Abstract
Vehicle-to-everything (V2X) communications enable vehicles to interact with each other and various components of the traffic system, forming the backbone of modern intelligent transportation systems. However, V2X communications are highly susceptible to cyberattacks, posing a threat to both safety and operational efficiency. This paper proposes a real-time anomaly detection framework that integrates the reconstruction capabilities of Variational Autoencoders (VAEs) with the feature extraction power of Convolutional Neural Networks (CNNs). Our model processes streaming data using a sliding window mechanism, ensuring prompt detection of anomalies in the dynamic V2X environment. Extensive experiments demonstrate that our method achieves high performance across diverse anomaly types, with precision, recall, and F1-scores reaching up to 0.91, 0.99, and 0.95, respectively, on challenging anomalies such as constant position offsets. The model consistently outperforms both a traditional autoencoder and a VAE with Long Short-Term Memory (LSTM) layers, particularly on complex anomalies like vehicle speed and position offsets. Additionally, our framework maintains a low inference time of approximately 0.0013 s, making it highly suitable for real-time deployment. Designed to adapt to evolving traffic patterns through periodic retraining, the proposed approach ensures long-term reliability and robustness. By delivering high performance, adaptability, and efficiency, our method provides a reliable way to detect and prevent cyberattacks, thereby making intelligent transportation systems safer and more dependable.
1. Introduction
Vehicle-to-everything (V2X) communication is a key component of intelligent transportation systems (ITSs). It enables vehicles to communicate with each other (V2V), with infrastructure (V2I), with pedestrians (V2P), and with networks (V2N) [1]. For instance, Basic Safety Messages (BSMs) [2] are the most common V2X messages, whereby vehicles broadcast to inform surrounding vehicles about their position, speed, direction, and other state information. Because they contain critical data about vehicle dynamics, BSMs are highly relevant for detecting anomalies, such as sudden deviations in driving behavior, spoofed GPS coordinates, or irregular speeds, that may suggest sensor malfunctions or data falsification attacks. This interconnected environment aims to enhance road safety, improve traffic efficiency, and enhance the driving experience [3].
However, the increased connectivity also brings significant security challenges, making V2X systems vulnerable to various cyberattacks [4]. In this paper, V2X security specifically addresses the challenge of detecting anomalies in BSMs that cyberattacks, such as data injection or manipulation, may cause. Such attacks aim to falsify kinematic information (e.g., position, speed), thereby undermining the reliability of V2X communications and posing significant risks to road safety and traffic efficiency. Key security concerns include ensuring data integrity to prevent tampering, verifying the identity of entities through robust authentication mechanisms to prevent unauthorized access, maintaining the confidentiality of sensitive data, guaranteeing the availability of V2X services amidst attacks like Denial of Service (DoS), and protecting user privacy to prevent the exposure or misuse of personal information [5].
Traditional security mechanisms such as encryption and robust authentication protocols are necessary for securing communication. It is essential to emphasize that anomaly detection systems, such as the one proposed in this work, are designed to operate as part of a defense-in-depth strategy. They complement other essential security measures, such as cryptographic mechanisms and network-level security. Our approach focuses on identifying anomalies in the semantic content of V2X messages, which might still occur even if messages are cryptographically sound. These traditional approaches alone are often inadequate in dynamic V2X environments where attacks evolve rapidly, and computational efficiency is a priority [6]. Encryption, while effectively safeguarding data confidentiality and integrity, does not inherently detect or mitigate real-time cyber threats. For instance, encrypted malicious messages can still disrupt operations or cause accidents if not identified and addressed in real time. Therefore, there is a pressing need for a robust security framework that can effectively counter these threats while maintaining the efficiency and reliability of V2X communications [7].
Generative AI offers innovative solutions to enhance the security of V2X communications, particularly through the use of Generative Adversarial Networks (GANs) and Variational Autoencoders (VAEs) [8]. These models excel in anomaly detection by learning the expected behavior of V2X communication patterns and flagging any deviations as potential security threats. For instance, GANs can be trained to generate synthetic network traffic that mimics normal traffic patterns, and the discriminator in the GAN can then detect abnormal traffic, indicating a possible attack.
VAEs have emerged as a powerful tool for anomaly detection due to their ability to learn latent representations of normal behavior in high-dimensional data. VAEs can identify deviations that signify anomalous behavior by reconstructing input data and measuring reconstruction errors. This probabilistic framework allows VAEs to model uncertainty, making them highly effective in detecting subtle and complex anomalies that are difficult to identify using traditional methods [9]. For example, in V2X communication, VAEs can identify anomalous patterns in vehicle dynamics, such as irregular speed variations, abnormal acceleration, or positional deviations, by learning a probabilistic representation of normal patterns.
VAEs can also significantly improve security training through data augmentation [10]. By creating realistic synthetic data, these models can augment training datasets for security algorithms, enabling the development of more robust models capable of detecting a wide range of attack scenarios. In terms of authentication, generative models can produce diverse biometric data, such as voice and facial features [11]. They can also generate synthetic behavioral data, like driving patterns, to enhance the accuracy of behavioral biometrics-based authentication. Furthermore, adversarial training, which involves training Intrusion Detection Systems (IDSs) with adversarial examples generated by GANs, makes these systems more resilient to sophisticated attacks that attempt to evade detection [12]. Overall, integrating generative AI into V2X security frameworks promises a substantial improvement in safeguarding these critical communication networks. Our main contributions can be summarized as
- We propose a novel real-time anomaly detection framework that leverages a sliding window mechanism in combination with a VAE integrated with a CNN architecture, resulting in a lightweight and robust model.
- The performance of the proposed model is rigorously evaluated using a custom Basic Safety Message dataset, where various anomalies were systematically injected to simulate real-world scenarios.
The remainder of this paper is organized as follows. Section 2 presents a review of related work in the field of V2X communication security, with a focus on generative models for anomaly detection. Section 3 provides details of the proposed method, which involves integrating CNNs with VAEs to enhance anomaly detection in V2X systems. Section 4 outlines the experimental setup, discusses the results, and evaluates the effectiveness of our proposed model in detecting various types of anomalies. Finally, Section 5 concludes the paper by summarizing the key findings and suggesting potential directions for future research.
2. Related Work
This section reviews recent advancements in anomaly detection for V2X communication, with a focus on generative models. It highlights key approaches, their limitations, and the motivations for our proposed method. Additionally, this section outlines the key considerations of our study and highlights the novelty of our proposed solution.
2.1. Key Considerations
The following were the key considerations for our study:
- Inference time: We considered the importance of low-latency processing to meet real-time detection requirements in V2X environments.
- Detection accuracy: We focused on designing a model capable of identifying anomalies without relying on labeled attack data.
- Unsupervised problem: The solution was developed under an unsupervised setting to ensure practicality, given the difficulty of obtaining labeled anomalies in real-world V2X data.
