Integral Security Pillars for Medical Devices: A Comprehensive Analysis
Abstract
:1. Introduction
2. Materials and Methods
- Phase 1: Problem Statement
- Phase 2: Review of Regulations, Cybersecurity Studies, and Common Vulnerabilities
- Phase 3: Presentation and Analysis of Research Results
- Phase 4: Development of the Security Pillars Model
3. Results
3.1. Problem Statement
3.2. Review of Regulations, Cybersecurity Studies, and Common Vulnerabilities
3.2.1. Regulations
- ISO
| Normative | Year | Name | Description |
|---|---|---|---|
| ISO 27701 [8] | 2019 | Extension to ISO/IEC 27001 [9] and ISO/IEC 27002 [10] for information privacy management. | This document provides requirements and guidelines for establishing, implementing, maintaining, and improving a privacy information management system (PIMS), which is crucial for protecting personal data on medical devices. |
| ISO/IEC 27799 [11] | 2016 | Managing health information security using ISO/IEC 27002 | Provides guidelines to support the interpretation and implementation of ISO/IEC 27002 in the healthcare sector, ensuring the protection of personal health information (PII) in health information systems. |
| ISO 13485 [12] | 2016 | Quality management systems for medical devices | Although this standard focuses primarily on quality management systems, it includes requirements for risk management and security of software and computer systems used in medical devices. |
| ISO/IEC 27001 [9] | 2013 | Information Security Management Systems (ISMSs) | It establishes the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). This standard can be applied to any organization handling sensitive information, including manufacturers and suppliers of medical devices. |
| ISO/IEC 82304-1 [13] | 2016 | Health informatics—health software | General requirements for health software products: Defines quality and safety requirements for health software products, including those used in medical devices, and ensures that the software meets information security standards. |
| ISO/IEC 27002 [14] | 2013 | Code of practice for information security controls | Provides guidelines for implementing information security controls based on industry best practices, applicable to medical devices to protect the confidentiality, integrity, and availability of information. |
| ISO/IEC 80001-1 [15] | 2010 | Application of risk management for IT networks incorporating medical devices | Provides a framework for risk management related to integrating medical devices into information technology networks, ensuring that risks associated with information security and interoperability are addressed. |
- NIST
| Normative | Year | Name | Description |
|---|---|---|---|
| NIST Cybersecurity Framework (CSF) [17] | 2024 | - | A flexible, risk-based framework for improving cybersecurity in critical infrastructure, including the healthcare sector. Medical device manufacturers and users can use this framework to develop and improve cybersecurity programs. |
| NIST SP 800-63-3 [18] | 2023 | Digital Identity Guidelines: | Guides digital identity management; relevant for medical devices that require authentication and access control. |
| NIST Special Publication (SP) 800-53 Rev. 5 [19] | 2020 | Security and Privacy Controls for Information Systems and Organizations | Provides a catalog of security and privacy controls to protect information and information systems, including those used in medical devices. |
| NIST SP 800-37 Rev. 2 [20] | 2018 | Risk Management Framework for Information Systems and Organizations | A “System Life Cycle Approach for Security and Privacy" describes the NIST risk management framework, which can be applied to manage security and privacy risks in medical devices throughout their life cycle. |
| NIST SP 1800-1 [21] | 2018 | Securing Electronic Health Records on Mobile Devices | Provides practical examples and reference architectures for protecting electronic health records on mobile devices, applicable to mobile and wearable medical devices. |
| NIST SP 800-82 Rev. 2 [22] | 2015 | Guide to Industrial Control Systems (ICSs) Security: | This document provides guidance on the security of industrial control systems, which may apply to certain medical devices operating in industrial or manufacturing environments. |
| NIST SP 800-88 Rev. 1 [23] | 2014 | Guidelines for Media Sanitization | Provides guidelines for the secure disposal of data on storage media, applicable to medical devices that store sensitive information. |
| NIST SP 800-30 Rev. 1 [24] | 2012 | Guide for Conducting Risk Assessments | Guides performing risk assessments are essential for identifying and mitigating security risks in medical devices. |
| NIST SP 800-66 Rev. 1 [25] | 2008 | An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule: | This document provides guidance on how to comply with the HIPAA Security Rule, which is relevant to medical devices that handle protected health data. |
- HIPAA
| Normative | Year | Name | Description |
|---|---|---|---|
