Abstract
The integrated navigational system (INS) enhances the effectiveness and safety of ship navigation by providing multifunctional display on the basis of integration of at least two navigational functions, the voyage route monitoring with Electronic Chart Display and Information System (ECDIS) and collision avoidance with radar. The INS is essentially a software platform for fusion of data from the major ECDIS and radar systems with sensors for the additional navigation functions of route planning, status and data display, and alert management. This paper presents a study on cyber security resilience examination of a shipboard INS installed on a RoPax ship engaged in international trade. The study was based on a mixed-method approach, combining an interview of the ship’s navigational ranks and cyber security testing of the INS using an industry vulnerability scanner. The identified threats were analyzed qualitatively to study the source of cyber risks threatening the INS. The results obtained point out cyber threats related to weaknesses of the INS underlying operating system, suggesting a need for occasional preventive maintenance in addition to the regulatory compliance required.
1. Introduction
Ship navigation systems have been increasingly relying on cyber technologies to improve the effectiveness and safety of navigation, which has consequently resulted in a need for safeguarding the shipping from cyber threats [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21]. Therefore, the International Maritime Organization (IMO) has published the guidelines on maritime cyber risk management [22], and has also included cyber security assessment in the International Safety Management (ISM) code to be introduced on ships by the beginning of the year 2021 [23]. In addition, the IMO is preparing in collaboration with the International Electrotechnical Commission (IEC), a new standard for maritime navigation and radio-communication equipment and systems, IEC 63154 “Cybersecurity—General Requirements, Methods of Testing and Required Test Results” [24].
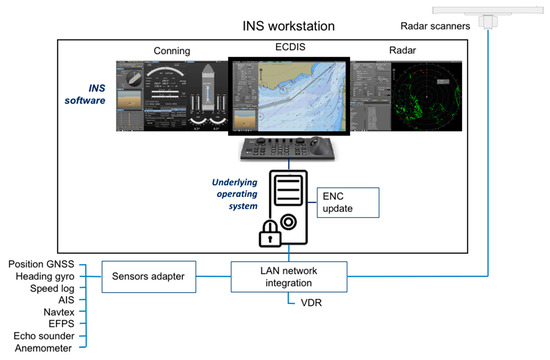
The integrated navigational system (INS) is a composite system, whose purpose is to enhance the effectiveness and safety of ship navigation by providing the multifunctional display on the basis of integration of at least two navigational functions [25]—collision avoidance using a radar sensor and voyage route monitoring using the Electronic Chart Display and Information System (ECDIS) [26]. The INS is essentially a software platform for fusion of data from the major radar and ECDIS systems with sensors for the additional navigation functions of route planning, status and data display, and alert management. The INS is recognized as the one type of equipment by IMO and its functionality is standardized with the performance standards [26].
Recently, cybersecurity assessments of a shipboard ECDIS and a shipboard radar have been presented [1,21]. Although both the ECDIS and radar are IMO type approved and computer-based systems, they are installed as an individual equipment, providing their basic functionality. This paper reports on an examination of the cyber security resilience of a shipboard INS. The examined INS is installed on a roll-on/roll-off ship for freight vehicle transport with passenger accommodation (RoPax), which is engaged in international trade (Figure 1). The examination is based on a mixed-method approach, combining an interview of the ship’s navigational ranks to identify implemented safeguards and cybersecurity testing of the INS to detect existing vulnerabilities. The threats identified were qualitatively analyzed to determine the level of cyber risks threatening the INS.

Figure 1.
The RoPax ship engaged in international trade.
3. Implemented Safeguards
The implemented safeguard measures and mechanisms were identified by interviewing the ship navigational ranks, in particular the ship’s master, and first and second officers. During the interview, we focused on three elements of the safeguard regarding the INS’s operating environment: the ship’s security management system, INS navigation tools, and integration network system. For each of the elements, the identified safeguard measures and mechanisms, together with the description, are given in Table 2.

Table 2.
Implemented safeguards.
The results regarding the cyber security management system showed that the cyber security was implemented only partially in the ship’s security policies and procedures. However, the policies and procedures were well communicated and reviewed regularly. The ship navigational ranks training was conducted by the INS vendor, and cyber security awareness was at quite a high level. The shipboard INS navigation tools were not connected to the Internet. Strong physical protection policy was in place for unauthorized personnel, and INS hardware interfaces were kept in a locked case. The electronic navigation chart (ENC) update portable storage device was strictly controlled, the device provided by the INS vendor was used, and the ship navigational ranks cyber hygiene was at a high level. A confidentiality agreement with the vendor was in place. The LAN network for integration was also disconnected from the Internet, and strong physical protection and logical authentication policies were in place.