- Deployability: We aimed for lightweight and modular architecture that is suitable for deployment on resource-constrained devices, such as OBUs and RSUs.
2.2. Recent Studies on Anomaly Detection in V2X Communications
The increasing reliance on V2X communication has led to significant research efforts aimed at enhancing its security. Generative AI and, more broadly, machine learning models have emerged as promising tools for anomaly detection, capable of identifying unusual patterns indicating cyber threats or system malfunctions. These models can learn from vast amounts of data to detect and predict anomalies with high accuracy [13].
One notable approach is the use of GANs for anomaly detection by Devika et al. [14], who present an unsupervised anomaly detection framework optimized for Connected and Autonomous Vehicles (CAVs). The model utilizes LSTM, RNN, and GRU architectures to identify anomalies in vehicle dynamics, including position, speed, acceleration, and heading. Although effective, GANs require complex training and are prone to instability, making them less suitable for real-time deployment in resource-constrained vehicular environments. Conversely, Huang et al. [15] propose a framework, addressing the challenge of deploying resource-intensive deep learning models on constrained devices like Roadside Units (RSUs) and On-Board Units (OBUs). The authors combine unsupervised learning with autoencoders and knowledge distillation to create a lightweight yet effective anomaly detection system, introducing a Feature-based Knowledge Distillation (FKD) method that enhances traditional techniques by transferring knowledge across multiple network layers.
VAEs have emerged as an alternative due to their ability to learn probabilistic representations of normal behavior. Unlike GANs, VAEs offer a structured latent space, allowing for the detection of anomalies based on reconstruction errors. VAEs are based on an autoencoder, a concept widely recognized in the anomaly detection literature. Khanmohammadi et al. [16] developed a D-CNN-LSTM Autoencoder for time-series anomaly detection in CAVs, emphasizing data preprocessing techniques like Differencing (DIFF) and Moving Standard Deviation (MSD) to enhance detection performance. Their work highlights the efficacy of combining CNNs for spatial feature extraction and LSTMs for temporal dependencies within an autoencoder framework. While their focus on preprocessing is notable, their use of a standard autoencoder differs from our proposed VAE, which incorporates a probabilistic latent space to offer better generalization and handling of data uncertainty, potentially.
Al-Yarimi et al. [17] demonstrated the effectiveness of VAEs in Vehicular Ad-hoc Networks (VANETs), particularly when combined with multi-objective optimization strategies to improve detection performance. The framework mentioned employed algorithms such as AGE-MOEA and R-NSGA-III to optimize multiple objectives, including divergence, Kullback–Leibler (KL) divergence, and reconstruction error. Additionally, hybrid models that integrate VAEs and GANs have been explored, such as CoGAN [18], which leveraged the strengths of both architectures to enhance anomaly detection in Cellular Vehicle-to-Everything (C-V2X) communication.
An approach worth mentioning involves detecting and correcting errors in BSMs to improve V2X security. A study by Qian et al. [19] proposes a collaborative scheme in which vehicles, RSUs, and Data Centers work together to identify and correct erroneous BSMs caused by sensor failures. By leveraging historical data and statistical analysis, the system effectively improves message accuracy. However, while this method enhances data integrity, it does not explicitly address cyber threats, which require real-time anomaly detection capabilities.
Other machine learning techniques, including Support Vector Machines (SVMs) and ensemble learning, are also being investigated for V2X anomaly detection. For instance, Venkatasamy et al. [20] propose an ML-based Cryptographic Protocol IDS (ML-CPIDS) that integrates ML with cryptographic methods for authentication, encryption, and threat detection. This approach underscores the importance of a layered defense but differs from our focus on detecting semantic anomalies in potentially already authenticated message content. Moreover, the broader context of V2X security highlights unique challenges, including the dynamic nature of vehicular networks, the need for real-time detection, scalability, and adaptability [21]. Lightweight ML solutions play a critical role in a robust, adaptive, and secure vehicular network against emerging threats [22]. Challenges such as data privacy, computational constraints on OBUs/RSUs, and the need for interpretable models are also widely acknowledged.
2.3. The Novelty of This Study
While previous studies have contributed valuable techniques for error correction and anomaly detection, many existing approaches either lack real-time processing capabilities or require extensive computational resources. In contrast, our work integrates a VAE with CNNs to enhance feature extraction and improve detection accuracy while maintaining low-latency inference. By employing a sliding window mechanism, our approach ensures timely anomaly detection in dynamic V2X environments.
What sets our study apart is the combination of three design principles: (1) an unsupervised learning approach that eliminates the dependency on labeled attack data, making it suitable for real-world deployment; (2) a lightweight architecture specifically engineered for execution on constrained V2X hardware such as OBUs and RSUs; and (3) a periodic retraining strategy that adapts the model to evolving traffic and environmental patterns while mitigating catastrophic forgetting through selective inclusion of historical data. Together, these contributions result in a scalable, robust, and adaptable solution for securing V2X communications against both known and emerging threats.
3. Proposed Methodology
This section outlines the proposed method for real-time anomaly detection in V2X communication systems. Starting with the attack model, we will detail the proposed VAE-based anomaly detection model.
3.1. Attack Model
To contextualize the anomaly detection framework, we define the threat landscape and attacker capabilities as follows:
- Attacker Access and Capabilities: We assume an attacker who has gained the ability to inject or manipulate BSMs within the V2X communication channel. This could be achieved through various means, such as compromising an OBU of a vehicle or an RSU by employing a rogue device capable of broadcasting V2X messages that mimic legitimate ones. An attacker can also exploit vulnerabilities in the V2X communication stack to alter messages in transit, e.g., a man-in-the-middle [23] scenario. The attacker is assumed to be familiar with the BSM format and content, but not necessarily with the internal parameters of the deployed anomaly detection system. Their goal is to introduce false information regarding a vehicle’s state (position, speed, acceleration) to disrupt V2X applications, potentially leading to unsafe conditions or reduced traffic efficiency.
- Resources Used by Attacker: An attacker might utilize software-defined radios (SDRs) [24] or custom-programmed V2X communication modules to craft and transmit anomalous BSMs. For attacks involving compromised OBUs/RSUs, the attacker leverages the existing communication hardware of the compromised unit. The injected anomalies, as simulated in our experiments in Section 4.2, such as constant offsets or targeted vehicle data falsification, represent attempts to broadcast deceptive kinematic information.
Our framework primarily focuses on detecting anomalies that are indicative of malicious, intelligently crafted attacks aimed at falsifying BSM data. However, the underlying principle of learning normal data patterns and identifying deviations means the system is also capable of flagging anomalies caused by severe sensor malfunctions or significant signal degradation, provided these events cause the BSM data to deviate from the learned norm significantly. The types of anomalies injected in our experiments could manifest from either a sophisticated attack or a critical sensor failure.
