Research of Integrity and Authentication in OPC UA Communication Using Whirlpool Hash Function
Abstract
:1. Introduction
2. Overview of Whirlpool Hash Function
2.1. Principle of Whirlpool
- (1)
- Append padding bits. The message is padded so that its length is congruent to 256 modulo 512, that is to say, the length of padded message is some times of 512 minus 256, and the reserved 256 bits will be used in step 2. The pattern of padding is the same, it consists of a single 1-bit followed by the necessary of 0-bits.
- (2)
- Append length. The padded message is appended by a block of 256 bits representing the length of message before the padding. After that the message m can be divided into t 512-bit blocks m1, ⋯, mt, each block can be treated as an 8 × 8 byte array called hash state.
- (3)
- Substitute bytes. This is a non-linear byte substitution, each byte of a state is substituted individually according to a table called S-box.
- (4)
- Shift columns. The shift column transformation is a simple cyclical permutation performed against a state column by column except column 0. For column i, it is shifted downwards by i − 1 bytes.
- (5)
- Mix rows. In this step, each row of a state array is treated as a polynomial a(x) over Galois field GF(28), a(x) is multiplied by a fixed polynomial c(x) modulo x8 + x4 + x3 + x2 + 1. The polynomial c(x) is expressed in the following formula in the designing of Whirlpool (the factors are expressed in hexadecimal numbers).
- (6)
- Add round key. This step is a simple bitwise XOR calculation between the state and round key. The round key is derived from a seed key and the length of round key is equal to the block size. The key schedule is same as the round function.
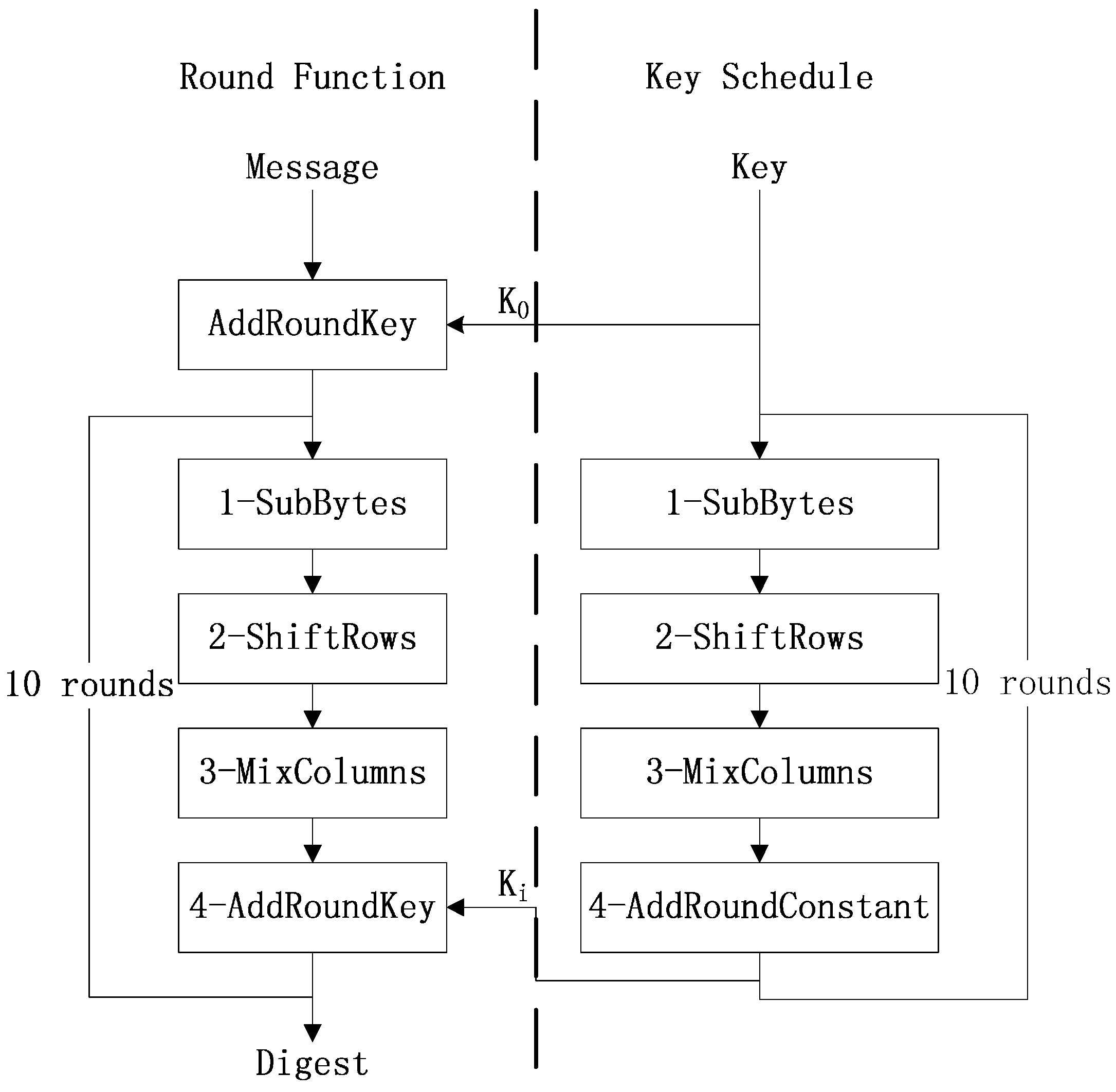
2.2. Features of Whirlpool
2.2.1. Adoption of AES-Like Structure to Construct Compression Function
