1. Introduction
Recently, there have been a growing number of incidents involving the deliberate damage of subsea infrastructure in the Baltic Sea. This issue primarily concerns telecommunications cables, power lines, and gas pipelines, the networks which connect the countries of Northern and Central–Eastern Europe. The damage is both physical and informational in nature, as it disrupts the transmission of data, electricity, and gas, thereby posing a threat to national security, destabilizing the economy, and undermining the integrity of critical infrastructure.
Examples of such incidents continue to occur regularly. In October 2023, the commercial vessel New Polar Bear damaged the Balticconnector gas pipeline and the EE-S1 fiber-optic cable between Estonia and Finland. In December 2024, the vessel Eagle S was suspected of severing the Estlink 2 cable and several communication links in the Gulf of Finland. Subsequent incidents involving vessels such as Yi Peng 3, Vezhen, and Silver Dania indicate a pattern of systematic activity—carried out covertly, often exploiting AIS gaps, transmitting false data, or operating in areas with limited surveillance.
The consequences of these incidents are both local and strategic. Disruptions in the transmission of energy or data between EU (European Union) and NATO (North Atlantic Treaty Organization) member states may impact the stability of energy systems, military communication, and the functioning of essential civilian services. Political tensions are also rising due to the difficulty of clearly attributing responsibility for acts of sabotage, which limits the scope for international response.
In response to these threats, technologically advanced detection and prevention systems are being implemented. In the field of information technology and artificial intelligence, AIS data analysis is being used to identify anomalies in vessel behavior. These systems monitor, among other things, sudden stops, drifting, position signals, or anchor deployments in critical infrastructure zones. The integration of satellite data (e.g., synthetic aperture radar), sonar, and hydrographic information is becoming increasingly widespread, enabling the detection of vessels operating with transponders turned off or engaging in underwater activities.
Complementing these approaches are hydroacoustic solutions, which utilize sonar networks, autonomous underwater vehicles or remotely controlled vehicles (AUVs/ROVs), and seabed-type sensors. These systems can detect characteristic acoustic signatures associated with sabotage operations, as well as analyze water turbidity and changes in seabed structure. Additionally, continuous monitoring of signals transmitted through both electrical and optical cables is employed to identify anomalies indicative of damage or interference.
Despite technological advances, significant systemic gaps remain. Currently, there is no coherent international early warning system for underwater sabotage. Data sharing between states is often fragmented, and many sections of subsea infrastructure remain beyond the reach of monitoring systems. There is also a lack of coordinated procedures for responding to suspicious activities by civilian vessels, especially in the context of legal loopholes related to hybrid operations conducted by third-party states under the guise of legitimate shipping.
To improve detection and counteraction capabilities, several solutions have been proposed: the integration of AIS, sonar, and satellite data within a unified analytical platform; the expansion of acoustic sensor networks along key cable routes; and the training of machine learning algorithms on real-world incident patterns. Simultaneously, political and legal actions are necessary: the development of a common maritime policy for the protection of subsea infrastructure, the harmonization of vessel control mechanisms, and the establishment of interoperable monitoring systems across the Baltic Sea region.
The vessel movement data recording systems introduced in the Baltic Sea and other maritime areas allow for subsequent or ongoing analysis. Records from the automatic identification system, AIS, are used. In this system, each conventional (but not only conventional) vessel regularly transmits static data such as vessel identification, size, draught, type, and destination, and, with varying frequency depending on speed, dynamic data such as current position, course, speed, and rate of turn [
1].
The authors propose a method adapted from medical screening procedures for use by coastal state authorities, enabling coordinated action based on radio-electronic surveillance of both national and adjacent waters. This approach is combined with a multi-criteria decision analysis (MCDA) of vessel behavior, enhanced by continuous analysis of available government and commercial databases that record vessel status and behavioral history.
The method is based on comparing vessels with one another. Against the background of ships exhibiting positive characteristics, operating in accordance with regulations, and having a clean record, suspicious vessels will stand out in the final evaluation.
In order to identify the groups and individual criteria, a survey (expert study) was conducted among participants of courses for the Master Mariner license and management-level deck department courses at the Officer Training Center of the Maritime University of Szczecin, as well as members of the Maritime Experts Association (MEA) in Szczecin. This study included participants from four such courses. A total of 75 questionnaires were collected, addressing, among other things, which groups of criteria and individual criteria were considered necessary, along with their assigned weights.
The authors developed a list of evaluation criteria and designed a procedure for a vessel selection system. Computational experiments were carried out, leading to the formulation of a set of recommendations for the early detection of suspicious vessels.
The proposed method will enable the early identification of potentially dangerous vessels for further close monitoring. The initial classification of a vessel as suspicious does not constitute evidence of criminal activity but rather serves as a trigger for further coordinated action. Applying this method will allow for an immediate yet proportionate response to potentially suspicious vessel behavior, ultimately helping to prevent damage or destruction of strategic infrastructure. In the literature, trajectory prediction based on AIS data is the most commonly addressed approach. In contrast, we propose an initial rapid pre-selection using MCDA, followed by trajectory prediction only when necessary. This reduces the burden on tracking systems and computational resources associated with predicting the movement of dozens or even hundreds of vessels.
This paper is divided into several sections. The literature background and review of related publications are presented in the State of the Art Section.
Section 2 presents a block diagram of the developed system along with its explanation, the AIS data decoding procedure, the computational principles of the PROMETHEE method, and a description of the criteria family and the set of alternatives.
Section 3 includes computational experiments and provides graphical outputs along with their interpretation. In
Section 4, the limitations and potential of the proposed method are addressed. A summary of this study is provided in
Section 5.
State of the Art
The problem of tracking vessel movements has gained importance in recent years. This is due to the increasing capabilities for recording and analyzing vessel behavior based on historical data. Real-time tracking techniques are also advancing. Currently, the most effective real-time system is arguably the British “Nordic Warden”, which successfully monitored the actions of a Russian scientific submarine [
2].
Artificial intelligence methods are commonly used for ship tracking. Various deep learning techniques for vessel trajectory prediction are widely applied in research and are presented, among others, in [
3,
4]. Pre-trained YOLO object detection algorithms are also commonly employed.
Applications of different versions of the YOLO algorithm (You Only Look Once) for object recognition and tracking are described in [
5,
6,
7,
8]. The “cascade vector” tracking method was presented by Liu et al. [
9]. Zhang et al. proposed a reliable UAV-based multi-ship tracking method [
10].
Novel approaches for tracking autonomous vessels were presented by Shao et al. and Damas et al. [
11,
12,
13].
Chen et al. developed an adaptive FairMOT tracking method applicable to maritime targets [
14]. FairMOT is a real-time multi-object tracking method. It is based on a neural network and performs simultaneous object tracking and identification. The method uses the CenterNet architecture with Deep Layer Aggregation (DLA). CenterNet detects objects by locating their centers, while DLA enables better fusion of information from different levels of the neural network, which improves the accuracy and efficiency of the model. ADP-based adaptive control for course tracking with prescribed performance was proposed in [
15]. ADP is an emerging advanced control technology developed for nonlinear dynamical systems and based on the idea of approximating dynamic programming solutions. Yang et al. introduced an enhanced SiamMask network for coastal ship tracking [
16]. A Siamese network is a deep learning architecture designed to compare two inputs by processing them through identical neural networks and measuring their similarity. The SiamMask architecture consists of two Siamese networks. Working in parallel, one is acting as a template and the other as a detection branch. A memory-guided perceptual network for coastal ship tracking was proposed in [
17].
D.S. Iltsev presented a contemporary architecture of Global Ship Tracking (GST) systems, including networks and equipment [
18]. A novel course-tracking control method for ships with input delay was described in [
19]. The feasibility of ship detection and tracking using GOCI-II satellite images was demonstrated by Jang et al. [
20]. The Geostationary Ocean Color Imager may be considered as an alternative for AIS tracking.
A method based on deep reinforcement learning for ship collision avoidance and path tracking was presented in [
21]. Zhongyi et al. introduced a robust online learning approach based on a Siamese network for ship tracking [
22]. Setiawan et al. developed a ship trajectory extraction method using a Python-based interpolation technique [
23]. Ship tracking using distributed acoustic sensing data was explored in [
24].
