Abstract
In order to identify and attack the multi-UUV (unmanned underwater vehicle) groups, this paper proposes a method for identifying the critical nodes of multi-UUV formations. This method helps in combating multi-UUV formations by identifying the key nodes to attack them. Moreover, these multi-UUV formations are considered to have an unknown structure as the research object. Therefore, the network structure of the formation is reconstructed according to its space–time trajectory, and the importance of nodes is determined based on network structure entropy. As for the methodology, firstly, based on the swarm intelligence behavior method, the motion similarity of multi-UUV nodes in the formation is analyzed in pairs; furthermore, the leader–follower relationship and the network structure of the formation are calculated successively. Then, based on this network structure, the importance of the network nodes is further determined by the network structure entropy method. Finally, through simulation and experiments, it is verified that the algorithm can accurately construct the network structure of the unknown multi-UUV formation, and the accuracy of the calculated time delay data reaches 84.6%, and compared with the traditional information entropy algorithm, the ordering of the important nodes obtained by this algorithm is more in line with the underwater formation network.
1. Introduction
Compared to a single UUV, multi-UUV formations have the advantages of modularity, high fault tolerance, high efficiency, etc., and they can also complete more challenging work through cooperation between them []. While the technology of using multiple UUV formations for coordinated search and exploration operations is becoming more sophisticated, this technology poses a threat to national maritime security. Facing the increasingly complex UUV formation structure, it is of great significance to effectively configure the UUV nodes in different positions according to the position relationship and the importance of UUV nodes in the cluster, save the equipment costs, improve the formation operation efficiency, or strike the important nodes of the enemy’s UUV formation to reduce the efficiency of the formation operation at a minimum cost [].
The coordinated behavior of the underwater formations can be viewed as a form of grouping of collaborative intelligence, which represents the traits of a group intelligence behavior displayed by individuals with simple intelligence through mutual cooperation and organization while maintaining the naturally distributed and self-organizing characteristics [,]. In nature, there are several groups of cooperative intelligent behaviors, such as flocks of birds and fish migrating in groups to adapt to air or seawater [,]. For instance, using high-precision GPS tracking of pairs of pigeons, Biro et al. found that if the conflict between two birds’ directional preferences was small, individuals averaged their routes []. This study shows that there is a leadership relationship exists between pairs of pigeons when the directional relationship between them exceeds a certain value. Based on the behavioral characteristics of crowd intelligence, several scholars have carried out a lot of research on this topic. Based on the leadership stability of the flock, Huo et al. designed a control model suitable for heterogeneous formation flight of UAVs, aiming to effectively avoid obstacles in unknown environments []. Moreover, Park and Kahng proposed a synchronous leader–follower switching method by observing the migration pattern of birds []. Furthermore, for hierarchical leader–follower networks with time-varying layer-to-layer delay, Xu et al. propose a new Hierarchical Event-based Control (HEC) algorithm [].
With the increase in UUV formation members, a complex network, along with complex interaction relationships and a large number of nodes, has been formed; therefore, it is necessary to further explore the impact of nodes on the entire network and improve the management and the control efficiency of the actual UUV network []. Currently, the identification methods of the critical nodes are mainly divided into adjacent node methods and path propagation methods, such as the degree centrality method [], the local centrality method [], and the mesocentric method []. For instance, Kitsak et al. believed that the location of a node in the center of the network indicates that the node is more critical, and they proposed a K-core decomposition method based on this theory []. Moreover, Yu et al. identified the key nodes from the perspective of entropy by using the impact of node clustering coefficient and the number of first and second-order neighbors on the node importance []. In addition, Wang et al. proposed a novel community-based method to identify a set of vital nodes for influence maximization in the attributed networks []. Finally, Jiang et al. developed an attenuation-based supra-adjacency matrix (ASAM) modeling method to further evaluate the importance of the nodes by calculating the similarity between adjacent layers and the cross-layer networks [].
For underwater confrontation scenarios, Liu et al. proposed a multi-UUV maneuvering decision-making algorithm for a counter-game with a dynamic target scenario []. The algorithm uses interval intuitionistic fuzzy rules to model the game and uses fractional order recurrent neural networks (RNN) to achieve optimal maneuvering strategies for the confrontation. From another point of view, considering the characteristics of large delay of underwater communication, the algorithm proposed in this paper is to reconstruct the network structure of enemy formation based on the time delay from the perspective of identification-strike, and then rank the importance of nodes based on the network, in order to strike the critical nodes of enemy formation to maximize the destruction of enemy combat effectiveness for confrontation. The innovations of this paper mainly include: 1. proposing a network reconstruction algorithm for unknown structure underwater formation, and reconstructing the formation network structure through its spatiotemporal trajectory; 2. based on the formation network, proposing a critical node identification algorithm with comprehensive importance network structure entropy to analyze the importance of each node in the multi-UUV formation.
