Identity Management and Access Control Based on Blockchain under Edge Computing for the Industrial Internet of Things
Abstract
Featured Application
Abstract
1. Introduction
2. Related Work
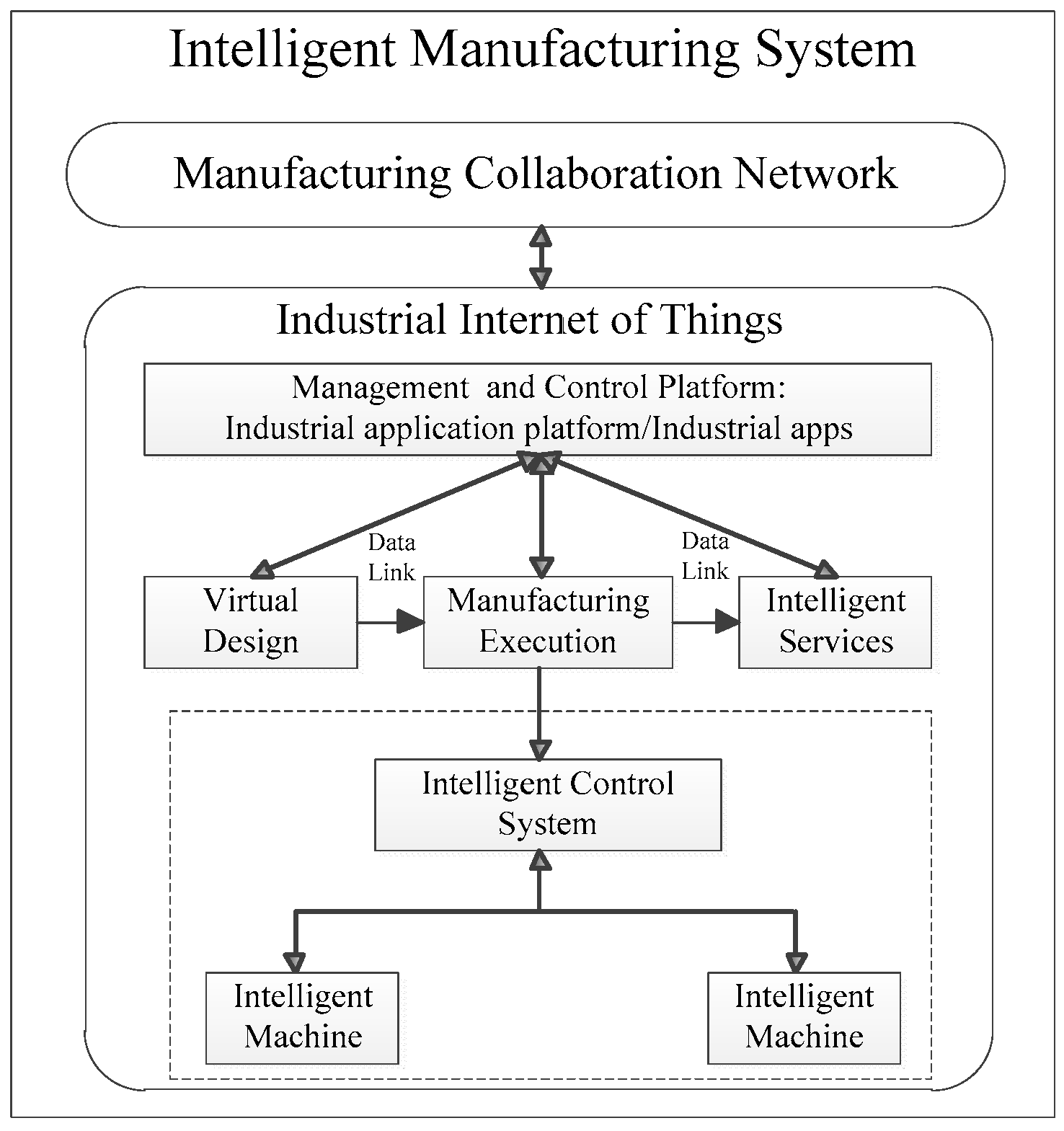
2.1. Intelligent Manufacturing and IIoT
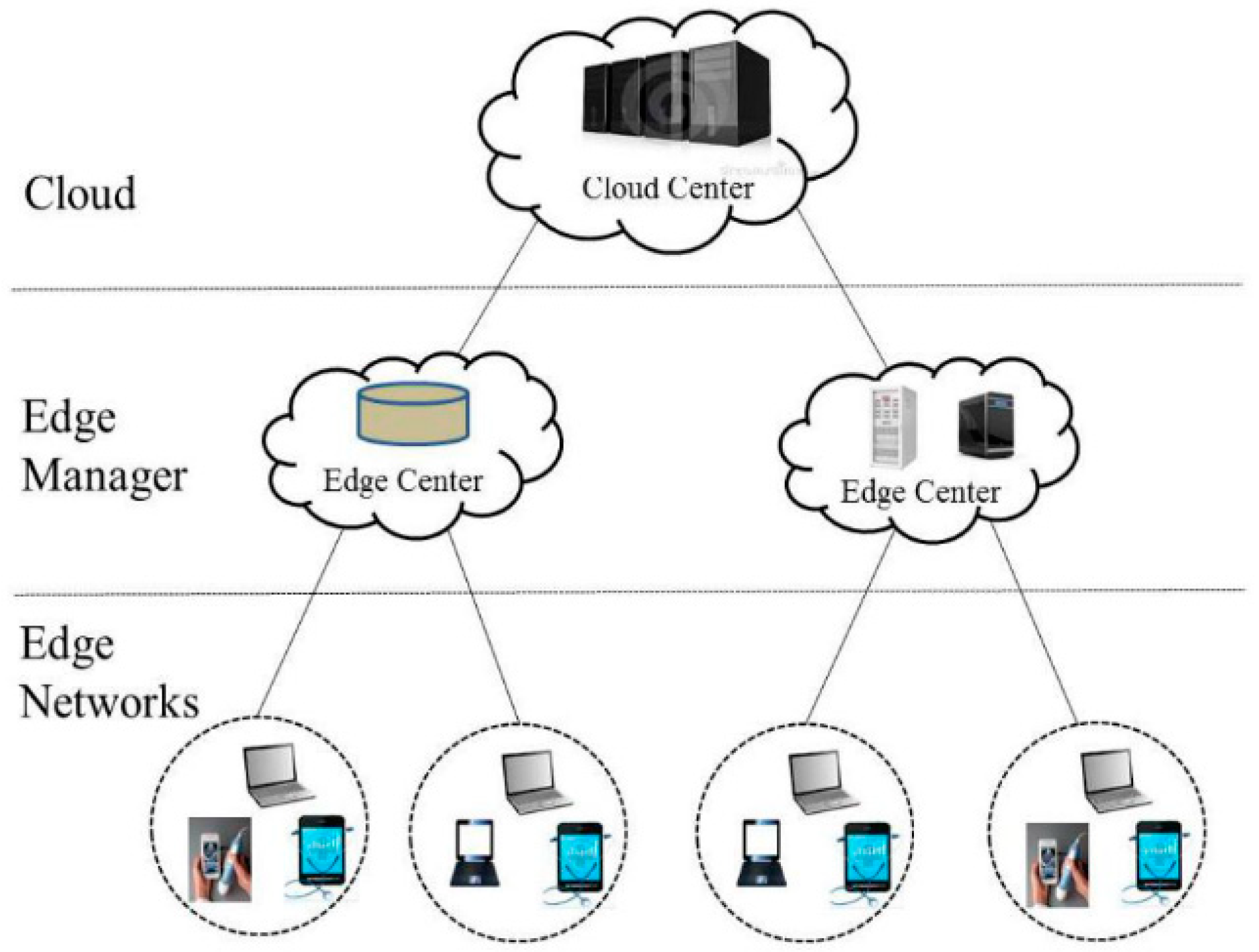
2.2. Edge Computing
2.3. Access Control
3. Problems Statement
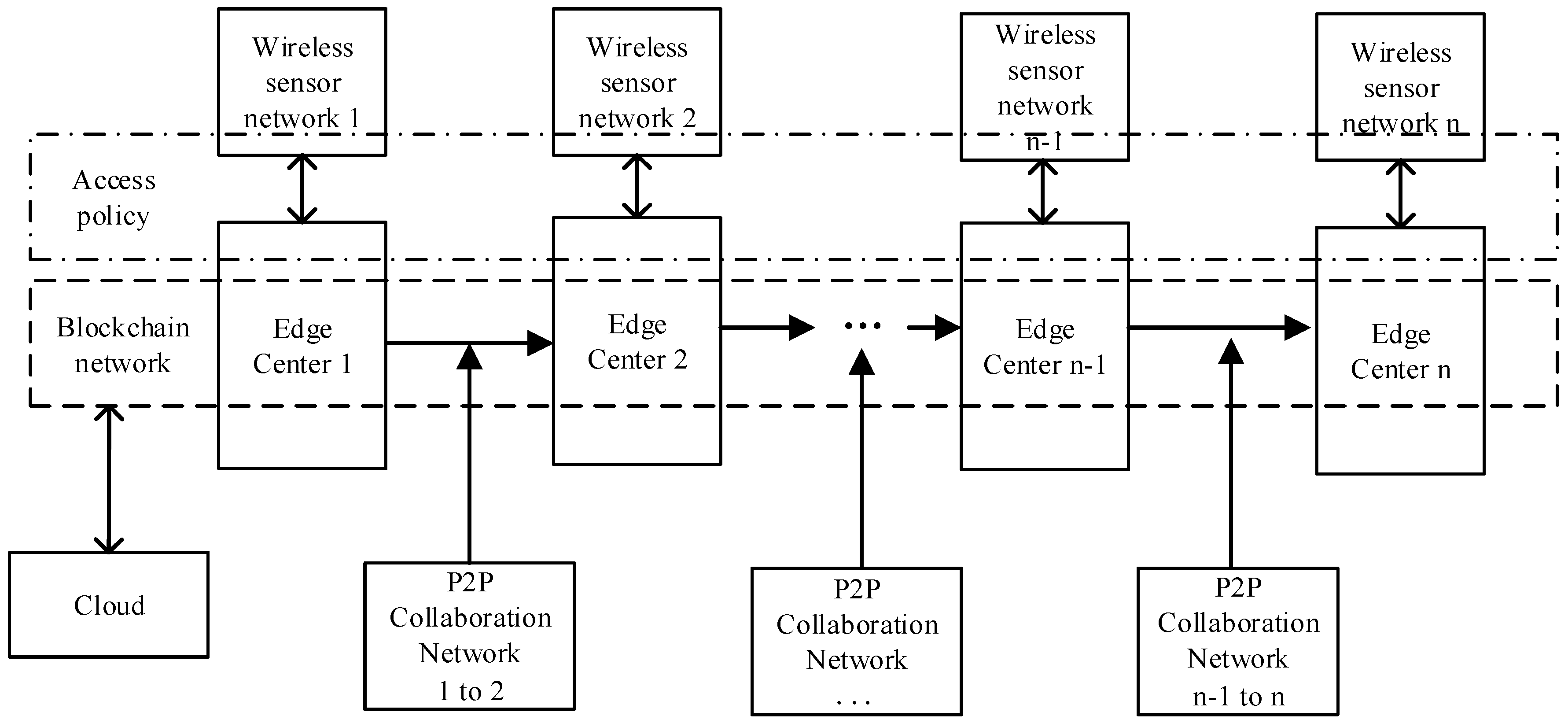
4. Identity Management and Access Control Based on Blockchain under Edge Computing for IIoT
4.1. System Architecture of IIoT
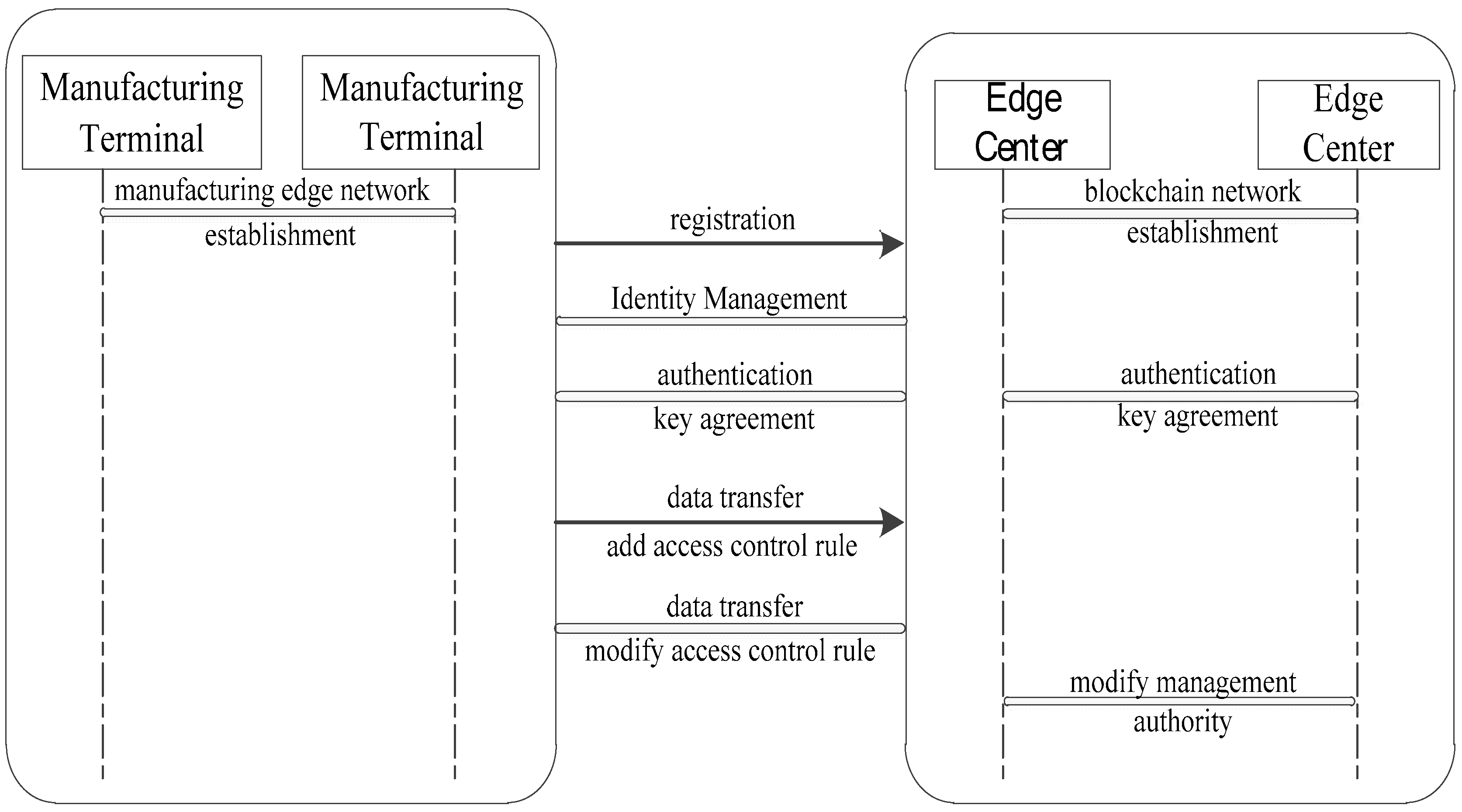
4.2. System Setup and Operation
4.3. Registration and Authentication Based on Self-Certified Public Key
4.4. Certificate and Identity Management Based on Blockchain
4.5. Lightweight Key Exchange Based on Self-Certified Public Key
4.6. Combining Identity Management and Access Policy
4.7. Performance Evaluation
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Xu, L.; He, W.; Li, S. Internet of Things in Industries: A Survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2242. [Google Scholar] [CrossRef]
- Chen, C.; Lin, M.; Liu, C. Edge computing gateway of the industrial Internet of Things using multiple collaborative microcontrollers. IEEE Netw. 2018, 38, 24–32. [Google Scholar] [CrossRef]
- Steiner, W.; Poledna, S. Fog computing as enabler for the Industrial Internet of Things. Elektrotech. Inf. 2016, 133, 310–314. [Google Scholar] [CrossRef]
