Efficient Conjunctive Keywords Search over Encrypted E-Mail Data in Public Key Setting
Abstract
:1. Introduction
- (1)
- Based on the keyword conversion method introduced in Reference [10], we create a novel keyword conversion method which can change the index and query keyword set into an attribute and a predicate vector, respectively. The dimension of vector generated by using our method is much less than that generated by adopting the previous method. Through applying the existing technique called bilinear map to encrypt the attribute and predicate vectors, our scheme achieves a better performance in time and space complexities than the previous schemes.
- (2)
- For security concern, we give a detailed proof to demonstrate that our scheme is secure against chosen keyword attack. Moreover, inspired by the idea introduced in Reference [11], through sharing a secret number between the senders and the receiver, our scheme can limit the capability of index building for adversaries. If the adversaries fail to generate the index, the adversaries cannot launch the keyword guessing attack. Compared with the previous schemes, our scheme can both defend against chosen keyword attack and keyword guessing attack.
2. Related Work
3. Preliminaries
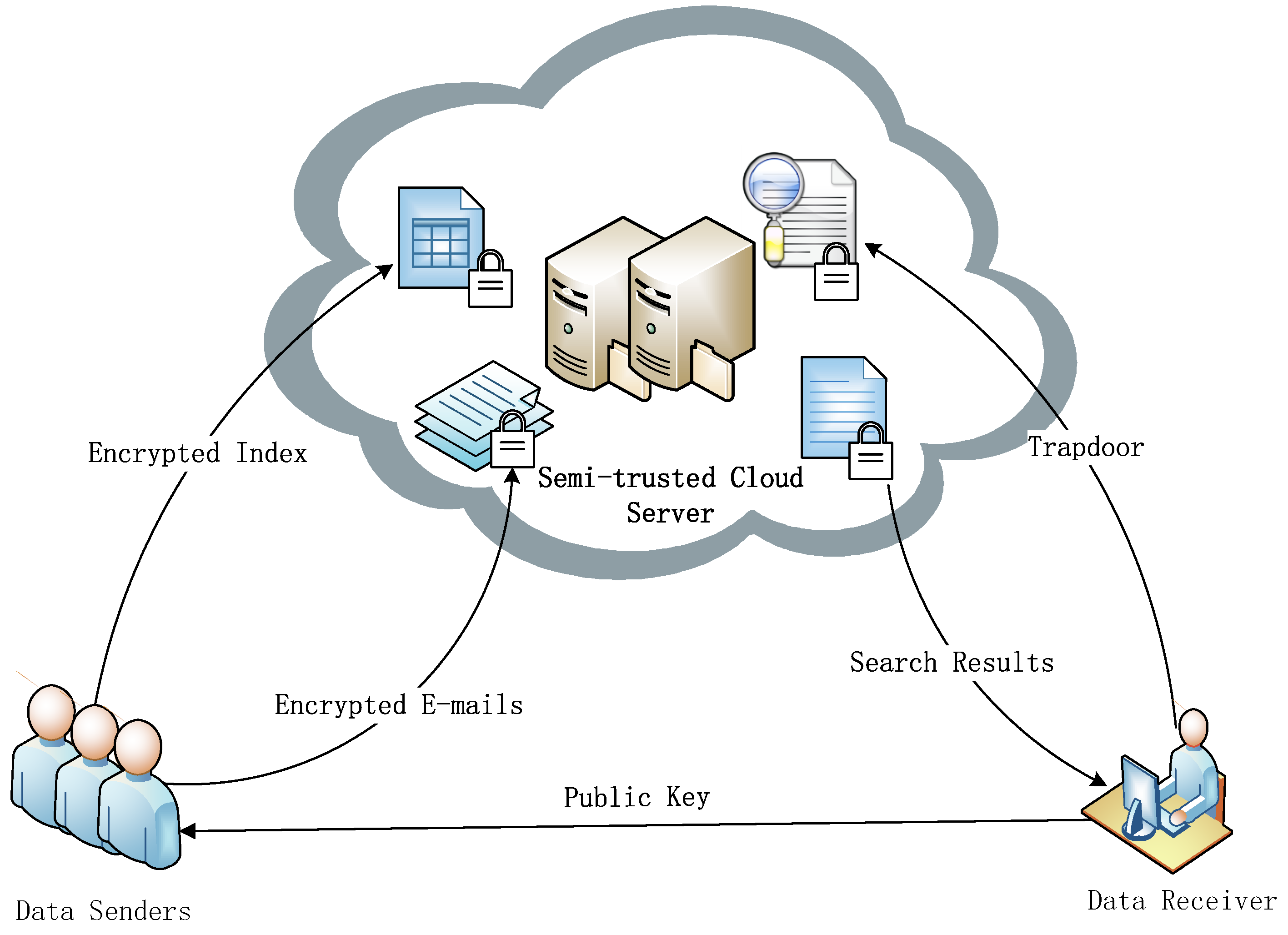
3.1. Model of Spe-Cks
- 1.