| HIPAA | 1996 | Original HIPAA law published | The original law was enacted to enhance health insurance portability, reduce fraud and the abuse in healthcare, and establish standards for the security and privacy of health information. |
| 2000 | Publication of the Privacy Rule | It establishes national standards for protecting Protected Health Information (PHI), limiting its use and disclosure and granting a patient rights regarding their information. | |
| 2003 | Publication of the Security Rule | It requires the implementation of administrative, physical, and technical security measures to protect electronic Protected Health Information (PHI) and ensure its confidentiality, integrity, and availability. | |
| 2004 | Publication of the National Identifier Rule | It requires the implementation of administrative, physical, and technical security measures to protect electronic Protected Health Information (PHI) and ensure its confidentiality, integrity, and availability. | |
| 2000 | Publication of the Transactions and Codes Rule | It establishes standards for electronic healthcare transactions and codes, promoting standardization and simplifying administrative processes. | |
| 2009 | Publication of the Breach Notification Rule | It requires covered entities and their business associates to notify affected individuals, the Department of Health and Human Services (HHS), and, in some cases, the media in the event of an unsecured Protected Health Information (PHI) breach. |
- ENISA
| Normative | Year | Name | Description |
|---|---|---|---|
| ENISA Good practices for the security of healthcare services [28] | 2017 | Professional services | It includes consulting, audits, and technical support. Good practices encompass cybersecurity training, restricted access policies, and continuous risk management. |
| Remote care systems | It includes telemedicine systems and remote patient monitoring. It is recommended to use secure connections, robust authentication, and personal and health data protection. | ||
| Building management systems | They manage the physical infrastructure of healthcare buildings (HVAC, lighting, security). Practices include network segmentation, continuous monitoring, and regular software updates. | ||
| Clinical information systems | They handle clinical information, such as electronic health records (EHR/EMR). Implementing role-based access controls, data encryption, and audits of access and modifications is crucial. | ||
| Cloud services | Cloud services for storing and processing health data. Best practices include vendor security assessment, encryption, and disaster recovery plans. | ||
| Identification systems | Verify the identity of users and devices. Multi-factor authentication, identity management, and monitoring of authentication activities are recommended. | ||
| Industrial control systems | They control industrial processes in healthcare facilities. Practices include network segmentation, real-time monitoring, and regular system updates. | ||
| Medical devices | It connected medical devices that manage patient data. Security by design, data encryption, and threat monitoring are essential. | ||
| Mobile client devices | Healthcare professionals and patients use mobile devices. Secure applications, mobile device management policies, and malware protection are recommended. | ||
| Network equipment | Network equipment that supports healthcare IT infrastructure. Best practices include implementing firewalls, network segmentation, and updating network firmware and software. |
- GDPR
| Normative | Year | Name | Description |
|---|---|---|---|
| GDRP | 2016 | Fundamental Principles | Since its adoption in 2016 and enforcement in 2018, the GDPR has established principles for processing personal data, ensuring that it is lawful, fair, transparent, and limited to specific purposes. |
| Informed Consent | It requires that users expressly, informally, and freely consent to the processing of personal data, especially in the sensitive context of medical data. | ||
| 2018 | Rights of Interested Parties | Since 2018, it has ensured rights such as access, rectification, erasure, and data portability, allowing individuals to control their personal information. | |
| Data Security | It requires the implementation of appropriate technical and organizational measures to protect personal data against loss or unauthorized access, which is essential for medical devices handling sensitive data. | ||
| Data Protection Impact Assessments (DPIA) | It establishes the need to conduct impact assessments when data processing involves high risks to individuals’ rights and freedoms, including situations that may arise with medical devices. | ||
| Responsibility and Compliance | Manufacturers and suppliers must demonstrate compliance with GDPR requirements, maintain records of processing activities, and cooperate with data protection authorities from the date of enforcement. |
- HITRUST
| Normative | Year | Name | Description |
|---|---|---|---|