The multi-criteria decision analysis method is outlined in [
25], with an example of its application in the maritime domain provided in [
26]. The authors applied decision-making analysis to evaluate and rank selection criteria and vehicle types for search and rescue operations at sea. Zhang et al. [
27] presented an approach to detecting anomalies in vessel movement that is similar to the one proposed by the authors of the present work. AIS data was also used in their analysis, appropriately filtered, clustered, and then processed using clustering and a Deep Recurrent Neural Network. A similar approach, combining clustering and movement prediction, was proposed by Xie Z. et al. in [
28]. Both references [
27,
28] are based on trajectory prediction using neural networks, which also serves as a means of anomaly detection. This approach additionally allows for the interpolation of “gaps” in AIS data. It aligns with the authors’ methodology, as reflected in certain criteria.
2. Materials and Methods
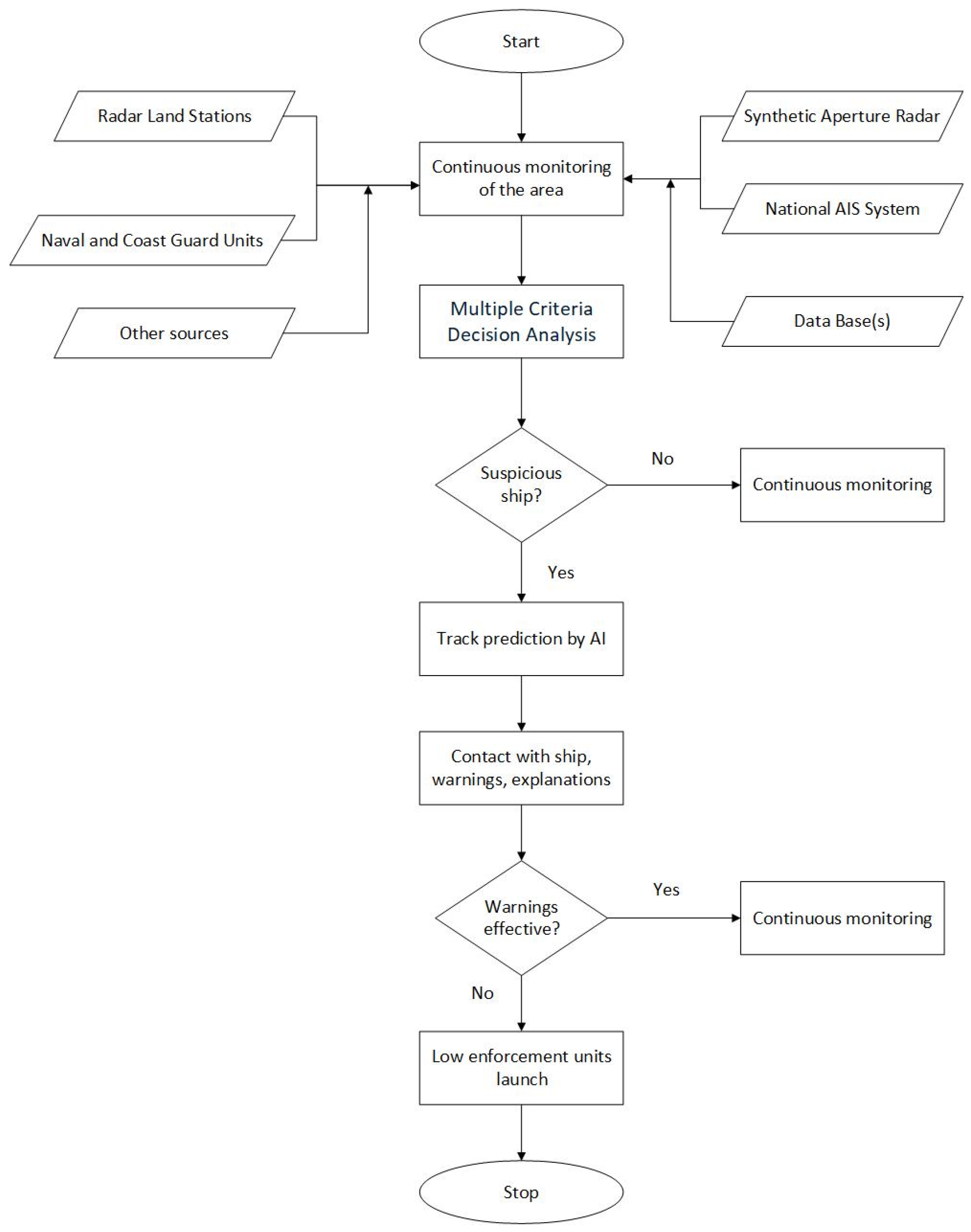
The authors propose an innovative method for the maritime sector, inspired by a well-established medical approach—screening—to enable the early identification of potentially suspicious vessels. The process comprises several sequential phases. The conceptual framework of the system is illustrated in
Figure 1.
In the first stage, the area is monitored using radio surveillance systems, including AIS, radar, and LRIT (Long-Range Identification and Tracking). In the future, satellite-based monitoring will also be employed, incorporating AIS signals and image recognition technologies. Vessel movement parameters and trajectories are continuously analyzed. Simultaneously, data is systematically collected from both national and international maritime databases.
These databases store essential information about a vessel’s history and performance. This stage is crucial, as the collected data including vessel parameters, activity records, and certification history significantly impacts the accuracy of the final results.
In the second stage, the vessels identified in the initial process undergo a multi-criteria evaluation. This type of analysis is an effective method for comparing the characteristics of different objects. It allows for the application of weighted criteria, and the computations enable the simultaneous assessment of various factors. As a result, the evaluated vessels are ranked from the one that best meets the criteria to the one that meets them the least, effectively ordering the ships according to their risk level.
In the second stage, vessels detected through this process undergo a multi-criteria evaluation. Those identified as potentially threatening are subjected to further scrutiny in the third stage, which includes the prediction of their future trajectories. If the level of suspicion increases as a result of this analysis, appropriate naval and law enforcement units are alerted and mobilized for potential intervention.
2.1. AIS Data Scope and Sources
In order to identify suspicious vessels, data from the automatic identification system (AIS) were analyzed. The data were collected by the Maritime University of Szczecin (Poland) using its own AIS receivers, as well as land-based systems such as AIS PL (Poland) and AIS DK (Denmark). The messages transmitted via the AIS are encoded according to the NMEA standard (National Marine Electronics Association), a protocol used for communication between electronic navigation devices. An example of raw data in NMEA format is presented in
Figure 2.
2.2. Data Preparation and Selection
The original raw data, presented in
Figure 2, underwent a decoding and filtering process to eliminate unnecessary information. Following this process, only data from Class A and Class B mobile units were retained. An excerpt of the data used for further analysis is shown in
Table 1.
The data prepared in this manner served as the basis for selecting units for multi-criteria analysis.
2.3. Multi-Criteria Decision Analysis (MCDA)
Multi-criteria decision analysis is based on a set of criteria used to evaluate a set of objects (alternatives—in this study, ships). The performance of the alternatives is compared in a structured, mathematical manner. In this article, the authors have chosen the PROMETHEE method (Preference Ranking Organization Method for Enrichment Evaluations), which is widely applied across various sectors. Other methods, such as the AHP (Analytic Hierarchy Process), are also commonly used in decision-making problems.
In comparison to the AHP, the PROMETHEE method offers several advantages. It handles a larger number of alternatives more efficiently and does not require pairwise comparisons for all criteria, which significantly reduces the cognitive load on decision-makers. PROMETHEE also allows for more nuanced preference modeling through the use of preference functions, enabling better handling of imprecise or uncertain data. Additionally, it avoids the rank reversal problem often associated with the AHP.
Developing a set of criteria and a method for evaluating alternatives in the maritime domain requires expert knowledge. The authors conducted a study involving a group of maritime professionals. To support this, an in-depth analysis was carried out on the risks associated with underwater infrastructure and vessel behavior in the vicinity of such critical areas.
