Abstract
Sensing strategy directly influences the sensing accuracy of a spectrum sensing scheme. As a result, the optimization of a sensing strategy appears to be of great significance for accuracy improvement in spectrum sensing. Motivated by this, a novel sensing strategy is proposed in this paper, where an improved tradeoff among detection probability, false-alarm probability and available throughput is obtained based on the energy detector. We provide the optimal sensing performance and exhibit its superiority in theory compared with the classical scheme. Finally, simulations validate the conclusions drawn in this paper.
1. Introduction
With the rapid development of wireless communication technology, the number of wireless users has been increasing dramatically, resulting in the shortage of spectrum resources. However, according to the investigation of the Federal Communication Commission (FCC), low utilization of the registered spectrum is not a new problem [1]. In consequence, how to improve the utilization of the registered spectrum has become a problem that deserves our attention [2].
To solve the shortage issue of the wireless spectrum as much as possible, Cognitive Radio (CR) [3,4,5] technology is proposed, where a CR can adaptively adjust its parameters with the change of environment for opportunistic spectrum reuse when the primary (registered) user (PU) is out. The main technology behind CR includes spectrum sensing (SS) [6,7,8], dynamic spectrum allocation (DSA) [9] and spectrum sharing [10]. SS mainly contributes to the decision on spectrum occupancy. The main research of DSA focuses on how to effectively optimize and allocate the perceived spectrum. Spectrum sharing aims at exploring high-efficiency sharing of the observed spectrum in the condition of multiple users. Since it functions as the foundation of DSA and spectrum sensing, SS appears indispensable for further development of CR.
Classical SS methods mainly contain energy detector (ED) [11], cyclostationary feature detector (CFD) [12], covariance matrix-based detector (CMD) [13] and cooperative spectrum sensing (CSS) [14]. Thanks to its low complexity and superior performance, ED is the most popular and classical scheme for SS [15]. However, ED is sensitive to environment noise and its sensing performance degrades sharply with the fall of environmental SNR. Consequently, most ED-based SS are devoted to restraining noise uncertainty. CFD has attracted the attention of many researchers due to its insensitivity to noise uncertainty [16], which is at the expense of computational complexity. In consequence, CFD works as a kind of SS scheme suitable for the situation, where there is no constraint on system complexity. CMD is based on the covariance matrix analysis of the received observed signal [17]. The essence of CMD is that received signals are correlated with each other; however, there is no correlation between noise and noise, as well as between noise and signals. The main purpose of CSS is to solve the hidden terminal issue where high buildings may interfere with the received signal of CR and results in judgment on the condition of observed spectrum bands [18]. By placing various CR terminals located in different positions, CSS helps to solve the hidden terminal issue and improves sensing accuracy as well. CSS contains centralized CSS and distributed CSS [19]. Distributed CSS communicates with each other and each node makes the final decision based on the decision of the others [20]. For centralized CSS, there is a fusion center where the decision result or received signal of each node is sent to the fusion center and the fusion center makes the final decision according to some decision rule [21]. The classical decision rules of centralized CSS contain AND rule [22], OR rule [23], Majoring voting rule [24], Equal Gain Combining rule [25], Selection Combining rule [26] and Maximal Ratio Combining rule [27].
In SS, three parameters are associated with the sensing performance, detection probability, false-alarm probability and available throughput [28]. The higher the detection probability is, the better the primary user (PU) can be protected. From the perspective of secondary users, the lower the false-alarm probability is, the greater chance the channel can be reused when it is available. Nevertheless, when detection probability is high, the corresponding false-alarm probability is also high, resulting in a lower available throughput. On the contrary, when the false alarm probability is at a low level, the corresponding detection probability is also comparatively low. As a result, how to establish a tradeoff among detection probability, false-alarm probability and available throughput deserves further discussion.
In the literature, three kinds of sensing strategies were explored. In [28], we can conclude that the detection performance is optimal and the false-alarm probability is in the maximum fault tolerance range of CR, when the detection probability is maximum. The CR system can be optimized when the system has the maximum throughput and the detection probability is greater than the minimum requirement of CR [29]. Evidently, [28] tended to improve the detection probability at the expense of false-alarm probability. Simultaneously, [29] sacrificed detection probability for a higher throughput. In [30], the authors insisted that the system performance was optimal when the sum of the false-alarm probability and miss probability was at the lowest level. Due to the negative correlations between false-alarm probability and available throughput, [30] provided a tradeoff among detection probability, false-alarm probability and available throughput.
Motivated by the reasons mentioned above, an improved sensing strategy is proposed in this paper, giving a better tradeoff among the detection probability, false-alarm probability and available throughput. The main contribution of this paper is concluded as follows:
- We analyze the advantages and disadvantages of three classical sensing strategies and demonstrate the superiority of the proposed strategy.
- We emphatically compare the proposed sensing strategy with the one proposed in [30] and reach a conclusion that the proposed strategy outperforms the one in [30].
- We conduct simulation experiments respectively in the AWGN, Rayleigh and Rician channel to validate our conclusion proposed in this paper.
