Anomaly Detection Method Considering PLC Control Logic Structure for ICS Cyber Threat Detection
Abstract
1. Introduction
- Propose an embedding method optimized for PLC control logic by embedding PLC IL code while preserving the structure and context of the control logic;
- Develop a control logic-based anomaly detection model to identify anomalous patterns within PLC control logic;
- Conduct experiments using 30 normal control logic samples and 30 malicious control logic samples, demonstrating that the proposed control logic anomaly detection method achieved an F1 score of 81% in detecting anomalous control logic code.
2. Background and Related Works
2.1. Background
2.2. Related Works
3. Proposal for PLC Control Logic Embedding and Anomaly Detection
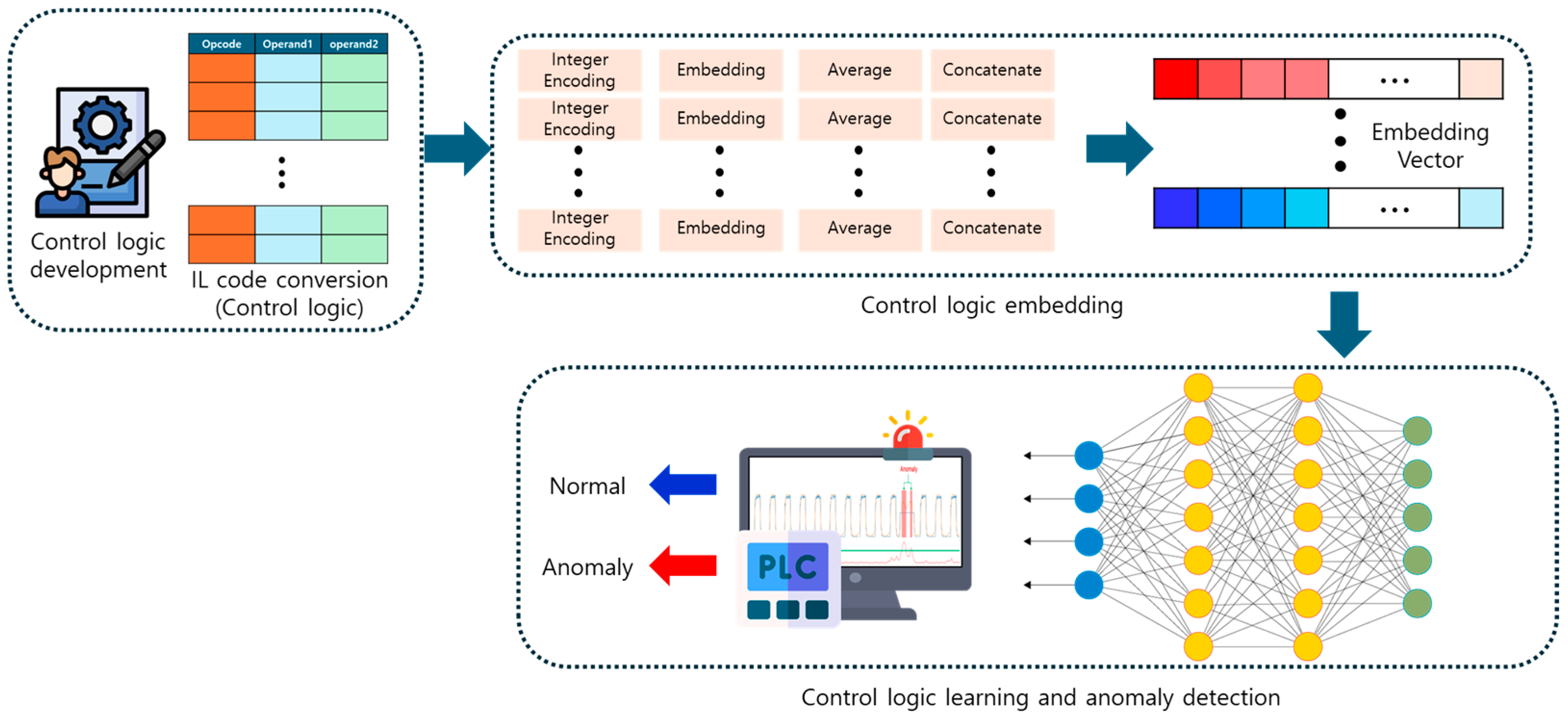
3.1. Overview
- Control Logic IL Code Conversion: Before being deployed to the PLC, normal control logic is converted into IL code. The anomaly detection model is trained using this IL code;
- Control Logic Embedding: The IL code is separated into opcodes and operands, which are then embedded using different integer encoding and embedding models. If an opcode has multiple operands, the average of the embedded operand values is used. The opcode and operand are then combined to preserve the original IL code structure;
- Control Logic Anomaly Detection: The embedded control logic is fed into a deep learning model for training. The model learns normal control logic and predicts expected normal behavior. If the difference between the predicted control logic and the input control logic exceeds a predefined threshold, it is detected as an anomaly.
