Identifying Node Importance in a Complex Network Based on Node Bridging Feature
Abstract
1. Introduction
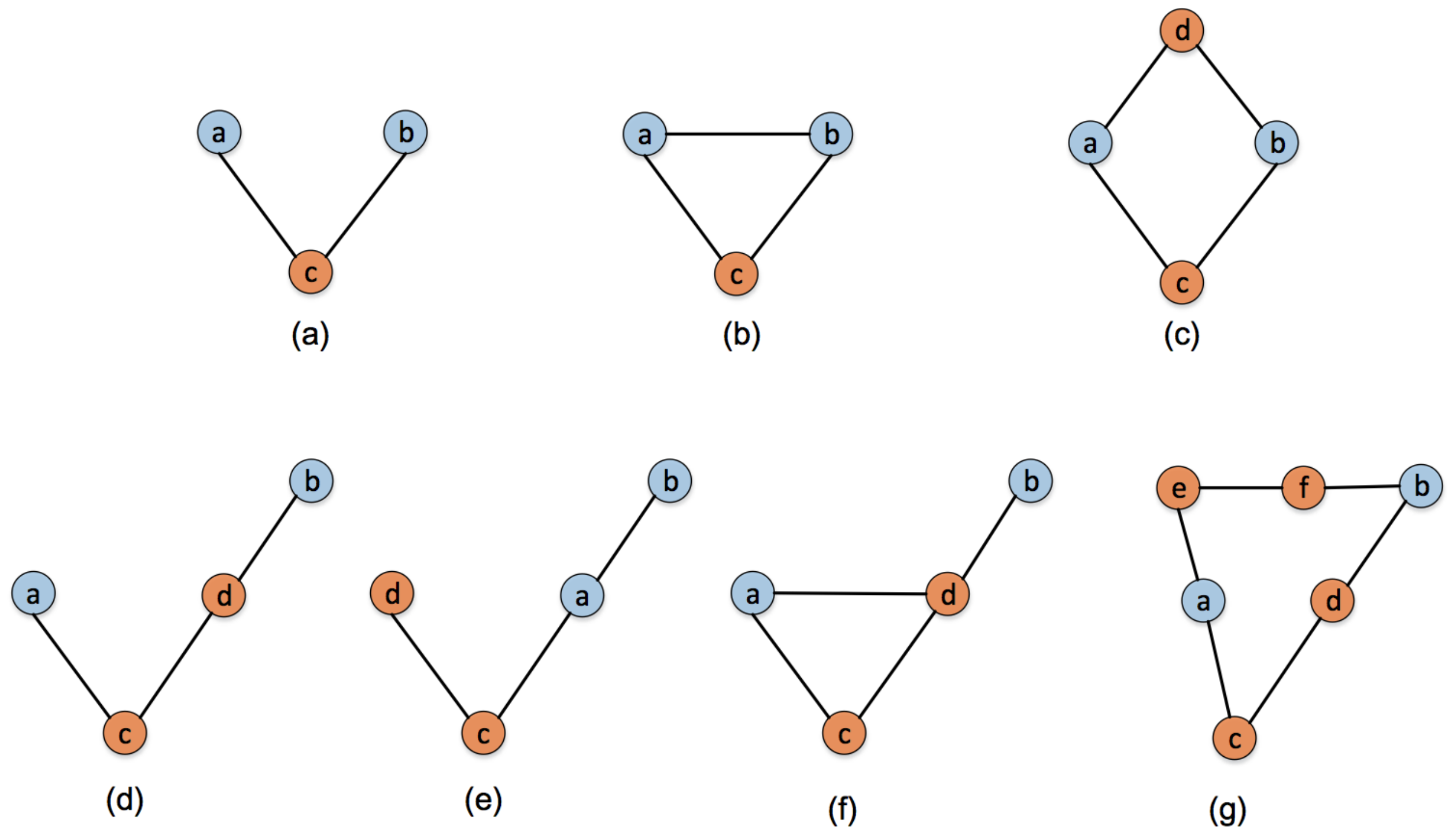
- The paper presents a node bridging feature in complex networks, which refers to the fact that the greater the number of node pairs whose shortest paths pass through the target node and the less the number of shortest paths in its neighborhood, the more significant bridge function and structure importance the node has;
- We propose a novel node importance identification algorithm based on the node bridging feature, which just needs local information of the target nodes, making the algorithm applicable in large-scale networks;
- Through comprehensive experiments on real and synthetic datasets, the proposed algorithm is demonstrated to outperform a state-of-the-art model compared with five benchmark algorithms on evaluation criteria of the maximum connectivity coefficient and the decline rate of network efficiency, no matter whether in static or dynamic attack strategies;
- The advantage of the proposed algorithm is more obvious when removing a small number of important nodes, which makes the algorithm applicable in the background of limited network attack cost.