- (): Given a security parameter , the algorithm is executed by the receiver and generates the a pair of key , where and are the public and private key for the receiver, respectively.
- 2.
- (): This is a key generation algorithm for the data sender. The algorithm creates a pair of key , where and are the public and private key for the sender, respectively.
- 3.
- IndexBuild(, , , W): The algorithm is executed by the sender to encrypt a keyword set without keyword field. It produces a searchable index of W by using the keys , and .
- 4.
- Trapdoor(, , , Q): The algorithm is executed by the receiver to construct a trapdoor. Given the keys , , and the keyword query where , the algorithm generates a trapdoor .
- 5.
- Test(, , , ): The algorithm is executed by the server to test the trapdoor whether matches the index or not. It takes a trapdoor , a secure index and the public keys as input, then outputs 1 if or 0 otherwise.
3.2. Security Definition of Spe-Cks
- Setup: the challenger runs the () and () algorithms to generate , , and and gives and to the attacker .
- Phase 1: the attacker can adaptively ask the challenger for the trapdoor for any query Q of his choice. Moreover, can adaptively ask for the encrypted index for any keyword set of his choice.
- Challenge: selects a target keyword set and sends it to the . selects a random keyword set R. The restrictions are that the secure indices of and R have not been obtained in the previous phase and the trapdoor queried in previous phase can not distinguish from R. Then, picks a random bit . Suppose that and , produces and sends to .
- Phase 2: can continue asking for trapdoor and index for any query Q and keyword set W of his choice. The restrictions in this phase are the same as that in the challenge phase.
- Response:the attacker outputs and wins the game if .
3.3. Bilinear Map
- Bilinear: , where and ;
- Non-degenerate: does not send all pairs of points in to the identity in . If g is a generator of then is a generator of ;
- Computable: There is an efficient algorithm to compute , for any .
3.4. Complexity Assumption
4. Proposed Spe-Cks Scheme
4.1. Keyword Conversion Method
- (1)
- For an index keyword set , the following function is given.The coefficients of the can be built as an index vector .
- (2)
- For an query keyword set , a vector can be obtained, where and .
4.2. Construction
- -
- (): Given a security parameter , the algorithm generates three cyclic groups G, , of prime order q and an admissible bilinear pairing and picks a random generator of G, a random generator g of and two hash functions and . and g are open to the public. Choosing random numbers , it outputs the public key and the secret key .
- -
- (, ): Given a security parameter , the algorithm generates a hash function . Randomly choosing a number , it outputs and .
- -
- (, , , W): The algorithm first computes . Then, given a keyword set , the algorithm constructs a n-degree polynomial by using the keyword conversion method mentioned in Section 4.1, where are n roots of the equation . Given a random numbers r and the coefficient of that is , it computes for each by using . Let and , the index of the keyword set W is: .
- -
- (, , , Q): The algorithm computes . Given a keyword set , it selects a random number and computes for each by using . Let , the trapdoor for the keyword query Q is .
- -
- (, , , ): Given a trapdoor and a secure index , the algorithm computes , and tests if . If so, outputs 1; otherwise, outputs 0.
4.3. Security Proof
- -
- Setup: Algorithm works as follows:
- Algorithm randomly chooses random numbers and computes .
- computes and . Since , gets where . Then stores the pairs in a list named S-list where .
- computes and sets . Obviously, if , then it has .
- randomly chooses numbers and computes . Let , constructs for each . randomly chooses a and a number and then computes . After that, gives the public key to . The corresponding private key unknown to is .
- randomly chooses a number and sets . generates a hash function . After that, outputs and keeps secret.
