A Tolerance-Degree-Based Sensitive Area Division Method for Improving Location Privacy Protection of Smart Terminal
Abstract
1. Introduction
- To enhance the local stability of location encoding, a spatial index strategy is designed based on Hilbert curves and Geohash.
- A tolerance-degree-based sensitive area radius design method is proposed for reasonably adjusting the privacy budget of smart terminal, and the privacy budget is calculated according to the divided sensitive area.
- To improve the similarity and statistical usability of the encoding, a distribution-aware random response method is designed, which implements a random response mechanism using allocated budgets.
- The effectiveness of the proposed method is verified by experiments based on the real-world dataset.
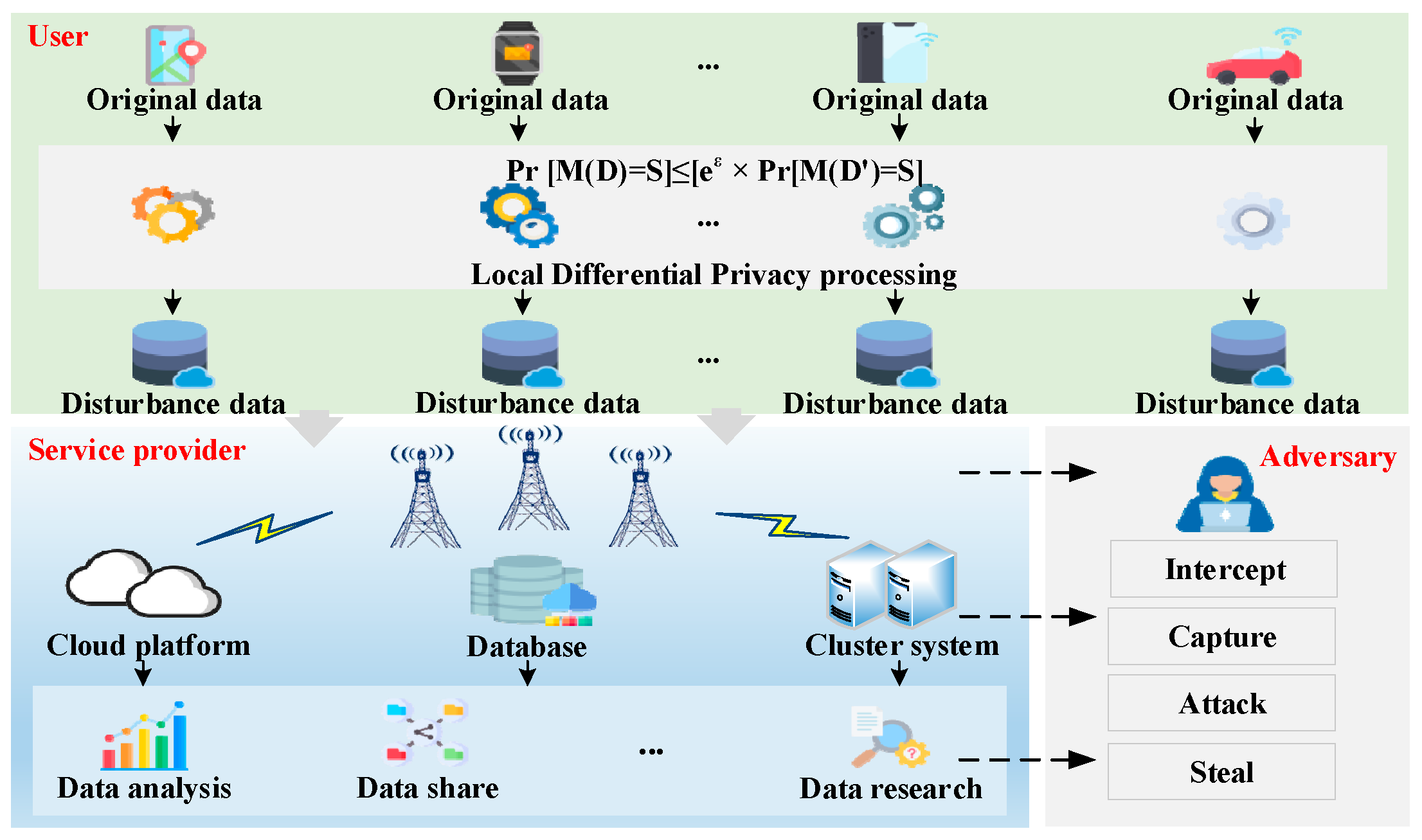
2. Location Privacy Protection of Smart Terminal
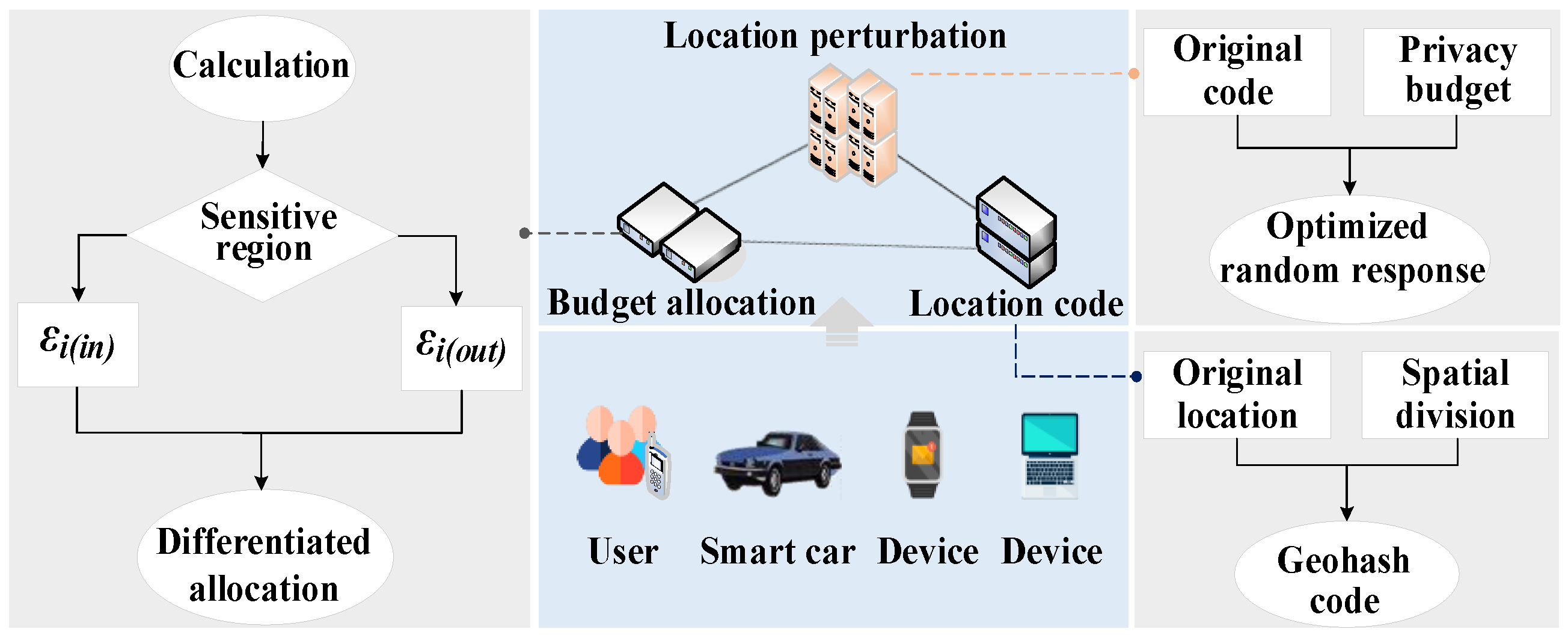
3. A Tolerance-Degree-Based Sensitive Area Division Method
3.1. Proposed Tolerance-Degree-Based Sensitive Area Division Method
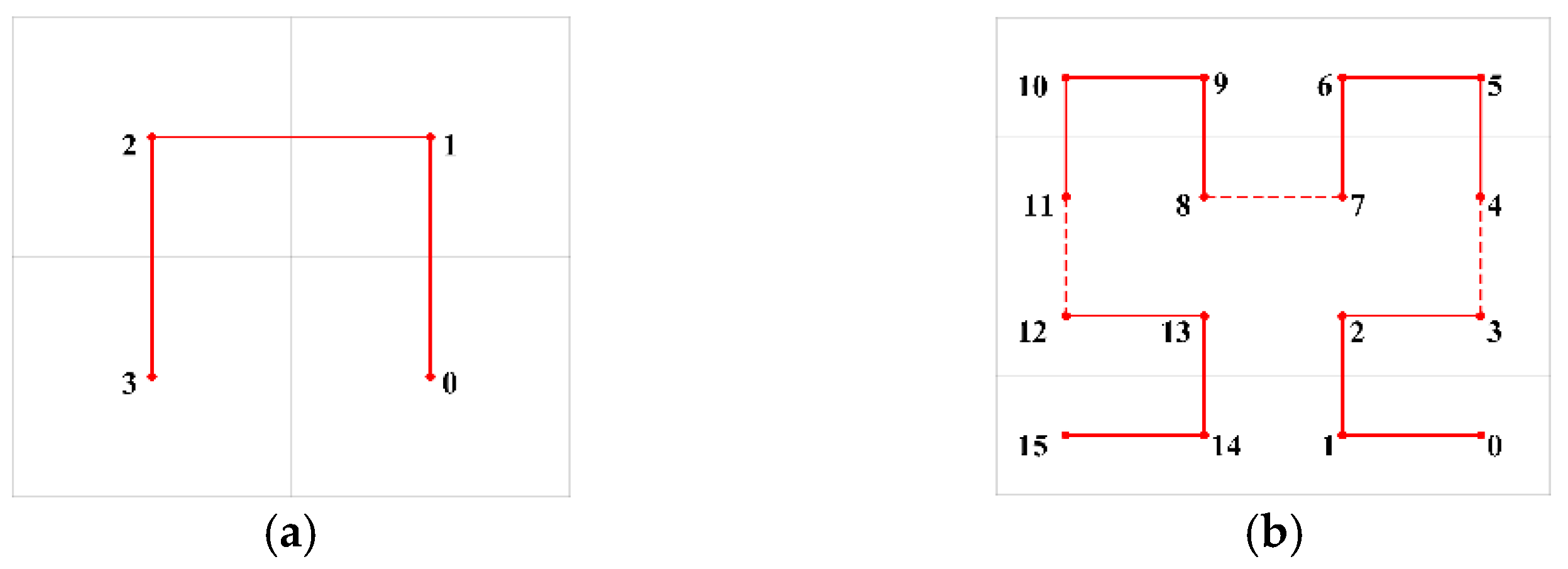
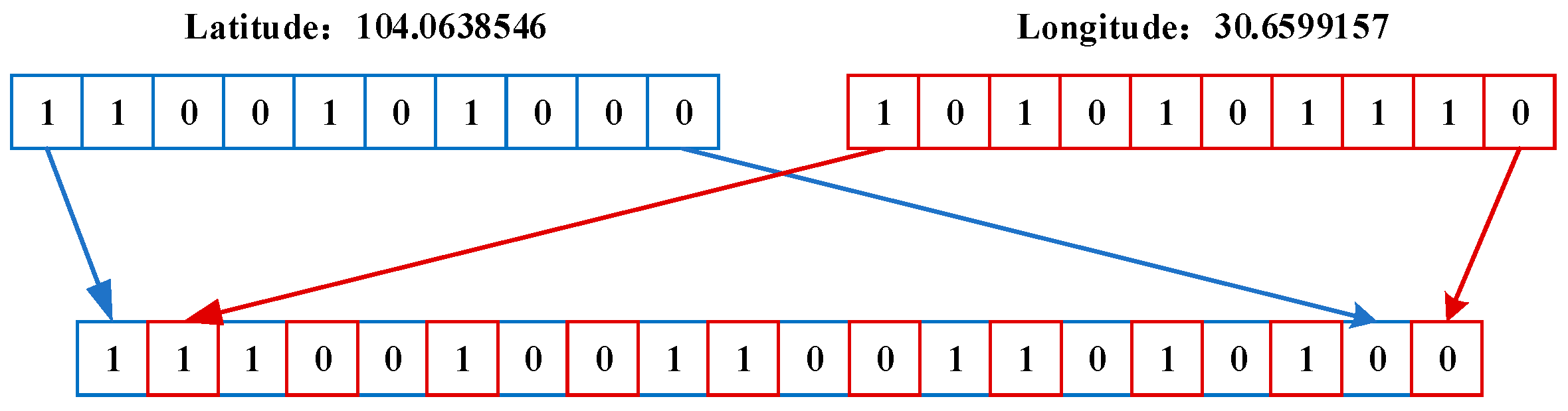
3.2. Location Encoding Based on Hilbert Space Filling