- Yin, C.Y.; Xi, J.W.; Sun, R.X.; Wang, J. Location Privacy Protection based on Differential Privacy Strategy for Big Data in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3628–3636. [Google Scholar] [CrossRef]
- Kim-Kwang, R.C.; Stefanos, G.; Jong, H.P. Cryptographic solutions for industrial Internet-of-Things: Research challenges and opportunities. IEEE Trans. Ind. Inform. 2018, 14, 3567–3569. [Google Scholar]
- Lian, J.; Zhang, H.; Zhang, Y.; Zhang, Y. Innovative Conception of Industrial Internet of Things. Process Autom. Instrum. 2018, 39, 39–42. [Google Scholar]
- Wang, J.; Cao, J.Y.; Simon, S.R.; Park, J.H. An improved ant colony optimization-based approach with mobile sink for wireless sensor networks. J. Supercomput. 2018, 74, 6633–6645. [Google Scholar] [CrossRef]
- Wang, W.; Deng, Z.; Wang, J. Enhancing Sensor Network Security with Improved Internal Hardware Design. Sensors 2019, 19, 1752. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Z.; Liu, F.; Cai, Z.; Xiao, N. Edge computing: Platforms, applications and challenge. J. Comput. Res. Dev. 2018, 55, 327–337. [Google Scholar]
- Wang, J.; Ju, C.W.; Gao, Y.; Sangaiah, A.K.; Kim, G.J. A PSO based Energy Efficient Coverage Control Algorithm for Wireless Sensor Networks. Comput. Mater. Contin. 2018, 56, 433–446. [Google Scholar]