| HITRUST | 2007 | Integral Approach | It provides a comprehensive approach to information security risk management, integrating and harmonizing multiple standards and regulations, such as HIPAA, NIST, ISO, and COBIT. This makes it easier for organizations to comply with multiple regulatory requirements using a single framework. |
| Adaptability | It is adaptable to different sizes of organizations and types of entities, from small clinics to large health systems and health-related service providers. This allows organizations to customize the implementation of controls based on their specific needs and operating environment. | ||
| Control-Based Structure | The HITRUST CSF is structured around a set of information security controls organized into domains covering critical areas such as access control, asset management, data protection, and incident response. This facilitates the assessment and continuous improvement of an organization’s security posture. | ||
| Assessment and Certification | HITRUST offers a formal assessment and certification process where organizations can independently review their compliance with the HITRUST CSF. This provides external validation that the recommended security controls and practices have been adequately implemented. | ||
| Risk Management Orientation | The HITRUST CSF framework focuses on risk management, not just the adoption of security controls. This involves ongoing risk assessment, implementing controls proportionate to those risks, and responding effectively to security incidents. | ||
| Multi-sectoral Application | Although initially developed for the healthcare sector, the HITRUST CSF also applies to other sectors that handle sensitive and critical information, such as the financial, government, and service sectors. |
- WHO
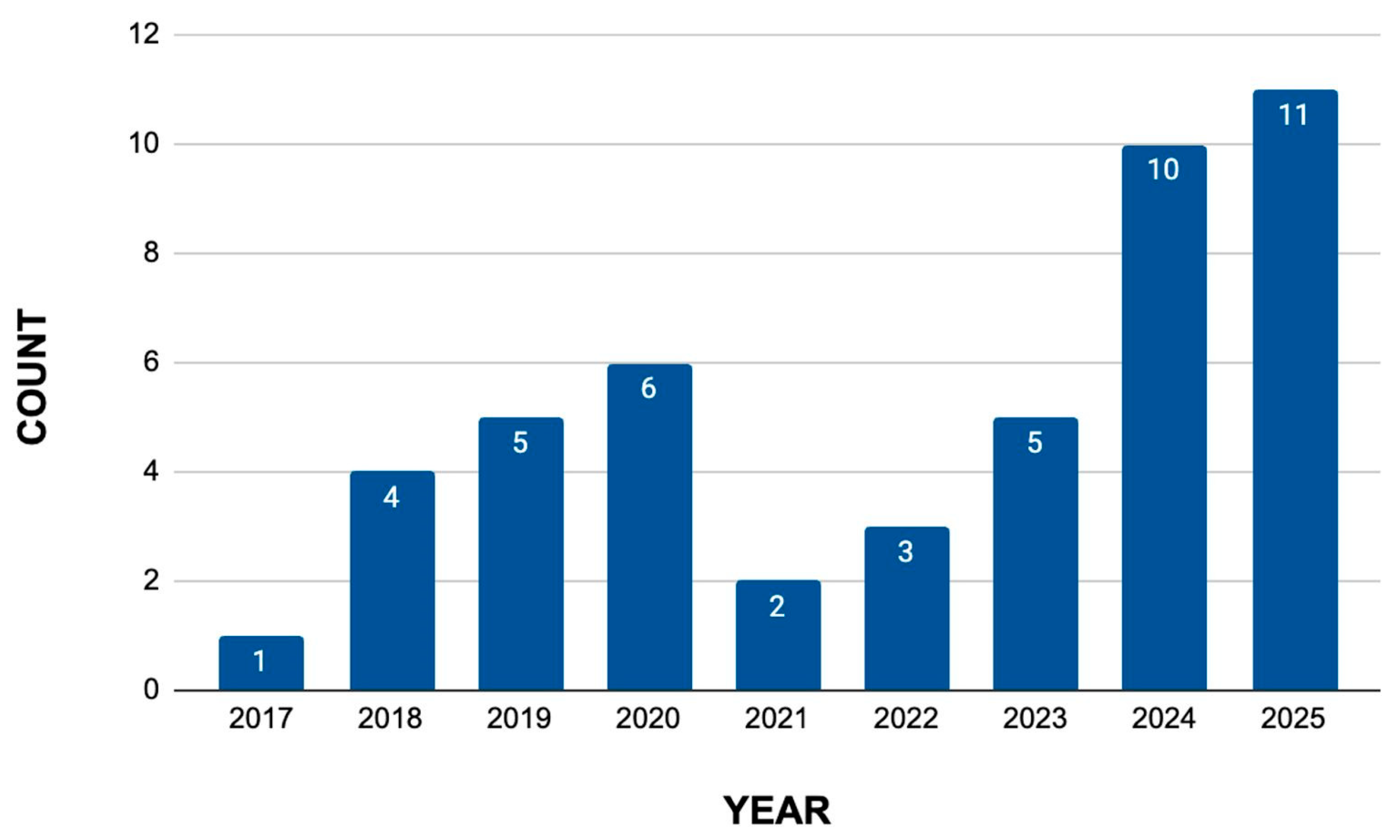
3.2.2. Literature Review
- Review of Scientific Articles
| Year | Title | Variable |
|---|---|---|
| 2025 | Cybersecurity Risk Assessment Frameworks For Engineering Databases: A Systematic Literature Review [31] | Data Security, Cybersecurity Threats, Healthcare Technology, GDPR, Attacks, IoMT Devices, Framework, Threat Detection Rate, Incident Response Time, System Uptime, Cost Efficiency. |
| 2025 | Intelligent two-phase dual authentication framework for Internet of Medical Things [32] | Internet of Medical Things (IoMT), Authentication Framework, Dual Authentication, Elliptic Curve Diffie–Hellman (ECDH), Security, Efficiency, Computational Cost, Latency, Packet Delivery Ratio, Cyber Threats. |
| 2025 | A comprehensive and systematic literature review on intrusion detection systems in the internet of medical things: current status, challenges, and opportunities [33] | Internet of Medical Things (IoMT), Intrusion Detection System (IDS), Cybersecurity, Artificial Intelligence (AI), Machine Learning (ML) and Deep Learning (DL), Datasets, Security Requirements, Intrusion Detection Process, Evaluation Metrics |
| 2025 | A New Model to Evaluate Signature and Anomaly Based Intrusion Detection in Medical IoT System Using Ensemble Approach [34] | Internet of Medical Things (IoMT), Intrusion Detection System (IDS), Ensemble Learning, Machine Learning (ML), Data Traffic, Signatures and Anomalies, Cyberattacks, Signatures and Anomalies |
| 2025 | A risk and conformity assessment framework to ensure security and resilience of healthcare systems and medical supply chain [35] | Healthcare Sector, Digital Transformation, Internet of Medical Things (IoMT), Connected Medical Devices, Healthcare Information Infrastructure (HCII), Cybersecurity Challenges, Risk and Conformity Assessment (RCA) Framework, (ISMS), Artificial Intelligence (AI), Risk Management, Security Controls, Regulatory Compliance, Cyberattacks, Medical Devices |
| 2025 | Maximizing healthcare security outcomes through AI/ML multi-label classification approach on IoHT devices [36] | Cybersecurity, Internet of Health Things (IoHT), AI/ML, Multi-Label Classification, Anomaly Detection, ECU Ioht Dataset, ARP Spoofing, DoS, Nmap Port Scan, Smurf Attack, Attacks |
| 2025 | Next-Gen fortified health monitoring for cyber physical systems in internet of things using logistic maps based encryption [37] | Health Monitoring Systems, Internet of Things (IoT), Cyber-Physical Systems (CPS), Encryption, Chaotic Mapping, ASCON Algorithm, Data Integrity, Randomization, Computational Overhead, Lightweight Cryptography (LWC), Health Data |
| 2025 | An advanced data analytics approach to a cognitive cyber-physical system for the identi-fication and mitigation of cyber threats in the medical internet of things (MIoT) [38] | Medical Internet of Things (MIoT), Cognitive Cyber-Physical System (CCPS), Cyber Threats, Anomaly Detection, Gated Recurrent Units (GRUs), Dense Neural Network (DNN), Whale Optimization Algorithm (WOA), Datasets |
| 2025 | Stacking Ensemble Deep Learning for Real-Time Intrusion Detection in IoMT Environ-ments [39] | Internet of Medical Things (IoMT), Cyber Threats, Intrusion Detection System (IDS), Machine Learning (ML), Deep Learning (DL), Stacking Ensemble Method, Kappa Architecture, ARP Spoofing, DoS, Smurf, Port Scan, Binary Classification, Multi-Class Classification |