2.2.2. Using Miyaguchi-Preneel Scheme to Construct Hash Function
2.2.3. Convenient for Hardware Implementation
2.3. Comparison between Whirlpool and SHA-1
2.3.1. Computation Speed
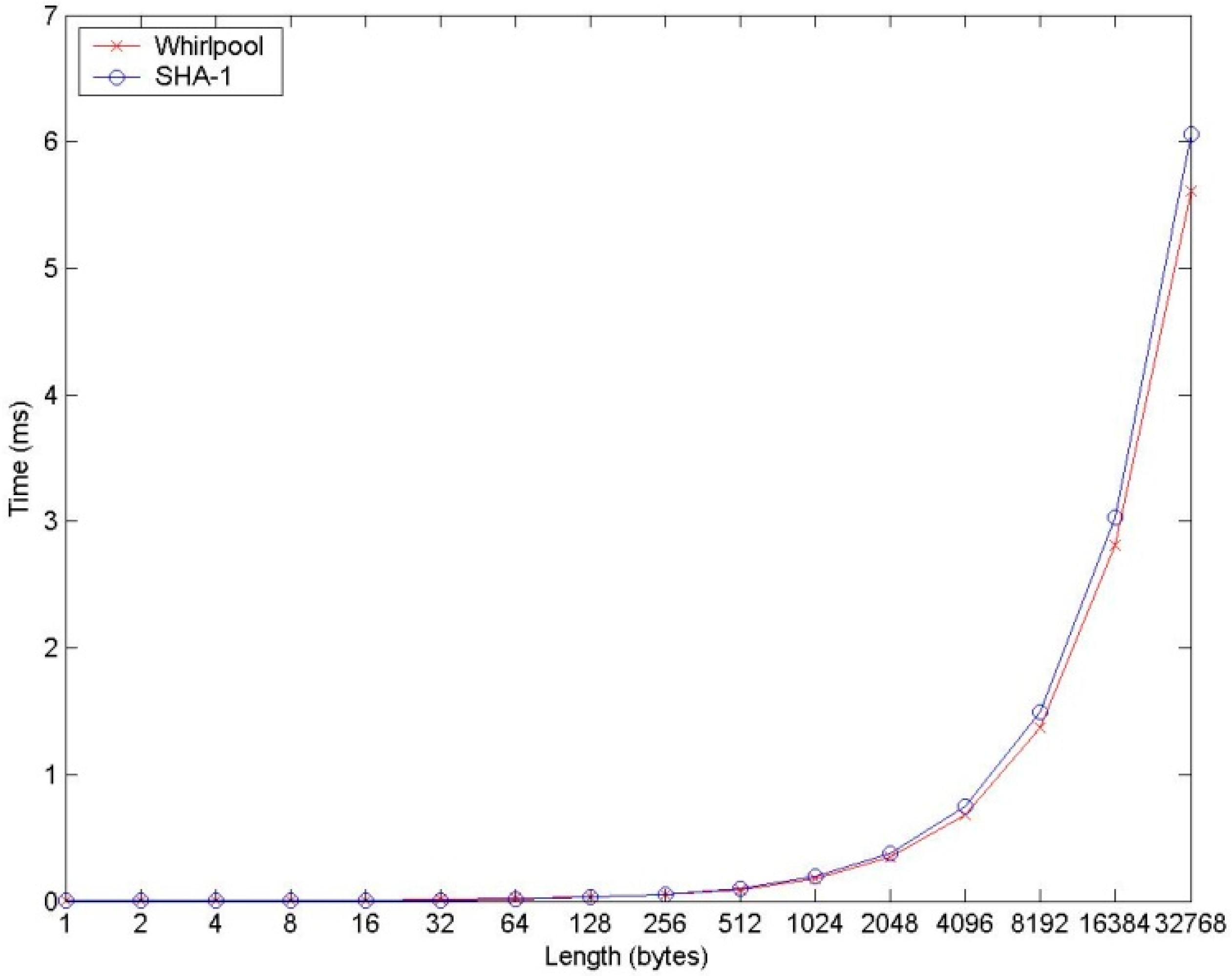
2.3.2. Security
3. Security Communication Model of OPC UA Based on Whirlpool
3.1. Architecture of Model
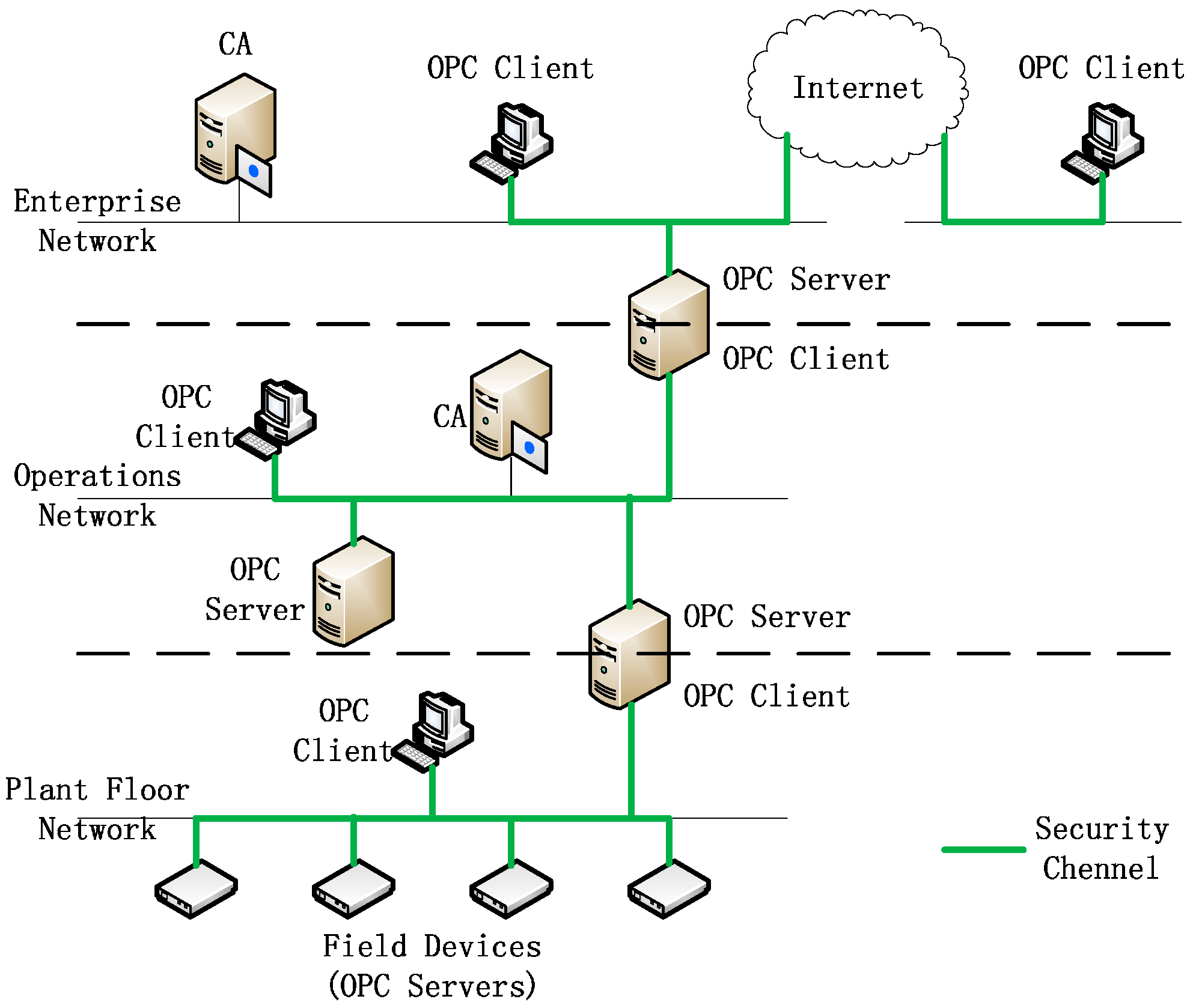
3.2. Procedure of Security Channel Establishment
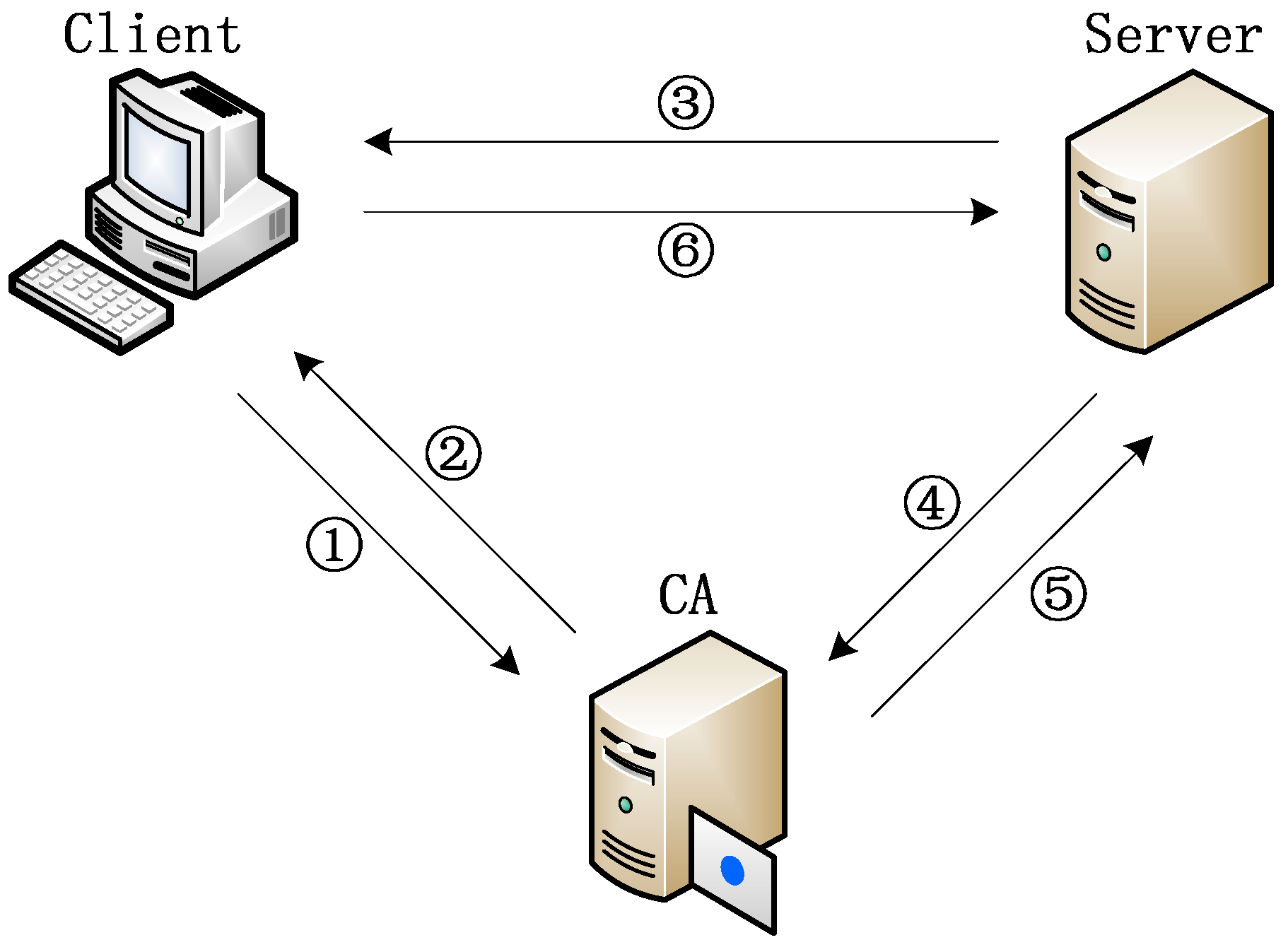
- (1)
- Before building a security channel, the client requests CA to authenticate whether the server is legal. The contents of authentication include CA signature, issue and expiry date, and CA revocation list.
- (2)
- The CA returns the result of authentication to the client.
- (3)
- The client requests the server to build security connection. The client provides its certificate and a nonce to the server. The data to be sent are signed with the private key of the client, and then encrypted by the public key of the server.
- (4)
- After the connection request is received by the server, the server requests CA to authenticate the client. The contents of authenticate also include CA signature, issue and expiry date, and CA revocation list.
- (5)
- The CA returns the result of authentication to the server.
- (6)
- After the client is authenticated, the server responses the connection request from the client. The server sends a nonce, security token, and the lifetime of the token to the client. The contents to be sent is encrypted by the private key of the server, and then encrypted by the public key of the client. After that the client and the server can communicate with each other through the security channel. In the subsequent communication, the receiver of the message calculates the digest of the received message using Whirlpool, then compares it with the digest in the signature to check whether the message is intact or not.