3.2. Real-Time Anomaly Detection Model
The method leverages a lightweight VAE architecture integrated with CNNs. Our model is designed to be deployable on board the vehicle, and on an RSU, given its lightweight nature. The model is designed to detect anomalies in real-time using a sliding window mechanism, as shown in Figure 1 below. This approach ensures that incoming data streams are processed incrementally, enabling low-latency anomaly detection in dynamic V2X environments.
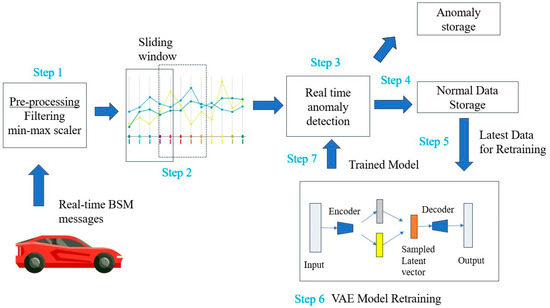
Figure 1.
Proposed Real-time Anomaly Detection Methodology.
A sliding window of size 4 with a stride of 1 is used to preprocess the time-series BSM data. Each window captures a short temporal sequence of vehicle features, allowing the model to learn temporal dependencies and detect anomalies at each time step. The window size of 4 was chosen empirically to capture sufficient temporal context from the BSM data, allowing the VAE-CNN to model short-term vehicle dynamics effectively without imposing excessive computational load per window. The stride of 1 ensures that every new incoming data point contributes to an immediate re-evaluation of the vehicle’s state, which is critical for the ‘prompt detection’ mentioned in the abstract. Each window, thus formed as a short temporal sequence of multivariate data points (position, speed, acceleration), is then fed as a single input sample to the VAE-CNN architecture. The model’s objective is to reconstruct this entire input window, and the magnitude of the reconstruction error [25] across the window serves as the basis for identifying anomalous patterns. The reconstruction error (RE) is defined as the Mean Squared Error:
where N is the total number of elements in the input window, anomalies are flagged when the reconstruction error exceeds a predefined threshold. The threshold is calibrated during validation to strike a balance between false positives and false negatives. This ensures that the model reliably detects anomalies while minimizing unnecessary alerts.
Our proposed method ensures the model adapts to evolving traffic patterns, weather conditions, and environmental changes through a periodic retraining strategy. This also enables the model to detect anomalies effectively despite shifts in data distribution. V2X communication operates in highly dynamic environments where the underlying data distribution can change. Previously normal behaviors, such as specific vehicle dynamics, may become anomalous as the environment changes. The model may fail to adapt to these changes without retraining, leading to degraded performance.
To retrain the model, recent BSM data is aggregated over fixed intervals (e.g., 30 min) to capture the latest traffic and environmental patterns while retaining historical knowledge. The model is then incrementally trained using recent and a small subset of historical data, balancing adaptability with the retention of long-term patterns. The dataset is preprocessed during retraining using the same sliding window approach as in the initial training phase. Following retraining, the anomaly detection threshold is recalibrated based on the reconstruction error distribution of the updated training dataset, ensuring sensitivity to anomalies under evolving data distributions. The rate of data distribution changes determines the retraining frequency; for highly dynamic environments, retraining can be frequent, while in less dynamic scenarios, intervals can be extended to reduce computational overhead. This means that during periods of significant change in traffic patterns, the retraining frequency would be adjusted. This adjustment can be triggered by actively monitoring data drift metrics or a noticeable decline in the model’s anomaly detection performance on a continuous validation set, ensuring the model remains adaptive rather than strictly adhering to a universally fixed interval under all circumstances.
A potential concern with periodic retraining on new data is the phenomenon of catastrophic forgetting. [26], where the model might lose its ability to accurately represent previously learned patterns. Our retraining strategy aims to mitigate this by not solely relying on recent data. As stated, the model is incrementally trained using recent and a small subset of historical data, balancing adaptability with the retention of long-term patterns. This inclusion of historical data helps to regularize the training process, anchoring the model to established normal behaviors while allowing it to adapt to evolving traffic dynamics and environmental conditions. While dedicated continual learning techniques could be explored in future work, this approach provides a practical balance for maintaining long-term reliability.
Our proposed anomaly detection methodology consists of seven steps, as depicted in Figure 1, which are further elaborated below.
- Step 1: Incoming messages are filtered in the preprocessing stage to retain only the essential features (position, speed, and acceleration), then normalized to the range [0, 1] using MinMaxScaler. This normalization process helps stabilize training and enhances model performance [27].
- Step 2: A sliding window approach is used to generate overlapping time-series windows [28], with each window containing four consecutive data points and a stride of one. This approach effectively enables the model to capture temporal dependencies within the data.
- Steps 3–6: The model analyzes each sliding window in real-time to determine whether it is anomalous or normal. If a window is classified as anomalous, an alarm is triggered, and the corresponding data is sent to an anomaly storage unit for further investigation. On the other hand, if the window is deemed normal, it is aggregated into a separate storage unit for normal data, which contributes to the dataset for periodic model retraining. The model retraining stage is executed at determined intervals to ensure the model remains updated with evolving data distributions. During retraining, the dataset is preprocessed using the same sliding window approach.
- Step 7: Following retraining and recalibration of the anomaly detection threshold, the updated model is deployed for continued real-time anomaly detection.
The proposed anomaly detection model leverages a lightweight VAE [29] integrated with CNNs as shown in Figure 2 below. The architecture enables the model to capture both temporal and spatial [30] dependencies in BSMs for V2X communication. Moreover, the architecture is designed to provide efficient and scalable anomaly detection, with a focus on real-time performance.
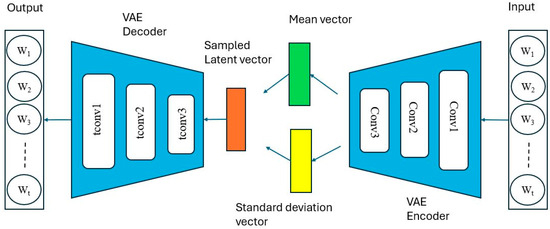
Figure 2.
Our VAE Architecture.
The encoder compresses the input data into a latent space representation. It consists of a sequence of convolutional layers for hierarchical feature extraction, batch normalization for stable training, and Leaky ReLU [31] activation functions for computational efficiency. The encoder extracts high-level features while retaining temporal dependencies critical for detecting subtle anomalies in V2X data. After the convolutional layers, the latent space is represented by two vectors, the mean () and the log variance (log ), which are used for sampling the latent vector via the reparameterization approach. This step ensures smooth latent space representations, allowing for gradient-based optimization.