The method is a multi-criteria decision analysis technique designed to rank a finite set of alternatives based on multiple, often conflicting criteria. PROMETHEE is particularly useful when decision-makers aim to evaluate and compare objects using both qualitative and quantitative criteria, while incorporating the concept of preference intensity.
The method begins by defining a set of alternatives
A,
and a set of evaluation criteria
C,
each associated with a weight
wj, where
For each criterion
Cj, a preference function
Pj,
is used to express the degree to which alternative
Ai is preferred over
Ak. The aggregated preference index
π between any two alternatives is given by
Based on the aggregated preference indices, two flows are computed for each alternative: the positive flow
φ+(
Ai), indicating how much an alternative outranks others, and the negative flow
φ−(
Ai), representing how much it is outranked by others:
The net flow
φ is then defined as
In the method, alternatives are fully ranked based on their net flow values. The higher the net flow value, the better the alternative meets the evaluated criteria. In the case of risk assessment, a higher score indicates that the alternative is considered more risky within the set of alternatives under consideration.
2.3.1. Set of Criteria
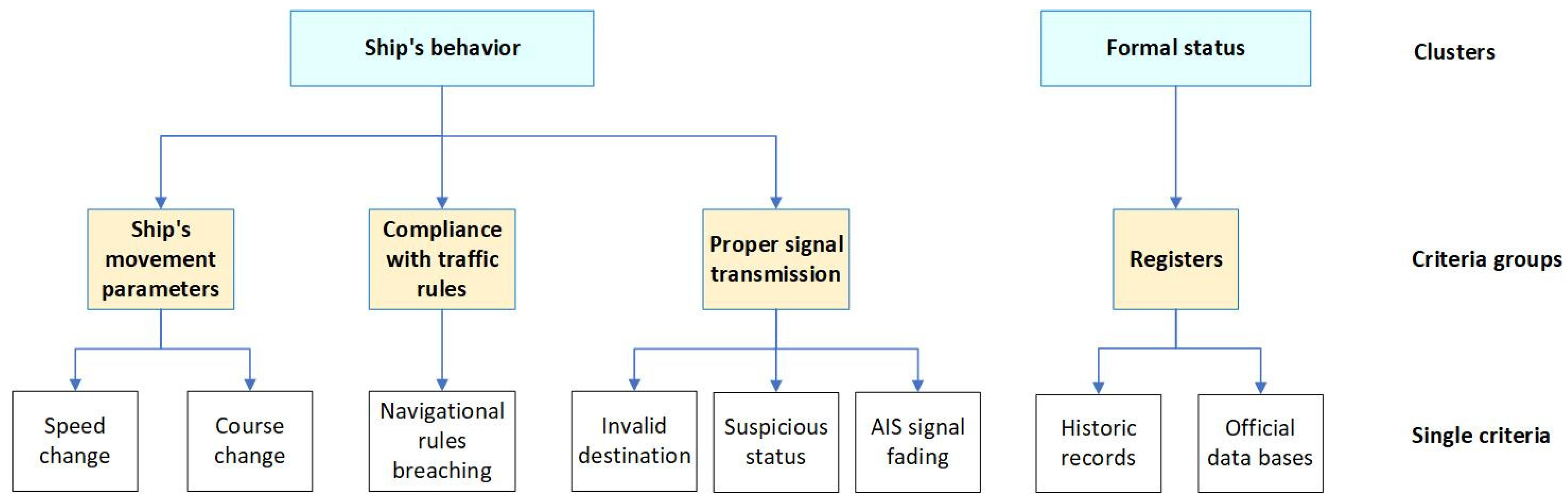
The ship assessment model was based on relevant criteria. These criteria constitute a coherent set that describes the ship and its behavior. The authors considered parameters that could signal anomalies, arouse suspicion, or point to potentially abnormal behavior of the vessel within the designated waterway.
The criteria set consists of eight individual criteria: C1, change in speed; C2, change in course; C3, breach of navigational rules; C4, invalid destination details; C5, suspicious navigational status; C6, AIS signal fading; C7, registers; and C8, databases. The individual criteria are grouped into categories and clusters, forming a three-level structure (
Figure 3). Two clusters have been defined as follows: parameters related to the ship’s behavior and its official status. The first cluster includes three groups: movement data, compliance with traffic rules, and proper signal transmission. The second cluster includes a group containing ship registers. The characteristics of the criteria and the evaluation method for the ships are presented below.
A sudden and significant reduction in speed (C1) is usually an important indicator that the ship intends to maneuver. In the context of an attempt to damage underwater infrastructure, low speeds or stopping the vessel is necessary in order to drop the anchor. Due to its size and weight, the anchor can be used to hook onto submarine cables. The weight of this criterion was set at 25%.
The same applies to course changes (C2). Large course changes are observed during various ship maneuvers (e.g., approaching a waypoint or deploying fishing gear). This type of behavior depends on the type of vessel; however, if it occurs near underwater infrastructure, it can serve as a warning signal. When observing streams of vessels navigating along established routes, noticeable deviations from these paths may raise suspicion. The weight of this criterion was set at 15%.
Criterion C3 (navigational rule breaching) examines the ship’s behavior in relation to the traffic regulations in force within a given body of water. There may be a fixed direction of navigation, or certain areas may be designated as restricted (e.g., wind farms). Non-compliance with these rules is always a cause for concern. The weight of this criterion was set at 15%.
The operator of the vessel’s AIS is expected to enter information about the ship’s destination (C4). However, this information is often outdated or intentionally omitted. In the context of underwater infrastructure sabotage, this may be considered suspicious. The weight of this criterion was set at 5%.
In accordance with the COLREGs (Convention on the International Regulations for Preventing Collisions at Sea), vessels communicate their navigational status (C5) through the use of navigation lights (e.g., underway, at anchor, not under command). This status is also reflected in the automatic identification system. Any change in navigational status may influence the behavior of other vessels in the vicinity, as it implies specific rights and obligations under maritime traffic regulations. However, there exists the potential for misuse of this mechanism, whereby a vessel may intentionally transmit a false status to compel other ships to alter course or yield navigational space. The weight of this criterion was set at 5%.
The deliberate deactivation of the AIS signal (C6) is typically intended to hinder vessel tracking or the acquisition of information about the ship. Vessels subject to the SOLAS Convention (International Convention for the Safety of Life at Sea) are required to operate this system continuously. The fading of an AIS signal is particularly concerning in areas of heightened security risk. It is possible that AIS signal loss may also result from other external terrorist activities (e.g., jamming, spoofing) that are independent of the crew. However, such actions typically affect all vessels in the vicinity, making this a specific and distinct scenario. In this study, we focus on deliberate actions undertaken by the vessel itself. The weight of this criterion was set at 10%.
Ships are required to be registered (C7) and to meet specific regulatory requirements, as evidenced by certificates issued by the competent maritime administration authorities. Each vessel is granted authorization for operation. Verification of a ship’s registration and certification records can facilitate the identification of potentially substandard or high-risk vessels. The weight of this criterion was set at 15%.
Another way to verify non-conformities, violations, and inappropriate activities of a vessel is to review its status in various ship databases (C8) (e.g., THETIS, Equasis, Sea-web, Lloyd’s Register, OCIMF, etc.). International and national databases are highly reliable sources of information on a ship’s history and current condition. The information available includes, among other things, results of surveys and inspections, and details of accidents and incidents. The weight of this criterion was set at 10%.
The sensitivity of the weights was assessed by comparing scenarios and observing changes in the positioning of alternatives within the final ranking. In accordance with the principles of the PROMETHEE method, several trials were conducted by varying the weights within a range of 5–10%. This process enabled the stabilization of the ranking structure.
2.3.2. Evaluation Method and Set of Alternatives
The method of evaluation is aligned with the assumptions and requirements of MCDA. The first two criteria are quantitative, while the remaining ones are qualitative. All criteria are maximized.