3.3. Budget Allocation
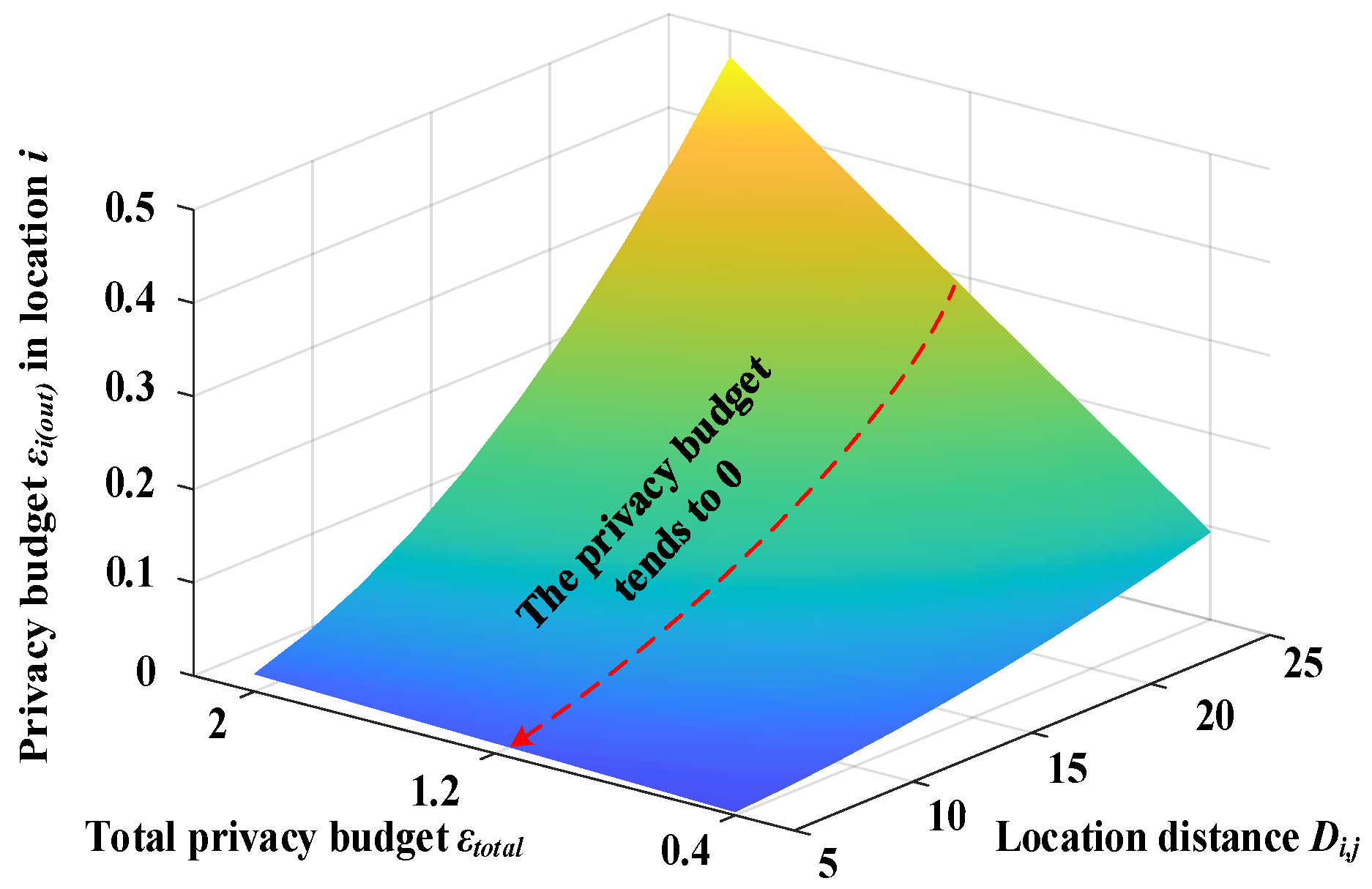
3.3.1. Privacy Allocation Outside Sensitive Areas
3.3.2. Privacy Allocation in Sensitive Areas
3.4. Perturbation Mechanism Based on Random Response
- When , the optimal solution for the mathematical expectation in Equation (3) is point A with P00 = 0 and P11 = 1, the perturbation matrix can be designed as .
