Perspectives on the Cybersecurity of the Integrated Navigation System
Abstract
:1. Introduction
2. Related Work
3. Research Community Perspective
3.1. Methodology
- Identify the purpose;
- Apply practical screen;
- Draft protocol and train the team;
- Search for literature;
- Appraise quality;
- Extract data;
- Synthesize studies;
- Write the review.
3.1.1. The Purpose of the Literature Review
- RQ 1. Identifying potential vulnerabilities and threats.
- RQ 2. Determining relevant data sources, hardware, and software tools for research activities.
- RQ 3. Identifying technical measures to mitigate risks.
3.1.2. Practical Screening
- Only publications in English;
- Only scientific publications published in journals, conferences, workshops, and books;
- The publication period: January 2010–15 February 2025.
3.1.3. Defining the Protocol
3.1.4. Searching for the Literature
3.1.5. Quality Appraisal
“Only studies that employed empirical methods (e.g., models, simulations, or practical testing) were considered.”
3.1.6. Data Extraction
3.1.7. Synthesis of Studies
3.1.8. Writing the Review
3.2. Tools and Data Sources for INS Cybersecurity Research
3.2.1. Hardware
3.2.2. Software and Data Sources
3.3. Cyber Threats and Vulnerabilities
3.3.1. AIS
3.3.2. ECDIS
3.3.3. GNSS
3.3.4. RADAR
3.3.5. Operating System
3.3.6. Other Threats and Vulnerabilities
3.4. Risk Mitigation Measures
3.4.1. AIS
3.4.2. GNSS
3.4.3. RADAR
3.4.4. Operating Systems
3.4.5. Network
3.4.6. Other Mitigation Measures
4. Professional Community Perspective
4.1. Methodology
- How is cybersecurity awareness of the employed seafarers improved?
- What technical and procedural measures are implemented against cyber risks?
- What observations do you have regarding cybersecurity?
4.2. Cybersecurity Officer (CySO)
- Recommendations of International Association of Classification Societies (IACS) member class societies;
- Better compliance with IMO and vetting requirements related to cybersecurity;
- Recommendation from another ship operator;
- Preparation for potential future IMO or vetting requirements.
4.3. Awareness and Training
4.4. Technical Measures
4.5. Procedural Measures
4.6. Other Observations
5. Discussion
5.1. Research Community Perspective
5.2. Professional Community Perspective
5.3. Comparing and Merging Perspectives
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| ID | Ref | Year | Publisher | Type | Component |
|---|---|---|---|---|---|
| 1 | [4] | 2014 | ACM | C | AIS |
| 2 | [48] | 2015 | IEEE | J | GNSS (GPS) |
| 3 | [49] | 2016 | DGLR | C | GNSS |
| 4 | [5] | 2017 | ION | J | GNSS (GPS) |
| 5 | [78] | 2017 | HRČAK | J | AIS |
| 6 | [40] | 2017 | Cambridge | J | GNSS |
| 7 | [77] | 2017 | ACM | C | AIS |
| 8 | [94] | 2017 | IEEE | C | GNSS (GPS) |
| 9 | [81] | 2018 | TransNav | J | GNSS |
| 10 | [6] | 2018 | Sjøkrigsskolen | J | INS (MFD) |
| 11 | [95] | 2019 | TransNav | J | GNSS |
| 12 | [147] | 2019 | Springer Link | J | GNSS |
| 13 | [91] | 2019 | Springer Link | J | AIS |
| 14 | [43] | 2019 | TransNav | J | ECDIS |
| 15 | [52] | 2019 | Springer Link | J | ECDIS |
| 16 | [35] | 2019 | Cambridge | J | ECDIS |
| 17 | [39] | 2019 | HRČAK | J | ECDIS |
| 18 | [38] | 2019 | MDPI | J | INS (MFD) |
| 19 | [109] | 2019 | IEEE | C | Network |
| 20 | [111] | 2019 | ScienceDirect | J | Network |
| 21 | [46] | 2020 | IEEE | C | AIS |
| 22 | [75] | 2020 | TransNav | J | AIS |
| 23 | [67] | 2020 | ScienceDirect | J | AIS |
| 24 | [60] | 2020 | IEEE | C | AIS |
| 25 | [90] | 2020 | TransNav | J | AIS |
| 26 | [45] | 2020 | ACM | C | GNSS |
| 27 | [37] | 2020 | Springer Link | J | ECDIS |
| 28 | [36] | 2020 | Cambridge | J | RADAR |
| 29 | [41] | 2021 | IEEE | C | GNSS (GPS) |
| 30 | [61] | 2021 | TransNav | J | Network |
| 31 | [44] | 2021 | Az-Buki | J | Network |
| 32 | [87] | 2021 | IAMU | C | AIS |
| 33 | [110] | 2021 | IEEE | C | Network |
| 34 | [33] | 2021 | MDPI | J | ECDIS, RADAR |
| 35 | [92] | 2021 | Cambridge | J | AIS |
| 36 | [53] | 2022 | MDPI | J | Network |
| 37 | [70] | 2022 | IEEE | C | Network |
| 38 | [96] | 2022 | IEEE | J | GNSS |
| 39 | [66] | 2022 | IEEE | C | AIS |
| 40 | [42] | 2022 | Springer Link | C | AIS |
| 41 | [65] | 2022 | MDPI | J | AIS |
| 42 | [62] | 2022 | IEEE | C | RADAR |
| 43 | [101] | 2022 | MDPI | J | GNSS |
| 44 | [69] | 2023 | IEEE | J | RADAR |
| 45 | [58] | 2023 | IEEE | C | RADAR |
| 46 | [98] | 2023 | MDPI | J | GNSS |
| 47 | [102] | 2023 | IEEE | C | GNSS |
| 48 | [100] | 2024 | Springer Link | B | GNSS |
| 49 | [55] | 2024 | IEEE | J | Network |
| 50 | [88] | 2024 | IEEE | C | Network |
| 51 | [51] | 2024 | IEEE | C | GNSS |
| 52 | [89] | 2024 | IEEE | C | MFD |
| 53 | [103] | 2024 | IEEE | C | RADAR |
| 54 | [76] | 2024 | IEEE | C | AIS |
| 55 | [79] | 2024 | Springer | B | ECDIS |
| 56 | [104] | 2024 | Springer | C | RADAR |
| 57 | [93] | 2024 | AIRCC | C | AIS |
References
- UNCTAD. Review of Maritime Transport; UNCTAD: Geneva, Switzerland, 2021. [Google Scholar]
- IMO. Resolution MSC.252(83) Adoption of the Revised Performance Standards for Integrated Navigation Systems (INS), Introduction, Contents, Module A-B; IMO: London, UK, 2018. [Google Scholar]
- Oruc, A.; Gkioulos, V.; Katsikas, S. Towards a cyber-physical range for the Integrated Navigation System (INS). J. Mar. Sci. Eng. 2022, 10, 107. [Google Scholar] [CrossRef]
- Balduzzi, M.; Pasta, A.; Wilhoit, K. A security evaluation of AIS Automated Identification System. In Proceedings of the ACSAC’14: Proceedings of the 30th Annual Computer Security Applications Conference, New Orleans, LA, USA, 8–12 December 2014; Payne, C.N., Hahn, A., Butler, K., Sherr, M., Eds.; Association for Computing Machinery: New York, NY, USA, 2014; pp. 436–445. [Google Scholar] [CrossRef]
- Bhatti, J.; Humphreys, T.E. Hostile control of ships via false GPS signals: Demonstration and detection. J. Inst. Navig. 2017, 64, 51–66. [Google Scholar] [CrossRef]
- Lund, M.S.; Hareide, O.S.; Jøsok, Ø. An attack on an Integrated Navigation System. Necesse 2018, 3, 149–163. [Google Scholar] [CrossRef]
- M-CAD. Info. Available online: https://maritimecybersecurity.nl/info (accessed on 21 April 2025).