| 2025 | Digital Health: The Cybersecurity for AI-based healthcare communication [40] | AI-Based Healthcare, Cybersecurity, Digital Health, Proactive System, Ransomware Attacks, AI Algorithms, Healthcare, Communication, Digital Inclusion, AI-Based Healthcare, Evolving Threats, Scalability of Networks, Authorization Methods |
| 2025 | Efficient lightweight cryptographic solutions for enhancing data security in healthcare systems based on IoT [41] | Internet of Things (IoT), Health Monitoring Systems, CPS, Cryptographic Techniques, Lightweight Cryptography (LWC), Authenticated Encryption, Permutation and Substitution Techniques Chaotic Maps, Hyper-Chaotic Systems, Fibonacci Q-Matrix, Cryptanalysis |
| 2024 | Cybersecurity and use of ICT in the health sector [42] | Cybersecurity, Risks, Threats, Health Sector, Digital Medical Records, Bioethical Implications, Vulnerabilities in Connected Medical Devices, Telemedicine. |
| 2024 | Machine learning cryptography methods for IoT in healthcare [43] | Machine Learning Cryptography Methods, IoT (Internet of Things), Healthcare |
| 2024 | Cybersecurity policy framework requirements for the establishment of highly interoperable and interconnected health data spaces [44] | Cybersecurity Policy, Interoperability of Health Data, Interconnectedness of Health Data Spaces. |
| 2024 | The need for cybersecurity self-evaluation in healthcare [45] | Cybersecurity Self-Evaluation, Healthcare. |
| 2024 | Managing cybersecurity risk in healthcare settings [46] | Managing Cybersecurity Risk, Healthcare Settings, Cybersecurity Threats, Environment. |
| 2024 | A Review on the Application of Internet of Medical Things in Wearable Personal Health Monitoring: A Cloud-Edge Artificial Intelligence Approach [47] | Internet of Medical Things (IoMT), Wearable Personal Health Monitoring, Cloud-Edge Artificial Intelligence Approach, Healthcare, IoMT System. |
| 2024 | Developing a Novel Ontology for Cybersecurity in Internet of Medical Things-Enabled Remote Patient Monitoring [48] | Cybersecurity, Internet of Medical Things (IoMT), Remote Patient Monitoring, Novel Ontology. |
| 2024 | Vulnerability to Cyberattacks and Sociotechnical Solutions for Health Care Systems: Systematic Review [49] | Vulnerability, Cyberattacks, Sociotechnical Solutions, Health Care Systems, Healthcare. |
| 2024 | Cyberattacks on health care-a growing threat [50] | Ransomware Attack, WannaCry, Healthcare Cyberattack, Phishing Scams, Health Care, Growing Threat. |
| 2024 | QUMA: Quantum Unified Medical Architecture Using Blockchain [51] | QUMA Architecture, Blockchain, Medical Sector, Security, Transparency. |
| 2023 | New cybersecurity requirements for medical devices in the eu: the forthcoming european health data space, data act, and artificial intelligence act [52] | Cybersecurity Requirements, Medical Devices, Health Data Space, Data Act, Artificial Intelligence, European Health. |
| 2023 | Insights into security and privacy issues in smart healthcare systems based on medical images [53] | Security Issues, Privacy Issues, Smart Healthcare Systems, Medical Images, Confidentiality, Unauthorized Access, Threats. |
| 2023 | Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives [54] | Cybersecurity, Internet of Medical Vehicles (IoMV), State-of-the-Art Analysis, Research Challenges, Future Perspectives. |
| 2023 | Attack Detection for Medical Cyber-Physical Systems–A Systematic Literature Review [55] | Attack Detection, Medical Cyber-Physical Systems (Mcps), Systematic Literature Review, Synthesize. |
| 2023 | Framework for a Secure and Sustainable Internet of Medical Things, Requirements, Design Challenges, and Future Trends [56] | Patient Health Data, IoMT System, IoMT System Design and Implementation, Architecture, Security Measures, Healthcare Systems, System Performance and Effectiveness, User Interaction and Acceptance, Response Time, Sensitivity, Specificity, Accuracy, and Error Rates. |
| 2022 | A cybersecurity culture survey targeting healthcare critical infrastructures [57] | Cybersecurity Culture Survey, Healthcare Critical Infrastructures, Awareness of Cyber Threats, Security Behaviors, Compliance With Security Policies. |
| 2022 | Cyber security in health: Standard protocols for IoT and supervisory control systems [58] | IoT Devices, Data Breaches, Cybersecurity Budgets, Medical Equipment, Artificial Organs, Biosensors, Information, Medical Records, Networks. |
| 2022 | A review on healthcare data privacy and security [59] | Cloud Computing and Healthcare, Viruses and Worms, Botnets, Ransomware, Phishing, Cloud, Cyberattacks, Identify Theft, Security, Blockchain, Legal Aspect, Remote Patient Monitoring. |
| 2021 | Influence of human factors on cyber security within healthcare organisations: A systematic review [60] | Systematic Review, Human Factors, Cyber Security, Healthcare, Data Extraction, Risk of Bias, Cyber Risk, Economic Impact of Data Breaches, ICT Infrastructure, Cybercrime, Cyberattacks, Cybersecurity, Governance Strategies. |