- When , the optimal solution is point B. The optimal value of the mathematical expectation is , so the perturbation matrix can be designed as .
- When , the optimal solution is point C, with P00 = 1 and P11 = 0, so the perturbation matrix can be designed as .
4. Privacy Protection Security Analysis
- Parameter Inference: adversaries can infer location encoding and decoding methods based on the obtained parameters of grid partitioning and location encoding. But the information does not reveal the specific location of user, which protects the privacy.
- Request Interception: adversaries can infer the service location by intercepting location service requests. But the information obtained is the perturbed location, which does not involve privacy information. The protectiveness of response interception is similar to case 2.
- Collusive service providers: multiple providers can share and jointly analyze acquired location information. But the accessed information is the sum of several privacy perturbations. Moreover, stronger perturbation is used by TD-SAD in sensitive areas, further reducing the success rate of adversaries in re-identification.
5. Experimentation and Analysis
5.1. Experimental Data
5.2. Experimental Methods
5.3. Practical Utility in LBS Scenarios Based on TD-SAD Method
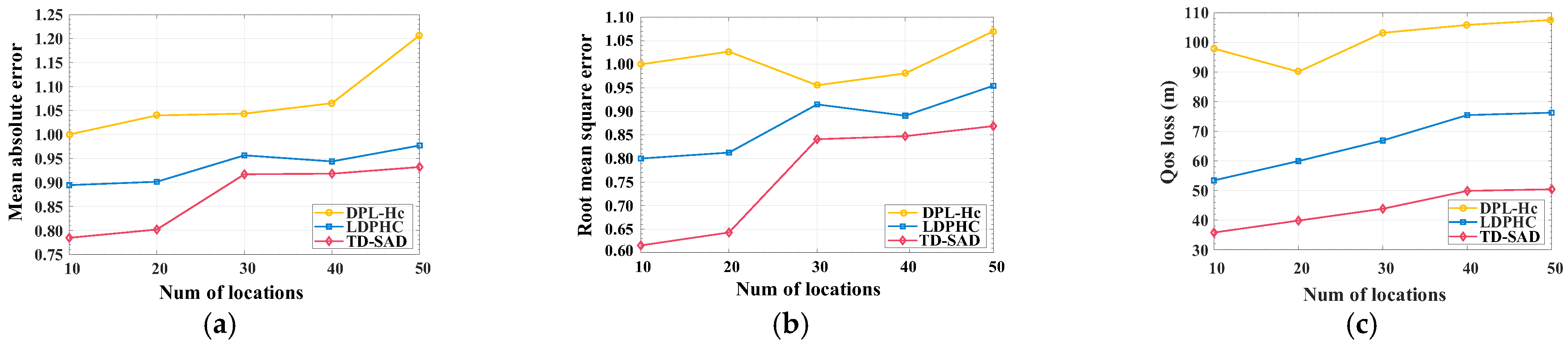
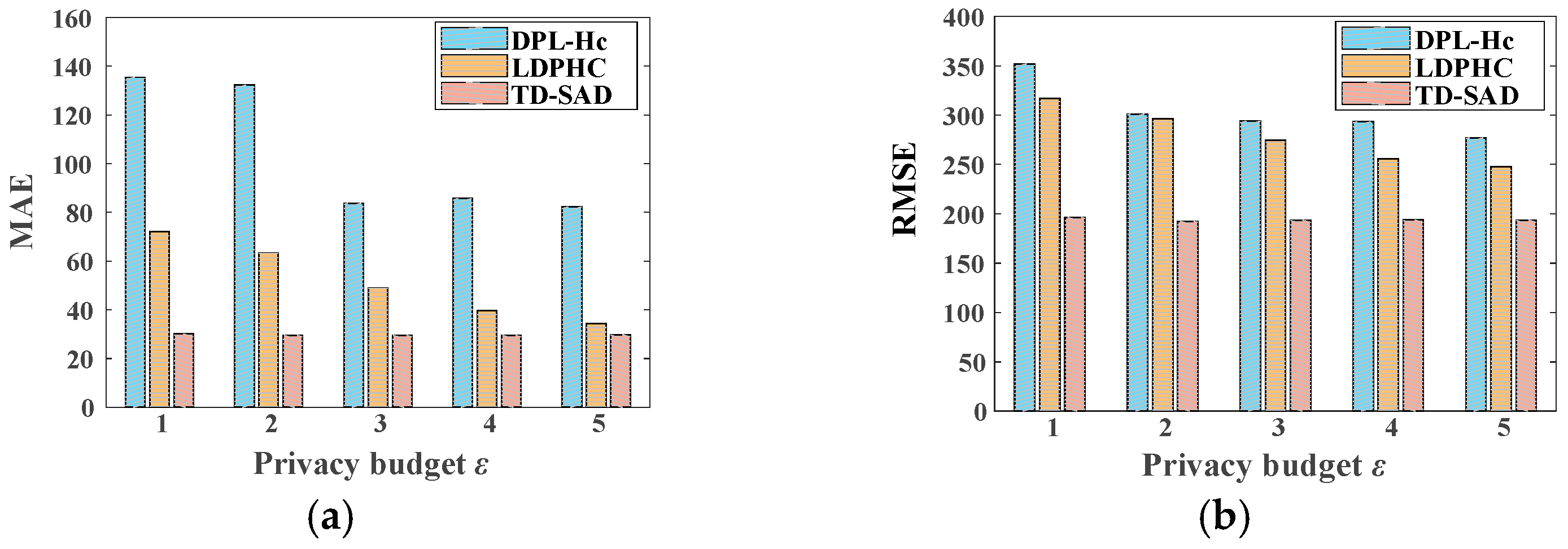
5.4. Relative Error of Range Query
5.5. Quality Loss of Proposed TD-SAD Method
5.6. Accuracy of Location Data Aggregation
5.7. Runtime of the Proposed TD-SAD Method
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lashkari, B.; Rezazadeh, J.; Farahbakhsh, R.; Sandrasegaran, K. Crowdsourcing and sensing for indoor localization in IoT: A review. IEEE Sens. J. 2019, 19, 2408–2434. [Google Scholar] [CrossRef]
- Su, Y.; Li, X.; Tang, W.; Xiang, J.; He, Y. Next Check-in Location Prediction via Footprints and Friendship on Location-Based Social Networks. In Proceedings of the 19th IEEE International Conference on Mobile Data Management (MDM), Aalborg, Denmark, 25–28 June 2018; pp. 251–256. [Google Scholar]
- Kim, J.W.; Kim, J.S.; Chung, Y.D.; Jang, B. A Survey of differential privacy-based techniques and their applicability to location-Based services. Comput. Secur. 2021, 111, 102464. [Google Scholar] [CrossRef]
