Dual Zero-Watermarking Scheme for Two-Dimensional Vector Map Based on Delaunay Triangle Mesh and Singular Value Decomposition
Abstract
1. Introduction
2. Methodology
2.1. Data Preprocessing
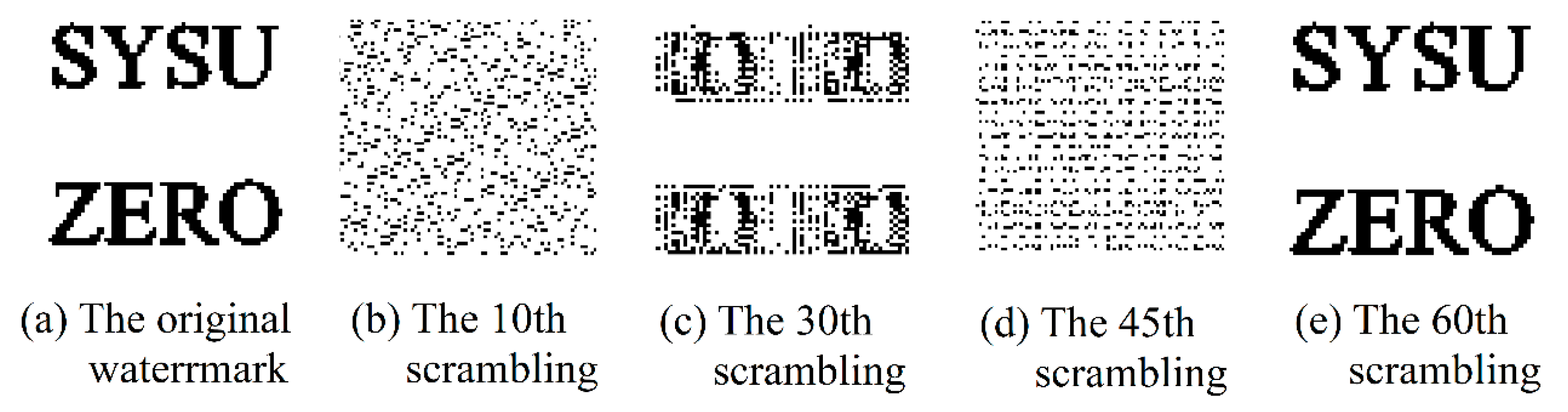
2.2. Watermark Encryption
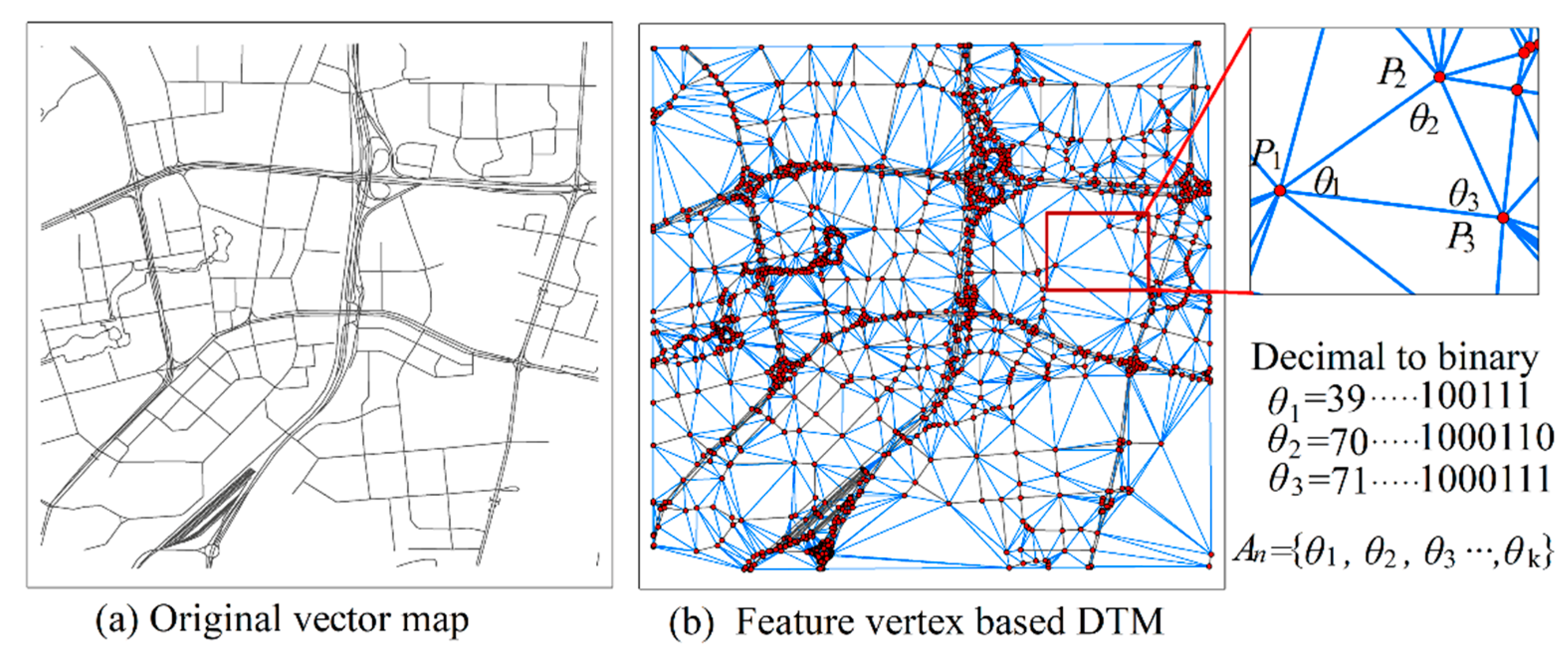
2.3. Zero-Watermark Based on Delaunay Triangle Mesh
2.4. Zero-Watermark Based on Singular Value Decomposition
2.5. Watermark Detection
3. Experimental Design
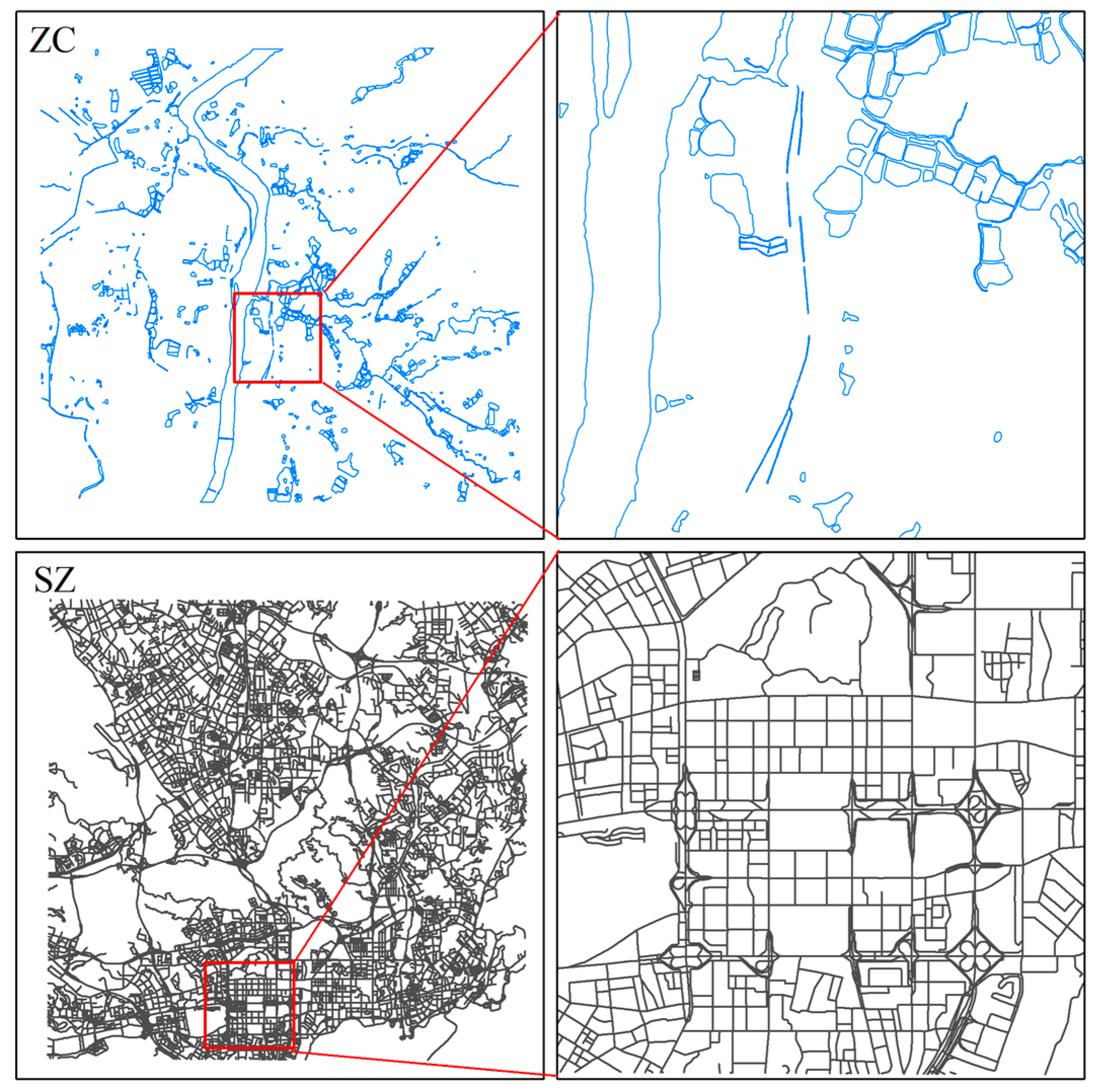
3.1. Experimental Data
3.2. Watermark Construction
3.3. Attack Experiment Design
3.3.1. Geometric Attack Experiment
3.3.2. Vertex Attack Experiment
3.3.3. Object Attack Experiment
3.3.4. Compound Attack Experiment
4. Results and Discussion
4.1. Watermark Capacity
4.2. Watermark Robustness
4.2.1. Resistance to Geometric Attacks
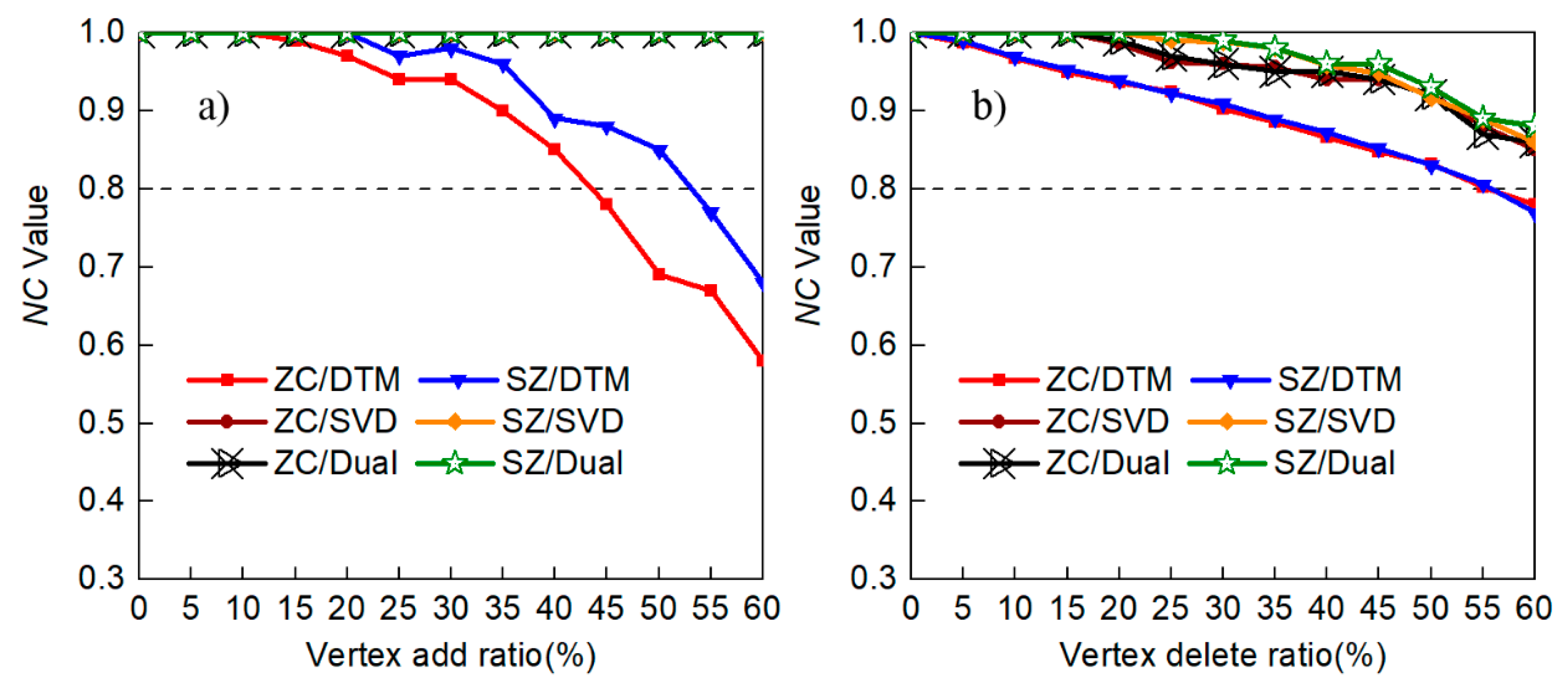
4.2.2. Resistance to Vertex Attack
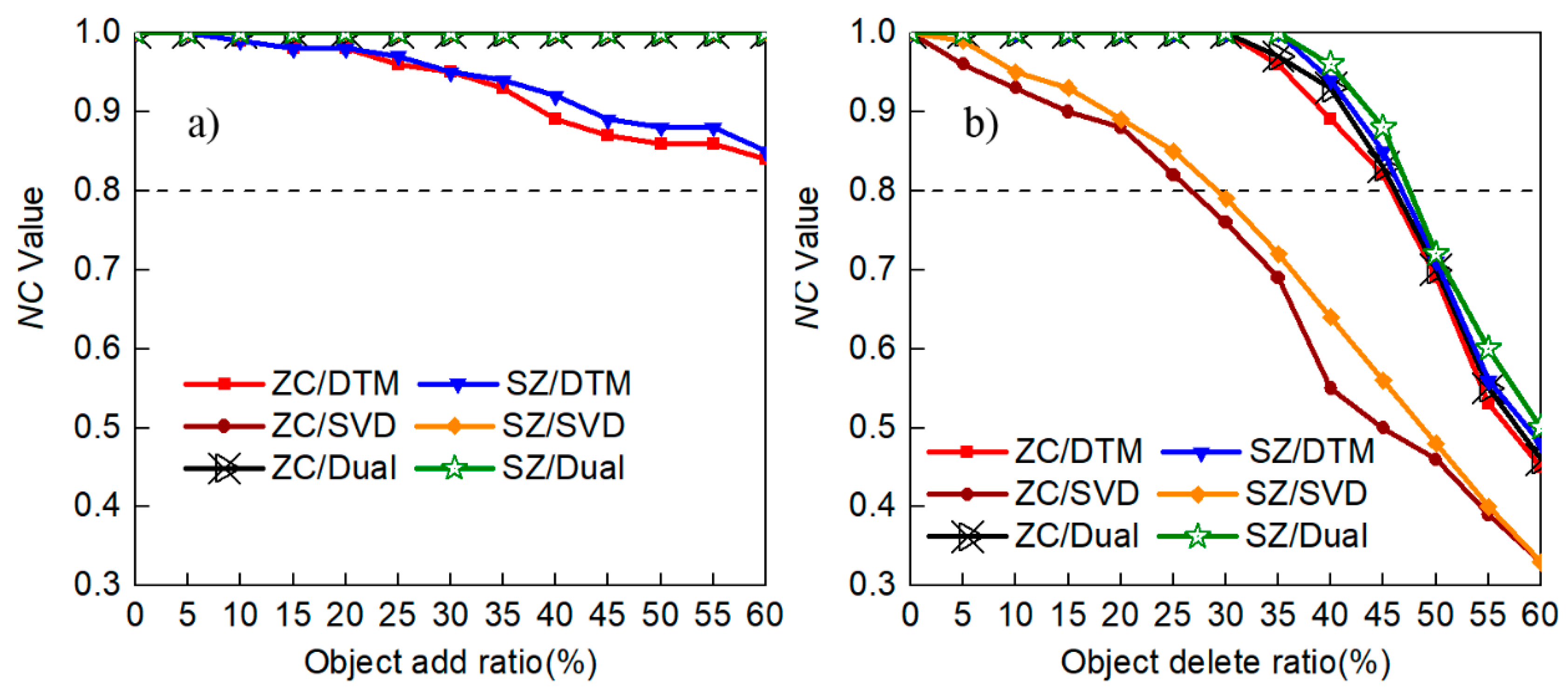
4.2.3. Resistance to Object Attack
4.2.4. Resistance to Compound Attack
4.3. Robustness Complementarity
4.4. Uniqueness Test
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Ohbuchi, R.; Ueda, H.; Endoh, S. Robust watermarking of vector digital maps. In Proceedings of the IEEE International Conference on Multimedia and Expo, Lausanne, Switzerland, 26–29 August 2002; pp. 577–580. [Google Scholar]
- Abubahia, A.; Cocea, M. Advancements in GIS map copyright protection schemes—A critical review. Multimed. Tools Appl. 2017, 76, 12205–12231. [Google Scholar] [CrossRef]
- John, S.; Brundage, T.J. Digital Watermarks for Unmanned Vehicle Navigation. US Patent US7340076, 16 April 2003. [Google Scholar]
- Cox, I.J.; Kilian, J.; Leighton, F.T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 1997, 6, 1673–1687. [Google Scholar] [CrossRef] [PubMed]
- Tirkel, A.Z.; Rankin, G.A.; Van Schyndel, R.G.; Ho, W.J.; Mee, N.R.A.; Osborne, C.F. Electronic Watermark. In Proceedings of the Digital Image Computing, Technology and Applications (DICTA’93), Sydney, Australia, 8–10 December 1993; pp. 666–673. [Google Scholar]