Criterion C1 is expressed as a percentage. The authors determined that this criterion would have two thresholds: 50% (the indifference threshold) and 90% (the preference threshold). When comparing two alternatives, they are treated as equivalent if the difference in their values is below the indifference threshold (they receive a score of 0). If the difference falls between the two thresholds, a score is calculated using a linear scale ranging from 0 to 1. A difference exceeding the preference threshold automatically classifies one of the alternatives as the leading one, which then receives a value of 1 in the evaluation. Reductions in speed are observed during the voyage, which is considered normal operation. However, significant reductions may indicate an intention to perform specific maneuvers.
A similar principle applies to changing courses. Criterion C2 is expressed in degrees. Following TSS routes (traffic separation scheme) forces ships to maintain specific headings. Course changes of smaller magnitude can be related to normal navigation, such as giving way to another ship. The authors set the indifference threshold at 30 degrees and the preference threshold at 60 degrees. The method of evaluation is analogous to that used for C1.
Criteria C3–C8 are evaluated on a two-level yes/no scale. If the factor is present, the alternative receives 1 point; otherwise, it receives 0 points.
Criterion C3 examines the ship’s behavior in relation to applicable, region-specific traffic regulations. An alternative receives 1 point if the vessel’s movement is non-compliant (e.g., entering a restricted navigation area), and 0 points if the movement complies with the rules. For the correctness of entering the destination port code (C4), an alternative receives 1 point if this information is inconsistent with the direction of traffic or voyage information, or if the information is missing. The alternative receives 1 point if there is a change in navigation status (C5) or a suspected mismatch in status. The disappearance of the AIS signal (C6) or the detection of a malfunctioning system results in the assignment of 1 point to the alternative. When abnormalities related to registration, flags, or certificates (C7) are detected for an alternative, 1 point is assigned. Similarly, if the ship receives a negative evaluation based on database records (C8), 1 point is assigned.
The set of alternatives consists of several vessels operating in the study area. Thirteen sample vessels were selected for analysis (
Table 2). Information about these vessels was simulated and based on realistic data. The simulated data reflect typical navigation scenarios. During navigation, ships perform various maneuvers, such as changing course, overtaking, or stopping. Some of these maneuvers may not comply with traffic regulations in a given water area. Additionally, ships may transmit incorrect signals. The ship’s official status data were modeled to reflect standard operating conditions; some ships may have a negative history, while others may have a clean record. So, in the first step, information about each alternative A is collected.
Table 2 shows the evaluation matrix for the set of alternatives A1–A13, assessed according to each criterion C1–C8. For example, vessel A3 made an alteration of course by 15 degrees relative to the previously maintained heading. The course change criterion is designated as C2, and the value is recorded in the data table. Additionally, documentation irregularities were retrieved from the vessel databases. Under criterion C8, the vessel is assigned a score of (1).
3. Research and Results
The Baltic Sea, which has been particularly targeted in recent months, was selected for a more comprehensive analysis. Since the attacks have been carried out by commercial vessels flying the flags of countries not involved in any conflicts, all cargo, passenger, and fishing vessels operating in the area were included in the study.
3.1. Area of Research
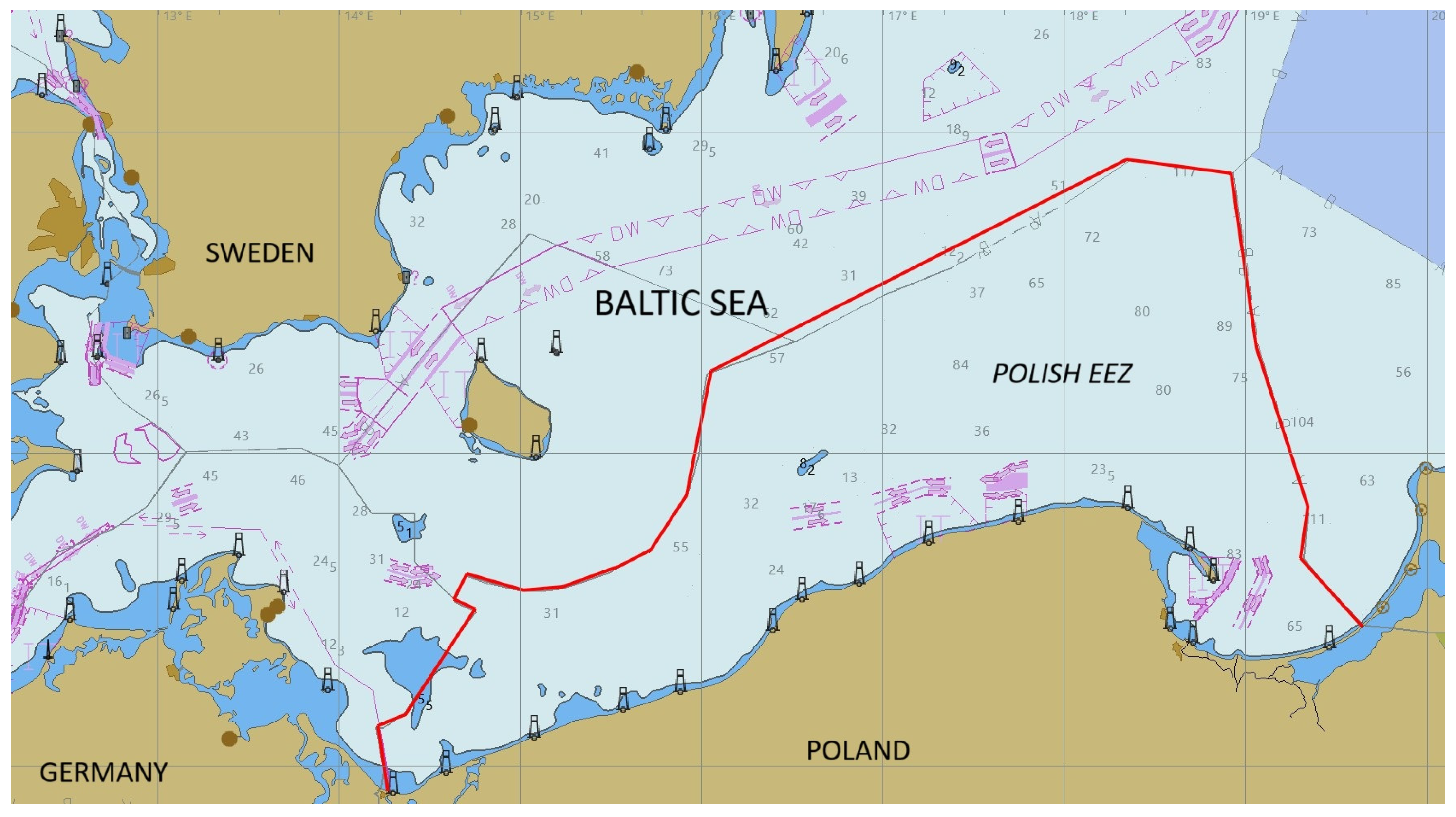
This paper presents selected studies conducted in the sea areas of the Polish Exclusive Economic Zone (
Figure 4), with the EEZ boundary marked in red.
The analysis included vessels in transit along traffic separation schemes or customary shortest routes, as well as those arriving at or departing from Polish ports (
Figure 5). Vessel route traces are marked in blue.
3.2. MCDA Results
In this study, five computational experiments were conducted. In the first scenario, the research group consisted of thirteen vessels. In the remaining scenarios, the groups included between two and four vessels. This approach made it possible to demonstrate different ways of interpreting the results depending on varying conditions.
The results of the MCDA for the examined set of ships are presented in the form of a PROMETHEE complete ranking, based on the net flow values computed for each alternative. The alternatives are ranked according to their aggregated preference scores, which reflect the degree to which they meet or fail to meet the established evaluation criteria. A higher net flow value (closer to +1) indicates a greater concentration of negative or suspicious characteristics in the corresponding vessel, as it is less preferred relative to others in the set. This ranking structure facilitates the efficient identification of outlier ships that deviate significantly from the normative behavioral pattern.
In the first scenario (
Figure 6), a significant concentration of alternatives is observed at the lower end of the net flow axis, with minimal pairwise preference differences. This part represents ships that exhibit a low degree of compliance with the evaluation criteria and can therefore be classified as non-suspect (or safe) at the current time.