- Boussada, R.; Hamdane, B.; Kamoun, F.; Saidane, L.A. Surveying and Analyzing Privacy Issues in Contact tracing apps. In Proceedings of the 10th IFIP International Conference on Performance Evaluation and Modeling in Wireless and Wired Networks (PEMWN), Waterloo, ON, Canada, 23–25 November 2021; pp. 1–5. [Google Scholar]
- Andrs, M.E.; Bordenabe, N.E.; Chatzikokolakis, K.; Palamidessi, C. Geo-indistinguishability: Differential privacy for location-based systems. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 901–914. [Google Scholar]
- Wang, W.; Wang, Y.; Duan, P.; Liu, T.; Tong, X.; Cai, Z. A Triple Real-Time Trajectory Privacy Protection Mechanism Based on Edge Computing and Blockchain in Mobile Crowdsourcing. IEEE Trans. Mob. Comput. 2023, 22, 5625–5642. [Google Scholar] [CrossRef]
- Cao, T.; Yin, R.; Zhu, L.; Xu, Z. Survey of Personalized Location Privacy Protection Technologies. Comput. Sci. 2025, 52, 307–321. [Google Scholar]
- Zhang, S.; Hu, B.; Liang, W.; Li, K.C.; Gupta, B.B. A Caching-Based Dual K-Anonymous Location Privacy-Preserving Scheme for Edge Computing. IEEE Internet Things J. 2023, 10, 9768–9781. [Google Scholar] [CrossRef]
- Hu, P.; Chu, X.; Zuo, K.; Ni, T.; Xie, D.; Shen, Z. Security-Enhanced Data Sharing Scheme with Location Privacy Preservation for Internet of Vehicles. IEEE Trans. Veh. Technol. 2024, 73, 13751–13764. [Google Scholar] [CrossRef]
- Men, H.; Cao, L.; Zheng, G.; Li, Y.; Ma, H. LBS privacy protection scheme based on sparse user environment of VANET. Appl. Res. Comput. 2024, 41, 2831–2838. [Google Scholar]
- Dwork, C. Differential privacy. In Encyclopedia of Cryptography and Security; van Tilborg, H.C.A., Jajodia, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Zhang, Q.; Zhang, X.; Wang, M.; Li, X. DPLQ: Location-based service privacy protection scheme based on differential privacy. IET Inf. Secur. 2021, 15, 442–456. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, J.; Zhang, H.; Li, L.; Pan, M.; Han, Z. Data-Driven Transportation Network Company Vehicle Scheduling With Users’ Location Differential Privacy Preservation. IEEE Trans. Mob. Comput. 2023, 22, 813–823. [Google Scholar] [CrossRef]
- Tao, Y.; Wang, T.; Qiang, Y.; Shen, L.; Chen, F.; Zhao, C. A differential privacy location protect approach with intelligence data collection paradigm for MCS. Compu. Netw. 2024, 247, 110421. [Google Scholar] [CrossRef]
- Wang, T.; Tao, Y.; Zhang, Q.; Xu, N.; Chen, F.; Zhao, C. Group Coding Location Privacy Protection Method Based on Differential Privacy in Crowdsensing. IEEE Internet Things J. 2024, 11, 28398–28408. [Google Scholar] [CrossRef]