4. Cybersecurity Testing
The cybersecurity testing of the INS was conducted with the world’s most widely deployed industry vulnerability scanner, Nessus Professional version 8.0.1 [29]. Vulnerability scanning is a passive method of reviewing the INS to gain comprehensive insight into all vulnerabilities that are already known to the cybersecurity community, attackers, and software developers [6,30]. A laptop with the installed vulnerability scanner was connected directly to the INS with a crossover Ethernet cable. The INS software was running with administrative rights, whereas the remote scanning was conducted without administrative permission. Figure 3 shows the testing setup. During the testing, the ship was docked in a port. The INS was activated to use the ECDIS as the base display layer, together with the radar and conning data (Figure 3).

Figure 3.
Testing setup for the INS cyber-vulnerability scanning.
The scanning report summary is shown on Figure 4. In total, 4 vulnerabilities and 27 pieces of information were detected. According to the severity level, the report showed that 1, 1, and 2 vulnerabilities were assigned under the critical, high, and medium severity, respectively.
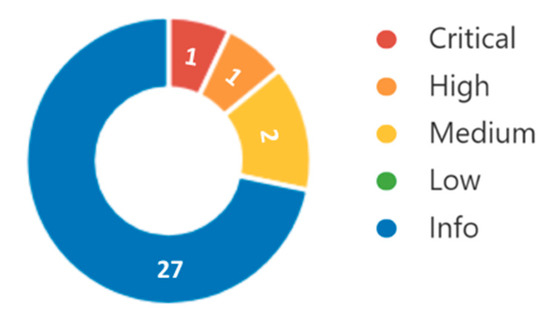
Figure 4.
The vulnerability scanning summary report.
Table 3 shows descriptions and possible solutions of the INS cyber-vulnerabilities detected. The critical vulnerability detected (Table 3, vulnerability 1) alerts that a vulnerable version of the Server Message Block (SMB) service is running on the INS. Namely, the underlying operating system of the INS software is Microsoft Windows 7 Professional (Service Pack 1), and the SMB is its default service for file and printer sharing. By following the manufacturer’s recommendation, immediate implementation of a security update for the INS underlying operating system is required [31]. This vulnerability is particularly interesting because of one of the most recognized maritime cyber security incidents, the NotPetya attack on Maersk container shipping company [32]. NotPetya is a malicious ransomware program that was rapidly spreading worldwide by utilizing the SMB version 1 vulnerabilities [33]. Although the INS underlying operating system update recommended by the manufacturer is relatively complex to implement in a ship environment, it offers reactive protection, such as is provided with anti-malicious code security programs. A proactive solution would be secure setup of the INS underlying operating system by blocking or disabling the SMB service version 1. However, it is very important to point out that the update of the underlying operating system could significantly impact the INS software functionality [26] and should be only conducted by INS vendor authorized personnel.

Table 3.
Results of the vulnerability scan.
The vulnerabilities with high and medium severities detected (Table 3, vulnerabilities 2–4) are related to weaknesses of services running on the INS underlying operating system, allowing possible remote code execution and unauthorized access gaining. As in the case of the critical vulnerability detected, the vulnerable services are not necessary for the INS operational functionality. The solution includes underlying operating system update with a security patch released by the manufacturer and secure setup by disabling or blocking the vulnerable services and forcing strong cryptography. These activities are also to be conducted by the INS vendor authorized personnel.
5. Risk Level Determination
The INS cyber risk determination was conducted on the basis of a qualitative analysis of cyber threats identified by the interview and vulnerability scanning conducted. Whereas the vulnerabilities scan is used to detect all known vulnerabilities existing in the INS, the used vulnerability scanner is a general industry tool, and the results could inaccurately reflect the actual severity of threats due to specifics of the ship environment. Therefore, the scan results were studied in the context of the INS’s operating environment and implemented safeguards on the ship. On the basis of the interview and vulnerability scan results, we conducted the identification of cyber threats. Table 4 shows the list of the identified cyber threats together with our estimation of the threats’ impact magnitude and likelihood. The impact magnitude represented a damage resulting from a threat execution, and was given with a value from 0 (no impact) to 100 (total impact). The threat likelihood represented a probability that a threat was executed, and the likelihood rate was given with a value from 0 up to 1.

Table 4.
The identified INS cyber threats.