To sum up, this paper is divided as follows: in Section 2, the formation network reconstruction is provided whereas the key node identification algorithm is presented in Section 3. As for Section 4, it represents the results and the discussion and finally, the conclusion and some future works are proposed in Section 5.
2. Formation Network Reconstruction
2.1. Leader–Follower Relationship
According to the analysis method of group intelligence behavior, the formation with group intelligence has some similarity with the leader in behavioral actions, and there is a hierarchical relationship characterized by the time delay between individuals []. For example, in a pigeon flock, the follower pigeons will observe the movements of the leader pigeons visually and make corresponding movements to maintain the consistency of the formation. In the underwater formation, other UUVs follow the trajectory of the leader UUV and keep the relative angle and distance to stabilize the formation, i.e., there are also motion similarities between individuals and leaders in the group. In reverse analysis, the leader–follower relation between UUVs in underwater formations can be derived based on their motion similarity analysis. The spatiotemporal trajectory data of UUV nodes is analyzed in arbitrary pairs by using the correlation function, and the obtained correlation coefficient can be used to characterize the motion similarity between the paired UUVs. Moreover, when the corresponding motion correlation coefficient remains at a fairly high value at any given moment, it can be regarded as the behavior of one UUV being “inherited” by another one, that is, it is considered that there is a leader–follower relation between the UUVs. Among them, the “inherited” behavior is to follow the UUV whereas the other is to pilot the UUV. To quantify this link, the spatiotemporal trajectory function of any UUV in the formation and other UUVs is analyzed to determine the motion correlation, and the motion similarity function is established as follows:
where represents the ’s normalized speed at moment , represents the ’s normalized speed at moment , is time delay which is a variable, is the inner product operator sign, and is the function of the motion correlation coefficient between and at time but for different delay times.
In addition, we set a threshold : when the motion correlation coefficient at a certain point in time is bigger than the threshold (e.g., ), it is believed that there is a leader–follower relation between the two UUVs at this moment. Therefore, in order to better determine the appropriate delay time, in the actual calculation process, individual motion correlation coefficients, having smaller values than the threshold, and mainly caused by the instability of the data or the error of acquiring the data, are used. Thus, the average motion correlation coefficient is determined as follows:
where is the number of spatiotemporal trajectories, , that is, a total of motion correlation coefficients are generated in trajectory points at time delay . is the average motion correlation coefficient between the and at different delay times . Moreover, the similarity of motion between the pairs of UUV is determined.
By establishing the above similar motion model, the correlation coefficient relative to the action between the paired UUVs under different time delays is obtained, and the threshold to is set. Moreover, if is obtained for any value of , it is considered that there is a leader–follower relationship between the paired vehicle; therefore, the delay time resulting in the maximum value of is defined to be the relevant time delay between the paired and , and it will be denoted by . Thus, the next step consists of setting the time delay matrix to represent the delay relationship between the formation UUVs: when is positive, it means that the navigation direction of is ahead of the , that is, is the leader, and is the following UUV. However, if is negative, the roles of the UUVs are the opposite.
2.2. Formation Hierarchy
Limited by the narrow bandwidth of the underwater acoustic channel and the UUV formation method, the UUV formation movement mostly adopts a hierarchical interaction structure []. Moreover, it is faster and more efficient in navigation and command execution than in the equal interaction structure. While using hierarchical interaction in the underwater unmanned cluster formation, there is a hierarchical structure relationship between UUVs, and the higher the level of UUVs, the better its control and the greater the importance in the formation network will be.
Based on the similar motion model, the leader–follower relationship between all UUVs and other UUVs in the formation is obtained and the hierarchical relationship of the entire network is analyzed. In the leader–following model, the movement command is issued according to the hierarchy, and the UUV at the top of the hierarchy has a certain leadership relationship with the other UUVs. However, when both and of the previous level have a leadership relationship with the pair of the next level, returning to the judgment of the time delay is performed: if , it Is considered that it has a leadership following relationship of the UUV with a smaller delay, that is, has a leadership relationship with .