- Van Schyndel, R.G.; Tirkel, A.Z.; Osborne, C.F. A digital watermark. In Proceedings of the 1st International Conference on Image Processing, Austin, TX, USA, 13–16 November 1994; Volume 2, pp. 86–90. [Google Scholar]
- Cox, I.J.; Miller, M.L. The First 50 Years of Electronic Watermarking. Eurasip J. Appl. Signal Process. 2002, 2002, 126–132. [Google Scholar] [CrossRef]
- Bird, S.; Bellman, C.; Van Schyndel, R. A Shape-based Vector Watermark for Digital Mapping. In Proceedings of the 2009 Digital Image Computing: Techniques and Applications, Melbourne, Australia, 1–3 December 2009; pp. 454–461. [Google Scholar]
- Lie, W.N.; Lin, G.S.; Cheng, S.L. Dual protection of JPEG images based on informed embedding and two-stage watermark extraction techniques. IEEE Trans. Inf. Forensics Secur. 2006, 1, 330–341. [Google Scholar] [CrossRef]
- Zhu, X.S.; Ding, J.; Dong, H.H.; Hu, K.F.; Zhang, X.B. Normalized Correlation-Based Quantization Modulation for Robust Watermarking. IEEE Trans. Multimed. 2014, 16, 1888–1904. [Google Scholar] [CrossRef]
- Kandi, H.; Mishra, D.; Gorthi, S.R.K.S. Exploring the learning capabilities of convolutional neural networks for robust image watermarking. Comput. Secur. 2017, 65, 247–268. [Google Scholar] [CrossRef]
- Huynh-The, T.; Banos, O.; Lee, S.; Yoon, Y.; Le-Tien, T. Improving digital image watermarking by means of optimal channel selection. Expert Syst. Appl. 2016, 62, 177–189. [Google Scholar] [CrossRef]
- Hwang, M.J.; Lee, J.S.; Lee, M.S.; Kang, H.G. SVD Based Adaptive QIM Watermarking on Stereo Audio Signals. IEEE Trans. Multimed. 2017, 20, 45–54. [Google Scholar] [CrossRef]
- Chung, T.Y.; Park, K.S.; Oh, Y.N.; Shin, D.H.; Park, S.H. Digital Watermarking for Copyright Protection of Mpeg2 Compressed Video. IEEE Trans. Consum. Electron. 1998, 44, 895–901. [Google Scholar] [CrossRef]
- Doerr, G.; Dugelay, J.L. Security pitfalls of frame-by-frame approaches to video watermarking. IEEE Trans. Signal Process. 2004, 52, 2955–2964. [Google Scholar] [CrossRef]