- France Cyber Maritime. ADMIRAL Dataset. 2025. Available online: https://www.m-cert.fr/admiral/index.html (accessed on 21 April 2025).
- France Cyber Maritime. About. Available online: https://www.france-cyber-maritime.eu/en/about/ (accessed on 21 April 2025).
- France Cyber Maritime. Maritime Cybersecurity Statistics—Global Scale. Available online: https://www.m-cert.fr/admiral/statistics.html (accessed on 21 April 2025).
- France Cyber Maritime. Detailed Maritime Cybersecurity Statistics by Threat. Available online: https://www.m-cert.fr/admiral/threats.html (accessed on 21 April 2025).
- Blake, T. Hackers Took ‘Full Control’ of Container Ship’s Navigation Systems for 10 Hours-IHS Fairplay. 2017. Available online: https://rntfnd.org/2017/11/25/hackers-took-full-control-of-container-ships-navigation-systems-for-10-hours-ihs-fairplay/ (accessed on 21 April 2025).
- Meland, P.H.; Bernsmed, K.; Wille, E.; Rødseth, Ø.J.; Nesheim, D.A. A retrospective analysis of maritime cyber security incidents. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2021, 15, 519–530. [Google Scholar] [CrossRef]
- Androjna, A.; Brcko, T.; Pavic, I.; Greidanus, H. Assessing cyber challenges of maritime navigation. J. Mar. Sci. Eng. 2020, 8, 776. [Google Scholar] [CrossRef]
- Paganini, P. A Sophisticated Cyberattack Hit the International Maritime Organization (IMO). 2020. Available online: https://securityaffairs.com/109154/hacking/international-maritime-organization-imo-cyberattack.html (accessed on 21 April 2025).
- Bateman, T. HMS Defender: AIS Spoofing Is Opening up a New Front in the War on Reality. 2021. Available online: https://www.euronews.com/next/2021/06/28/hms-defender-ais-spoofing-is-opening-up-a-new-front-in-the-war-on-reality (accessed on 21 April 2025).
- Smith, A. Anonymous Trolls Vladimir Putin by Renaming His Yacht ‘FCKPTN’ and Sending It to ‘Hell’ by Hacking Maritime Data. 2022. Available online: https://www.independent.co.uk/tech/anonymous-vladimir-putin-yacht-fckptn-b2024780.html (accessed on 21 April 2025).
- Oruc, A. Second Cyber Incident at IMO: Data Leakage. 2024. Available online: https://cyberonboard.com/second-cyber-incident-at-imo-data-leakage/ (accessed on 21 April 2025).
- Kessler, G.C.; Craiger, J.P.; Haass, J.C. A taxonomy framework for maritime cybersecurity: A demonstration using the automatic identification system. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2018, 12, 429. [Google Scholar] [CrossRef]
- ProWritingAid. Features. Available online: https://prowritingaid.com/features (accessed on 21 April 2025).
- Grammarly. Our Features. Available online: https://www.grammarly.com/features (accessed on 21 April 2025).
- Ben Farah, M.A.; Ukwandu, E.; Hindy, H.; Brosset, D.; Bures, M.; Andonovic, I.; Bellekens, X. Cyber security in the maritime industry: A systematic survey of recent advances and future trends. Information 2022, 13, 22. [Google Scholar] [CrossRef]
- Bolbot, V.; Kulkarni, K.; Brunou, P.; Banda, O.V.; Musharraf, M. Developments and research directions in maritime cybersecurity: A systematic literature review and bibliometric analysis. Int. J. Crit. Infrastruct. Prot. 2022, 39, 100571. [Google Scholar] [CrossRef]
- Erbas, M.; Khalil, S.M.; Tsiopoulos, L. Systematic literature review of threat modeling and risk assessment in ship cybersecurity. Ocean Eng. 2024, 306, 118059. [Google Scholar] [CrossRef]
- Clavijo Mesa, M.V.; Patino-Rodriguez, C.E.; Guevara Carazas, F.J. Cybersecurity at sea: A literature review of cyber-attack impacts and defenses in maritime supply chains. Information 2024, 15, 710. [Google Scholar] [CrossRef]
- Dimakopoulou, A.; Rantos, K. Comprehensive analysis of maritime cybersecurity landscape based on the NIST CSF v2.0. J. Mar. Sci. Eng. 2024, 12, 919. [Google Scholar] [CrossRef]
- DNV. Maritime Cyber Priority 2024/25. Available online: https://www.dnv.com/cyber/insights/publications/maritime-cyber-priority-2024/ (accessed on 21 April 2025).
- M-CERT. Maritime Cyber Threat Overview 2023. Available online: https://www.france-cyber-maritime.eu/wp-content/uploads/2024/11/Rapport_menace_2023_NUMERIQUE_BD.pdf (accessed on 21 April 2025).
- NORMA Cyber. Annual Threat Assessment 2025. Available online: https://www.normacyber.no/news/annual-threat-assessment-2024-46a4p (accessed on 21 April 2025).