2.3. Network Weight Matrix
In the network topology diagram, there is a certain weight coefficient between the two nodes to characterize the location proximity relationship between them. For example, when vertices represent some physical locations, the weight of the edge between two vertices can be set to the actual distance. During network formation, the distance between the different UUVs reflects the proximity relationship between the nodes, and here the normalized distance is used to represent the weight of the connected edges of nodes, usually the closer the distance the more reliable the interaction between two nodes is, and the weight of the connected edges is considered to be higher. Moreover, the distance between and is normalized as one of the factors affecting the weights on the edges; thus, one can get the following equation:
where is the result of normalized distance . In addition, considering that the correlation between the different UUVs is related to the motion similarity, higher motion similarity implies higher inheritance, and the more important the connected edge is considered to be. Thus, the average motion correlation coefficient of and at the time delay is introduced into the weights on the edges of both nodes and in the network topology. It is then combined with the above-normalized distance in order to obtain the weight on the edge formed by both nodes:
2.4. Mobile Formation Network Structure
According to the above steps, the leader–follower relationship, the hierarchical structure, and the weights on the edges of two nodes in the network were obtained. Therefore, the adjacency matrix , pointed to the network nodes, and the weight matrix representing the weights of the nodes, was established. In this matrix, if there is a leader–following relationship between nodes, the value of the cell will be equal to one (e.g., ), and vice versa, the absence of a relation yields a null value (e.g., ). Based on these definitions, we attained a map of the network topology of the mobile UUV formation. The following guidelines are made when creating the network topology diagram, though, in order to be more in line with the characteristics of the underwater cluster formation. This is because underwater communication has a distance limit, each UUV in the unmanned cluster formation has a different task, and the sensors carried on the boat are also different. Information is only dealt with layer by layer across neighboring levels; each UUV only receives instructions provided by one UUV, but can issue instructions to several UUVs. Thus, through regular filtering, the network structure reconstruction of the mobile UUV formation is completed.
3. Key node Identification Algorithm
3.1. Network Structure Model
In order to represent the connection between the different individuals in the mobile UUV formation in a more intuitive and clear way, the use of diagrams, where the nodes represent UUVs and the edges represent the interconnections between UUVs, was the applied solution. This network structure model is usually expressed as , where is the set of network nodes and is the total number of nodes in the network. Moreover, is the set of edges between nodes, and is the total number of edges in the network. Finally, represents the weight matrix where represents the weight value on the edge of nodes and , and generally has in directed networks. As for a weighted network, it can be thought of as a weighted network with all the weight values of 1. Finally, it is important to mention that there are four basic types of networks: undirected networks, weighted undirected networks, unweighted directed networks, and weighted directed networks []. All types are shown in Figure 1:
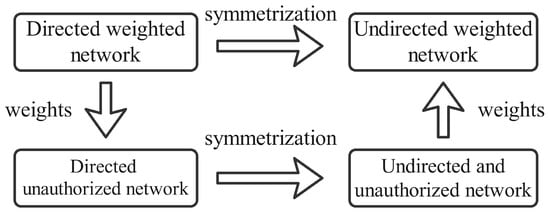
Figure 1.
Four network types.
3.2. Network Structure Entropy
In the network topology, the performance of the network scalelessness is considered a kind of network “heterogeneity”, and this “heterogeneity” of complex networks can be described using the concept of “entropy”, that is, the entropy of the network structure [].
In order to better establish the entropy model based on the network structure, the following keywords have been defined:
(1) Degree value. The degree value of a node is called the node strength, and the degree of node is defined as the number of nodes directly connected to the node . Moreover, is expressed using the following relation:
where is the collection of neighbor nodes of the particle node . As for the weighted network,
where is the weight on the edge connecting node to node . In a directed network, the degree value of a node is divided into an outdegree value and an in-degree value, and it is generally believed that both values have different effects on the node, that is
where and are the indegree and outdegree values of node , respectively, and is the influence coefficient. When , the relevance of the node is thought to be more influenced by its input strength.
(2) Adjacency. To more accurately reflect the impact of a node on its connected neighbor nodes, the adjacency of a node is defined as follows:
where and are the degree value of the node pointing to and the node pointed by in the neighboring nodes of node , is the set of neighbor nodes of node , and is the degree of adjacency of node (the greater the value of is, the higher its impact on neighboring nodes will be).
(3) Importance. The nodes in the network affect each other, and considering only the degree value will lose the influence of indirect neighbors on the nodes, and considering the global nodes will increase the complexity of the algorithm, and the effect may not be very good. The influence of a node is limited, and it only has a large influence on its nearby neighbors. The probability function is used to describe the chance to select a given node among its neighbors, which is defined as:
In the entropy of network structures based on the node degree, the probability functions can be used to express the importance of nodes. However, in underwater mobile formations, often the higher the level of UUV is, the greater its importance will be. Therefore, considering the importance of the degree and level of nodes, the comprehensive importance is introduced to express the importance of the network nodes. Considering that the control commands and the information transmission in the formation are carried out layer by layer, the high-level UUV will have an impact on the low-level UUV; therefore, for an N-level network, the importance of the hierarchical nodes should be continuously reduced, and the weight factor of the nodes on the level is expressed as follows:
The comprehensive importance of the node is calculated as follows:
(4) Network structure entropy. Information entropy uses probabilistic and statistical methods to measure the complexity of a system, which represents the expectation of the amount of information brought by all possible events, and it can be used as well to measure the importance of network nodes. Consider the unrelated events and to be equal to the sum of the information obtained when the observed events occur at the same time, that is , and . Therefore, it can be obtained that must be related to the logarithm of . Thus, the relation between both variables can be written as follows:
Moreover, the expected amount of information is defined as follows:
Make sure, at this level, that the information entropy value is always positive, take the absolute value of the node information entropy when calculating it, and replace the probability function with the comprehensive importance to obtain the entropy of the collar network structure. Therefore, the resulting equation is as follows:
3.3. Critical Node Identification Algorithm
By analyzing the interaction between the nodes and their indirect nodes, the entropy of the network structure is used to measure the importance of several nodes in the network. Considering that in the formation network structure, the instruction is transmitted from a high level to a low-level UUV, the node importance of the directed network is only analyzed; therefore, it is considered that the entry value of the node is smaller than the influence of the degree value on the node, and the impact factor is . In more detail, the milestone algorithm steps are presented as follows:
Step 1: Analyze the formation network according to the mobile UUV formation spatiotemporal trajectory meter and get the adjacency matrix and the weight matrix .