- Hesham, E.; Sharmi, S.; Mukesh, P.; Deepak, P.; Akshansh, G.; Manoranjan, M.; Lin, C. Edge of Things: The big picture on the Integration of edge, IoT and the cloud in a distributed computing environment. IEEE Access 2017, 6, 1706–1717. [Google Scholar]
- Shirazi, S.N.; Gouglidis, A.; Farshad, A.; Hutchison, D. The extended cloud: Review and analysis of mobile edge computing and fog from a security and resilience perspective. IEEE J. Sel. Areas Commun. 2017, 35, 2586–2595. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Yin, X.; Li, F.; Kim, H. An Enhanced PEGASIS Algorithm with Mobile Sink Support for Wireless Sensor Networks. Wirel. Commun. Mobile Comput. 2018, 2018, 9472075. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhang, D. Near-end cloud computing: Opportunities and challenges in the post-cloud computing era. Chin. J. Comput. 2019, 42, 677–700. [Google Scholar]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile edge computing: A survey. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef]
- Gusev, M.; Dustdar, S. Going back to the roots—The evolution of edge computing, an IoT perspective. IEEE Internet Comput. 2018, 22, 5–15. [Google Scholar] [CrossRef]
- Wang, J.; Cao, Y.Q.; Li, B.; Kim, H.J.; Lee, S. Particle Swarm Optimization based Clustering Algorithm with Mobile Sink for WSNs. Future Gener. Comput. Syst. 2017, 76, 452–457. [Google Scholar] [CrossRef]