| 2021 | A survey on security and privacy issues in modern healthcare systems: Attacks and defenses [61] | Protect Healthcare Systems, Privacy Issues, Phishing Attack, Brute Force Attack, Keylogger Attack, Man-in-the-Middle Attack, Eavesdropping Attack, Pharming Attack, Denial of Service (DoS) Attack, Healthcare Systems, Types of Attacks, Cybersecurity Countermeasures, Cybersecurity Vulnerabilities. |
| 2020 | Health Care Cybersecurity Challenges and Solutions Under the Climate of COVID-19: Scoping Review [62] | Endpoint Complexity, Human Factors, Phishing, Ransomware, Distributed Denial of Service (DDoS), Malware, Published Vulnerabilities, Innumerable Wireless Connected Devices, Reliance on Perimeter Defense, Remote Working Security Assurance, VPN, RDP, Integration of New Endpoint Devices with Legacy Systems. |
| 2020 | Artificial intelligence in healthcare: An essential guide for health leaders [63] | Artificial Intelligence (AI), Machine Learning (ML), Natural Language Processing (NLP), AI Voice Technology and Assistants, Medical Robotics, Electronic Health Records (EHRs), Clinical Decision Support, Patient Self-Management, Drug Research, Medical Imaging, Genomics, Telehealth, Big Data, Remote Healthcare. |
| 2020 | Integration of cyber security in healthcare equipment [64] | Operational Technologies (OTs), Information Technologies (ITs), Cyber Security Risks, Operational Risks, Healthcare Equipment, Vulnerabilities, Cyberattacks, Safety, Security Controls and Mitigation. |
| 2020 | Cybersecurity in PACS and Medical Imaging: An Overview [65] | PACS, Medical Imaging, Cybersecurity, Healthcare IT, Physical Mitigation Measures, Technical Mitigation Measures, Organizational Mitigation Measures, Image De-Identification, Transport Security, DICOM, Digital Signatures, Watermarking Techniques, Authenticity, Integrity, Healthcare. |
| 2020 | Medical device safety management using cybersecurity risk analysis [66] | MEMPs, Medical Devices, ICT, Security Threats, Cybersecurity, Risk Management, Internet of Things (IoT), Implantable Medical Devices (IMDs), Attack Occurrence Probability (AOP), Attack Success Probability (ASP), Fennigkoh Model, Smith Model, Analytic Hierarchy Process (AHP). |
| 2020 | An exhaustive survey on security and privacy issues in Healthcare 4.0 [67] | Healthcare 1.0 To 4.0, Electronic Healthcare Records (EHRs), Cloud Computing (CC), Fog Computing (FC), Internet of Things (IoT), Telehealthcare, Security, Privacy, Blockchain, Wearable Devices (WDs), Biometric, Network Traffic, Machine Learning (ML). |
| 2019 | Assessment of Employee Susceptibility to Phishing Attacks at US Health Care Institutions [68] | Cybersecurity, Phishing, Phishing Simulation, Health Care Delivery, Health Care Data and Systems, Email Click Rate, Employee Awareness and Training, Phishing Attacks. |
| 2019 | Health care and cybersecurity: bibliometric analysis of the literature [69] | Cybersecurity, Healthcare Delivery, Healthcare Information Systems, Cyberattacks, Data Breaches, Ransomware, Phishing, Security Incidents, Mitigation Measures, Vulnerabilities, Weaknesses, Exploit, Confidentiality, Integrity, Availability. |
| 2019 | Security Vulnerabilities, Attacks, Countermeasures, and Regulations of Networked Medical Devices—A Review [70] | Networked Medical Devices, Medical Telemetry, Security Vulnerabilities, Cyberattacks, Countermeasures, Regulations, FDA, HIPAA, GDPR. |
| 2019 | Medical device vulnerability mitigation effort gap analysis taxonomy [71] | Medical Devices, Vulnerabilities, Mitigation, Cybersecurity, Associated Parties, Effort, Risk Assessment, Data Breaches, Healthcare, Standards Organizations, Academia, Device Manufacturers, Including Authorities, Sensitive Data. |
| 2019 | Integrated security, safety, and privacy risk assessment framework for medical devices [72] | Medical Devices, Security, Safety, Privacy, Risk Assessment, FDA (Food and Drug Administration), EU (European Union), MDR (Medical Device Regulation), CVSS (Common Vulnerability Scoring System), CWE (Common Weaknesses Enumeration), Cyber Threats, Healthcare. |
| 2018 | Cybersecurity in healthcare: A narrative review of trends, threats and ways forward [73] | Cybersecurity, Healthcare, Medical Devices, Electronic Health Records (EHRs), Hacking, Malware, Ransomware, Insider Threats, Vulnerabilities to Exploit, WannaCry Attack, General Data Protection Regulation (GDPR), Internet of Things (IoT). |
| 2018 | Cybersecurity in Hospitals: A Systematic, Organizational Perspective [74] | HITECH, HIPAA, National Institute of Standards and Technology (NIST), Internal Politics, Technology Saturated Environment, Cybersecurity, FDA, Cybercriminal, Hospital Systems, Cyberattacks. |