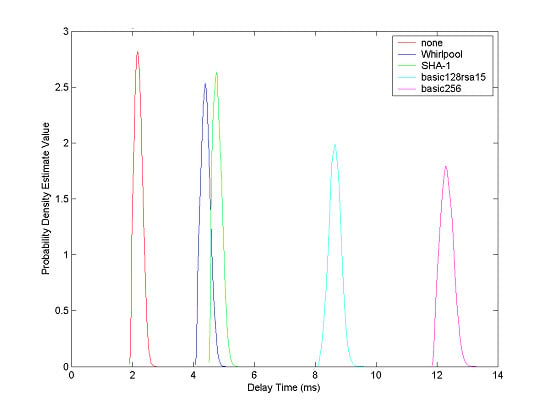
4. Experiment and Analysis
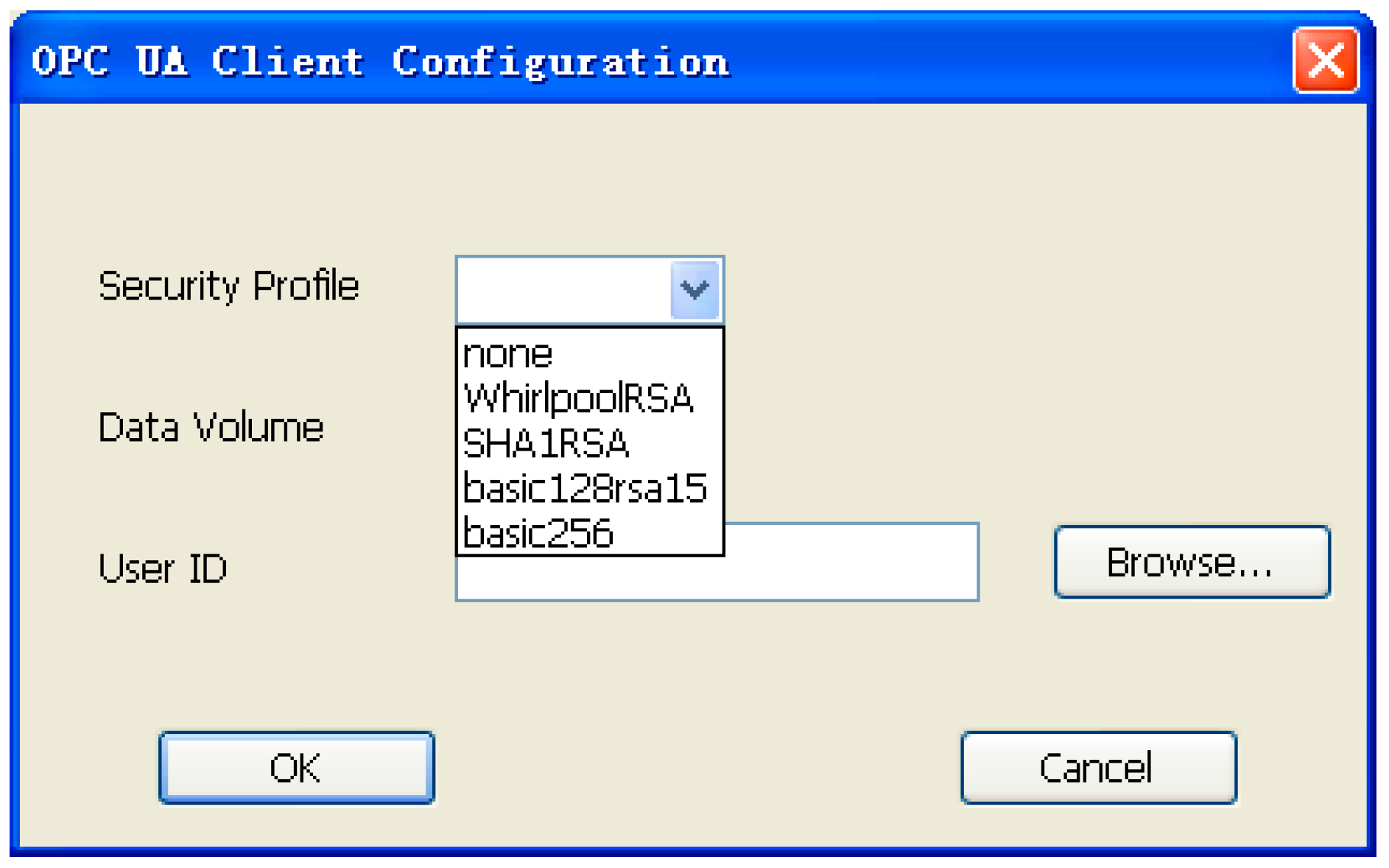
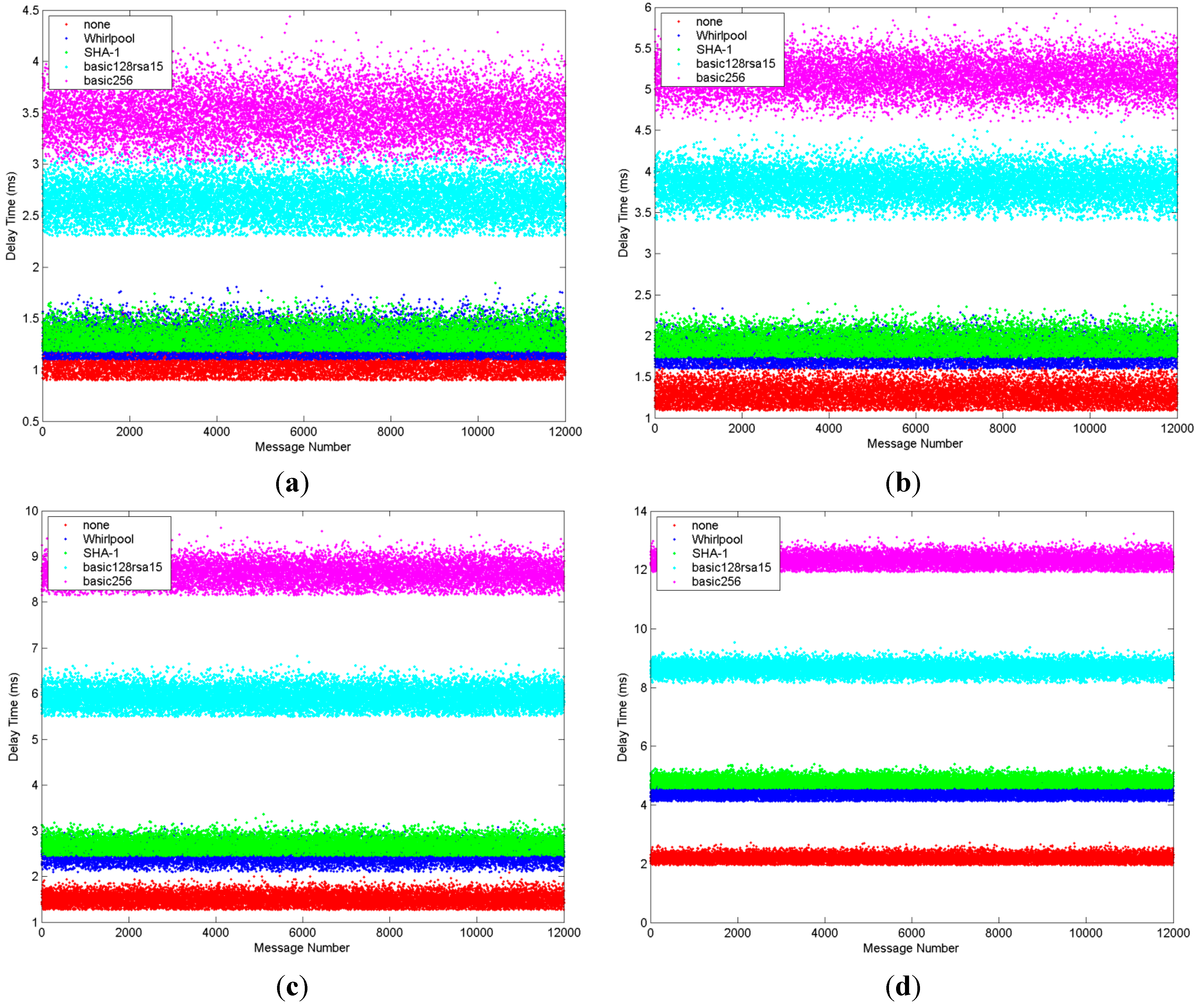
| Profile | 1024 Bytes | 4096 Bytes | 8192 Bytes | 16384 Bytes |
|---|---|---|---|---|
| none | 1.052 ms | 1.265 ms | 1.684 ms | 2.179 ms |
| WhirlpoolRSA | 1.215 ms | 1.736 ms | 2.485 ms | 4.387 ms |
| SHA1RSA | 1.268 ms | 1.859 ms | 2.659 ms | 4.753 ms |
| basic128rsa15 | 2.648 ms | 3.839 ms | 5.914 ms | 8.647 ms |
| basic256 | 3.473 ms | 5.164 ms | 8.627 ms | 12.304 ms |

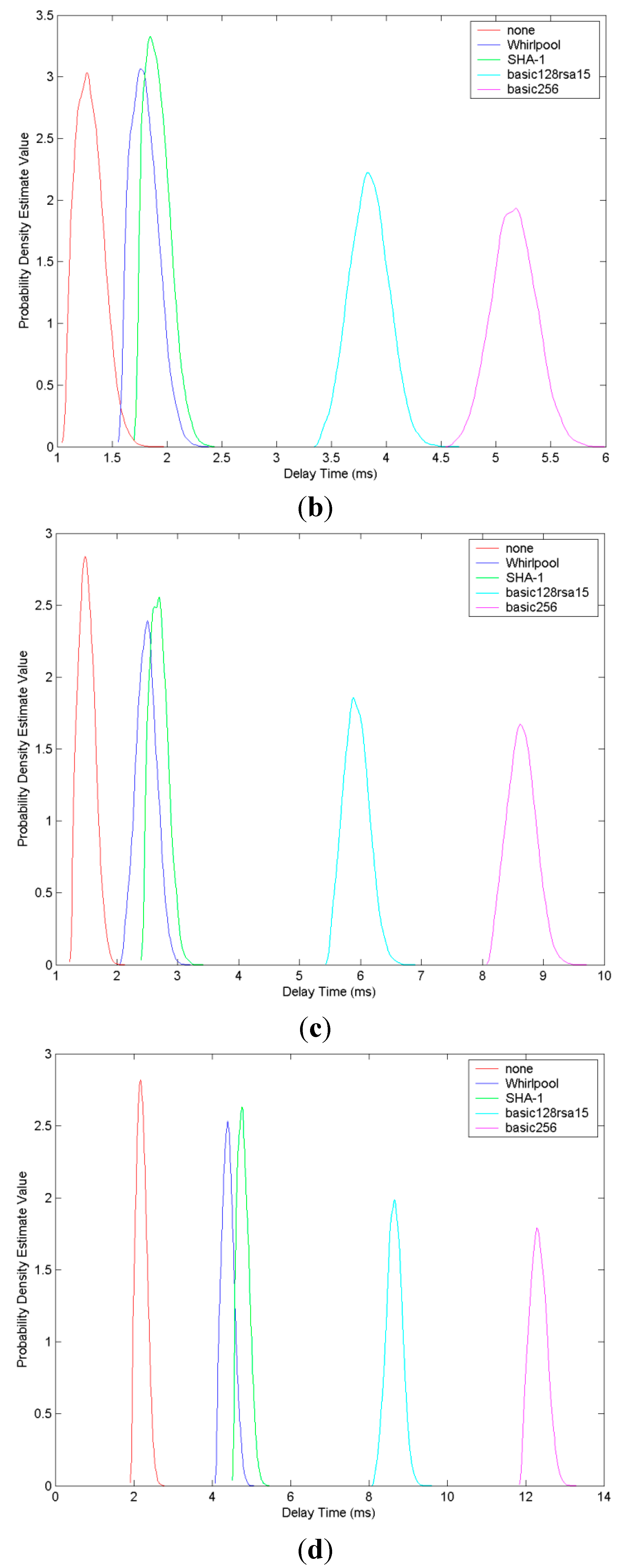
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Fernbach, A.; Granzer, W.; Kastner, W. Interoperability at the management level of building automation systems: A case study for BACnet and OPC UA. In Proceedings of the 2011 IEEE 16th Conference on Emerging Technologies & Factory Automation (ETFA), Toulouse, France, 5–9 September 2011; pp. 1–8.
- Huang, R.; Liu, F. Research on OPC UA based on electronic device description. In Proceedings of the 3rd IEEE Conference on Industrial Electronics and Applications (ICIEA 2008), Singapore, 3–5 June 2008; pp. 2162–2166.
