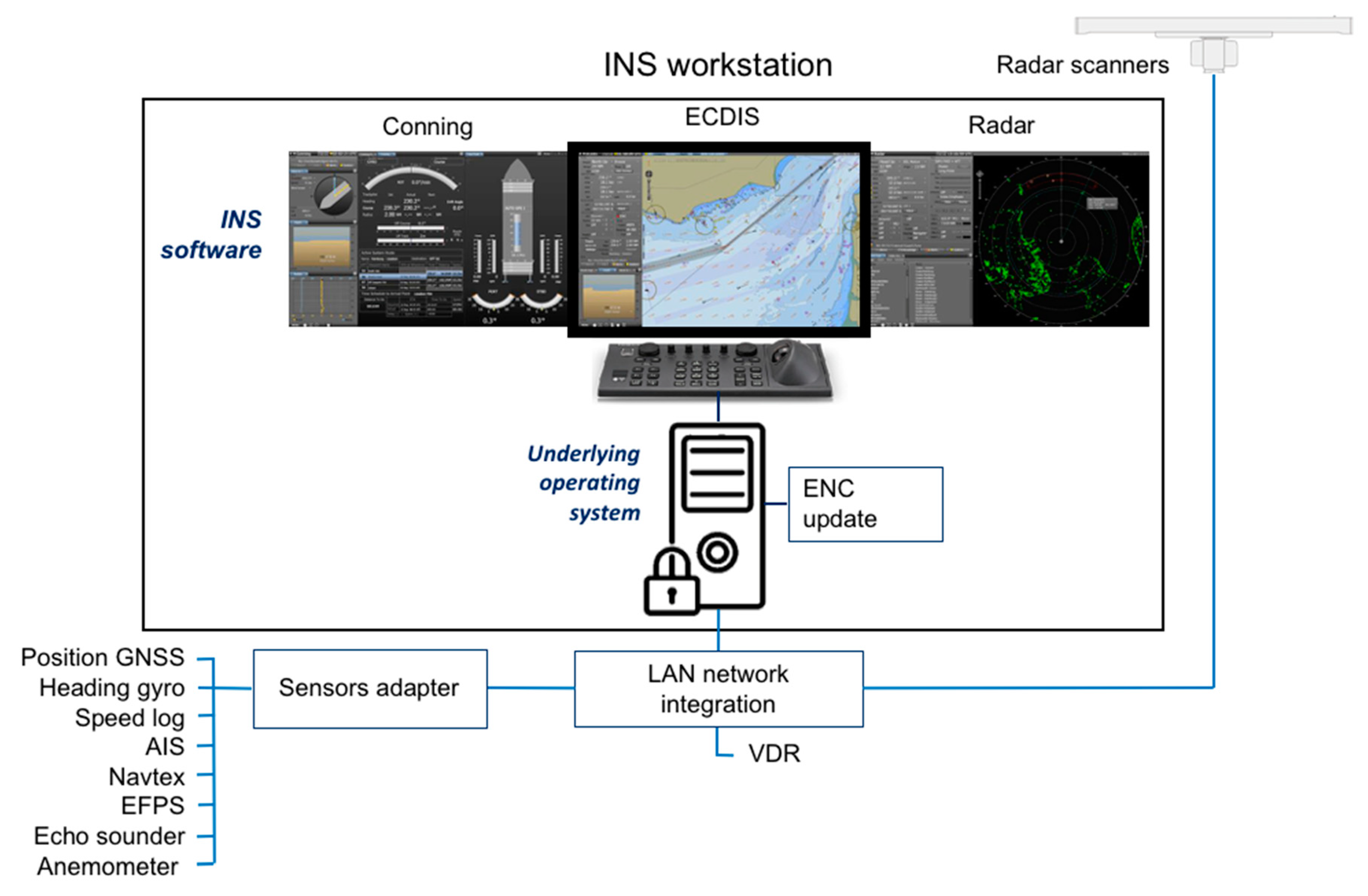

| INS’s Elements | Parameter | Specification |
|---|---|---|
| General | Manufacturer | Wärtsilä SAM Electronics GmbH |
| Model | NACOS MULTIPILOT Platinum 2017 | |
| Software version | 2.1.02.10 | |
| International Maritime Organization (IMO) compliant | Yes | |
| Navigation tools | Electronic Chart Display and Information System (ECDIS) | NACOS ECDISPILOT Platinum |
| Radar | NACOS RADARPILOT Platinum | |
| Conning | NACOS CONNINGPILOT Platinum | |
| Charts | IHO electronic navigation chart (ENC) | IHO S-57 (Edition 3.1.1) |
| IHO RNC | IHO S-61 (Edition 1.0) | |
| IHO chart content | IHO S-52 (Edition 6.1.1) | |
| IHO data protection | IHO S-63 (Edition 1.2.0) | |
| Interfaces | Serial NMEA | IEC61162-1 |
| Serial high speed | IEC61162-2 | |
| Network | Ethernet local area network (LAN) | |
| Chart update | USB | |
| Remote maintenance | Possible |
| Safeguard Elements | Measures and Mechanisms | Description |
|---|---|---|
| Security management system | Policies and procedures | –Developed but cyber security partially dedicated –Well-communicated –Periodic review is in place |
| Training and awareness | –Ship navigational ranks training is provided by the integrated navigational system (INS) vendor –Quite a high level of awareness | |
| Incident handling | –Incident reporting is in place –The procedures are adhered to | |
| INS navigation tools | Internet access | –Internet connection is not established |
| Physical protection | –Access controls are in place and enforced –Physical access allowed for authorized personnel –Hardware interfaces are kept in a locked case –Portable storage device handling is controlled | |
| Confidentiality agreement | –Confidentiality agreement with the vendor is in place | |
| Network for integration | Internet communication | –Internet connection is not established |
| Physical protection policy | –Access controls are in place and enforced –Physical access allowed for authorized personnel –Hardware interfaces are kept in a locked case | |
| Authentication policy | –Authentication controls are in place and enforced –Default passwords are changed |
| Name | Description | Solution | Severity | |
|---|---|---|---|---|
| 1. | Server Message Block (SMB) service | The INS is affected by following vulnerabilities:
|
| Critical |
| 2. | Remote Desktop service | Arbitrary remote code vulnerability exists in the Remote Desktop service running on the INS. The vulnerability can be exploited by a remote attacker to execute arbitrary code. | Update the operating system with a security patch released by the manufacturer. | High |