- Dresch, A.; Lacerda, D.P.; Antunes, J.A.V. Systematic Literature Review. In Design Science Research; Dresch, A., Lacerda, D.P., Antunes, J.A.V., Jr., Eds.; Springer International Publishing: Cham, Switzerland, 2015; pp. 129–158. [Google Scholar] [CrossRef]
- Okoli, C.; Schabram, K. A Guide to Conducting a Systematic Literature Review of Information Systems Research. 2015. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=1954824 (accessed on 25. May 2025). [CrossRef]
- Okoli, C. A guide to conducting a standalone systematic literature review. Commun. Assoc. Inf. Syst. 2015, 37. [Google Scholar] [CrossRef]
- Leite Junior, W.C.; de Moraes, C.C.; de Albuquerque, C.E.P.; Machado, R.C.S.; de Sá, A.O. A triggering mechanism for cyber-attacks in naval sensors and systems. Sensors 2021, 21, 3195. [Google Scholar] [CrossRef]
- Lumivero. Citavi Tour: Organize. Available online: https://lumivero.com/products/citavi/citavi-product-tour/ (accessed on 21 April 2025).
- Svilicic, B.; Kamahara, J.; Rooks, M.; Yano, Y. Maritime cyber risk management: An experimental ship assessment. J. Navig. 2019, 72, 1108–1120. [Google Scholar] [CrossRef]
- Svilicic, B.; Rudan, I.; Frančić, V.; Mohović, D. Towards a cyber secure shipboard radar. J. Navig. 2020, 73, 547–558. [Google Scholar] [CrossRef]
- Svilicic, B.; Kristić, M.; Žuškin, S.; Brčić, D. Paperless ship navigation: Cyber security weaknesses. J. Transp. Secur. 2020, 13, 203–214. [Google Scholar] [CrossRef]
- Svilicic, B.; Rudan, I.; Jugović, A.; Zec, D. A study on cyber security threats in a shipboard Integrated Navigational System. J. Mar. Sci. Eng. 2019, 7, 364. [Google Scholar] [CrossRef]
- Svilicic, B.; Rudan, I.; Frančić, V.; Doričić, M. Shipboard ECDIS cyber security: Third-party component threats. Sci. J. Marit. Res. 2019, 33, 176–180. [Google Scholar] [CrossRef]
- Glomsvoll, O.; Bonenberg, L.K. GNSS jamming resilience for close to shore navigation in the Northern Sea. J. Navig. 2017, 70, 33–48. [Google Scholar] [CrossRef]
- Boudehenn, C.; Jacq, O.; Lannuzel, M.; Cexus, J.C.; Boudraa, A. Navigation anomaly detection: An added value for Maritime Cyber Situational Awareness. In Proceedings of the 2021 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), Dublin, Ireland, 14–18 June 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Amro, A.; Gkioulos, V. From Click to sink: Utilizing AIS for Command and Control in maritime cyber attacks. In Proceedings of the Computer Security—ESORICS 2022; Atluri, V., Di Pietro, R., Jensen, C.D., Meng, W., Eds.; Springer: Cham, Switzerland, 2022; pp. 535–553. [Google Scholar]
- Svilicic, B.; Brčic, D.; ŽuŁkin, S.; Kalebic, D. Raising awareness on cyber security of ECDIS. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2019, 13, 231–236. [Google Scholar] [CrossRef]
- Stoynov, S.; Nikolov, B. Approach to ship’s IT and OT systems cybersecurity improvement. Pedagogika-Pedagogy 2021, 93, 185–196. [Google Scholar] [CrossRef]
- Oligeri, G.; Sciancalepore, S.; Di Pietro, R. GNSS spoofing detection via opportunistic IRIDIUM signals. In Proceedings of the WiSec’20: Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Linz, Austria, 8–10 July 2020; Mayrhofer, R., Roland, M., Eds.; Association for Computing Machinery: New York, NY, USA, 2020; pp. 42–52. [Google Scholar] [CrossRef]
- Aziz, A.; Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. SecureAIS—Securing pairwise vessels communications. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Avignon, France, 29 June 2020–1 July 2020; pp. 1–9. [Google Scholar] [CrossRef]
- ADI. ADALM-PLUTO Software-Defined Radio Active Learning Module. Available online: https://www.analog.com/en/design-center/evaluation-hardware-and-software/evaluation-boards-kits/adalm-pluto.html#eb-overview (accessed on 21 April 2025).
- Fan, Y.; Zhang, Z.; Trinkle, M.; Dimitrovski, A.D.; Song, J.B.; Li, H. A cross-layer defense mechanism against GPS spoofing attacks on PMUs in smart grids. IEEE Trans. Smart Grid 2015, 6, 2659–2668. [Google Scholar] [CrossRef]
- Iliopoulos, A.; Fohlmeister, F.; Appel, M.; Pérez Marcos, E.; Sgammini, M.; Caizzone, S.; Cuntz, M.; Antreich, F. Testing of a multi-antenna GNSS receiver in DLR’s maritime jamming testbed. In Proceedings of the Deutscher Luft- und Raumfahrtkongress, DGLR, Braunschweig, Germany, 13–15 September 2016. [Google Scholar]
- Tenable. Nessus Professional. Available online: https://www.tenable.com/products/nessus/nessus-professional (accessed on 21 April 2025).
- Chinnarong, T.; Pomsathit, A.; Yongsiriwit, K. Analysis of cybersecurity vulnerabilities in maritime GNSS systems. In Proceedings of the 2024 8th International Conference on Information Technology (InCIT), Chonburi, Thailand, 14–15 November 2024; pp. 325–330. [Google Scholar] [CrossRef]
- Svilicic, B.; Kamahara, J.; Celic, J.; Bolmsten, J. Assessing ship cyber risks: A framework and case study of ECDIS security. WMU J. Marit. Aff. 2019, 18, 509–520. [Google Scholar] [CrossRef]
- Amro, A.; Oruc, A.; Gkioulos, V.; Katsikas, S. Navigation data anomaly analysis and detection. Information 2022, 13, 104. [Google Scholar] [CrossRef]
- Kali. hping3. Available online: https://www.kali.org/tools/hping3/ (accessed on 21 April 2025).
- Vu, L.; Nguyen, T.L.; Abdelrahman, M.S.; Vu, T.; Mohammed, O.A. A Cyber-HIL for investigating control systems in ship cyber physical systems under communication issues and cyber attacks. IEEE Trans. Ind. Appl. 2024, 60, 2142–2152. [Google Scholar] [CrossRef]
- Scapy. About Scapy. Available online: https://scapy.readthedocs.io/en/latest/introduction.html#about-scapy (accessed on 21 April 2025).
- Fedora. Fedora Linux. Available online: https://fedoraproject.org/ (accessed on 21 April 2025).
- Longo, G.; Merlo, A.; Armando, A.; Russo, E. Electronic Attacks as a Cyber False Flag against Maritime Radars Systems. In Proceedings of the 2023 IEEE 48th Conference on Local Computer Networks (LCN), Daytona Beach, FL, USA, 2–5 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Trend Micro. Trend Micro Safe Lock. Available online: https://docs.trendmicro.com/all/ent/tmsl/v2.0_SP1/en-us/_tmsl_server_olh_2.0sp1/about_tmsl.html (accessed on 21 April 2025).