- Van Tan, V.; Yoo, D.S.; Yi, M.J. Security in automation and control systems based on OPC techniques. In Proceedings of the International Forum on Strategic Technology (IFOST 2007), Ulaanbaatar, Mongolia, 3–6 October 2007; pp. 136–140.
- Gaitan, A.M.; Popa, V.; Gaitan, V.G.; Petrariu, A.I.; Ungurean, I. Products Authentication and Traceability using RFID Technology and OPC UA Servers. Elektron. Elektrotech. 2012, 18, 73–76. [Google Scholar] [CrossRef]
- OPC Foundation. OPC Unified Architecture Specification, Release 1.00; OPC Foundation: Scottsdale, AZ, USA, 2006. [Google Scholar]
- Chou, J.; Chen, L.; Zhang, Y.J.; Pan, L.H. OPC Unified Architecture for Industrial Demand Response. Int. J. Secur. Appl. 2012, 6, 275–280. [Google Scholar]
- Renjie, H.; Feng, L.; Dongbo, P. Research on OPC UA security. In Proceedings of the 2010 the 5th IEEE Conference on Industrial Electronics and Applications (ICIEA), Taichung, Taiwan, 15–17 June 2010; pp. 1439–1444.
- Fernbach, A.; Kastner, W. Certificate management in OPC UA applications: An evaluation of different trust models. In Proceedings of the 2012 IEEE 17th Conference on Emerging Technologies & Factory Automation (ETFA), Krakow, Poland, 17–21 September 2012; pp. 1–6.