2. Materials and Methods
2.1. The Proposed Method
2.2. Benchmark Methods
- Degree centralityDegree centrality is a very simple ranking algorithm. The node degree represents the number of neighbours of node i, namely
- K-shell algorithmThe implementation of the k-shell decomposition method is as follows: firstly, continuously remove the nodes with degree one until all nodes’ degrees are larger than one. All of these removed nodes are assigned 1-shell. Then, keep removing the existing nodes until all nodes’ degrees are larger than two and add the removed nodes to 2-shell. Repeat this procedure until all nodes have been assigned to one of the shells.
- WL algorithmWL algorithm holds the opinion that the importance of nodes in the network is closely related to the importance of edges the nodes connected. The weight of edge is expressed aswhere is the degree of node i. The weight of node is expressed aswhere is the set of neighbors of node i. Thus, the importance of the node is expressed as
- Ego betweenness (Abbreviated as EgoBet)Ego network consists of a target node and the nodes (1-hop neighbors) which are connected to the target node and all the edges between those nodes. The standard measure of betweenness considers all the shortest paths of node pairs across the target node, while ego betweenness just takes into account the shortest paths of node pairs within the ego network. Ego betweenness can be expressed aswhere is the number of shortest paths passing through node i between node s and node t, is the total number of shortest paths between node s and node t, and represents the set of 1-hop neighbors of node i.
- LLS algorithmLLS algorithm is a method to evaluate the importance of nodes based on similarity of node neighbors. The similarity of node neighbors is calculated by Jaccard index when nodes b and c are not connected, while the value of similarity is 1 when nodes b and c are connected, namelywhere is the set of one hop and two hop neighbors of node i. Thus, the node importance is denoted as