Step 2: Calculate the node degree value according to the difference between the node outdegree and indegree:
Step 3: Calculate the degree of adjacency:
Step 4: Calculate the overall importance:
Step 5: Calculate the entropy of the network structure:
The calculation process is shown in Figure 2. Based on the above steps, the network structure entropy of each node in the network can be calculated. According to the size of entropy, each node is ordered, and the node entropy value is classified from large to small corresponding to the importance of this node.
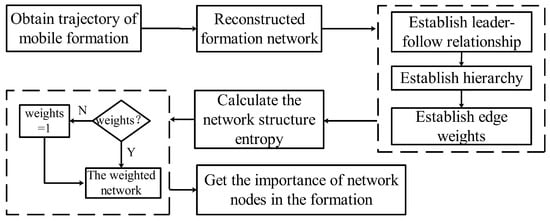
Figure 2.
Algorithm flow of critical node identification.
4. Validation and Analysis
The identification of the key nodes of the mobile UUV formation is to establish the network topology of the mobile formation by analyzing spatiotemporal trajectories in order to further rank the importance of the nodes by the key node identification algorithm. Therefore, this section sets up the simulation experiments and the lake experiments to verify the efficiency of the proposed algorithm.
4.1. Simulation and Experiments Analysis
In order to verify the effectiveness of the key node identification algorithm based on the entropy of the network structure, this section uses Matlab© to perform the simulation experiments. Based on the leader–follower formation control model, we considered one leader and seven followers to navigate a “U” trajectory in a triangular formation to verify the discrimination effect of the algorithm. In this simulation, the distance matrix and delay matrix are set as follows. (In the matrix , the element 0 indicates that the two nodes are not directly related and have no real physical significance):
In addition, we added the trajectory of an unrelated UUV to the formation in the simulation to compare and judge the effects of this additional feature. Therefore, the simulation results are displayed in Figure 3.
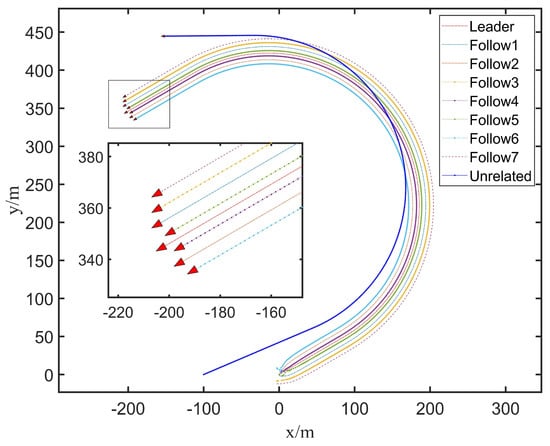
Figure 3.
“U”−shaped formation trajectory. It shows the trajectories of each node navigating in formation in the simulation, and the enlarged portion of the figure shows the structure of the formation.
Figure 3 shows that the follower trajectories the leader well at a predetermined angle and distance based on the influence of the controller. Then, a pairwise analysis was performed on the spatiotemporal trajectories of all UUVs using the aforementioned motion similarity model. The delay matrix and the motion correlation coefficient (refer to Table 1) of the UUV formation are calculated as follows:

Table 1.
“U” shape trajectory motion correlation coefficient.
By comparing the time delay matrix and , the accuracy of the time delay data obtained by the algorithm was 84.6%, and in addition, the erroneous time delay data did not appear between nodes with the direct leader–follower relationships, and the erroneous data did not affect the accuracy of the subsequent reconstruction of the formation network structure. Based on the above delay matrix, the time delay between UUVs with a leader–following relationship represents an antisymmetric transfer, and the positive and negative delays indicate whether the UUV is following or being followed. Moreover, these values also specified the delay time for the follower to receive the leader’s movement information and take action, which is in line with the law of following a relationship. When the time delay was null, it means that there was no leader–following relationship between the paired UUVs.
