Developing a New Haptic Passcode for User Authentication with a Personal ID Tag to Prevent Copying Attacks
Abstract
1. Introduction
2. Background and Related Studies
3. Design and Implementation
3.1. Hardware and Functional Units
3.2. Haptic Gestures for Passcode
3.3. Classification Algorithm
if (Pr_interactionaxisa ≥ Threshold_level[k]){ change k through predefined rule; if (Pr_interactionaxisb ≥ Threshold_level[k]) { type_of_interaction = haptic_interaction[k]; break; } … } else …where,
- Threshold_value[k]: k-th probability values learned from the 250 trials to branch.
- Thr_low[k], Thr_high[k]: the kth upper or lower range value of the l axis in order to decide type_of_pattern or branch.
- haptic_pattern[k]: name of the kth haptic pattern.
| Algorithm 1. Pseudocode of the authentication algorithm: (a) Phase 1. Detecting effective gestures; (b) Phase 2. Classification of the seven haptic gestures |
| (a) Phase 1: Algorithm for detecting effectivegestures Input: a piece of raw data from each of the five axes of the acceleration sensor Output: TRUE or FALSE. TRUE when an effective gesture has been detected Definition of variable in Phase 1: Thr_low,Thr_high: threshold values in order to search a starting point of haptic gesture t: the duration for initial data gathering. Default is 5 seconds HZ: Sampling frequency of the gathered data per sec |
While(t*HZ) { Gather current x, y, z, x–z, and y–z axis data from the sensor; Calculate moving average of z axis; Normalize the calculated moving averages and store to Nz; if!(Thr_low < Nz < Thr_high) Return TRUE;//effective gesturedetected! } |
| (b)Phase 2: Gesture classification algorithm Input: a piece of raw data from each of the five axes of the acceleration sensor Output: classified haptic pattern Definition of variable in Phase2: DATA_SIZE: the number of data to discriminate the seven haptic gestures (default is 50) |
