The Integration of Azure Sphere and Azure Cloud Services for Internet of Things
Abstract
Featured Application
Abstract
1. Introduction
- A new IoT integrated solution including hardware, software and services is proposed based on Azure Sphere device and Azure cloud services to meet the requirements of high security and low cost.
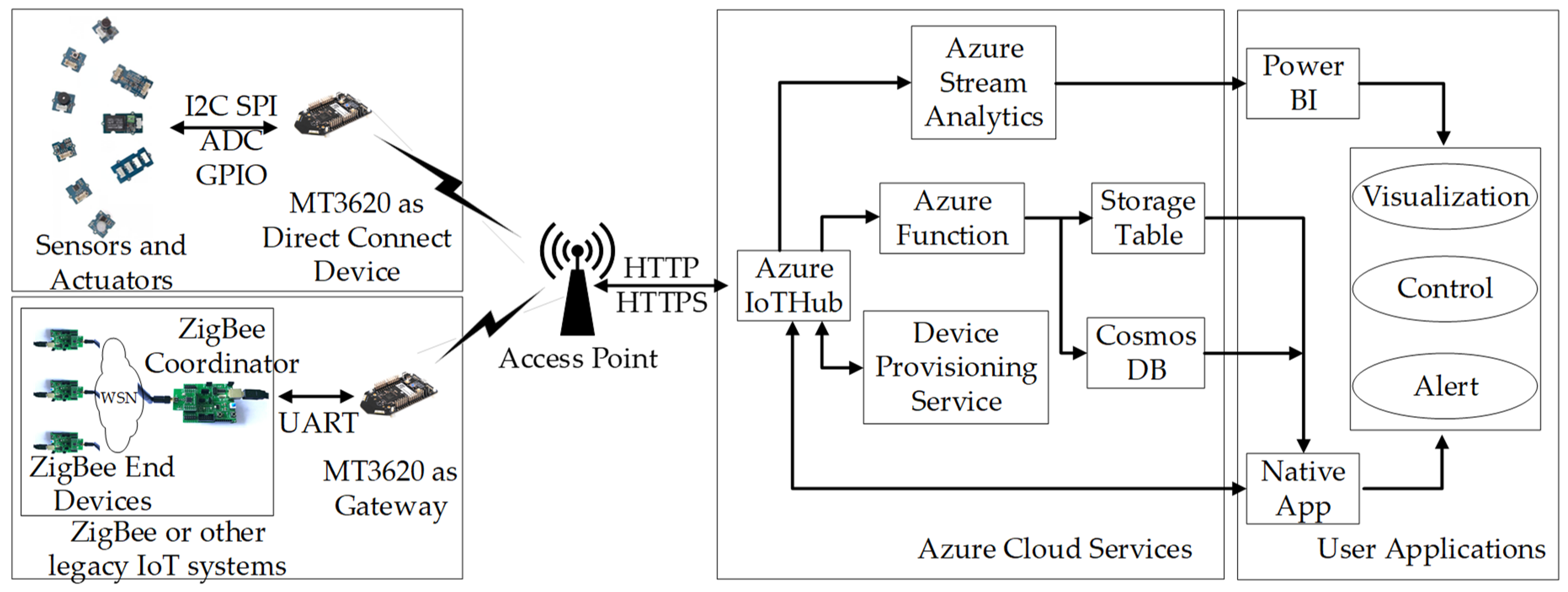
- The hardware prototypes for Azure Sphere device, which act either as a direct connected device or a gateway, are designed and implemented based on the MT3620 development kit.
- The programs for MT3620 and CC2530 ZigBee devices, as well as applications for Windows devices are designed and implemented. Meanwhile, a proof of concept for the proposed integration is demonstrated and verified based on the hardware prototypes and Azure cloud services.
2. Related Work
2.1. Security Research in IoT Systems
2.2. Azure Sphere
- The Azure Sphere MCU is composed of multiple ARM Cortex cores, network connectivity subsystem, multiplexed I/O peripherals, integrated RAM and flash, hardware firewalls, and the Pluton security subsystem, which provide built-in security from a hardware perspective.
- The custom Linux-based kernel, the Security Monitor and OS services that host the application container add a four-layer defense, in-depth secure environment from a software perspective.
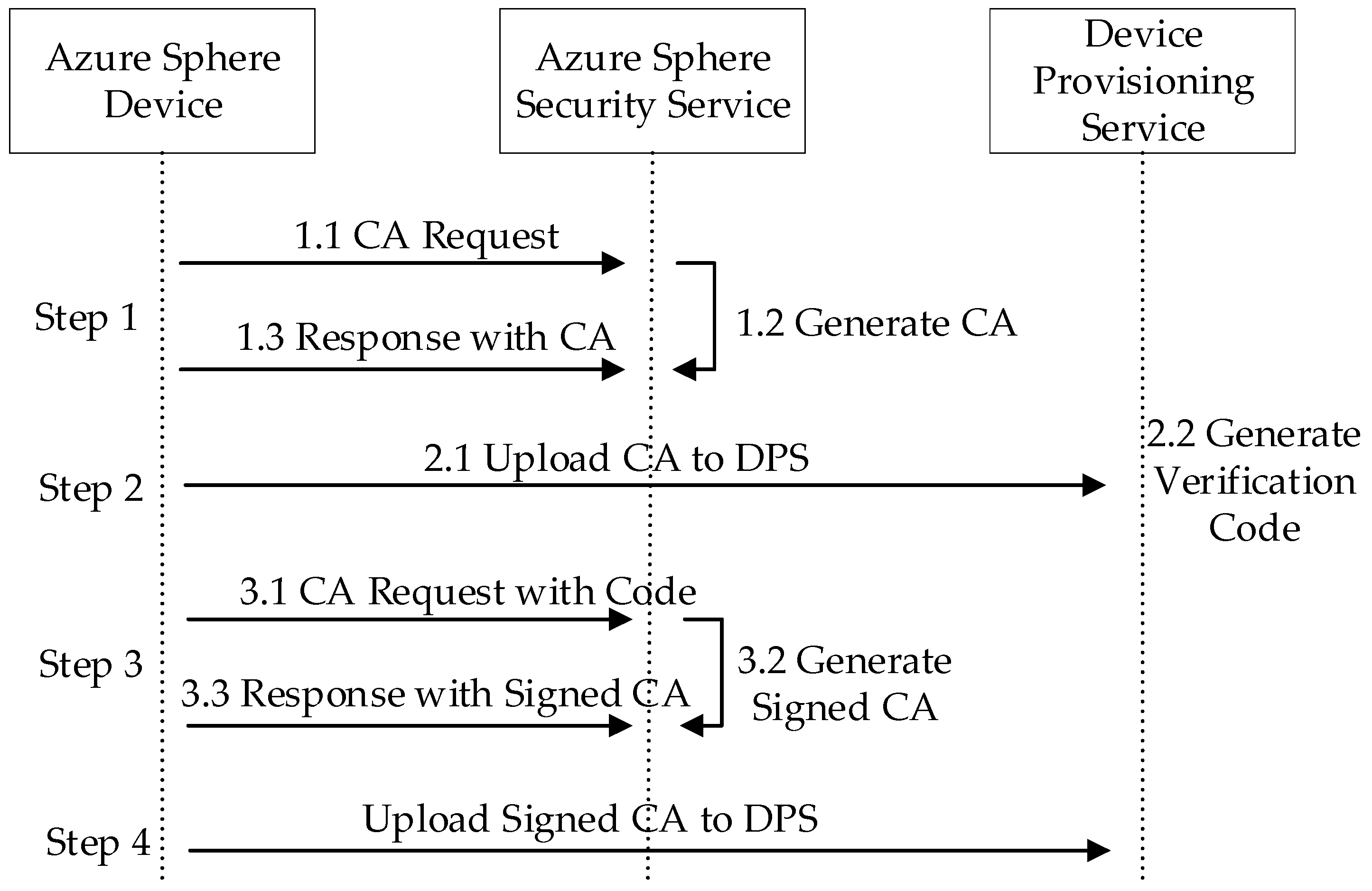
- The Azure Sphere Security Service that merges with certificate-based authentication, timely update and failure reporting renews security to confront with emerging threats from a service perspective [34].