Referring to Table 1, the correlation coefficient corresponds to the time delay, and the motion correlation coefficient between the UUVs is varying at different time delays, as shown in Figure 4. Since the leader following the model does not introduce errors, such as propulsion, hydroacoustic delay, and complex environmental interference, the motion correlation coefficient between each UUV at the corresponding delay time was very large; however, when being compared to the motion correlation coefficient of the unrelated-UUV, there was a significant gap, and the unrelated UUV’s motion correlation coefficient was much smaller than others. Setting the threshold value , and as , the correlation coefficient of the motion of the unrelated UUV and any other UUV was less than the threshold; therefore, it is considered that the unrelated UUV does not have a leader–follower relationship with any other UUV.
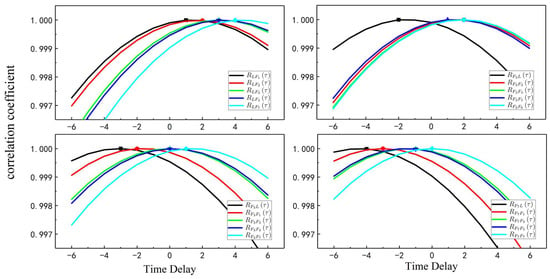
Figure 4.
Correlation coefficient and time delay function.
Referring to the matrix Equation (23), and according to the size of the delay, the leader–following relationship of UUVs between pairs was judged, and it was sorted according to the leader–follower level, and the following points were calculated: all followers had a following relationship for the leader, whereas Follow1 and Follow2 had a leadership relationship for the remaining UUVs, and Follow3, Follow4, Follow5, and Follow6 had a leadership relationship for Follow7.
Therefore, the formation network hierarchy was obtained: the UUV leader belonged to the first level, Follow1, Follow2 were part of the second level, Follow3, Follow4, Follow5, and Follow6 belonged to the third level, and, finally, Follow7 belonged to the fourth level. The network relationship, obtained through the above analysis, was still relatively complex where one UUV had a following relationship with multiple UUVs at the same time. Considering the communication restrictions of the underwater formation, etc., it was considered to have a following relationship with the nearest vehicle. Through the analysis of the network again using this rule, the network structure of the formation can be obtained, as shown in Figure 5.
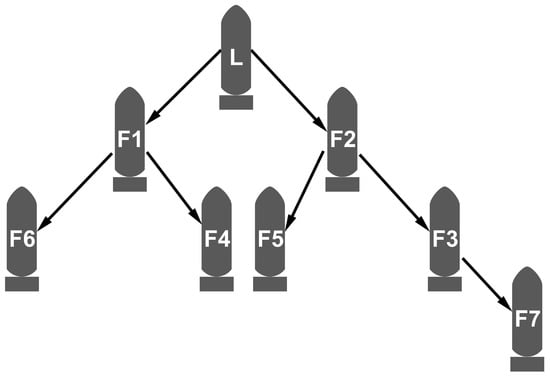
Figure 5.
Mobile UUV formation network structure. The letters L and F stand for leader UUV and follower UUV; F1 denotes Follow1 UUV and F2 denotes Follow2 UUV and so on. The arrows indicate the direction of information transmission in the formation network.
Therefore, the collar matrix of the formation network was obtained as follows, and, when being combined with the behavioral correlation coefficient matrix, it was brought into the established node edge weight coefficient model; hence, the weight coefficient matrix of the formation network can be expressed as follows:
According to the formation network structure and its corresponding collar relationship and weight coefficient matrices, the node importance is calculated by using the network structure entropy model. Firstly, according to the adjacency and the weight matrices of the network, the input intensity value and the output intensity value of each node are calculated. Moreover, according to Equation (17), the comprehensive strength value of each node is calculated to get Table 2.

Table 2.
Node comprehensive strength value.
Then, also taking , according to Equation (18), the comprehensive adjacency strength value q of the node is calculated as shown in Table 3.

Table 3.
Node adjacency strength value.
Finally, according to Equation (21), the entropy of each network structure is calculated, and the following results are presented in Table 4.

Table 4.
Node network structure entropy.
Based on the entropy of the network structure calculated above, the followers can be arranged using the following order: Follow2 > Follow1 > Leader > Follow3 > Follow5 > Follow4 = Follow6 > Follow7. According to the network structure, the relevance of the Follow1 and Follow2 nodes was higher, since Follow1 and Follow2 regulated information relative to the input and output flows. Moreover, Follow3 controlled Follow7; therefore, it was more critical than other followers of the same level. Finally, Follow4, Follow5, and Follow6 were all considered as edge nodes of the formation network; thus, their information entropy was basically the same, and this was conforming to the network structure law.
By using the traditional information entropy algorithm [], the information entropy of each node under the network result was calculated as shown in Table 5.

Table 5.
Node information entropy.