Note that the proposed strategy greatly differs from energy harvesting (EH)-based SS [31]. To the best knowledge of the author, EH-based SS is devoted to collect enough energy from the environment to ensure that sensor nodes could work stably. As for the proposed strategy in this paper, a better tradeoff among detection probability, false-alarm probability and available throughput is considered. The essence of the proposed scheme consists in providing a sensing strategy with PU protection considering the communication capacity of cognitive users.
The rest of this paper is organized as follows. Section 2 reviews the basic work of SS. The main contribution of this paper is shown in Section 3, which contains all of the theoretical derivations. Simulation experiments and analysis results are reported in Section 4. Finally, Section 5 concludes this paper.
2. System Model
Let us define and separately as the carrier frequency and bandwidth of the observed radio signal. Generally, SS is regarded as a binary hypothesis issue,
where denotes the presence of PU while denotes the absence of PU; and , respectively, represent received mixed signal, clean signal and noise at the receiver of CR; signifies the corresponding channel gain. In addition, (1) and (2) are based on three assumptions as follows [32]:
- (1)
- and are assumed as independent and identically distributed stationary random process with mean zero and , ;
- (2)
- and are independent mutually;
- (3)
- is a complex Gaussian random variable with mean zero.
Suppose is the sampling frequency and is the sampling time at the receiver of CR. The corresponding sampling point is . As a result, the false-alarm probability is defined as
and the corresponding detection probability could be written as
where is the environment SNR in the location of CR; is the presupposed threshold;
is the complementary distribution function of standard Gaussian.
Denote as the throughput of the secondary network in the case and as the throughput in the case. Since a length of period , out of the total frame time is used for sensing [32], the achievable throughputs of the SUs under these scenarios are, respectively, given as
where denotes the absence probability of PU in the observed bands and denotes the presence probability of PU in the observed bands. We assume, in this paper, that the secondary user (SU) can stop communicating with its users at once when PU resumes the observed band (). Therefore, the average throughput for the secondary network is given by
3. Proposed Sensing Strategy
In this section, we firstly discuss three classical sensing strategies and exhibit their advantages and disadvantages, respectively. Then, we emphatically compare the proposed sensing strategy with the one proposed in [30].
3.1. Three Classical Sensing Strategies
Table 1 shows comparisons of three classical sensing strategies, where and , respectively, signify the maximum false-alarm probability and minimum detection probability that a CR could allow. For Sensing Strategy 1, the detection probability is maximized, which indicates the best protection for the PU. However, the corresponding false alarm probability is not the lowest. This manifests that Sensing Strategy 1 is suitable for the case where there is not much requirement for communication capacity and quality of secondary network. The communication capacity of the secondary network is optimal for Sensing Strategy 2, while its protection towards PU is limited. Different from Sensing Strategy 1 and 2, Sensing Strategy 3 concentrates on a tradeoff between PU protection and communication capacity of the secondary network, where denotes probability of miss and This is conducive to balancing the performance of a registered user and cognitive user and promotes the development and application of CR. As a result, this paper attempts to make a further optimization on Sensing Strategy 3.

Table 1.
Comparisons of three classical sensing strategies.
3.2. Classical Sensing Strategy 3
In this section, we discuss the sensing strategy proposed in [30]. Subsequently, the proposed sensing strategy is exhibited and analyzed in the next section.
The sensing strategy in [30] can be simplified as
Theorem 1.
Given,,and,reaches the minimum when
Proof.
According to (3), (4) and (9)
For , we have
Then, we get
So, we can find that monotonically increases within the internal while it monotonically decreases if That is, reaches the minimum, when
□
3.3. Proposed Sensing Strategy
Detection probability is beneficial to secure communication of PU and available throughput indicates the communication capacity of SU, while the false-alarm probability is to the disadvantage of CR. Consequently, we proposed an improved sensing strategy as follows:
Theorem 2.
Given,,and,reaches the maximum, when
Proof.
According to (3), (4) and (18),
Based on (3), (4) and (5), we can get
Thus, monotonically decreases with the internal while it monotonically increases as Finally, obtains the maximum value when
□
Compared with the classical sensing strategy in (9), the main difference between them is shown as follows:
From (21) and (22), According to (3), (4) and (8), When varies from to , the variation percentage for detection probability, the false-alarm probability and achievable throughput in equal weight is approximately defined as
Note that the fall of detection probability is to the disadvantage of protecting PU for a CR while the decline of false alarm probability is beneficial to available throughput of SU. In consequence, we define (26) to compare , and . Considering (23), (24), and (25), (26) can be further written as
Obviously, is far less than , then , .
(29): See Appendix A.
Due to and then
Overall, when (), our proposed sensing strategy (17) is the optimal sensing strategy for a given detection probability, false-alarm probability and achievable throughput. The performance of sensing strategies (17) and (9) are almost the same in terms of their detection probability, false-alarm probability and the achievable throughput of SU, especially when the number of sampling points is large enough.
