VirtFogSim: A Parallel Toolbox for Dynamic Energy-Delay Performance Testing and Optimization of 5G Mobile-Fog-Cloud Virtualized Platforms
Abstract
1. Introduction
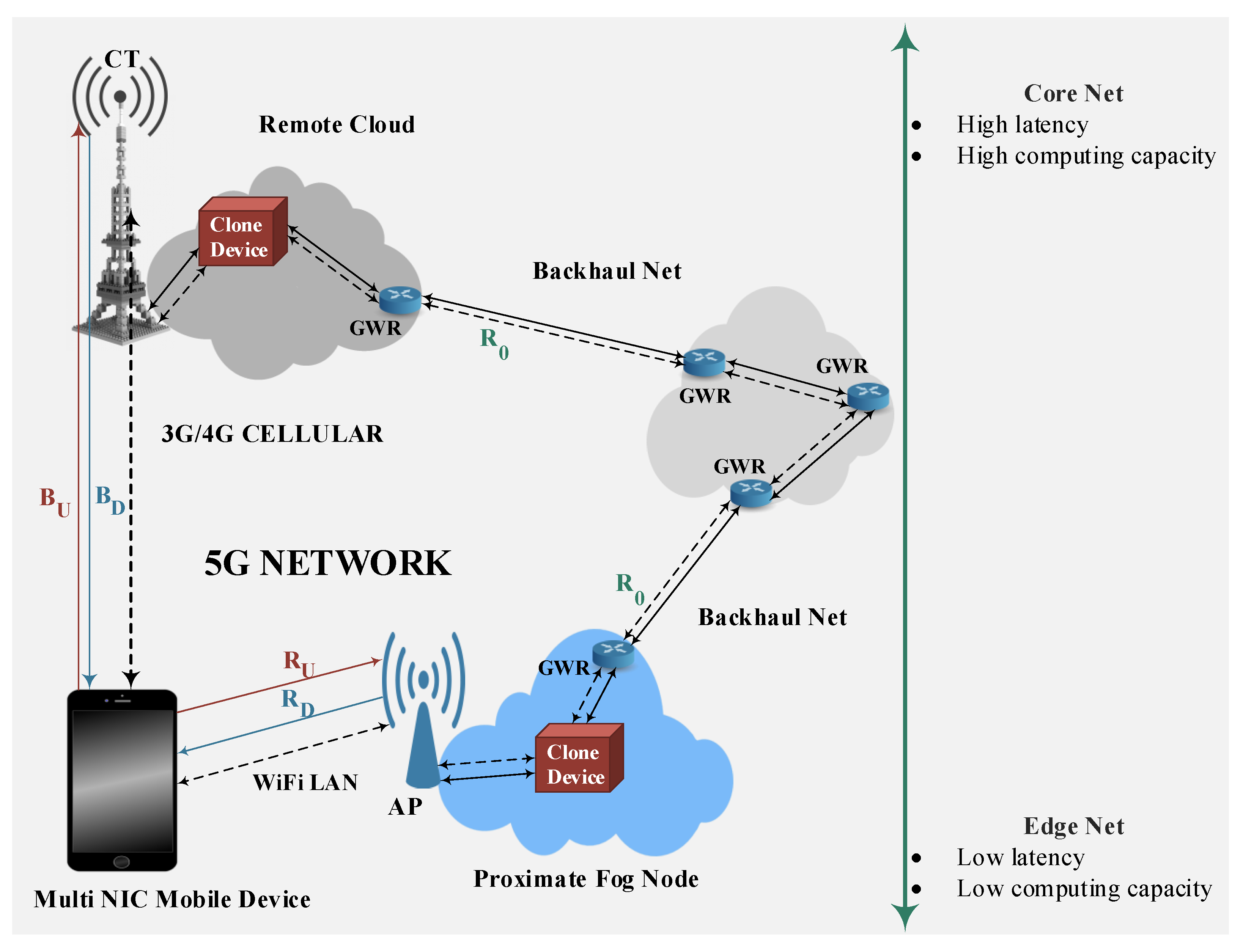
1.1. The Multi-Tiered Networked Simulated Environment
- Mobile-Fog communication is supported by a two-way WiFi-based (possibly, mobile) single-hop TCP/IP connection. (resp., ) is the steady-state throughput of the Mobile-to-Fog (resp., Fog-to-Mobile) upstream (resp., downstream) TCP/IP one-way connection. Their peak values depend, in turn, on the adopted WiFi technology;
- Mobile-Cloud communication is supported by a two-way 3G/4G cellular (possibly, mobile and/or multi-hop) TCP/IP connection. (resp., ) is the steady-state throughput of the Mobile-to-Cloud (resp., Cloud-to-Mobile) upstream (resp., downstream) TCP/IP one-way connection;
- Cloud-Fog communication is supported by a two-way (possibly, wired and multi-hop) backhaul TCP/IP connection. is the corresponding steady-state throughput.
1.2. A Motivational Example
1.3. Motivations, Main Contributions, and Organization of the Paper
- simulation on parallel hardware machines;
- dynamic optimization;
- dynamic tracking;
- comparison;
- graphic rendering through an ad-hoc-designed Graphic Use Interface (GUI),
- test their desired application DAGs by customizing the simulation environment of Figure 1 through the setting of the 67 input parameters of the simulator package;
- track dynamically the energy-delay DAG performance against abrupt (possibly, unpredictable) changes of the simulated environment of Figure 1, like mobility-induced changes of the available up/down Cellular-WiFi bandwidths;
- optimize the obtained DAG performance against a number of metrics, like total consumed energy, network consumed energy, network bandwidth, computing frequency, and execution delays, just to name a few.
- it allows the numerical evaluation of the delay-constrained minimization of the overall computing-plus-network energy consumed by the execution of the input DAG. The optimization is performed by task offloading and allocation of the per-core computing frequencies and up/down Cellular-WiFi bandwidths of the platform of Figure 1 in a joint and adaptive way;
- resource allocation is performed by explicitly accounting for the container-based virtualized nature of the reference platform of Figure 1. For this purpose, the VirtFogSim toolbox relies on a gradient-based primal-dual iterative procedure that implements a set of ad-hoc designed adaptive (e.g., time-varying) step-sizes: The goal is to speed up the convergence to the corresponding steady-states of the per-core computing frequencies and per-connection bandwidths to be dynamically allocated;
- it allows the user to test the energy-delay performances of six different task allocation strategies, namely the Genetic, Only-Mobile, Only-Fog, Only-Cloud, Only-Task Allocation, and Exhaustive-Search strategies (see Section 4), and to add new user-defined strategies;
- the code of the core engine of the simulator leverages the Parallel Toolbox of MATLAB, in order to exploit automatically the multi-core capability possibly retained by the execution environment of the simulator.
- the display of the dynamic time behavior of the performed resource allocation under the time-varying simulation environment set by the user and;
- the rendering of the data output by the simulator in tabular, bar-plot, and colored map graph formats (see Section 5).
- the adaptive capability and the energy-delay performance of the (aforementioned) six task allocation strategies have been checked and compared under three benchmark DAGs. They refer to different use cases featuring some computing, multimedia, and scientific applications of practical interest and exhibit different symmetric/asymmetric/pseudo-random topologies of various sizes and in/out node degrees;
- the scaling capability of the simulator has been numerically profiled in terms of both simulation times and volumes of data that are exchanged among the running cores.
2. Related Work
3. VirtFogSim: A View of the Simulated Formal Models
3.1. Profiling the Simulated Workflows
- the processing frequency at the Mobile device;
- the processing frequency at the Fog clone;
- the processing frequency at the Cloud clone;
- the throughput of the Mobile-to-Fog TCP/IP connection;
- the throughput of the Fog-to-Mobile TCP/IP connection;
- the throughput of the Mobile-to-Cloud TCP/IP connection;
- the throughput of the Cloud-to-Mobile TCP/IP connection.
3.2. The Considered Throughput-Constrained Joint Task and Dynamic Resource Allocation Problem
- is the resource allocation vector defined in Equation (2);
- is the task allocation vector defined in Equation (1);
- (s) is the overall time needed to execute the assigned application DAG, in short, the DAG execution time. It generally depends on the optimization variables and ;
- (app/s) is the required minimum application throughput, i.e., the minimum number of application DAGs to be performed in the time interval of one second. It is a non-negative real number;
3.3. Simulated Computing and Networking Energy Profiles
- the static energy accounts for the energy wasted by the device in the idle state (e.g., the device is turned ON, but it is not running). As a consequence, since the power consumed by the device in the idle state (Watt) does not depend on the optimization variables, the static energy depends on the optimization variables and only through the corresponding DAG execution time (s);
- the dynamic energy accounts for the energy wasted by the device when it is in the running state. As a consequence, since the resulting dynamic power depends on the operating computing frequency or communication bit rate, the dynamic energy of each device depends on the optimization variables and through both the DAG execution time (s) and the corresponding dynamic power (Watt).
- Kronecker’s delta (e.g., for and , otherwise); and by:
- the unit-step function (e.g., for and , otherwise),
3.4. Simulated Profiles of the per-DAG and per-Task Execution Times
3.5. Simulated Adaptive Resource Allocation Framework
4. VirtFogSim: Supported Task Allocation Strategies and Their Parallel Execution
4.1. General Architecture of the Developed Simulation Platform
- allows the user to setup 67 input parameters that characterize the scenario to be simulated by the user (see Figure 1);
- calls the GeneticTA_par function for parallel execution and returns the corresponding:
- (a)
- , i.e., ternary V-tuple best allocation vector;
- (b)
- (bit/s), i.e. the seven-tuple vector of the optimal resource allocation of the Mobile computing frequency, Fog computing frequency, Cloud computing frequency, Mobile-to-Fog transport throughput, Fog-to-Mobile transport throughput, Mobile-to-Cloud transport throughput, and Cloud-to-Mobile transport throughput (see Figure 1);
- (c)
- (Joule), i.e., the total computing-plus-network energy consumed by the infrastructure of Figure 1 under the returned task allocation vector. For this purpose, the GeneticTA function calls, in turn, the auxiliary functions RAP, Crossover, and Mutation;
- optionally, calls the OM_S function and returns:
- (a)
- (bit/s), i.e., the seven-tuple vector of the optimal resource allocation under the All-Mobile task allocation vector: ;
- (b)
- (Joule), i.e., the total computing-plus-network energy consumed by the infrastructure of Figure 1 under . If the returned is infinite, then the All-Mobile task allocation is infeasible. The OM_S function calls, in turn, the RAP function;
- optionally, calls the OF_S function and returns:
- (a)
- (bit/s), i.e., the seven-tuple vector of the optimal resource allocation under the All-Fog task allocation vector: ;
- (b)
- (Joule), i.e., the total computing-plus-network energy consumed by the infrastructure of Figure 1 under . If the returned is infinite, then the All-Fog task allocation is infeasible. The OF_S function calls, in turn, the RAP function;
- optionally, calls the OC_S function and returns:
- (a)
- (bit/s), i.e., the seven-tuple vector of the optimal resource allocation under the All-Cloud task allocation vector: ;
- (b)
- (Joule), i.e., the total computing-plus-network energy consumed by the infrastructure of Figure 1 under . If the returned is infinite, then, the All-Cloud task allocation is infeasible. The OC_S function calls, in turn, the RAP function;
- optionally, calls the O_TAS_par function for parallel execution and returns:
- (a)
- , i.e., the ternary V-tuple best allocation vector computed by O_TAS under the assumption that the optimization of the resource allocation is not performed;