- Jakovlev, S.; Daranda, A.; Voznak, M.; Lektauers, A.; Eglynas, T.; Jusis, M. Analysis of the possibility to detect fake vessels in the Automatic Identification System. In Proceedings of the 2020 61st International Scientific Conference on Information Technology and Management Science of Riga Technical University (ITMS), Riga, Latvia, 15–16 October 2020. [Google Scholar] [CrossRef]
- Hemminghaus, C.; Bauer, J.; Padilla, E. BRAT: A BRidge Attack Tool for cyber security assessments of maritime systems. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2021, 15, 35–44. [Google Scholar] [CrossRef]
- Wolsing, K.; Saillard, A.; Bauer, J.; Wagner, E.; van Sloun, C.; Fink, I.B.; Schmidt, M.; Wehrle, K.; Henze, M. Network attacks against marine RADAR systems: A taxonomy, simulation environment, and dataset. In Proceedings of the 2022 IEEE 47th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 26–29 September 2022; pp. 114–122. [Google Scholar] [CrossRef]
- Trend Micro. Toolkit for Research Purposes in AIS. 2014. Available online: https://github.com/trendmicro/ais (accessed on 21 April 2025).
- Maritec Solutions. AIS VDM/VDO Decoder. Available online: https://www.maritec.co.za/tools/aisvdmvdodecoding/ (accessed on 21 April 2025).
- Goudosis, A.; Katsikas, S. Secure Automatic Identification System (SecAIS): Proof-of-concept implementation. J. Mar. Sci. Eng. 2022, 10, 805. [Google Scholar] [CrossRef]
- Shyshkin, O. Cybersecurity providing for maritime Automatic Identification System. In Proceedings of the 2022 IEEE 41st International Conference on Electronics and Nanotechnology (ELNANO), Kyiv, Ukraine, 10–14 October 2022; pp. 736–740. [Google Scholar] [CrossRef]
- Iphar, C.; Napoli, A.; Ray, C. An expert-based method for the risk assessment of anomalous maritime transportation data. Appl. Ocean Res. 2020, 104, 102337. [Google Scholar] [CrossRef]
- Bridge Command. Home. Available online: https://www.bridgecommand.co.uk/ (accessed on 21 April 2025).
- Longo, G.; Russo, E.; Armando, A.; Merlo, A. Attacking (and defending) the maritime RADAR system. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3575–3589. [Google Scholar] [CrossRef]
- Ruhland, L.; Schmidt, M.; Bauer, J.; Padilla, E. Keeping the baddies out and the bridge calm: Embedded authentication for maritime networks. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications (ISNCC), Shenzhen, China, 19–22 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Wireshark. About Wireshark. Available online: https://www.wireshark.org/ (accessed on 21 April 2025).
- Amazon. Cinematic RADAR Simulator 2.0. Available online: https://www.amazon.com/CINEMATIC-RADAR-SIMULATOR-2-0-Download/dp/B075R1PLP9 (accessed on 21 April 2025).
- VMware. What Is ESXI. Available online: https://www.vmware.com/products/cloud-infrastructure/esxi-and-esx (accessed on 21 April 2025).
- OPAL-RT Technologies. OPAL-RT, Real-Time Simulation Solutions. Available online: https://www.opal-rt.com/ (accessed on 21 April 2025).
- Goudosis, A.; Katsikas, S. Secure AIS with identity-based authentication and encryption. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2020, 14, 287–298. [Google Scholar] [CrossRef]
- Klör, F.; Bauer, J.; Paulus, S.; Rademacher, M. Dude, Where’s that ship? Stealthy radio attacks against AIS broadcasts. In Proceedings of the 2024 IEEE 49th Conference on Local Computer Networks (LCN), Normandy, France, 8–10 October 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Su, P.; Sun, N.; Zhu, L.; Li, Y.; Bi, R.; Li, M.; Zhang, Z. A privacy-preserving and vessel authentication scheme using Automatic Identification System. In Proceedings of the SCC’17: Proceedings of the Fifth ACM International Workshop on Security in Cloud Computing, Abu Dhabi, United Arab Emirates, 2 April 2017; Wang, C., Kantarcioglu, M., Eds.; Association for Computing Machinery: New York, NY, USA, 2017; pp. 83–90. [Google Scholar] [CrossRef]
- Botunac, I.; Gržan, M. Analysis of software threats to the Automatic Identification System. Brodogradnja 2017, 68, 97–105. [Google Scholar] [CrossRef]
- Jones, K.D.; Tam, K. High impact malware targeting maritime infrastructure. In The Practice of Formal Methods: Essays in Honour of Cliff Jones, Part I; Cavalcanti, A., Baxter, J., Eds.; Springer: Cham, Switzerland, 2024; pp. 236–250. [Google Scholar] [CrossRef]
- Deng, Z.L.; Liu, H.D.; Huang, J.M.; Zou, D.J. A novel anti-jam navigation system based on A-GNSS. In Proceedings of the 2009 Joint Conferences on Pervasive Computing (JCPC), Tamsui, Taiwan, 3–5 December 2009; pp. 279–284. [Google Scholar] [CrossRef]
- Filic, M. Foundations of GNSS spoofing detection and mitigation with Distributed GNSS SDR receiver. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2018, 12, 649–656. [Google Scholar] [CrossRef]
- Świerczyński, S.; Zwolan, P.; Rutkowska, I. Jamming as a threat to navigation. Annu. Navig. 2016, 23, 219–233. [Google Scholar] [CrossRef]
- Liu, Y.; Li, S.; Fu, Q.; Liu, Z. Impact assessment of GNSS spoofing attacks on INS/GNSS Integrated Navigation System. Sensors 2018, 18, 1433. [Google Scholar] [CrossRef]
- Jan, S.S.; Tao, A.L. Comprehensive comparisons of satellite data, signals, and measurements between the BeiDou Navigation Satellite System and the Global Positioning System. Sensors 2016, 16, 689. [Google Scholar] [CrossRef]
- Lund, M.S.; Gulland, J.E.; Hareide, O.S.; Jøsok, Ø.; Weum, K.O.C. Integrity of Integrated Navigation Systems. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018. [CrossRef]
- Summers, W.C.; Bosworth, E. Password policy: The good, the bad, and the ugly. In Proceedings of the Winter International Synposium on Information and Communication Technologies, Cancun, Mexico, 5–8 January 2004. [Google Scholar]
- Dimitrov, N.; Alexandrov, C.; Todorov, M. Cyber security analysis of maritime surveillance systems. In Proceedings of the 21st Annual General Assembly Proceedings of the International Association of Maritime Universities (IAMU) Conference, Alexandria, Egypt, 26–28 October 2021. [Google Scholar]