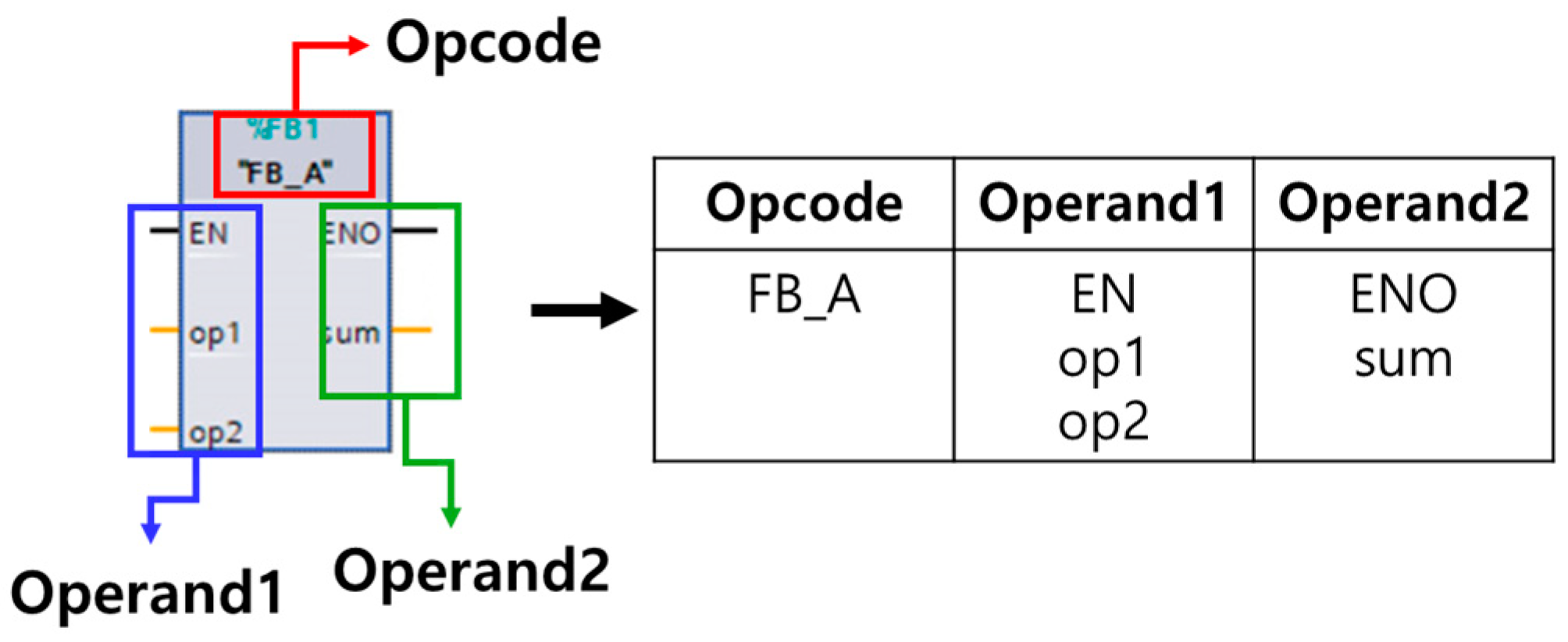
3.2. Control Logic IL Code Conversion
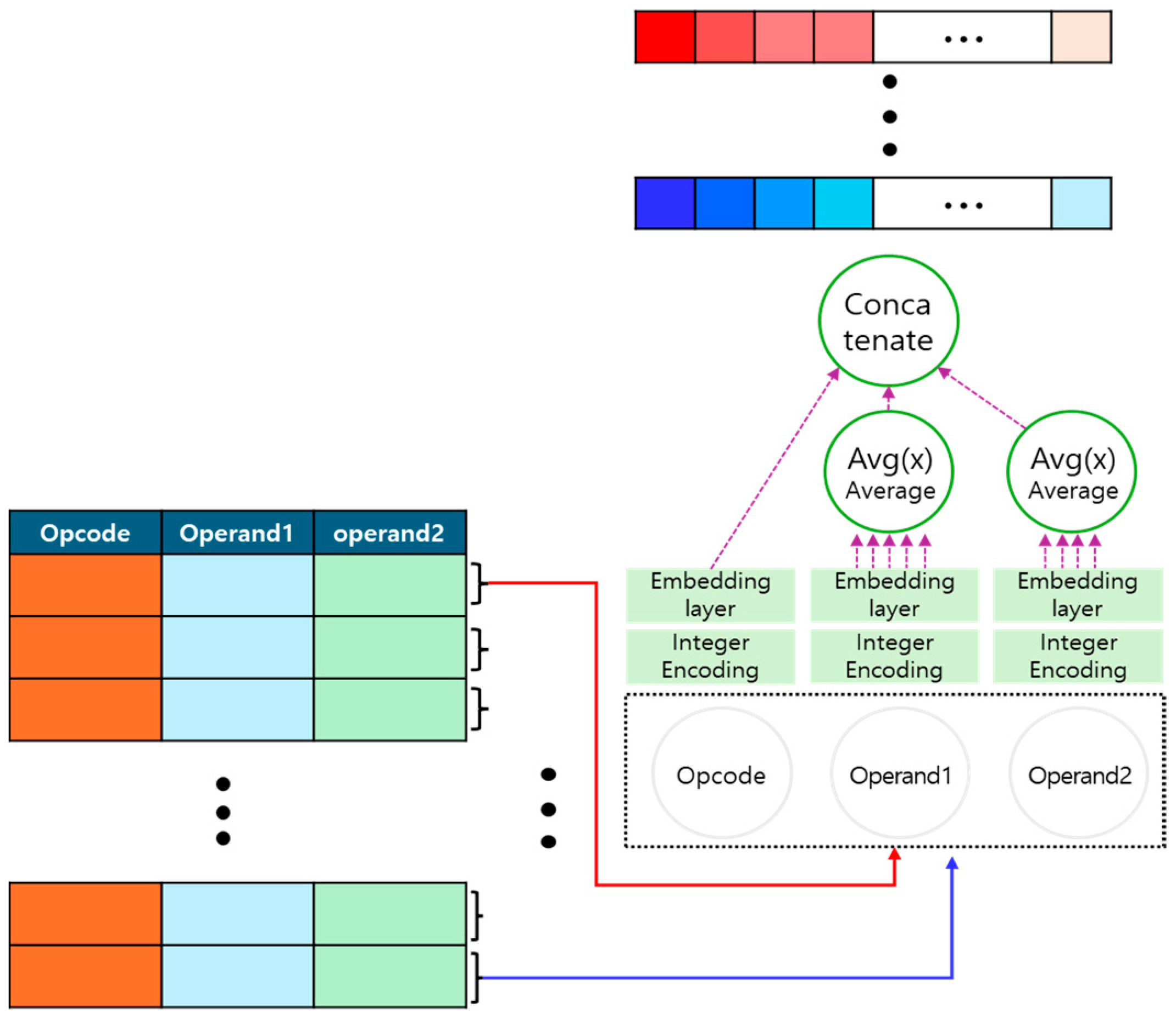
3.3. Control Logic Embedding
| Algorithm 1: Control logic embedding |
| Input: Control logic IL Code ; Output: Control logic Vector ; Start: Operand; ; ; ; ; ; ; end |
- The IL code is divided into opcode and operands.