Above this group, four alternatives are positioned at intermediate net flow values and are more widely spaced, indicating varying degrees of deviation from the baseline group. Alternatives A7 and A6 occupy mid-ranking positions and may be interpreted as vessels of heightened risk, based on their partial compliance across multiple criteria. Alternatives A3 and A10 are located at the upper end on the net flow scale. These outlier alternatives display significantly higher aggregated preference indices and form a distinct suspect group, suggesting potential anomalies or elevated operational risk.
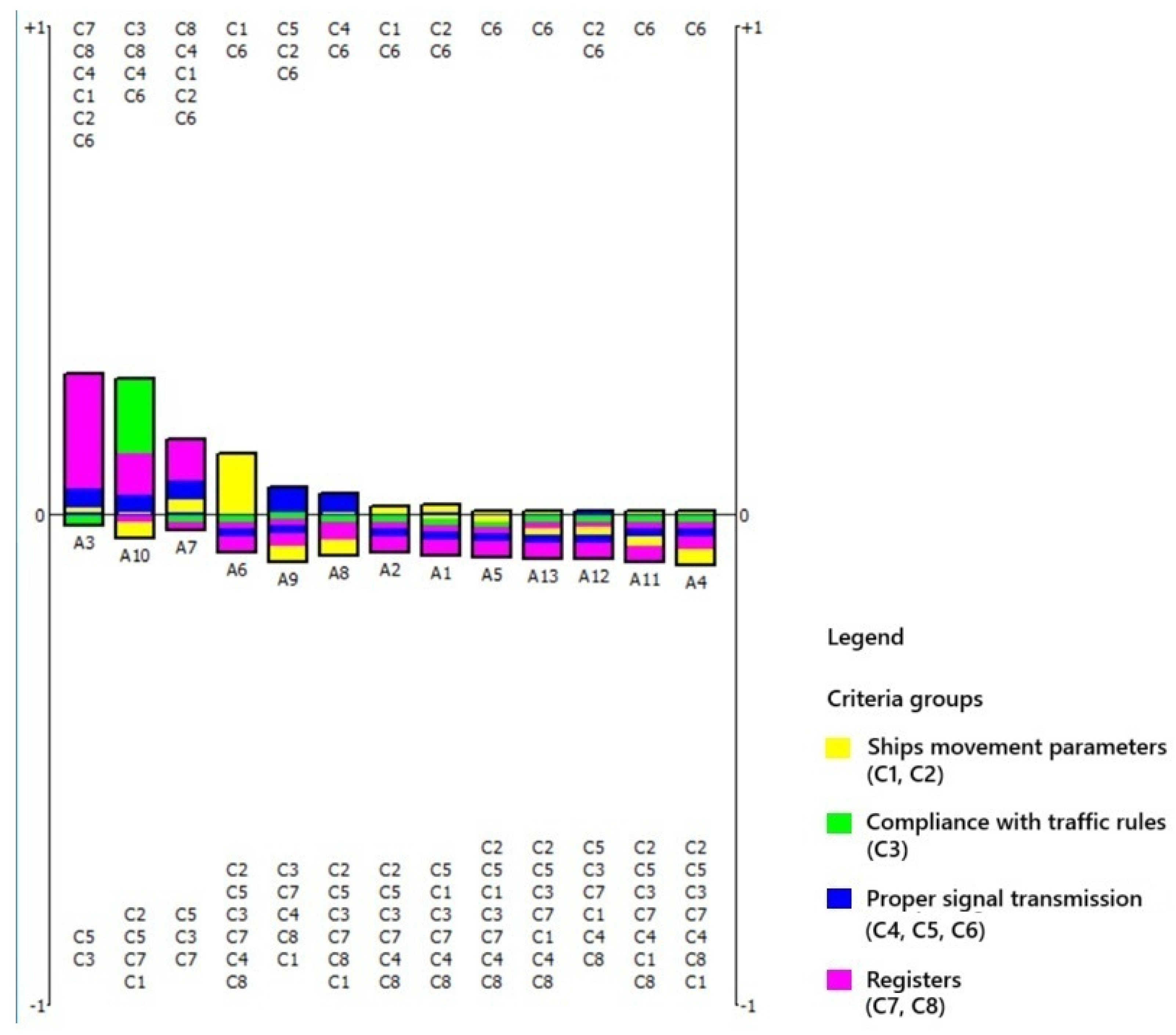
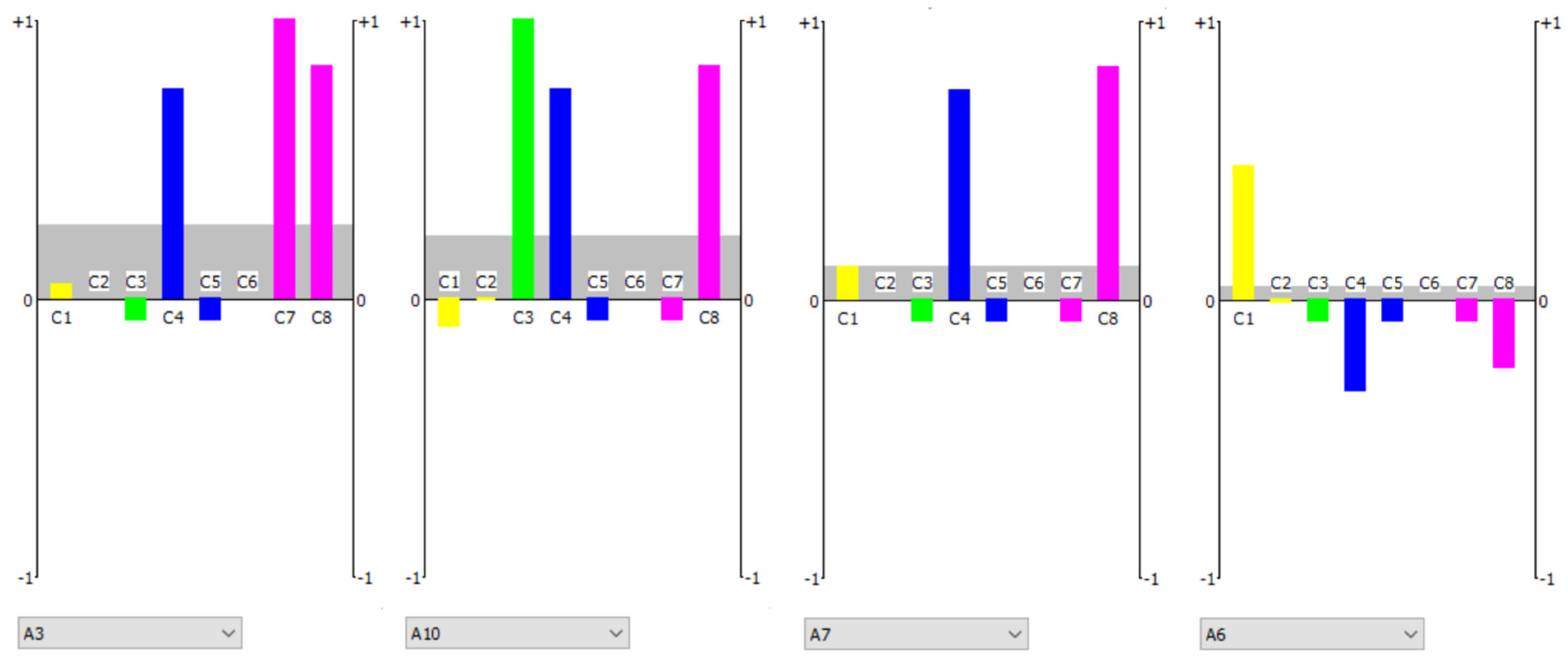
The results can also be visualized using supplementary methods that enable a rapid assessment of which individual criteria, or groups of criteria, had the most significant influence on the evaluation of a given alternative. In other words, they help identify the specific reasons why a vessel is classified as suspect. For this purpose, the PROMETHEE rainbow (
Figure 7) visualization is applied, as it allows for the decomposition of the global preference flow into partial contributions from each criterion. Visualization enables the identification of a subgroup of potentially high-risk vessels (A3, A10, A7, A6), based on the intensity and structure of criterion-level contributions. In contrast, the remaining alternatives (A9, A8, A2, A1, A5, A12, A13, A11, A4) form a baseline group, characterized by lower cumulative scores and less pronounced indicators of non-compliance. An individual evaluation of each alternative is also possible.