2.3. Evaluation Criterion of Algorithms
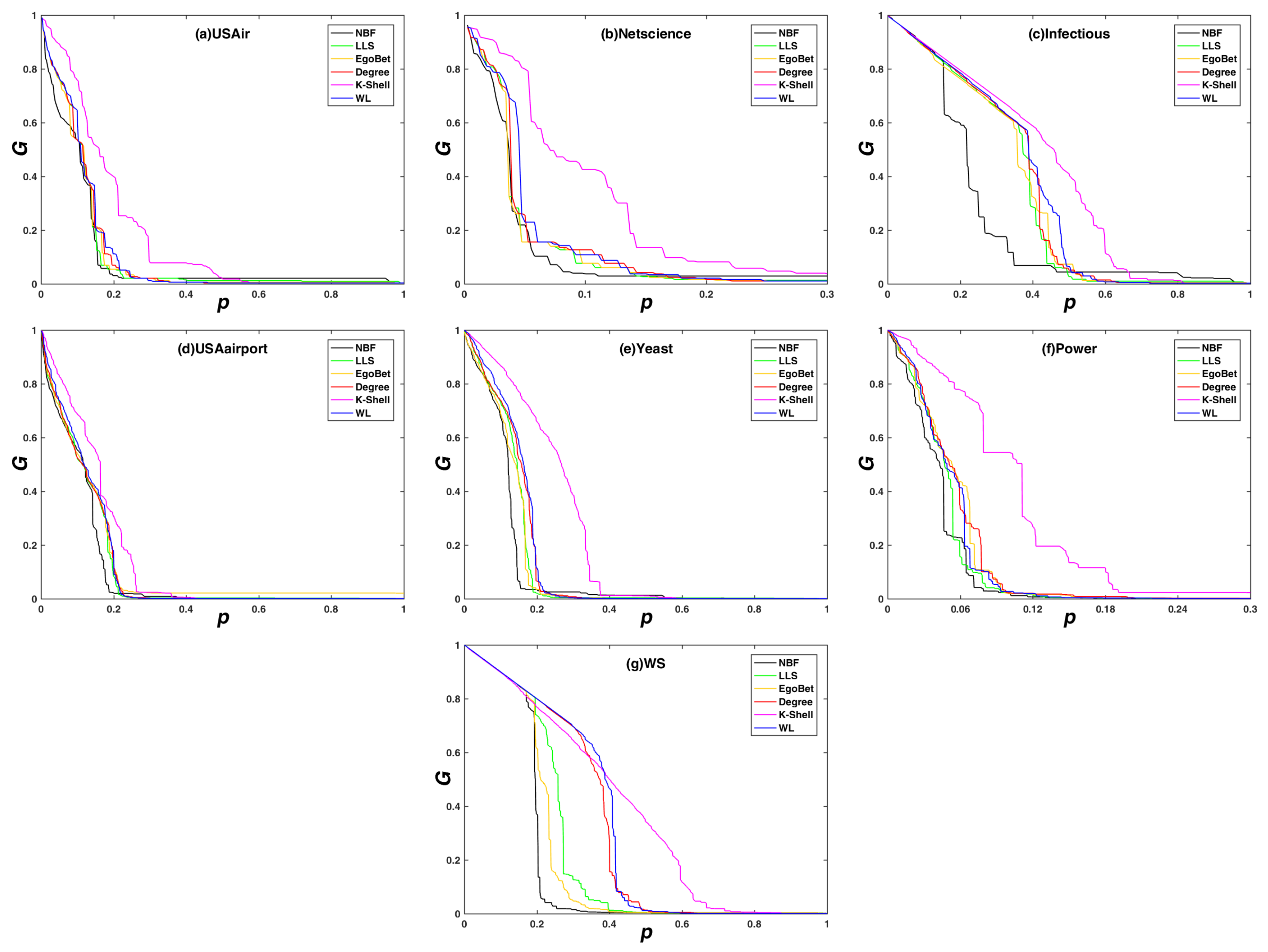
2.3.1. Maximum Connectivity Coefficient
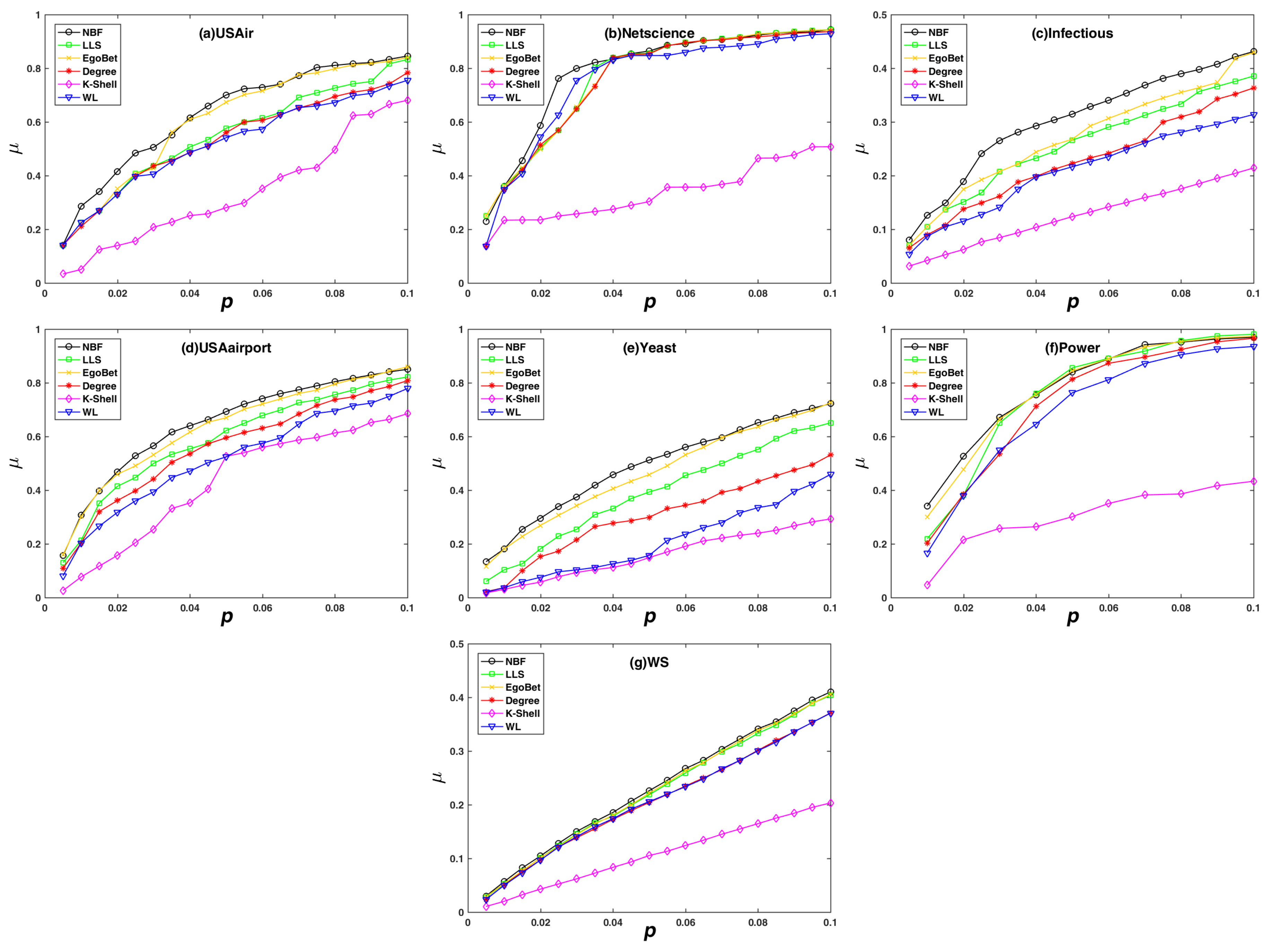
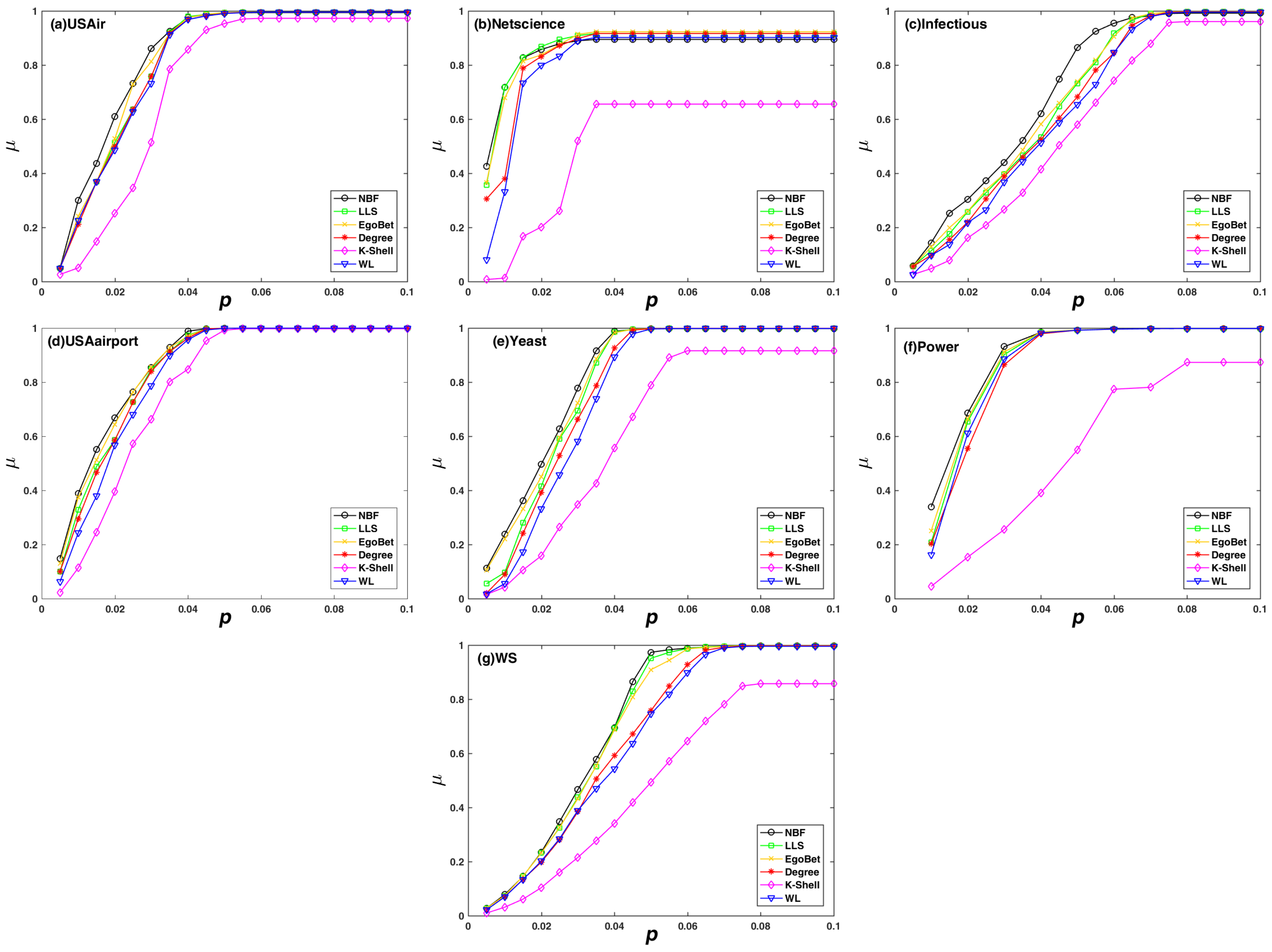
2.3.2. Decline Rate of Network Efficiency
2.4. Data Description
3. Results and Analysis
3.1. Experimental Results on the Maximum Connectivity Coefficient
3.2. Experimental Results on the Decline Rate of Network Efficiency
3.3. Complexity Analysis
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Barabási, A.L.; Albert, R. Emergence of scaling in random networks. Science 1999, 286, 509–512. [Google Scholar] [PubMed]
- Watts, D.J.; Strogatz, S.H. Collective dynamics of ’small-world’ networks. Nature 1998, 393, 440–442. [Google Scholar] [CrossRef] [PubMed]
- Dorogovtsev, S.N.; Goltsev, A.V.; Mendes, J.F.F. Critical phenomena in complex networks. Rev. Mod. Phys. 2007, 80, 1275–1335. [Google Scholar] [CrossRef]
- Albert, R.; Barabási, A.L. Statistical mechanics of complex networks. Rev. Mod. Phys. 2002, 74, 47–97. [Google Scholar] [CrossRef]
- Jun, T.; Piera, M.A.; Ruiz, S. A causal model to explore the ACAS induced collisions. J. Aerosp. Eng. 2014, 228, 1735–1748. [Google Scholar] [CrossRef]
- Wang, G.Z.; Cao, Y.J.; Bao, Z.J.; Han, Z.X. A novel local-world evolving network model for power grid. Acta Phys. Sin. 2009, 58, 3597–3602. [Google Scholar]
- Li, Y.S.; Ma, D.Z.; Zhang, H.G.; Sun, Q.Y. Critical nodes identification of power systems based on controllability of complex networks. Appl. Sci. 2015, 5, 622–636. [Google Scholar] [CrossRef]
- Zhao, X.; Xiao, C.; Lin, X.; Zhang, W.; Wang, Y. Efficient structure similarity searches: A partition-based approach. VLDB J. 2018, 27, 53–78. [Google Scholar] [CrossRef]