3. System Design
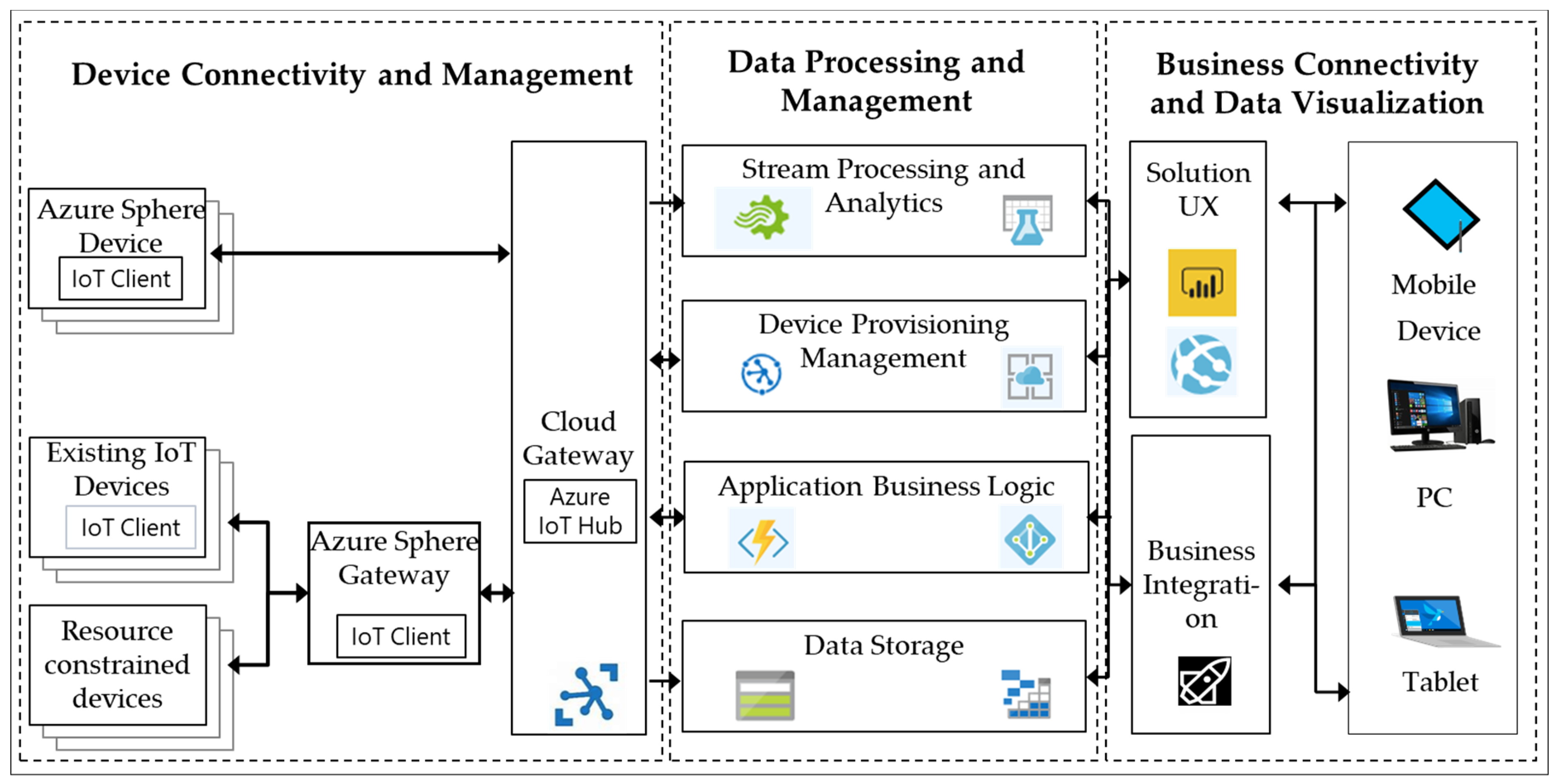
3.1. Overview
- Azure Sphere device stands for the MT3620 development kit that directly connects with Azure IoT Hub.
- Existing IoT device and resource constrained device are the legacy IoT devices that cannot establish secure communication with Azure IoT Hub directly. Instead, they communicate with the Azure Sphere gateway to achieve data sending and receiving.
- Azure Sphere gateway acts as the bridge between legacy IoT devices and Azure IoT Hub.
- Azure IoT Hub is the cloud gateway that acts as a central message hub for bidirectional communication between Azure services and the IoT end devices.
- Stream processing and analytics mainly make use of Azure Stream Analytics service for large-scale data processing with complex rules.
- Device provisioning management functionality is provided by Azure Device Provisioning Service, which allows the registration and connection of large sets of MT3620 devices to Azure IoT Hub for bidirectional communication.
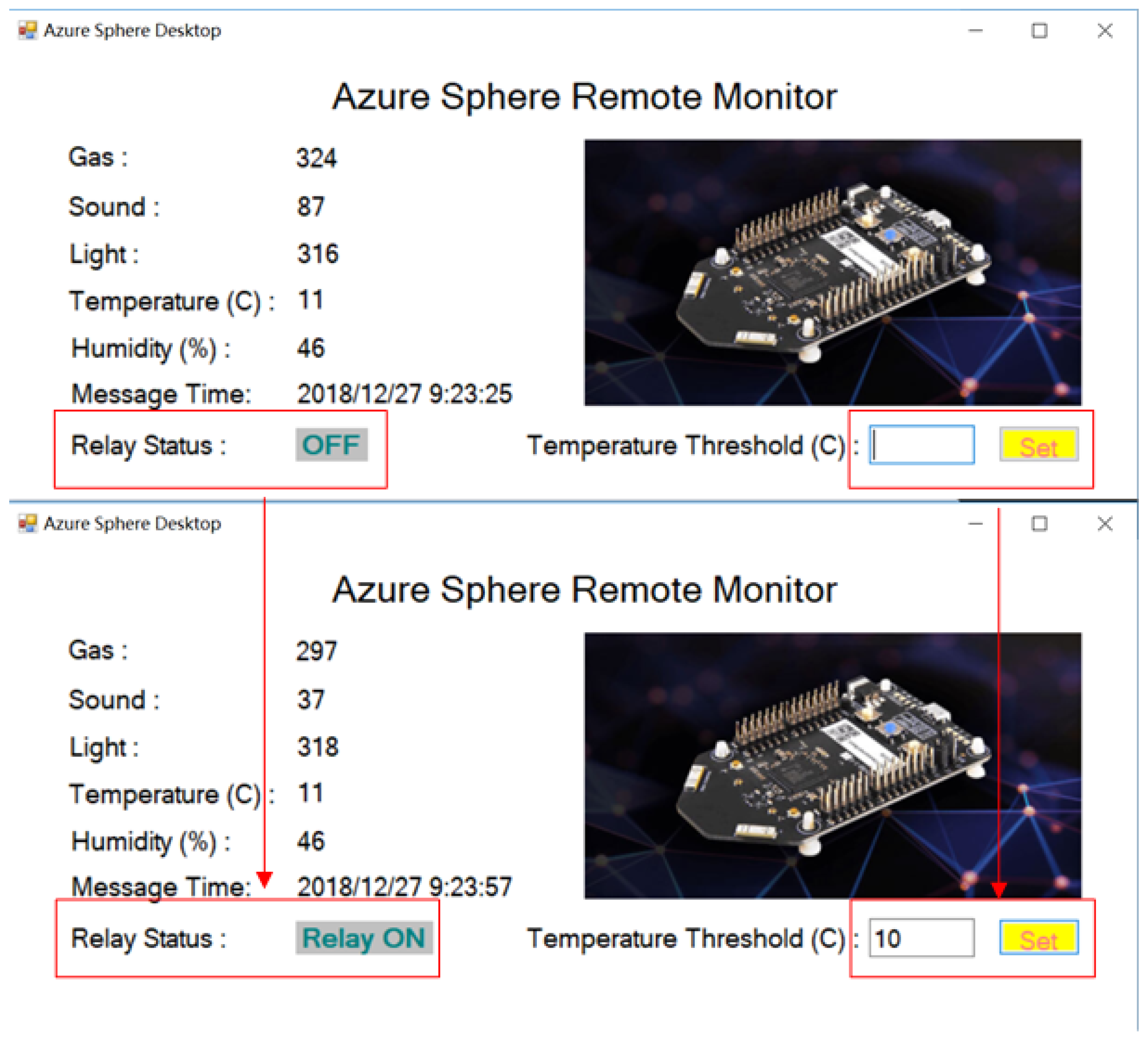
- Application business logic is responsible for action executing based on insights generated from data during stream processing.