- Wang, H.; Hong, H.; Xiong, L.; Qin, Z.; Hong, Y. L-SRR: Local differential privacy for location-based services with staircase randomized response. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 2809–2823. [Google Scholar]
- Navidan, H.; Moghtadaiee, V.; Nazaran, N.; Alishahi, M. Hide me Behind the Noise: Local Differential Privacy for Indoor Location Privacy. In Proceedings of the 2022 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 6–10 June 2022; pp. 514–523. [Google Scholar]
- Wang, J.; Wang, F.; Li, H. Differential privacy location protection scheme based on Hilbert curve. Secur. Commun. Netw. 2021, 2021, 5574415. [Google Scholar] [CrossRef]
- Primault, V.; Boutet, A.; Mokhtar, S.B.; Brunie, L. The Long Road to Computational Location Privacy: A Survey. IEEE Commun. Surv. Tuts. 2019, 21, 2772–2793. [Google Scholar] [CrossRef]
- Min, M.; Zhu, H.; Li, S.; Zhang, H.; Xiao, L.; Pan, M. Semantic Adaptive Geo-Indistinguishability for Location Privacy Protection in Mobile Networks. IEEE Trans. Veh. Technol. 2024, 73, 9193–9198. [Google Scholar] [CrossRef]
- Song, H.; Shen, H.; Zhao, N.; He, Z.; Wu, M.; Xiong, W. APLDP: Adaptive personalized local differential privacy data collection in mobile crowdsensing. Comput. Secur. 2024, 136, 103517–103531. [Google Scholar] [CrossRef]
- He, Y.; Zhang, J.; Shuai, L.; Luo, J.; Yang, X.; Sun, Q.T. A Personalized Secure Publishing Mechanism of the Sensing Location Data in Crowdsensing Location-Based Services. IEEE Sens. J. 2021, 21, 13628–13637. [Google Scholar] [CrossRef]
- Yan, Y.; Lyu, Y.; Li, F. Local Differential Privacy Location Protection for Mobile Terminals Based on Huffman Coding. J. Jisuanji Kexue Yu Tansuo 2025, 19, 802–817. [Google Scholar]
- Jiang, H.; Li, J.; Zhao, P.; Zeng, F.; Xiao, Z.; Iyengar, A. Location privacy-preserving mechanisms in location-based services: A comprehensive survey. ACM Comput. Surv. 2022, 54, 1–36. [Google Scholar] [CrossRef]
- Ye, Q.; Meng, X.; Zhu, M.; Zheng, H. Survey on local differential privacy. J. Softw. 2017, 29, 1981–2005. [Google Scholar]
- Lian, H.; Qiu, W.; Yan, D.; Guo, J.; Li, Z.; Tang, P. Privacy-preserving spatial query protocol based on the Moore curve for location-based service. Comput. Secur. 2020, 96, 101845. [Google Scholar] [CrossRef]
- Geohash Converter. 2023. Available online: https://geohash.jorren.nl/ (accessed on 28 April 2024).