4. Simulation and Discussion
In this section, simulations based on the MATLAB platform are used to examine the performance of the proposed sensing strategy for SS. The simulation band is conducted at very high frequency (VHF), where the carrier frequency is set as and sampling frequency is An Orthogonal Frequency Division Multiplexing (OFDM) signal is chosen as the test signal (PU) for its generality and popularity in wireless communication networks. Additionally, the sampling point at the receiving terminal of a CR is without special instructions. In the simulation, the OFDM signal is first generated and then white Gaussian noise with mean zero and variance one is added into the OFDM signal. After the sampling and energy normalization of the noise-only case and the signal-plus-noise case, the detection probability and false-alarm probability are calculated by the corresponding energy comparisons with the presupposed threshold. Note that the optimal sensing performance in Figure 1, Figure 2, Figure 3 and Figure 4 is obtained when the corresponding sensing threshold is used, just as analyzed in (9)–(30).
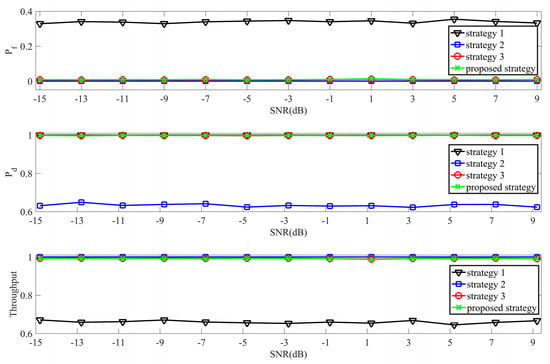
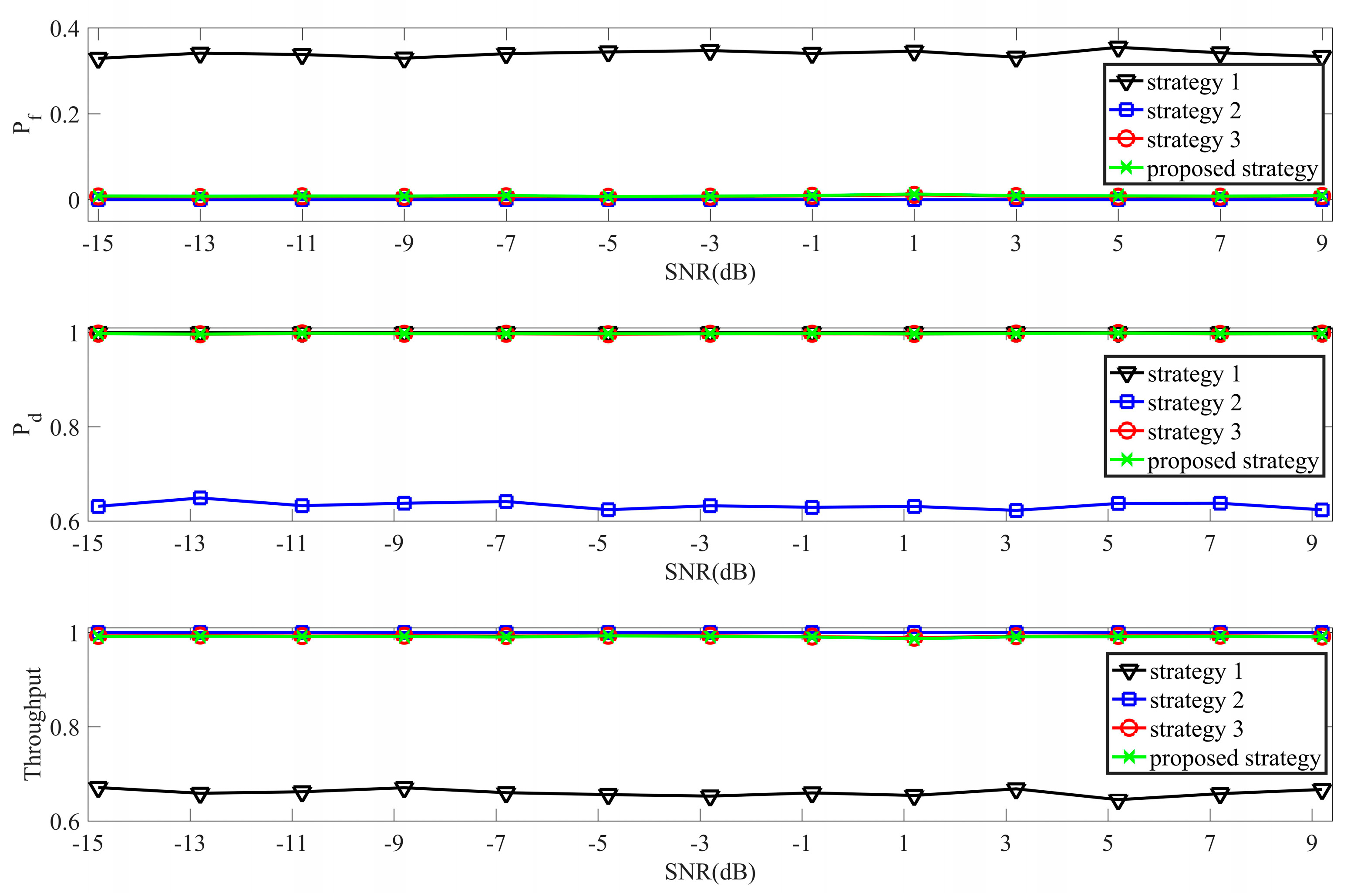
Figure 1.