In the above table, the order of the information entropy of the nodes is: Follower1 > Follower2 > Follower3 > Leader > Follower5 > Follower4 = Follower6 > Follower7, but we believe that the node leader was more important than the node Follower3, and the node Follower2 was more important than the node Follower1. Compared with the network structure entropy results in Table 4, it can be obtained that the improved algorithm in this paper was more in line with the actual situation in ordering the important nodes of the underwater network structure than the traditional information entropy algorithm.
4.2. Lake Experiments and Analysis
In order to verify the effectiveness of critical node identification of the multi-UUV formation algorithm proposed in this paper, the lake formation experiment was carried out, and the real dead reckoning data were obtained to place the detection of UUV formations. Therefore, three vehicles set up the trajectory of vehicles, not linked to the formation navigation, while sailing in linear and triangular formations on the Qiandao Lake in Hangzhou City as the test location in order to confirm that the algorithm can successfully recognize different network structures. Figure 6a shows the experiment platform and Figure 6b shows UUV formation sailing on the water. Two sets of trajectory points recorded by the UUV itself are shown in Figure 7:

Figure 6.
Photos of lake experiments. (a) Experiment platform, (b) UUV formation navigation.
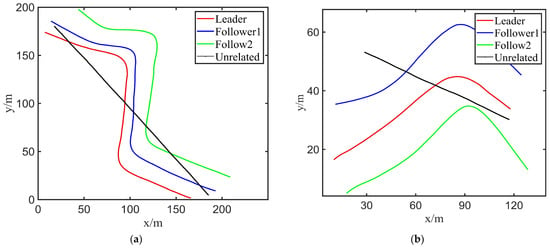
Figure 7.
UUV formation waypoints in two groups of different formations. (a) Liner shape navigation trajectory, (b) triangular navigation trajectory.
Referring to the paths of Figure 7, the follower has several degrees of error with respect to the leader’s trajectory, but the trajectory it follows has generally the same shape. The space–time UUV trajectories were substituted every two pairs with the motion similarity model to obtain the following motion correlation coefficient (refer to Equation (25)) and time delay tables (refer to Table 6 and Table 7):

Table 6.
Liner shape motion correlation coefficient.

Table 7.
Triangular motion correlation coefficient.
In the above motion correlation coefficients table, the average motion similarity between the leaders and the followers was high; however, the motion similarity coefficients of spatiotemporal trajectories of unrelated UUV and other UUVs were quite different compared to others. Setting the threshold , the similarity coefficient of the motion between the unrelated UUV and any other UUV was below the threshold; therefore, it is considered that there is no leader–follower relationship with any other UUV.
In the above time delay matrix, when the formation was carried out in a liner shape, if the UUV leader is the leader, the time delay between it and Follow1 and Follow2 is greater than zero. However, when Follow1 was the leader, the time delay between it and the UUV leader was less than zero, and the time delay with Follow2 was greater than zero. Therefore, the UUV leader had the leadership relationships for Follow1 and Follow2, and Follow1 also had leadership relationships for Follow2, which resulted in the structural relationship shown in Figure 8a. When moving in a triangle, the UUV leader had a leadership relationship with Follow1 and Follow2. Regardless of whether Follow1 or Follow2 were leaders or followers, the time delay between them was equal to zero, that is, there was no leader–following relationship, belonging to the same level, and the structural relationship, shown in Figure 8b, can be obtained, which was in line with the experimental setting.
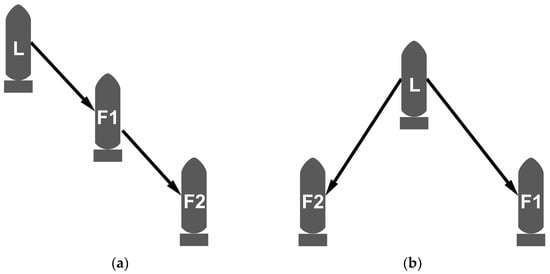
Figure 8.
Multi-UUV formation. (a) Linear shape formation structure, (b) Triangular shape formation structure. The letters L and F stand for leader UUV and follower UUV; F1 denotes Follow1 UUV and F2 denotes Follow2 UUV. The arrows indicate the direction of information transmission in the formation network.
Thus, the adjacency matrix and of the formation network was obtained:
In this experiment, the distances between the vehicles were all the same, and, combined with the motion similarity coefficient, the weight matrices under the two formations can be obtained:
According to the weight coefficient matrix, we found out that the difference between the weight coefficients was very small, so the directed weightless network structure entropy algorithm was applied to calculate the importance between the nodes.
According to the Equation (17), the comprehensive strength value of each node in both networks is calculated to get Table 8 and Table 9.

Table 8.
Liner shape node comprehensive strength value.

Table 9.
Triangular node comprehensive strength value.
Then, also taking , according to the Equation (18), the comprehensive adjacency strength value of the node in both networks was calculated as shown in Table 10 and Table 11.