- -
- queries: Algorithm can query the random oracles or at any time. To respond to queries, algorithm maintains a list of tuples called list which is initially empty. generates by using the keys . When queries the random oracle at a point , algorithm responds as follows:queries:
- If the query already appears on the -list in a tuple , algorithm responds with , where .
- Otherwise, generates a random coin so that .
- If , set . Otherwise, picks a random and sets .
- adds the tuple to the -list. responds with .
The queries is similar to queries. To respond to queries from , algorithm maintains a list of tuples called list which initially empty. When queries the random oracle at a point , algorithm responds as follows:queries:- If the query already appears on the -list in a tuple , then algorithm responds with , where .
- Otherwise, picks a random and sets .
- adds the tuple to the -list and responds with .
- -
- Index queries: For any keyword set in which , when asks for the secure index of , responds as follows:
- runs queries algorithm to obtain such that where . Let be the corresponding tuples on the -list. If for all , then reports failure and terminates.
- Otherwise, by using , adopts the keyword conversion method in Section 4.1 to generate a vector . Following the algorithm in Section 4.2, generates the secure index by using .
- -
- Trapdoor queries: When issues a query for the trapdoor corresponding to the keyword query where , algorithm responds as follows:
- Algorithm runs queries algorithm to obtain such that where . Let be the corresponding tuples on the -list. If for all , then reports failure and terminates.
- Otherwise, by using and , constructs the trapdoor for query . computes: and , which are satisfied with the equality . Moreover, constructs which is satisfied with the equality for each . Obviously, is a trapdoor for keyword query .
- Through searching the S-list to obtain the tuple , sends to as the correct trapdoor for the query .
- -