Comparisons between three classical sensing strategies and the proposed sensing strategy when N = 100.

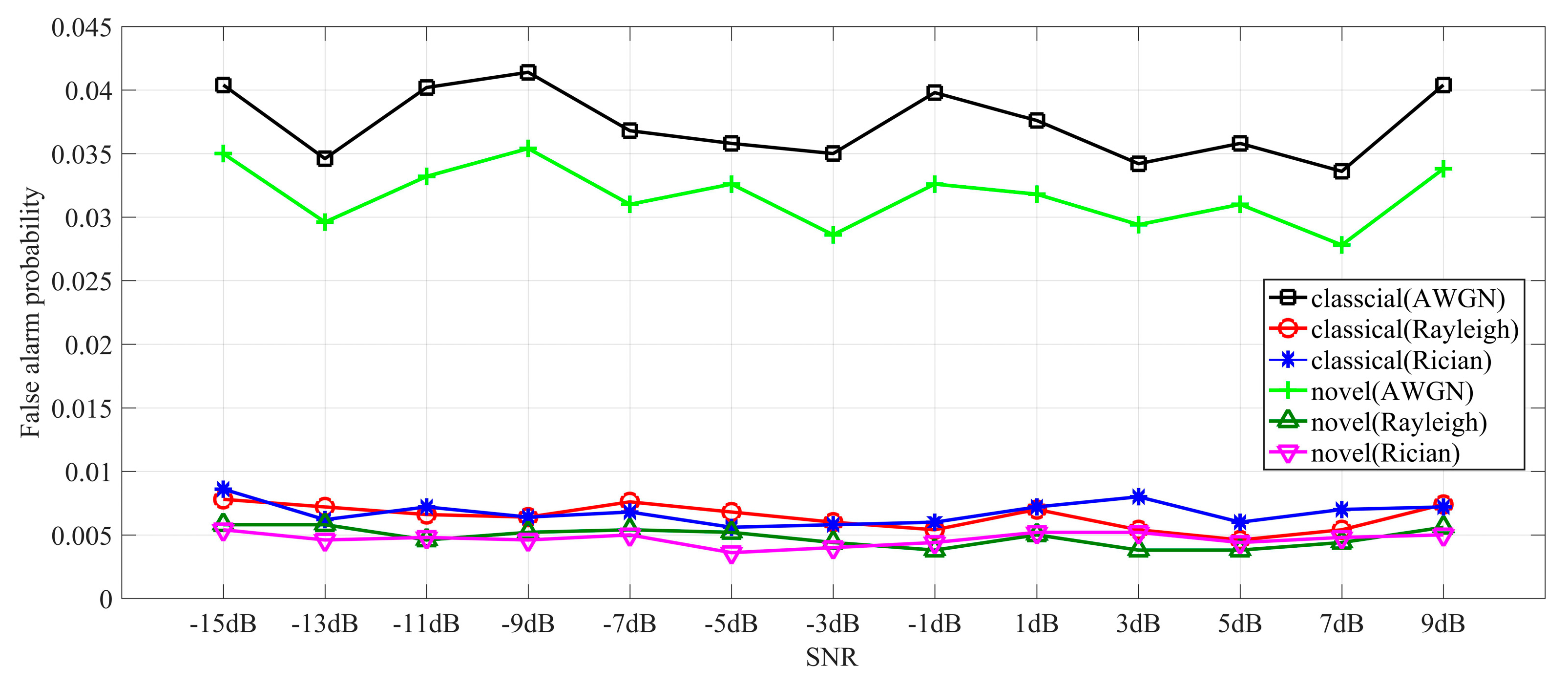
Figure 2.
False-alarm probability comparisons when sensing performance is optimal.