Four of the eight determined cyber threats were assigned with the highest impact magnitude (Table 4, threats 1, 2, 5, 6). The threats were related to the INS underlying operating system being out of date and setup insecurely, as well as establishment of the Internet connection and unauthorized access. The middle impact magnitude was assigned to two threats (Table 4, threats 3 and 4) that were related to the ship training and awareness. The low impact magnitude was assigned to the threats raised from lack of cyber security-dedicated policies and procedures, and continuous assessment and improvement (Table 4, threats 7 and 8). Five of the eight determined cyber threats were assigned with the low likelihood level (Table 4, threats 3–6, 8). The threats assigned with middle likelihood level (Table 4, threats 1, 2, 7) were related to the INS underlying operating system being out of date and having insecure setup, as well as lack of cyber security dedicated policies and procedures. The given values of the impact magnitude and likelihood are discussed with the risk level analysis in the following part of the chapter.
The INS cyber risk levels were calculated by multiplying the impact magnitude value with the likelihood value. The given result represented the qualitative cyber risk level: (i) acceptable low risk (product of the multiplication was lower than 25), (ii) medium risk that is acceptable for a short time (product of the multiplication was between 25 and 50), (iii) high risk demanding a risk mitigation plan (product of the multiplication was between 50 and 75), and (iv) critical risk demanding instant action (product of the multiplication was higher than 75). Figure 5 shows the cyber risk-level radar graph of the results obtained with the qualitative risk analysis.
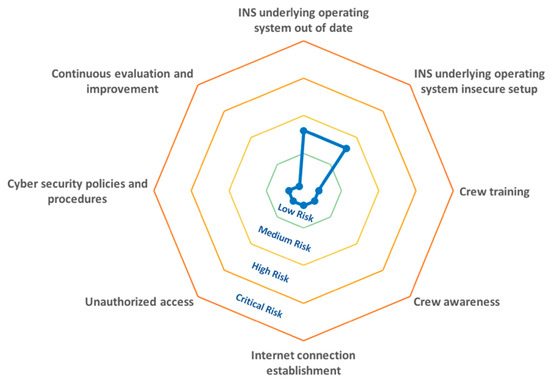
Figure 5.
Risk level radar graph of the cyber threats determined for the INS.
The risk level radar graph (Figure 5) indicated that two cyber threats that were determined were classified as medium risk (the highest risk level assigned) for the ship INS cyber security. The threats were related to the INS underlying operating system, in particular to the operating system update and secure setup. The out-of-date INS underlying operating system implied that an attacker can exploit a known vulnerability using publicly available instructions without significant expertise in ship navigation and computing technologies (analyzed in detail in Chapter 4). Securing the underlying operating system by disabling unnecessary services provides proactive protection from from unknown vulnerabilities and threats, and also could improve the performance of the INS because of additional resources released. On the other hand, relying on reactive protection solution and having out-of-date supporting software, cyber risk level over time will probably increase. In the case of the tested INS, the manufacturer of the underlying operating system will discontinue support and strongly recommend moving to next generation before the end of the current year (2019) [34]. The identified cyber threats corresponded to the previous findings with shipboard ECDIS and radar systems, indicating the same cyber risk threatening each of the navigation systems that are from different manufacturers and are installed on different types of ships [1,21].
The low (acceptable) risk level was assigned to most of the threats determined (six of eight), which are shown in Figure 5. The cyber threats were related to the ship navigational ranks training and awareness, physical protection controls, the cyber security-dedicated policy and procedure development, and periodic assessment and improvements. One of the threats assigned with the lowest risk level was related to the establishment of the Internet connection (Table 4, threat 5). The tested INS was not connected to the Internet and operated in the environment with strong physical protection and logical authentication control policies; thus, the Internet connection by installation of a network device was very unlikely to happen. Although disconnection from the Internet prevents outside threats, the vulnerabilities rising from the unmaintained operating system (its update and secure setup) could be triggered by inside actors (the ship’s crew), either unintentionally or maliciously. However, it should be noted that with the INS connection to the Internet, risk level of all of the cyber threats determined would raise to the critical level, demanding instant action.
6. Conclusions
The comprehensive cyber security resilience examination of the INS installed on the RoPax ship engaged in international trade was presented. The examination was based on the mixed-method approach, combining an interview of the ship’s navigational ranks and the following cyber security testing of the INS. The test was conducted using the industry vulnerability scanner, and the results were studied in the context of the INS’s operating environment and implemented safeguards on the ship. While six determined threats were classified with acceptable risk level, the two medium risk level threats are related to the maintenance of the INS’s underlying operating system, in particular its update and secure setup. The satisfactory risk level was attributed not only to maritime traditionally strong physical protection controls, navigational ranks’ training, and adherence to security policies and procedures, but also to the INS’s disconnection from the Internet.