- (a)
- (Joule), i.e., the total computing-plus-network energy consumed by the infrastructure of Figure 1 under . If the returned is infinite, then the O_TAS task allocation is infeasible. The O_TAS function calls, in turn, the Crossover, Mutation, and evaluatestaticenergy_p functions;
- optionally, calls the ES_S_par function and returns:
- (a)
- , i.e., the ternary V-tuple best task allocation vector computed by performing the exhaustive search over the full population of task allocation vectors of the size ;
- (b)
- (bit/s), i.e., the seven-tuple vector of the optimal resource allocation under ;
- (c)
- (Joule), i.e., the total computing-plus-network energy consumed by the infrastructure of Figure 1 under . If the returned is infinite, then the overall afforded optimization problem is infeasible. The ES_S function calls, in turn, the RAP function and requires that the task allocation vectors and are already available;
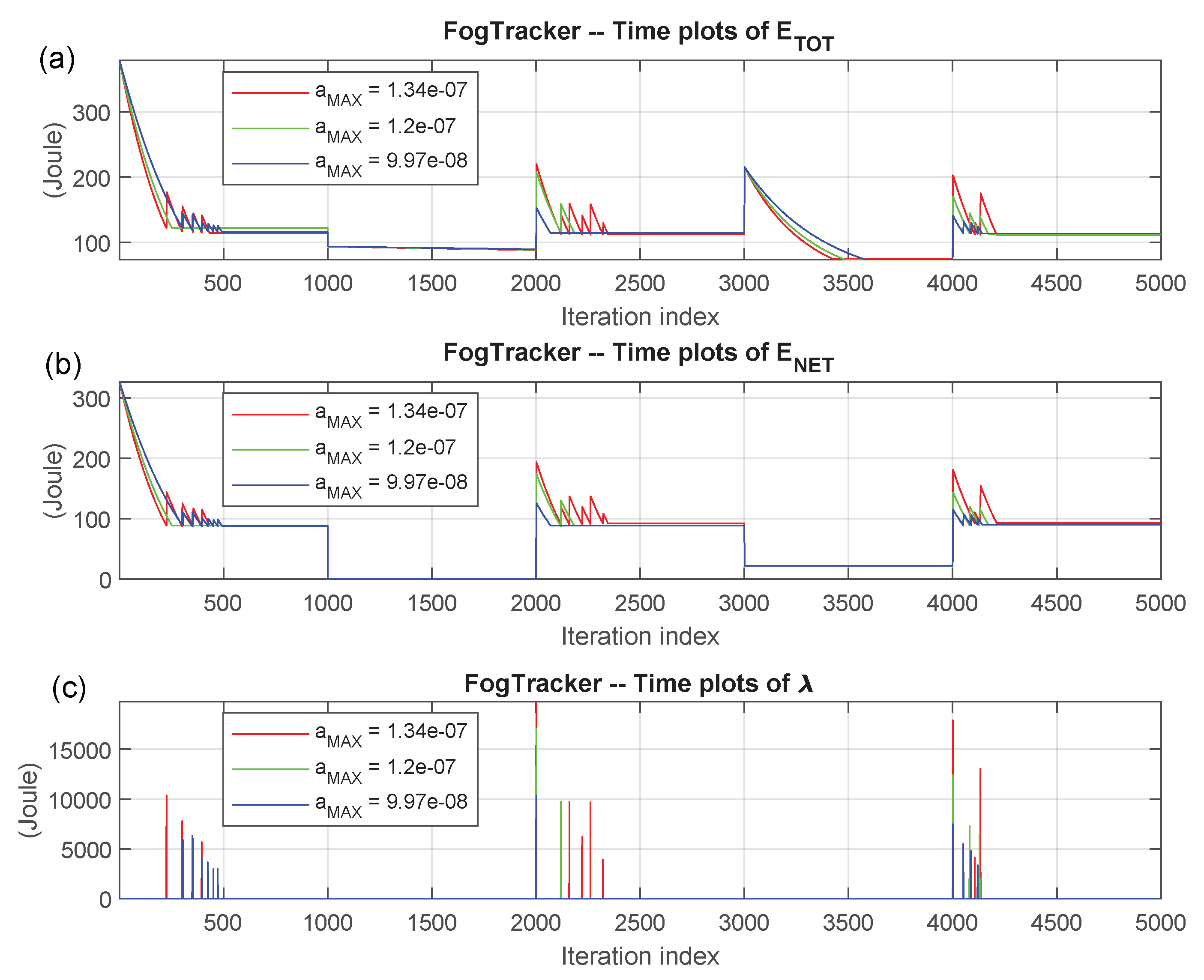
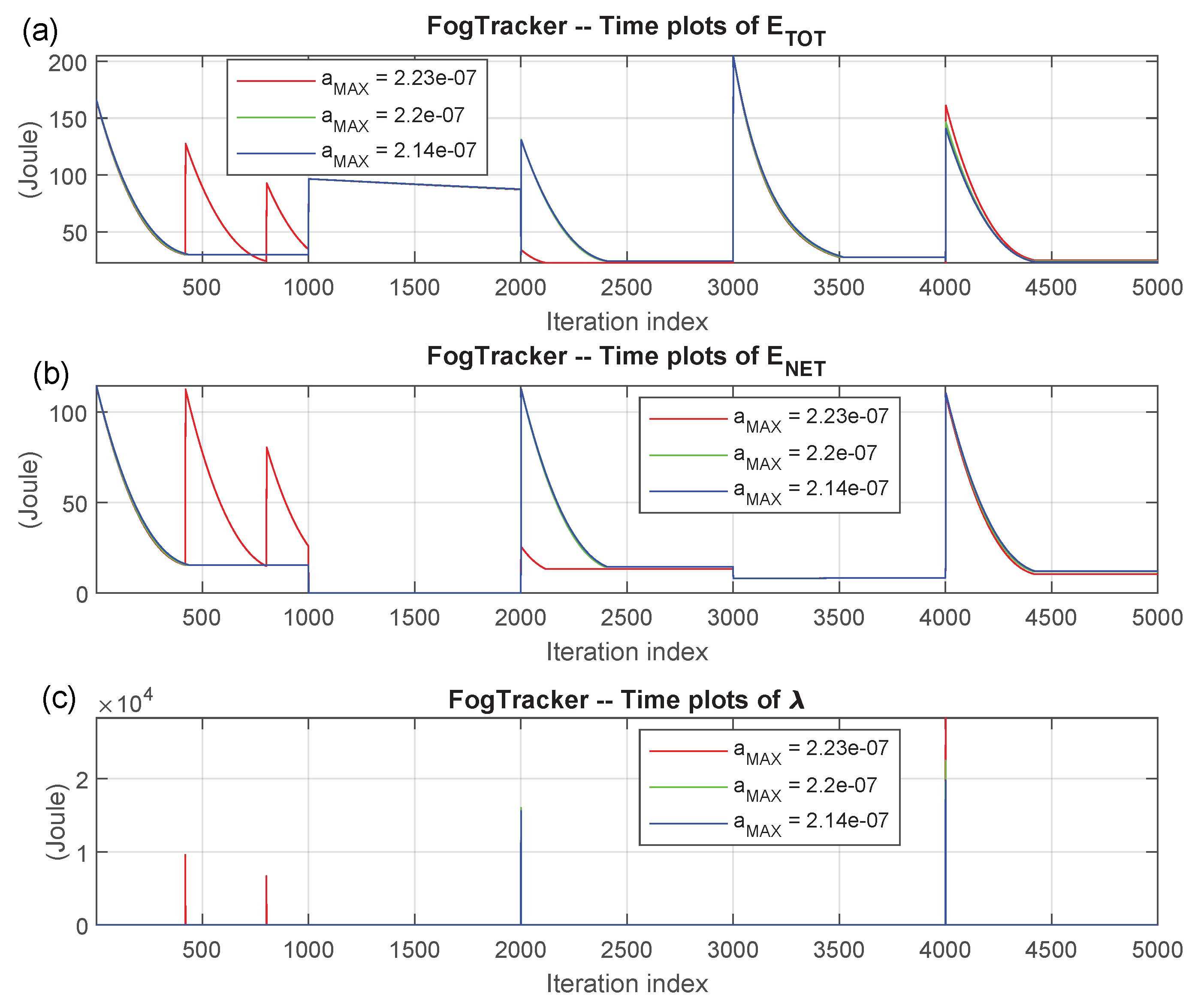
- optionally, calls the FogTracker function. It returns the time plots over the interval: of the:when abrupt changes in the pattern of the allocated tasks and/or maximum bandwidths of the WiFi/Cellular connections occur. The user may set the magnitude of these changes, in order to test various (possibly mobility induced) time-fluctuations of the simulated environment of Figure 1 (see Section 4.4 in the sequel for a full description of the FogTracker function and supported options).
- the numerical values of the up/down WiFi-Cellular-Backhaul bandwidths and Mobile-Fog-Cloud computing frequencies returned by the allocation policies GeneticTA_par, O_TAS_par, ES_S_par, OM_S, OF_S, and OC_S in the form of colored bar plots;
- the (generally different) task allocation patterns performed by GeneticTA_par, O_TAS_par, ES_S_par, OM_S, OF_S, and OC_S in the form of suitably-colored labeled graphs of the underlying application DAG (see Appendix A.2 in the sequel for a description of the main screen-shoots returned by the GUI of VirtFogSim).
- set 67 input parameters, in order to customize the desired computing and communication setup of the infrastructure of Figure 1;
- select any subset of the (aforementioned) GeneticTA_p, OM_S, OC_S, OF_S, O_TAS_ par, ES_S_par, and FogTracker functions, in order to test and compare various task and/or resource allocation strategies under the scenario dictated by the desired input parameters.
4.2. Supported Task Allocation Strategies and Adaptive Resource Allocation
- it performs task allocation by implementing (in a parallel way) a genetic algorithm. For this purpose, O_TAS_par calls the Crossover and Mutation functions over a randomly-generated population of -ternary task allocation vectors of size ;
- it evaluates the energy of each tested ternary allocation vector by computing the corresponding energies: , , , , , and under the static (e.g., not optimized) maximal resource allocation vector: (bit/s). For this purpose, O_TAS_par not longer calls the RAP_p function, but calls the evaluatestaticenergy_ p function.
- the V-tuple -ternary minimum-energy task allocation vector: , which is computed by applying the genetic algorithm run by O_TAS_par under ;
- the corresponding total energy: (Joule) and network energy: (Joule) consumed by under the (aforementioned) fixed maximal resource allocation vector .
- is the population size of the checked task allocation vectors;
- is the number of iterations (that is, the number of generations) run by the genetic algorithm implemented by ; and,
- is the number of available parallel cores that support the execution of VirtFogSim.
| Algorithm 1O_TAS_ par function. | ||
| function: . Output: ternary vector of the best task allocation under the fixed maximal resource allocation vector; scalar total energy (Joule) and network energy (Joule) consumed by under the fixed maximal allocation vector. | ||
| ▷Begin O_TAS_ par function | ||
| ▷Initialization phase | ||
| 1: | Randomly generate a list of task allocation vectors and store it into ; | |
| 2: | Compute and store into the column of the energy consumed by each by calling times the evaluatestaticenergy_p function; | |
| 3: | Sort the elements of for increasing values of their energies; | |
| 4: | Copy the first row of the sorted into , , and ; | |
| 5: | Set the number of the elements of for crossover at each generation; | |
| 6: | fordo | ▷Iterative phase |
| 7: | Perform the pair-wise crossover of the first Q elements of by calling times the Crossover function and store the Q crossover elements in ; | |
| 8: | Randomly mute positions of the last elements of by calling times the Mutation function and store the mutated elements into ; | |
| 9: | Compute and store the consumed energy of each element of and by calling times the function evaluatestaticenergy_p; | |
| 10: | Copy the first Q elements of and the overall and into ; | |
| 11: | Sort the elements of for increasing values of their energies; | |
| 12: | Copy the first elements of into ; | |
| 13: | if the total energy of the first element of is lower than then | |
| 14: | Copy the first row of into , and ; | |
| 15: | end if | |
| 16: | end for | |
| 17: | return. | ▷End O_TAS_ par function |
- is a -dimensional -ternary vector. It fixes the allocation to the Fog/Mobile/Cloud nodes of the V tasks that compose the considered application DAG. Specifically, , and 2 means that the application task is executed at the Fog clone, Mobile device, and Cloud clone, respectively;
- is a vector of real-valued non-negative scalars. It fixes the vector starting point of the primal-dual iterations to be performed. Its first seven components are measured in bit/s, while the starting Lagrange multiplier is measured in Joule.
- is a vector of real-valued non-negative scalars. It returns the vector of the optimal resource allocation attained by the performed primal-dual iterations. Its seven components are measured in bit/s;
- is the total communication-plus-computing energy consumed by the computed optimal resource allocation under the given task allocation x. is measured in Joule.
- is the overall network energy consumed by the computed optimal resource allocation under the given task allocation x. is measured in Joule;
- s, A and are respectively the global workload vector, adjacency matrix, and edge matrix of the underlying DAG;
- is the -dimensional vector of all other global variables used by for its execution.
- the V-tuple -ternary . It is the globally best task allocation vector, which is generated by performing the exhaustive search over the full population of the ternary task allocation vectors. The first and last components of each ternary task allocation vector are unit valued, i.e., the first and last tasks of the application DAG are executed, by design, at the Mobile device;
- the seven-tuple resource allocation vector: (bit/s), corresponding to the returned global task allocation vector ;
- the total communication-plus-computing energy (Joule), network energy (Joule), and bandwidth (bit/s) of the backhaul connection consumed under the returned searched global best task allocation vector .
| Algorithm 2ES_S_par function. | ||
| function: . Output: ternary vector of the best task allocation over the full population ; resource allocation vector: (bit/s) under ; total energy (Joule) and network energy (Joule) and backhaul bandwidth (bit/s) consumed by . | ||
| ▷Begin ES_S_par function | ||
| 1: | Call the find-allocation function, in order to generate the full set list: of ternary V-tuple candidate task allocation vectors, with the first and last elements set to the unit; | |
| 2: | Store (by row) into the first V columns of the matrix; | |
| 3: | fordo | |
| 4: | Compute the resource allocation vector and the total consumed energy of each by calling the RAP_p function, and store them (by row) into the last columns of the matrix; | |
| 5: | end for | |
| 6: | Sort the elements of the matrix for increasing values of their total energies; | |
| 7: | Store the first row of the sorted matrix into , , , and ; | |
| 8: | return. | ▷End ES_S_par function |
- the -ternary V-long vector of the best searched task allocation;
- the corresponding vector: (bit/s), of the optimal resource allocation computed by the RAP_p function under the best task allocation vector ;
- the total and network energies: , (Joule) that are consumed under the returned ;
- the actual transmission rate: (bit/s) of the two-way Fog ↔ Cloud backhaul connection.