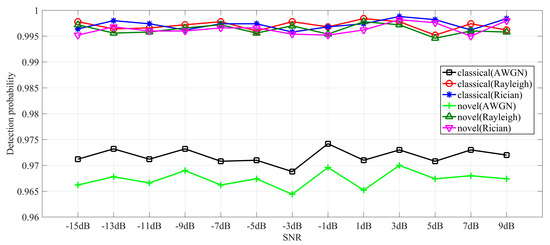
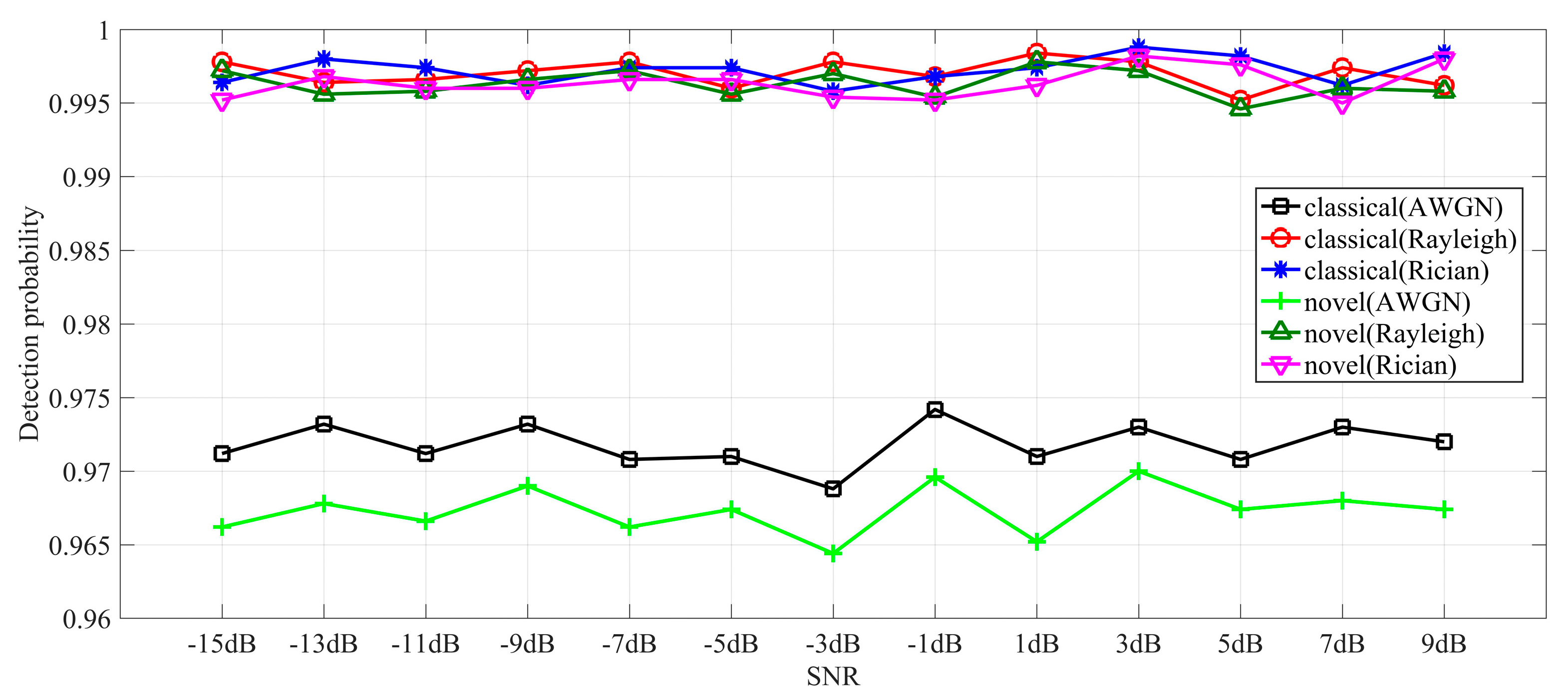
Figure 3.
Detection probability comparisons when sensing performance is optimal.

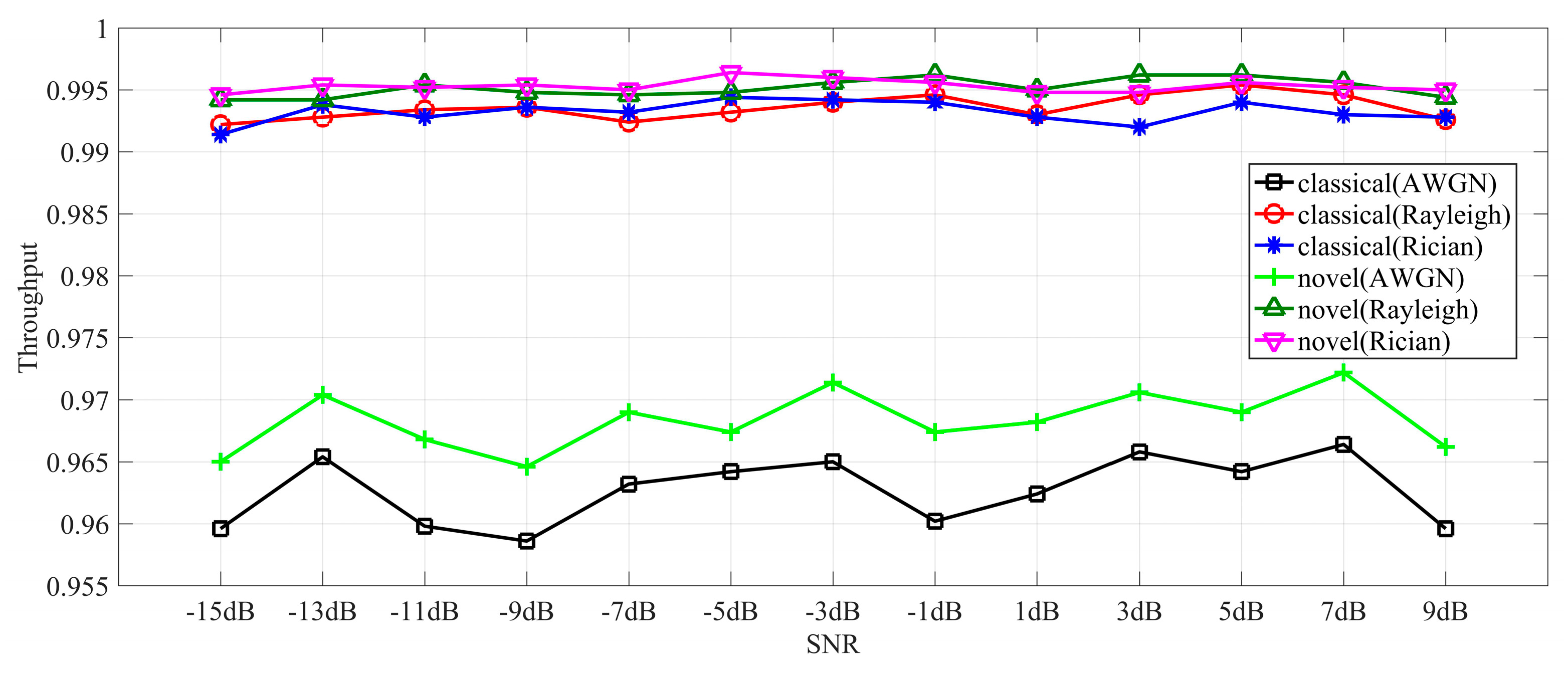
Figure 4.