- Challenge: Algorithm produces a target keyword set which it wants to challenge on and sends to . Algorithm chooses a random keyword set R and sets , . The only restriction is that the trapdoor queried in previous phase can not distinguish from . Let be the corresponding tuples on the list, for each , if , then reports failure and terminates. After that, selects a random bit and runs the above algorithm for responding to queries to obtain the values where . Then, generates the challenge SPE-CKS index as follows:
- (1)
- constructs . Then computes for each and . Let , observe that if , then . This means that is a valid SPE-CKS index of keyword set when .
- (2)
- sends and two keyword sets and to .
- -
- More queries: continues to issue index and trapdoor queries. The only restriction is that no index and trapdoor query can distinguish from .
- -
- Response: outputs a guess . If , then outputs 1 which means . Otherwise, outputs 0 which means R is a random number where .
5. Performance Evaluation
5.1. Theoretical Analysis
5.2. Experimental Results
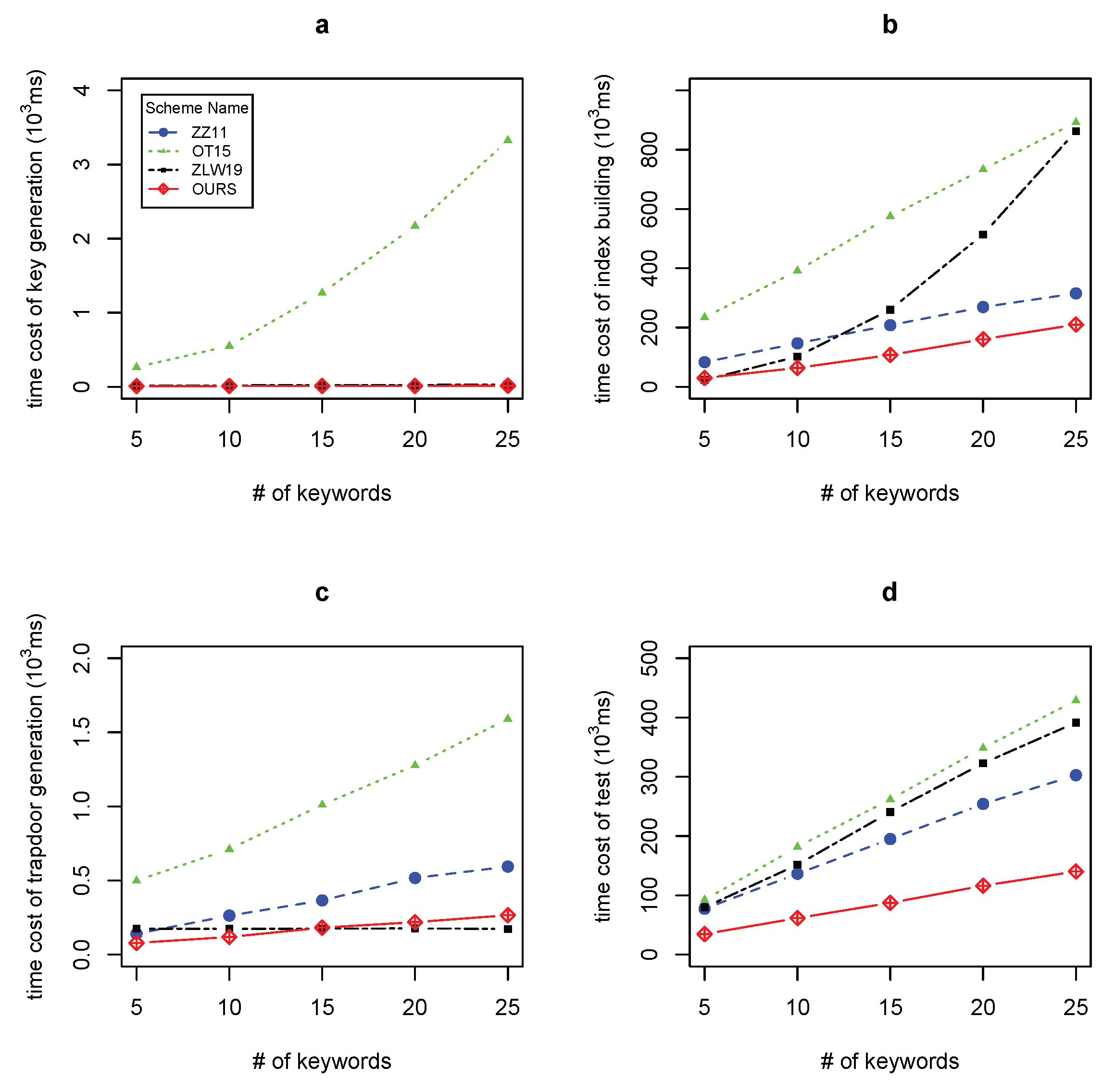
5.2.1. Time Overhead
- 1.
- Key generation. Because of adopting the technique called dual pairing vector space (DPVS)[8], the time complexity of key generation in OT15 is . The time cost of key generation in other three schemes are all linear with n.
- 2.
- Index building. The time cost of index building in ZZ11, OT15 and ours are all linearly with n. The time cost of index building in our scheme is still much less than that in ZZ11 and OT15. Furthermore, as n grows, for example, , the time cost of index building in ZLW19 is more than that in our scheme since it is linear with .
- 3.
- Trapdoor generation. Although the time cost of trapdoor generation in ZZ11, OT15 and ours are all linear with n, our scheme needs less time cost than ZZ11 and OT15 due to needing less exponentiation computation operations. The time cost of trapdoor generation in ZLW19 is linear with m. Because m is less than n, the time cost of trapdoor generation in our scheme is slightly more than that in ZLW19.
- 4.
- Testing. The time cost of test in these four schemes are all linear with n. Compared with ZZ11 and ZLW19, our scheme needs less pairing operations. Compared with OT15, our scheme needs less exponentiation operations on group elements. Since the time cost of exponentiation operation is only one fourth of that of pairing operation, our solution requires less test time.