The upper section of the PROMETHEE rainbow graph displays the criteria numbers that contributed the most to the total score assigned to a given alternative, indicating the presence of undesirable or suspicious features. The lower section shows criteria numbers with a lower impact on the alternative’s final assessment. In the case of alternative A3, the most influential criteria include C7, C8, C4, C1, C2, and C6, which collectively contributed the largest share of points. The criteria are grouped and color-coded by criteria group. For A3, the dominant contributions are observed in the purple group (irregularities in vessel registration).
In the next step, the profile of the selected alternatives can be analyzed (
Figure 8). Criteria that contributed to the overall score are represented as upward-facing bars. Groups of criteria are distinguishable by color. The net flow value is indicated by a gray horizontal line. In the case of alternative A3, the final two criteria (C7 and C8) contribute significantly to the evaluation due to issues related to the vessel’s registration and certification, as well as its history of inspections or accidents (purple group). For alternative A10, three criteria (C3, C4, and C8), each from a different group, are responsible for its high score. The green group reflects non-compliance with navigational regulations, the blue group indicates signaling irregularities, and the purple group relates to the vessel’s official status. The rank position of A6 suggests that this alternative also should be subject to further risk-oriented analysis. Its relatively high score results from the fulfillment of a single, but highly significant, criterion—C1—which belongs to the yellow group associated with vessel movement parameters. This ship may be classified as a unit requiring further monitoring.
The proposed method provides quick results, and the analysis is straightforward. Compared to average ships, a suspect vessel will typically appear at the top of the ranking. A more detailed analysis can reveal the individual criterion or group of criteria responsible for the final score. However, the method also has its limitations. Currently, there is no integrated access to all necessary databases. Implementing this method will require both legislative and technical solutions. On the legislative side, appropriate international agreements are needed to enable data sharing. On the technical side, IT solutions will require a seamless and attack-resistant platform capable of integrating the relevant parameters.
The above analysis was carried out for a relatively large set of alternatives. In real-world maritime conditions, within such a group, most vessels will typically be positively evaluated. A vessel that receives a negative evaluation will stand out clearly against the background of positively rated ships.
When the set of alternatives is smaller, the analysis becomes more challenging.
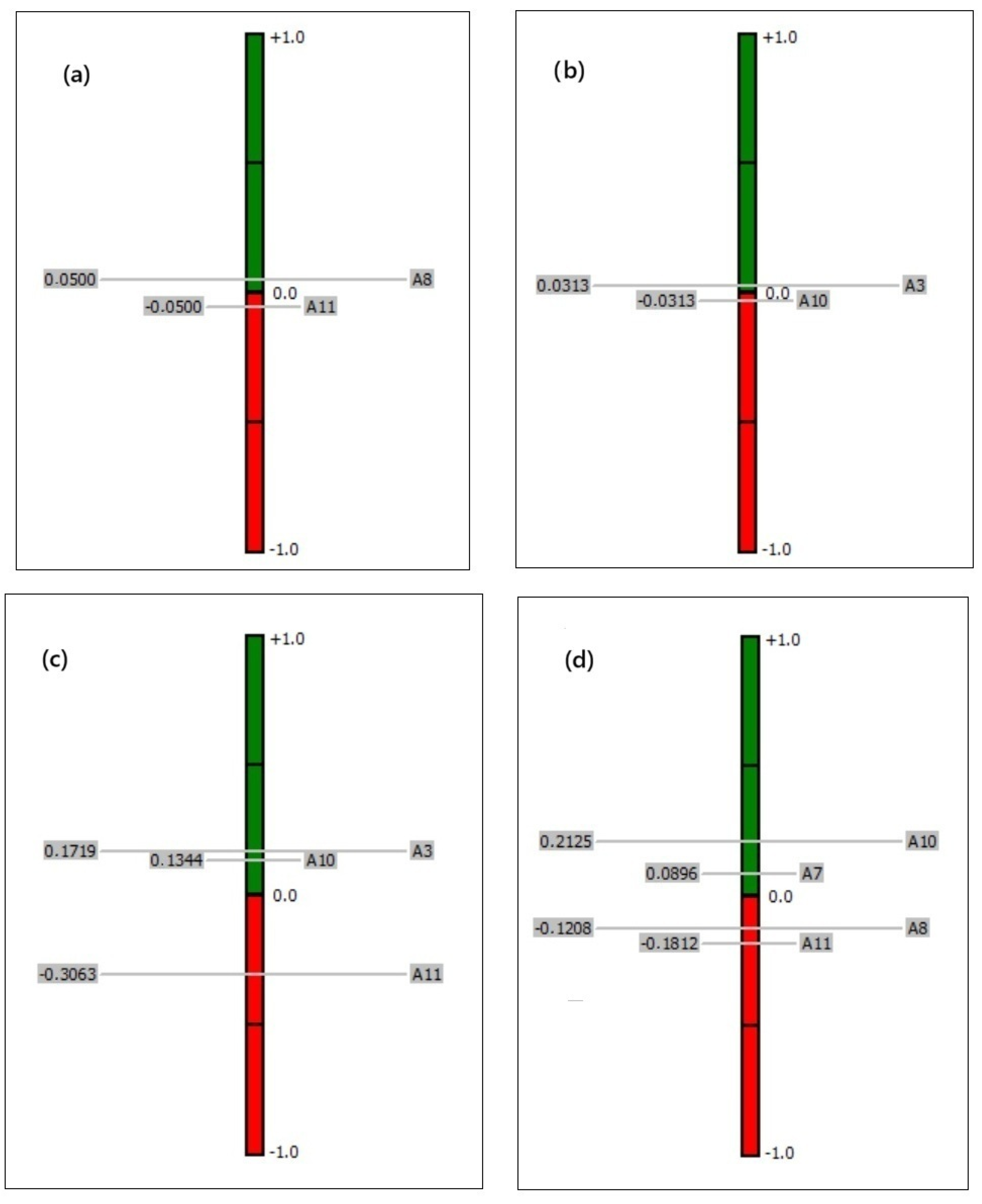
Figure 9a–d present the results of additional scenarios (Nos. 2, 3, 4, and 5) involving small groups of vessels.
Figure 9a,b (Scenarios 2 and 3) show the results of a multi-criteria evaluation involving two pairs of vessels. This means that the analysis is based solely on a comparison between the two vessels in each pair. Two pairs of vessels with remarkably similar characteristics were selected for the study (A8 and A11, and A3 and A10). From the first scenario, it is known that the first pair is considered safe, while the second pair is classified as suspicious.
If the vessels are indeed remarkably similar to each other, their net flow values will be close to zero. A small distance between them in the ranking suggests only minor differences in their evaluations. In such cases, it is not possible to determine definitively whether the vessels are safe or suspicious. We can only observe which one meets the risk criteria to a greater extent—meaning that it is considered more dangerous.
However, this issue can be addressed by introducing a reference alternative into the analysis. Such a reference alternative is defined as having a desirable set of attributes—meaning that it is positively evaluated across all criteria. In this case, it is a ship that complies with traffic regulations, possesses clean records, transmits AIS signals properly, and exhibits stable maneuvering behavior. Alternative A11 serves as an example of such a reference vessel.
Figure 9c (Scenario 4) presents the results of an analysis of three vessels: A3, A10, and A11. Knowing that A11 is a reference alternative, vessels that deviate significantly—such as A3 and A10—will be ranked far apart.