| for(i = 0; i < DATA_SIZE; i++) { Gather current x, y, z, x–z, and y–z data from the sensor; Calculate moving average of x, y, z, x–z, and y–z; Normalize the calculated moving averages and store to Nx, Ny, Nz, Nx-z, and Ny-z; arrayNx[i] = Nx; arrayNy[i] = Ny; arrayNz[i] = Nz; arrayNy-z[i] = Ny-z; arrayNx-z[i] = Nx-z; Decide the type of gesture by comparing arrayNx, arrayNy, arrayNz, arrayNy-z, arrayNx-z to the predefined pattern information of each gesture; Return type of gesture; } |
4. User Performance and Usability
4.1. Experimental Setup
4.2. Results
4.2.1. System Accuracy
4.2.2. User Preference Evaluation
4.2.3. Copying Attack Experiment
5. Conclusions
5.1. General Conclusion
5.2. Mobile Application
5.3. Future Studies
Author Contributions
Funding
Conflicts of Interest
References
- Ayoade, J. Security implications in RFID and authentication processing framework. Comput. Secur. 2006, 25, 207–212. [Google Scholar] [CrossRef]
- Feldhofer, M. An authentication protocol in a security layer for RFID smart tags. In Proceedings of the 12th IEEE Mediterranean Electrotechnical Conference (IEEE Cat. No. 04CH37521), Dubrovnik, Croatia, 12–15 May 2004; pp. 759–762. [Google Scholar]
- Hwang, I.-K.; Baek, J.-W. Wireless access monitoring and control system based on digital door lock. IEEE Trans. Consum. Electron. 2007, 53, 1724–1730. [Google Scholar] [CrossRef]
- Bardram, J.E.; Kjær, R.E.; Pedersen, M.Ø. Context-aware user authentication–supporting proximity-based login in pervasive computing. In Proceedings of the International Conference on Ubiquitous Computing, Seattle, WA, USA, 12–15 October 2003; pp. 107–123. [Google Scholar]
- See, J.; Lee, S.-W. An integrated vision-based architecture for home security system. IEEE Trans. Consum. Electron. 2007, 53, 489–498. [Google Scholar] [CrossRef]
- Langheinrich, M. RFID and privacy. In Security, Privacy, and Trust in Modern Data Management; Springer: Berlin, Germany, 2007; pp. 433–450. [Google Scholar]
- Jabbar, H.; Jeong, T.; Hwang, J.; Park, G. Viewer identification and authentication in IPTV using RFID technique. IEEE Trans. Consum. Electron. 2008, 54, 105–109. [Google Scholar] [CrossRef]