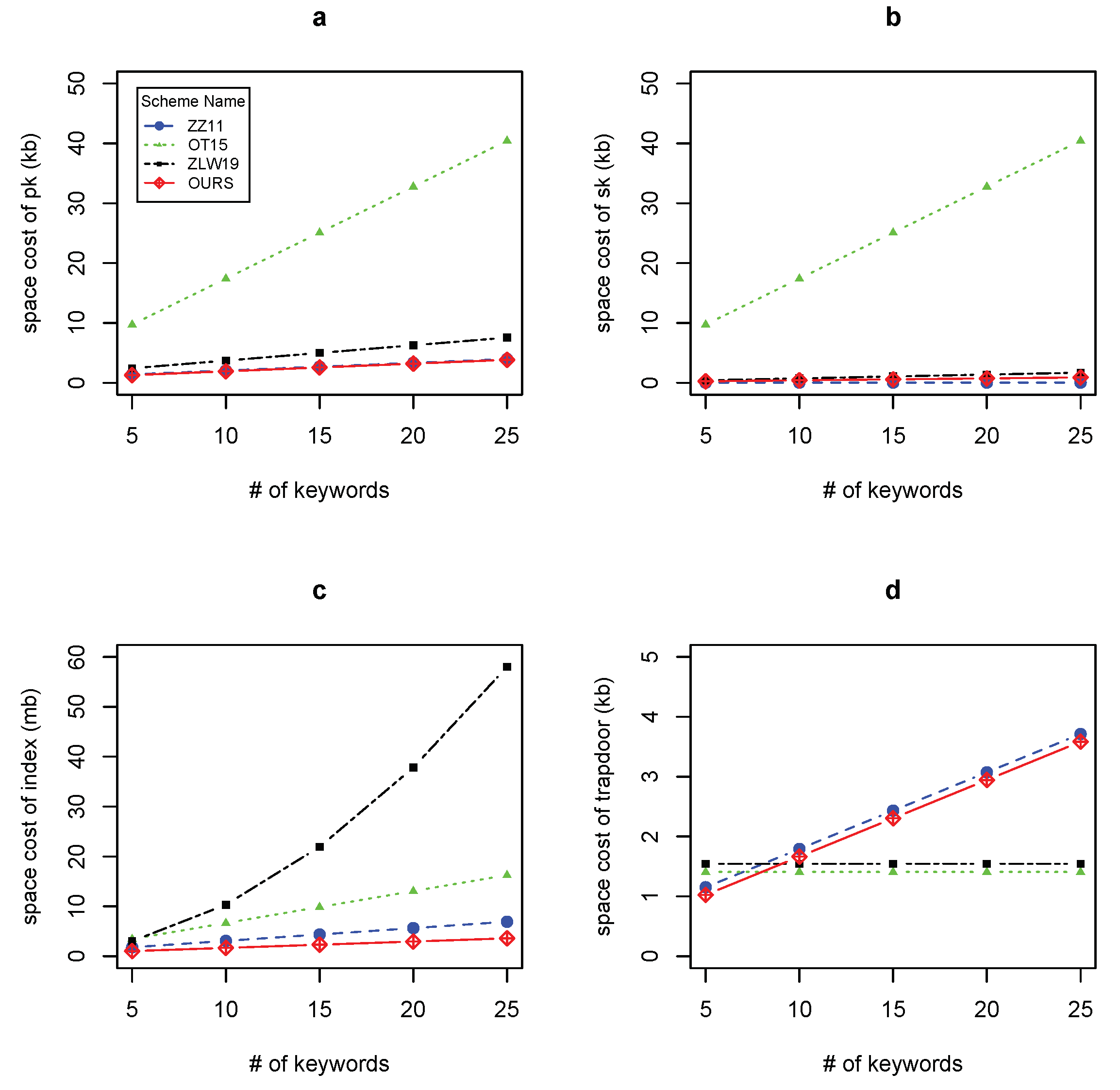
5.2.2. Space Overhead
- 1.
- size. The size in these four schemes are all linear with n. Our scheme is the best of these four schemes since it needs less elements in group .
- 2.
- size. ZZ11 only needs one integer in . Although size in OT15, ZLW19 and ours are all linear with n, both ZLW19 and our scheme need less space cost since the space cost of is less than that of . In addition, the size in our scheme is only a half of that in ZLW19.
- 3.
- Index size. Our scheme needs less space cost than OT15 and ZLW19, although the index size of OT15, ZLW19 and our scheme are all linear with n. This is fit to the theoretical analysis. The index size of ZLW19 is linear with , so it is not as efficient as our scheme.
- 4.
- Trapdoor size. The space complexity of trapdoor in OT15 and ZLW19 are and , respectively. Thus, these two schemes need less storage cost. The space cost of trapdoor in ZZ11 and our scheme are both linear with n. Our scheme needs less storage consumption than ZZ11 for trapdoor since our scheme needs less group element in trapdoor.
