False Image Injection Prevention Using iChain
Abstract
1. Introduction
- Introduction of false image injection attack (FIIA);
- Critical analysis of image tampering detection techniques; and
- Blockchain-based security framework, iChain to prevent FIIA.
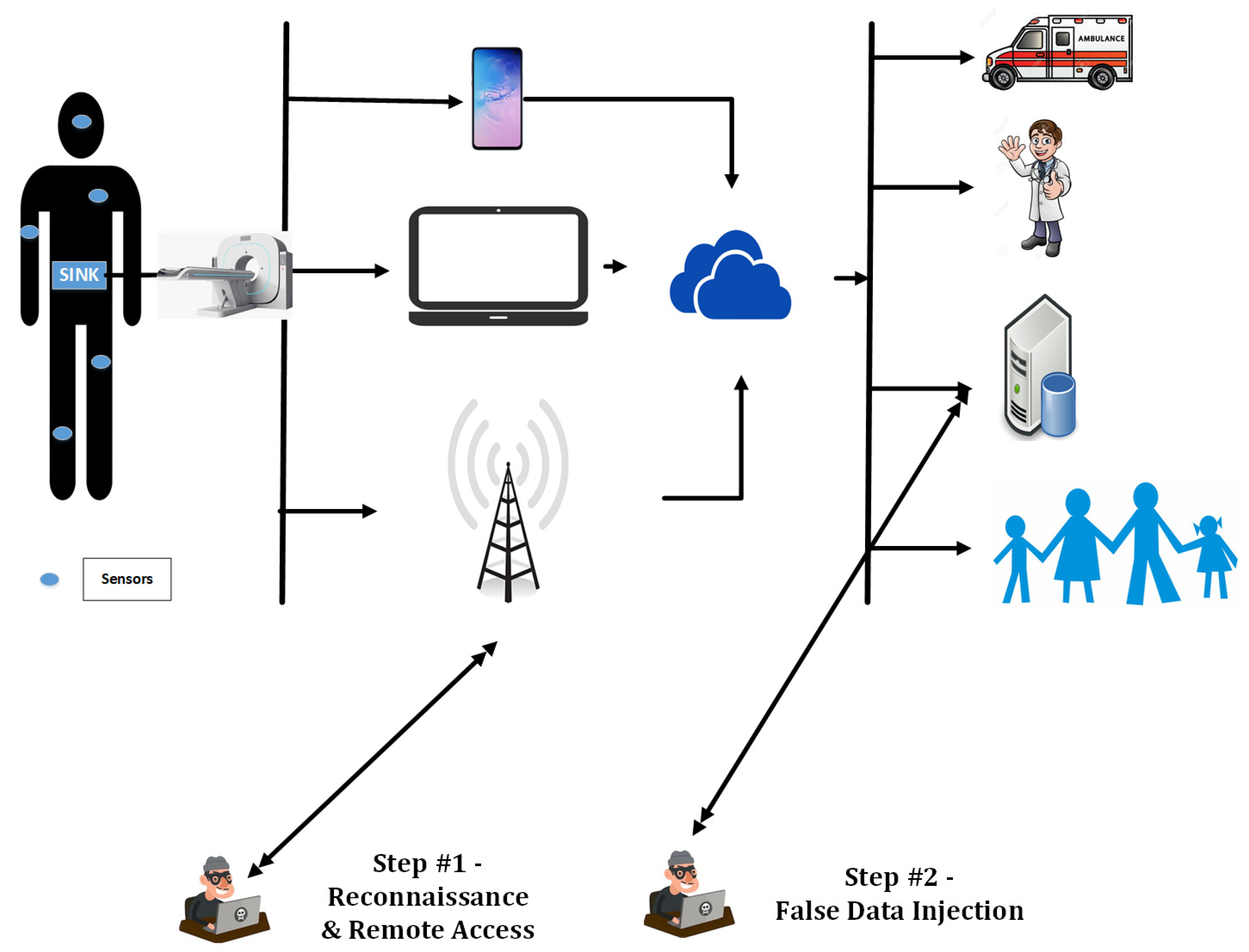
2. False Image Injection Attacks
- Original image vector,
- Observed image vector, {, , …, }
- False image vector,
- = I + a; when .
- Counterfeit insurance claim: Injecting false imaging records may cause the insurance provider to pay unnecessarily as the patient data is not legitimate [7]. For example, if a cyber attacker, injects a false image for a surgery which is supposed to be covered by insurance, then the beneficiary will get paid without having any surgery.
- Emergency situations: While a complicated tele-surgery is going on and the physicians are dependent on the real time images, even a slight variation of these images (as a consequence of FIIA) can lead to loss of life [7].