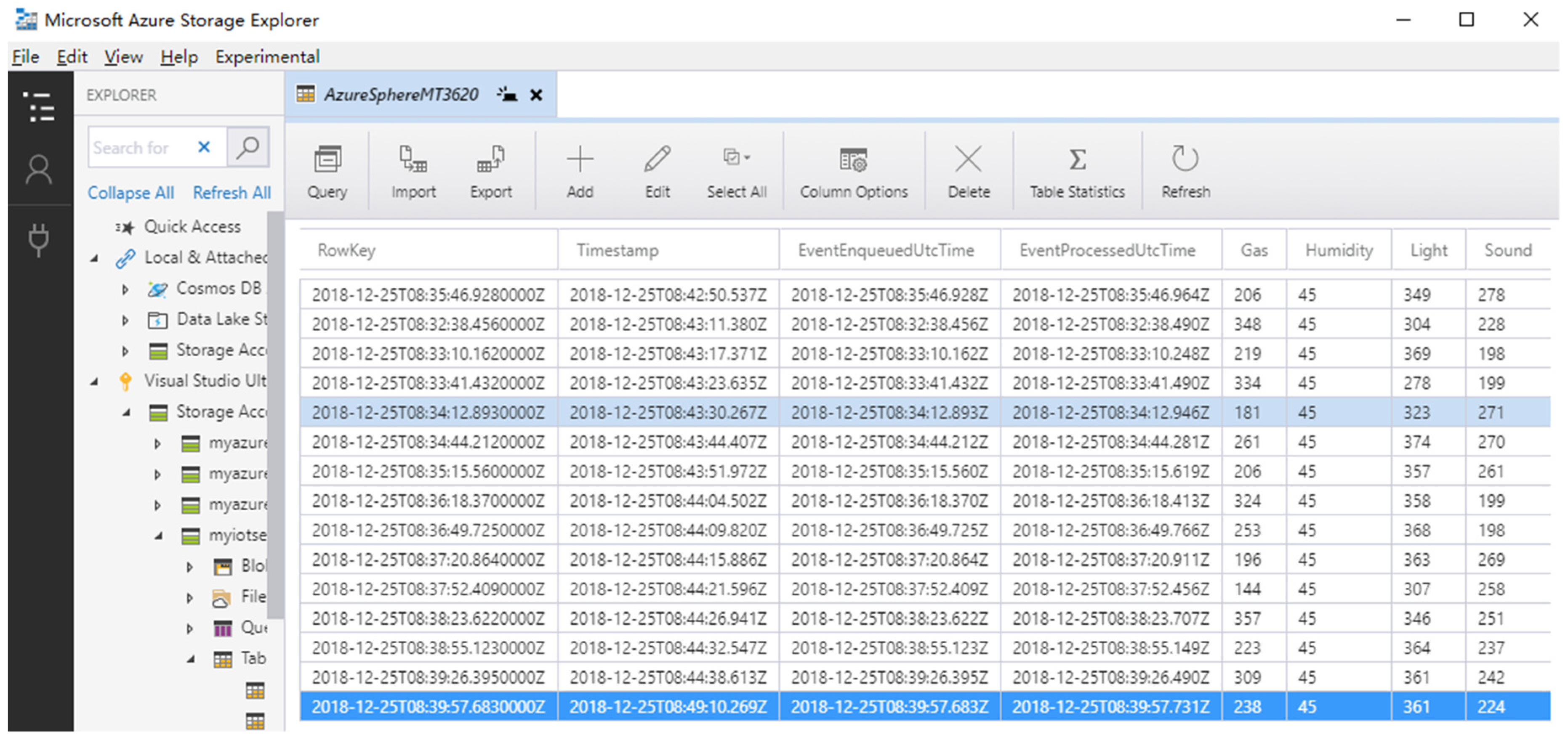
- Azure Table Storage service is used for data storage in the cloud.
3.2. Hardware Design
3.3. Azure Cloud Intergration
3.3.1. Azure IoT Hub
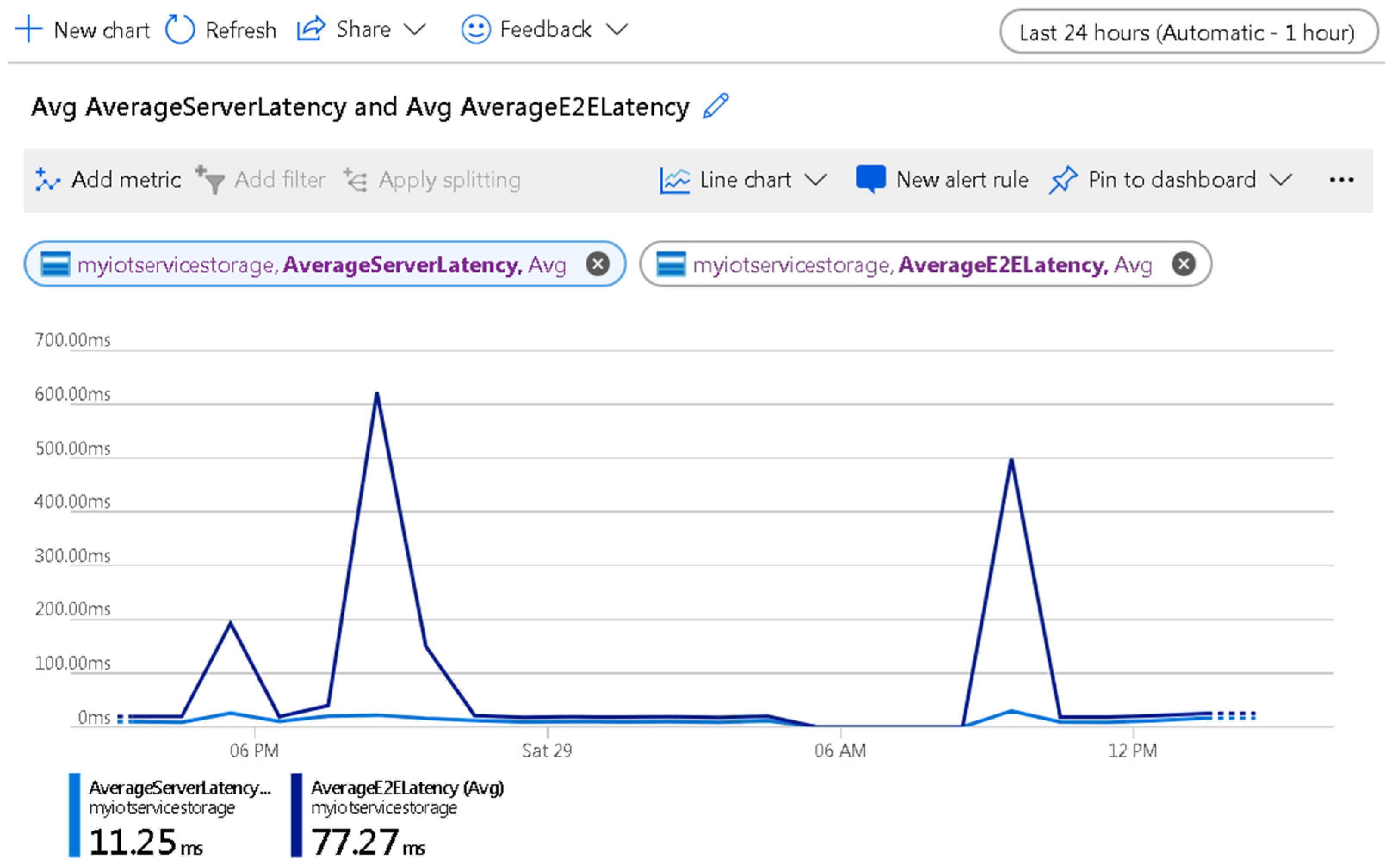
3.3.2. Azure Stream Analytics
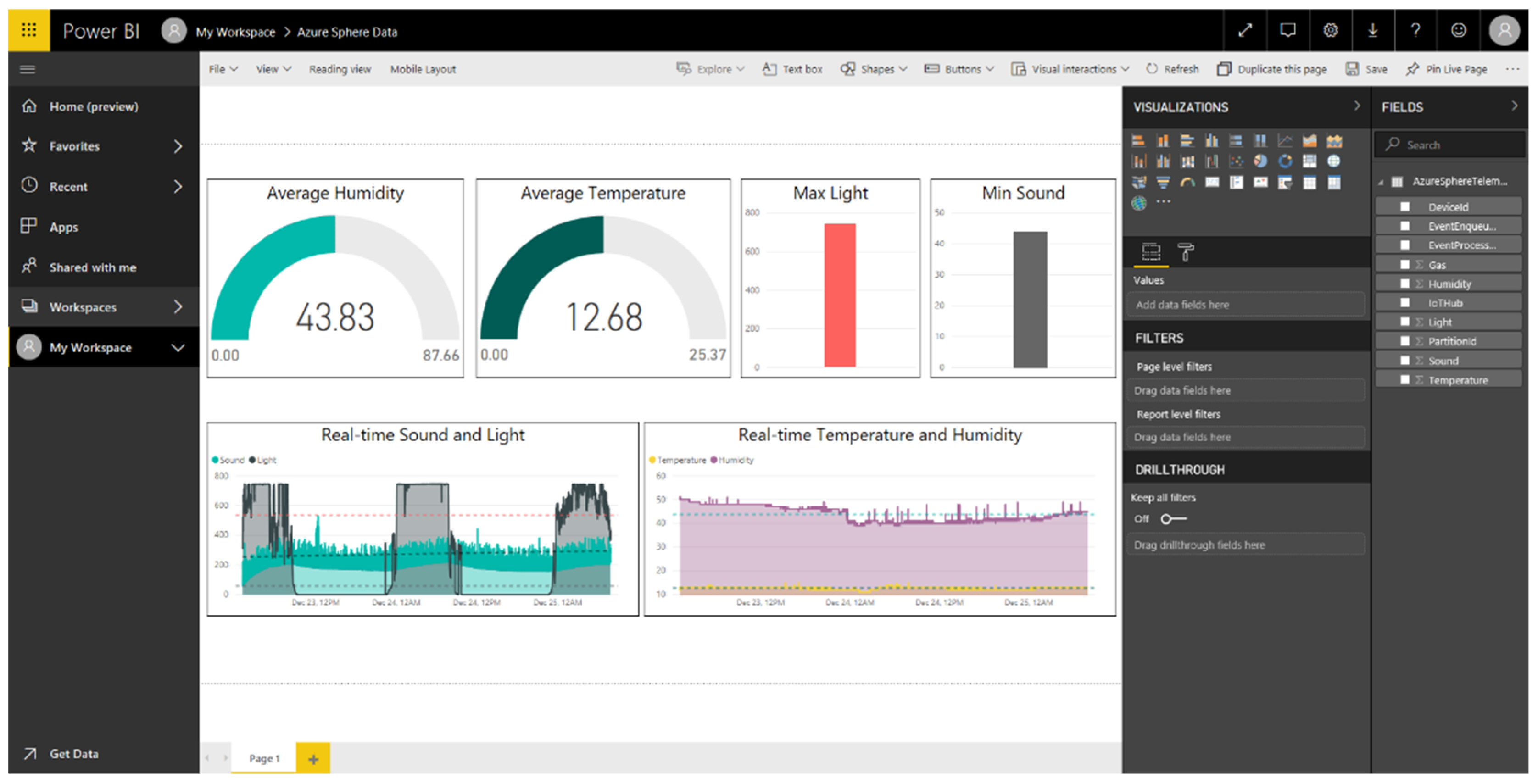
3.3.3. Data Visualization and Storage
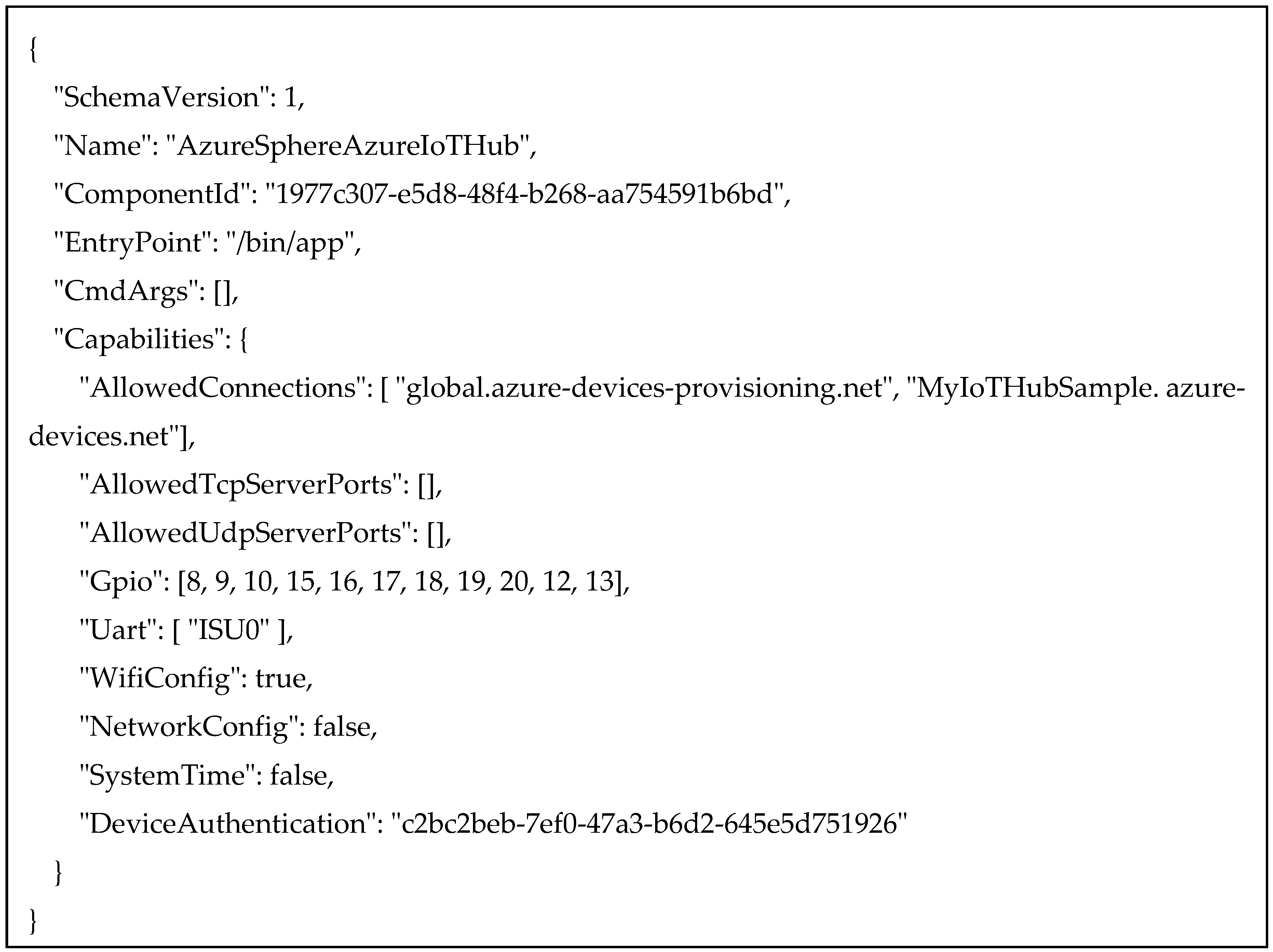
3.4. Configure Azure IoT Hub for Azure Sphere
3.5. System Security
4. System Implementation
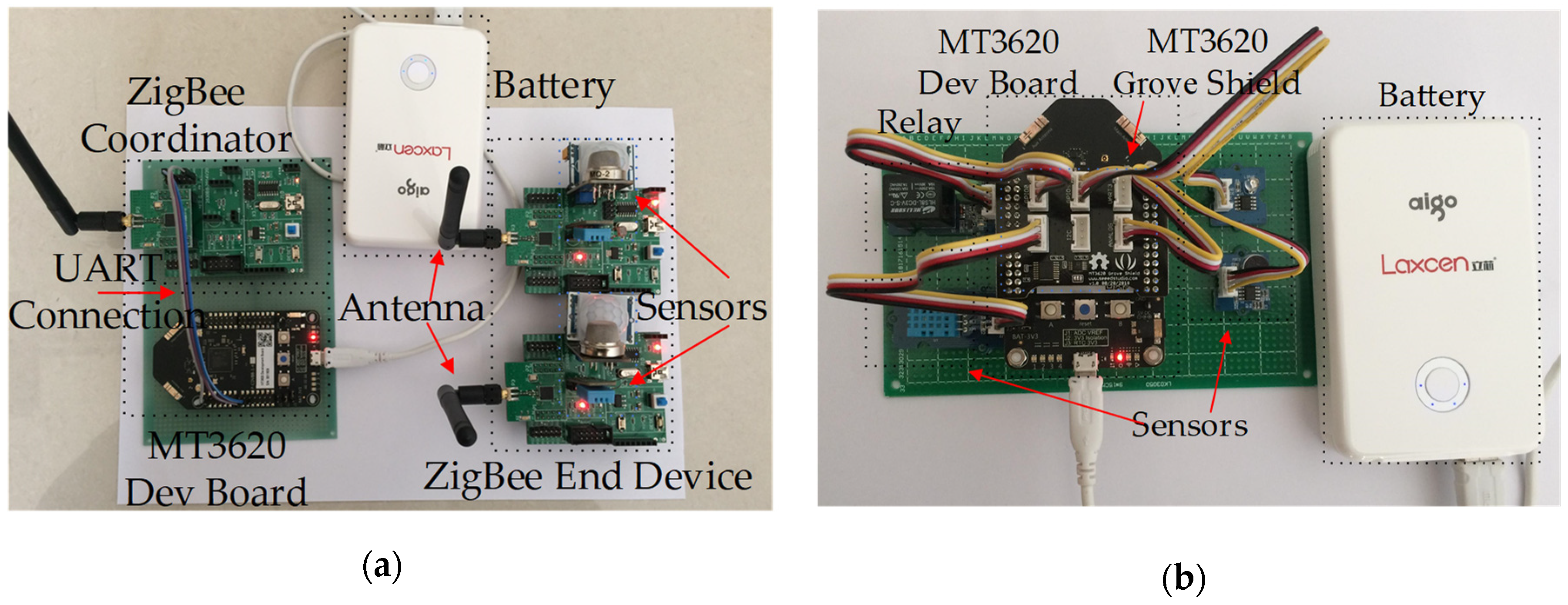
4.1. Hardware
4.2. Software
4.2.1. Prerequisites
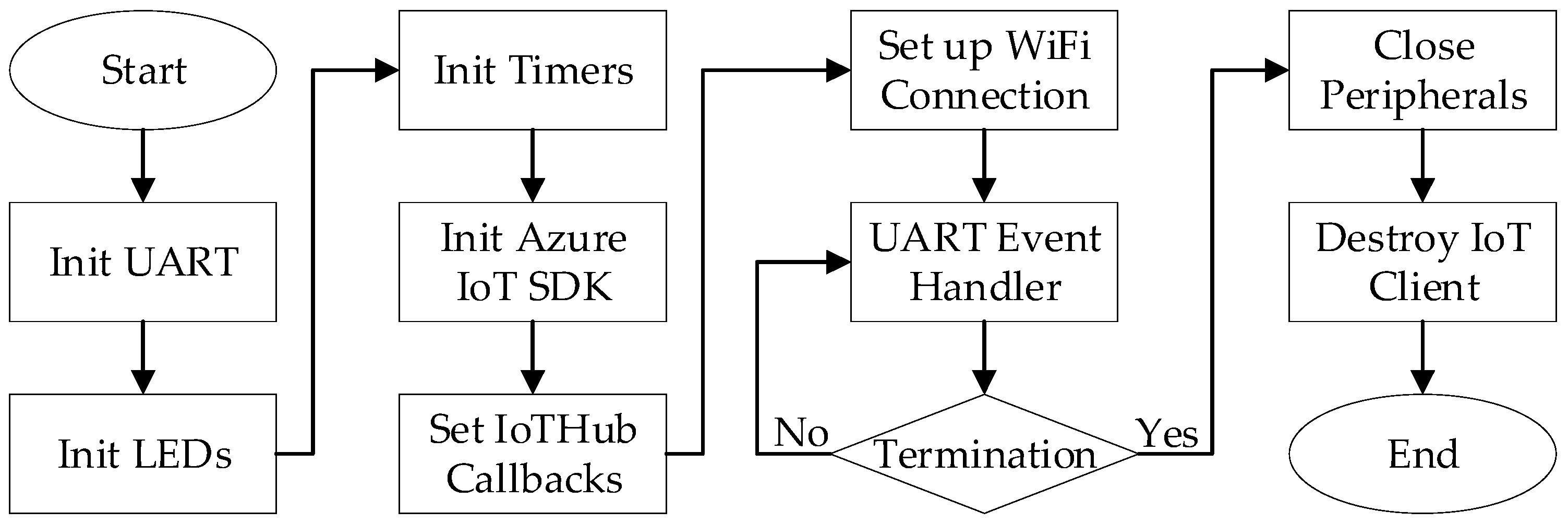
4.2.2. Software for MT3620 as Direct Connected Device
4.2.3. Software for MT3620 as Gateway
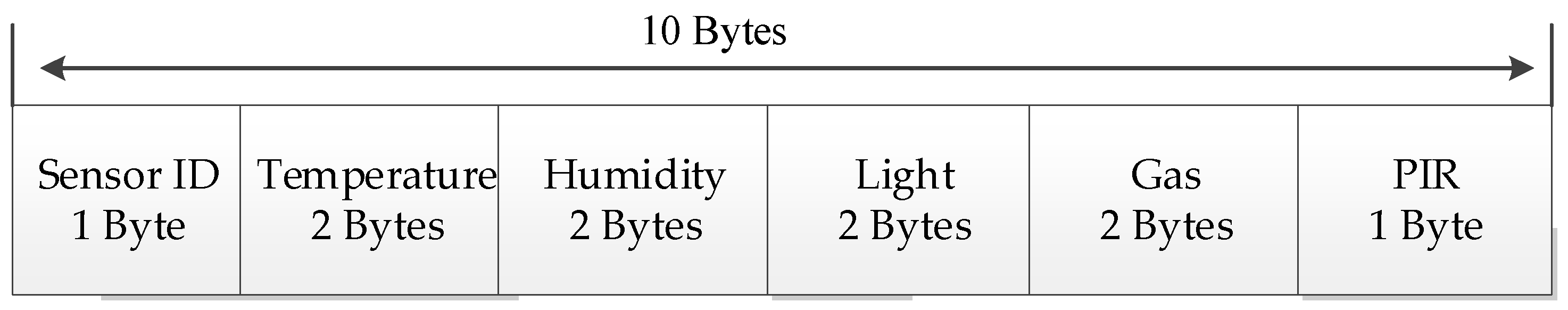
4.2.4. Software for ZigBee Wireless Sensor Network
4.3. Azure Cloud Services
5. Experimental Results
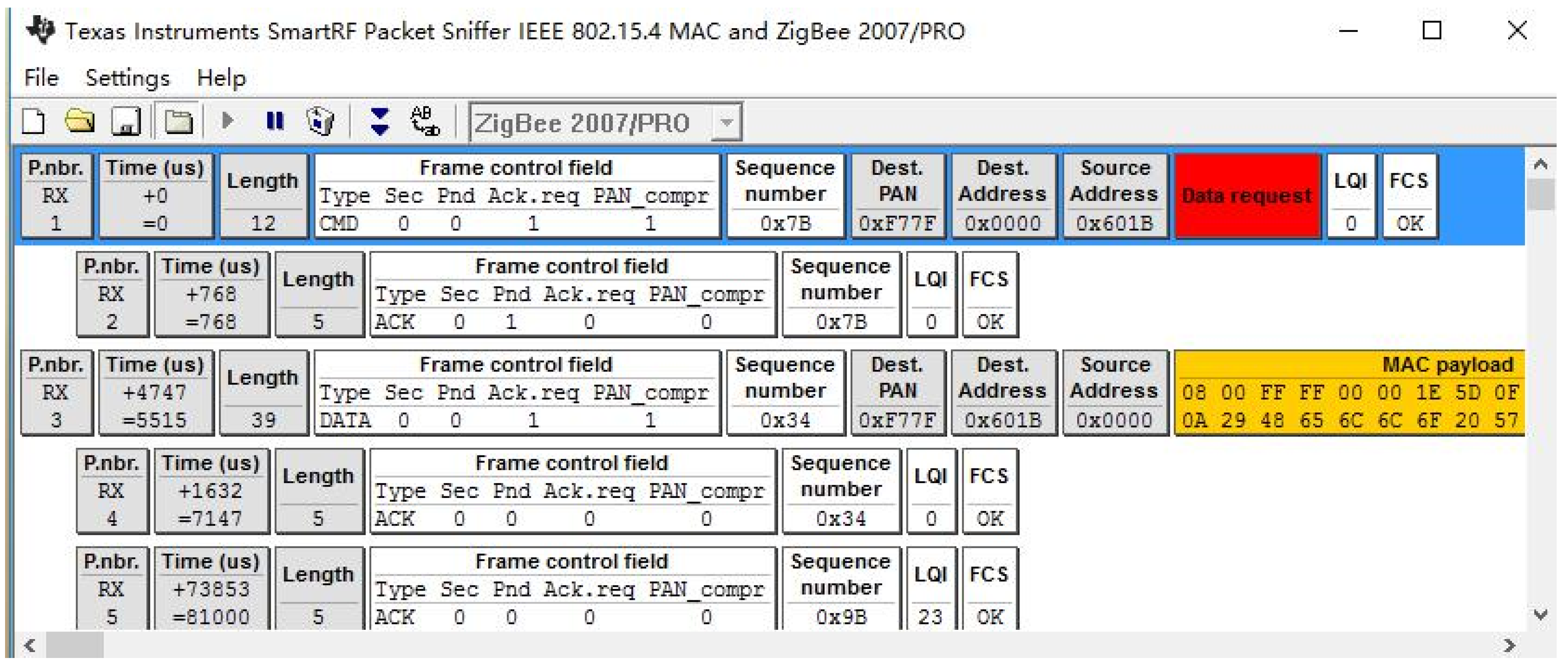
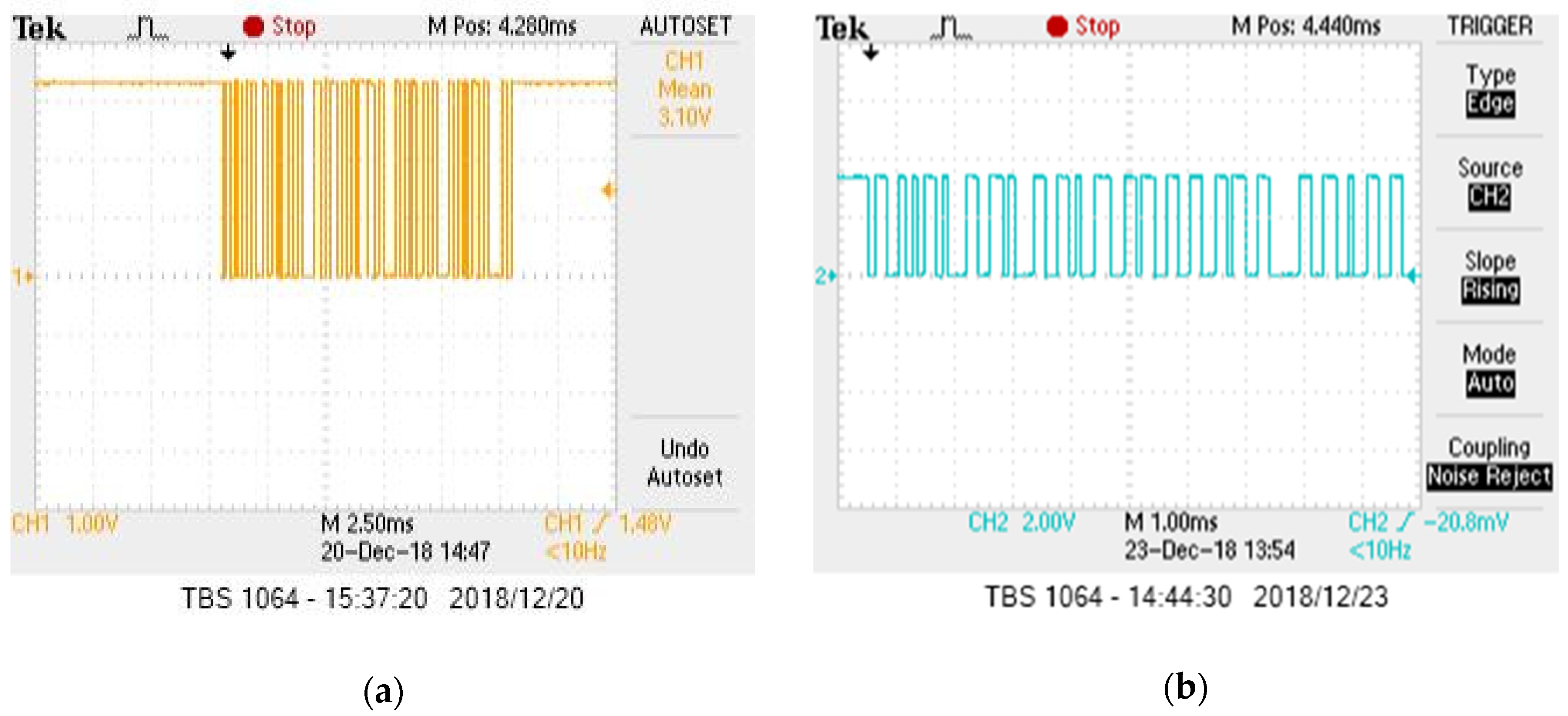
5.1. Device Layer
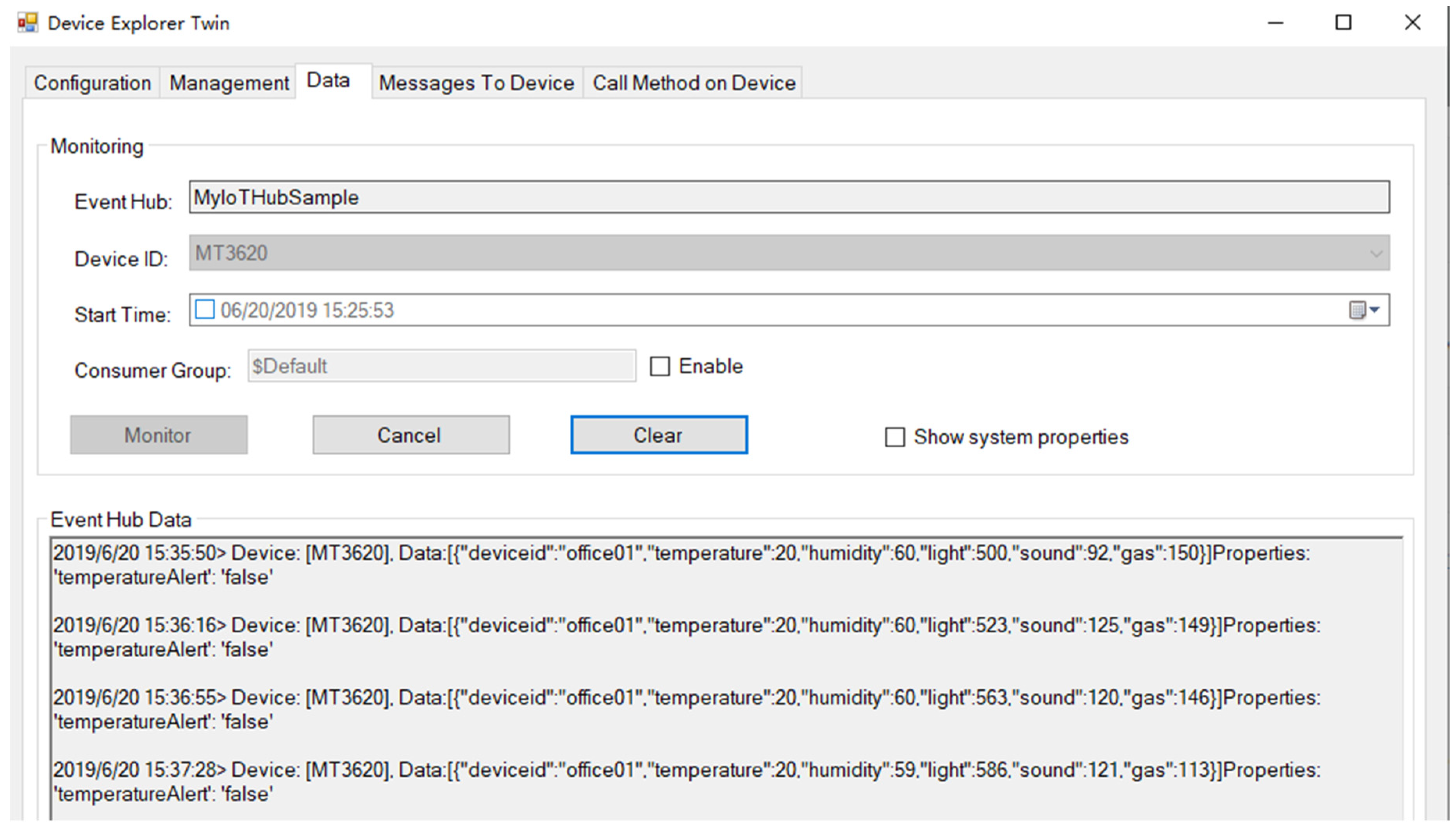
5.2. Cloud Layer
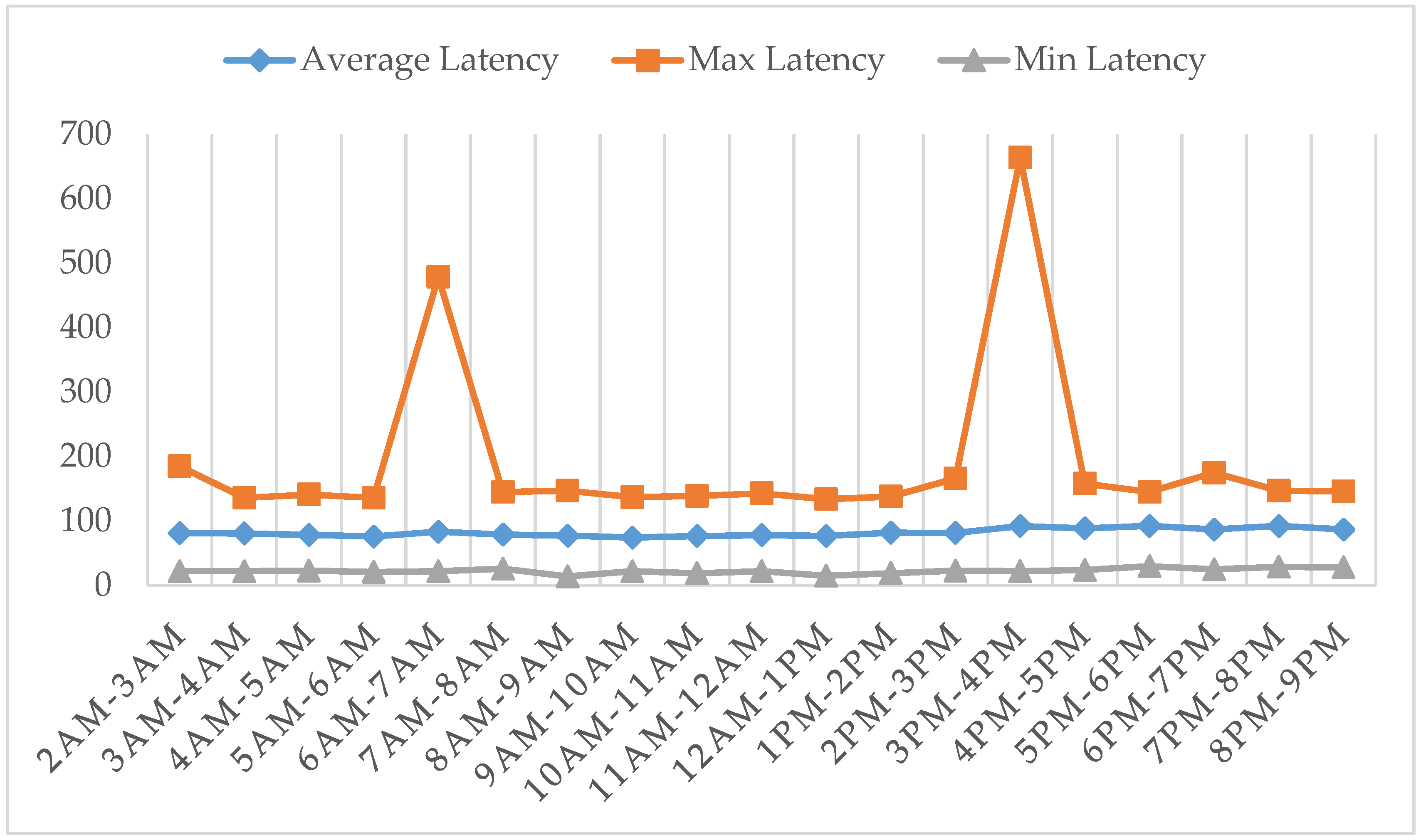
5.3. Application Layer
6. Discussion
7. Conclusions
Supplementary Materials
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kuutti, S.; Fallah, S.; Katsaros, K.; Dianati, M.; Mccullough, F.; Mouzakitis, A. A survey of the state-of-the-art localization techniques and their potentials for autonomous vehicle applications. IEEE Internet Things J. 2018, 5, 829–846. [Google Scholar] [CrossRef]