Throughput comparisons when the sensing performance is optimal.
In Figure 1, we mainly discuss comparisons among three classical sensing strategies and the proposed strategy when the respective optimal sensing performance is obtained (N = 100). Strategies 1–3, respectively, correspond with the one in [28,29,30]. From Figure 1, the false-alarm probability of Sensing Strategy 1 is evidently higher than others while its corresponding throughput is the lowest. Meanwhile, the detection probability of Strategy 2 is dramatically inferior to the other three. Compared with Sensing Strategy 1 and Sensing Strategy 2, Sensing Strategy 3 and the proposed strategy consider both the false-alarm probability and detection probability. These results correspond with the first section of Chapter 3.
Figure 2 exhibits false-alarm comparisons between classical (strategy 3) and proposed sensing strategies in AWGN, Rayleigh, and Rician channels, when the sensing performance is optimal according to Theorem 1 and Theorem 2. Evidently, the proposed sensing strategy appears to have lower false-alarm scores compared with Sensing Strategy 3, which indicates the spectrum sensing scheme with a novel sensing strategy a greater chance of discovering the idle spectrum.
Figure 3 provides detection comparisons between Strategy 3 and the proposed sensing strategy when the sensing performance is optimal. From Figure 3, the detection probability of the spectrum sensing scheme with Sensing Strategy 3 has a greater advantage over the proposed one. This states that the proposed scheme tends to discover a more available idle spectrum, while the classical scheme is specialized in the protection of PU.
An available throughput comparison between classical and proposed sensing strategies is shown in Figure 4 in AWGN, Rayleigh and Rician channels when the sensing performance is optimal. From the standpoint of a secondary network, the CR equipment with the proposed sensing strategy has an increasing capability to communicate with its users compared to a classical sensing strategy. Based on (23)–(30), the proposed strategy has a better sensing performance when considering the detection probability, false-alarm probability and available throughput.
Note that a delay spread nature exists in the process of SS, even if narrow-band-based SS is considered. For narrow-band-based SS, the delay mainly consists in the sampling duration at the receiver of CR. For wide-band-based SS, the delay of SS is the sum of the scanning time over multiple spectrum bands. As a result, the delay in the simulation experiments is because narrow-band-based SS is discussed in the simulations.
5. Conclusions
In this paper, an investigation is carried out on the sensing strategy of spectrum sensing given the detection probability, false-alarm probability and available throughput. On this basis, a novel sensing strategy is proposed and analyzed. Both theoretical derivation and simulative experiments exhibit the effectiveness of the proposed strategy.
Author Contributions
Conceptualization, H.H. and J.M.; methodology, J.Z.; validation, J.Z., H.H. and J.M.; formal analysis, J.M.; investigation, H.H.; data curation, J.Z.; writing-original draft preparation, J.Z.; writing-review and editing, H.H. and J.M.
Funding
This research has been partially funded by the open funding project of State Key Lab of Virtual Reality Technology and Systems at Beihang University, Grant No. VRLAB2018A21.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Proof.
We assume that Because of then According to the , we can get that , , , . is shown in Figure A1.
Based on (26) and (27), we can get
For the purpose of calculation, we assume that
Due to , , then
If we only consider point-to-point transmission in the secondary network, the SNR of this secondary network link can be defined as where is the power of the secondary user and is the power of noise [20]. Suppose both the primary and secondary users are independent, white, Gaussian signals, then . For this case, we only consider the probability for which the primary user is inactive, then and where .
Synthesis of the above assumptions, we can get that . (A6) is equivalent to . □
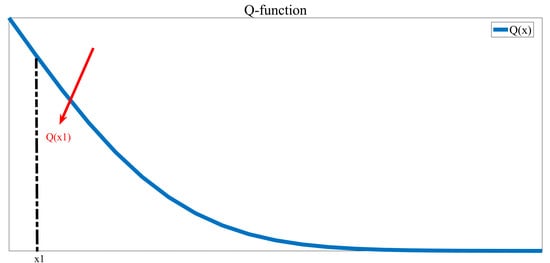
Figure A1.