- Rivas, L.; Stevens, S.; Zitter, A.; Khandelwal, V.; Vardhan, A.; Lohani, C.; Rouff, C.; Watkins, L. Assuring safe navigation and network operations of autonomous ships. In Proceedings of the 2024 IEEE 14th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–10 January 2024; pp. 0138–0143. [Google Scholar] [CrossRef]
- Visky, G.; Rohl, A.; Vaarandi, R.; Katsikas, S.; Maennel, O.M. Hacking on the high seas: How automated reverse-engineering can assist vulnerability discovery of a proprietary communication protocol. In Proceedings of the 2024 IEEE 49th Conference on Local Computer Networks (LCN), Normandy, France, 8–10 October 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Kessler, G.C. Protected AIS: A demonstration of capability scheme to provide authentication and message integrity. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2020, 14, 279–286. [Google Scholar] [CrossRef]
- Goudossis, A.; Katsikas, S.K. Towards a secure automatic identification system (AIS). J. Mar. Sci. Technol. 2019, 24, 410–423. [Google Scholar] [CrossRef]
- Wimpenny, G.; Šafář, J.; Grant, A.; Bransby, M. Securing the Automatic Identification System (AIS) Using public key cryptography to prevent spoofing whilst retaining backwards compatibility. J. Navig. 2021, 75, 333–345. [Google Scholar] [CrossRef]
- Silonosov, A.; Henesey, L. Crypto-agility performance analysis for AIS data sharing confidentiality based on attribute-based encryption. In Proceedings of the 14th International Conference on Computer Science and Information Technology (CCSIT 2024), Copenhagen, Denmark, 21–22 September 2024; AIRCC Publishing Corporation: Tamil Nadu, India, 2024; Volume 14, pp. 193–212. [Google Scholar]
- Hassani, V.; Crasta, N.; Pascoal, A.M. Cyber security issues in navigation systems of marine vessels from a control perspective. In Proceedings of the ASME 2017 36th International Conference on Ocean, Offshore and Arctic Engineering, Trondheim, Norway, 25–30 June 2017. [Google Scholar] [CrossRef]
- Filic, M.; Dimc, F. Logistic Map-encrypted chaotic ranging code as a proposed alternative to GNSS PRN pseudorange code. TransNav Int. J. Mar. Navig. Saf. Sea Transp. 2019, 13, 587–590. [Google Scholar] [CrossRef]
- Ke, Y.; Lv, Z.; Zhang, C.; Deng, X.; Zhou, W.; Song, D. Tightly coupled GNSS/INS integration spoofing detection algorithm based on innovation rate optimization and robust estimation. IEEE Access 2022, 10, 72444–72457. [Google Scholar] [CrossRef]
- Williams, P.; Basker, S.; Ward, N. e-Navigation and the case for eLoran. J. Navig. 2008, 61, 473–484. [Google Scholar] [CrossRef]
- Spravil, J.; Hemminghaus, C.; von Rechenberg, M.; Padilla, E.; Bauer, J. Detecting maritime GPS spoofing attacks based on NMEA sentence integrity monitoring. J. Mar. Sci. Eng. 2023, 11, 928. [Google Scholar] [CrossRef]
- Ochin, E. Detection of spoofing using Differential GNSS. Sci. J. Marit. Univ. Szczecin, Zesz. Nauk. Akad. Morska W Szczecinie 2017, 50, 59–67. [Google Scholar] [CrossRef]
- Raiyn, J. Maritime cyber-attacks detection based on a convolutional neural network. In Computational Intelligence and Mathematics for Tackling Complex Problems 5; Cornejo, M., Kóczy, L.T., Medina, J., Ramírez-Poussa, E., Eds.; Springer: Cham, Switzerland, 2024; pp. 115–122. [Google Scholar] [CrossRef]
- Singh, S.; Singh, J.; Singh, S.; Goyal, S.B.; Raboaca, M.S.; Verma, C.; Suciu, G. Detection and mitigation of GNSS spoofing attacks in maritime environments using a genetic algorithm. Mathematics 2022, 10, 4097. [Google Scholar] [CrossRef]
- Shyshkin, O.; Konovets, V. Detection of satellite navigation jamming in the maritime shipping. In Proceedings of the 2023 IEEE International Conference on Information and Telecommunication Technologies and Radio Electronics (UkrMiCo), Kyiv, Ukraine, 13–18 November 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Basels, F.; Wolsing, K.; Padilla, E.; Bauer, J. Demo: Maritime Radar Systems under Attack. Help is on the Way! In Proceedings of the 2024 IEEE 49th Conference on Local Computer Networks (LCN), Normandy, France, 8–10 October 2024; pp. 1–4. [Google Scholar] [CrossRef]
- Saillard, A.; Wolsing, K.; Wehrle, K.; Bauer, J. Exploring anomaly detection for marine RADAR systems. In Proceedings of the European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2024; pp. 361–381. [Google Scholar]
- IMO. MSC.1/Circ.1595 E-Navigation Strategy Implementation Plan—Update 1; IMO: London, UK, 2018. [Google Scholar]
- IEC 61162-1; Maritime Navigation and Radiocommunication Equipment and Systems: Part 1: Single Talker and Multiple Listeners. IEC: Geneva, Switzerland, 2016.
- IEC 61162-450; Maritime Navigation and Radiocommunication Equipment and Systems—Digital Interfaces—Part 450: Multiple Talkers and Multiple Listeners—Ethernet Interconnection. IEC: Geneva, Switzerland, 2024.
- IEC 61162-460; Maritime Navigation and Radiocommunication Equipment and Systems—Digital Interfaces—Part 460: Multiple Talkers and Multiple Listeners—Ethernet Interconnection—Safety and Security. IEC: Geneva, Switzerland, 2024.
- Zhu, J.; Yan, L.; Guo, S. Research on ship network security based on game theory. In Proceedings of the 2019 2nd International Conference on Safety Produce Informatization (IICSPI), Chongqing, China, 28–30 November 2019; pp. 78–81. [Google Scholar] [CrossRef]
- Hemminghaus, C.; Bauer, J.; Wolsing, K. SIGMAR: Ensuring integrity and authenticity of maritime systems using digital signatures. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October–2 November 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Sahay, R.; Meng, W.; Estay, D.S.; Jensen, C.D.; Barfod, M.B. CyberShip-IoT: A dynamic and adaptive SDN-based security policy enforcement framework for ships. Future Gener. Comput. Syst. 2019, 100, 736–750. [Google Scholar] [CrossRef]
- IMO. Resolution MSC.428(98) Maritime Cyber Risk Management in Safety Management Systems; IMO: London, UK, 2017. [Google Scholar]
- RWO Veolia. Bilge Water Management. Available online: https://ship.nridigital.com/ship_mar19/veolia_water_technologies (accessed on 21 April 2025).