- Carías, J.F.; Labaka, L.; Sarriegi, J.M.; Hernantes, J. Defining a Cyber Resilience Investment Strategy in an Industrial Internet of Things Context. Sensors 2019, 19, 138. [Google Scholar] [CrossRef]
- Yan, H.; Zhang, Y.; Pang, Z.; Xu, L.D. Superframe planning and access latency of slotted mac for industrial wsn in iot environment. IEEE Trans. Ind. Inform. 2014, 10, 1242–1251. [Google Scholar]
- Alam, M.M.; Malik, H.; Khan, M.I.; Pardy, T.; Kuusik, A.; Moullec, Y.L. A survey on the roles of communication technologies in iot-based personalized healthcare applications. IEEE Access 2018, 6, 36611–36631. [Google Scholar] [CrossRef]
- Yang, P.; Stankevicius, D.; Marozas, V.; Deng, Z.; Liu, E.; Lukosevicius, A.; Dong, F.; Xu, L.; Min, G. Lifelogging data validation model for internet of things enabled personalized healthcare. IEEE Trans. Syst. ManCybern. Syst. 2018, 48, 50–64. [Google Scholar] [CrossRef]
- Park, S.; Park, S.H.; Park, L.W.; Park, S.; Lee, S.; Lee, T.; Lee, S.H.; Jang, H.; Kim, S.M.; Chang, H.; et al. Design and Implementation of a Smart IoT Based Building and Town Disaster Management System in Smart City Infrastructure. Appl. Sci. 2018, 8, 2239. [Google Scholar] [CrossRef]
- Vallati, C.; Virdis, A.; Mingozzi, E.; Stea, G. Mobile-edge computing come home connecting things in future smart homes using LTE D2D communications. IEEE Consum. Electron. Mag. 2016, 5, 77–83. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Wang, N.; Jiang, T.; Li, W.; Lv, S. Physical-layer security in internet of things based on compressed sensing and frequency selection. IET Commun. 2017, 11, 1431–1437. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the internet of things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and security in internet of things and wearable devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- He, H.; Maple, C.; Watson, T. The security challenges in the IoT enabled cyber-physical systems and opportunities for evolutionary computing & other computational intelligence. In Proceedings of the 2016 IEEE Congress on Evolutionary Computation, Vancouver, BC, Canada, 24–29 July 2016. [Google Scholar]
- Hossain, M.S.; Muhammad, G. Cloud-assisted industrial internet of things (iiot)–enabled framework for health monitoring. Comput. Netw. 2016, 101, 192–202. [Google Scholar] [CrossRef]
- Zhou, J.; Cao, Z.; Dong, X.; Vasilakos, A.V. Security and privacy for cloud-based iot: Challenges. IEEE Commun. Mag. 2017, 55, 26–33. [Google Scholar] [CrossRef]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (iot) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions, London, UK, 14–16 December 2015. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Mosenia, A.; Jha, N.K. A comprehensive study of security of internet-of-things. IEEE Trans. Emerg. Top. Comput. 2017, 5, 586–602. [Google Scholar] [CrossRef]
- Wu, L.; Du, X.; Guizani, M.; Mohamed, A. Access control schemes for implantable medical devices: A survey. IEEE Internet Things J. 2017, 4, 1272–1283. [Google Scholar] [CrossRef]
- Altawy, R.; Youssef, A.M. Security tradeoffs in cyber physical systems: A case study survey on implantable medical devices. IEEE Access 2016, 4, 959–979. [Google Scholar] [CrossRef]
- Xiaojiang, D.; Dapeng, W. Adaptive cell relay routing protocol for mobile ad hoc networks. IEEE Trans. Veh. Technol. 2006, 55, 278–285. [Google Scholar]
- Guan, Z.; Li, J.; Zhu, L.; Zhang, Z.; Du, X.; Guizani, M. Toward delay-tolerant flexible data access control for smart grid with renewable energy resources. IEEE Trans. Ind. Inform. 2017, 13, 3216–3225. [Google Scholar] [CrossRef]
- Rath, A.T.; Colin, J. Strengthening access control in case of compromised accounts in smart home. In Proceedings of the WiMob 2017 IEEE International Conference on Wireless and Mobile Computing, Networking and Communications, Rome, Italy, 9–11 October 2017. [Google Scholar]
- Cheminod, M.; Durante, L.; Seno, L.; Valenzano, A. Semiautomated verification of access control implementation in industrial networked systems. IEEE Trans. Ind. Inform. 2015, 11, 1388–1399. [Google Scholar] [CrossRef]
- Munir, M.; Siddiqui, S.A.; Dengel, A.; Ahmed, S. Deepant: A deep learning approach for unsupervised anomaly detection in time series. IEEE Access 2018, 7, 1991–2005. [Google Scholar] [CrossRef]