- Park, S.; Locher, I.; Savvides, A.; Srivastava, M.B.; Chen, A.; Muntz, R.; Yuen, S. Design of a wearable sensor badge for smart kindergarten. In Proceedings of the Sixth International Symposium on Wearable Computers, Seattle, WA, USA, 10 October 2002; pp. 231–238. [Google Scholar]
- Patel, S.N.; Pierce, J.S.; Abowd, G.D. A gesture-based authentication scheme for untrusted public terminals. In Proceedings of the 17th Annual ACM Symposium on User Interface Software and Technology, Santa Fe, NM, USA, 24–27 October 2004; pp. 157–160. [Google Scholar]
- Villar, N.; Schmidt, A.; Kortuem, G.; Gellersen, H.-W. Interacting with proactive public displays. Comput. Graph. 2003, 27, 849–857. [Google Scholar] [CrossRef]
- Zuo, F.; de With, P. Real-time embedded face recognition for smart home. IEEE Trans. Consum. Electron. 2005, 51, 183–190. [Google Scholar]
- Chong, M.K.; Marsden, G. Exploring the use of discrete gestures for authentication. In Proceedings of the IFIP Conference on Human-Computer Interaction, Uppsala, Sweden, 24–28 August 2009; pp. 205–213. [Google Scholar]
- Mayrhofer, R.; Gellersen, H. Shake well before use: Authentication based on accelerometer data. In Proceedings of the International Conference on Pervasive Computing, Toronto, Canada, 13–16 May 2007; pp. 144–161. [Google Scholar]
- Liu, J.; Zhong, L.; Wickramasuriya, J.; Vasudevan, V. User evaluation of lightweight user authentication with a single tri-axis accelerometer. In Proceedings of the 11th International Conference on Human-Computer Interaction with Mobile Devices and Services, Bonn, Germany, 15–18 September 2009; p. 15. [Google Scholar]
- Orozco, M.; Asfaw, Y.; Shirmohammadi, S.; Adler, A.; El Saddik, A. Haptic-based biometrics: A feasibility study. In Proceedings of the 2006 14th Symposium on Haptic Interfaces for Virtual Environment and Teleoperator Systems, Alexandria, VA, USA, 25–26 March 2006; pp. 265–271. [Google Scholar]