- Jiang, R.; Hang, Z.; Zhang, W.; Yu, N.H. Reversible Data Hiding in Encrypted Three-Dimensional Mesh Models. IEEE Trans. Multimed. 2018, 20, 55–67. [Google Scholar] [CrossRef]
- Cox, G.S.; De Jager, G. A Survey of Point Pattern Matching Techniques and a New Approach to Point Pattern Recognition. In Proceedings of the 1992 South African Symposium on Communications and Signal Processing, Cape Town, South Africa, 11 September 1992; pp. 243–248. [Google Scholar]
- Jia, P.; Chen, Y.; Ma, J.S.; Zhu, D. Digital Watermark-based Security Technology for Geo-spatial Graphics Data. Chin. Geogr. Sci. 2006, 16, 276–281. [Google Scholar] [CrossRef]
- Voigt, M.; Busch, C. Watermarking 2D-vector data for geographical information systems. SPIE Proc. 2002, 4675, 621–628. [Google Scholar]
- Schulz, G.; Voigt, M. A high capacity watermarking system for digital maps. In Proceedings of the MM&Sec ‘04 Proceedings of the 2004 workshop on Multimedia and Security, Magdeburg, Germany, 20–21 September 2004; pp. 180–186. [Google Scholar]
- Wang, Y.; Huang, Z.B. Digital Watermarking; Publishing House of Electronics Industry: Beijing, China, 2003. [Google Scholar]
- Yang, C.S.; Zhu, C.Q.; Tao, D.X. A blind watermarking algorithm for vector geospatial data based on coordinate mapping. J. Image Graph. 2010, 15, 684–688. [Google Scholar]
- Shao, C.Y.; Wang, H.L.; Niu, X.M.; Wang, X.T. Shape-Preserving Algorithm for Watermarking 2-D Vector Map Data. In Proceedings of the 2005 IEEE 7th Workshop on Multimedia Signal Processing, Shanghai, China, 30 October–2 November 2005; pp. 1–4. [Google Scholar]
- Ohbuchi, R.; Ueda, H.; Endoh, S. Watermarking 2D vector maps in the mesh-spectral domain. In Proceedings of the Shape Modeling International, Seoul, Korea, 12–15 May 2003; pp. 216–225. [Google Scholar]
- Lee, S.H.; Kwon, K.R. Vector watermarking scheme for GIS vector map management. Multimed. Tools Appl. 2013, 63, 757–790. [Google Scholar] [CrossRef]