| 2018 | Cyber Attacks Classification in IoT-Based-Healthcare Infrastructure [75] | Cyberattacks in IoT-Based Healthcare Infrastructure, Independent Variables, Attack Vectors/Types, Malicious Action, Infrastructure Layers, Specific Attack Classifications, Session Medjacking, Ransomware, Denial Of Service, RFID-Related Attacks, Malware Injection Attacks, Vulnerabilities, Threats, Risks, Weaknesses in IoT Systems. |
| 2018 | Cybersecurity of healthcare IoT-based systems: Regulation and case-oriented assessment [76] | Cybersecurity of IoT-Based Healthcare Systems, Cybersecurity, International Regulations and Standards, ISO, IEC, HIPAA, IoT Architecture, IoT Healthcare Architecture Layers, Cybersecurity Assessment, Protected Health Information (PHI), Threats and Vulnerabilities, Sensing, Network, Service, Application Interfaces. |
| 2017 | Cybersecurity in healthcare: A systematic review of modern threats and trends [77] | Cybersecurity Threats, Healthcare Technology, Data Breaches, Security Measures, Government Regulations and Policies, ACA, HITECH, Security, Medical Information, HIPAA, Ransomware. |
3.2.3. Vulnerability and Attack Types Analysis
| Vendor | Model | CVE | Type of Attack |
|---|---|---|---|
| Philips (Andover, MA, USA) | SureSigns VS4 | CVE-2020-16237 | Exploitable Remotely |
| CVE-2020-16239 | |||
| CVE-2020-1624 | |||
| IntelliVue MX700 and MX800 | CVE-2020-16216 | Low Attack Complexity | |
| CVE-2019-13530 | Use of Hard-coded Password, Download of Code Without Integrity Check | ||
| IntelliVue MX100 | CVE-2020-16214 | Low Attack Complexity | |
| Philips HealthSuite Health Android App, all versions | CVE-2018-19001 | Inadequate Encryption Strength | |
| IntelliBridge EC 40 and 60 Hub | CVE-2021-33017 | Authentication Bypass Using an Alternate Path or Channel | |
| GE Healthcare (Chicago, IL, USA) | GE CARESCAPE B450/B650/B850 | CVE-2020-6961 | Exploitable Remotely/Low Skill Level to Exploit |
| CVE-2020-6962 | |||
| CVE-2020-6963 | |||
| CVE-2020-6964 | |||
| CVE-2020-6965 | |||
| CVE-2020-6966 | |||
| EchoPAC | CVE-2024-27106 | Exploitation Activity | |
| Ultrasound devices | CVE-2024-1628 | OS Command Injection Vulnerabilities | |
| Imaging and Ultrasound Products | CVE-2020-25179 | Information Leak | |
| XZ Utils | CVE-2024-3094 | Embedded Malicious Code | |
| Welch Allyn (Skaneateles Falls, NY, USA) | Spot Vital Signs 4400 | CVE-2021-27410 | Exploitable Remotely |
| CVE-2021-27408 | |||
| Vital Signs Monitor | CVE-2024-1275 | Exploitable Remotely | |
| Dräger (Lübeck, Germany) | Infinity® Delta Series | CVE-2019-6446 | Probability of Exploitation Activity |
| IBM (Armonk, NY, USA) | Merge Healthcare eFilm Workstation | CVE-2024-23619 | Execute Code |
| Merge Healthcare eFilm Workstation | CVE-2024-23622 | Buffer Overflow | |
| Merge Healthcare eFilm Workstation | CVE-2024-23621 | Buffer Overflow | |
| CodeProjects | Health Care hospital Management System v1.0 | CVE-2024-38348 | SQL Injection Vulnerability |
| Health Care hospital Management System v1.0 | CVE-2024-38347 | SQL Injection Vulnerability |
3.3. Presentation of the Data and Analysis of the Results
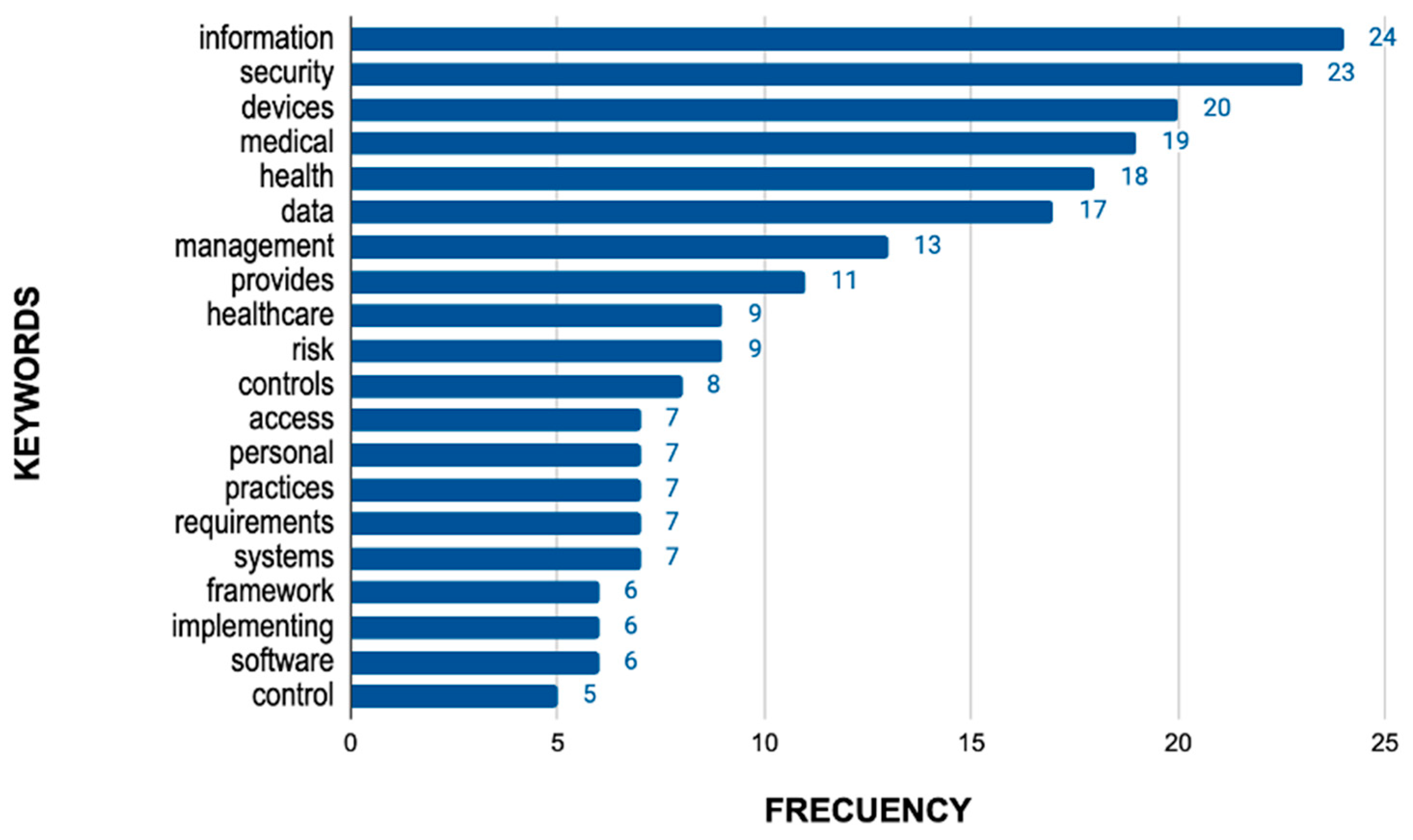
3.3.1. Analysis of the Data Obtained from the Regulations
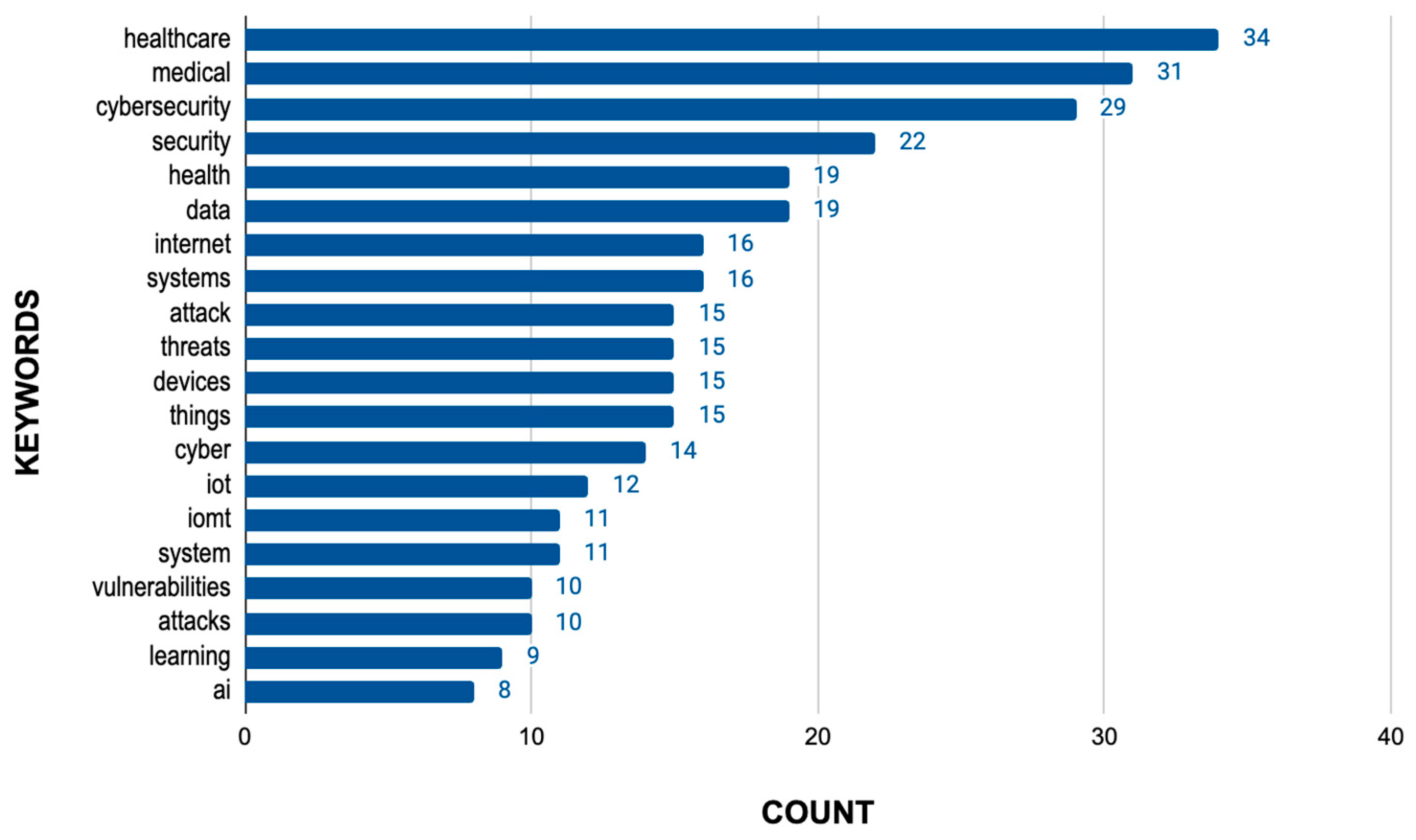
3.3.2. Analysis of Data Extracted from the Literature Review
3.3.3. Analysis of Data Extracted from the Common Vulnerabilities Exposed
3.3.4. Result of the Analysis of the Information Obtained
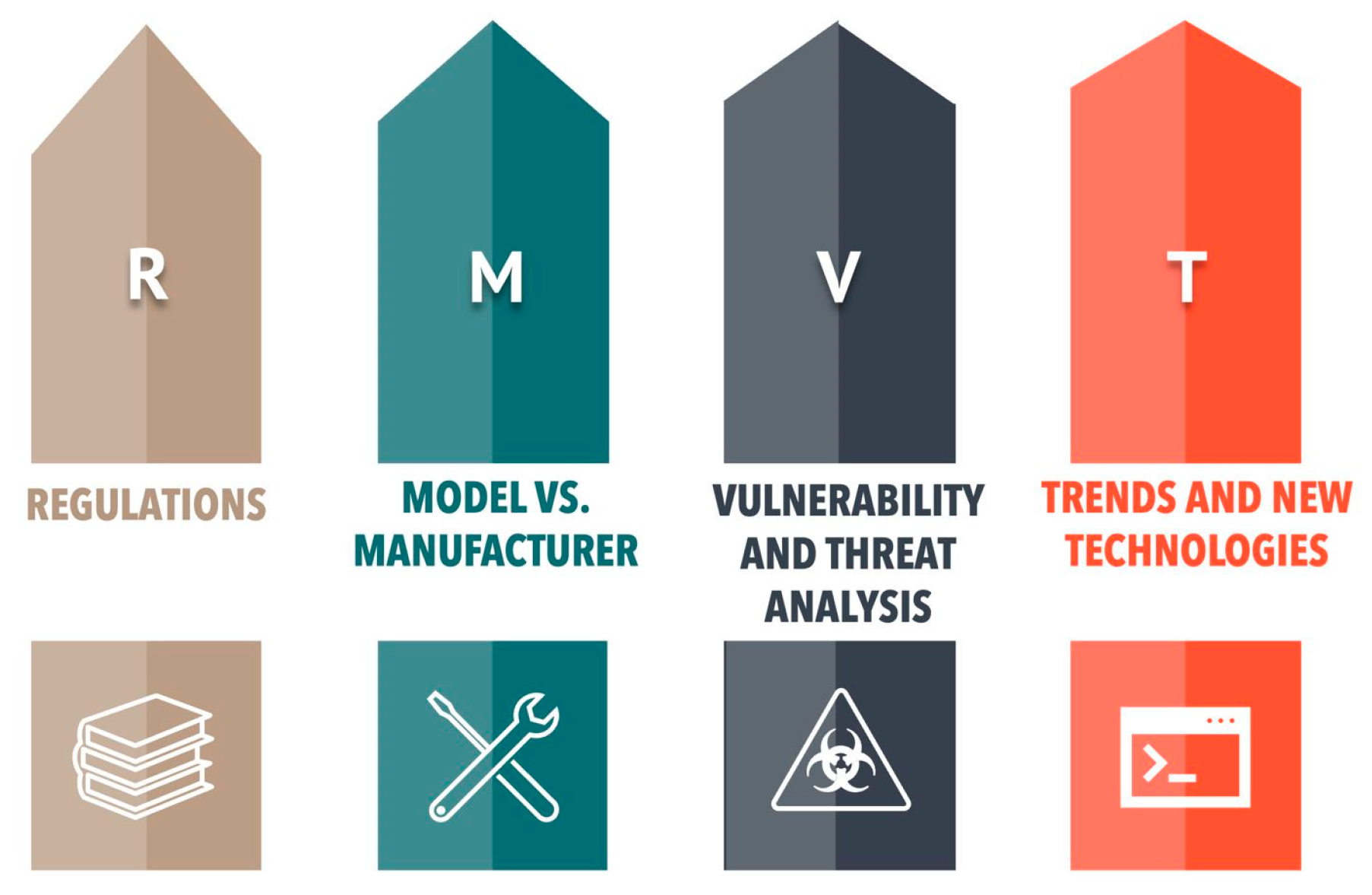
3.4. Development of the Security Pillars Model
- Regulations:
- Model vs. Manufacturer:
- Vulnerability and Threat Analysis:
- Trends and Emerging Technologies:
- R: Regulations
- M: Model vs. Manufacturer
- V: Vulnerability and Threat Analysis
- T: Trends and New Technologies
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Yazid, A. Cybersecurity and Privacy Issues in the Internet of Medical Things (IoMT). Eig. Rev. Sci. Technol. 2023, 7, 1–21. [Google Scholar]
- Ogu, E.C. Cybersecurity for eHealth: A Simplified Guide to Practical Cybersecurity for Non-Technical Healthcare Stakeholders & Practitioners; Routledge: London, UK, 2021. [Google Scholar]
- Wong, J.; Tong, R.K. (Eds.) Medical Regulatory Affairs: An International Handbook for Medical Devices and Healthcare Products; CRC Press: Boca Raton, FL, USA, 2022. [Google Scholar]
- Wirth, A.G. Medical Device Cybersecurity for Engineers and Manufacturers; Artech House: Norwood, MA, USA, 2020. [Google Scholar]
- Arnab, R. Chapter Three: Regulatory overview. In Cybersecurity for Connected Medical Devices; Arnab, R., Ed.; Elsevier Inc.: Amsterdam, The Netherlands, 2022; pp. 46–64. [Google Scholar]
- ISO. Available online: https://www.iso.org/es/home (accessed on 24 June 2024).
- Hitrustalliance. HITRUST. Available online: https://hitrustalliance.net/ (accessed on 24 June 2024).
- ISO/IEC 27701:2019; Security Techniques—Extension to ISO/IEC 27001 and ISO/IEC 27002 for Privacy Information Management—Requirements and Guidelines. ISO: Genewa, Switzerland, 2019.
- ISO/IEC 27001:2013; Information Technology—Security Techniques—Information Security Management Systems—Requirements. International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC): Geneva, Switzerland, 2013.