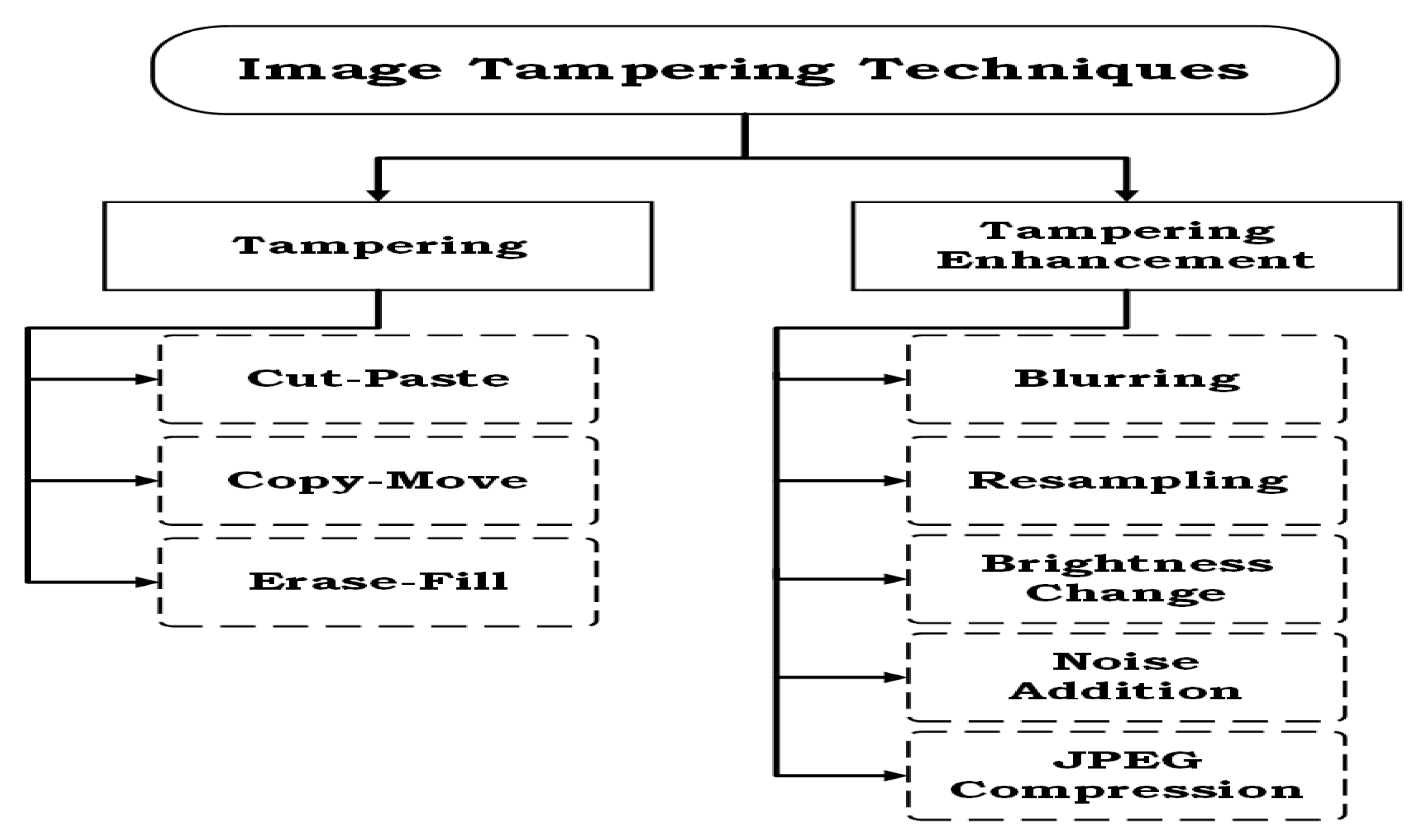
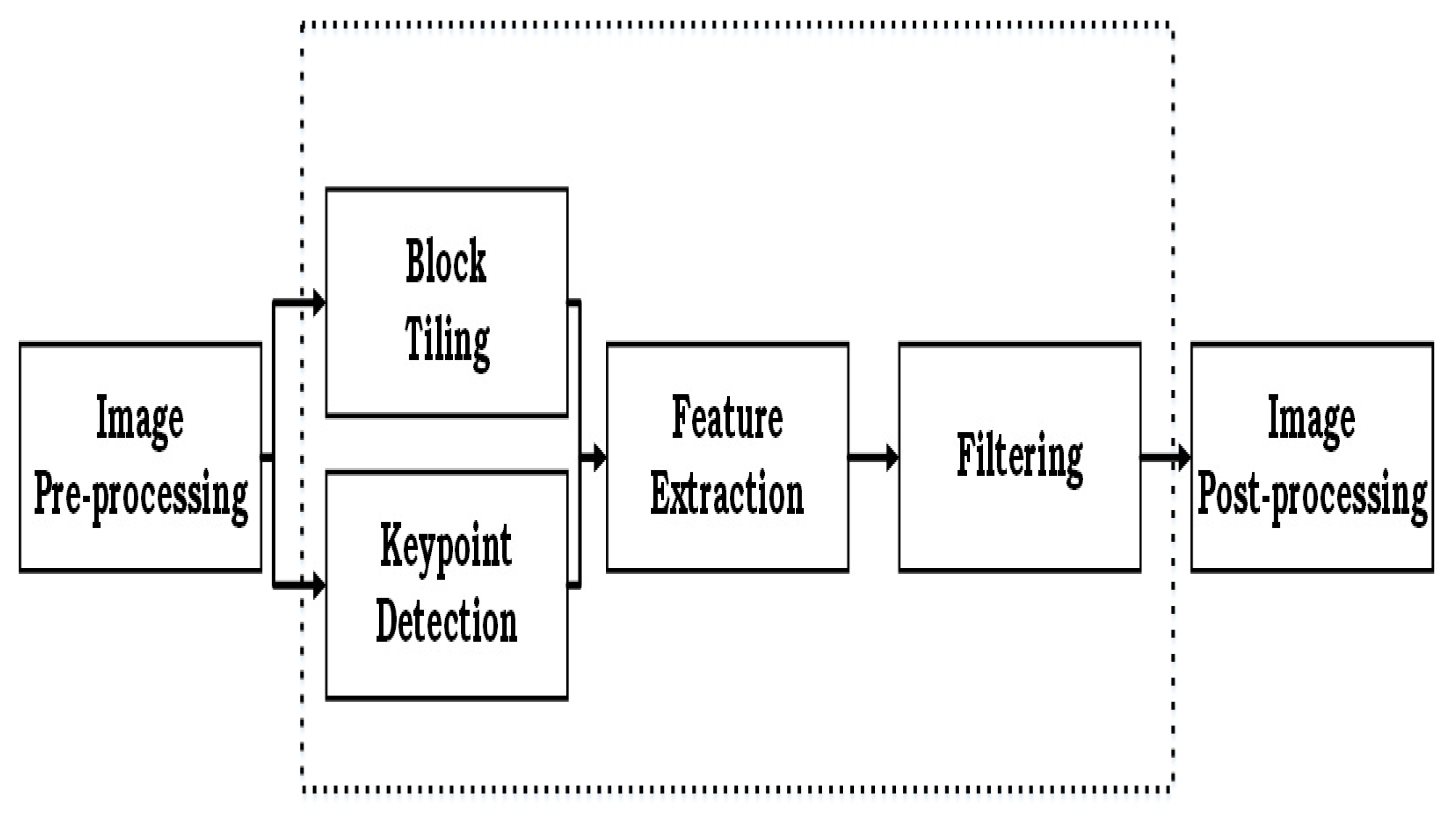
3. Critical Analysis of Image Tampering Detection Techniques
4. Blockchain: Panacea to Cyber Crime
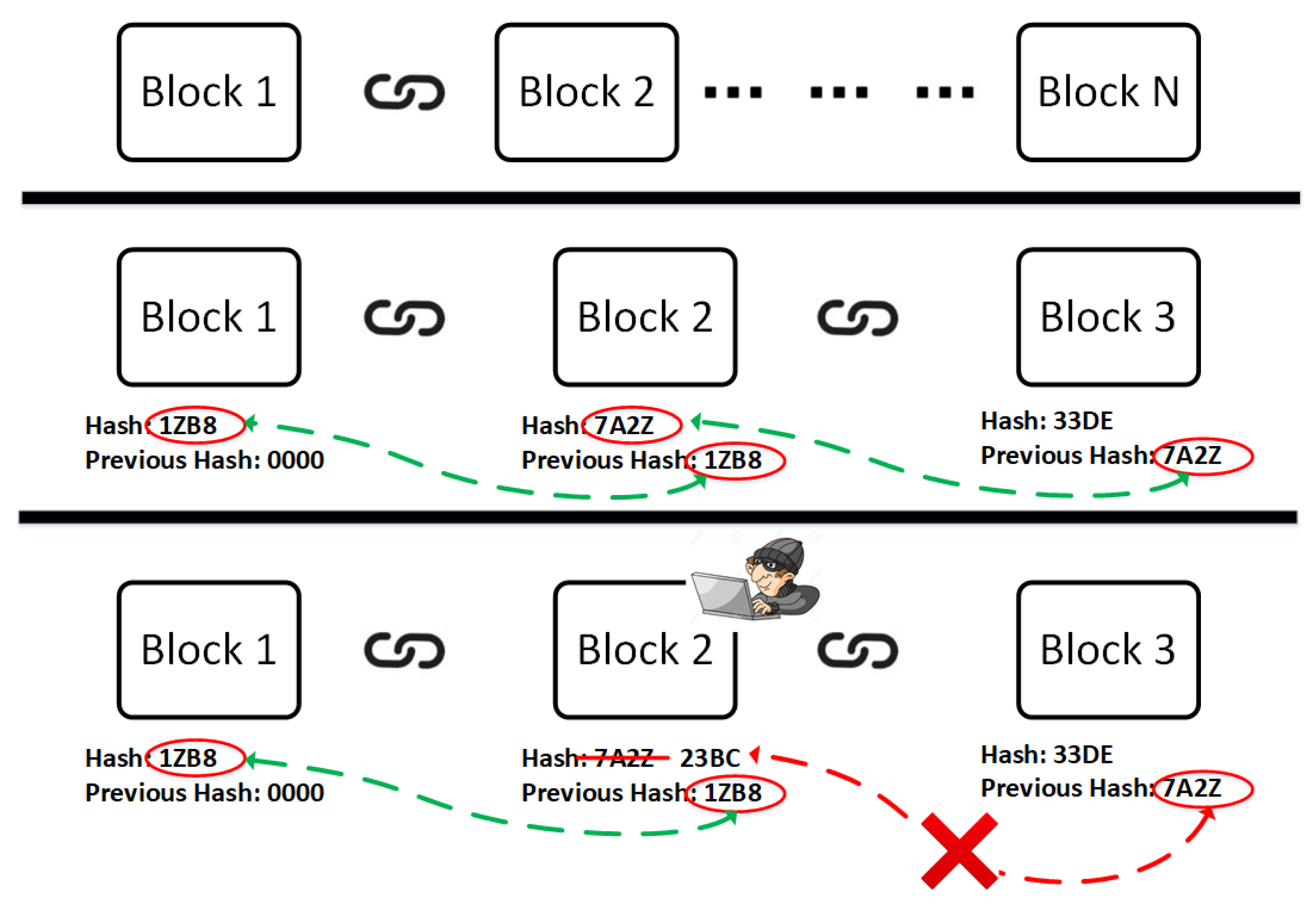
- Hash: A hash algorithm changes arbitrary data into a definite length hash. Any change in the original data results in a different hash value. Therefore, it makes falsification difficult in blockchain. Every new block creation utilizes the calculation of a hash value for creating a new block or