In comparing rankings in
Figure 9b and
Figure 9c, it is clear that introducing a reference alternative not only allows for the examination of differences between A3 and A10, but also reveals that they differ significantly from A11. On this basis, even though the group is small, these vessels can be identified as suspicious. This confirms also the results obtained in Scenario 1 (
Figure 6). An analogous result was noticed in the assessment of a group of four vessels, illustrated in
Figure 9d (Scenario 5).
3.3. AIS Results
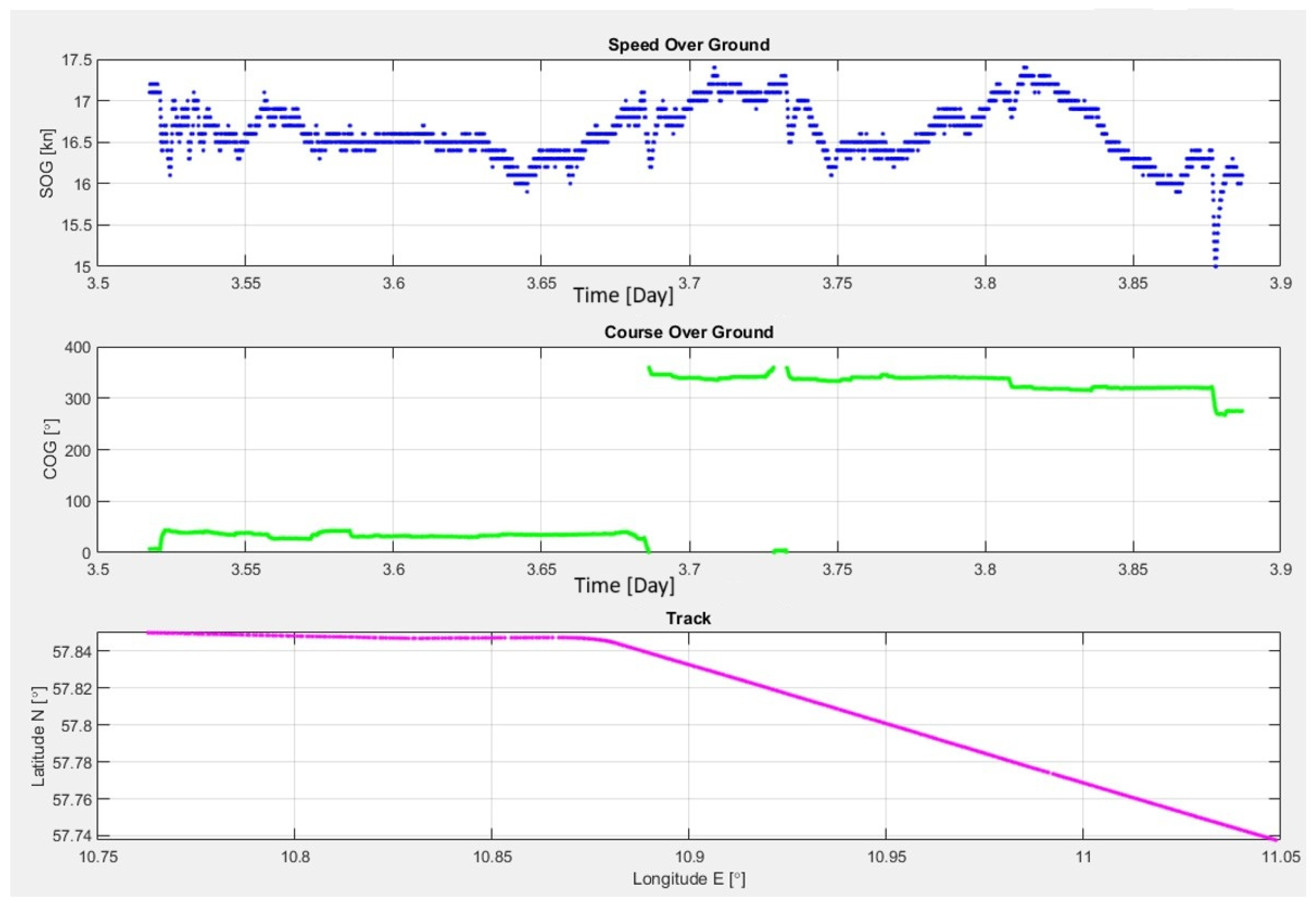
Selected examples of vessel movement parameter visualizations are presented in
Figure 10. The figure shows the speed over ground (SOG), course over ground (COG), and the position of one of the analyzed vessels.
The figure above shows the normal operating parameters of a vessel, including a slight decrease in speed to 15 knots, which does not raise suspicion during the initial stage of analysis and is only subject to routine monitoring.
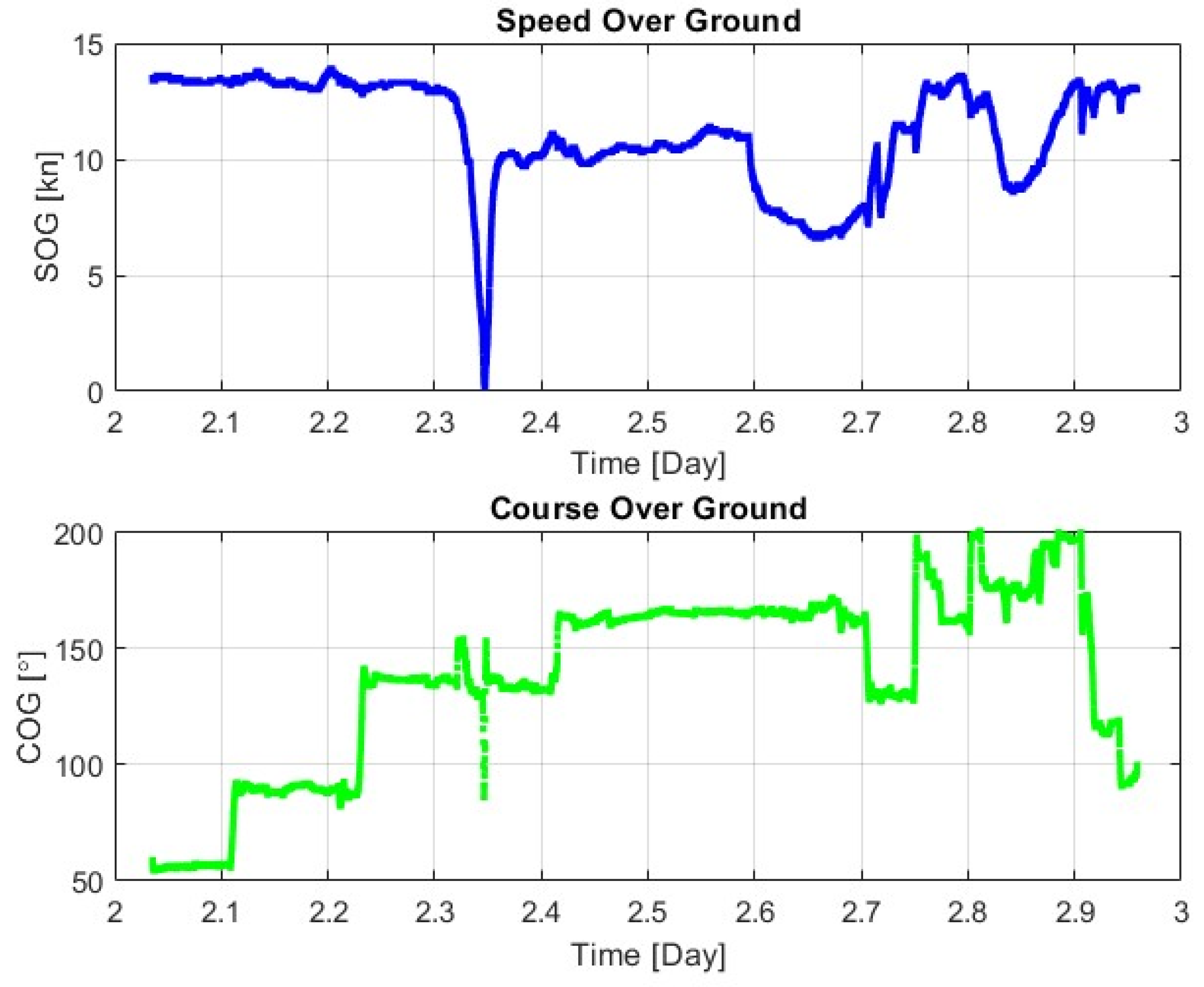
Figure 11, on the other hand, presents actual graphs of the speed over ground (SOG) and course over ground (COG) of a ship behaving suspiciously. The ship is on a transit route, directly above submarine power cables. A sudden and significant reduction in speed to zero is visible, which is considered abnormal at this location.