- Schwarz, M.H.; Borcsok, J. A survey on OPC and OPC-UA: About the standard, developments and investigations. In Proceedings of the 2013 XXIV International Symposium on Information, Communication and Automation Technologies (ICAT), Sarajevo, Bosnia and Herzegovina, 30 October–1 November 2013; pp. 1–6.
- Cavalieri, S. Evaluating Overheads Introduced by OPC UA Specifications. In Human–Computer Systems Interaction: Backgrounds and Applications 2; Zdzisław, S.H., Juliusz, L.K., Teresa, M., Eds.; Springer Berlin Heidelberg: Heidelberg, Germany, 2012; pp. 201–221. [Google Scholar]
- Braune, A.; Hennig, S.; Hegler, S. Evaluation of OPC UA secure communication in web browser applications. In Proceedings of the 6th IEEE International Conference on Industrial Informatics (INDIN 2008), Daejeon, Korea, 13–16 July 2008; pp. 1660–1665.
- Cavalieri, S.; Cutuli, G.; Monteleone, S. Evaluating impact of security on OPC UA performance. In Proceedings of the 2010 3rd Conference on Human System Interactions (HSI), Rzeszow, Poland, 13–15 May 2010; pp. 687–694.
- Post, O.; Seppälä, J.; Koivisto, H. Certificate based security at device level of automation system. In Proceedings of the Preprints of 4th IFAC Wokshop on Discrete-Event System Design, Gandia Beach, Spain, 6–8 October 2009; pp. 120–124.