| 3. | Terminal Service | Remote Desktop Protocol Server (Terminal Service) running on the INS is vulnerable to a man-in-the-middle attack due to low encryption level used. The vulnerability can be exploited by a remote attacker to gain access to the INS. | Operating system secure setup by forcing strong cryptography. | Medium |
| 4. | Remote protocols | Remote Desktop Protocol Server (Terminal Service) running on the INS is vulnerable to a man-in-the-middle attack due to low encryption level used. The vulnerability can be exploited by a remote attacker to get access to the INS. | Operating system secure setup by forcing strong cryptography. | Medium |
| Threat | Description | Impact Magnitude | Likelihood | |
|---|---|---|---|---|
| 1. | INS underlying operating system out of date | Allows exploitation of well-known vulnerabilities of the INS underlying operating system | 100 | 0.4 |
| 2. | INS underlying operating system insecure setup | Backdoors are open for possible intrusions and performance is reduced | 100 | 0.4 |
| 3. | Navigational ranks training | Ship navigational ranks are not able to perform their duties and responsibilities | 50 | 0.2 |
| 4. | Navigational ranks awareness | Ship navigational ranks are not able to adhere to policies and procedures | 50 | 0.2 |
| 5. | Internet connection establishment | Remote attacker is provided with access to the INS’s navigational tools | 100 | 0.1 |
| 6. | Unauthorized access | Attacker is provided with physical or logical access to the INS’s navigational tools | 100 | 0.1 |
| 7. | Cyber security policies and procedures | Ship navigational ranks are not aware of their roles and responsibilities | 20 | 0.5 |
| 8. | Continuous assessment and improvement | Lack of ability to respond to rapid technological development | 20 | 0.2 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Svilicic, B.; Rudan, I.; Jugović, A.; Zec, D. A Study on Cyber Security Threats in a Shipboard Integrated Navigational System. J. Mar. Sci. Eng. 2019, 7, 364. https://doi.org/10.3390/jmse7100364
Svilicic B, Rudan I, Jugović A, Zec D. A Study on Cyber Security Threats in a Shipboard Integrated Navigational System. Journal of Marine Science and Engineering. 2019; 7(10):364. https://doi.org/10.3390/jmse7100364
Chicago/Turabian StyleSvilicic, Boris, Igor Rudan, Alen Jugović, and Damir Zec. 2019. "A Study on Cyber Security Threats in a Shipboard Integrated Navigational System" Journal of Marine Science and Engineering 7, no. 10: 364. https://doi.org/10.3390/jmse7100364
APA StyleSvilicic, B., Rudan, I., Jugović, A., & Zec, D. (2019). A Study on Cyber Security Threats in a Shipboard Integrated Navigational System. Journal of Marine Science and Engineering, 7(10), 364. https://doi.org/10.3390/jmse7100364