- the best (that is, the minimum energy) task allocation vector ;
- the corresponding resource allocation vector ;
- the total consumed energy and the corresponding network energy computed up to the current generation.
4.3. Implemented Auxiliary Functions
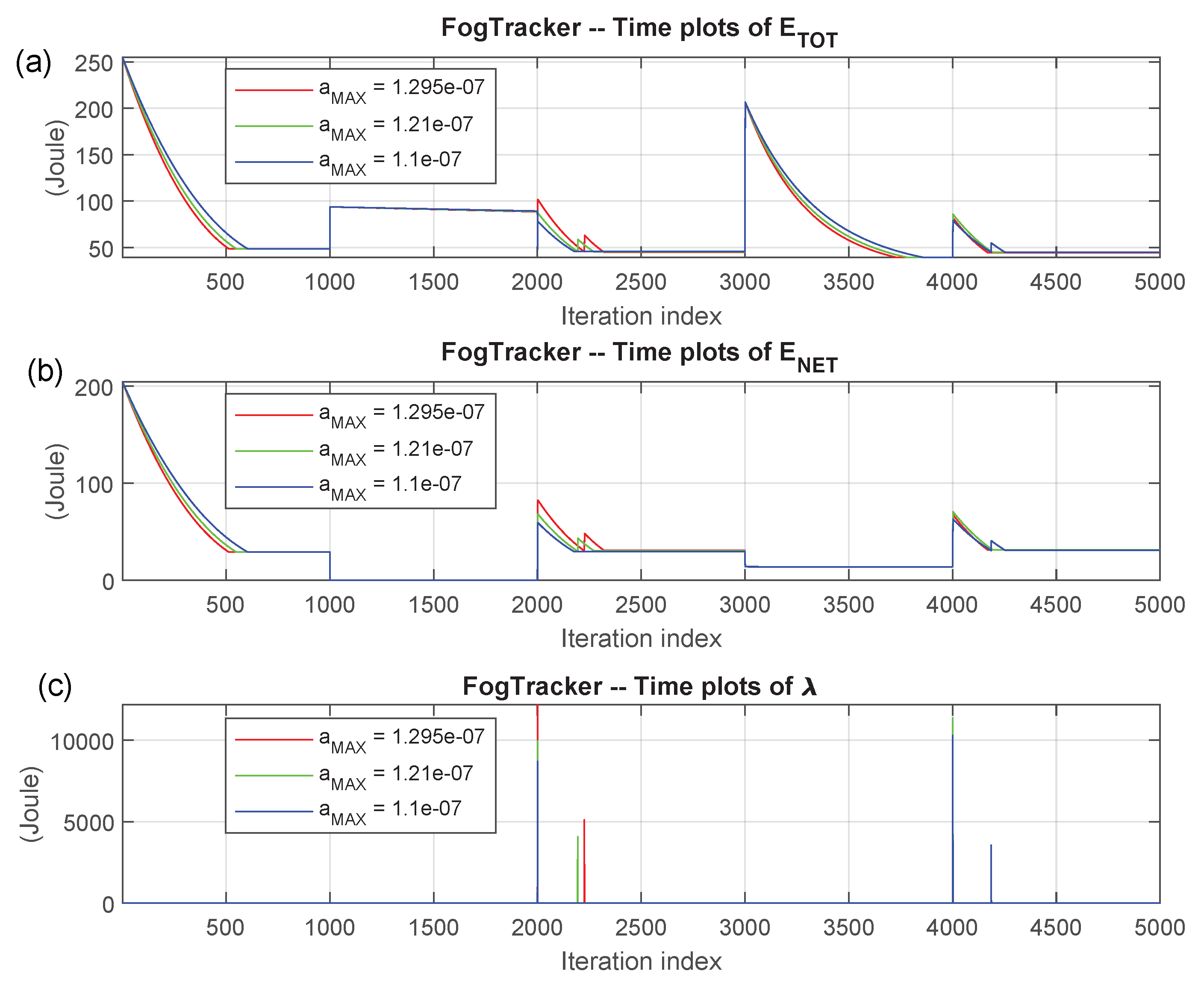
4.4. Dynamic Performance Tracking Function
- ;
- ;
- ;
- ,
- it begins to run the RAP_ p function over the time interval: , under the original settings of: , , , dictated by the main program VirtFogSim and the first input task allocation vector ;
- at the end of the iteration number: , the WiFi maximum bandwidths: and are multiplied by the (non-negative) scaling factor: , while the maximum cellular bandwidths: and are multiplied by the corresponding (possibly, coincident) scaling factor: . Furthermore, the task allocation vector is changed into . In so doing, both the maximum available bandwidths and the task allocation vector undergo abrupt (typically, user mobility induced) variations;
- the RAP_ p function runs over the time-interval:under the setting of Step 2. Its initial vector is the last returned vector of the RAP_p at the previous iteration: ;
- at the end of iteration number: , all four maximum bandwidths: , , , and are restored to their original values. Furthermore, even the task allocation vector is set back to its original value ;
- the RAP_ p function runs over the time interval:under the setting of Step 4. Its initial vector is the last returned vector of the RAP_ p at the previous iteration number: ;
- after the iteration number: , the WiFi maximum up/down bandwidths: , and are multiplied by the non-negative scaling factor , while the cellular maximum up/down bandwidths: and are multiplied by the scaling factor: . At the same time, even the task allocation vector is changed to the third value . In so doing, both the maximum available bandwidths and the task allocation vector undergo abrupt (typically, user mobility-induced) variations;
- the RAP_ p function runs over the time-interval:under the setting of Step 6. Its initial vector is the last returned vector of the at the previous iteration number: ;
- after the iteration number: , all four WiFi/CELLmaximum up/down bandwidths are restored to their original values. Furthermore, even the task allocation vector is set back to the first value ;
- finally, the RAP_ p function runs over the time-interval:under the setting of Step 8. Its initial vector is the last returned vector of the RAP_ p at the previous iteration number: .
5. VirtFogSim: Supported Formats of the Rendered Data
- the Tabular format. It is enabled by the print_solution graphic function;
- the Colored Bar Plot format. It is enabled by the plot_solution graphic function;
- the Colored Time Plot format. It is enabled by the plot_FogTracker graphic function;
- the Colored Labeled DAG Map format. It is enabled by the plot_ DAG graphic function.
- the Computing/Communication Ratio (CCR);
- the required minimum DAG execution throughput ();
- the per-core computing frequency at the Mobile device ();
- the per-core computing frequency at the Fog clone ();
- the per-core computing frequency at the Cloud clone ();
- the transport bit rate of the WiFi-based TCP/IP Mobile-to-Fog connection ();
- the transport bit rate of the WiFi-based TCP/IP Fog-to-Mobile connection ();
- the transport bit rate of the 3G/4G Cellular TCP/IP Mobile-to-Cloud connection ();
- the transport bit rate of the 3G/4G Cellular TCP/IP Cloud-to-Mobile connection ();
- the transport rate of the TCP/IP two-way Fog↔Cloud backhaul connection ();
- the total computing-plus-networking consumed energy ();
- the consumed computing energy ();
- the consumed networking energy ();
- the percent networking-to-total ratio of the consumed energies: .
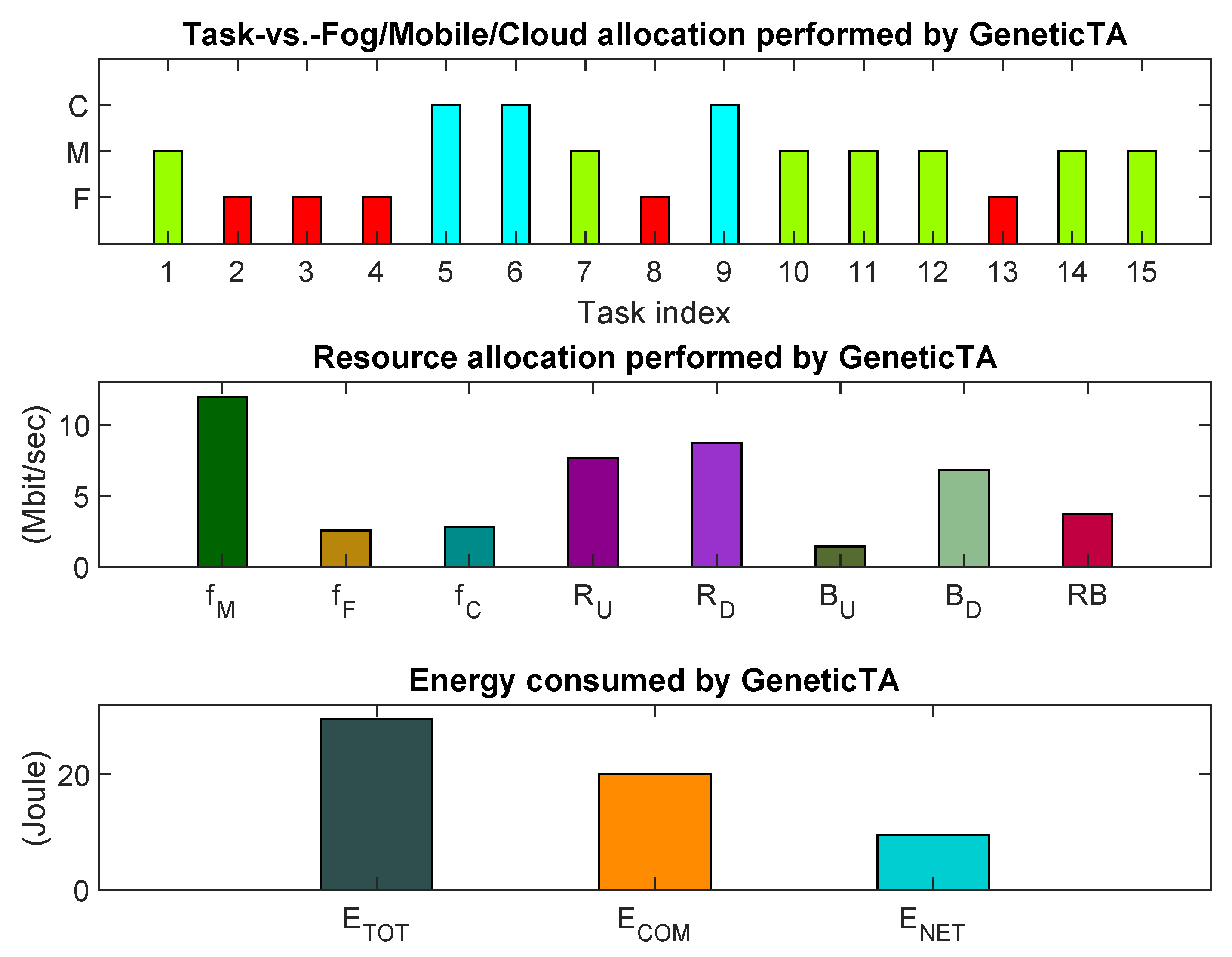
- the returned task allocation in the form of a three-color bar plot;
- the allocated computing frequencies and network bandwidths in the form of a plot with eight bars;
- the total, computing and networking consumed energies in the form of a plot with three bars.
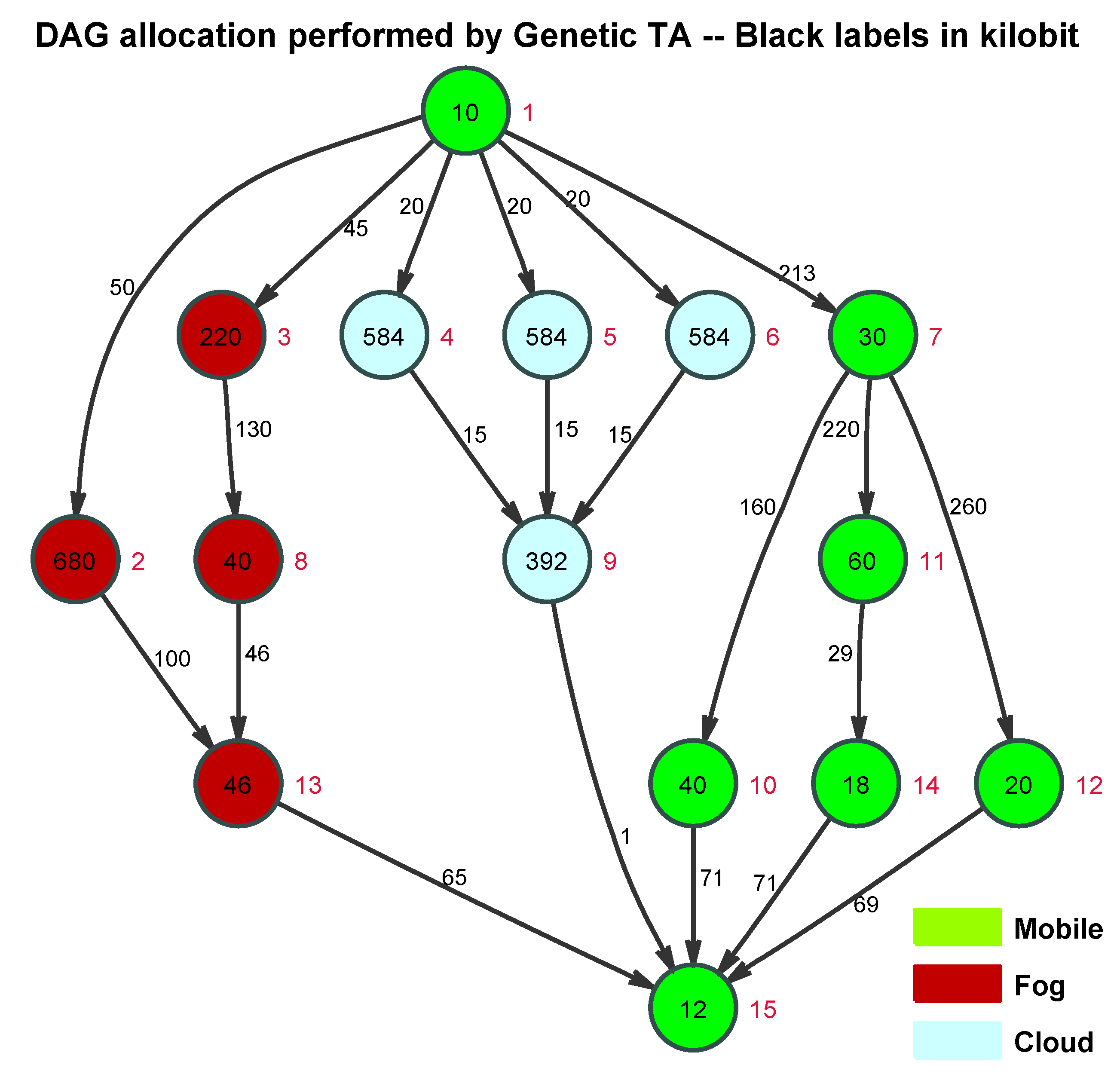
- all DAG nodes with the same color and unlabeled;
- all DAG nodes with the same color and labeled by increasing identification numbers;
- each DAG node is numbered and colored on the basis of the allocation actually stored by the input vector .