5.2.3. Comments
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Song, D.; Wagner, D.; Perrig, A. Practical Techniques for Searching on Encrypted Data. In Proceedings of the IEEE Symposium on Research in Security and Privacy 2000, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R.; Persiano, G. Public Key Encryption with Keywrod Search. In EUROCRYPT 2004; Cachin, C., Camenisch, J.L., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3027, pp. 506–522. [Google Scholar]
- Xu, P.; He, S.; Wang, W.; Susilo, W.; Jin, H. Lightweight Searchable Public-key Encryption for Cloud-assisted Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2017, 14, 3712–3723. [Google Scholar] [CrossRef]
- Park, D.J.; Kim, K.; Lee, P.J. Public Key Encryption with Conjunctive Field Keyword Search. In WISA 2004; Lim, C.H., Yung, M., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3325, pp. 73–86. [Google Scholar]
- Hwang, Y.H.; Lee, P.J. Public Key Encryption with Conjunctive Keyword Search and Its Extension to a Multi-user System. In Pairing 2007; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4575, pp. 2–22. [Google Scholar]
- Boneh, D.; Waters, B. Conjunctive, Subset, and Range Queries on Encrypted Data. In TCC 2007; Vadhan, S.P., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4392, pp. 535–554. [Google Scholar]
- Zhang, B.; Zhang, F. An efficient public key encryption with conjunctive-subset keywords search. J. Netw. Comput. Appl. 2011, 34, 262–267. [Google Scholar] [CrossRef]
- Okamoto, T.; Takashima, K. Achieving short ciphertexts or short secret-keys for adaptively secure general inner-product encryption. Des. Codes Cryptogr. 2015, 77, 138–159. [Google Scholar] [CrossRef]
- Zhang, Y.; Lu, S. POSTER: Efficient method for disjunctive and conjunctive keyword search over encrypted data. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 1535–1537. [Google Scholar]
- Zhang, Y.; Li, Y.; Wang, Y. Conjunctive and Disjunctive Keyword Search over Encrypted Mobile Cloud Data in Public Key System. Mob. Inf. Syst. 2018, 2018, 3839254. [Google Scholar] [CrossRef]
- Lu, Y.; Wang, G.; Li, J. Keyword guessing attacks on a public key encryption with keyword search scheme without random oracle and its improvement. Inf. Sci. 2019, 479, 270–276. [Google Scholar] [CrossRef]
- Goh, E.-J. Secure Indexes. Cryptology ePrint Archive. Report; 2003/216. Available online: http://eprint.iacr.org/2003/216/ (accessed on 25 February 2004).
- Golle, P.; Staddon, J.; Waters, B. Secure Conjunctive Search over Encrypted Data. In ACNS 2004; Jakobsson, M., Yung, M., Zhou, J., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3089, pp. 31–45. [Google Scholar]
- Byun, J.W.; Lee, D.H.; Lim, J. Efficient Conjunctive Keyword Searches on Encrypted Data Storage System. In EuroPKI 2006; Atzeni, A.S., Lioy, A., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 4043, pp. 184–196. [Google Scholar]
- Byun, J.W.; Rhee, H.S.; Park, H.; Lee, D.H. Off-line keyword guessing attacks on recent keyword search schemes over encrypted data. In SDM 2006; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4165, pp. 75–83. [Google Scholar]
- Cao, N.; Wang, C.; Li, M.; Ren, K.; Lou, W. Privacy-preserving multi-keyword ranked search over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 222–233. [Google Scholar] [CrossRef]
- Fu, Z.; Sun, X.; Liu, Q.; Zhou, L.; Shu, J. Achieving Efficient Cloud Search Services: Multi-Keyword Ranked Search over Encrypted Cloud Data Supporting Parallel Computing. IEICE Trans Commun. 2015, 98, 190–200. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Sun, X.; Wang, Q. A Secure and Dynamic Multi-Keyword Ranked Search Scheme over Encrypted Cloud Data. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 340–352. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity based Encryption from the Weil Pairing. In CRYPTO 2001; Kilian, J., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2139, pp. 213–229. [Google Scholar]