- Milo, R.; Shen-Orr, S.; Itzkovitz, S.; Kashtan, N.; Chklovskii, D.; Alon, U. Network motifs: Simple building blocks of complex networks. Science 2002, 298, 824–827. [Google Scholar] [CrossRef] [PubMed]
- Kinney, R.; Crucitti, P.; Albert, R.; Latora, V. Modeling cascading failures in the North American power grid. Eur. Phys. J. 2005, 46, 101–107. [Google Scholar] [CrossRef]
- Rogers, T. Assessing node risk and vulnerability in epidemics on networks. Europhys. Lett. 2015, 109, 28005–28011. [Google Scholar] [CrossRef]
- Nie, T.; Guo, Z.; Zhao, K.; Lu, Z.M. Using mapping entropy to identify node centrality in complex networks. Phys. A Stat. Mech. Appl. 2016, 453, 290–297. [Google Scholar] [CrossRef]
- Liu, J.; Xiong, Q.; Shi, W.; Shi, X.; Wang, K. Evaluating the importance of nodes in complex networks. Phys. A Stat. Mech. Appl. 2016, 452, 209–219. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, F.M.; Zhou, W.P.; Zou, W.; Yang, F. Evaluating complex network functional robustness by node efficiency. Acta Phys. Sin. 2012, 61, 190201. [Google Scholar]
- Chen, G.; Dong, Z.Y.; Hill, D.J.; Zhang, G.H.; Hua, K.Q. Attack structural vulnerability of power grids: A hybrid approach based on complex networks. Phys. A Stat. Mech. Appl. 2010, 389, 595–603. [Google Scholar] [CrossRef]
- Dey, P.; Mehra, R.; Kazi, F.; Wagh, S.; Singh, N.M. Impact of topology on the propagation of cascading failure in power grid. IEEE Trans. Smart Grid 2016, 7, 1970–1978. [Google Scholar] [CrossRef]
- Jung, J.; Liu, C.C. Multi-agent technology for vulnerability assessment and control. In Proceedings of the Power Engineering Society Summer Meeting, Vancouver, BC, Canada, 15–19 July 2001; pp. 1287–1292. [Google Scholar]
- Zhang, G.; Yu, S.S.; Zou, S.; Iu, H.H.; Fernando, T.; Zhang, Y. An Investigation into Cascading Failure in Large-Scale Electric Grids: A Load-Redistribution Approach. Appl. Sci. 2018, 8, 2076–3417. [Google Scholar] [CrossRef]