- Since the embedding layer cannot process text directly, opcode and operands are separately converted into integers using distinct integer encoding methods.
- The integer-encoded opcode and operands are embedded using their respective embedding layers. At this stage, the embedding dimension is set, and each opcode and operand are transformed into a vector representation.
- If an opcode has multiple operands, the average of the operand embeddings is calculated and used as the final embedding representation.
- The embedded opcode and operand are combined while preserving the original IL code structure.
3.4. Control Logic Learning and Anomaly Detection
4. Experiment and Evaluation
- How does the embedding process preserve the structure and context of control logic?
- How does the proposed method detect cyber threats that existing ICS anomaly detection systems fail to identify?
- What makes the proposed method more effective than existing PLC control logic tampering detection studies?
4.1. Dataset Description
4.2. Experiment Settings
4.3. Ablation Study of Proposal Methods
5. Comparative Study
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ICS | Industrial Control System |
| AI | Artificial Intelligence |
| PLC | Programmable Logic Controller |
| EWS | Engineering Workstation |
| USB | Universal Serial Bus |
| LD | Ladder Diagram |
| IL | Instruction List |
| ST | Structured Text |
| FBD | Function Block Diagram |
| SFC | Sequential Function Chart |
| I&C | Instrumentation and Control Systems |
| CPLCD | Control Program Logic Change Detector |
| LLB | Ladder Logic Bombs |
| TPs | True Positives |
| TNs | True Negatives |
| FPs | False Positives |
| FNs | False Negatives |
| FNR | False Negative Rate |
| FPR | False Positive Rate |
| LSTM | Long Short-Term Memory |
| RNN | Recurrent Neural Network |
| GRU | Gated Recurrent Unit |
References
- Koay, A.M.; Ko, R.K.L.; Hettema, H.; Radke, K. Machine learning in industrial control system (ICS) security: Current landscape, opportunities and challenges. J. Intell. Inf. Syst. 2023, 60, 377–405. [Google Scholar] [CrossRef]
- Luo, Y.; Xiao, Y.; Cheng, L.; Peng, G.; Yao, D. Deep learning-based anomaly detection in cyber-physical systems: Progress and opportunities. ACM Comput. Surv. CSUR 2021, 54, 1–36. [Google Scholar] [CrossRef]
- Jiang, J.-R.; Chen, Y.-T. Industrial control system anomaly detection and classification based on network traffic. IEEE Access 2022, 10, 41874–41888. [Google Scholar] [CrossRef]
- Mokhtari, S.; Abbaspour, A.; Yen, K.K.; Sargolzaei, A. A machine learning approach for anomaly detection in industrial control systems based on measurement data. Electronics 2021, 10, 407. [Google Scholar] [CrossRef]
- Hudedmani, M.G.; Umayal, R.; Kabberalli, S.K.; Hittalamani, R. Programmable logic controller (PLC) in automation. Adv. J. Grad. Res. 2017, 2, 37–45. [Google Scholar] [CrossRef]
- Baezner, M.; Robin, P. Stuxnet; ETH Zurich: Zürich, Switzerland, 2017. [Google Scholar]
- Choia, M.K.; Yeunb, C.Y.; Seonga, P.H. Development of a Monitoring System for Data integrity of PLC code using blockchain technologies. In Proceedings of the Transactions of the Korean Nuclear Society Spring Meeting, Jeju, Republic of Korea, 23–24 May 2019. [Google Scholar]
- Yang, K.; Wang, H.; Sun, L. An effective intrusion-resilient mechanism for programmable logic controllers against data tampering attacks. Comput. Ind. 2022, 138, 103613. [Google Scholar] [CrossRef]