- Tirkolaee, E.B.; Hosseinabadi, A.A.R.; Soltani, M.; Sangaiah, A.K.; Wang, J. A Hybrid Genetic Algorithm for Multi-trip Green Capacitated Arc Routing Problem in the Scope of Urban Services. Sustainability 2018, 10, 1366. [Google Scholar] [CrossRef]
- Wang, J.; Cao, J.Y.; Ji, S.; Park, H.J. Energy Efficient Cluster-based Dynamic Routes Adjustment Approach for Wireless Sensor Networks with Mobile Sinks. J. Supercomput. 2017, 73, 3277–3290. [Google Scholar] [CrossRef]
- Gao, Y.; Wang, J.; Wu, W.; Sangaiah, A.K.; Lim, S. A Hybrid Method for Mobile Agent Moving Trajectory Scheduling using ACO and PSO in WSNs. Sensors 2019, 19, 575. [Google Scholar] [CrossRef]
- Pan, J.; McElhannon, J. Future Edge Cloud and Edge Computing for Internet of Things Applications. IEEE Internet Things J. 2018, 5, 439–449. [Google Scholar] [CrossRef]
- He, D.; Chan, S.; Guizani, M. Security in the IoT supported by mobile edge computing. IEEE Commun. Mag. 2018, 56, 56–61. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-Physical Systems Security—A Survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Tschorsch, F.; Scheuermann, B. Bitcoin and beyond: A technical survey on decentralized digital currencies. IEEE Commun. Surv. Tutor. 2018, 18, 2084–2123. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.J. An Improved Routing Schema with Special Clustering using PSO Algorithm for Heterogeneous Wireless Sensor Network. Sensors 2019, 19, 671. [Google Scholar] [CrossRef]