transactions as well. Blockchain adopts this security mechanism to generate random hash values for data storage and authentication [17].
- Block: A block is the data storage facilitator of a transaction. A block is thus a permanent store of records, which, once written, cannot be altered or removed. If we make a comparison with a common record keeping style it is a page of a ledger, we only go to the next page of a ledger when it finishes. Similarly, a block indicates a current transaction and when the next block is created that one becomes the latest one. Each time a block is ‘completed’, it gives way to the next block in the blockchain. There is no maximum number of blocks, it will continue to grow as long as people use it for transactions. It has three parts: header, transaction counter, and block content [17].
- Digital signature: The digital signature was first used by D Johnson [18]. A digital signature is a procedure to prove the authenticity of the blockchain transmission. It mainly contains a public and private key to provide a double layer protection of transaction information. Signing phase and verification phase are two steps needed for this verification. The private key is reserved for personal transactions, and the public key is shared globally. In the signing part, one encrypts data with the private key and sends the original data with encryption. In the verification part, the receiver can easily check the validity of the received data with the sender’s public key. When the sender sends the data and hash value, on the other hand, the receiver can verify that the information was actually generated from the hash and the private key of the sender [17].
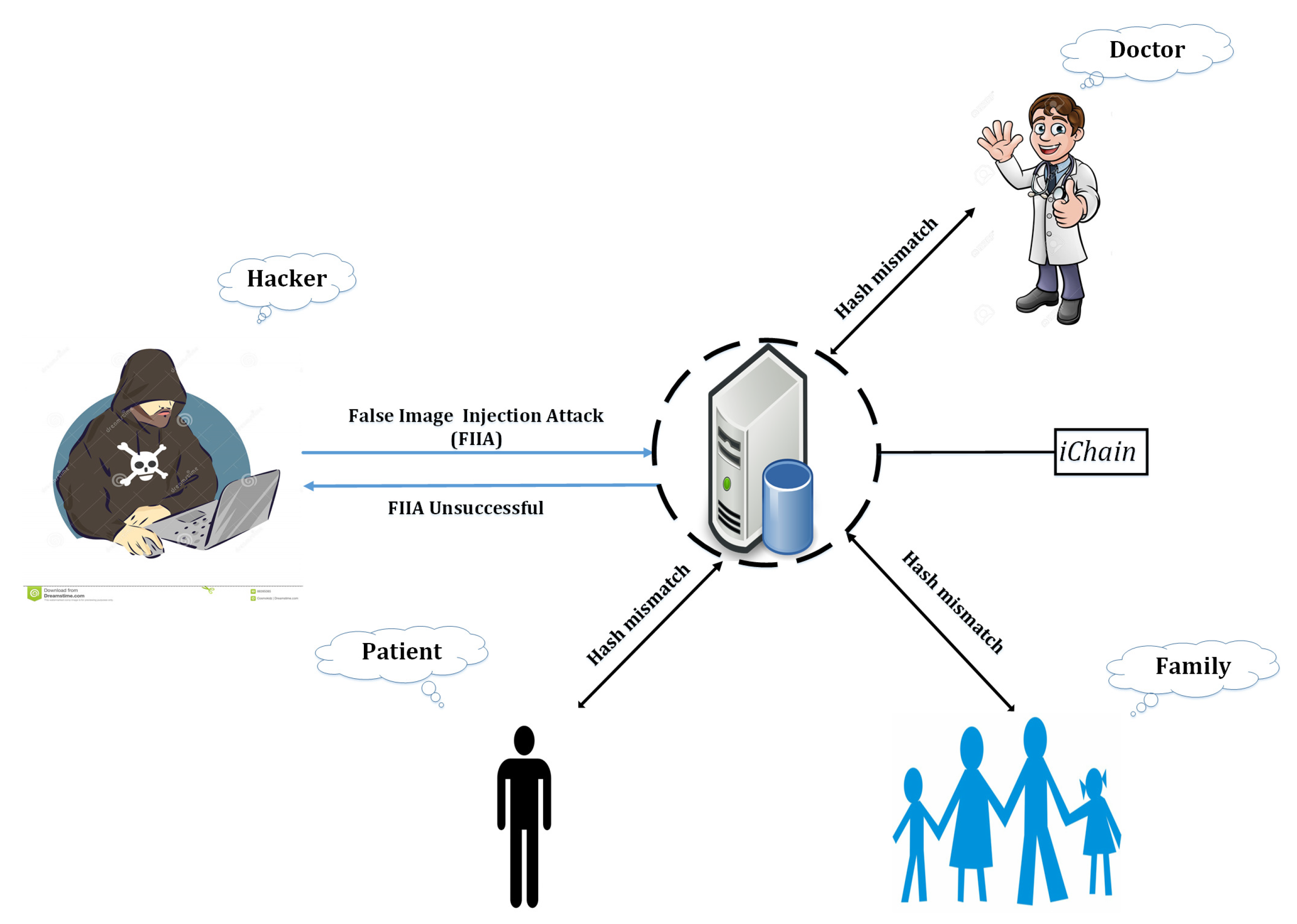
5. Image Chain (iChain) to Prevent False Image Injection Attacks
| Algorithm 1:iChain Algorithm |
 |
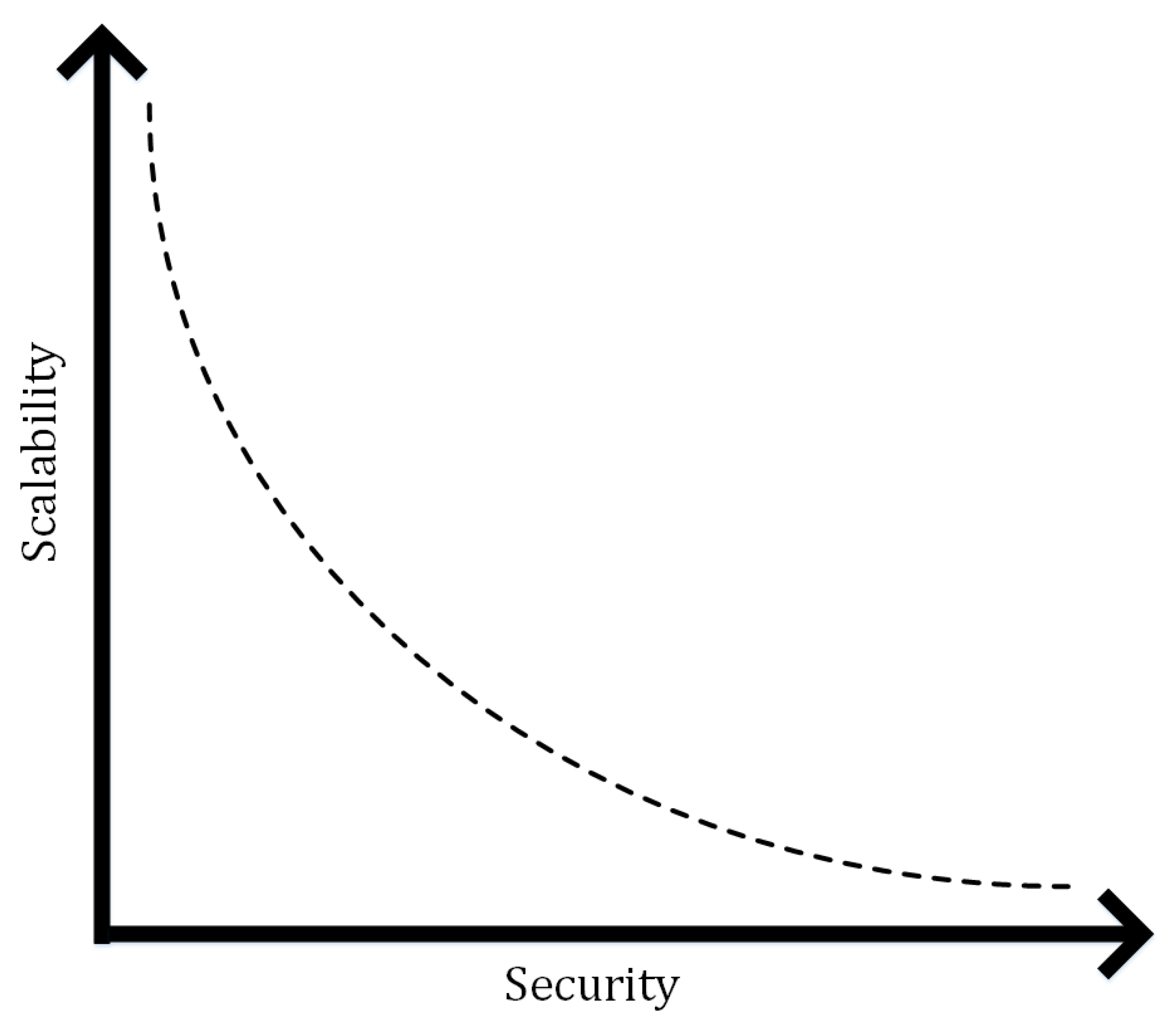
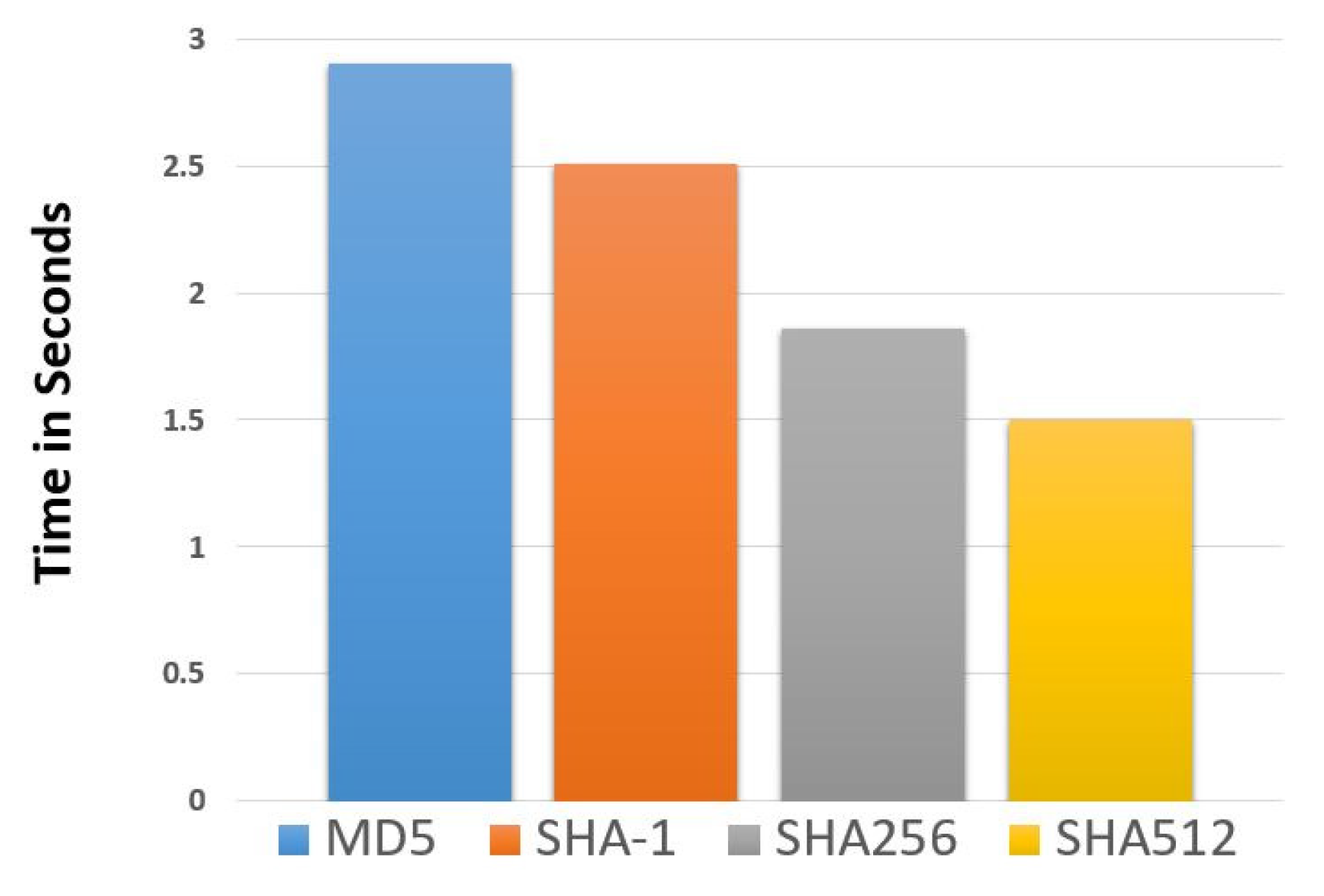
6. Evaluation
7. Conclusions and Future Research
- How ethical hacking tools can be utilised to identify vulnerabilities of blockchain based frameworks?