- ISO/IEC 27002:2019; Information Technology—Security Techniques—Code of Practice for Information Security Controls. International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC): Geneva, Switzerland, 2019.
- ISO 27799:2016; Health Informatics—Guidelines for Information Security Management in Health. International Organization for Standardization (ISO): Geneva, Switzerland, 2016.
- ISO 13485:2016; Medical Devices—Quality Management Systems—Requirements for Regulatory Purposes. International Organization for Standardization (ISO): Geneva, Switzerland, 2016.
- ISO/IEC 82304-1:2016; Health Software—Part 1: General Requirements for Product Safety and Security. International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC): Geneva, Switzerland, 2016.
- ISO/IEC 27002:2013; Information Technology—Security Techniques—Code of Practice for Information Security Controls. International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC): Geneva, Switzerland, 2013.
- ISO/IEC 80001-1:2010; Application of Risk Management for IT-Networks Incorporating Medical Devices—Part 1: Roles, Responsibilities and Activities. International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC): Geneva, Switzerland, 2010.
- NIST.GOB. Available online: https://www.nist.gov/ (accessed on 20 June 2024).
- NIST Cybersecurity Framework (CSF) 2.0; The NIST Cybersecurity Framework (CSF) 2.0; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2024.
- NIST Special Publication 800-63-3; Digital Identity Guidelines; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2023.
- NIST Special Publication 800-53, Revision 5; Security and Privacy Controls for Information Systems and Organizations; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2020.
- NIST Special Publication 800-37, Revision 2; Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2018.
- NIST Special Publication 1800-1; Securing Electronic Health Records on Mobile Devices; National Institute of Standards and Technology (NIST)/National Cybersecurity Center of Excellence (NCCoE): Gaithersburg, MD, USA, 2018.
- NIST Special Publication 800-82, Revision 2; Guide to Industrial Control System (ICS) Security; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2015.
- NIST Special Publication 800-88, Revision 1; Guidelines for Media Sanitization; National Institute of Standards and Technology; (NIST): Gaithersburg, MD, USA, 2014.
- NIST Special Publication 800-30, Revision 1; Guide for Conducting Risk Assessments; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2012.
- NIST Special Publication 800-66, Revision 1; An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2008.
- HHS. Available online: https://www.hhs.gov/programs/hipaa/index.html (accessed on 20 June 2024).
- ENISA. Available online: https://www.enisa.europa.eu/about-enisa/what-we-do (accessed on 20 June 2024).
- WHO. Available online: https://www.who.int/ (accessed on 20 June 2024).
- GDRP. EU. Available online: https://gdpr.eu/ (accessed on 20 June 2024).
- Jelić, L. Cybersecurity, Data Protection, and Artificial Intelligence in Medical Devices. In Inspection of Medical Devices: For Regulatory Purposes; Springer: Cham, Switzerland, 2023; pp. 417–445. [Google Scholar]
- Islam, M.T.; Mission, M.R.; Refat, T.K.; Kynatun, M. Cybersecurity risk assessment frameworks for engineering databases: A systematic literature review. Strateg. Data Manag. Innov. 2025, 2, 224–243. [Google Scholar] [CrossRef]
- Asif, M.; Abrar, M.; Salam, A.; Amin, F.; Ullah, F.; Shah, S.; AlSalman, H. Intelligent two-phase dual authentication framework for Internet of Medical Things. Sci. Rep. 2025, 15, 1760. [Google Scholar] [CrossRef]
- Naghib, A.; Gharehchopogh, F.S.; Zamanifar, A. A comprehensive and systematic literature review on intrusion detection systems in the internet of medical things: Current status, challenges, and opportunities. Artif. Intell. Rev. 2025, 58, 114. [Google Scholar] [CrossRef]
- Abdullah, A.S.; Sunil, H.J.; Nazmudeen, M.S.H. A New Model to Evaluate Signature and Anomaly Based Intrusion Detection in Medical IoT System Using Ensemble Approach. SN Comput. Sci. 2025, 6, 347. [Google Scholar] [CrossRef]
- Kioskli, K.; Grigoriou, E.; Islam, S.; Yiorkas, A.M.; Christofi, L.; Mouratidis, H. A risk and conformity assessment framework to ensure security and resilience of healthcare systems and medical supply chain. Int. J. Inf. Secur. 2025, 24, 90. [Google Scholar] [CrossRef]
- Shombot, E.S.; Dusserre, G.; Bestak, R.; Ahmed, N.B. Maximizing healthcare security outcomes through AI/ML multi-label classification approach on IoHT devices. Health Technol. 2025, 15, 539–551. [Google Scholar] [CrossRef]
- Sarkar, A.; Jhamb, M. Next-Gen fortified health monitoring for cyber physical systems in internet of things using logistic maps based encryption. Eng. Res. Express 2025, 7, 015305. [Google Scholar] [CrossRef]
- Tang, Y.; Mishra, S.; Alduaiji, N.; Shukla, P.K.; Yahya, M.; Pang, T. An advanced data analytics approach to a cognitive cyber-physical system for the identification and mitigation of cyber threats in the medical internet of things (MIoT). J. Supercomput. 2025, 81, 623. [Google Scholar] [CrossRef]
- Alalwany, E.; Alsharif, B.; Alotaibi, Y.; Alfahaid, A.; Mahgoub, I.; Ilyas, M. Stacking Ensemble Deep Learning for Real-Time Intrusion Detection in IoMT Environments. Sensors 2025, 25, 624. [Google Scholar] [CrossRef]
- Algarni, A.; Thayananthan, V. Digital Health: The Cybersecurity for AI-based healthcare communication. IEEE Access 2025, 13, 5858–5870. [Google Scholar] [CrossRef]
- Rasheed, A.M.; Kumar, R.M.S. Efficient lightweight cryptographic solutions for enhancing data security in healthcare systems based on IoT. Front. Comput. Sci. 2025, 7, 1522184. [Google Scholar] [CrossRef]
- García, C.; Goussens, A. Cybersecurity and use of ICT in the health sector. Aten. Prim. 2024, 56, 102854. [Google Scholar]
- Chinbat, T.; Madanian, S.; Airehrour, D.; Hassandoust, F. Machine learning cryptography methods for IoT in healthcare. BMC Med. Inform. Decis. Mak. 2024, 24, 153. [Google Scholar] [CrossRef]
- Luidold, C.; Jungbauer, C. Cybersecurity policy framework requirements for the establishment of highly interoperable and interconnected health data spaces. Front. Med. 2024, 11, 1379852. [Google Scholar] [CrossRef]
- Burke, W.; Stranieri, A.; Oseni, T.; Gondal, I. The need for cybersecurity self-evaluation in healthcare. BMC Med. Inform. Decis. Mak. 2024, 24, 133. [Google Scholar] [CrossRef] [PubMed]