The latent space is a compact representation of the input data. The μ and log are optimized during training to learn a robust distribution of standard BSM patterns. The latent vector is sampled using
where and . This step ensures the model learns probabilistic representations of normal behavior, making it sensitive to deviations. The decoder reconstructs the input data from the latent vector. It consists of transposed convolutional layers to upsample the latent representation back to its original dimensions. The decoder reconstructs normal BSM patterns and evaluates the reconstruction quality to identify anomalies. A sigmoid activation function is applied at the output layer to constrain the reconstructed data within the normalized range of [0, 1]. The model utilizes the Kullback-Leibler (KL) Divergence term to regularize the latent distribution towards a standard Gaussian, while the Mean Squared Error is used for the reconstruction loss. The total loss combines these components using a configurable parameter (beta), balancing between accurate reconstruction and latent space regularization [32].
4. Experimental Setup and Results
In this section, we discuss the experimental setup and procedures employed to evaluate the effectiveness of our proposed VAE-based real-time anomaly detection framework. Additionally, we present the results of our experiments, highlighting the model’s performance in detecting various types of anomalies in V2X communications under realistic conditions.
4.1. Dataset Collection and Experiment Setup
To evaluate our proposed model for V2X communication security, we first utilized a simulation environment created using the Simulation of Urban Mobility (SUMO) tool to generate the normal dataset. SUMO [33] is a widely recognized, open-source traffic simulation suite designed to model large road networks and generate realistic vehicle movement patterns. It provides a detailed, microscopic simulation of individual vehicle behaviors, making it well-suited for research on V2X communication.
The road network for a selected region of Gangnam, Seoul, was obtained from OpenStreetMap (OSM) data and converted into a SUMO-compatible format using the NETCONVERT tool. Initial traffic demand, resulting in over 680 unique vehicles during the 1000 s simulation period, was generated using SUMO’s capabilities for creating trips based on the imported OSM network. Parameters such as ‘Through Traffic Factor’ set to 5 for cars and vehicle ‘Count’ set to 12 for initial car departures were used to influence the trip generation process, aiming to simulate typical urban traffic flow and density variations. The simulation included a default mix of passenger car vehicle types.
The primary data collector vehicle, , was manually assigned a specific, recurring route within the selected map area using SUMO’s NETEDIT tool. This ensured remained active and collected data consistently throughout the simulation period within the boundaries of the Gangnam district map. While this simulation utilized a single collector vehicle () to systematically gather BSM data for evaluating the proposed anomaly detection model, the framework itself is designed to process incoming BSM streams. As such, it can be deployed on individual vehicles that process data received from their peers or on RSUs that aggregate data from multiple vehicles in the vicinity.
The SUMO simulation initially produced Floating Car Data (FCD) [34] for all vehicles active in the scenario. The FCD output included Vehicle ID, X and Y positions, Vehicle type, Speed, Position on the lane, Heading angle, and Acceleration parameters for each vehicle. To simulate the BSM collection process by , a post-processing step was implemented. This involved filtering the comprehensive FCD output: for each 0.1 s time step, only data from vehicles located within the 500 m [35] communication range of ’s current position was retained. For our simulation, this 500 m value was used to define the data collection radius for , with the understanding that the anomaly detection itself processes the content of successfully received messages. From this subset, only the essential BSM attributes—X and Y positions, Speed, and Acceleration—were extracted to form the raw dataset for our anomaly detection model.
After filtering, the dataset was divided into training and testing sets. The data was split, with 90% allocated for training the model and the remaining 10% reserved for testing. To evaluate the model’s capability in detecting anomalies, the test set was manually injected with various types of anomalies to simulate potential security threats and data abnormalities in V2X communications [7].
The experiments were conducted on Google Colab, utilizing its free GPU resources to ensure computational efficiency. The proposed VAE with CNN layers was implemented using the PyTorch 2.x framework on Google Colab [36], leveraging its NVIDIA Tesla T4 GPU with 16 GB of VRAM to ensure efficient computation and training. The training data consisted of a simulated Basic Safety Message dataset generated using the SUMO tool and preprocessed as described in Section 3.2, Steps 1 and 2.
A set of carefully chosen hyperparameters was used to balance training stability and detection performance during model training. The learning rate was set to 0.001 and optimized using the Adam optimizer with a weight decay of 10−3 to avoid overfitting [37]. The loss function was a combination of reconstruction loss (Mean Squared Error) and KL divergence, designed to encourage accurate reconstruction of normal data while regularizing the latent space. The model was trained with a batch size of 32 for 100 epochs to ensure convergence. An early stopping mechanism was incorporated to prevent overfitting, where training was stopped if the validation loss showed no improvement for 20 consecutive epochs. These parameters were selected after repeated experimentation to optimize the trade-off between training efficiency and anomaly detection accuracy, making the model suitable for real-time V2X applications.
4.2. Anomaly Injection and Evaluation Metrics
To evaluate the anomaly detection performance of our proposed model, we introduced synthetic anomalies into the test data using a controlled injection method. The first type of anomaly is the Constant Offset Injection, where anomalies are injected by applying a constant offset [38] to select features (speed, acceleration, and position of the test dataset. The offset magnitude was scaled using a parameterized factor relative to the feature’s maximum value. The second type of anomaly was introduced by applying a constant offset to randomly selected vehicles of specific features (speed, acceleration, and position (x, y)). We injected the offset to a target vehicle to demonstrate an attacker in the V2X communications or a compromised vehicle sending false messages.
To simulate a constant offset, an attack factor ranging from 0.1 to 2 with a step size of 0.1 was used to introduce varying levels of abnormality, representing mild, moderate, and extreme deviations from normal behavior. To focus on the anomalies within specific regions of the dataset, a subset of the test data (the middle 30% of records) was selected for modification. This ensured anomalies were localized and mimicked real-world scenarios where errors or attacks may occur in bursts. The method was independently applied to different features, speed, and position (x, y). For example, the offset value added to the speed column was determined as follows.
where is the maximum value in the speed column of the dataset. We also simulated random offset, as mentioned above, with the same type of scaling factor relative to the feature’s maximum value. The injection was applied to various features to simulate diverse types of message errors, speed (simulating speed sensor malfunctions with abrupt, random deviations), and position (x, y) (mimicking GPS or localization errors with random positional shifts). Finally, a binary anomaly label was generated, where normal samples were marked as 0 and injected anomalies as 1.
The proposed model’s performance in detecting anomalies in V2X communications was evaluated using several standard metrics and additional performance indicators. These metrics assess the detection accuracy and the model’s ability to generalize and operate efficiently in real-time scenarios. The F1 score is particularly useful in scenarios where false positives and false negatives have significant consequences.
- Precision (P): Precision measures the proportion of correctly identified anomalies among all the instances flagged as anomalies by the model. It is defined as
- Recall (R): Recall measures the model’s ability to accurately identify all actual anomalies. It is defined as
- F1-Score: The F1-score provides a harmonic mean of precision and recall, offering a single measure that balances the trade-off between these two metrics. It is calculated as
- Accuracy (A): Accuracy is a measure of the proportion of correct predictions (both positive and negative) made by the model out of the total number of predictions. It is mathematically defined as
We determined the anomaly detection threshold by computing the 98th percentile of the reconstruction errors obtained from the training data. This approach ensures that 98% of the normal instances are correctly classified as non-anomalous, thereby focusing on maximizing recall, which is crucial in anomaly detection tasks. High recall is significant as it minimizes the risk of missing anomalies, which could have considerable consequences in real-time applications.