- How to inject software vulnerabilities or malware into blockchains?
- How to address the scalability of the blockchain based security framework used in implanted medical devices such as pacemakers, CRT-D (Cardiac resynchronization therapy devices) etc.?
Funding
Acknowledgments
Conflicts of Interest
References
- Ahmed, M.; Mahmood, A.N.; Hu, J. Outlier Detection. In The State of the Art in Intrusion Prevention and Detection; Pathan, A.-S.K., Ed.; CRC Press: New York, NY, USA, 2014; Chapter 1; pp. 3–21. [Google Scholar]
- Ahmed, M.; Mahmood, A.N.; Hu, J. A survey of network anomaly detection techniques. J. Netw. Comput. Appl. 2016, 60, 19–31. [Google Scholar] [CrossRef]
- Ahmed, M.; Mahmood, A.N.; Islam, M.R. A survey of anomaly detection techniques in financial domain. Future Gen. Comput. Syst. 2016, 55, 278–288. [Google Scholar] [CrossRef]
- Ahmed, M. Thwarting dos attacks: A framework for detection based on collective anomalies and clustering. Computer 2017, 50, 76–82. [Google Scholar] [CrossRef]
- Ahmed, M.; Ullah, A.S.S.M.B. False data injection attacks in healthcare, In Australasian Conference on Data Mining 2017; Boo, Y.L., Stirling, D., Chi, L., Liu, L., Ong, K.-L., Williams, G., Eds.; Springer: Singapore, 2018; pp. 192–202. [Google Scholar]
- Ahmed, M.; Anwar, A.; Mahmood, A.N.; Shah, Z.; Maher, M.J. An investigation of performance analysis of anomaly detection techniques for big data in scada systems. EAI Endorsed Trans. Ind. Netw. Intell. Syst. 2015, 15, 5. [Google Scholar] [CrossRef][Green Version]
- Aiello, M.; Cavaliere, C.; D’Albore, A.; Salvatore, M. The challenges of diagnostic imaging in the era of big data. J. Clin. Med. 2019, 8, 316. [Google Scholar] [CrossRef]
- Stanford Medicine 2018 Health Trends Report; Stanford School of Medicince: Stanford, CA, USA, 2018.
- Klonoff, D.C. Cybersecurity for connected diabetes devices. J. Diabetes Sci. Technol. 2015, 9, 1143–1147. [Google Scholar] [CrossRef]
- Pycroft, L.; Aziz, T.Z. Security of implantable medical devices with wireless connections: The dangers of cyber-attacks. Expert Rev. Med. Dev. 2018, 15, 403–406. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A review on the use of blockchain for the internet of things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Zheng, L.; Zhang, Y.; Thing, V.L. A survey on image tampering and its detection in real-world photos. J. Vis. Commun. Image Represent. 2019, 58, 380–399. [Google Scholar] [CrossRef]
- Pouyanfar, S.; Sadiq, S.; Yan, Y.; Tian, H.; Tao, Y.; Reyes, M.P.; Shyu, M.-L.; Chen, S.-C.; Iyengar, S.S. A survey on deep learning: Algorithms, techniques, and applications. ACM Comput. Surv. 2018, 51, 92. [Google Scholar] [CrossRef]
- Ahmed, M.; Pathan, A.S.K. Investigating deep learning for collective anomaly detection—An experimental study. In Proceedings of the Sixth International Symposium on Security in Computing and Communications (SSCC 2018), Bangalore, India, 19–22 September 2018; Volume 969. [Google Scholar]
- Rao, Y.; Ni, J. A deep learning approach to detection of splicing and copy-move forgeries in images. In Proceedings of the 2016 IEEE International Workshop on Information Forensics and Security (WIFS), Abu Dhabi, UAE, 4–7 December 2016; pp. 1–6. [Google Scholar]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of blockchains in the internet of things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2018, 21, 1676–1717. [Google Scholar] [CrossRef]
- Hassan, M.; Ahmed, M. Blockchain in the era of Industry 4.0. In Data Analytics: Concepts, Techniques, and Applications; Ahmed, M., Pathan, A.S.K., Eds.; CRC Press: New York, NY, USA, 2018; Chapter 10; pp. 235–273. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ecdsa). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Siyal, A.A.; Junejo, A.Z.; Zawish, M.; Ahmed, K.; Khalil, A.; Soursou, G. Applications of blockchain technology in medicine and healthcare: Challenges and future perspectives. Cryptography 2019, 3, 3. [Google Scholar] [CrossRef]