At this point, the ship, moving at a course of approximately 135°, makes a sharp turn to port (left) to approximately 080°, and then to starboard (right) to approximately 155°. According to experienced maritime navigators, this is a typical indication of dropping the port anchor, which is considered unjustified at this location. The ship then quickly increases its speed to 10 knots and proceeds along the recommended route, moving away from the area. Such a vessel is immediately subjected to a full MCDA, and appropriate measures are taken by law enforcement and naval units.
Since the described incidents are relatively infrequent, simulation studies using machine learning were also conducted to predict ship movements.
Figure 12 shows a simulated maritime infrastructure area (highlighted in yellow) marked on the chart, which several vessels are approaching. Ship traces are presented in blue.
Vessel 1, moving on a westerly course, does not alter its heading early enough to avoid the area and is proceeding directly toward it. Vessel 2, following a west–southwest course near the boundary, is being monitored and warned.
The forecast trajectory, marked in red, half an hour before entering the area, combined with the MCDA, indicates the need for decisive action by the authorities supervising the maritime area.
4. Discussion
The protection concept for critical maritime infrastructure against potential attacks by vessels, developed by the authors, consists of several stages.
The first stage involves the detection of vessels approaching sensitive maritime zones and the collection of detailed data. Currently used radar, radio (including satellite), and hydroacoustic systems are helpful to some extent, but they are not fully reliable and do not operate as part of an integrated platform.
The proposed method primarily relies on the automatic identification system and Vessel Traffic Service (VTS) radar imaging, which provide precise information on vessel movements, including speed, course, vessel type, and voyage-related data. However, the AIS operates in the VHF band (Very High Frequency), making it susceptible to signal interference.
In the initial research phase, the authors collected AIS data from the southern Baltic Sea using their own receiver, decoded the transmissions, and performed a detailed analysis. This enabled the construction of traffic maps and the behavioral analysis of selected vessels during maneuvering operations (
Figure 5,
Figure 10 and
Figure 11), which served as a foundation for the subsequent stages of the methodology.
Data acquisition should also include access to historical information, such as the results of technical inspections and the vessel’s registration and certification status in maritime administrations. These datasets are highly valuable for identifying potential threats, though integrating such large and diverse sources requires both legal frameworks for international data access and advanced IT solutions. The European SafeSeaNet system serves as a relevant example of such integration in practice. Emerging technologies, such as cloud-based data analytics and artificial intelligence, provide promising solutions to address these challenges.
In the second stage, the detected vessels are assessed using multi-criteria decision analysis based on the PROMETHEE method. The authors defined eight key criteria, thematically grouped, and determined their respective weights and preference functions. The method is based on pairwise comparisons of vessels, resulting in a ranking from the one most to the one least aligned with the risk-related criteria.
When analyzing a large set of vessels, graphical results allow for rapid identification of potentially suspicious units. The outcomes are presented in the form of a final ranking (net flow), a criterion-based overview (rainbow), and individual alternative profiles. However, a high position in the ranking does not necessarily indicate malicious intent; the vessel may simply be maneuvering (satisfying criteria C1 and C2). These two criteria carry significant weights (25% and 15%, respectively), as sudden reductions in speed near subsea infrastructure may signal attempts to deploy anchors or interfere with underwater installations. Therefore, such vessels should be subject to continued monitoring and trajectory prediction, as illustrated in
Figure 12.
Another important criterion is compliance with certification standards (C7). While most vessels maintain a valid legal and technical status, there are notable exceptions. For instance, in 2025, the vessel Kiwala was detained after operating without registration under any national flag, thereby engaging in illegal maritime activity.
The most important features of the MCDA method in the proposed approach are as follows:
The results are dimensionless and relative.
The outcome of the analysis reveals differences in the degree to which the vessels in the set meet the defined criteria.
The analysis requires the provision of multiple data inputs; however, it can still be conducted in the absence of some information, although this may reduce the quality of the results.
A minimum of two vessels must be included in the evaluation.
Vessels with similar final scores will be positioned close to each other in the net flow ranking.
The use of a reference vessel is recommended.
A reference vessel is an alternative characterized by desirable features, meaning that it does not meet any of the risk criteria.
Including a reference vessel in the analysis facilitates the selection of units based on their potential threat level.
In most real-world cases, the majority of vessels will score lowly, making suspicious units easily distinguishable in comparison.
The MCDA method is a supporting tool; its results should be treated as decision support rather than definitive conclusions.
In the third stage, vessels identified as high-risk are subjected to enhanced monitoring. Early detection of anomalies enables a faster response by relevant authorities and more effective protection of subsea infrastructure.
The proposed method is based on mathematical models and IT technologies; however, final verification must be performed by a human expert, such as a naval officer or analyst. In the future, artificial intelligence—utilizing machine learning—may play a greater role in supporting decision-making processes. The proposed concept is developed with this direction in mind.
Currently, there are no civilian tracking systems that analyze anomalies, so it was not possible to compare our results with those of other systems. Anomaly detection systems are still in the research phase, and their results have been presented, among others, in [
27,
28]. This is consistent with the authors’ approach, as reflected in criteria C1 and C2. However, the authors’ method is broader, incorporating additional criteria C3 through C8. As a result, this study is more comprehensive and better adapted to the nature of terrorist threats.
5. Conclusions
Rapid and effective response to threats to the normal functioning of humanity and the economy is one of the greatest challenges of the third decade of the 21st century. To combat elements of unspoken hybrid warfare, it is necessary to expand existing surveillance systems, adapt solutions from other fields of knowledge unfamiliar to the maritime sector, or develop new systems from scratch based on the latest scientific advancements.
The methods currently used for protecting maritime critical infrastructure primarily focus on visual and radio-electronic monitoring of supervised waters. However, existing approaches do not incorporate real-time analysis of available official databases, which prevents early pre-selection of potentially suspicious vessels.
The presented method is based on a combination of the MCDA method and AIS technology, supported by continuous radio-electronic observation of the water area, and extended with access to official ship databases. In the next stage, due to the volume of data being processed, the use of artificial intelligence is planned to support basin surveillance. It would be the AI that performs the initial selection of vessels, which would then be further analyzed by traffic monitoring experts. The application of AI will require advanced IT technologies that either do not yet exist or are still in the early stages of development.
The developed method is not a definitive tool for identifying illegal ship activities; rather, it is intended as a support mechanism for protecting critical infrastructure and assisting in post-incident investigations. The reliability of the method depends on the appropriate selection of the criteria set and the accurate evaluation of alternatives based on these criteria. A key factor is the choice of qualified experts to define the evaluation framework. In this study, the assessment team consisted of experienced captains and merchant marine officers. This method requires further development, particularly in securing official access to national and international databases. Such access, however, requires standardization and the implementation of a unified authorization system.
The key aspects of the method’s applicability include:
The possibility of using it in any sensitive maritime area;
Acceleration of the vessel identification process;
Facilitation of the selection of potentially dangerous vessels;
Enhancement of the protection of critical maritime infrastructure;
Improved protection of human life and the environment;
Strengthened international cooperation in the field of safety and security at sea.
The innovative aspects of this study include the expert research conducted, the development of vessel evaluation criteria, and the design of a comprehensive system that collects heterogeneous data on vessel anomalies, processes the information using preference functions, and generates results for the selection of high-risk vessels and early warning of threats to critical submarine infrastructure.
The overarching goal of this study was to improve and ensure maritime security, and to counter emerging threats that have either not occurred before or only appeared on a limited scale. The implementation of the method developed by the authors requires further research, but it holds great potential for application in the offshore sector to protect the maritime sector.