- Shedge, S.; Tade, S. Design of instruction list processor for industrial applications. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–3. [Google Scholar]
- Alphonsus, E.R.; Abdullah, M.O. A review on the applications of programmable logic controllers (PLCs). Renew. Sustain. Energy Rev. 2016, 60, 1185–1205. [Google Scholar] [CrossRef]
- Alsabbagh, W.; Langendörfer, P. A flashback on control logic injection attacks against programmable logic controllers. Automation 2022, 3, 596–621. [Google Scholar] [CrossRef]
- Tiegelkamp, M.; John, K.-H. IEC 61131-3: Programming Industrial Automation Systems; Springer: Berlin/Heidelberg, Germany, 2010; Volume 166. [Google Scholar]
- Lee, J.; Choi, H.; Shin, J.; Seo, J.T. Detection and analysis technique for manipulation attacks on plc control logic. In Proceedings of the 2020 ACM International Conference on Intelligent Computing and Its Emerging Applications, GangWon, Republic of Korea, 12–15 December 2020; pp. 1–6. [Google Scholar]
- Yau, K.; Chow, K.-P. PLC forensics based on control program logic change detection. J. Digit. Forensics Secur. Law 2015, 10, 5. [Google Scholar]
- Xiao, Y.-j.; Xu, W.-y.; Jia, Z.-h.; Ma, Z.-r.; Qi, D.-l. NIPAD: A non-invasive power-based anomaly detection scheme for programmable logic controllers. Front. Inf. Technol. Electron. Eng. 2017, 18, 519–534. [Google Scholar]
- Ghosh, A.; Qin, S.; Lee, J.; Wang, G.-N. FBMTP: An automated fault and behavioral anomaly detection and isolation tool for PLC-controlled manufacturing systems. IEEE Trans. Syst. Man Cybern. Syst. 2016, 47, 3397–3417. [Google Scholar] [CrossRef]
- Han, S.; Lee, K.; Cho, S.; Park, M. Anomaly detection based on temporal behavior monitoring in programmable logic controllers. Electronics 2021, 10, 1218. [Google Scholar] [CrossRef]
- Chan, C.F. Enhancing PLC Logging and Abnormality Detection Through Machine Learning and Process Mining. Ph.D. Thesis, The University of Hong Kong, Hong Kong, China, 2024. [Google Scholar]
- Ayub, A. Stealthy Control Logic Attacks and Defense in Industrial Control Systems. Ph.D. Thesis, Virginia Commonwealth University, Richmond, VA, USA, 2024. [Google Scholar]
- Ding, S.H.; Fung, B.C.; Charland, P. Asm2vec: Boosting static representation robustness for binary clone search against code obfuscation and compiler optimization. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 472–489. [Google Scholar]
- Iacobelli, A.; Rinieri, L.; Melis, A.; Al Sadi, A.; Prandini, M.; Callegati, F. Detection of Ladder Logic Bombs in PLC Control Programs: An Architecture based on Formal Verification. In Proceedings of the 2024 IEEE 7th International Conference on Industrial Cyber-Physical Systems (ICPS), St. Louis, MO, USA, 12–15 May 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–7. [Google Scholar]
- Alves, T.R.; Buratto, M.; De Souza, F.M.; Rodrigues, T.V. OpenPLC: An open source alternative to automation. In Proceedings of the IEEE Global Humanitarian Technology Conference (GHTC 2014), San Jose, CA, USA, 10–13 October 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 585–589. [Google Scholar]
- Hossin, M.; Sulaiman, M.N. A review on evaluation metrics for data classification evaluations. Int. J. Data Min. Knowl. Manag. Process 2015, 5, 1. [Google Scholar]
- Dalvi, S.; Gressel, G.; Achuthan, K. Tuning the false positive rate/false negative rate with phishing detection models. Int. J. Eng. Adv. Technol. 2019, 9, 7–13. [Google Scholar] [CrossRef]