- Huber, S.; Held, M.; Meerwald, P.; Kwitt, R. Topology-preserving watermarking of vector graphics. Int. J. Comput. Geom. Appl. 2014, 24, 61–86. [Google Scholar] [CrossRef]
- Solachidis, V.; Pitas, I. Watermarking polygonal lines using Fourier descriptors. IEEE Comput. Graph. Appl. 2004, 24, 44–51. [Google Scholar] [CrossRef]
- Kitamura, I.; Kanai, S.; Kishinami, T. Copyright protection of vector map using digital watermarking method based on discrete Fourier transform. In Proceedings of the IEEE 2001 International Geoscience and Remote Sensing Symposium, Sydney, Australia, 9–13 July 2001; pp. 1191–1193. [Google Scholar]
- Xu, D.H.; Wang, Q.S.; Zhu, C.Q. Watermarking algorithm for vector geo-spatial data based on amplitude of DFT domain. Sci. Surv. Mapp. 2008, 33, 129–131. [Google Scholar]
- Kitamura, I.; Kanai, S.; Kishinami, T. Watermarking Vector Digital Map using Wavelet Transformation. In Proceedings of the Annual Conference of the Geographical Information Systems Association (GISA), Tokyo, Japan, 28–29 October 2000; pp. 417–421. [Google Scholar]
- Yang, C.S.; Zhu, C.Q. Watermarking Algorithm for Vector Geo-spatial Data on Wavelet Transformation. J. Zhengzhou Inst. Surv. Mapp. 2007, 1, 37–39. [Google Scholar]
- Voigt, M.; Yang, B.; Busch, C. Reversible watermarking of 2D-vector data. In Proceedings of the 2004 workshop on Multimedia and Security, Magdeburg, Germany, 20–21 September 2004; pp. 160–165. [Google Scholar]
- Celik, M.U.; Sharma, G.; Tekalp, A.M.; Saber, E. Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 2005, 14, 253–266. [Google Scholar] [CrossRef]
- Peng, F.; Lei, Y.Z.; Long, M.; Sun, X.M. A reversible watermarking scheme for two-dimensional CAD engineering graphics based on improved difference expansion. Comput. Aided Des. 2011, 43, 1018–1024. [Google Scholar] [CrossRef]
- Wang, N.; Zhang, H.; Men, C. A high capacity reversible data hiding method for 2D vector maps based on virtual coordinates. Comput. Aided Des. 2014, 47, 108–117. [Google Scholar] [CrossRef]