- all the workload values labeling the DAG nodes and edges are expressed in kilo-bit;
- red-colored tasks are understood to be allocated to the Fog node;
- green-colored tasks are understood to be allocated to the Mobile node; and,
- blue-colored tasks are understood to be allocated to the Cloud node.
- the total consumed computing-plus-networking energies under the three values of the step-size stored by ;
- the corresponding consumed networking energies;
- the related values of the lambda multiplier.
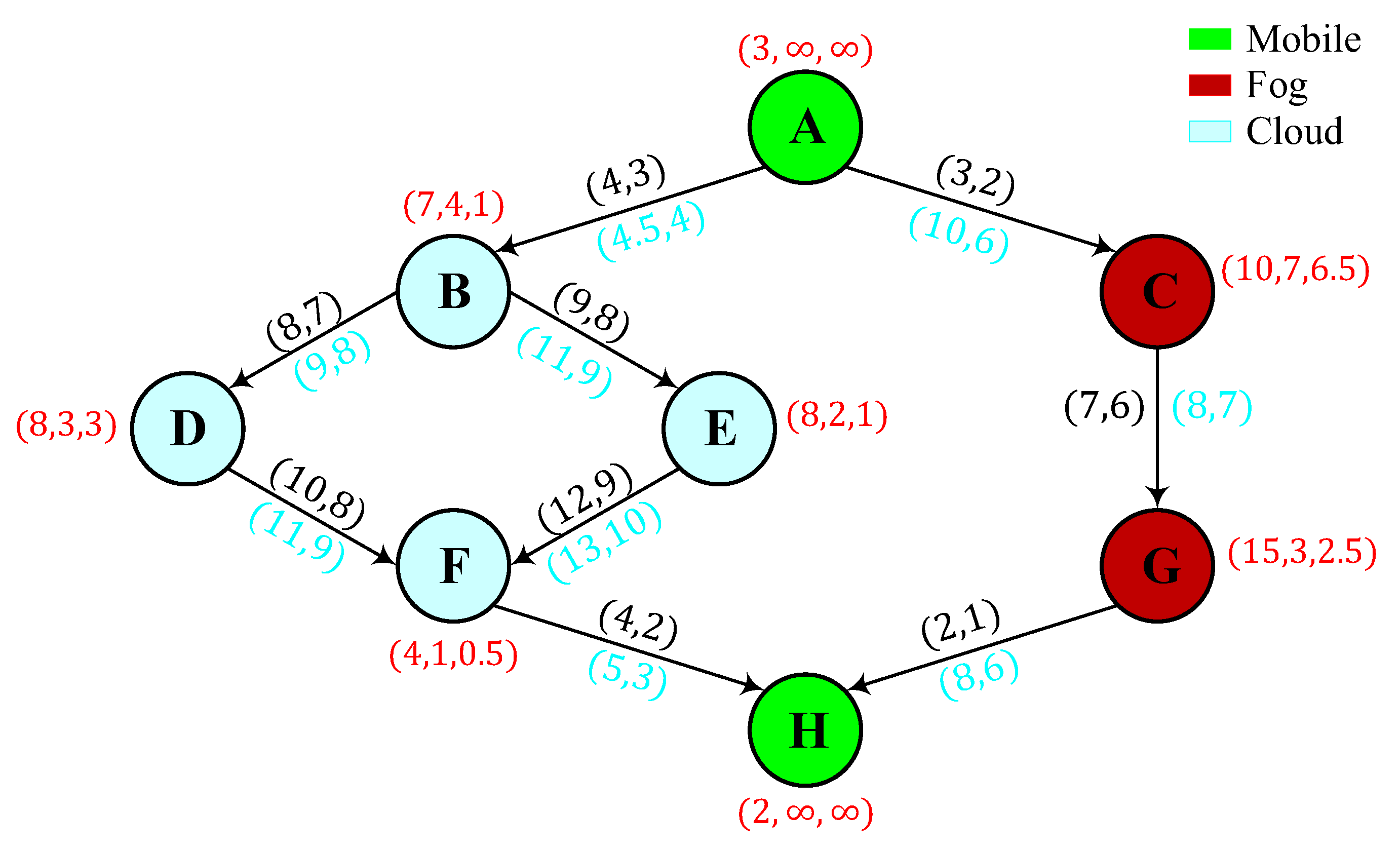
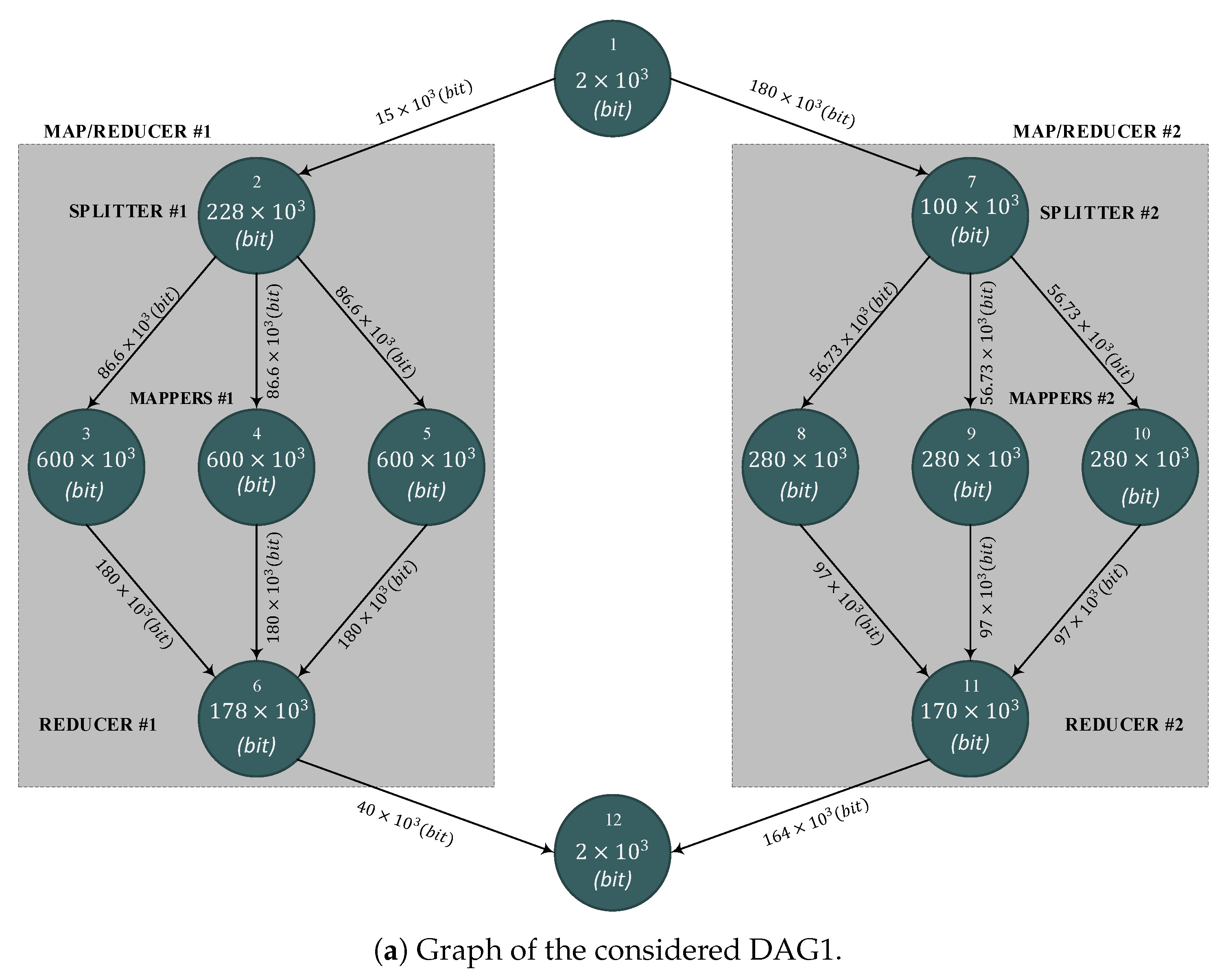
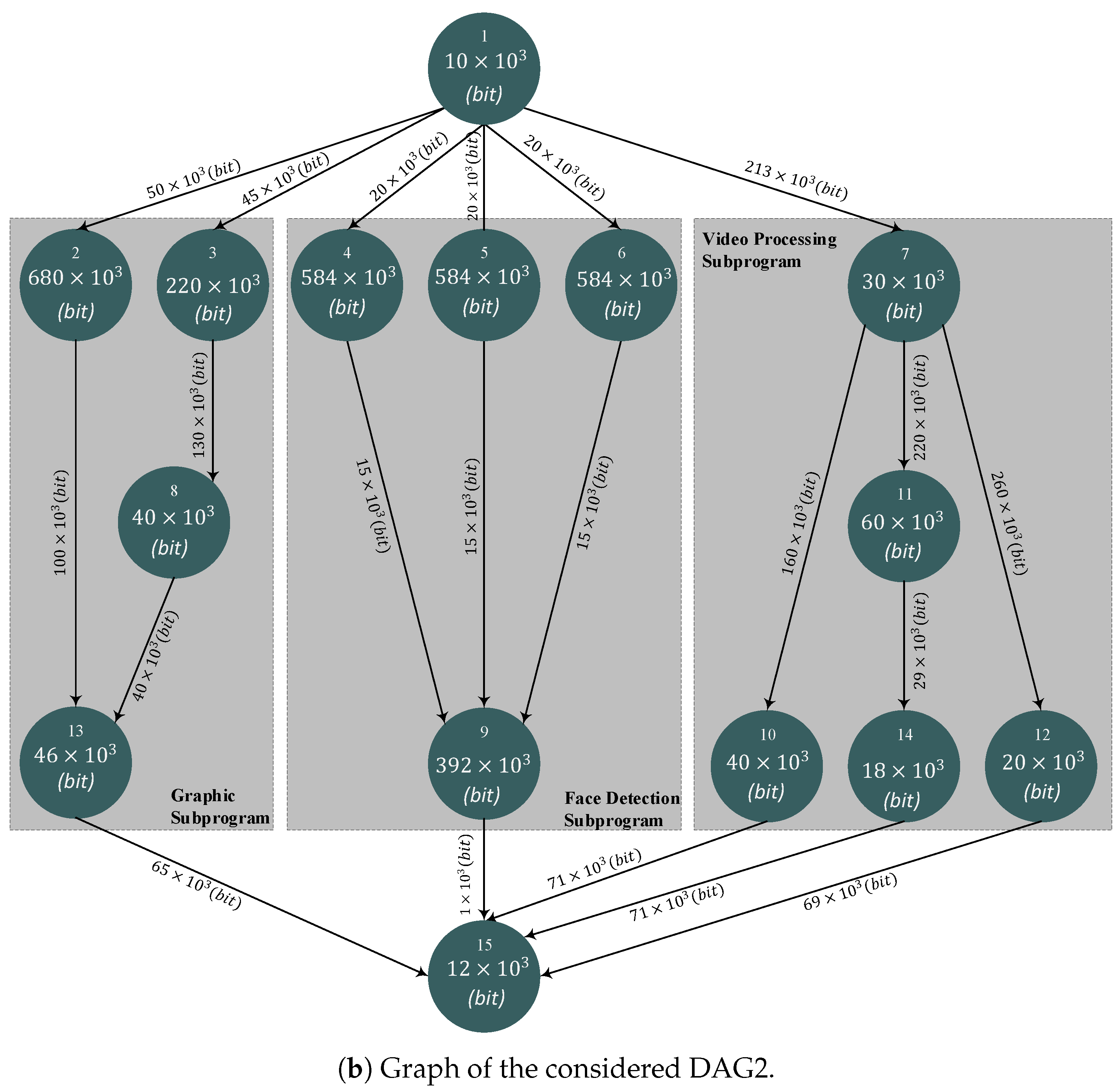
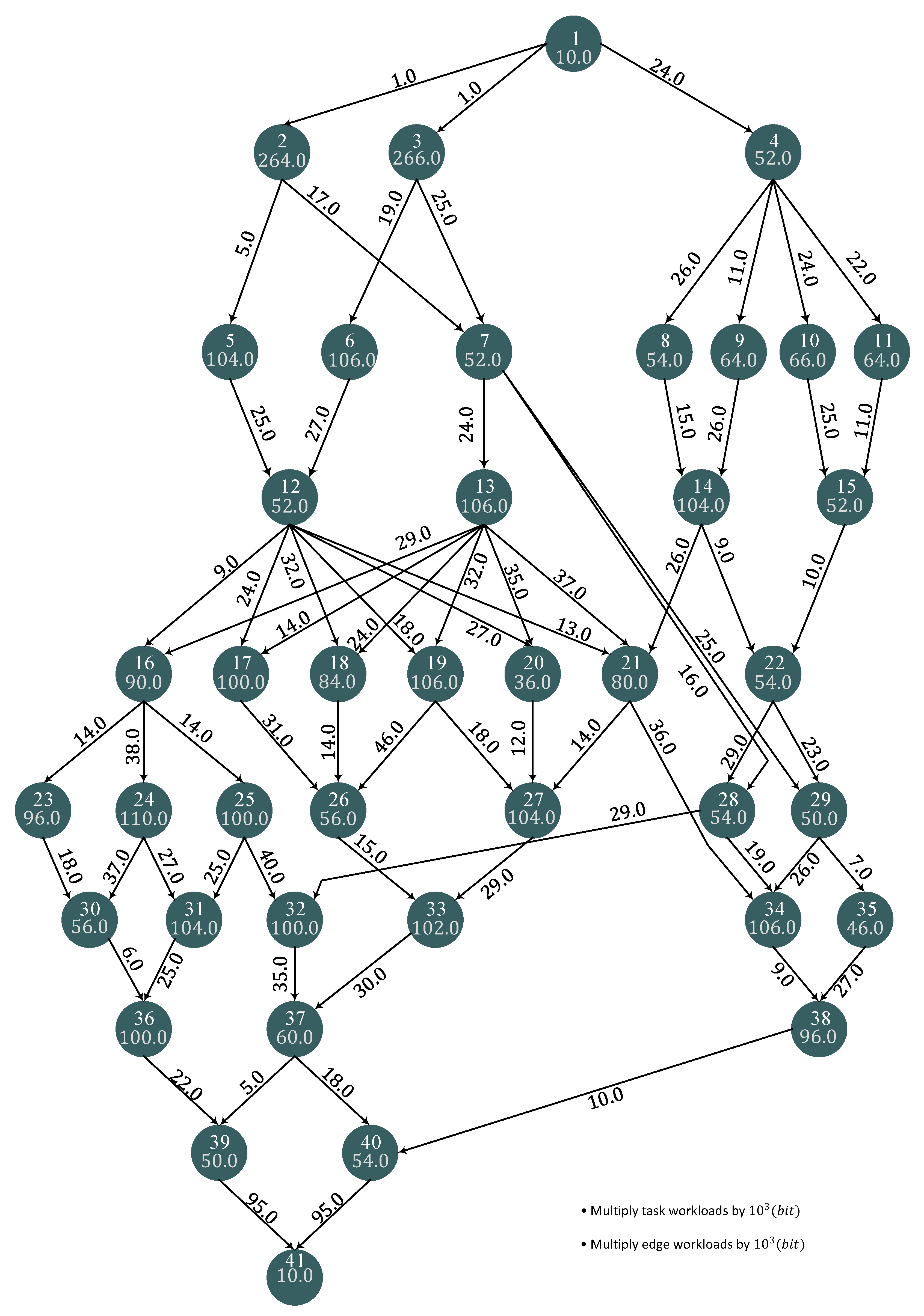
Pre-Loaded Application DAGs
6. VirtFogSim in Action: Testing Its Numerical Capabilities
6.1. Use Cases and Related DAGs
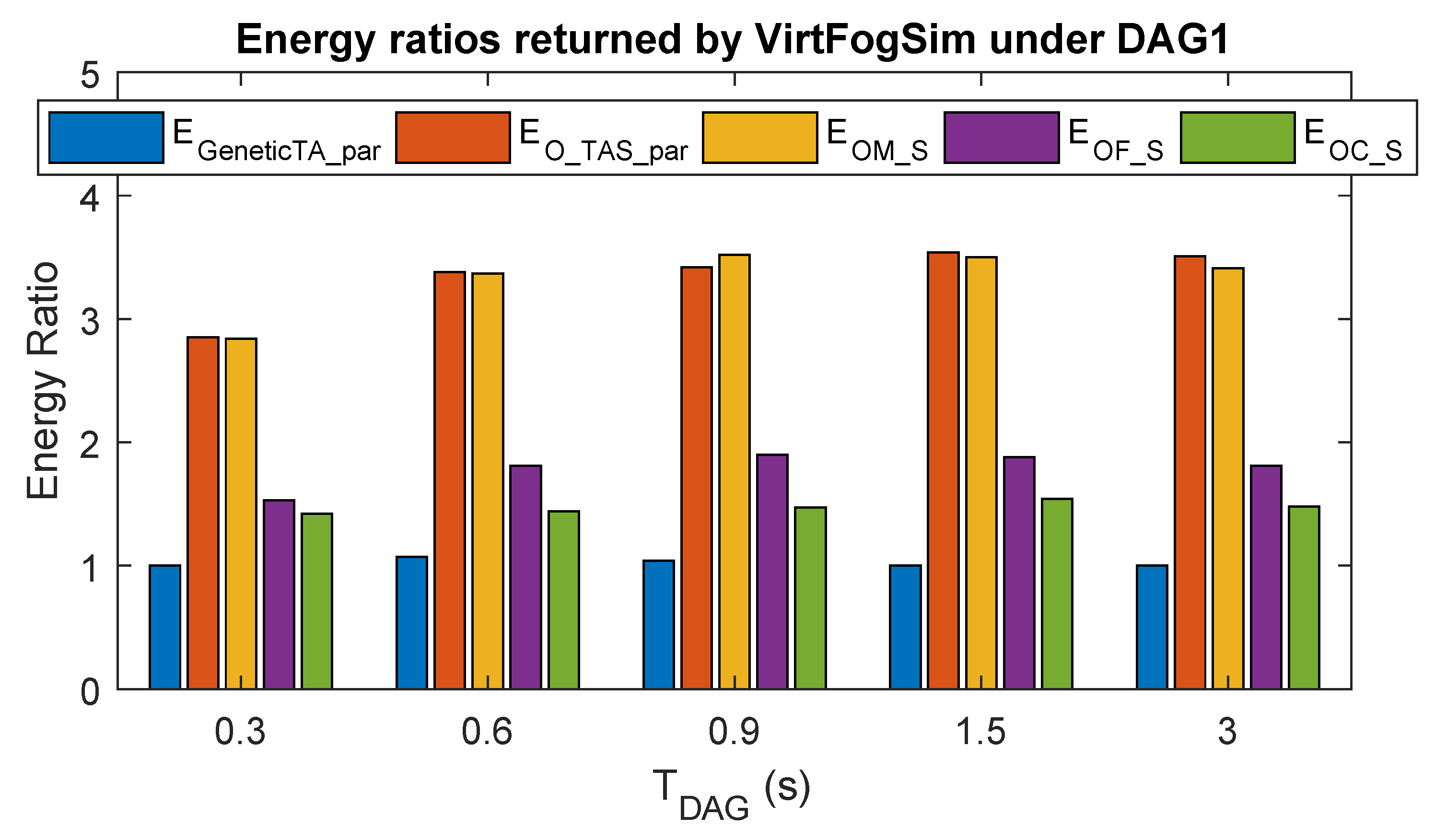
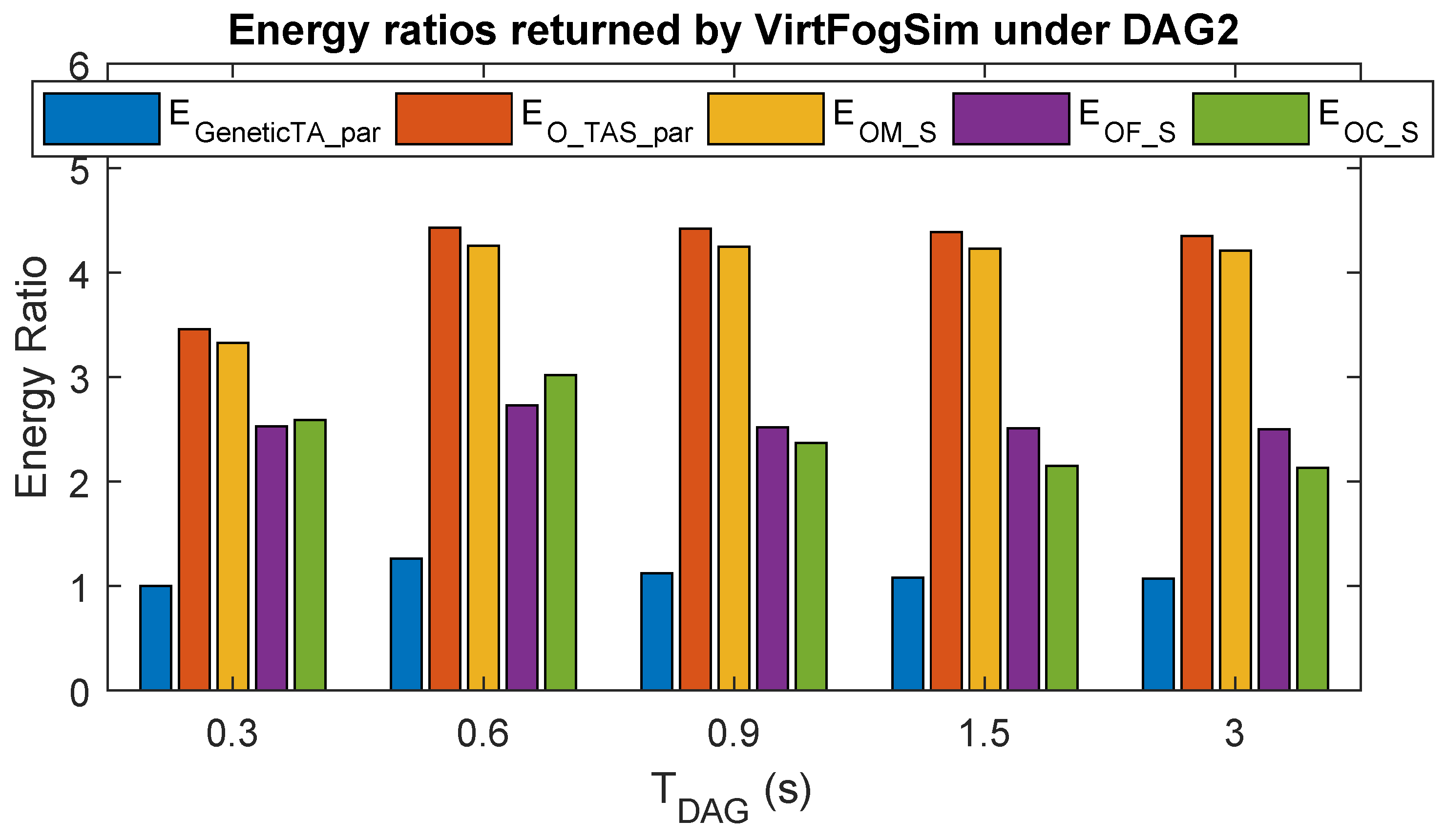
6.2. Comparative Tracking Performance under Intermittent WiFi Connectivity
6.3. Comparative Task and Resource Allocation Performance
6.4. The Performance Impact of Different Task and Resource Allocation Strategies
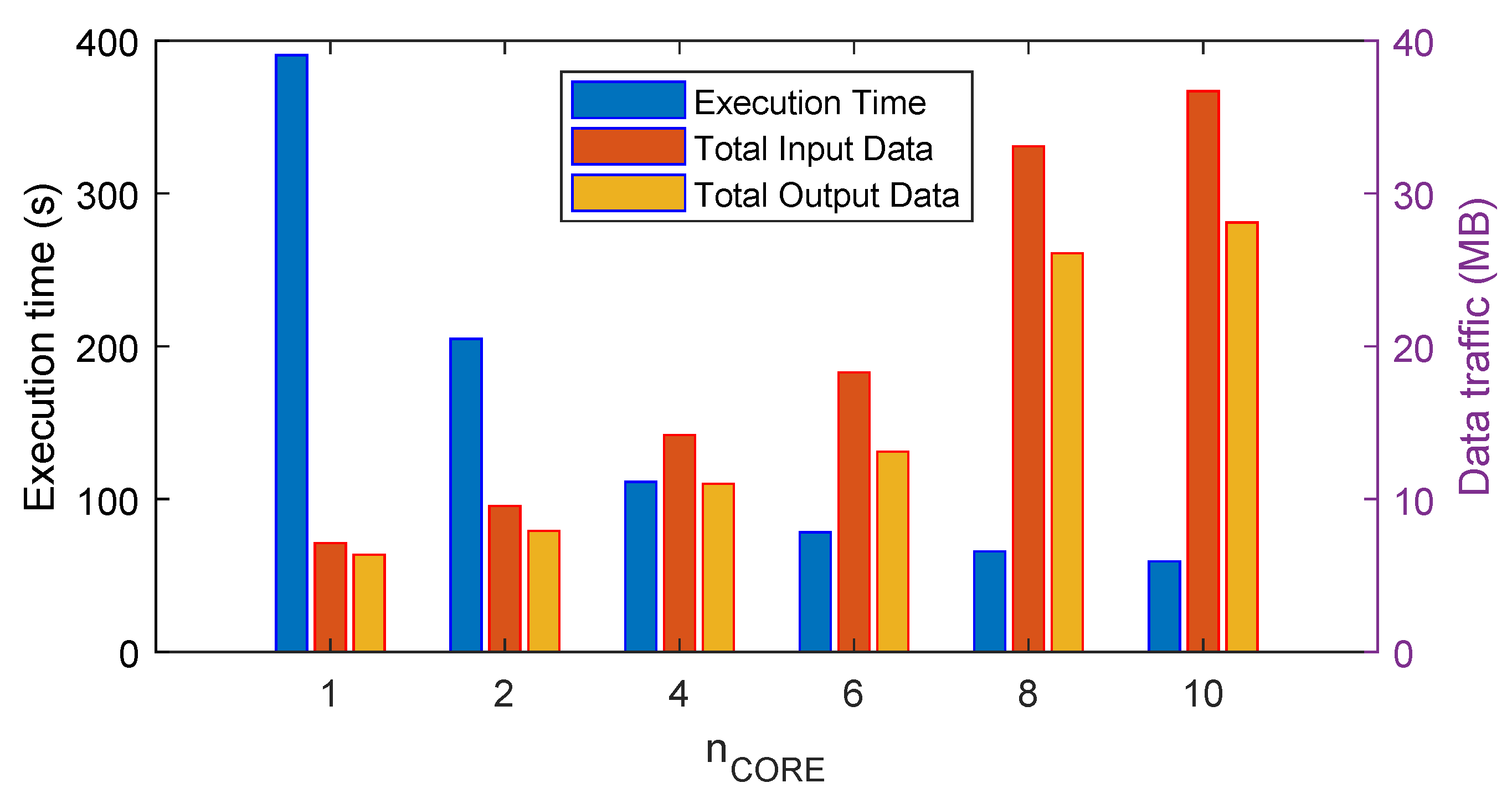
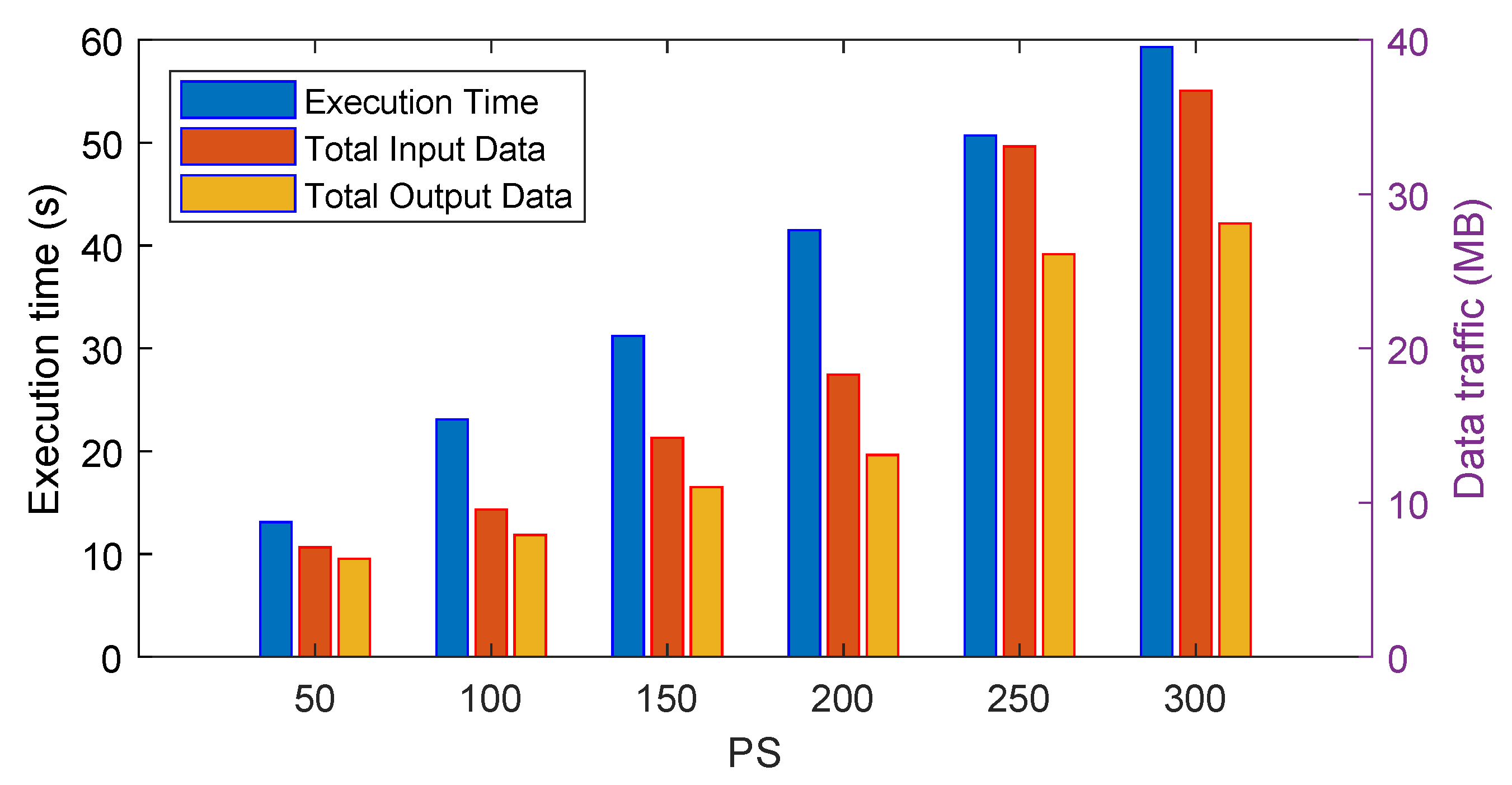
6.5. Scalability of the Simulation Time of the VirtFogSim Toolbox
7. Conclusions and Future Developments
8. Availability of the VirtFogSim Package
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| CC | Cloud Computing |
| CNT | Container |
| ES | Exhaustive Search |
| DAG | Direct Acyclic Graph |
| FC | Fog Computing |
| GUI | Graphical User Interface |
| LAN | Local Area Network |
| NIC | Network Interface Card |
| OC | Only Cloud |
| OF | Only Fog |
| OM | Only Mobile |
| OTA | Only Task Allocation |
| VM | Virtual Machine |
| WAN | Wide Area Network |
Appendix A. VirtFogSim: Supported Dual-Mode User Interfaces