- Lindemann, B.; Maschler, B.; Sahlab, N.; Weyrich, M. A survey on anomaly detection for technical systems using LSTM networks. Comput. Ind. 2021, 131, 103498. [Google Scholar] [CrossRef]
- Nguyen, H.D.; Tran, K.P.; Thomassey, S.; Hamad, M. Forecasting and Anomaly Detection approaches using LSTM and LSTM Autoencoder techniques with the applications in supply chain management. Int. J. Inf. Manag. 2021, 57, 102282. [Google Scholar] [CrossRef]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention is all you need. In Advances in Neural Information Processing Systems 30; NeurIPS: Long Beach, CA, USA, 2017. [Google Scholar]
- Sherstinsky, A. Fundamentals of recurrent neural network (RNN) and long short-term memory (LSTM) network. Phys. D Nonlinear Phenom. 2020, 404, 132306. [Google Scholar] [CrossRef]
- Dey, R.; Salem, F.M. Gate-variants of gated recurrent unit (GRU) neural networks. In Proceedings of the 2017 IEEE 60th International Midwest Symposium on Circuits and Systems (MWSCAS), Boston, MA, USA, 6–9 August 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1597–1600. [Google Scholar]
- Agarap, A.F. Deep learning using rectified linear units (relu). arXiv 2018, arXiv:1803.08375. [Google Scholar]
- Chen, Y.; Zhang, S.; Zhang, W.; Peng, J.; Cai, Y. Multifactor spatio-temporal correlation model based on a combination of convolutional neural network and long short-term memory neural network for wind speed forecasting. Energy Convers. Manag. 2019, 185, 783–799. [Google Scholar] [CrossRef]
- Gulli, A.; Pal, S. Deep Learning with Keras; Packt Publishing Ltd.: Birmingham, UK, 2017. [Google Scholar]
- Perera, P.; Oza, P.; Patel, V.M. One-class classification: A survey. arXiv 2021, arXiv:2101.03064. [Google Scholar]
- Ahsan, M.M.; Mahmud, M.P.; Saha, P.K.; Gupta, K.D.; Siddique, Z. Effect of data scaling methods on machine learning algorithms and model performance. Technologies 2021, 9, 52. [Google Scholar] [CrossRef]
- Waqas, M.; Humphries, U.W. A critical review of RNN and LSTM variants in hydrological time series predictions. MethodsX 2024, 13, 102946. [Google Scholar] [PubMed]
- Zheng, Y.; Pujar, S.; Lewis, B.; Buratti, L.; Epstein, E.; Yang, B.; Laredo, J.; Morari, A.; Su, Z. D2a: A dataset built for ai-based vulnerability detection methods using differential analysis. In Proceedings of the 2021 IEEE/ACM 43rd International Conference on Software Engineering: Software Engineering in Practice (ICSE-SEIP), Madrid, Spain, 25–28 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 111–120. [Google Scholar]

| Types of Programming Languages | Description |
|---|---|
| Ladder Diagram (LD) | A programming language written using ladder diagram symbols |
| Instruction List (IL) | Programming using one operator and one or more operands (like assembly language) |
| Structured Text (ST) | High-level programming languages like Basic, PASCAL, and C |
| Function Block Diagram (FBD) | Programming language using block diagrams |
| Sequential Function Chart (SFC) | A programming language like the format of a sequence diagram. |
| Scaler | Batch Sizes | Node | F1 Score |
|---|---|---|---|
| Robust | 8 | 64 | 0.7610 |
| 128 | 0.8129 | ||
| 256 | 0.7610 | ||
| 512 | 0.7780 | ||
| 16 | 64 | 0.7383 | |
| 128 | 0.7606 | ||
| 256 | 0.7763 | ||
| 512 | 0.7520 | ||
| 32 | 64 | 0.6958 | |
| 128 | 0.7587 | ||
| 256 | 0.7547 | ||
| 512 | 0.7437 |
| Scaler | Batch Sizes | Node | F1 Score |