- Gaddam, S.R.; Phoha, V.V.; Balagani, K.S. K-means+id3: A novel method for supervised anomaly detection by cascading k-means clustering and id3 decision tree learning methods. IEEE Trans. Knowl. Data Eng. 2007, 19, 345–354. [Google Scholar] [CrossRef]
- Hussain, B.; Du, Q.; Ren, P. Semi-supervised learning based big data-driven anomaly detection in mobile wireless networks. China Commun. 2018, 15, 41–57. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the iot world: Present and future challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Ali, B.; Awad, A.I. Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes. Sensors 2018, 18, 817. [Google Scholar] [CrossRef] [PubMed]
- Cui, Z.; Lv, H.; Chao, Y.; Gao, G.; Zhou, C. Efficient key management for IoT owner in the cloud. In Proceedings of the 2015 IEEE International Conference on Big Data & Cloud Computing, Dalian, China, 26–28 August 2015. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Security analysis of existing IoT key management protocols. In Proceedings of the 2016 IEEE/ACS International Conference of Computer Systems and Applications, Agadir, Morocco, 29 November–2 December 2016. [Google Scholar]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Conti, M.; Jo, M. Design of secure user authenticated key management protocol for generic IoT networks. IEEE Internet Things J. 2018, 5, 269–282. [Google Scholar] [CrossRef]
- Azure Sphere Documentation. Available online: https://docs.microsoft.com/en-us/azure-sphere/ (accessed on 26 December 2018).