- Lin, Z.X.; Peng, F.; Long, M. A Low Distortion Reversible Watermarking for 2D Engineering Graphics Based on Region Nesting. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2372–2382. [Google Scholar] [CrossRef]
- Li, A.B.; Lin, B.X.; Chen, Y.; Lv, G.N. Study on copyright authentication of GIS vector data based on Zero-watermarking. In Proceedings of the International Archives of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Beijing, China, 3–11 July 2008; pp. 1783–1786. [Google Scholar]
- Zhou, Y.X.; Wei, J. A Novel Image Zero-watermarking Scheme Based on DWT-SVD. In Proceedings of the International Conference on Multimedia Technology, Hangzhou, China, 26–28 July 2011; pp. 2873–2876. [Google Scholar]
- Wang, X.Y.; Zhan, Y. A zero-watermarking scheme for three-dimensional mesh models based on multi-features. In Multimedia Tools & Applications; Springer: New York, NY, USA, 2017; pp. 1–28. [Google Scholar]
- Tsai, H.H.; Lai, Y.S.; Lo, S.C. A zero-watermark scheme with geometrical invariants using SVM and PSO against geometrical attacks for image protection. J. Syst. Softw. 2013, 86, 335–348. [Google Scholar] [CrossRef]
- Wang, X.; Huang, D.J.; Zhang, Z.Y. A Robust Zero-Watermarking Algorithm for Vector Digital Maps Based on Statistical Characteristics. J. Softw. 2012, 7, 23–49. [Google Scholar] [CrossRef]
- Peng, Y.W.; Yue, M.L. A Zero-Watermarking Scheme for Vector Map Based on Feature Vertex Distance Ratio. J. Electr. Comput. Eng. 2015, 35, 1–6. [Google Scholar] [CrossRef]
- Xun, W.; Ding-Jun, H.; Zhi-Yong, Z. A Robust Zero-Watermarking Algorithm for 2D Vector Digital Maps. In Computer, Informatics, Cybernetics and Applications; Springer: Dordrecht, The Netherlands, 2012; pp. 533–541. [Google Scholar]
- Wong, P.H.W.; Au, O.C.; Yeung, Y.M. Novel blind multiple watermarking technique for images. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 813–830. [Google Scholar] [CrossRef]
- Lin, Y.H.; Wu, J.L. A novel blind watermarking scheme for depth-image-based rendering 3D images. IEEE Trans. Broadcast. 2011, 57, 602–611. [Google Scholar] [CrossRef]