- Oruc, A. Tanker industry is more ready against cyber threats. In Proceedings of the International Conference on Marine Engineering and Technology Oman 2019 (ICMET Oman), Muscat, Oman, 5–7 November 2019. [Google Scholar] [CrossRef]
- INTERTANKO. Social Media Guidance for Seafarers. Available online: https://cyberonboard.com/wp-content/uploads/Intertanko-Golden-Rules.pdf (accessed on 21 April 2025).
- ICS; BIMCO; MPA. Cyber Security Onboard Ships. Available online: https://cyberonboard.com/wp-content/uploads/ICS-Cyber-Security-onboard-Ships.pdf (accessed on 21 April 2025).
- MarineLink. From Mines to AIS Spoofing, Assessing the Risks to Shipping in the Black Sea. 2022. Available online: https://www.marinelink.com/news/mines-ais-spoofing-assessing-risks-494729 (accessed on 21 April 2025).
- OCIMF. SIRE 2.0 Question Library: Part 1—Chapters 1 to 7; OCIMF: London, UK, 2022; Available online: https://www.ocimf.org/document-libary/630-sire-2-0-question-library-part-1-chapters-1-to-7-version-1-0-january-2022/file (accessed on 21 April 2025).
- Oruc, A. In September 2024, SIRE 2.0 Enforces Improved Cybersecurity Requirements. 2024. Available online: https://cyberonboard.com/in-september-2024-sire-2-0-enforces-improved-cybersecurity-requirements/ (accessed on 21 April 2025).
- Leovy, J. Cyberattack Cost Maersk as Much as $300 Million and Disrupted Operations for 2 Weeks. 2017. Available online: https://www.latimes.com/business/la-fi-maersk-cyberattack-20170817-story.html (accessed on 21 April 2025).
- Oruc, A.; Amro, A.; Gkioulos, V. Assessing Cyber Risks of an INS Using the MITRE ATT&CK Framework. Sensors 2022, 22, 8745. [Google Scholar] [CrossRef]
- IMO. MSC.192(79) Adoption of the Revised Performance Standards for RADAR Equipment; IMO: London, UK, 2004. [Google Scholar]
- BIMCO; CSA; DCSA; ICS; INTERCARGO; InterManager; INTERTANKO; IUMI; OCIMF; WSC; et al. The Guidelines on Cyber Security Onboard Ships. Available online: https://www.ics-shipping.org/wp-content/uploads/2021/02/2021-Cyber-Security-Guidelines.pdf (accessed on 21 April 2025).
- IACS. E26 Cyber Resilience of Ships. Available online: https://iacs.s3.af-south-1.amazonaws.com/wp-content/uploads/2022/02/04140503/UR-E26-Rev.1-Nov-2023-CR.pdf (accessed on 21 April 2025).
- IACS. E27 Cyber Resilience of On-Board Systems and Equipment. Available online: https://iacs.s3.af-south-1.amazonaws.com/wp-content/uploads/2022/05/29103853/UR-E27-Rev.1-Sep-2023-CLN.pdf (accessed on 21 April 2025).
- Blenkey, N. ABS Issues First Cyber Security-Ready Notation to HHI VLCC. 2018. Available online: https://www.marinelog.com/news/abs-issues-first-cyber-security-ready-notation-to-hhi-vlcc/ (accessed on 21 April 2025).
- Safety4Sea. BV Awards Cyber Security Notation to LNG Carrier. 2020. Available online: https://safety4sea.com/bv-awards~-cyber-security-notation-to-lng-gas-carrier/ (accessed on 21 April 2025).
- O’dwyer, R. NYK Line Oil Tanker Gets First ClassNK Cyber Notation. 2021. Available online: https://smartmaritimenetwork.com/2021/11/10/nyk-line-oil-tanker-gets-first-classnk-cyber-notation/ (accessed on 21 April 2025).
- DNV. Stena Drilling and DNV GL Sign Contract for First Cyber Secure Class notation. 2019. Available online: https://www.dnv.com/news/stena-drilling-and-dnv-gl-sign-contract-for-first-cyber-secure-class-notation-149153 (accessed on 21 April 2025).
- Digital Ship. KR Issues First Cybersecurity Class Notation to HHI for Very Large LPG Carriers. 2020. Available online: https://thedigitalship.com/news/maritime-satellite-communications/kr-issues-first-cybersecurity-class-notation-to-hhi-for-very-large-lpg-carriers/ (accessed on 21 April 2025).
- Safety4Sea. Lloyd’s Register Gives World’s First Cyber SAFE Notation. 2017. Available online: https://safety4sea.com/lloyds-register-gives-worlds-first-cyber-safe-notation/ (accessed on 21 April 2025).
- ISO 14001; Environmental Management Systems—Requirements with Guidance for Use. International Organization for Standardization: Geneva, Switzerland, 2015.
- IMO. MSC.112(73) Adoption of the Revised Performance Standards for Shipborne Global Positioning System (GPS) Receiver Equipment; IMO: London, UK, 2000. [Google Scholar]
- Howell, E. Russia Is Jamming GPS Satellite Signals in Ukraine, US Space Force Says. 2022. Available online: https://www.space.com/russia-jamming-gps-signals-ukraine (accessed on 21 April 2025).
- Son, P.W.; Park, S.G.; Han, Y.; Seo, K. eLoran: Resilient positioning, navigation, and timing infrastructure in maritime areas. IEEE Access 2020, 8, 193708–193716. [Google Scholar] [CrossRef]
- Luccio, M. eLoran: Part of the Solution to GNSS Vulnerability. 2021. Available online: https://www.gpsworld.com/eloran-part~-of-the-solution-to-gnss-vulnerability/ (accessed on 21 April 2025).