- Hunt, G.; Letey, G.; Nightingale, E. The Seven Properties of Highly Secure Devices. Tech. Report MSR-TR-2017-16. Available online: https://www.microsoft.com/en-us/research/publication/seven-properties-highly-secure-devices (accessed on 26 December 2018).
- Azure Sphere Architecture. Available online: https://docs.microsoft.com/en-us/azure-sphere/product-overview/architecture/ (accessed on 26 December 2018).
- MT 3620 Product Information. Available online: https://www.mediatek.com/products/azureSphere/mt3620 (accessed on 26 December 2018).
- Azure Sphere MT3620 Development Kit. Available online: https://www.seeedstudio.com/Azure-Sphere-MT3620-Development-Kit-US-Version-p-3052.html (accessed on 26 December 2018).
- Set up Your Azure Sphere Device. Available online: https://azure.microsoft.com/en-us/services/azure-sphere/get-started/ (accessed on 26 December 2018).
- Azure Stream Analytics Documentation. Available online: https://docs.microsoft.com/en-us/azure/stream-analytics/ (accessed on 26 December 2018).
- Azure Portal. Available online: https://portal.azure.com (accessed on 26 December 2018).
- Azure IoT Hub Device Provisioning Service Documentation. Available online: https://docs.microsoft.com/en-us/azure/iot-dps/ (accessed on 26 December 2018).
- Azure IoT Security. Available online: https://docs.microsoft.com/en-us/azure/iot-fundamentals/iot-security-ground-up (accessed on 26 December 2018).
- WolfSSL Support for Microsoft Azure Sphere. Available online: https://www.wolfssl.com/wolfssl-support-microsoft-azure-sphere-pluton-security (accessed on 26 December 2018).
- Azure Stream Analytics Updates Certifications and Compliance. Available online: https://azure.microsoft.com/en-us/blog/stream-analytics-compliance/ (accessed on 26 December 2018).
- Azure Storage. Available online: https://docs.microsoft.com/en-us/azure/storage/common/storage-service-encryption (accessed on 26 December 2018).
- IEEE Standard for Low-Rate Wireless Networks. IEEE Std 802.15.4 2016, 22, 1–709.
- Azure Sphere SDK. Available online: https://aka.ms/AzureSphereSDKDownload (accessed on 26 December 2018).
- CC2530 Product Information. Available online: http://www.ti.com/product/CC2530/toolssoftware (accessed on 26 December 2018).
- Power BI Portal. Available online: https://powerbi.microsoft.com/ (accessed on 26 December 2018).
- IoT Security Architecture. Available online: https://docs.microsoft.com/en-us/azure/iot-fundamentals/iot-security-architecture (accessed on 26 December 2018).
- Security Development Lifecycle. Available online: https://www.microsoft.com/en-us/sdl/default.aspx (accessed on 26 December 2018).
- Operational Security Assurance. Available online: https://www.microsoft.com/en-us/securityengineering/osa. (accessed on 26 December 2018).

| Solution | Application Area | IoT Layers | Security Considerations |
|---|---|---|---|
| [12] | Industrial IoT | Cisco IoT Framework | Security threats in data mining and big data |
| [13] | Health care | Things and clouds layer | Signal monitoring in health care application |
| [14] | General | Sensing, network and application layer | Authentication, privacy encryption, packet forwarding |
| [15] | General | Perception, network and application layer | Security threats and strategies in three layers |
| [16] | General | Object, object abstraction, service management, application and business layer | Security protocols in IoT |
| [17] | General | Cisco IoT seven-layer model | Security threats and strategies in three layers |
| Categories | Policies and Rules |
|---|---|
| Device security | Seven highest levels of security properties Certificate-based authentication Application and its data Security |
| Connection security | Transport Layer Security HTTPS and MQTT protocols |
| Cloud security | User authentication and authorization ISO 27001 and ISO 27018 certified 256-bit AES encryption |
| Application security | 128-bit AES algorithm for ZigBee Application capabilities, device capabilities and signing deployment for MT3620 |
| Sensor | Model | Type |
|---|---|---|
| Temperature and Humidity | Grove 1-DHT11 | Digital |
| Light | Grove-Light Sensor | Analogue |
| Sound | Grove-Sound Sensor | Analogue |
| Gas | Grove-Gas Sensor (MQ2) | Analogue |
| PIR | Grove-PIR Motion Sensor | Digital |
| Relay | Grove-Relay | Digital |
| Name | Value | SFR 1 or Function |
|---|---|---|
| Radio Channel | 2405 MHz | FREQCTRL.FREQ[6:0] |
| Receiver Sensitivity | −85 dBm | CCACTRL0[7:0] |
| Transmit Power | 4.5 dBm | TXPOWER[7:0] |
| Network Topology | Star | GenericApp_Init |
| Light AD Channel | AIN6, P0_6 | ADCCON3[7:0] |
| Gas AD Channel | AIN7, P0_7 | ADCCON3[7:0] |
| UART Selection | 0 | P0SEL, U0CSR |
| UART Baud Rate | 9600 | U0GCR, U0BAUD |
| Target | Integrated Development Environment | Version | Language |
|---|---|---|---|
| CC2530 | IAR Embedded Workbench for 8051 | 8.10 | C |
| MT3620 | Visual Studio 2017 Community | 15.9.5 | C |
| Desktop | Visual Studio 2017 Community | 15.9.5 | C# |
| Properties | Type |
|---|---|
| Partition key | String |
| Row key | String |
| Timestamp | DateTime |
| Device ID | String |
| Enqueued UTC time | DateTime |
| Processed UTC time | DateTime |
| Gas | Analogue |
| Humidity | Int64 |
| Light | Int64 |
| Sound | Int64 |
| Temperature | Int64 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shi, J.; Jin, L.; Li, J. The Integration of Azure Sphere and Azure Cloud Services for Internet of Things. Appl. Sci. 2019, 9, 2746. https://doi.org/10.3390/app9132746
Shi J, Jin L, Li J. The Integration of Azure Sphere and Azure Cloud Services for Internet of Things. Applied Sciences. 2019; 9(13):2746. https://doi.org/10.3390/app9132746
Chicago/Turabian StyleShi, Jiong, Liping Jin, and Jun Li. 2019. "The Integration of Azure Sphere and Azure Cloud Services for Internet of Things" Applied Sciences 9, no. 13: 2746. https://doi.org/10.3390/app9132746
APA StyleShi, J., Jin, L., & Li, J. (2019). The Integration of Azure Sphere and Azure Cloud Services for Internet of Things. Applied Sciences, 9(13), 2746. https://doi.org/10.3390/app9132746