- Abdalla, M.; Bellare, M.; Catalano, D.; Kiltz, E.; Kohno, T.; Lange, T.; Malone-Lee, J.; Neven, G.; Paillier, P.; Shi, H. Searhable Encryption Revisited: Consistency Properties, Relation to Anonymous IBE, and Extensions. In CRYPTO 2005; Shoup, V., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621, pp. 205–222. [Google Scholar]
- Katz, J.; Sahai, A.; Waters, B. Predicate encryption supporting disjunctions, polynomial equations, and inner products. J. Cryptol. 2013, 26, 191–224. [Google Scholar] [CrossRef]
- Lewko, A.; OkamotoT, S.; ATakashima, K.; Takashima, K.; Waters, B. Fully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption. In Advances in Cryptology—EUROCRYPT 2010; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6110, pp. 62–91. [Google Scholar]
- Wang, B.; Hou, Y.; Li, M.; Wang, H.; Li, H. Maple: Scalable multi-dimensional range search over encrypted cloud data with tree-based index. In Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security, Kyoto, Japan, 4–6 June 2014; pp. 111–122. [Google Scholar]
- Zhu, H.; Mei, Z.; Wu, B.; Li, H.; Cui, Z. Fuzzy keyword search and access control over ciphertexts in cloud computing. In Information Security and Privacy; Springer: Cham, Switzerland, 2017; pp. 248–265. [Google Scholar]
- Jeong, I.R.; Kwon, J.O.; Hong, D.; Lee, D.H. Constructing PEKS schemes secure against keyword guessing attacks is possible? Comput. Commun. 2009, 32, 394–396. [Google Scholar] [CrossRef]
- Rhee, H.S.; Susilo, W.; Kim, H. Secure searchable public key encryption scheme against keyword guessing attacks. IEICE Electron. Express 2009, 6, 237–243. [Google Scholar] [CrossRef] [Green Version]
- Tang, Q.; Chen, L. Public-key Encryption with Registered Keyword Search. In Proceedings of the Sixth European Workshop on Public Key Services, Applications and Infrastructures, Pisa, Italy, 10–11 September 2009. [Google Scholar]
- Shao, Z.; Yang, B. On security against the server in designated tester public key encryption with keyword search. Inform. Process. Lett. 2015, 115, 957–961. [Google Scholar] [CrossRef]
- Joux, A. The Weil and Tate Pairing as Building Blocks for Public Key Cryptosystems. In Algorithmic Number Theory; Fieker, C., Kohel, D.R., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2369, pp. 20–32. [Google Scholar]
- Boneh, D.; Boyen, X. Efficient selective-ID secure identity based encryption. In Advances in Cryptology—EUROCRYPT 2004; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3027, pp. 223–238. [Google Scholar]
- Bao, F.; Deng, R.H.; Zhu, H. Variations of Diffie-Hellman Problem. In Proceedings of the International Conference on Information and Communications Security, ICICS, Huhehaote, China, 10–13 October 2003. [Google Scholar]
- Caro, A.D. The Java Pairing Based Cryptography Library (JPBC). Available online: Http://gas.dia.unisa.it/projects/jpbc/ (accessed on 24 February 2013).
- Cohen, W.W. Enron E-Mail Dataset. Available online: Http://www.cs.cmu.edu/./enron/ (accessed on 20 June 2019).
| Algorithm | ZZ11 [7] | OT15 [8] | ZLW19 [10] | Our Scheme |
|---|---|---|---|---|
| KeyGen | ||||
| IndexBuild | ||||
| Trapdoor | ||||
| Test | ||||
| Denotation | P, , : The time cost of one exponentiation computation in G, and , respectively. | |||
| e: The time cost of one pairing operation. | ||||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Y.; Li, Y.; Wang, Y. Efficient Conjunctive Keywords Search over Encrypted E-Mail Data in Public Key Setting. Appl. Sci. 2019, 9, 3655. https://doi.org/10.3390/app9183655
Zhang Y, Li Y, Wang Y. Efficient Conjunctive Keywords Search over Encrypted E-Mail Data in Public Key Setting. Applied Sciences. 2019; 9(18):3655. https://doi.org/10.3390/app9183655
Chicago/Turabian StyleZhang, Yu, Yin Li, and Yifan Wang. 2019. "Efficient Conjunctive Keywords Search over Encrypted E-Mail Data in Public Key Setting" Applied Sciences 9, no. 18: 3655. https://doi.org/10.3390/app9183655
APA StyleZhang, Y., Li, Y., & Wang, Y. (2019). Efficient Conjunctive Keywords Search over Encrypted E-Mail Data in Public Key Setting. Applied Sciences, 9(18), 3655. https://doi.org/10.3390/app9183655