- the VirtFogSim interface is oriented to a scientific use of the simulator. Its utilization requires some basics about the MATLAB environment. Hence, it may be appealing for skilled research users, who desire to work in an interactive way and are mainly interested in checking and optimizing the performance of their own customized DAGs under (possibly multiple) customized simulation setups;
- the VirtFogSimGUI interface provides a rich set of self-explanatory, ready-to-use native facilities that allow less (or even un-) skilled users to directly run the simulator under a number of pre-loaded (but, in any case, customizable) application scenarios. Hence, since its utilization does not require any specific skill regarding the MATLAB environment, it allows the user to interact with the simulator as a “black-box”. For this purpose: (i) the obtained numerical results are rendered in the form of graphics, colored maps, and plots, in order to make their interpretation and mining more intuitive; and (ii) an easy-to-consult on-line version of this User Guide is also enclosed.

Appendix A.1. The VirtFogSim Interface
- edit the desired DAG by setting the corresponding workload vector , adjacency matrix A, and edge weight matrix ;
- define the desired simulation setup by editing the input parameters listed in Table A2;
- select any subset of the supported optimization functions of Table 4;
- resort to the on-line help of MATLAB, in order to display information about any specific function supported by the VirtFogSim package; and,
- write and call user-defined customized functions that are not natively supported by the current version of the simulator.
Appendix A.2. The VirtFogSimGUI Interface
| Available GUI Functions | Associated Actions | |
|---|---|---|
| Help | Allows access to the User Guide of the simulator by opening a dedicated PDF file. | |
| Algorithm | Allows selecting any subset of the natively-supported optimization algorithms by clicking the corresponding labels. | |