- Tan, Y.J.; Wu, J.; Deng, H.Z.; Zhu, D.Z. Invulnerability of Complex Networks: A Survey. Syst. Eng. 2006, 24, 1–5. [Google Scholar]
- Zamora-López, G.; Zhou, C.H.; Kurths, J. Cortical hubs form a module for multisensory integration on top of hierarchy of cortical networks. Front. Comput. Neurosci. 2010, 4, 1–13. [Google Scholar] [CrossRef] [PubMed]
- Crucitti, P.; Latora, V.; Marchiori, M. Model for cascading failures in complex networks. Phys. Rev. E 2004, 69, 045104. [Google Scholar] [CrossRef] [PubMed]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Rong, L.; Zhang, L.; Zhang, Z. Attack vulnerability of scale-free networks due to cascading failures. Phys. A Stat. Mech. Appl. 2008, 387, 6671–6678. [Google Scholar] [CrossRef]
- Boccaletti, S.; Latora, V.; Moreno, Y.; Chavez, M.; Hwang, D.U. Complex networks: Structure and dynamics. Phys. Rep. 2006, 424, 175–308. [Google Scholar] [CrossRef]
- Restrepo, J.G.; Ott, E.; Hunt, B.R. Characterizing the dynamical importance of network nodes and links. Phys. Rev. Lett. 2006, 97, 094102. [Google Scholar] [CrossRef] [PubMed]
- Albert, R.; Jeong, H.; Barabási, A.L. Internet: Diameter of the world-wide web. Nature 1999, 401, 130–131. [Google Scholar] [CrossRef]
- Sabidussi, G. The centrality index of a graph. Psyehometrika 1966, 31, 581–603. [Google Scholar] [CrossRef]
- Freeman, L.C. A set of measures of centrality based on betweenness. Sociometry 1977, 40, 35–41. [Google Scholar] [CrossRef]
- Barthelemy, M. Betweenness centrality in large complex networks. Eur. Phys. J. B 2004, 38, 163–168. [Google Scholar] [CrossRef]
- Everett, M.; Borgatti, S.P. Ego network betweenness. Soc. Netw. 2005, 27, 31–38. [Google Scholar] [CrossRef]