Q function graph.
Figure A1.
Q function graph.
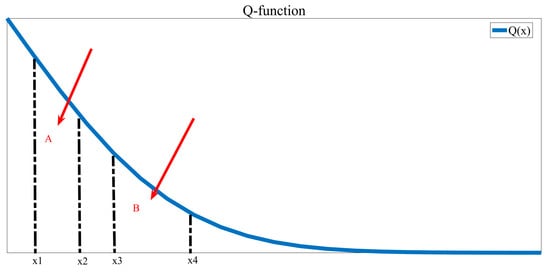
Figure A2.
The diagram of A and B.
Figure A2.
The diagram of A and B.
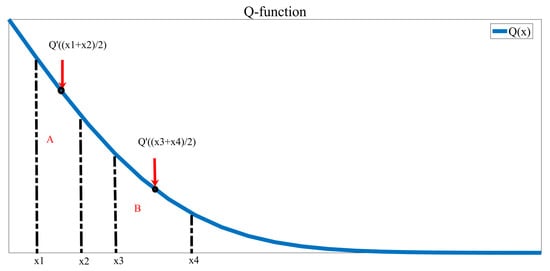
Figure A3.
Approximate schematics of Area A and B
Figure A3.
Approximate schematics of Area A and B
References
- Federal Communications Commission. Spectrum Policy Task Force Report; FCC Document ET Docket No. 02-155; Federal Communications Commission: Washington, DC, USA, 2002. [Google Scholar]
- Rawat, P.; Singh, K.D.; Bonnin, J.M. Cognitive Radio for M2M and Internet of Things: A survey. Comput. Commun. 2016, 94, 1–29. [Google Scholar] [CrossRef]
- Stevenson, C.R.; Chouinard, G.; Lei, Z.; Hu, W.; Shellhammer, S.J.; Caldwell, W. IEEE 802.22: The First Cognitive Radio Wireless Regional Area Network Standard. IEEE Commun. Mag. 2009, 47, 130–138. [Google Scholar] [CrossRef]
- Lee, W.Y.; Akyildiz, I.F. Optimal spectrum sensing framework for cognitive radio networks. IEEE Trans. Wirel. Commun. 2008, 7, 3845–3857. [Google Scholar]
- Ghasemi, A.; Sousa, E.S. Spectrum sensing in cognitive radio networks: Requirements, challenges and design trade-offs. IEEE Commun. Mag. 2008, 46, 32–39. [Google Scholar] [CrossRef]
- Wang, X.; Ekin, S.; Serpedin, E. Joint Spectrum Sensing and Resource Allocation in Multi-Band-Multi-User Cognitive Radio Networks. IEEE Trans. Commun. 2018, 66, 3281–3293. [Google Scholar] [CrossRef]
- Ren, J.; Hu, J.; Zhang, D.; Guo, H.; Zhang, Y.; Shen, X. RF Energy Harvesting and Transfer in Cognitive Radio Sensor Networks: Opportunities and Challenges. IEEE Commun. Mag. 2018, 56, 104–110. [Google Scholar] [CrossRef]
- Chen, Y.; Xiong, Y.; Wang, Q.; Yin, X.; Li, B. Ensuring Minimum Spectrum Requirement in Matching-based Spectrum Allocation. IEEE Trans. Mob. Comput. 2018, 17, 2028–2040. [Google Scholar] [CrossRef]
- Leaves, P.; Moessner, K.; Tafazolli, R.; Grandblaise, D.; Bourse, D.; Tonjes, R.; Breveglieri, M. Dynamic spectrum allocation in composite reconfigurable wireless networks. IEEE Commun. Mag. 2004, 42, 72–81. [Google Scholar] [CrossRef]
- Etkin, R.; Parekh, A.; Tse, D. Spectrum Sharing for unlicensed bands. In Proceedings of the 2nd IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Dublin, Ireland, 17–20 April 2007. [Google Scholar]
- Ranjan, A.; Singh, B. Design and analysis of spectrum sensing in cognitive radio based on energy detection. In Proceedings of the International Conference on Signal and Information Processing, Vishnupuri, India, 6–8 October 2016; pp. 1–5. [Google Scholar]
- Ilyas, I.; Paul, S.; Rahman, A.; Kundu, R.K. Comparative evaluation of cyclostationary detection based cognitive spectrum sensing. In Proceedings of the Ubiquitous Computing, Electronics, and Mobile Communication Conference, New York, NY, USA, 20–22 October 2016; pp. 1–7. [Google Scholar]
- Zeng, Y.; Liang, Y.C. Spectrum-sensing algorithms for cognitive radio based on statistical covariances. IEEE Trans. Veh. Technol. 2009, 58, 1804–1815. [Google Scholar] [CrossRef]
- Ganesan, G.; Li, Y. Cooperative spectrum sensing in cognitive radio networks. In Proceedings of the IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, MD, USA, 8–11 November 2005. [Google Scholar]
- Digham, F.F.; Alouini, M.-S.; Simon, M.K. On the Energy Detection of Unknown Signals Over Fading Channels. IEEE Trans. Commun. 2007, 55, 21–24. [Google Scholar] [CrossRef]
- Kozłowski, S. Implementation and verification of cyclostationary feature detector for DVB-T signals. IET Signal Process. 2016, 10, 162–167. [Google Scholar] [CrossRef]