- IMO. MSC-FAL.1/Circ.3/Rev.3 Guidelines on Maritime Cyber Risk Management; IMO: London, UK, 2025. [Google Scholar]
- Salim, H.M. Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2014. [Google Scholar]
- Ahn, W.; Chung, M.; Min, B.G.; Seo, J. Development of cyber-attack scenarios for nuclear power plants using scenario graphs. Int. J. Distrib. Sens. Netw. 2015, 11, 836258. [Google Scholar] [CrossRef]
- Torres, D. Cyber security and cyber defense for Venezuela: An approach from the Soft Systems Methodology. Complex Intell. Syst. 2018, 4, 213–226. [Google Scholar] [CrossRef]
- Omrani, M.; Shafiee, M.; Khorsandi, S. A model to measure cyber security maturity at the national level. In Proceedings of the 2023 31st International Conference on Electrical Engineering (ICEE), Tehran, Iran, 9–11 May 2023; pp. 110–116. [Google Scholar] [CrossRef]
- Oruc, A.; Chowdhury, N.; Gkioulos, V. A modular cyber security training programme for the maritime domain. Int. J. Inf. Secur. 2024, 23, 1477–1512. [Google Scholar] [CrossRef]
- United Nations. The 17 Goals. Available online: https://sdgs.un.org/goals (accessed on 21 April 2025).
- IMO. HTW 8/15/1 Any Other Business. Necessity of Developing Relevant Provisions Concerning Cybersecurity-Related Training for Seafarers; IMO: London, UK, 2021. [Google Scholar]
- TalTech. Introduction to Cyber Security. Available online: https://ois2.ttu.ee/uusois/subject/VLL1480 (accessed on 21 April 2025).
- NHL Stenden University of Applied Sciences. MCAD Maritime Cyber Attack Database. 2025. Available online: https://maritimecybersecurity.nl/ (accessed on 21 April 2025).
- Appel, M.; Iliopoulos, A.; Fohlmeister, F.; Pérez Marcos, E.; Cuntz, M.; Konovaltsev, A.; Antreich, F.; Meurer, M. Experimental validation of GNSS repeater detection based on antenna arrays for maritime applications. CEAS Space J. 2019, 11, 7–19. [Google Scholar] [CrossRef]
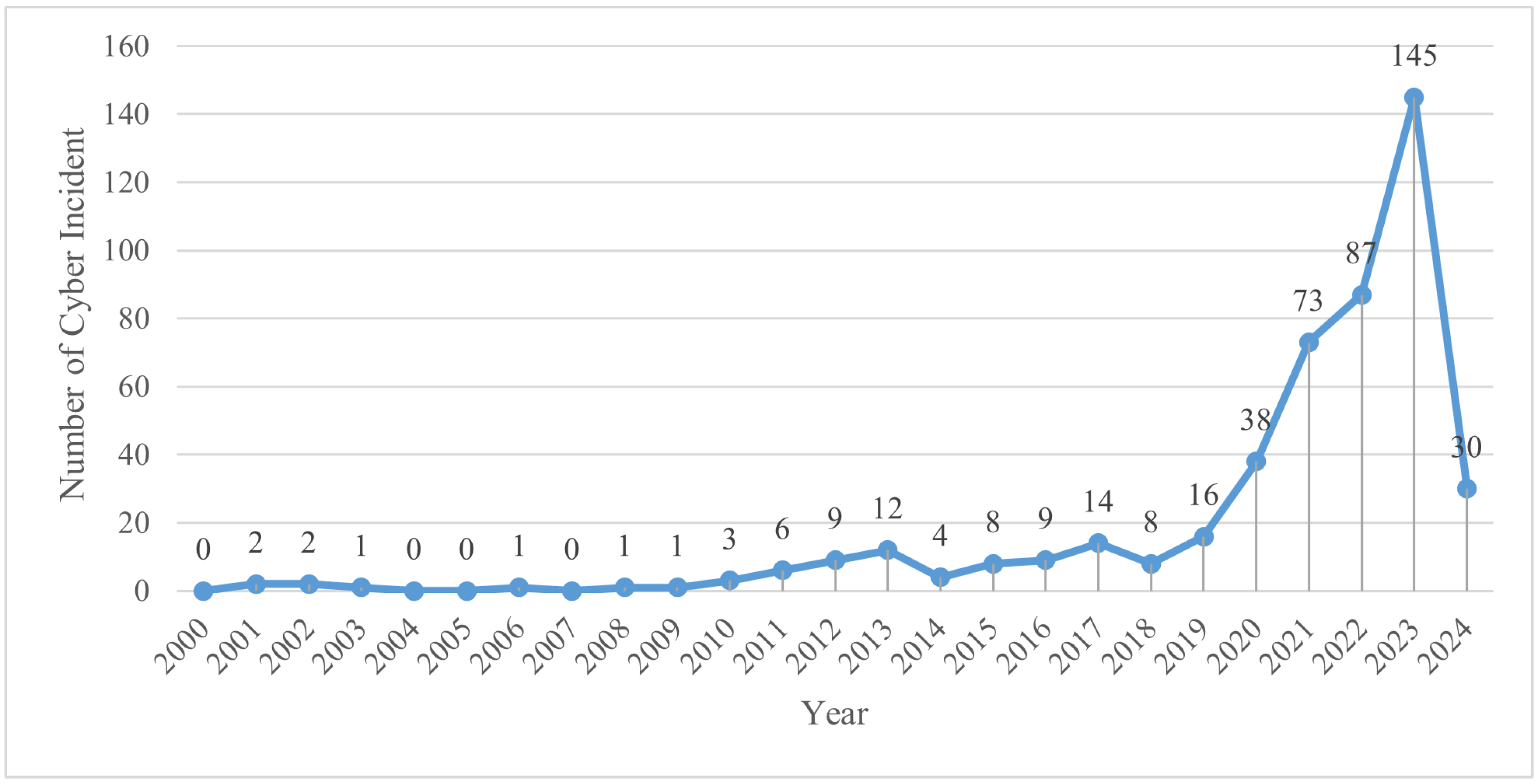
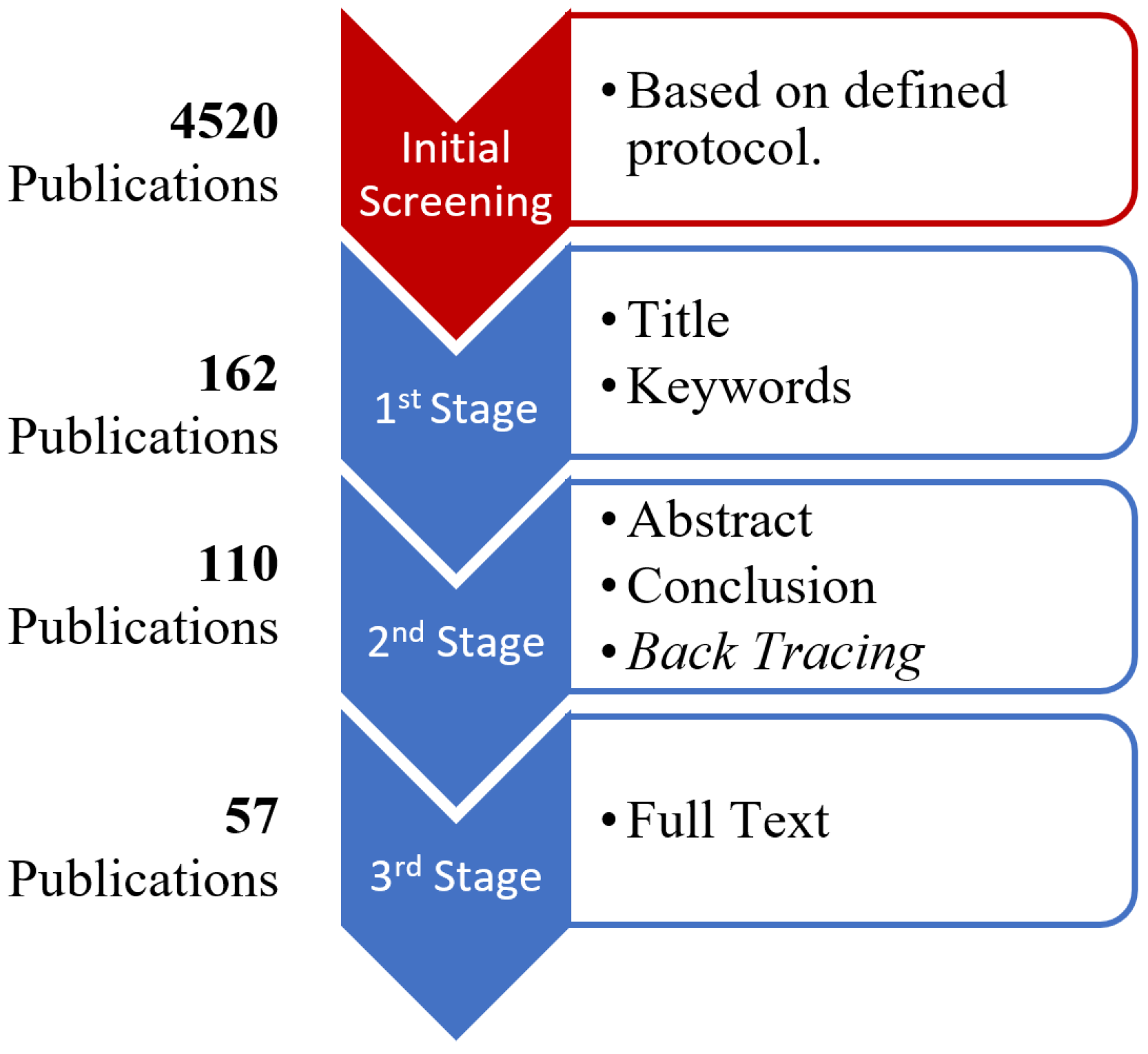
| Year | AIS | ECDIS | GNSS | MFD | Network | RADAR | Total |
|---|---|---|---|---|---|---|---|
| 2014 | 1 | 1 | |||||
| 2015 | 1 | 1 | |||||
| 2016 | 1 | 1 | |||||
| 2017 | 2 | 3 | 5 | ||||
| 2018 | 1 | 1 | 2 | ||||
| 2019 | 1 | 4 | 2 | 1 | 2 | 10 | |
| 2020 | 5 | 1 | 1 | 1 | 8 | ||
| 2021 | 2 | 1 | 1 | 3 | 1 | 8 | |
| 2022 | 3 | 2 | 2 | 1 | 8 | ||
| 2023 | 2 | 2 | 4 | ||||
| 2024 | 2 | 1 | 2 | 1 | 2 | 2 | 10 |
| Last 3 years | 5 | 1 | 6 | 1 | 4 | 5 | 22 |
| Total | 16 | 7 | 16 | 3 | 9 | 7 | 58 |
| # | Role & Organization | Competency | Reason for Interview |