4.3. Performance Evaluation
We compared our VAE architecture with both a standard autoencoder and a VAE combined with LSTM layers. Autoencoders are simpler models that focus on reconstructing input data. Still, they lack the probabilistic framework of VAEs, which enables them to model uncertainty and better handle variations in the data. We chose to include LSTM layers because they are well-suited for capturing temporal dependencies in sequential data, which is helpful for effective anomaly detection. This choice aligns with findings from other studies that highlight LSTMs as a substantial addition to generative models, such as VAEs and GANs, for this purpose.
The performance of our proposed anomaly detection model was more specifically evaluated across four distinct anomaly types: constant or vehicle-targeted offsets in both position and speed. The evaluation focused on key metrics, including precision, recall, F1-score, accuracy, the minimum high-value factor required to achieve satisfactory anomaly detection, and average inference time. Table 1 highlights the superiority of the proposed VAE model over the other architectures in detecting anomalies effectively, especially in challenging scenarios. For instance, the model achieves near-perfect recall of 0.9998 for the Constant Position Offset, indicating its ability to capture nearly all anomalies of this type. In comparison, the traditional autoencoder generally performs worse than the proposed VAE model across all key metrics, especially for more complex anomalies, such as the Constant Speed Offset and Vehicle Speed Offset, the autoencoder’s recall and precision drop significantly. Despite its lower detection performance, the autoencoder achieves a slightly lower average inference time of around 0.0010–0.0012 s. Still, this marginal gain in speed comes at a significant cost to detection accuracy and reliability.

Table 1.
Performance Results of Our VAE Real-time Anomaly Detection Model compared to Traditional Autoencoder and VAE model with LSTM layers.
The VAE with LSTM layers exhibits mixed performance, performing well in simpler anomalies but struggling with more complex ones. For anomalies like Constant Position Offset, it achieves comparable results to the proposed VAE. However, for anomalies such as Vehicle Position Offset and Vehicle Speed Offset, its performance deteriorates significantly. For the Vehicle Position Offset, the precision drops to 0.1679, and the F1-score is only 0.2758, indicating poor anomaly detection capabilities for this type of anomaly. Additionally, the average inference time of the LSTM-based model is higher, ranging from 0.0029 to 0.0034 s, which could impact its usability for real-time applications. The proposed VAE model shows an optimal balance between high detection performance and low computational cost, making it the most effective and efficient choice for real-time anomaly detection in V2X communication systems. Its robust performance across diverse anomaly types and low inference time ensures its applicability in safety-critical environments.
To evaluate the real-time performance of the proposed VAE-based anomaly detection model, test data was streamed row by row with a simulated time interval, mimicking real-world scenarios where data arrives incrementally. A MinMaxScaler was fitted on the training data to normalize the features of incoming test data. A fixed-size sliding window of size four was employed to capture temporal dependencies in the data. The sliding window buffer updates incrementally with each new row, maintaining a continuous flow of recent observations for analysis. The reconstruction error is computed and classified as normal or anomalous for each complete window in real time.
The inference time was measured for each sliding window prediction to validate the proposed anomaly detection model’s real-time capabilities. The inference time is defined as the duration between the input of a complete sliding window into the trained VAE model and the computation of the reconstruction error. For each complete sliding window, the time taken for the model to generate a reconstruction and compute the reconstruction error was recorded. The average inference time was calculated over all sliding window predictions during the test. In the dataset used for evaluation, the number of vehicles present at a single time step ranged from 1 to 30. To ensure the framework could handle the upper limit of this range, performance metrics were calculated assuming 30 rows (representing data from 30 vehicles) per time step.
With a sliding window size of 4 and a stride of 1, each batch of 30 rows was processed sequentially, generating overlapping windows per batch. The highest average inference time per sliding window was measured as 0.0013 s. Given the 0.1 s interval between consecutive batches, the total time required to process all 27 windows within a batch was calculated as 0.0351 s based on the Equation (8) below.
This is significantly less than the available 0.1 s interval, demonstrating that the system can reliably process incoming data in real-time. Moreover, the training process was computationally efficient, requiring an average of only 5 min to complete on the given training dataset, which consisted of data collected over 800 s. The resulting trained model is also compact, saving the model’s state dictionary results in a file size of approximately 0.02 megabytes. These characteristics—fast inference, efficient training, and small model size—collectively support the ‘lightweight’ designation of the proposed framework, making it suitable for deployment on typical V2X hardware, such as OBUs and RSUs.
Figure 3 and Figure 4 illustrate the distribution of reconstruction errors for normal and anomalous data across different anomaly types. The histograms separate the reconstruction error values of normal and anomalous samples, with the detection threshold indicated by a red dashed line at the 98th percentile. These distributions show the effectiveness of the VAE model in distinguishing between normal and anomalous behavior based on reconstruction error. In both figures, the left-side histograms represent the reconstruction errors of normal data, while the right-side histograms represent the reconstruction errors of anomalous data.
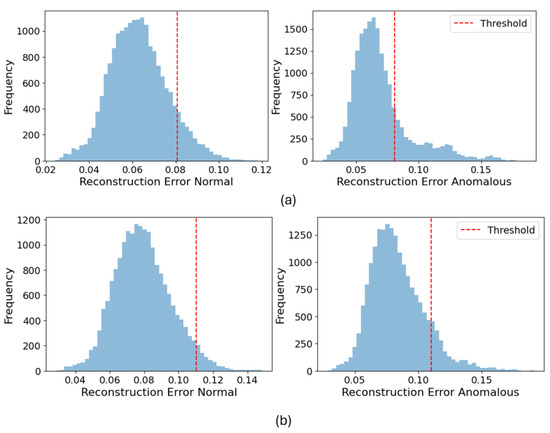
Figure 3.
Reconstruction error distribution comparison between (a) our VAE and (b) the VAE with LSTM layers for vehicle targeted position offset.
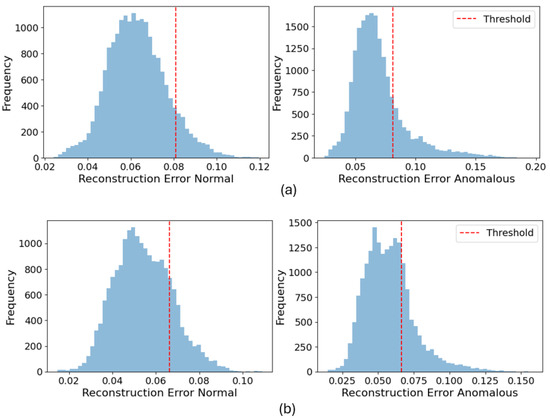
Figure 4.