- Cao, J.H.; Li, A.B.; Lv, G.N. Study on multiple watermarking scheme for GIS vector data. In Proceedings of the International Conference on Geoinformatics, Beijing, China, 18–20 June 2010; pp. 1–6. [Google Scholar]
- Ren, N.; Wu, W.; Zhu, C.Q. An accurate authentication algorithm based on point constraint block for vector geographic data. J. Geo-Inf. Sci. 2015, 17, 166–171. [Google Scholar]
- Zhang, C.; Wang, J.; Wang, X. Digital image watermarking algorithm with double encryption by Arnold transform and logistic. In Proceedings of the NCM’08. Fourth International Conference on Networked Computing and Advanced Information Management, Gyeongju, Korea, 2–4 September 2008; Volume 1, pp. 329–334. [Google Scholar]
- Wang, C.J.; Peng, Z.Y.; Peng, Y.W.; Yu, L.; Wang, J.Z.; Zhao, Q.Z. Watermarking geographical data on spatial topological relations. Multimed. Tools Appl. 2012, 57, 67–89. [Google Scholar] [CrossRef]
- Kim, J. Robust Vector Digital Watermarking Using Angles and a Random Table. Adv. Inf. Sci. Serv. Sci. 2010, 2, 79–90. [Google Scholar]
- Li, J. Research on Digital Image Watermarking Technology Against Geometric Attacks; Nanjing University of Science & Technology: Nanjing, China, 2009. [Google Scholar]
- Wen, Q.; Sun, T.F.; Wang, S.X. Concept and application of zero-watermark. Acta Electron. Sin. 2003, 31, 214–216. [Google Scholar]
- Wang, C.Y.; Zhang, Y.P.; Zhou, X. Review on Digital Image Watermarking Based on Singular Value Decomposition. J. Inf. Process. Syst. 2017, 13, 1585–1601. [Google Scholar]
- Sun, H.R. Study on Lossless Digital Watermarking Technology and Algorithm for Vector Map; Central South University: Changsha, China, 2013. [Google Scholar]
- Du, Q.Z.; Peng, F. A Zero-Watermark Algorithm with Real-Mean for 2D Engineering Graphic. In Proceedings of the 2008 International Symposium on Electronic Commerce and Security, Guangzhou, China, 3–5 August 2008; pp. 890–893. [Google Scholar]
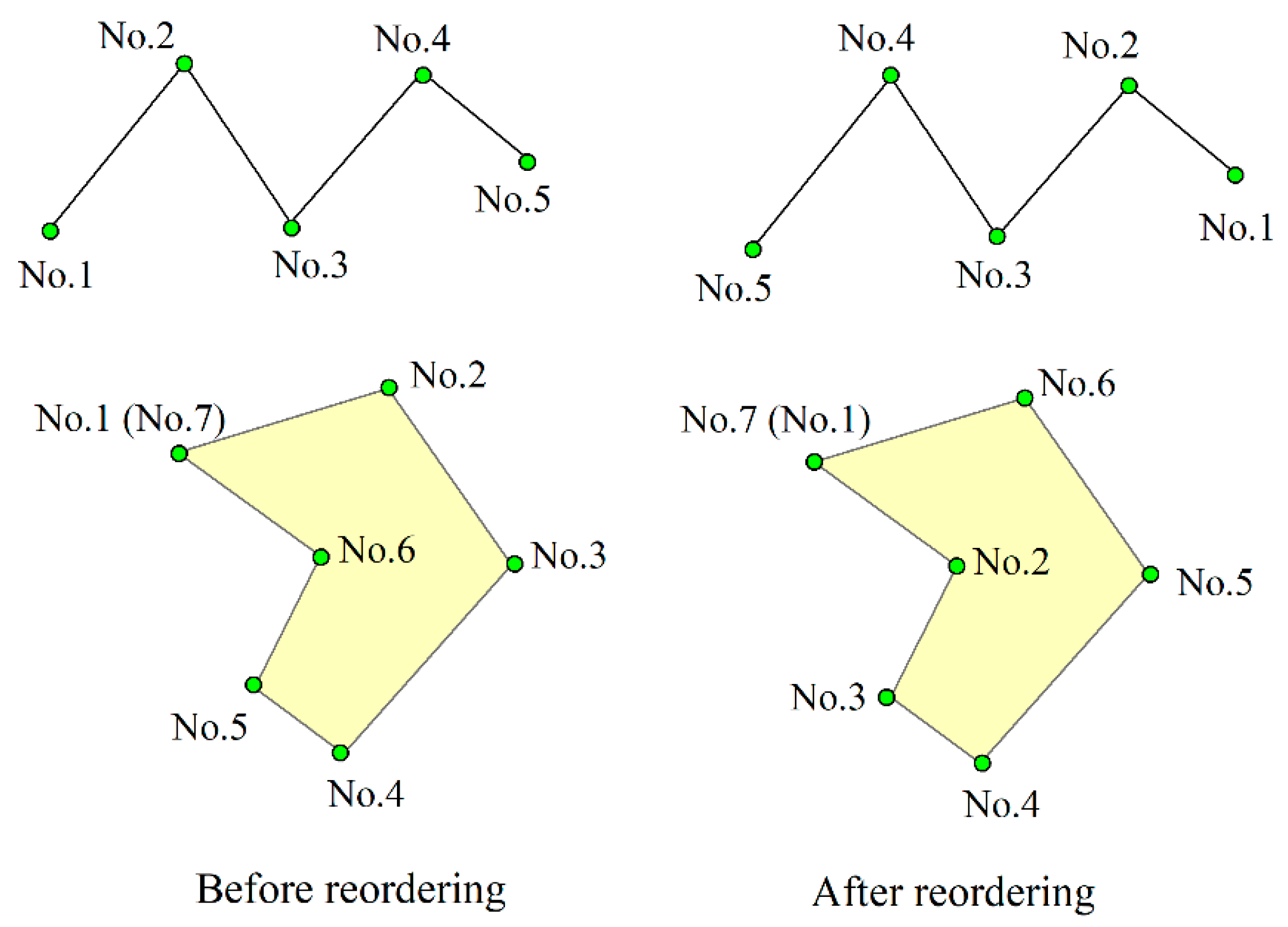