| Archived DAG | Allows retrieving an already archived DAG with the corresponding simulation setup, in order to run it. | |
| Edit DAG | Allows editing a new DAG and/or a new simulation setup by compiling the list of input parameters of Table A2. | |
| Save DAG | Allows saving the last edit of DAG and assigning it an identification label. | |
| Run | Allows running the selected optimization algorithm under the retrieved/edit DAG and associated simulation setup. | |
| Close | Shuts down the current working session of the VirtFogSim simulator and closes all the figure windows. |
- enter VirtFogGUI at the MATLAB prompt, in order to open the GUI interface;
- click the Help button, in order to access the PDF version of the User Guide. This step is optional;
- select any desired subset of the supported optimization procedures by clicking the corresponding labels in the Algorithm window. This step is mandatory;
- retrieve an already stored DAG in format and the associated list of input parameters by accessing the Archived DAG. Alternatively, build a new DAG and set the desired input parameters of Table A by clicking the Edit DAG button. This step is mandatory;
- store in the Archived DAG database the last edit of DAG in format by clicking the Save DAG button. An identification label for the Save DAG is required. This step is optional;
- click the Run button, in order to start the execution of the selected algorithms under the (retrieved or edit) selected DAG. At the end of the execution, the attained results are returned in tabular form, and/or as colored time-plots, and/or as colored bar plots, and/or as colored DAG maps (see Section 5 for additional details about the graphic rendering capabilities and related options supported by the simulator);
- after finishing the current working session of the simulator, click the Close button, in order to shut down the VirtFogSimGUI interface.