|---|---|---|---|
| 1 | 2nd Officer (dry cargo operator) | Oceangoing Watchkeeping Officer | Ship Cybersecurity Officer; Giving training onboard to seafarers about the cyber risks of ships. |
| 2 | Consultant (independent) | Oceangoing Chief Engineer | Maritime cybersecurity consultant; (Ex) Company Cybersecurity Officer; Developing cybersecurity plan, including risk assessment; Giving training onboard and at the office to seafarers about the cyber risks of ships. |
| 3 | Maritime Pilot (private port) | Oceangoing Master | Completed M.Sc. thesis on maritime cybersecurity. |
| 4 | DPA/CSO (dry cargo operator) | Oceangoing Master | Developing a cybersecurity plan, including risk assessment. |
| 5 | Technical Superintendent (tanker & container operator) | Oceangoing Chief Engineer | Experienced in safety risk assessments. |
| 6 | Training Superintendent (tanker operator) | Oceangoing Master | Giving training at the office to seafarers about the cyber risks of ships. |
| 7 | Marine Superintendent (tanker operator) | Oceangoing Chief Officer | Developing cybersecurity plan, including risk assessment. |
| 8 | Chief Officer (dry cargo operator) | Oceangoing Chief Officer | Ship Cybersecurity Officer; Giving training onboard to seafarers about the cyber risks of ships. |
| 9 | Research Fellow (university) | (Ex) Oceangoing Watchkeeping Officer | Ongoing Ph.D. thesis on maritime cybersecurity. |
| 10 | Research Fellow (university) | (Ex) Oceangoing Watchkeeping Officer | Ongoing Ph.D. thesis on maritime cybersecurity. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oruc, A.; Kavallieratos, G.; Gkioulos, V.; Katsikas, S. Perspectives on the Cybersecurity of the Integrated Navigation System. J. Mar. Sci. Eng. 2025, 13, 1087. https://doi.org/10.3390/jmse13061087
Oruc A, Kavallieratos G, Gkioulos V, Katsikas S. Perspectives on the Cybersecurity of the Integrated Navigation System. Journal of Marine Science and Engineering. 2025; 13(6):1087. https://doi.org/10.3390/jmse13061087
Chicago/Turabian StyleOruc, Aybars, Georgios Kavallieratos, Vasileios Gkioulos, and Sokratis Katsikas. 2025. "Perspectives on the Cybersecurity of the Integrated Navigation System" Journal of Marine Science and Engineering 13, no. 6: 1087. https://doi.org/10.3390/jmse13061087
APA StyleOruc, A., Kavallieratos, G., Gkioulos, V., & Katsikas, S. (2025). Perspectives on the Cybersecurity of the Integrated Navigation System. Journal of Marine Science and Engineering, 13(6), 1087. https://doi.org/10.3390/jmse13061087