Reconstruction error distribution comparison between (a) our VAE and (b) the autoencoder for vehicle targeted speed offset.
In Figure 3, a comparison of the performance of our proposed VAE model and the VAE with LSTM layers is shown. For our VAE model, the reconstruction error distribution for normal data is tightly clustered below the threshold, with very few false positives. However, the reconstruction error for anomalous data is well-separated, with most anomalous samples exceeding the threshold. This clear distinction between normal and anomalous reconstruction errors demonstrates the model’s strong ability to effectively differentiate anomalies from normal behavior.
In contrast, the VAE with LSTM layers struggles to achieve the same level of separation. A significant portion of anomalous samples fall below the threshold, resulting in a higher false negative rate. Furthermore, the reconstruction error for normal data is more spread out, leading to a slightly higher false positive rate. These results indicate that while the VAE with LSTM layers can detect some anomalies, it is less effective than our VAE, especially for vehicle-targeted position offset anomalies.
Figure 4 illustrates the reconstruction error distributions for vehicle-targeted speed offset anomalies, comparing our VAE model with a traditional autoencoder. The VAE model shows a well-defined separation between normal and anomalous reconstruction errors. The normal data exhibits a narrow distribution concentrated below the threshold, with minimal overlap with the anomalous distribution. The reconstruction errors of the anomalous data are significantly higher than those of the normal data, ensuring a low false negative rate and robust anomaly detection for speed offset anomalies.
The traditional autoencoder, on the other hand, exhibits a much less distinct separation. The reconstruction error distribution for anomalous data overlaps with the normal data, resulting in a higher rate of both false positives and false negatives. The threshold fails to effectively separate the two distributions, showing the limitations of the autoencoder in detecting vehicle-targeted speed offset anomalies. These findings further highlight the superior capability of our VAE model in distinguishing anomalies with greater precision and reliability.
5. Discussion
The experimental results presented in Section 4 demonstrate the efficacy of the proposed VAE-CNN framework for real-time anomaly detection in V2X BSM data. This section discusses the interpretation of these results, the implications for V2X security, the limitations of the current study, and directions for future research.
5.1. Interpretation of Results and the Implications for V2X Security
Our proposed VAE-CNN model consistently outperformed both a traditional autoencoder and a VAE-LSTM architecture, particularly in detecting complex anomalies such as vehicle speed and position offsets. The superiority of the VAE-CNN can be attributed to several factors. Firstly, the integration of CNN layers enables effective hierarchical feature extraction from the windowed time-series BSM data, capturing localized patterns and spatial relationships within the sequence of observations within a window. Secondly, the VAE component, with its probabilistic encoder and decoder, learns a robust representation of the normal data distribution. This probabilistic approach, regularized by the KL divergence term, enables the model to generalize more effectively and identify subtle deviations that a deterministic autoencoder might overlook. The VAE-LSTM, while theoretically capable of capturing temporal dependencies, exhibited higher inference times and struggled with certain complex vehicle-targeted anomalies. This suggests that for the specific BSM anomaly detection task with short window sizes, the feature extraction capabilities of the CNN, combined with the VAE’s reconstruction fidelity, offer a more efficient and effective solution.
The very low average inference time of approximately 0.0013 s per sliding window, as shown in Equation (8), is a critical finding that underscores the model’s suitability for real-time deployment in latency-sensitive V2X applications. This efficiency, coupled with a training time of around 5 min on the specified hardware, confirms the “lightweight” nature of the framework, making it viable for implementation on resource-constrained OBUs or RSUs. The sliding window mechanism is instrumental in this real-time capability, ensuring prompt processing of incoming BSMs.
The reconstruction error distributions in Figure 3 and Figure 4 visually affirm the model’s discriminative power. Our VAE-CNN demonstrated a more precise separation between the reconstruction errors of normal and anomalous samples compared to the VAE-LSTM and traditional autoencoder, particularly for vehicle-targeted offsets. This clear distinction is crucial for setting an effective detection threshold that balances high recall with acceptable precision, as targeted by our 98th percentile thresholding strategy.
The high performance achieved by our model indicates its potential to enhance the security of V2X communication significantly. By accurately detecting falsified BSMs in real-time, the system can help prevent the propagation of misleading information that could lead to incorrect decisions by vehicle safety applications or traffic management systems. The framework’s design for adaptability through periodic retraining is also vital for long-term reliability in dynamic V2X environments, where normal traffic patterns can evolve due to various factors, such as time of day, weather, or road construction. The inclusion of a subset of historical data during retraining aims to mitigate catastrophic forgetting, allowing the model to adapt without losing previously learned knowledge of normal patterns.
5.2. Limitations of Our Model
While the results are promising, several limitations should be acknowledged. Firstly, the dataset was generated using SUMO for a specific urban environment (Gangnam, Seoul); although realistic, real-world V2X data can exhibit greater diversity and noise, and the synthetically injected anomalies might differ from actual attack signatures. Secondly, the study focused on anomalies in fundamental BSM kinematics, meaning that more sophisticated attacks, such as Sybil attacks, advanced DoS, or ‘ghost vehicle’ generation [39], might require analysis of additional message fields or data correlation. Furthermore, while the concept of adaptive retraining was proposed, its effectiveness under dynamically evolving data distributions was not experimentally validated in this work due to dataset limitations, and the optimal triggers for retraining warrant further investigation. Lastly, the defined attack model covers common data falsification; however, highly sophisticated attackers with a deep understanding of the detection system might devise strategies to evade it.
5.3. Future Research Direction
Building upon the current findings and addressing these limitations, future research will explore several key areas. A primary focus will be to extend the methodology to detect a broader spectrum of anomalies and more sophisticated attack scenarios, such as ‘ghost vehicle’ creation or advanced DoS attacks, which will involve incorporating additional BSM parameters and potentially fusing data from other V2X message types (CAMs, DENMs) [40] or even V2N messages relevant to applications like teleoperated driving. Crucially, the adaptive retraining mechanism requires rigorous experimental validation using datasets that feature evolving data distributions to quantify its benefits and determine optimal strategies. In conjunction, we plan to investigate advanced continual learning techniques to mitigate catastrophic forgetting during these retraining cycles more effectively. Validation on larger-scale, diverse real-world V2X datasets, collected from different geographical locations and under various data aggregation scenarios, such as distributed detection by multiple agents, is also a priority. Furthermore, we intend to explore the model’s scalability and performance when deployed on actual OBU/RSU hardware to assess its practical efficiency and resource utilization. Finally, the attack model will be further refined to include more sophisticated adversarial strategies, and the model’s robustness against such advanced threats will be evaluated, potentially incorporating adversarial retraining techniques. Addressing these directions will further enhance the reliability and applicability of VAE-based anomaly detection for securing V2X communications.