Table 10.
Liner shape node adjacency strength value.

Table 11.
Triangular node adjacency strength value.
Finally, according to Equation (21), the entropy of each network structure was calculated, and the following results of both networks are presented in Table 12 and Table 13.

Table 12.
Liner shape node network structure entropy.

Table 13.
Triangular node network structure entropy.
According to the node network structure entropy obtained in the above tables, the size of the entropy of each node was ordered, in the liner shape formation, as Follow1 was responsible for connecting the UUV leader and Follow2 in the middle position of the line shape; therefore, this position was more critical, and the UUV leader was responsible for piloting and sending data, so its importance was greater than that of Follow2.
As for the triangular formation, the UUV leader was responsible for connecting Follow1 and Follow2, and it was also responsible for calculating and sending the route data, which was more critical than the other two; moreover, the other two followers had the same position, the same role, and the same importance.
In this paper, the trajectory used was recorded by the aircraft itself. The experiment in this paper was mainly to prove that under a series of continuous spatiotemporal trajectories, the algorithm of this paper can be used to reconstruct the network structure of unknown formations and effectively rank the importance of nodes. However, in real situations, the results obtained when observing the formation’s trajectory through sonar equipment or other methods will not be so dense, and the results obtained due to sensor interference will be biased. It is possible to consider adding an error model and using a filtering algorithm to process the tracks detected by the sonar.
5. Conclusions
Aiming at the critical node identification problem of UUV formation, this paper proposed a formation key node identification method, based on network structure entropy, which establishes the network structure of mobile UUV formation by presenting the motion similarity model, and then calculating the information entropy of network nodes by using the weighted network structure entropy algorithm to determine the importance of each node. The simulation experiments and lake experiments in this paper fully verify the effectiveness of the identification algorithm, which can be calculated from the spatiotemporal trajectory of the formation to calculate the importance ranking of the formation nodes, and also verify that it is feasible to use this method for underwater cluster countermeasures. As for future works, it should be considered to use sonar equipment to acquire formation trajectory data with disturbances to further validate the effectiveness of the algorithm. In the next step, it is planned to further enhance the structure reconstruction of unknown multi-UUV formations in other complex situations for discontinuous multi-UUV spatiotemporal trajectories, considering the impact of the hydroacoustic communication packet’s loss and other effects on the control formation for more accurate critical node identification.
Author Contributions
Conceptualization, L.L.; Data curation, Y.C. and X.Z.; Funding acquisition, L.L.; Methodology, Y.C.; Project administration, L.Z.; Resources, Y.Y.; Software, B.Z.; Supervision, G.P.; Validation, L.L. and R.R.; Writing—original draft, Y.C.; Writing—review & editing, W.Q. and R.R. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Local Science and Technology Special Foundation under the Guidance of the Central Government of Shenzhen under Grant 2021Szvup111; in part by the Shenzhen Science and Technology Program under Grant JCYJ20210324122010027 and JCYJ20210324122406019; in part by the National Natural Science Foundation of China under Grant 52001259, Grant 11902252, and Grant 51979229; in part by the National Research and Development Project under Grant 2021YFC2803001; in part by the Maritime Defense Technology Innovation Center Innovation Fund under Grant JJ-2021-702-09; and in part by the China Postdoctoral Science Foundation under Grant 2020M673484.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data that support the findings of this study are available within the article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Das, B.; Subudhi, B.; Pati Bibhuti, B. Cooperative Formation Control of Autonomous Underwater Vehicles: An Overview. Int. J. Autom. Comput. 2016, 13, 199–225. [Google Scholar] [CrossRef]