- Ren, Y.; Liu, Y.; Ji, S.; Sangaiah, A.K.; Wang, J. Incentive Mechanism of Data Storage Based on Blockchain for Wireless Sensor Networks. Mob. Inf. Syst. 2018, 2018. [Google Scholar] [CrossRef]
- Kyusakov, R.; Eliasson, J.; Delsing, J. Integration of wireless sensor and actuator nodes with it infrastructure using service-oriented architecture. IEEE Trans. Ind. Inform. 2013, 9, 43–51. [Google Scholar] [CrossRef]
- Zeng, D.; Dai, Y.; Li, F.; Sherratt, B.; Wang, J. Adversarial learning for distant supervised relation extraction. CMC Comput. Mater. Contin. 2018, 55, 243–254. [Google Scholar]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog computing for the Internet of Things: Security and privacy issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Satyanarayanan, M. The emergence of edge computing. IEEE Comput. 2017, 50, 30–39. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Wu, W.; Lim, S.J. An Asynchronous Clustering and Mobile Data Gathering Schema based on Timer Mechanism in Wireless Sensor Networks. Comput. Mater. Contin. 2019, 58, 711–725. [Google Scholar] [CrossRef]
- Ouaddah, A.; Mousannif, H.; Elkalam, A.; Ouahman, A. Access control in the Internet of Things: Big challenges and new opportunities. Comput. Netw. 2017, 112, 237–262. [Google Scholar] [CrossRef]
- Vahid, R.; Karimi, P.; Alencar, C.; Donald, D. A formal modeling and analysis approach for access control rules, policies, and their combinations. Int. J. Inf. Secur. 2017, 16, 43–74. [Google Scholar]