The results from this study advance understanding of the source of cyber risks threatening the INS, and are applicable to any shipboard integrated system or type of ship. The results indicate the importance of the cyber security test performing as well as the analysis of the detected vulnerabilities regarding the ship operating environment. The cyber vulnerabilities detected with the passive scanning method suggest significance of the cyber security testing for the proactive protection by disabling unnecessary services. In addition, the findings contribute to the development of the new testing standard IEC 63154 and suggest the testing results that should be targeted. The study implies the need for occasional preventive maintenance of the underlying operating system to address weaknesses, despite the care taken for the purpose of regulatory compliance.
Author Contributions
B.S. developed the methodology; B.S. and I.R. performed the investigation; B.S., A.J., and D.Z. provided the resources; B.S. and A.J. ensured funding acquisition; B.S. wrote the original draft; B.S., I.R., A.J., and D.Z. wrote and edited the paper.
Funding
This research was financially supported by the University of Rijeka, grant number uniri-tehnic-18-68.
Acknowledgments
The research was financially supported by the University of Rijeka under the research project Cyber Security of Maritime ICT-Based Systems (grant number: Uniri-tehnic-18-68).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Svilicic, B.; Kamahara, J.; Rooks, M.; Yano, Y. Maritime Cyber Risk Management: An Experimental Ship Assessment. J. Navig. 2019, 72, 1108–1120. [Google Scholar] [CrossRef]
- Kaleem Awan, M.S.; Al Ghamdi, M.A. Understanding the Vulnerabilities in Digital Components of An Integrated Bridge System (IBS). J. Mar. Sci. Eng. 2019, 7, 350. [Google Scholar] [CrossRef]
- Tam, K.; Jones, K. MaCRA: A model-based framework for maritime cyber-risk assessment. WMU J. Mar. Affairs. 2019, 18, 129–163. [Google Scholar] [CrossRef]
- Chybowski, L.; Gawdzinska, K.; Laskowski, R. Assessing the Unreliability of Systems during the Early Operation Period of a Ship—A Case Study. J. Mar. Sci. Eng. 2019, 7, 213. [Google Scholar] [CrossRef]
- Tsimplis, M.; Papadas, S. Information Technology in Navigation: Problems in Legal Implementation and Liability. J. Navig. 2019, 72, 833–849. [Google Scholar] [CrossRef]
- Svilicic, B.; Kamahara, J.; Celic, J.; Bolmsten, J. Assessing Ship Cyber Risks: A Framework and Case Study of ECDIS Security. WMU J. Mar. Affairs 2019, in press. [Google Scholar] [CrossRef]
- Chen, Y.; Liu, Q.; Wan, C.; Li, Q.; Yuan, P. Identification and Analysis of Vulnerability in Traffic-Intensive Areas of Water Transportation Systems. J. Mar. Sci. Eng. 2019, 7, 174. [Google Scholar] [CrossRef]
- Svilicic, B.; Brčić, D.; Žuškin, S.; Kalebić, D. Raising Awareness on Cyber Security of ECDIS. TransNav Int. J. Mar. Navig. Safety Sea Trans. 2019, 13, 231–236. [Google Scholar] [CrossRef]
- Lee, E.; Mokashi, A.J.; Moon, S.Y.; Kim, G. The Maturity of Automatic Identification Systems (AIS) and Its Implications for Innovation. J. Mar. Sci. Eng. 2019, 7, 287. [Google Scholar] [CrossRef]
- Hareide, O.S.; Jøsok, Ø.; Lund, M.S.; Ostnes, R.; Helkala, K. Enhancing Navigator Competence by Demonstrating Maritime Cyber Security. J. Navig. 2018, 71, 1025–1039. [Google Scholar] [CrossRef]
- Zăgan, R.; Raicu, G.; Pazara, R.H.; Enache, S. Realities in Maritime Domain Regarding Cyber Security Concept. Adv. Eng. Forum 2018, 27, 221–228. [Google Scholar] [CrossRef]
- Dobryakova, L.A.; Lemieszewski, L.S.; Ochin, E.F. GNSS spoofing detection using static or rotating single-antenna of a static or moving victim. IEEE Access 2018, 6, 79074–79081. [Google Scholar] [CrossRef]
- Polatidis, N.; Pavlidis, M.; Mouratidis, H. Cyber-attack path discovery in a dynamic supply chain maritime risk management system. Comput. Stand. Interfaces 2018, 56, 74–82. [Google Scholar] [CrossRef]