- Pfeffer, J.; Carley, K.M. k-centralities: Local approximations of global measures based on shortest paths. In Proceedings of the 21st International Conference on World Wide Web, Lyon, France, 16–20 April 2012; pp. 1043–1050. [Google Scholar]
- Stai, E.; Sotiropoulos, K.; Karyotis, V.; Papavassiliou, S. Hyperbolic Embedding for Efficient Computation of Path Centralities and Adaptive Routing in Large-Scale Complex Commodity Networks. IEEE Trans Netw. Sci. Eng. 2017, 4, 140–153. [Google Scholar] [CrossRef]
- Puzis, R.; Zilberman, P.; Elovici, Y.; Dolev, S.; Brandes, U. Heuristics for speeding up betweenness centrality computation. In Proceedings of the 2012 International Conference on Privacy, Security, Risk and Trust and 2012 International Confernece on Social Computing, Amsterdam, The Netherlands, 3–5 September 2012; pp. 302–311. [Google Scholar]
- Brandes, U.; Pich, C. Centrality estimation in large networks. Int. J. Bifurc. Chaos 2007, 17, 2303–2318. [Google Scholar] [CrossRef]
- Kitsak, M.; Gallos, L.K.; Havlin, S.; Liljeros, F.; Muchnik, L.; Eugene Stanley, H.; Makse, H.A. Identification of influential spreaders in complex networks. Nat. Phys. 2010, 6, 888–893. [Google Scholar] [CrossRef]
- Wang, J.W.; Rong, L.L.; Guo, T.Z. A new measure method of network node importance based on local characteristics. J. Dalian Univ. Technol. 2010, 50, 822–826. [Google Scholar]
- Ugander, J.; Backstrom, L.; Marlow, C.; Kleinberg, J. Structural diversity in social contagion. Proc. Natl. Acad. Sci. USA 2012, 109, 5962–5966. [Google Scholar] [CrossRef] [PubMed]
- Ai, X. Node importance ranking of complex networks with entropy variation. Entropy 2017, 19, 303. [Google Scholar] [CrossRef]
- Ruan, Y.R.; Lao, S.Y.; Wang, J.D.; Bai, L.; Chen, L.D. Node importance measurement based on neighborhood similarity in complex network. Acta Phys. Sin. 2017, 66, 038902. [Google Scholar]