- Kumar, D.; Ashish, M.; Sagar, P. A novel proxy signature scheme based on user hierarchical access control policy. J. King Saud Univ. 2013, 25, 219–228. [Google Scholar]
- Cirani, S.; Picone, M.; Gonizzi, P. Iot-OAS: An OAuth-based authorization service architecture for secure services in IoT scenarios. J. Sens. 2015, 15, 1224–1234. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Huang, X.; Choo, K.; Athanasios, K. BSeIn: A blockchain-based secure mutual authentication with fine-grained access control system for industry 4.0. J. Netw. Comput. Appl. 2018, 116, 42–52. [Google Scholar] [CrossRef]
- Konstantions, C.; Michael, D. Blockchains and smart contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar]
- Aafaf, O.; Anas, A.E.; Abdellah, A.O. FairAccess: A new Blockchain-based access control framework for the Internet of Things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar]
- Maesa, D.D.F.; Mori, P.; Ricci, L. Blockchain Based Access Control. Distrib. Appl. Interoper. Syst. 2017, 10320, 206–220. [Google Scholar]
- Novo, O. Blockchain meets IoT: An architecture for scalable access management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Ren, Y.J.; Leng, Y.; Cheng, Y.P.; Wang, J. Secure data storage based on blockchain and coding in edge computing. Math. Biosci. Eng. 2019, 16, 1874–1892. [Google Scholar] [CrossRef]