6. Conclusions
This study successfully developed and validated a real-time anomaly detection framework for V2X communications, centered on a lightweight VAE-CNN architecture complemented by a sliding window mechanism for processing streaming BSM data. The core innovation lies in the synergistic integration of the VAE’s probabilistic modeling for robust normality learning and the CNN’s capacity for effective feature extraction from sequential vehicular data. Our comprehensive experimental evaluation rigorously demonstrated the framework’s ability to achieve high-performance anomaly detection across a range of challenging attack simulations, consistently outperforming comparable autoencoder-based approaches. Remarkably, the system exhibited outstanding low inference times and efficient training, confirming its viability for real-time deployment on resource-constrained V2X hardware such as OBUs and RSUs. Ultimately, the demonstrated combination of robust detection accuracy, operational efficiency, and adaptability positions this VAE-CNN framework as a significant and practical contribution towards enhancing the security and trustworthiness of V2X communications. By offering a reliable means to identify and mitigate data falsification attacks, this work paves the way for safer and more dependable intelligent transportation systems.
Author Contributions
Conceptualization, Y.T.G.; methodology, Y.T.G., software, Y.T.G. and S.R.J.; validation, Y.T.G., S.R.J., S.G. and J.H.P.; formal analysis, S.G. and S.R.J.; investigation, Y.T.G. and S.G.; resources, J.H.P.; data curation, S.G.; writing—original draft preparation, Y.T.G. and S.R.J.; writing—review and editing, Y.T.G. and S.R.J.; visualization, S.G.; supervision, J.H.P.; project administration, J.H.P.; funding acquisition: J.H.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Strategic Networking & Development Program funded by the Ministry of Science and ICT through the National Research Foundation of Korea (RS-2023-00267476).
Institutional Review Board Statement
Not applicable.
Data Availability Statement
Our code is available at https://github.com/yonishat/my-repository/blob/main/VAE_Based_Real_Time_Anomaly_Detection_Approach_for_En_hanced_V2X_Communication_Security.ipynb (accessed on 10 February 2025).
Conflicts of Interest
The authors declare that they have no competing interests.
Abbreviations
The following abbreviations are used in this manuscript:
| VAE | Variational Autoencoder |
| LSTM | Long Short-Term Memory |
| CNN | Convolutional Neural Network |
| V2X | Vehicle-to-Everything |
| ITS | Intelligent Transportation Systems |
| GAN | Generative Adversarial Network |
| RSU | Roadside Unit |
| OBU | On-Board Unit |
| KL | Kullback–Leibler |
| SUMO | Simulation of Urban Mobility |
References
- Yogarayan, S.; Razak, S.F.A.; Azman, A.; Mohd, F.A. Abdullah, Vehicle to Everything (V2X) Communications technology for Smart Mobility in Malaysia: A comprehensive Review. J. Southwest Jiaotong Univ. 2021, 56, 534–563. [Google Scholar] [CrossRef]
- Dokur, O.; Katkoori, S. Three Connected V2V Applications Based on DSRC Basic Safety Messages. In Proceedings of the ICCVE 2022—IEEE International Conference on Connected Vehicles and Expo, Lakeland, FL, USA, 7–9 March 2022. [Google Scholar] [CrossRef]
- El Azzaoui, A.; Jeremiah, S.R.; Xiong, N.N.; Park, J.H. A digital twin-based edge intelligence framework for decentralized decision in IoV system. Inf. Sci. 2023, 649, 119595. [Google Scholar] [CrossRef]
- Sandeep, Y.; Venugopal, P. In-depth evaluation of security requirements and attacks for secure data communication in ITS. AIP Conf. Proc. 2024, 2966, 030002. [Google Scholar] [CrossRef]
- Enrique, O.; Castro, L.; Deng, X.; Park, J.H. Comprehensive Survey on AI-Based Technologies for Enhancing IoT Privacy and Security: Trends, Challenges, and Solutions. Hum.-Centric Comput. Inf. Sci. 2023, 13, 39. [Google Scholar] [CrossRef]
- Ha, N.B.; Jeong, Y.S. Fusion of Digital Twin and Blockchain for Secure and Efficient IoV Networks. Hum.-Centric Comput. Inf. Sci. 2024, 14, 1–17. [Google Scholar] [CrossRef]
- Gularte, K.H.M.; Vargas, J.A.R.; da Costa, J.P.J.; Da Silva, A.A.S.; Santos, G.A.; Wang, Y.; Müller, C.A.; Lipps, C.; Júnior, R.T.d.S.; Filho, W.d.B.V.; et al. Safeguarding the V2X Pathways: Exploring the Cybersecurity Landscape Through Systematic Review. IEEE Access 2024, 12, 72871–72895. [Google Scholar] [CrossRef]
- Zhang, R.; Xiong, K.; Du, H.; Niyato, D.; Kang, J.; Shen, X.; Poor, H.V. Generative AI-enabled Vehicular Networks: Fundamentals, Framework, and Case Study. IEEE Netw. 2024, 38, 259–267. [Google Scholar] [CrossRef]
- Pinto, A.; Herrera, L.C.; Donoso, Y.; Gutierrez, J.A. Enhancing Critical Infrastructure Security: Unsupervised Learning Approaches for Anomaly Detection. Int. J. Comput. Intell. Syst. 2024, 17, 236. [Google Scholar] [CrossRef]
- Bauer, L.A.; Bindschaedler, V. Generative Models for Security: Attacks, Defenses, and Opportunities. 2021. Available online: https://arxiv.org/abs/2107.10139v2 (accessed on 16 July 2024).