- Dereich, S.; Mörters, P. Random networks with sublinear preferential attachment: The giant component. Ann. Probab. 2013, 41, 329–384. [Google Scholar] [CrossRef]
- Vragović, I.; Louis, E.; Díaz-Guilera, A. Efficiency of informational transfer in regular and complex networks. Phys. Rev. E 2005, 71, 036122. [Google Scholar] [CrossRef] [PubMed]
- Latora, V.; Marchiori, M. A measure of centrality based on network efficiency. New J. Phys. 2007, 9, 188. [Google Scholar] [CrossRef]
- Batagelj, V.; Mrvar, A. Pajek-program for large network analysis. Connections 1998, 21, 47–57. [Google Scholar]
- Zeng, A.; Liu, W. Enhancing network robustness against malicious attacks. Phys. Rev. E 2012, 85, 066130. [Google Scholar] [CrossRef] [PubMed]
- Newman, M.E. Finding community structure in networks using the eigenvectors of matrices. Phys. Rev. E 2006, 74, 036104. [Google Scholar] [CrossRef] [PubMed]
- Chen, D.; Lü, L.; Shang, M.S.; Zhang, Y.C.; Zhou, T. Identifying influential nodes in complex networks. Phys. A Stat. Mech. Appl. 2012, 391, 1777–1787. [Google Scholar] [CrossRef]
- Isella, L.; Stehle, J.; Barrat, A.; Cattuto, C.; Pinton, J.F.; vanden Broeck, W. What’s in a crowd? Analysis of face-to-face behavioral networks. J. Theor. Biol. 2011, 271, 166–180. [Google Scholar] [CrossRef] [PubMed]
- Andrews, M.A.; Bauch, C.T. The impacts of simultaneous disease intervention decisions on epidemic outcomes. J. Theor. Biol. 2016, 395, 1–10. [Google Scholar] [CrossRef] [PubMed]
- Lü, L.; Chen, D.; Ren, X.L.; Zhang, Q.M.; Zhang, Y.C.; Zhou, T. Vital nodes identification in complex networks. Phys. Rep. 2016, 650, 1–63. [Google Scholar] [CrossRef]
- Sun, X.; Gollnick, V.; Wandelt, S. Robustness analysis metrics for worldwide airport network: A comprehensive study. Chin. J. Aeronaut. 2017, 30, 500–512. [Google Scholar] [CrossRef]