- Tsaur, W. Several security schemes constructed using ECC-based self-certified public key cryptosystems. Appl. Math. Comput. 2005, 168, 447–464. [Google Scholar] [CrossRef]
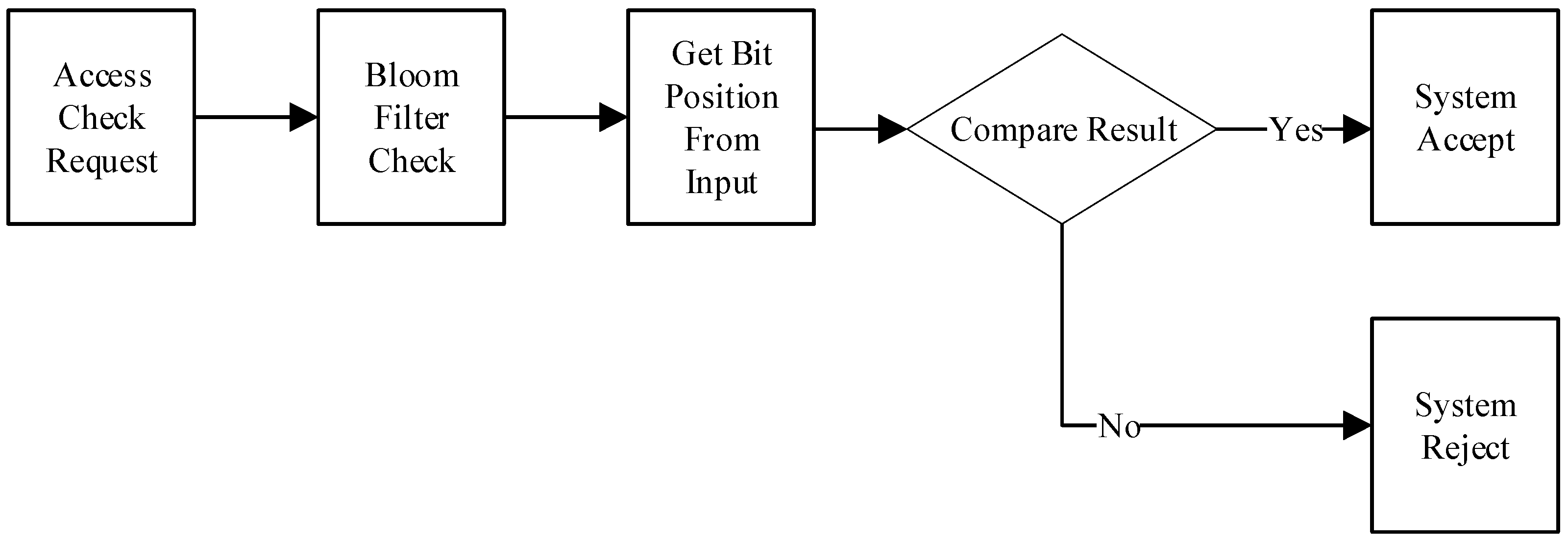
- Hieb, J.; Schreiver, J.; Graham, J. Using bloom filters to ensure access control and authentication requirements for SCADA field devices. Crit. Infrastruct. Prot. 2012, 390, 85–97. [Google Scholar]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, Y.; Zhu, F.; Qi, J.; Wang, J.; Sangaiah, A.K. Identity Management and Access Control Based on Blockchain under Edge Computing for the Industrial Internet of Things. Appl. Sci. 2019, 9, 2058. https://doi.org/10.3390/app9102058
Ren Y, Zhu F, Qi J, Wang J, Sangaiah AK. Identity Management and Access Control Based on Blockchain under Edge Computing for the Industrial Internet of Things. Applied Sciences. 2019; 9(10):2058. https://doi.org/10.3390/app9102058
Chicago/Turabian StyleRen, Yongjun, Fujian Zhu, Jian Qi, Jin Wang, and Arun Kumar Sangaiah. 2019. "Identity Management and Access Control Based on Blockchain under Edge Computing for the Industrial Internet of Things" Applied Sciences 9, no. 10: 2058. https://doi.org/10.3390/app9102058
APA StyleRen, Y., Zhu, F., Qi, J., Wang, J., & Sangaiah, A. K. (2019). Identity Management and Access Control Based on Blockchain under Edge Computing for the Industrial Internet of Things. Applied Sciences, 9(10), 2058. https://doi.org/10.3390/app9102058