|---|---|---|---|
| Robust | 8 | 64 | 0.7782 |
| 128 | 0.7712 | ||
| 256 | 0.7685 | ||
| 512 | 0.7828 | ||
| 16 | 64 | 0.7393 | |
| 128 | 0.7756 | ||
| 256 | 0.7834 | ||
| 512 | 0.7690 | ||
| 32 | 64 | 0.7355 | |
| 128 | 0.7598 | ||
| 256 | 0.7847 | ||
| 512 | 0.8160 |
| Scaler | Batch Sizes | Layers | Vector Dimension | F1 Score |
|---|---|---|---|---|
| Standard | 8 | 2 | 64 | 0.7657 |
| 128 | 0.6987 | |||
| 256 | 0.7458 | |||
| 512 | 0.8117 | |||
| 4 | 64 | 0.7795 | ||
| 128 | 0.7232 | |||
| 256 | 0.7558 | |||
| 512 | 0.6878 | |||
| 6 | 64 | 0.7467 | ||
| 128 | 0.7370 | |||
| 256 | 0.6878 | |||
| 512 | 0.6974 | |||
| 16 | 2 | 64 | 0.7493 | |
| 128 | 0.7612 | |||
| 256 | 0.6341 | |||
| 512 | 0.6761 | |||
| 4 | 64 | 0.7333 | ||
| 128 | 0.6882 | |||
| 256 | 0.7031 | |||
| 512 | 0.7285 | |||
| 6 | 64 | 0.7232 | ||
| 128 | 0.7489 | |||
| 256 | 0.7651 | |||
| 512 | 0.7146 | |||
| 32 | 2 | 64 | 0.7766 | |
| 128 | 0.6653 | |||
| 256 | 0.6687 | |||
| 512 | 0.7334 | |||
| 4 | 64 | 0.7034 | ||
| 128 | 0.7312 | |||
| 256 | 0.7431 | |||
| 512 | 0.7213 | |||
| 6 | 64 | 0.7013 | ||
| 128 | 0.7305 | |||
| 256 | 0.7558 | |||
| 512 | 0.7099 |
| Model | Accuracy | FNR | FPR | Precision | Recall | F1-Score |
|---|---|---|---|---|---|---|
| RNN | 0.704762 | 0.199675 | 0.386646 | 0.66442 | 0.800325 | 0.726068 |
| GRU | 0.755556 | 0.232143 | 0.256211 | 0.741379 | 0.767857 | 0.754386 |
| LSTM | 0.811905 | 0.121160 | 0.133869 | 0.756241 | 0.87884 | 0.812944 |
| LSTM-Autoencoder | 0.810317 | 0.139609 | 0.100148 | 0.775988 | 0.86039 | 0.816012 |
| Transformer | 0.810317 | 0.121160 | 0.137046 | 0.754026 | 0.87884 | 0.811663 |
| Model | F1 Score | |
|---|---|---|
| Proposed Embedding Methods | General Embedding Methods | |
| LSTM | 0.812944 | 0.74079 |
| LSTM-Autoencoder | 0.816012 | 0.756549 |
| Transformer | 0.811663 | 0.723404 |
| Reference | Detection Objective | Detection Method | Additional Storage Requirement | Tampering Detection Capability | Anomaly Detection Capability |
|---|---|---|---|---|---|
| Choia, M.K. [7] | Tampering verification | Blockchain (hash value comparison) | O | O | X |
| Yang, K. [8] | Tampering verification | Message digest | X | O | X |
| Lee, J.C. [13] | Tampering verification | Comparison with normal control logic code | O | O | X |
| Yau, Ken [14] | Tampering verification | Review of modifications to rung | X | O | X |
| Our | Anomaly detection | AI-based anomaly detection | X | △ (Detection if tampering causes anomalies) | O |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.H.; Ji, I.H.; Jeon, S.H.; Seo, J.T. Anomaly Detection Method Considering PLC Control Logic Structure for ICS Cyber Threat Detection. Appl. Sci. 2025, 15, 3507. https://doi.org/10.3390/app15073507
Lee JH, Ji IH, Jeon SH, Seo JT. Anomaly Detection Method Considering PLC Control Logic Structure for ICS Cyber Threat Detection. Applied Sciences. 2025; 15(7):3507. https://doi.org/10.3390/app15073507
Chicago/Turabian StyleLee, Ju Hyeon, Il Hwan Ji, Seung Ho Jeon, and Jung Taek Seo. 2025. "Anomaly Detection Method Considering PLC Control Logic Structure for ICS Cyber Threat Detection" Applied Sciences 15, no. 7: 3507. https://doi.org/10.3390/app15073507
APA StyleLee, J. H., Ji, I. H., Jeon, S. H., & Seo, J. T. (2025). Anomaly Detection Method Considering PLC Control Logic Structure for ICS Cyber Threat Detection. Applied Sciences, 15(7), 3507. https://doi.org/10.3390/app15073507