- Jin, M.; Guo, Q.; Xi, J.; Li, Y.; Yu, Y.; Huang, D. Spectrum Sensing Using Weighted Covariance Matrix in Rayleigh Fading Channels. IEEE Trans. Veh. Technol. 2015, 64, 5137–5148. [Google Scholar] [CrossRef]
- Zhou, X.; Ma, J.; Li, G.Y.; Kwon, Y.H.; Soong, A.C. Probability-based combination for cooperative spectrum sensing. IEEE Trans. Commun. 2010, 58, 463–466. [Google Scholar] [CrossRef]
- Letaief, K.B.; Wei, Z. Cooperative Spectrum Sensing. In Cognitive Wireless Communication Networks; Springer: Berlin, Germany, 1970. [Google Scholar]
- Li, Z.; Yu, F.R.; Huang, M. A Distributed Consensus-Based Cooperative Spectrum-Sensing Scheme in Cognitive Radios. IEEE Trans. Veh. Technol. 2010, 59, 383–393. [Google Scholar]
- Tong, J.; Jin, M.; Guo, Q.; Li, Y. Cooperative Spectrum Sensing: A Blind and Soft Fusion Detector. IEEE Trans. Wirel. Commun. 2018, 17, 2726–2737. [Google Scholar] [CrossRef]
- Maleki, S.; Leus, G.; Chatzinotas, S.; Ottersten, B. To AND or To OR: On Energy-Efficient Distributed Spectrum Sensing with Combined Censoring and Sleeping. IEEE Trans. Wirel. Commun. 2015, 14, 4508–4521. [Google Scholar] [CrossRef]
- Umebayashi, K.; Lehtomaki, J.J.; Yazawa, T.; Suzuki, Y. Efficient Decision Fusion for Cooperative Spectrum Sensing Based on OR-rule. IEEE Trans. Wirel. Commun. 2012, 11, 2585–2595. [Google Scholar] [CrossRef]
- Nallagonda, S.; Bandari, S.K.; Roy, S.D.; Kundu, S. Cooperative spectrum sensing with censoring of cognitive radios in presence of log-normal shadowing under majority logic fusion. In Proceedings of the International Conference on Communications, Kolkata, India, 28–29 December 2012. [Google Scholar]
- Yang, G.; Wang, J.; Luo, J.; Wen, O.Y.; Li, H.; Li, Q.; Li, S. Cooperative Spectrum Sensing in Heterogeneous Cognitive Radio Networks Based on Normalized Energy Detection. IEEE Trans. Veh. Technol. 2016, 65, 1452–1463. [Google Scholar] [CrossRef]
- Mamidi, R.; Sundru, A. Throughput Analysis in Proposed Cooperative Spectrum Sensing Network with an Improved Energy Detector scheme over Rayleigh Fading Channel. AEU Int. J. Electron. Commun. 2017, 83, 416–426. [Google Scholar] [CrossRef]
- Al Hammadi, A.; Alhussein, O.; Sofotasios, P.C.; Muhaidat, S.; Al-Qutayri, M.; Al-Araji, S.; Karagiannidis, G.K.; Liang, J. Unified Analysis of Cooperative Spectrum Sensing over Composite and Generalized Fading Channels. IEEE Trans. Veh. Technol. 2015, 65, 6949–6961. [Google Scholar] [CrossRef]
- Pandit, S.; Singh, G. Spectrum Sensing in Cognitive Radio Networks: Potential Challenges and Future Perspective. In Spectrum Sharing in Cognitive Radio Networks; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Peh EC, Y.; Liang, Y.C.; Guan, Y.L. Optimization of Cooperative Sensing in Cognitive Radio Networks: A Sensing-Throughput Tradeoff View. IEEE Trans. Veh. Technol. 2009, 58, 5294–5299. [Google Scholar] [CrossRef]
- Zhang, W.; Mallik, R.K.; Letaief, K. Cooperative Spectrum Sensing Optimization in Cognitive Radio Networks. In Proceedings of the IEEE International Conference on Communications, Berjing, China, 19–23 May 2008; pp. 3411–3415. [Google Scholar]
- Zhang, D.; Chen, Z.; Ren, J.; Zhang, N.; Awad, M.K.; Zhou, H.; Shen, X.S. Energy Harvesting-Aided Spectrum Sensing and Data Transmission in Heterogeneous Cognitive Radio Sensor Network. IEEE Trans. Veh. Technol. 2016, 66, 831–843. [Google Scholar] [CrossRef]
- Liang, Y.C.; Zeng, Y.; Peh, E.C.; Hoang, A.T. Sensing-Throughput Tradeoff for Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2008, 7, 1326–1337. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).