Appendix B. Full List of the Input Parameters of VirtFogSim
| Parameter | Meaning/Role | Measuring Units | Simulated Settings |
|---|---|---|---|
| V | Number of tasks of the application DAG | Dimensionless | |
| V-tuple row vector of the task workloads | (bit) | Computing- and communi- cation-intensive DAG | |
| A | binary (i.e., ) DAG adjacency matrix | Dimensionless | |
| weight matrix of the (directed) edges of the DAG | (bit) | Computing- and communi- cation-intensive DAG | |
| Number of the (virtual) computing cores equipping the Mobile device | Dimensionless | ||
| Number of the (virtual) computing cores equipping the device clone at the Fog node | Dimensionless | ||
| Number of (virtual) computing cores equipping the device clone at the Cloud node | Dimensionless | ||
| Average per-connection number of failures of the one-way Mobile→Fog and Fog→Mobile WiFi TCP/IP connections | Dimensionless | ||
| Average per-connection number of failures of the cellular one-way Mobile→Cloud and Cloud→Mobile TCP/IP connections | Dimensionless | ||
| Average per-connection number of failures of the two-way Cloud↔Fog TCP/IP backhaul connection | Dimensionless | ||
| Per-core maximum computing frequency at the Mobile device | (bit/s) | ||
| Per-core maximum computing frequency at the Fog clone | (bit/s) | ||
| Per-core maximum computing frequency at the Cloud clone | (bit/s) | ||
| Maximum bit rate of the WiFi-based one-way Mobile→Fog TCP/IP connection | (bit/s) | ||
| Maximum bit rate of the WiFi-based one-way Fog→Mobile TCP/IP connection | (bit/s) | ||
| Maximum bit rate of the cellular one-way Mobile→Cloud TCP/IP connection | (bit/s) | ||
| Maximum bit rate of the cellular one-way Cloud→Mobile TCP/IP connection | (bit/s) | ||
| Scalar non-negative real parameter. It is the minimum required application throughput | (DAG/s) | ||
| Binary -parameter. It depends on the utilized application service model at the Mobile device | Dimensionless | (resp., ) if computing-plus-networking energy consumed by the Mobile device is (resp., is not) for free | |
| Binary -parameter. It depends on the utilized application service model at the Fog node | Dimensionless | (resp., ) if the computing-plus-networking energy consumed by the Fog clone is (resp., is not) for free | |
| Binary -parameter. It depends on the utilized application service model at the Cloud node | Dimensionless | (resp., ) if computing-plus-networking energy consumed by the Cloud clone is (resp., is not) for free | |
| Power consumed in the idle state by the physical CPU at the Mobile device | (Watt) | ||
| Power consumed by a single physical server in the idle state at the Fog node | (Watt) | ||
| Power consumed by a single physical server in the idle state at the Cloud node | (Watt) | ||
| Number of containers simultaneously running on the Mobile CPU | Dimensionless | ||
| Number of containers simultaneously running on a single physical server at the Fog node | Dimensionless | ||
| Number of containers simultaneously running on a single physical server at the Cloud node | Dimensionless | ||
| Positive exponent of the dynamic power consumption of the CPU at the Mobile device | Dimensionless | ||
| Positive exponent of the dynamic power consumption of a single physical server at the Fog node | Dimensionless | ||
| Positive exponent of the dynamic power consumption of a single physical server at the Cloud node | Dimensionless | ||
| Positive parameter. It profiles the dynamic power consumption of the CPU at the Mobile device | (Watt)/(bit/s) | ||
| Positive parameter. It profiles the dynamic power consumption of a single physical server at the Fog node | (Watt)/(bit/s) | ||
| Positive scalar parameter. It profiles the dynamic power consumption of a single physical server at the Cloud node | (Watt)/(bit/s) | ||
| Scalar fraction of the overall computing power shared by the computing cores at the Mobile device | Dimensionless | ||
| Scalar fraction of the overall computing power shared by the computing cores of a single physical server at the Fog node | Dimensionless | ||
| Scalar fraction of the overall computing power shared by the computing cores of a single physical server at the Cloud node | Dimensionless | ||
| Power consumed in the idle state by each physical Ethernet NIC at the Fog and Cloud nodes | (Watt) | ||
| Power consumed in the idle state by each physical WiFi NIC at the Mobile device and Fog node | (Watt) | ||
| Power consumed in the idle state by each physical cellular NIC at the Mobile device and Cloud node | (Watt) | ||
| Positive scalar exponent of the dynamic power consumption of the WiFi NIC in the transmit mode | Dimensionless | ||
| Positive scalar exponent of the dynamic power consumption of the WiFi NIC in the receive mode | Dimensionless | ||
| Positive scalar exponent of the dynamic power consumption of the cellular NIC in the transmit mode | Dimensionless | ||
| Positive exponent of the dynamic power consumption of the cellular NIC in the receive mode | Dimensionless | ||
| Positive exponent of the Round Trip Times (RTTs) of the TCP/IP WiFi and Cellular connections | Dimensionless | ||
| Average RTT of the TCP/IP WiFi up/down connections | (s) | ||
| Average RTT of the TCP/IP cellular up/down connections | (s) | ||
| Average RTT of the (possibly, multi-hop) two-way backhaul | (s) | ||
| Maximum size of a TCP segment | (bit) | Typically | |
| Loss probability of the Cloud↔Fog TCP/IP connection | Dimensionless | ||
| Power profile of the WiFi NIC in the transmit mode | |||
| Power profile of the WiFi NIC in the receive mode | |||
| Power profile of the cellular NIC in the transmit mode | |||
| Power profile of the cellular NIC in the receive mode | |||
| Maximum number of primal-dual iterations performed by the RAP_p function | Dimensionless | ||
| Speed-factor of the iterations performed by the RAP_p function | Dimensionless | ||
| Number of hops of the two-way Cloud↔Fog backhaul connection | Dimensionless | ||
| Per-hop average power consumed the two-way backhaul connection | (Watt) | ||
| Population size of the simulated genetic functions. It must be even and no less than 4 | Dimensionless | ||
| Fraction of the population size that undergoes genetic crossover | Dimensionless | ||
| Positive scalar integer parameter. It is the number of generations run by the genetic functions | Dimensionless | ||
| Number of elements of each task allocation vector that undergo genetic mutation | Dimensionless | ||
| 3-tuple vector of positive speed-factors of the gradient-based iterations performed by FogTracker | Dimensionless | Each element of the vector is in the range: | |
| Non-negative parameter. It is the first multiply scaling applied by FogTracker to and | Dimensionless | ||
| Non-negative parameter. It is the first multiply scaling applied by FogTracker to and | Dimensionless | ||
| Non-negative parameter. It is the second multiply scaling applied by FogTracker to and | Dimensionless | ||
| Non-negative parameter. It specifies the second multiply scaling applied by FogTracker to and | Dimensionless | ||
| Number of iterations performed by FogTracker (must be in multiples of 5) | Dimensionless |
References
- Khan, A.U.R.; Othman, M.; Madani, S.A.; Khan, S.U. A survey of mobile cloud computing application models. IEEE Commun. Surv. Tutor. 2014, 16, 393–413. [Google Scholar] [CrossRef]
- Gupta, A.; Jha, R.K. A survey of 5G network: Architecture and emerging technologies. IEEE Access 2015, 3, 1206–1232. [Google Scholar] [CrossRef]
- Baccarelli, E.; Vinueza Naranjo, P.G.; Scarpiniti, M.; Shojafar, M.; Abawajy, J.H. Fog of Everything: Energy-efficient Networked Computing Architectures, Research Challenges, and a Case Study. IEEE Access 2017, 5, 9882–9910. [Google Scholar] [CrossRef]
- Checko, A.; Christiansen, H.L.; Yan, Y.; Scolari, L.; Kardaras, G.; Berger, M.S.; Dittmann, L. Cloud RAN for mobile networks: A technology overview. IEEE Commun. Surv. Tutor. 2015, 17, 405–426. [Google Scholar] [CrossRef]
- Baccarelli, E.; Biagi, M.; Bruno, R.; Conti, M.; Gregori, E. Broadband Wireless Access Networks: A Roadmap on Emerging Trends and Standards. In Broadband Services: Business Models and Technologies for Community Networks; Wiley Online Library: Hoboken, NJ, USA, 2005; Chapter 14; pp. 215–240. [Google Scholar] [CrossRef]
- Baccarelli, E.; Scarpiniti, M.; Momenzadeh, A. Fog-Supported Delay-Constrained Energy-Saving Live Migration of VMs Over MultiPath TCP/IP 5G Connections. IEEE Access 2018, 6, 42327–42354. [Google Scholar] [CrossRef]
- Pahl, C.; Brogi, A.; Soldani, J.; Jamshidi, P. Cloud container technologies: A state-of-the-art review. IEEE Trans. Cloud Comput. 2017. [Google Scholar] [CrossRef]
- Calheiros, R.N.; Ranjan, R.; Beloglazov, A.; De Rose, C.A.; Buyya, R. CloudSim: A toolkit for modeling and simulation of cloud computing environments and evaluation of resource provisioning algorithms. Softw. Pract. Exp. 2011, 41, 23–50. [Google Scholar] [CrossRef]
- Kliazovich, D.; Bouvry, P.; Audzevich, Y.; Khan, S.U. GreenCloud: A packet-level simulator of energy-aware cloud computing data centers. In Proceedings of the 2010 IEEE Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010. [Google Scholar] [CrossRef]
- Núñez, A.; Vázquez-Poletti, J.L.; Camineiro, A.C.; Castañé, G.G.; Carretero, J.; Llorente, I.M. iCanCloud: A flexible and scalable cloud infrastructure simulator. J. Grid Comput. 2012, 10, 185–209. [Google Scholar] [CrossRef]
- Sotiriadis, S.; Bessis, N.; Asimakopoulos, E.; Mustafee, N. Towards simulating the Internet of Things. In Proceedings of the 28th International Conference on Advanced Information Networking and Application Workshops, Victoria, BC, Canada, 13–16 May 2014. [Google Scholar] [CrossRef]
- Zeng, X.; Garg, S.K.; Strazdnis, P.; Jayaraman, P.; Georgakopoulos, D.; Ranjan, R. IOTSim: A simulator for analysing IoT applications. J. Syst. Archit. 2017, 72, 93–107. [Google Scholar] [CrossRef]
- Gupta, H.; Dastjerdi, A.V.; Ghosh, S.K.; Buyya, R. iFogSim: A toolkit for modeling and simulation of resource management techniques in the Internet of Things, Edge and Fog computing environments. Softw. Pract. Exp. 2017, 47, 1275–1296. [Google Scholar] [CrossRef]
- Sotiriadis, S.; Bessis, N.; Antonopoulos, N.; Anjum, A. SimIC: Designing a new inter-cloud simulation platform for integrating large-scale resource management. In Proceedings of the 27th IEEEE International Conference on Advanced Information Networking and Applications (ANIA 2013), Barcelona, Spain, 25–28 March 2013. [Google Scholar] [CrossRef]
- Sonmez, C.; Ozgovde, A.; Ersoy, C. EdgeCloudSim: An environment for performance evaluation of Edge Computing systems. Trans. Emerg. Telecommun. Technol. 2018, 29, e3493. [Google Scholar] [CrossRef]
- Padhye, J.; Firoiu, V.; Towsley, D.; Kurose, J. Modeling TCP throughput: A simple model and its empirical validation. In Proceedings of the ACM SIGCOMM ’98 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Vancouver, BC, Canada, 31 August–4 September 1998; ACM: New York, NY, USA, 1998; pp. 303–314. [Google Scholar] [CrossRef]