| ID | Vertex | Feature Vertex | Polylines | Blocks | ||
|---|---|---|---|---|---|---|
| ZC | 77,343 | 17,020 | 1848 | 26 | 42 | 1 |
| SZ | 128,069 | 26,913 | 4683 | 38 | 68 | 1 |
| Attack Types | Range of Magnitude |
|---|---|
| Translation | 0–100 on x-axis or y-axis |
| Rotation | 0°−360° |
| Scaling | −500%–500% |
| CST | Transform to Beijing54 and Xian80 |
| Compression | Compression ratios are 30%, 50%, 78% and 88% |
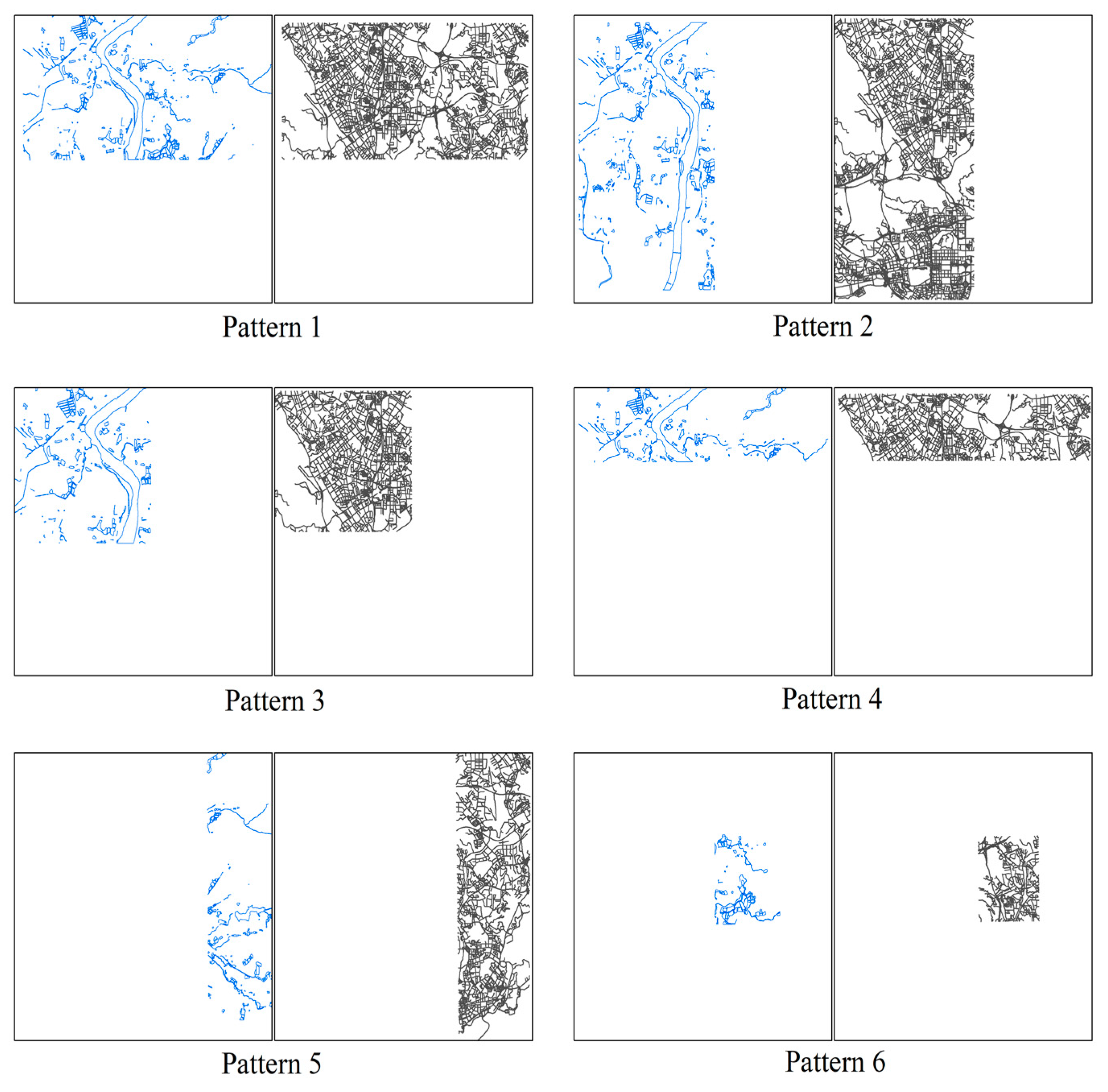
| Cropping | Multiple cropping patterns show in Figure 4 |
| Data Set | 2D Vector Data Set | Capacity | Basic Algorithm | Reference |
|---|---|---|---|---|
| G1 | Engineering Graphic | 1 | reversible watermarking | Peng et al. (2011) [34] |
| G2 | Engineering Graphic | 1 | ||
| G3 | Engineering Graphic | 1 | ||
| Average | Engineering Graphic | 1 | ||
| Coastline map | Geospatial data | 1.98271 | reversible watermarking | Wang et al. (2014) [35] |
| Road map | Geospatial data | 1.97605 | ||
| Windmill Islands map | Geospatial data | 1.95686 | ||
| Average | Geospatial data | 1.97187 | ||
| G1 | Engineering Graphic | 3.9981 | reversible watermarking | Lin et al. (2018) [36] |
| G2 | Engineering Graphic | 3.9986 | ||
| G3 | Engineering Graphic | 3.9956 | ||
| Average | Engineering Graphic | 3.9978 | ||
| An engineering graphic | Engineering graphic | 1 | zero-watermarking | Du and Peng (2008) [55] |
| ZC | Geospatial data | 3.55818 | zero-watermarking | The proposed |
| SZ | Geospatial data | 3.44814 | ||
| Average | Geospatial data | 3.50316 |
| Attack | NC(DTM)/(a) | NC(DTM)/(b) | NC(SVD)/(a) | NC(SVD)/(b) | ||||
|---|---|---|---|---|---|---|---|---|
| Translation 0–100 | 1 |  | 1 |  | 1 |  | 1 |  |
| Rotation 0°–360° | 1 |  | 1 |  | 1 |  | 1 |  |
| Scaling −500%–500% | 1 |  | 1 |  | 1 |  | 1 |  |
| Transfer coordinate to Xian80 | 0.84 |  | 0.85 |  | 1 |  | 1 |  |
| Transfer coordinate to Beijing54 | 0.83 |  | 0.84 |  | 1 |  | 1 |  |
| Compression 30% ratio | 1 |  | 1 |  | 0.94 |  | 0.95 |  |