- Iglesias, R.; Orozco, M.; El Saddik, A. Haptics for recognizing and quantifying hand movement patterns for authentication. In Proceedings of the 2007 IEEE International Symposium on Intelligent Signal Processing, Alcala de Henares, Spain, 3–5 October 2007; pp. 1–6. [Google Scholar]
- Alsulaiman, F.A.; Cha, J.; El Saddik, A. User identification based on handwritten signatures with haptic information. In Proceedings of the International Conference on Human Haptic Sensing and Touch Enabled Computer Applications, Madrid, Spain, 10–13 June 2007; pp. 114–121. [Google Scholar]
- Cain, A.A.; Chiu, L.; Santiago, F.; Still, J.D. Swipe authentication: Exploring over-the-shoulder attack performance. In Advances in Human Factors in Cybersecurity; Springer: Berlin, Germany, 2016; pp. 327–336. [Google Scholar]
- Pozo, A.; Fierrez, J.; Martinez-Diaz, M.; Galbally, J.; Morales, A. Exploring a statistical method for touchscreen swipe biometrics. In Proceedings of the 2017 International Carnahan Conference on Security Technology (ICCST), Madrid, Spain, 23–26 October 2017; pp. 1–4. [Google Scholar]
- Antal, M.; Szabó, L.Z. Biometric authentication based on touchscreen swipe patterns. Procedia Technol. 2016, 22, 862–869. [Google Scholar] [CrossRef]
- Song, Y.; Cai, Z.; Zhang, Z.-L. Multi-touch authentication using hand geometry and behavioral information. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2017; pp. 357–372. [Google Scholar]
- Meng, W.; Li, W.; Wong, D.S.; Zhou, J. TMGuard: A touch movement-based security mechanism for screen unlock patterns on smartphones. In Proceedings of the International Conference on Applied Cryptography and Network Security, Guildford, UK, 19–22 June 2016; pp. 629–647. [Google Scholar]
- De Luca, A.; Hang, A.; Brudy, F.; Lindner, C.; Hussmann, H. Touch me once and i know it’s you!: Implicit authentication based on touch screen patterns. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Austin, TX, USA, 5–10 May 2012; pp. 987–996. [Google Scholar]