- Kalogeraki, E.; Apostolou, D.; Polemi, N.; Papastergiou, S. Knowledge management methodology for identifying threats in maritime/ logistics supply chains. Knowl. Manag. Res. Pract. 2018, 16, 508–524. [Google Scholar] [CrossRef]
- Lund, M.S.; Gulland, J.E.; Hareide, O.S.; Jøsok, O.; Carlsson Weum, K.O. Integrity of Integrated Navigation Systems. In Proceedings of the IEEE International Workshop on Cyber-Physical Systems Security, Beijing, China, 30 May–1 June 2018. [Google Scholar]
- Lewis, S.; Maynard, L.; Chow, C.E.; Akos, D. Secure GPS Data for Critical Infrastructure and Key Resources: Cross-Layered Integrity Processing and Alerting Service. Navig. J. Inst. Navig. 2018, 65, 389–403. [Google Scholar] [CrossRef]
- Shapiro, L.R.; Maras, M.-H.; Velotti, L.; Pickman, S.; Wei, H.-L.; Till, R. Trojan horse risks in the maritime transportation systems sector. J. Trans. Secur. 2018, 8, 1–19. [Google Scholar] [CrossRef]
- Kessler, G.C.; Craiger, J.P.; Haass, J.C. A Taxonomy Framework for Maritime Cybersecurity: A Demonstration Using the Automatic Identification System. Trans. Nav. Int. J. Mar. Navig. Safety Sea Trans. 2018, 12, 429–437. [Google Scholar] [CrossRef]
- Lee, Y.C.; Park, S.K.; Lee, W.K.; Kang, J. Improving cyber security awareness in maritime transport: A way forward. J. Korean Soc. Mar. Eng. 2017, 41, 738–745. [Google Scholar] [CrossRef]
- Borkowski, P. Presentation algorithm of possible collision solutions in a navigational decision support system. Sci. J. Marit. Univ. Szczec. 2014, 38, 20–26. [Google Scholar]
- Svilicic, B.; Rudan, I.; Frančić, V.; Mohović, Đ. Towards a Cyber Secure Shipboard Radar. J. Navig. 2019, in press. [Google Scholar] [CrossRef]
- International Maritime Organization. Guidelines on Maritime Cyber Risk Management, MSC-FAL.1/Circ.3; IMO: London, UK, 2017. [Google Scholar]
- International Maritime Organization. Maritime Cyber Risk Management in Safety Management Systems, MSC 98/23/Add.1; IMO: London, UK, 2017. [Google Scholar]
- International Electrotechnical Commission. Maritime Navigation and Radiocommunication Equipment and Systems-Cybersecurity-General Requirements, Methods of Testing and Required Test Results. IEC 63154 ED1; IEC: Geneva, Switzerland, 2019. [Google Scholar]
- Vu, V.D.; Lützhöft, M.; Emad, G.R. Frequency of use—the First Step Toward Human-Centred Interfaces for Marine Navigation Systems. J. Navig. 2019, 72, 1089–1107. [Google Scholar] [CrossRef]
- International Maritime Organization. Adoption of the Revised Performance Standards for Integrated Navigation Systems (INS), Resolution MSC.252(83); IMO: London, UK, 2007. [Google Scholar]
- International Maritime Organization. ECDIS—Guidance for Good Practice, Resolution MSC.1/Circ.1503/Rev.1; IMO: London, UK, 2017. [Google Scholar]
- International Maritime Organization. Adoption of the Revised Performance Standards for Radar Equipment, Resolution MSC.192(79); IMO: London, UK, 2004. [Google Scholar]
- Tenable, Tenable Products: Nessus Professional. Available online: https://www.tenable.com/products/nessus/nessus-professional (accessed on 1 September 2019).
- Svilicic, B.; Celic, J.; Kamahara, J.; Bolmsten, J. A Framework for Cyber Security Risk Assessment of Ships. In Proceedings of the 19th International Association of Maritime Universities (IAMU) Conference, Barcelona, Spain, 17–19 October 2018; pp. 21–28. [Google Scholar]
- Microsoft, Microsoft Security Bulletin MS17-010 -Critical. Available online: https://technet.microsoft.com/library/security/MS17-010 (accessed on 1 September 2019).
- Swiss Government Computer Emergency Response Team, Notes About the NotPetya Ransomware. Available online: https://www.govcert.admin.ch/blog/32/notes-about-the-notpetya-ransomware# (accessed on 1 September 2019).
- United States Computer Emergency Readiness Team, Alert (TA17-181A) Petya Ransomware. Available online: https://www.us-cert.gov/ncas/alerts/TA17-181A (accessed on 1 September 2019).
- Microsoft, Microsoft: Search Product Lifecycle. Available online: https://support.microsoft.com/en-us/lifecycle (accessed on 1 September 2019).
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).