| Compression 50% ratio | 1 |  | 1 |  | 0.71 |  | 0.73 |  |
| Compression 78% ratio | 1 |  | 1 |  | - | - | - | - |
| Compression 88% ratio | 0.89 |  | 0.82 |  | - | - | - | - |
| Cropping | ZC/DTM | ZC/SVD | SZ/DTM | SZ/SVD | The Proposed | Ohbuchi et al. (2002) [1] | Ohbuchi et al. (2003) [24] | |
|---|---|---|---|---|---|---|---|---|
| Pattern 1 | 0 | 45.0 | 0 | 43.5 | 0 | 1.4 | 0.0 | 0.0 |
| Pattern 2 | 0 | 43.6 | 0 | 44.6 | 0 | 1.8 | 0.1 | 0.4 |
| Pattern 3 | 0 | 62.6 | 0 | 65.0 | 0 | 7.0 | 0.7 | 1.3 |
| Pattern 4 | 0 | 67.0 | 0 | 63.6 | 0 | 6.8 | 0.4 | 0.0 |
| Pattern 5 | 0 | 67.3 | 0 | 63.9 | 0 | 11.3 | 1.4 | 0.4 |
| Pattern 6 | 0 | 76.1 | 0 | 75.5 | 0 | 35.9 | 18.8 | 15.1 |
| Watermarked Data | |||||
|---|---|---|---|---|---|
| Zero-watermarks | (ZC/DTM) | 0.4008 | 0.3936 | 0.3805 | 0.3794 |
| (ZC/SVD) | 0.4039 | 0.4005 | 0.3905 | 0.3881 | |
| (SZ/DTM) | 0.4009 | 0.3884 | 0.3872 | 0.3986 | |
| (SZ/SVD) | 0.3886 | 0.3895 | 0.3923 | 0.3863 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xi, X.; Zhang, X.; Liang, W.; Xin, Q.; Zhang, P. Dual Zero-Watermarking Scheme for Two-Dimensional Vector Map Based on Delaunay Triangle Mesh and Singular Value Decomposition. Appl. Sci. 2019, 9, 642. https://doi.org/10.3390/app9040642
Xi X, Zhang X, Liang W, Xin Q, Zhang P. Dual Zero-Watermarking Scheme for Two-Dimensional Vector Map Based on Delaunay Triangle Mesh and Singular Value Decomposition. Applied Sciences. 2019; 9(4):642. https://doi.org/10.3390/app9040642
Chicago/Turabian StyleXi, Xu, Xinchang Zhang, Weidong Liang, Qinchuan Xin, and Pengcheng Zhang. 2019. "Dual Zero-Watermarking Scheme for Two-Dimensional Vector Map Based on Delaunay Triangle Mesh and Singular Value Decomposition" Applied Sciences 9, no. 4: 642. https://doi.org/10.3390/app9040642
APA StyleXi, X., Zhang, X., Liang, W., Xin, Q., & Zhang, P. (2019). Dual Zero-Watermarking Scheme for Two-Dimensional Vector Map Based on Delaunay Triangle Mesh and Singular Value Decomposition. Applied Sciences, 9(4), 642. https://doi.org/10.3390/app9040642