- Von Mering, C.; Krause, R.; Snel, B.; Cornell, M.; Oliver, S.G.; Fields, S.; Bork, P. Comparative assessment of large-scale data sets of protein-protein interactions. Nature 2002, 417, 399–403. [Google Scholar] [CrossRef] [PubMed]
- Guelzim, N.; Bottani, S.; Bourgine, P.; Kepes, F. Topological and causal structure of the yeast transcriptional regulatory network. Nat. Genet. 2002, 31, 60–63. [Google Scholar] [CrossRef] [PubMed]

| Network | n | m | 〈k〉 | C | L |
|---|---|---|---|---|---|
| USAir | 332 | 2126 | 12.807 | 0.625 | 2.729 |
| Netscience | 379 | 914 | 4.823 | 0.741 | 6.026 |
| Infectious | 410 | 2765 | 13.488 | 0.456 | 3.631 |
| USAirport | 1574 | 28,236 | 21.901 | 0.505 | 3.113 |
| Yeast | 2375 | 11,693 | 9.847 | 0.306 | 5.094 |
| Power | 4941 | 6964 | 2.669 | 0.080 | 18.989 |
| Method | Information | Computational Complexity |
|---|---|---|
| K-shell | Global information | |
| WL | Local information | |
| Degree | Local information | |
| EgoBet | Local information | |
| LLS | Local information | |
| NBF | Local information |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, L.; Jing, Y.; Hu, S.; Ge, B.; Xiao, W. Identifying Node Importance in a Complex Network Based on Node Bridging Feature. Appl. Sci. 2018, 8, 1914. https://doi.org/10.3390/app8101914
Jiang L, Jing Y, Hu S, Ge B, Xiao W. Identifying Node Importance in a Complex Network Based on Node Bridging Feature. Applied Sciences. 2018; 8(10):1914. https://doi.org/10.3390/app8101914
Chicago/Turabian StyleJiang, Lincheng, Yumei Jing, Shengze Hu, Bin Ge, and Weidong Xiao. 2018. "Identifying Node Importance in a Complex Network Based on Node Bridging Feature" Applied Sciences 8, no. 10: 1914. https://doi.org/10.3390/app8101914
APA StyleJiang, L., Jing, Y., Hu, S., Ge, B., & Xiao, W. (2018). Identifying Node Importance in a Complex Network Based on Node Bridging Feature. Applied Sciences, 8(10), 1914. https://doi.org/10.3390/app8101914