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.R. Blockchain: A panacea for healthcare cloud-based data security and privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- Aggarwal, S.; Chaudhary, R.; Aujla, G.S.; Kumar, N.; Choo, K.-K.R.; Zomaya, A.Y. Blockchain for smart communities: Applications, challenges and opportunities. J. Netw. Comput. Appl. 2019, 144, 13–48. [Google Scholar] [CrossRef]
- Banerjee, M.; Lee, J.; Choo, K.-K.R. A blockchain future for internet of things security: A position paper. Digit. Commun. Netw. 2018, 4, 149–160. [Google Scholar] [CrossRef]
- Yang, J.; Hassan, M.; Lee, N.-Y.; Ahmed, M.; Kim, C.-S. Proof-of-Familiarity: A Privacy-Preserved Blockchain Scheme for Collaborative Medical Decision-Making. Appl. Sci. 2019, 9, 1370. [Google Scholar] [CrossRef]
- Ye, C.; Li, G.; Cai, H.; Gu, Y.; Fukuda, A. Analysis of Security in Blockchain: Case Study in 51%-Attack Detecting. In Proceedings of the 2018 5th International Conference on Dependable Systems and Their Applications (DSA), Dalian, China, 22–23 September 2018; Volume 4, pp. 15–24. [Google Scholar]
- Christlein, V.; Riess, C.; Jordan, J.; Riess, C.; Angelopoulou, E. An evaluation of popular copy-move forgery detection approaches. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1841–1854. [Google Scholar] [CrossRef]
- Al-Qershi, O.M.; Khoo, B.E. Passive detection of copy-move forgery in digital images: State-of-the-art. Forensic Sci. Int. 2013, 231, 284–295. [Google Scholar] [CrossRef]
- Ng, T.-T.; Chang, S.-F.; Sun, Q. Blind detection of photomontage using higher order statistics. IEEE Int. Symp. Circuits Syst. (ISCAS) 2004, 5, V. [Google Scholar]
- Cozzolino, D.; Gragnaniello, D.; Verdoliva, L. Image forgery localization through the fusion of camera-based, feature-based and pixel-based techniques. In Proceedings of the 2014 IEEE International Conference on Image Processing (ICIP), Paris, France, 27–30 October 2014; pp. 5302–5306. [Google Scholar]
- Zhang, P.; White, J.; Schmidt, D.C.; Lenz, G.; Rosenbloom, S.T. Fhirchain: Applying blockchain to securely and scalably share clinical data. Comput. Struct. Biotechnol. J. 2018, 16, 267–278. [Google Scholar] [CrossRef] [PubMed]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 136. [Google Scholar] [CrossRef] [PubMed]
- Tseng, J.-H.; Liao, Y.-C.; Chong, B.; Liao, S.-W. Governance on the drug supply chain via gcoin blockchain. Int. J. Environ. Res. Public Health 2018, 15, 1055. [Google Scholar] [CrossRef]
- Esmaeilzadeh, P.; Mirzaei, T. The potential of blockchain technology for health information exchange: Experimental study from patients’ perspectives. J. Med. Internet Res. 2019, 21, e14184. [Google Scholar] [CrossRef] [PubMed]
- Dubovitskaya, A.; Xu, Z.; Ryu, S.; Schumacher, M.; Wang, F. Secure and trustable electronic medical records sharing using blockchain. AMIA Annu. Symp. Proc. 2017, 2017, 650–659. [Google Scholar] [PubMed]

| Technique | FIIA Countermeasure | Privacy | Complexity | Learning |
|---|---|---|---|---|
| Deep Learning [15] | × | × | High | Supervised |
| Keypoint Features [25,26] | × | × | High | Supervised |
| Support Vector Machine [27] | × | × | High | Supervised |
| Pixel Feature [28] | × | × | High | Supervised |
| iChain | ✓ | ✓ | Medium | Unsupervised |
| Type | User | Cost | Security | Architecture | Privacy |
|---|---|---|---|---|---|
| Public | Crypto Traders | High | High | Decentralized | Medium |
| Private | Government | Medium | Medium | Partially Decentralized | High |
| Hybrid | Private Sector | Low | Medium | Partially Decentralized | High |
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmed, M. False Image Injection Prevention Using iChain. Appl. Sci. 2019, 9, 4328. https://doi.org/10.3390/app9204328
Ahmed M. False Image Injection Prevention Using iChain. Applied Sciences. 2019; 9(20):4328. https://doi.org/10.3390/app9204328
Chicago/Turabian StyleAhmed, Mohiuddin. 2019. "False Image Injection Prevention Using iChain" Applied Sciences 9, no. 20: 4328. https://doi.org/10.3390/app9204328
APA StyleAhmed, M. (2019). False Image Injection Prevention Using iChain. Applied Sciences, 9(20), 4328. https://doi.org/10.3390/app9204328