- Zhao, Y.; Du, J.; Chen, J. Scenario-based Adaptations of Differential Privacy: A Technical Survey. ACM Comput. Surv. 2024, 56, 1–39. [Google Scholar] [CrossRef]
- Xu, C.; Luo, L.; Ding, Y.; Zhao, G.; Yu, S. Personalized Location Privacy Protection for Location-Based Services in Vehicular Networks. IEEE Wirel. Commun. Lett. 2020, 9, 1633–1637. [Google Scholar] [CrossRef]
- Warner, S.L. Randomized response: A survey technique for eliminating evasive answer bias. J. Am. Sta. Assoc. 2012, 60, 63–69. [Google Scholar]
- Zhou, Y.; Lu, L.; Wu, Z. Study on utility optimization for randomized response mechanism. J. Commun. 2019, 40, 74–81. [Google Scholar]
- Zhao, Y.; Chen, J. Vector-Indistinguishability: Location Dependency Based Privacy Protection for Successive Location Data. IEEE Trans. Comput. 2024, 73, 970–979. [Google Scholar] [CrossRef]
- Ju, Z.; Li, Y. V2V-ESP: Vehicle-to-Vehicle Energy Sharing Privacy Protection Scheme Based on SDP Algorithm. IEEE Trans. Netw. Sci. Eng. 2024, 11, 1093–1105. [Google Scholar] [CrossRef]
- Zhu, X.; Lin, L.; Huang, Y.; Wang, X.; Que, Y.; Jedari, B. Secure Data Transmission Based on Reinforcement Learning and Position Confusion for Internet of UAVs. IEEE Internet Things J. 2024, 11, 21010–21020. [Google Scholar] [CrossRef]
- PoI Data Sample. 2020. Available online: https://snap.stanford.edu/data/loc-gowalla.html (accessed on 14 June 2024).
- Min, M.; Xiao, L.; Ding, J.; Zhang, H.; Li, S.; Pan, M.; Han, Z. 3D geo-indistinguishability for indoor location-based services. IEEE Trans. Wirel. Commun. 2022, 21, 4682–4694. [Google Scholar] [CrossRef]
- Su, Y.; Li, X.; Liu, B.; Zha, D.; Xiang, J.; Tang, W.; Gao, N. FGCRec: Fine-Grained Geographical Characteristics Modeling for Point-of-Interest Recommendation. In Proceedings of the ICC 2020–2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]



| Symbol | Description |
|---|---|
| ε | Privacy budget |
| Pr | Perturbation probability |
| Pi,j | Conditional probability that the output data is j when the input data is i |
| ui | Proportion of element i in the total data |
| R | Sensitive area radius |
| Di,j | Distance from original location i to the nearest sensitive location j |
| L | Encoding of the original location |
| L′ | Encoding of the original position after perturbation |
| L(bj) | The bit j of the original code |
| L(bj′)′ | The bit j of the perturbation code |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, X.; Lu, Y.; Chen, J.; Li, G. A Tolerance-Degree-Based Sensitive Area Division Method for Improving Location Privacy Protection of Smart Terminal. Appl. Sci. 2025, 15, 10528. https://doi.org/10.3390/app151910528
Liu X, Lu Y, Chen J, Li G. A Tolerance-Degree-Based Sensitive Area Division Method for Improving Location Privacy Protection of Smart Terminal. Applied Sciences. 2025; 15(19):10528. https://doi.org/10.3390/app151910528
Chicago/Turabian StyleLiu, Xiao, Yingchi Lu, Jining Chen, and Gaoxiang Li. 2025. "A Tolerance-Degree-Based Sensitive Area Division Method for Improving Location Privacy Protection of Smart Terminal" Applied Sciences 15, no. 19: 10528. https://doi.org/10.3390/app151910528
APA StyleLiu, X., Lu, Y., Chen, J., & Li, G. (2025). A Tolerance-Degree-Based Sensitive Area Division Method for Improving Location Privacy Protection of Smart Terminal. Applied Sciences, 15(19), 10528. https://doi.org/10.3390/app151910528