- De Luca, A.; Denzel, M.; Hussmann, H. Look into my eyes!: Can you guess my password? In Proceedings of the 5th Symposium on Usable Privacy and Security, Mountain View, CA, USA, 15–17 July 2009; p. 7. [Google Scholar]
- Kumar, M.; Garfinkel, T.; Boneh, D.; Winograd, T. Reducing shoulder-surfing by using gaze-based password entry. In Proceedings of the 3rd Symposium on Usable Privacy and Security, Pittsburgh, PA, USA, 18–20 July 2007; pp. 13–19. [Google Scholar]
- Hayashi, E.; Dhamija, R.; Christin, N.; Perrig, A. Use your illusion: Secure authentication usable anywhere. In Proceedings of the 4th Symposium on Usable Privacy and Security, Pittsburgh, PA, USA, 23–25 July 2008; pp. 35–45. [Google Scholar]
- Lee, S.; Song, K.; Choi, J. Access to an automated security system using gesture-based passwords. In Proceedings of the 2012 15th International Conference on Network-Based Information Systems, Melbourne, Australia, 26–28 September 2012; pp. 760–765. [Google Scholar]
- Lee, S.; Song, K.; Kim, J.; Choi, J. Ambient widget: An ambient information system using gesture-based interactions. In Proceedings of the 2012 15th International Conference on Network-Based Information Systems, Melbourne, Australia, 26–28 September 2012; pp. 703–708. [Google Scholar]
- Lee, S.; Song, K.; Choi, J.; Choi, Y.; Jang, M. Designing a gesture-based interaction with an ID tag. In Proceedings of the 2010 IEEE International Conference on Systems, Man and Cybernetics, Istanbul, Turkey, 10–13 October 2010; pp. 2220–2225. [Google Scholar]
- Vetter, R. Authentication by biometric verification. Computer 2010, 43, 28–29. [Google Scholar] [CrossRef]

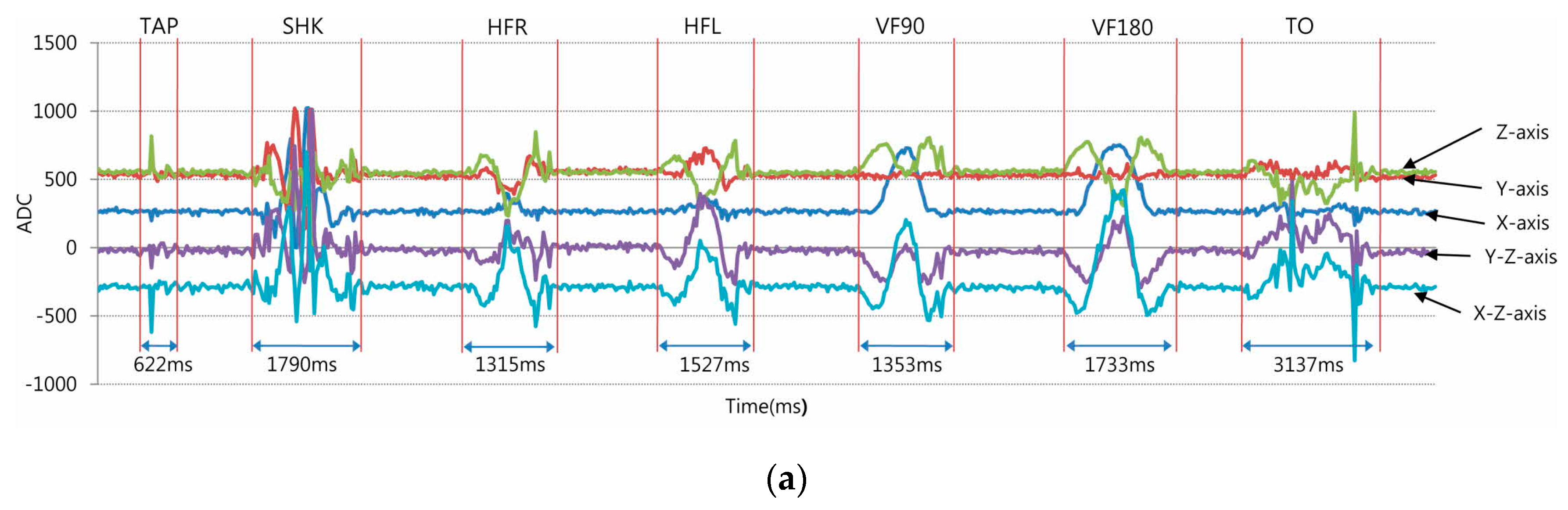
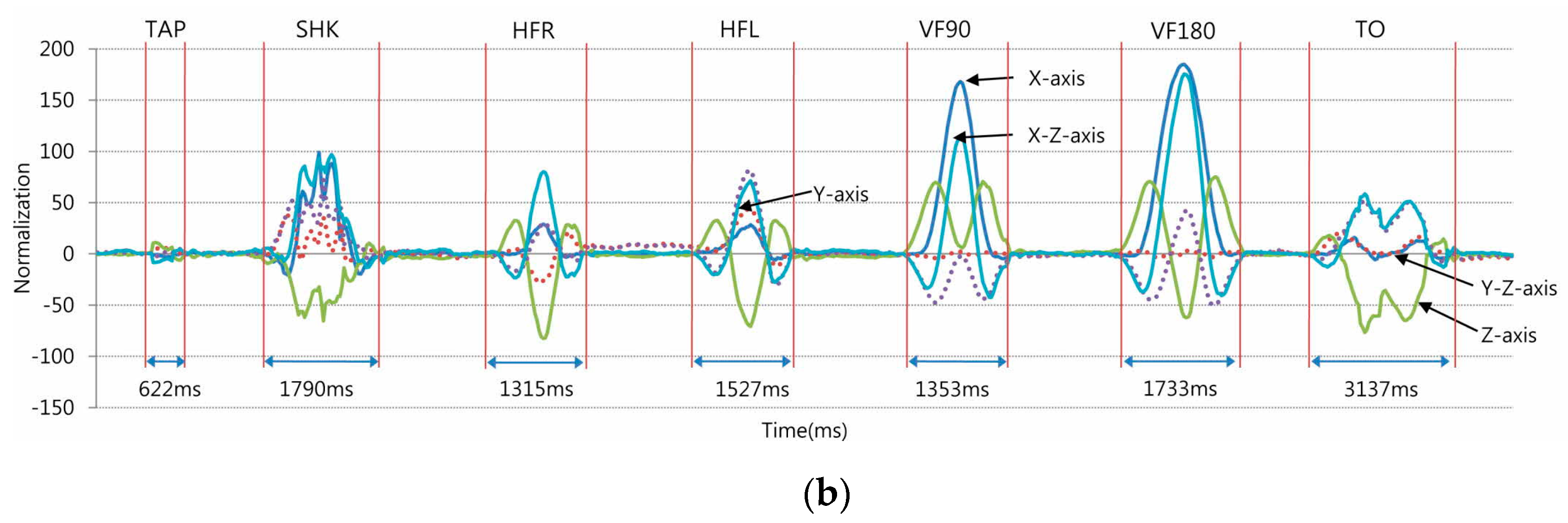
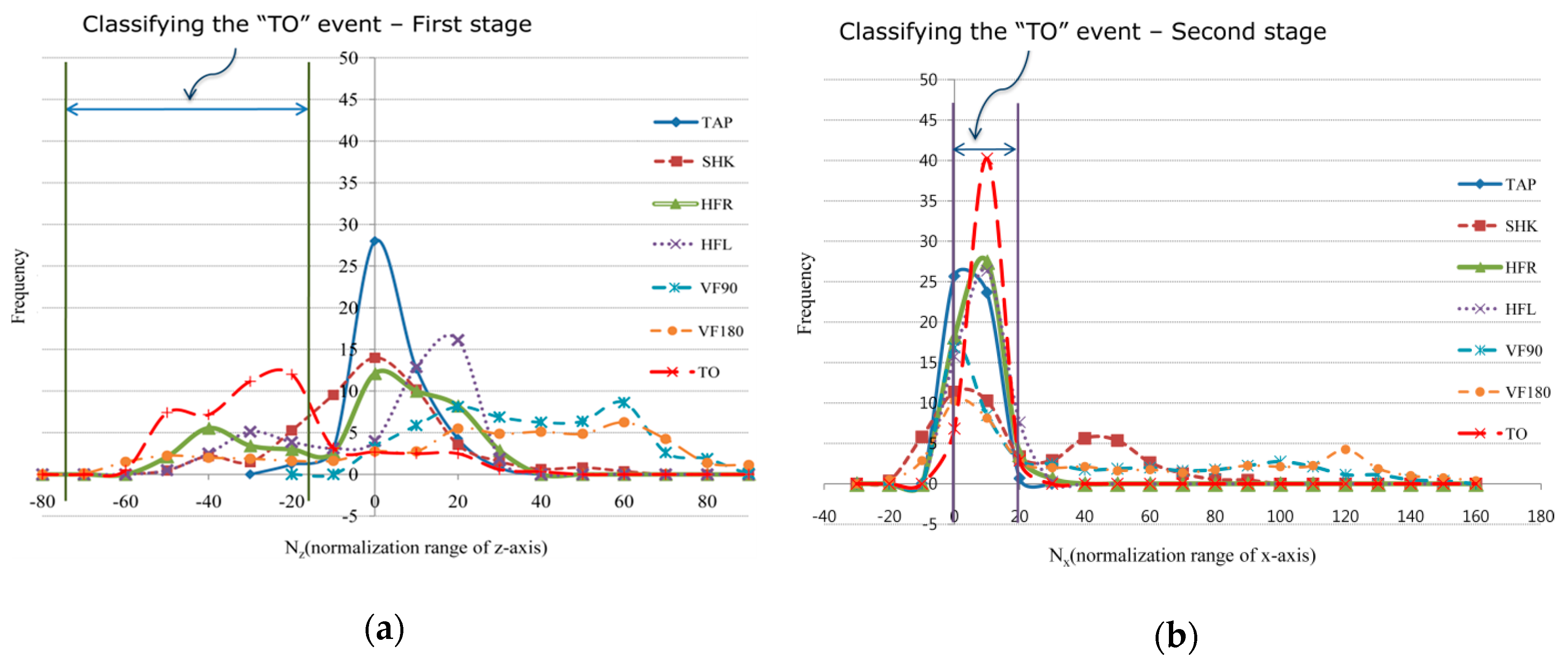
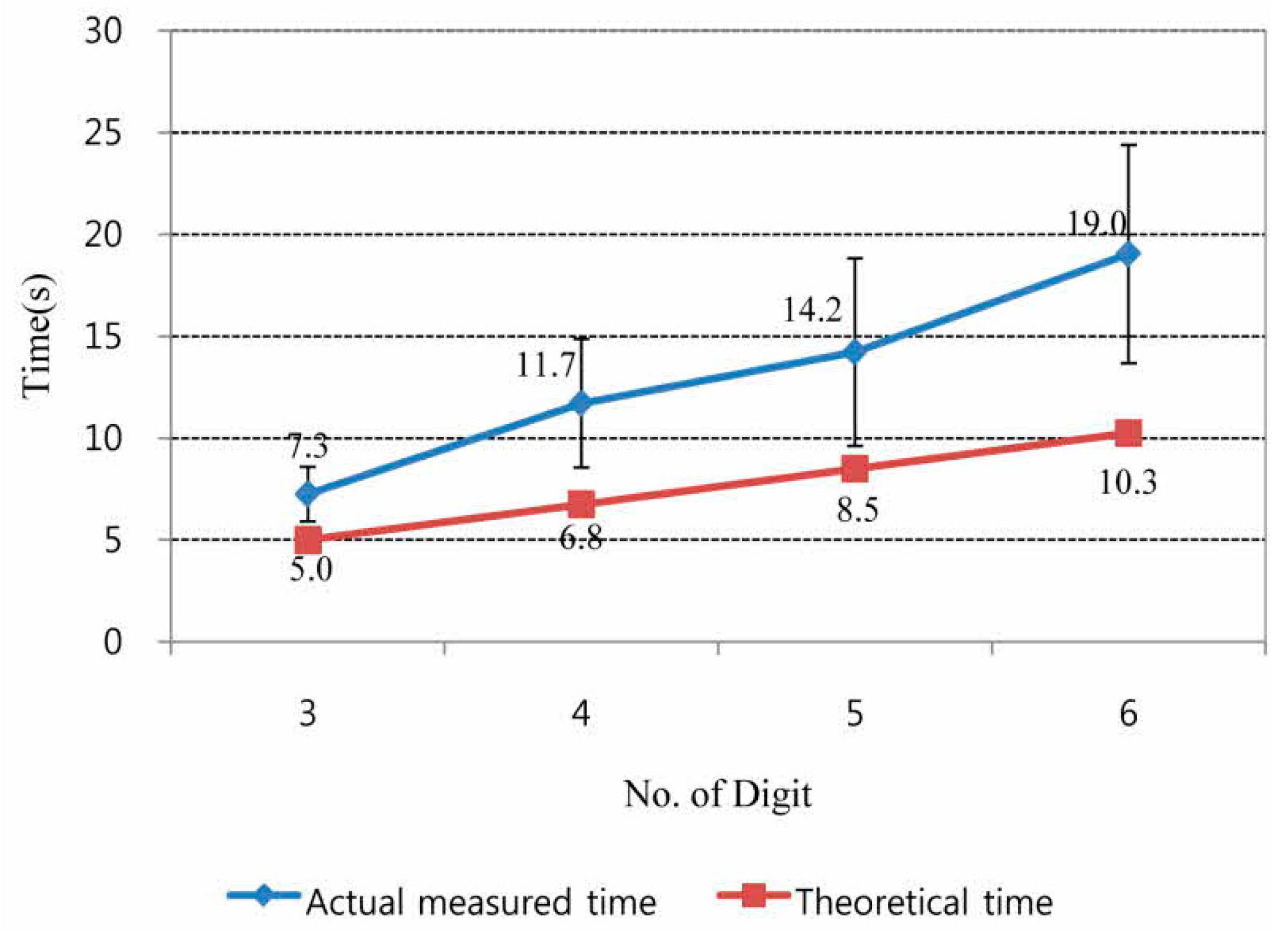

| Pattern | Description of Manipulation of the Identification (ID) Tag | Latency (ms) | User Preference | Data from Axes | |
|---|---|---|---|---|---|
| TAP | 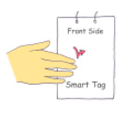 | TAPping on the frontal side of the tag | 622 | 17.8% | x, y, z |