- Vallina-Rodriguez, N.; Crowcroft, J. Energy management techniques in modern mobile handsets. IEEE Commun. Surv. Tutor. 2013, 15, 179–198. [Google Scholar] [CrossRef]
- Altamimi, M.; Abdrabou, A.; Naik, K.; Nayak, A. Energy cost models of smartphones for task offloading to the cloud. IEEE Trans. Emerg. Top. Comput. 2015, 3, 384–398. [Google Scholar] [CrossRef]
- Kwak, J.; Choi, O.; Chong, S.; Mohapatra, P. Processor-network speed scaling for energy: Delay tradeoff in smartphone applications. IEEE/ACM Trans. Netw. 2016, 24, 1647–1660. [Google Scholar] [CrossRef]
- Zhang, L.; Tiwana, B.; Qian, Z.; Wang, Z.; Dick, R.P.; Mao, Z.M.; Yang, L. Accurate online power estimation and automatic battery behavior based power model generation for smartphones. In Proceedings of the 2010 IEEE/ACM/IFIP International Conference on Hardware/Software Codesign and System Synthesis (CODES+ISSS), Scottsdale, AZ, USA, 24–29 October 2010; pp. 105–114. [Google Scholar]
- Huang, J.; Qian, F.; Gerber, A.; Mao, Z.M.; Sen, S.; Spatscheck, O. A close examination of performance and power characteristics of 4G LTE networks. In Proceedings of the 10-th International Conference on Mobile Systems, Applications, and Services, Lake District, UK, 25–29 June 2010; ACM: New York, NY, USA, 2012; pp. 225–238. [Google Scholar] [CrossRef]
- Xiao, Y.; Cui, Y.; Savolainen, P.; Siekkinen, M.; Wang, A.; Yang, L.; Ylä-Jääski, A.; Tarkoma, S. Modeling energy consumption of data transmission over Wi-Fi. IEEE Trans. Mob. Comput. 2014, 13, 1760–1773. [Google Scholar] [CrossRef]
- Lim, Y.s.; Chen, Y.C.; Nahum, E.M.; Towsley, D.; Gibbens, R.J. Improving energy efficiency of MPTCP for mobile devices. arXiv, 2014; arXiv:1406.4463. [Google Scholar]
- Mukherjee, A.; De, D.; Roy, D.G. A power and latency aware cloudlet selection strategy for multi-cloudlet environment. IEEE Transa. Cloud Comput. 2016, 7, 141–154. [Google Scholar] [CrossRef]
- Yang, S.; Kwon, D.; Yi, H.; Cho, Y.; Kwon, Y.; Paek, Y. Techniques to minimize state transfer costs for dynamic execution offloading in mobile cloud computing. IEEE Trans. Mob. Comput. 2014, 13, 2648–2660. [Google Scholar] [CrossRef]
- Yang, L.; Cao, J.; Yuan, Y.; Li, T.; Han, A.; Chan, A. A framework for partitioning and execution of data stream applications in mobile cloud computing. ACM SIGMETRICS Perform. Eval. Rev. 2013, 40, 23–32. [Google Scholar] [CrossRef]
- De Maio, V.; Brandic, I. First hop mobile offloading of dag computations. In Proceedings of the 18th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID 2018), Washington, DC, USA, 1–4 May2018; pp. 83–92. [Google Scholar] [CrossRef]
- Peng, Q.; Walid, A.; Hwang, J.; Low, S.H. Multipath TCP: Analysis, design, and implementation. IEEE/ACM Trans. Netw. 2016, 24, 596–609. [Google Scholar] [CrossRef]
- Topcuoglu, H.; Hariri, S.; Wu, M.Y. Performance-effective and low-complexity task scheduling for heterogeneous computing. IEEE Trans. Parallel Distrib. Syst. 2002, 13, 260–274. [Google Scholar] [CrossRef]
- Cuervo, E.; Balasubramanian, A.; Cho, D.K.; Wolman, A.; Saroiu, S.; Chandra, R.; Bahl, P. MAUI: Making smartphones last longer with code offload. In Proceedings of the 8th International Conference on Mobile Systems, Applications, and Services, San Francisco, CA, USA, 5–18 June 2010; ACM: New York, NY, USA, 2010; pp. 49–62. [Google Scholar] [CrossRef]
- Ra, M.R.; Sheth, A.; Mummert, L.; Pillai, P.; Wetherall, D.; Govindan, R. Odessa: Enabling interactive perception applications on mobile devices. In Proceedings of the 9-th International Conference on Mobile Systems, Applications, and Services, Bethesda, MD, USA, 28 June–1 July 2011; ACM: New York, NY, USA, 2011; pp. 43–56. [Google Scholar] [CrossRef]
- Juve, G.; Chervenak, A.; Deelman, E.; Bharathi, S.; Mehta, G.; Vahi, K. Characterizing and profiling scientific workflows. Future Gener. Comput. Syst. 2013, 29, 682–692. [Google Scholar] [CrossRef]
- Mahmoodi, S.E.; Uma, R.; Subbalakshmi, K. Optimal joint scheduling and cloud offloading for mobile applications. IEEE Trans. Cloud Comput. 2016. [Google Scholar] [CrossRef]
- Sarkar, A.; Gosh, A.; Nath, A. MapReduce: A comprehensive study on applications, scope and challenges. Int. J. Adv. Res. Comput. Sci. Manag. Stud. 2015, 3, 256–272. [Google Scholar]
- Baccarelli, E.; Biagi, M. Performance and optimized design of space-time codes for MIMO wireless systems with imperfect channel estimates. IEEE Trans. Signal Process. 2004, 52, 2911–2923. [Google Scholar] [CrossRef]
- Baccarelli, E.; Biagi, M.; Pelizzoni, C. On the information throughput and optimized power allocation for MIMO wireless systems with imperfect channel estimation. IEEE Trans. Signal Process. 2005, 53, 2335–2347. [Google Scholar] [CrossRef]
- Baccarelli, E.; Biagi, M. Power-allocation policy and optimized design of multiple-antenna systems with imperfect channel estimation. IEEE Trans. Veh. Technol. 2004, 53, 136–145. [Google Scholar] [CrossRef]
- Baccarelli, E.; Cusani, R. Recursive Kalman-type optimal estimation and detection of hidden Markov chains. Signal Process. 1996, 51, 55–64. [Google Scholar] [CrossRef]
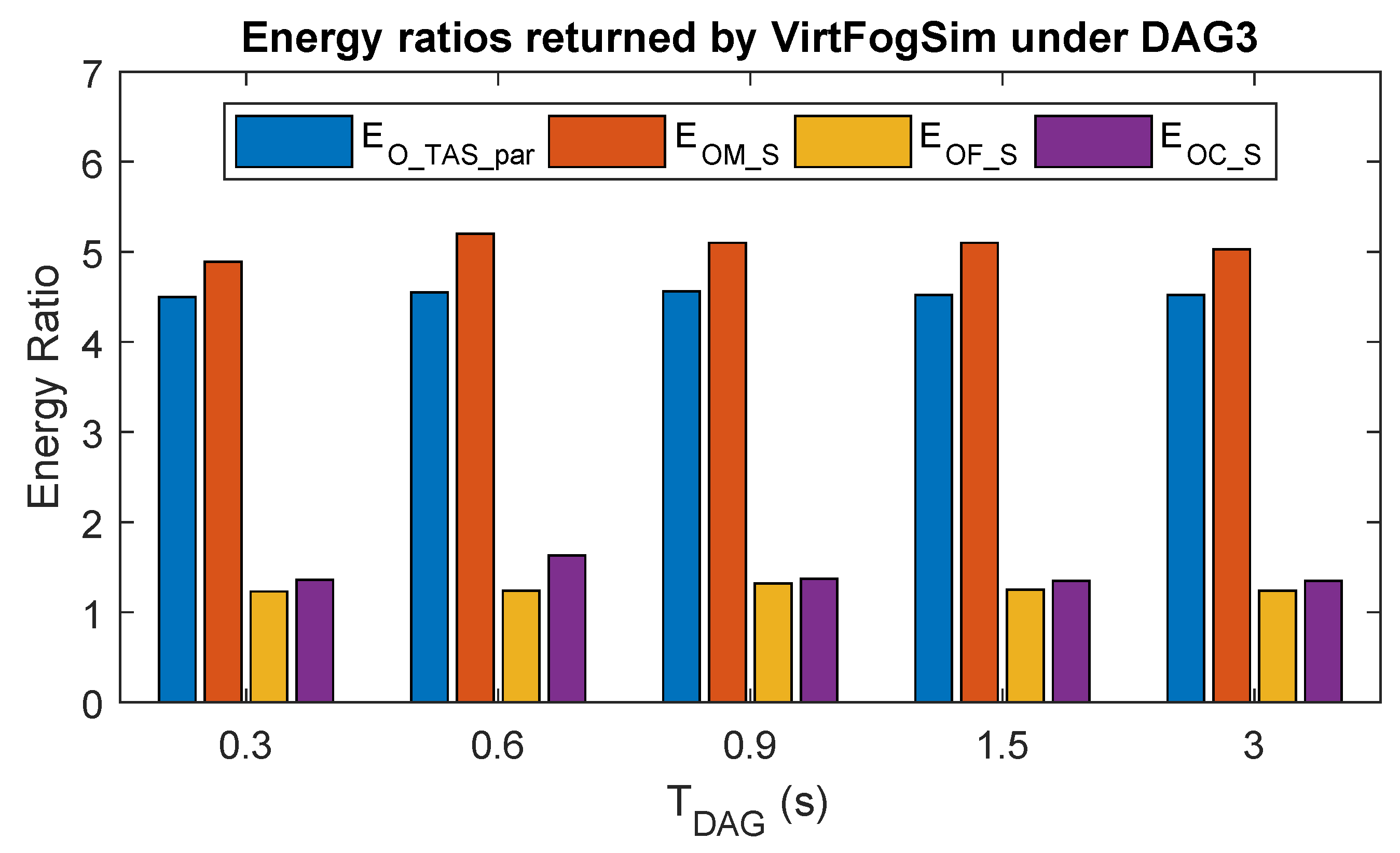
| FOG | CLOUD | 5G | |||
|---|---|---|---|---|---|
| Distributed deployment and low-access latency | Fog nodes are expected to undergo a pervasive deployment. This reduces the access distance and, then, the resulting propagation delay | Centralized deployment and high-access latency | Cloud data centers typically serve large spatial areas and, then, incur high propagation delays | Real-time support for heterogeneous network technologies | A number of ultra-short-/short-/long- range UWB/WiFi/ 3G-4G Cellular network technologies are simultaneously supported and dynamically turned ON-OFF |
| Low-density resource virtualization | Clones of the served mobile devices may be allocated onto medium-/small-sized Fog servers in real time. In order to reduce the resulting bootstrapping delays, light low-density virtualization technologies are employed | High-density resource virtualization | Clones of the served devices are quasi-statically deployed by resorting to high-density virtualization of the computing resources of large servers | Dynamic provisioning, multiplexing, and isolation of the wireless bandwidth | Wireless bandwidth is dynamically provided on-demand to the requiring Mobile devices. Dynamic multiplexing is used, in order to provide inter-device isolation and per-device bandwidth guarantee. |
| Support for light delay-sensitive Mobile applications | Fog nodes may exploit low-latency WiFi links, in order to enable seamless light data/code offloading from Mobile devices | Support for computing-intensive delay-tolerant applications | By exploiting the their huge computing resources, Cloud data centers may support computing-intensive delay-tolerant applications offloaded by remote devices | Bandwidth pooling | The simultaneous utilization of multiple transmission technologies allows increasing the total available wireless bandwidth |
| Energy efficient | Resource-limited Mobile devices may save energy by exploiting nearby Fog nodes as computing clones | Energy hungry | Both network and server infrastructures hosted by Cloud data centers are resource-rich, but energy hungry | Ultra-low access latency | Sub-millisecond access delays are achieved by the synergic exploitation of multiple network technologies |
| Function | Description |
|---|---|
| It implements the Resource Allocation Problem described in Equation (4). | |
| It tests the convergence rate to the steady-state and the steady-state stability of the primal-dual iterations performed by the RAP_p function when abrupt changes happen. | |
| It runs the parallel Genetic Task Allocation strategy. | |
| It runs the Only Mobile strategy. | |
| It runs the Only Fog strategy. | |
| It runs the Only Cloud strategy. | |
| It runs the Only Task Allocation strategy. | |
| It runs the Exhaustive Search strategy. |
| Function | Description |
|---|---|
| It implements the Crossover operation. | |
| It implements the Mutation operation. | |
| It evaluates the static energy evaluation in O_TAS. | |
| It returns all the patterns of N numbers that can assume the first K integer values: . |
| Function | Asymptotic Computational Complexity |
|---|---|
| GeneticTA_par | |
| OM_S | |
| OF_S | |
| OC_S | |
| O_TAS_par | |
| ES_S | |
| FogTracker |
| Function | Description |
|---|---|
| It implements the tabular format. | |
| It implements the colored bar plot format. | |
| It implements the colored labeled DAG map. | |
| It implements the colored time plot format. |
| Mobile Tasks | Fog Tasks | Cloud Tasks | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0.3 | 11.81 | 3.00 | 2.50 | 7.42 | 8.25 | 3.96 | 1.16 | 0.0 | 31.81 | 16.72 | |||
| 0.6 | 11.75 | 2.38 | 2.47 | 6.97 | 7.61 | 2.31 | 0.95 | 0.0 | 28.76 | 13.70 | |||
| 0.9 | 11.60 | 0.00 | 2.00 | 0.00 | 0.00 | 0.75 | 0.76 | 0.0 | 27.59 | 11.38 | |||
| 1.5 | 11.50 | 1.82 | 0.00 | 6.75 | 7.15 | 0.00 | 0.00 | 0.0 | 26.11 | 9.48 | |||
| 3.0 | 11.35 | 1.79 | 0.00 | 6.72 | 7.10 | 0.00 | 0.00 | 0.0 | 25.75 | 9.45 |
| Mobile Tasks | Fog Tasks | Cloud Tasks | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0.3 | 11.90 | 2.47 | 2.48 | 7.50 | 8.51 | 0.95 | 6.64 | 0.0 | 27.09 | 8.45 | |||
| 0.6 | 11.80 | 2.35 | 2.37 | 7.35 | 8.39 | 0.93 | 6.52 | 0.0 | 26.78 | 8.35 | |||
| 0.9 | 11.68 | 1.83 | 0.00 | 6.85 | 8.21 | 0.00 | 0.00 | 0.0 | 23.63 | 7.33 | |||
| 1.5 | 11.58 | 1.73 | 0.00 | 6.65 | 8.11 | 0.00 | 0.00 | 0.0 | 22.81 | 7.30 | |||
| 3.0 | 10.98 | 1.64 | 0.00 | 6.55 | 8.01 | 0.00 | 0.00 | 0.0 | 22.50 | 7.22 |
| Mobile Tasks | Fog Tasks | Cloud Tasks | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0.3 | 11.92 | 4.37 | 2.74 | 0.00 | 6.27 | 0.95 | 0.00 | 3.70 | 18.37 | 6.16 | |||
| 0.6 | 11.90 | 4.35 | 2.48 | 0.00 | 6.26 | 0.94 | 0.00 | 3.70 | 17.85 | 6.02 | |||
| 0.9 | 11.77 | 4.25 | 2.47 | 0.00 | 6.25 | 0.95 | 0.00 | 3.70 | 17.60 | 6.01 | |||
| 1.5 | 11.67 | 5.01 | 2.45 | 0.00 | 6.23 | 0.92 | 0.00 | 3.70 | 17.17 | 5.81 | |||
| 3.0 | 11.50 | 4.05 | 2.37 | 0.00 | 6.09 | 0.90 | 0.00 | 3.70 | 17.17 | 5.78 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Scarpiniti, M.; Baccarelli, E.; Momenzadeh, A. VirtFogSim: A Parallel Toolbox for Dynamic Energy-Delay Performance Testing and Optimization of 5G Mobile-Fog-Cloud Virtualized Platforms. Appl. Sci. 2019, 9, 1160. https://doi.org/10.3390/app9061160
Scarpiniti M, Baccarelli E, Momenzadeh A. VirtFogSim: A Parallel Toolbox for Dynamic Energy-Delay Performance Testing and Optimization of 5G Mobile-Fog-Cloud Virtualized Platforms. Applied Sciences. 2019; 9(6):1160. https://doi.org/10.3390/app9061160
Chicago/Turabian StyleScarpiniti, Michele, Enzo Baccarelli, and Alireza Momenzadeh. 2019. "VirtFogSim: A Parallel Toolbox for Dynamic Energy-Delay Performance Testing and Optimization of 5G Mobile-Fog-Cloud Virtualized Platforms" Applied Sciences 9, no. 6: 1160. https://doi.org/10.3390/app9061160
APA StyleScarpiniti, M., Baccarelli, E., & Momenzadeh, A. (2019). VirtFogSim: A Parallel Toolbox for Dynamic Energy-Delay Performance Testing and Optimization of 5G Mobile-Fog-Cloud Virtualized Platforms. Applied Sciences, 9(6), 1160. https://doi.org/10.3390/app9061160