- Post, O.; Seppälä, J.; Koivisto, H. The Performance of OPC-UA Security Model at Field Device Level. In Proceedings of the 6th International Conference on Informatics in Control, Automation and Robotics, Milan, Italy, 2–5 July 2009; INSTICC Press: Milan, Italy, 2009; pp. 337–341. [Google Scholar]
- Chen, G.Y.; Yin, X.; Zhang, K. Communication modeling for wide-area relay protection based on IEC 61850. Telkomnika 2012, 10, 1673–1684. [Google Scholar] [CrossRef]
- Feng, L.H.; Gui, W.H.; Yang, F. Application of Communication Optimization Strategy Based on Cascade PLC MODBUS in Fire Water System of Hydropower Station. In Proceedings of the Second International Conference on Intelligent Computation Technology and Automation, Changsha, China, 10–11 October 2009; IEEE: Changsha, China, 2009; pp. 45–48. [Google Scholar]
- Silva, R.M.; Martins, H.; Nascimento, I.; Baptista, J.M.; Ribeiro, A.L.; Santos, J.L.; Jorge, P.; Frazão, O. Optical Current Sensors for High Power Systems: A Review. Appl. Sci. 2012, 2, 602–628. [Google Scholar] [CrossRef]
- Rosyadi, M.; Muyeen, S.M.; Takahashi, R.; Tamura, J. A Design Fuzzy Logic Controller for a Permanent Magnet Wind Generator to Enhance the Dynamic Stability of Wind Farms. Appl. Sci. 2012, 2, 780–800. [Google Scholar] [CrossRef]
- Sjolte, J.; Tjensvoll, G.; Molinas, M. Power Collection from Wave Energy Farms. Appl. Sci. 2013, 3, 420–436. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, B.; G, Z.; Bo, Z. Influences of the time delay on the control effect of under-frequency load shedding in power systems. In Proceedings of the 2015 27th Chinese Control and Decision Conference (CCDC), Qingdao, China, 23–25 May 2015; IEEE: Qingdao, China, 2015; pp. 5182–5186. [Google Scholar]
- Wang, X.; Yin, Y.L.; Yu, H. Finding collisions in the full SHA-1. In Proceedings of the 25th Annual International Cryptology Conference (CRYPTO 2005), Santa Barbara, CA, USA, 14–18 August 2005; Springer Verlag: Santa Barbara, CA, USA, 2005; pp. 17–36. [Google Scholar]
- Stallings, W. The Whirlpool secure hash function. Cryptologia 2006, 30, 55–67. [Google Scholar] [CrossRef]
- Barreto, P.; Rijmen, V. The Whirlpool Hashing Function; First open NESSIE Workshop: Leuven, Belgium, 2000; pp. 1–20. [Google Scholar]
- Hartikainen, A.; Toivanen, T.; Kiljunen, H. Whirlpool Hashing Function; Lappeenranta University of Technology: Lappeenranta, Finland, 2006; Volume 26, pp. 1–19. Available online: http://www2.it.lut.fi/kurssit/05-06/Ti5318800/assign/Whirlpool.pdf (accessed on 8 September 2014).
- Alho, T.; Hämäläinen, P.; Hännikäinen, M.; Hamalainen, T.D. Compact hardware design of Whirlpool hashing core. In Proceedings of the conference on Design, Automation and Test in Europe, Nice Acropolis, France, 16–20 April 2007; Institute of Electrical and Electronics Engineers Inc.: Nice Acropolis, France, 2007; pp. 1247–1252. [Google Scholar]
- Krawczyk, K.; Tomaszewicz, P.; Rawski, M. SoPC Implementation of Whirlpool Hash Function. In Proceedings of the 2011 21st International Conference on Systems Engineering (ICSEng), Las Vegas, NV, USA, 16–18 August 2011; IEEE Computer Society: Las Vegas, NV, USA, 2011; pp. 461–462. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, K.; Li, Y.; Chen, L.; Wang, Z. Research of Integrity and Authentication in OPC UA Communication Using Whirlpool Hash Function. Appl. Sci. 2015, 5, 446-458. https://doi.org/10.3390/app5030446
Wu K, Li Y, Chen L, Wang Z. Research of Integrity and Authentication in OPC UA Communication Using Whirlpool Hash Function. Applied Sciences. 2015; 5(3):446-458. https://doi.org/10.3390/app5030446
Chicago/Turabian StyleWu, Kehe, Yi Li, Long Chen, and Zhuxiao Wang. 2015. "Research of Integrity and Authentication in OPC UA Communication Using Whirlpool Hash Function" Applied Sciences 5, no. 3: 446-458. https://doi.org/10.3390/app5030446
APA StyleWu, K., Li, Y., Chen, L., & Wang, Z. (2015). Research of Integrity and Authentication in OPC UA Communication Using Whirlpool Hash Function. Applied Sciences, 5(3), 446-458. https://doi.org/10.3390/app5030446