| SHK | 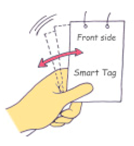 | SHaKing the tag | 1790 | 10.4% | x, y, z, y-z |
| VF90 |  | Vertical upward Flipping by 90 degree | 1315 | 13.3% | x, z, y-z |
| VF180 | 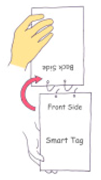 | Vertical upward Flipping by 180 degree | 1527 | 11.1% | x, z, y-z |
| HFR |  | Horizontal Flipping by 90 degree to the Right | 1353 | 24.4% | x, y, z, y-z |
| HFL |  | Horizontal Flipping by 90 degree to the Left | 1257 | 15.6% | x, y, z, y-z |
| TO | 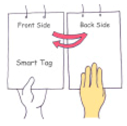 | Turning Over and back to the normal position | 3137 | 7.4% | x, z, x-z |
| Recognition Rate (%) | Actual Pattern | |||||||
|---|---|---|---|---|---|---|---|---|
| TAP | SHK | HFR | HFL | VF90 | VF180 | TO | ||
| Recognized Pattern | TAP | 95.3 | 0 | 0 | 0 | 0 | 0 | 0 |
| SHK | 0 | 92.7 | 0 | 0 | 0 | 0 | 0 | |
| HFR | 0 | 0.7 | 92.0 | 9.3 | 0 | 0 | 10.0 | |
| HFL | 0 | 0 | 0 | 88.0 | 0 | 0 | 4.7 | |
| VF90 | 0 | 0 | 0 | 0 | 94.0 | 7.3 | 0 | |
| VF180 | 0 | 0 | 0 | 0 | 0 | 74.0 | 0 | |
| TO | 0 | 0 | 0 | 0 | 0 | 0 | 82.0 | |
| No Response | 4.7 | 6.7 | 8.0 | 2.7 | 6.0 | 18.7 | 3.3 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.; Song, K.; Kim, S. Developing a New Haptic Passcode for User Authentication with a Personal ID Tag to Prevent Copying Attacks. Appl. Sci. 2019, 9, 5520. https://doi.org/10.3390/app9245520
Lee S, Song K, Kim S. Developing a New Haptic Passcode for User Authentication with a Personal ID Tag to Prevent Copying Attacks. Applied Sciences. 2019; 9(24):5520. https://doi.org/10.3390/app9245520
Chicago/Turabian StyleLee, Seongil, Kyohyun Song, and Sangmin Kim. 2019. "Developing a New Haptic Passcode for User Authentication with a Personal ID Tag to Prevent Copying Attacks" Applied Sciences 9, no. 24: 5520. https://doi.org/10.3390/app9245520
APA StyleLee, S., Song, K., & Kim, S. (2019). Developing a New Haptic Passcode for User Authentication with a Personal ID Tag to Prevent Copying Attacks. Applied Sciences, 9(24), 5520. https://doi.org/10.3390/app9245520