- Jeremiah, S.R.; Ha, J.; Singh, S.K.; Park, J.H. PrivacyGuard: Collaborative Edge-Cloud Computing Architecture for Attribute-Preserving Face Anonymization in CCTV Networks. Hum.-Centric Comput. Inf. Sci. 2024, 14, 43. [Google Scholar] [CrossRef]
- Chaitou, H.; Robert, T.; Leneutre, J.; Pautet, L. Intrinsic Weaknesses of IDSs to Malicious Adversarial Attacks and Their Mitigation. Commun. Comput. Inf. Sci. 2023, 1849, 122–155. [Google Scholar] [CrossRef]
- Halvorsen, J.; Izurieta, C.; Cai, H.; Gebremedhin, A. Applying Generative Machine Learning to Intrusion Detection: A Systematic Mapping Study and Review. CM Comput. Surv. 2024, 56, 1–33. [Google Scholar] [CrossRef]
- Devika, S.; Shrivastava, R.R.; Narang, P.; Alladi, T.; Yu, F.R. VADGAN: An Unsupervised GAN Framework for Enhanced Anomaly Detection in Connected and Autonomous Vehicles. IEEE Trans. Veh. Technol. 2024, 73, 12458–12467. [Google Scholar] [CrossRef]
- Huang, W.; Xu, H.; Gong, Y.; Liu, Z.; Li, F.; Lin, Z.; Hu, B.-J. UltraADV: An Unsupervised Deep Learning Lightweight Framework for Anomaly Detection in V2X. IEEE Internet Things J. 2024, 12, 12735–12747. [Google Scholar] [CrossRef]
- Khanmohammadi, F.; Azmi, R. Time-Series Anomaly Detection in Automated Vehicles Using D-CNN-LSTM Autoencoder. IEEE Trans. Intell. Transp. Syst. 2024, 25, 9296–9307. [Google Scholar] [CrossRef]
- Al-Yarimi, F.A.M. Enhancing road safety through advanced predictive analytics in V2X communication networks. Comput. Electr. Eng. 2024, 115, 109134. [Google Scholar] [CrossRef]
- Zhao, L.; Fan, X.; Hawbani, A.; Xu, L.; Yu, K.; Liu, Z.; Alfarraj, O. Generative Abnormal Data Detection for Enhancing Cellular Vehicle-to-Everything Based Road Safety. IEEE Trans. Green Commun. Netw. 2024, 8, 1466–1478. [Google Scholar] [CrossRef]
- Qian, H.; Chai, H.; Hawbani, A.; Bi, Y.; Lin, N.; Zhao, L. A Collaborative Error Detection and Correction Scheme for Safety Message in V2X. IEEE Trans. Mob. Comput. 2024, 24, 2594–2611. [Google Scholar] [CrossRef]
- Venkatasamy, T.K.; Hossen, M.J.; Ramasamy, G.; Aziz, N.H.B.A. Intrusion detection system for V2X communication in VANET networks using machine learning-based cryptographic protocols. Sci. Rep. 2024, 14, 31780. [Google Scholar] [CrossRef]
- Asaju, B.J. Advancements in Intrusion Detection Systems for V2X: Leveraging AI and ML for Real-Time Cyber Threat Mitigation. J. Comput. Intell. Robot. 2024, 4, 33–50. [Google Scholar] [CrossRef]
- John, B. Machine Learning-Based Anomaly Detection in V2V and V2X Networks. 2025. Available online: https://www.researchgate.net/publication/389089255 (accessed on 28 May 2025).
- Ahmad, F.; Adnane, A.; Franqueira, V.N.L.; Kurugollu, F.; Liu, L. Man-In-The-Middle Attacks in Vehicular Ad-Hoc Networks: Evaluating the Impact of Attackers’ Strategies. Sensors 2018, 18, 4040. [Google Scholar] [CrossRef]
- Mo, R.; Wu, B.; Tan, Z.; Qiu, H. Poster Abstract: SEE-V2X: Empirical Evaluation of C-V2X Direct Communica-tion in Real-World Scenarios. In Proceedings of the 23rd ACM Conference on Embedded Networked Sensor Systems, Irvine, CA, USA, 6–9 May 2025; pp. 598–599. [Google Scholar] [CrossRef]
- Wei, R.; Garcia, C.; El-Sayed, A.; Peterson, V.; Mahmood, A. Variations in Variational Autoencoders—A Comparative Evaluation. IEEE Access 2020, 8, 153651–153670. [Google Scholar] [CrossRef]
- Harang, R.; Sanders, H. Catastrophic Forgetting in the Context of Model Updates. 2023. Available online: https://arxiv.org/abs/2306.10181v1 (accessed on 5 June 2025).
- Cabello-Solorzano, K.; de Araujo, I.O.; Peña, M.; Correia, L.; Tallón-Ballesteros, A.J. The Impact of Data Normalization on the Accuracy of Machine Learning Algorithms: A Comparative Analysis. Lect. Notes Netw. Syst. 2023, 750, 344–353. [Google Scholar] [CrossRef]
- Yin, C.; Zhang, S.; Wang, J.; Xiong, N.N. Anomaly Detection Based on Convolutional Recurrent Autoencoder for IoT Time Series. IEEE Trans. Syst. Man, Cybern. Syst. 2020, 52, 112–122. [Google Scholar] [CrossRef]
- Cinelli, L.P.; Marins, M.A.; da Silva, E.A.B.; Lima Netto, S. Variational Autoencoder. In Variational Methods for Machine Learning with Applications to Deep Networks; Springer International Publishing: Cham, Switzerland, 2021; pp. 111–149. [Google Scholar] [CrossRef]
- Liu, Y.; Zhao, Z.; Zhang, S.; Jung, U. Identification of Abnormal Processes with Spatial-Temporal Data Using Convolutional Neural Networks. Processes 2020, 8, 73. [Google Scholar] [CrossRef]
- Szandała, T. Review and Comparison of Commonly Used Activation Functions for Deep Neural Networks. Stud. Comput. Intell. 2021, 903, 203–224. [Google Scholar] [CrossRef]
- Burgess, C.P.; Higgins, I.; Pal, A.; Matthey, L.; Watters, N.; Desjardins, G.; Lerchner, A. Understanding Disentangling in β-VAE. arXiv 2018, arXiv:1804.03599. [Google Scholar] [CrossRef]
- SUMO Documentation. Available online: https://sumo.dlr.de/docs/index.html (accessed on 19 September 2024).
- FCDOutput—SUMO Documentation. Available online: https://sumo.dlr.de/docs/Simulation/Output/FCDOutput.html (accessed on 5 June 2025).
- Metzner, A.; Wickramarathne, T. Exploiting Vehicle-to-Vehicle Communications for Enhanced Situational Awareness. In Proceedings of the 2019 IEEE Conference on Cognitive and Computational Aspects of Situation Management, CogSIMA, Las Vegas, NV, USA, 8–11 April 2019; pp. 88–92. [Google Scholar] [CrossRef]
- Welcome To Colab—Colab. Available online: https://colab.research.google.com/ (accessed on 29 December 2024).
- Nabila, P.; Setiawan, E.B. Adam and AdamW Optimization Algorithm Application on BERT Model for Hate Speech Detection on Twitter. In Proceedings of the 2024 International Conference on Data Science and Its Applications (ICoDSA), Bali, Indonesia, 10–11 July 2024; pp. 346–351. [Google Scholar] [CrossRef]
- Voce, G.; Griffith, H.; Rathore, H. Avoiding False Social Conformity in Majority-Malicious Connected Vehicle Networks Employing Consensus-Based Reputation Estimates. In Proceedings of the Digest of Technical Papers—IEEE International Conference on Consumer Electronics, Las Vegas, NV, USA, 6–8 January 2024. [Google Scholar] [CrossRef]
- Jin, K.; Han, X.; Wang, H. Conquering Ghosts: Relation Learning for Information Reliability Representation and End-to-End Robust Navigation. arXiv 2022, arXiv:2203.09952. [Google Scholar] [CrossRef]
- Jin, H.; Papadimitratos, P. Accountable, Scalable and DoS-resilient Secure Vehicular Communication. Comput. Secur. 2025, 156, 104469. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).