- Khawaja, W.; Semkin, V.; Ratyal, N.I.; Yaqoob, Q.; Gul, J.; Guvenc, I. Threats from and Countermeasures for Unmanned Aerial and Underwater Vehicles. Sensors 2022, 22, 3896. [Google Scholar] [CrossRef] [PubMed]
- Wang, G.-Y.; Cheng, D.-D.; Xia, D.-Y.; Jiang, H.-H. Swarm Intelligence Research: From Bio-inspired Single-population Swarm Intelligence to Human-machine Hybrid Swarm Intelligence. Mach. Intell. Res. 2023, 20, 121–144. [Google Scholar] [CrossRef]
- Kumoye, A.O.; Prasad, R.; Fonkam, M. Swarm Intelligence Algorithm and its Application: A Critical Review. In Proceedings of the 2020 International Conference in Mathematics, Computer Engineering and Computer Science (ICMCECS), Ayobo, Nigeria, 18–21 March 2020. [Google Scholar]
- Jung, N.; Weon, B.M.; Kim, P. Effects of adaptive acceleration response of birds on collective behaviors. J. Phys. Complex. 2022, 3, 015014. [Google Scholar] [CrossRef]
- Mugica, J.; Torrents, J.; Cristin, J.; Puy, A.; Miguel, M.C.; Pastor-Satorras, R. Scale-free behavioral cascades and effective leadership in schooling fish. Sci. Rep. 2022, 12, 10783. [Google Scholar] [CrossRef]
- Biro, D.; Sumpter, D.J.T.; Meade, J.; Guilford, T. From Compromise to Leadership in Pigeon Homing. Curr. Biol. 2006, 16, 2123–2128. [Google Scholar] [CrossRef]
- Huo, M.Z.; Duan, H.B.; Ding, X.L. Manned Aircraft and Unmanned Aerial Vehicle Heterogeneous Formation Flight Control via Heterogeneous Pigeon Flock Consistency. Unmanned Syst. 2021, 9, 227–236. [Google Scholar] [CrossRef]
- Park, J.; Kahng, B. Synchronization in leader-follower switching dynamics. Phys. Rev. Res. 2020, 2, 032061. [Google Scholar] [CrossRef]
- Xu, G.H.; Xu, M.; Ge, M.F.; Ding, T.F.; Qi, F.; Li, M. Distributed Event-Based Control of Hierarchical Leader-Follower Networks with Time-Varying Layer-To-Layer Delays. Energies 2020, 13, 1808. [Google Scholar] [CrossRef]
- Ugurlu, O. Comparative analysis of centrality measures for identifying critical nodes in complex networks. J. Comput. Sci. 2022, 62. [Google Scholar] [CrossRef]
- Cai, B.; Zeng, L.N.; Wang, Y.P.; Li, H.J.; Hu, Y.M. Community Detection Method Based on Node Density, Degree Centrality, and K-Means Clustering in Complex Network. Entropy 2019, 21, 1145. [Google Scholar] [CrossRef]
- Yang, X.H.; Xiong, Z.; Ma, F.N.; Chen, X.Z.; Ruan, Z.Y.; Jiang, P.; Xu, X.L. Identifying influential spreaders in complex networks based on network embedding and node local centrality. Phys. A-Stat. Mech. Its Appl. 2021, 573, 125971. [Google Scholar] [CrossRef]
- Wandelt, S.; Shi, X.; Sun, X.Q. Approximation of Interactive Betweenness Centrality in Large Complex Networks. Complexity 2020, 2020, 4046027. [Google Scholar] [CrossRef]
- Kitsak, M.; Gallos, L.K.; Havlin, S.; Liljeros, F.; Muchnik, L.; Stanley, H.E.; Makse, H.A. Identification of influential spreaders in complex networks. Nat. Phys. 2010, 6, 888–893. [Google Scholar] [CrossRef]
- Yu, Y.; Zhou, B.; Chen, L.J.; Gao, T.; Liu, J.Z. Identifying Important Nodes in Complex Networks Based on Node Propagation Entropy. Entropy 2022, 24, 275. [Google Scholar] [CrossRef]
- Wang, Y.; Zheng, Y.; Liu, Y. Identifying vital nodes for influence maximization in attributed networks. Sci. Rep. 2022, 12, 22630. [Google Scholar] [CrossRef]
- Jiang, J.-L.; Fang, H.; Li, S.-Q.; Li, W.-M. Identifying important nodes for temporal networks based on the ASAM model. Phys. A Stat. Mech. Its Appl. 2022, 586, 126455. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, S.; Zhang, L.; Pan, G.; Yu, J. Multi-UUV Maneuvering Counter-Game for Dynamic Target Scenario Based on Fractional-Order Recurrent Neural Network. IEEE Trans. Cybern. 2022, 53, 4015–4028. [Google Scholar] [CrossRef]
- Nagy, M.; Vasarhelyi, G.; Pettit, B.; Roberts-Mariani, I.; Vicsek, T.; Biro, D. Context-dependent hierarchies in pigeons. Proc. Natl. Acad. Sci. USA 2013, 110, 13049–13054. [Google Scholar] [CrossRef]
- Zhang, W.; Wang, N.; Wei, S.; Du, X.; Yan, Z. Overview of unmanned underwater vehicle swarm development status and key technologies. J. Harbin Eng. Univ. 2020, 41, 289–297. [Google Scholar]
- Yang, P.; Xu, C.; Chen, H. Multi-attribute ranking method for identifying key nodes in complex networks based on GRA. Int. J. Mod. Phys. B. Condens. Matter Phys. Stat. Phys. Appl. Phys. 2018, 32, 1850363. [Google Scholar] [CrossRef]
- Tyrsin, A.N. Entropy Modeling of Network Structures. Autom. Remote Control 2022, 83, 1608–1618. [Google Scholar] [CrossRef]
- Zhang, Q.; Li, M.; Deng, Y. A betweenness structure entropy of complex networks. Chaos Solitons Fractals 2022, 161, 112264. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).