- Clarke, M.; Martin, K. Managing cybersecurity risk in healthcare settings. In Healthcare Management Forum; SAGE Publications: Los Angeles, CA, USA, 2024; Volume 37, pp. 17–20. [Google Scholar]
- Putra, K.T.; Arrayyan, A.Z.; Hayati, N.; Damarjati, C.; Bakar, A.; Chen, H.C. A Review on the Application of Internet of Medical Things in Wearable Personal Health Monitoring: A Cloud-Edge Artificial Intelligence Approach. IEEE Access 2024, 12, 21437–21452. [Google Scholar] [CrossRef]
- Bughio, K.S.; Cook, D.M.; Shah, S.A.A. Developing a Novel Ontology for Cybersecurity in Internet of Medical Things-Enabled Remote Patient Monitoring. Sensors 2024, 24, 2804. [Google Scholar] [CrossRef]
- Ewoh, P.; Vartiainen, T. Vulnerability to cyberattacks and sociotechnical solutions for health care systems: Systematic review. J. Med. Internet Res. 2024, 26, e46904. [Google Scholar] [CrossRef]
- Lancet, T. Cyberattacks on health care—A growing threat. Lancet 2024, 403, 2263. [Google Scholar] [CrossRef] [PubMed]
- Balasubramaniam, A.; Surendiran, B. QUMA: Quantum Unified Medical Architecture Using Blockchain. Informatics 2024, 11, 33. [Google Scholar] [CrossRef]
- Biasin, E.; Yasar, B.; Kamenjasevic, E. New cybersecurity requirements for medical devices in the eu: The forthcoming european health data space, data act, and artificial intelligence act. Law Tech. Hum. 2023, 5, 43. [Google Scholar] [CrossRef]
- Yan, F.; Li, N.; Iliyasu, A.M.; Salama, A.S.; Hirota, K. Insights into security and privacy issues in smart healthcare systems based on medical images. J. Inf. Secur. Appl. 2023, 78, 103621. [Google Scholar] [CrossRef]
- Bhukya, C.R.; Thakur, P.; Mudhivarthi, B.R.; Singh, G. Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives. Sensors 2023, 23, 8107. [Google Scholar] [CrossRef] [PubMed]
- Weber, S.B.; Stein, S.; Pilgermann, M.; Schrader, T. Attack detection for medical cyber-physical systems–a systematic literature review. IEEE Access 2023, 11, 41796–41815. [Google Scholar] [CrossRef]
- Villegas-Ch, W.; García-Ortiz, J.; Urbina-Camacho, I. Framework for a Secure and Sustainable Internet of Medical Things, Requirements, Design Challenges, and Future Trends. Appl. Sci. 2023, 13, 6634. [Google Scholar] [CrossRef]
- Gioulekas, F.; Stamatiadis, E.; Tzikas, A.; Gounaris, K.; Georgiadou, A.; Michalitsi-Psarrou, A.; Doukas, G.; Kontoulis, M.; Nikoloudakis, Y.; Marin, S.; et al. A cybersecurity culture survey targeting healthcare critical infrastructures. Healthcare 2022, 10, 327. [Google Scholar] [CrossRef]
- Santos, B.J.; Tabacow, R.P.; Barboza, M.; Leão, T.F.; Bock, E.G. Cyber security in health: Standard protocols for IoT and supervisory control systems. In Research Anthology on Securing Medical Systems and Records; IGI Global: Hershey, PA, USA, 2022; pp. 238–254. [Google Scholar]
- Bommareddy, S.; Khan, J.A.; Anand, R. A review on healthcare data privacy and security. In Networking Technologies in Smart Healthcare; CRC Press: Boca Raton, FL, USA, 2022; pp. 165–187. [Google Scholar]
- Nifakos, S.; Chandramouli, K.; Nikolaou, C.K.; Papachristou, P.; Koch, S.; Panaousis, E.; Bonacina, S. Influence of human factors on cyber security within healthcare organisations: A systematic review. Sensors 2021, 21, 5119. [Google Scholar] [CrossRef]
- Newaz, A.I.; Sikder, A.K.; Rahman, M.A.; Uluagac, A.S. A survey on security and privacy issues in modern healthcare systems: Attacks and defenses. ACM Trans. Comput. Healthc. 2021, 2, 1–44. [Google Scholar] [CrossRef]
- He, Y.; Aliyu, A.; Evans, M.; Luo, C. Health care cybersecurity challenges and solutions under the climate of COVID-19: Scoping review. J. Med. Internet Res. 2021, 23, e21747. [Google Scholar] [CrossRef]
- Chen, M.; Decary, M. Artificial intelligence in healthcare: An essential guide for health leaders. In Healthcare Management Forum; SAGE Publications: Los Angeles, CA, USA, 2020; Volume 33, pp. 10–18. [Google Scholar]
- Buzdugan, A. Integration of cyber security in healthcare equipment. In Proceedings of the 4th International Conference on Nanotechnologies and Biomedical Engineering, ICNBME-2019, Chisinau, Moldova, 18–21 September 2019; Springer International Publishing: Cham, Switzerland, 2020; pp. 681–684. [Google Scholar]
- Eichelberg, M.; Kleber, K.; Kämmerer, M. Cybersecurity in PACS and medical imaging: An overview. J. Digit. Imaging 2020, 33, 1527–1542. [Google Scholar] [CrossRef] [PubMed]
- Kim, D.W.; Choi, J.Y.; Han, K.H. Medical device safety management using cybersecurity risk analysis. IEEE Access 2020, 8, 115370–115382. [Google Scholar] [CrossRef]
- Hathaliya, J.J.; Tanwar, S. An exhaustive survey on security and privacy issues in Healthcare 4.0. Comput. Commun. 2020, 153, 311–335. [Google Scholar] [CrossRef]
- Gordon, W.J.; Wright, A.; Aiyagari, R.; Corbo, L.; Glynn, R.J.; Kadakia, J.; Kufahl, J.; Mazzone, C.; Noga, J.; Parkulo, M.; et al. Assessment of employee susceptibility to phishing attacks at US health care institutions. JAMA Netw. Open 2019, 2, e190393. [Google Scholar] [CrossRef]
- Jalali, M.S.; Razak, S.; Gordon, W.; Perakslis, E.; Madnick, S. Health care and cybersecurity: Bibliometric analysis of the literature. J. Med. Internet Res. 2019, 21, e12644. [Google Scholar] [CrossRef]
- Yaqoob, T.; Abbas, H.; Atiquzzaman, M. Security Vulnerabilities, Attacks, Countermeasures, and Regulations of Networked Medical Devices—A Review. IEEE Commun. Surv. Tutor. 2019, 21, 3723–3768. [Google Scholar] [CrossRef]
- Holdsworth, J.; Glisson, W.B.; Choo, K.K.R. Medical device vulnerability mitigation effort gap analysis taxonomy. Smart Health 2019, 12, 82–98. [Google Scholar] [CrossRef]
- Yaqoob, T.; Abbas, H.; Shafqat, N. Integrated security, safety, and privacy risk assessment framework for medical devices. IEEE J. Biomed. Health Inform. 2019, 24, 1752–1761. [Google Scholar] [CrossRef]
- Coventry, L.; Branley, D. Cybersecurity in healthcare: A narrative review of trends, threats and ways forward. Maturitas 2018, 113, 48–52. [Google Scholar] [CrossRef]
- Jalali, M.S.; Kaiser, J.P. Cybersecurity in hospitals: A systematic, organizational perspective. J. Med. Internet Res. 2018, 20, e10059. [Google Scholar] [CrossRef]
- Djenna, A.; Saïdouni, D.E. Cyber attacks classification in IoT-based-healthcare infrastructure. In Proceedings of the 2018 2nd Cyber Security in Networking Conference (CSNet), Paris, France, 24–26 October 2018; pp. 1–4. [Google Scholar]
- Strielkina, A.; Illiashenko, O.; Zhydenko, M.; Uzun, D. Cybersecurity of healthcare IoT-based systems: Regulation and case-oriented assessment. In Proceedings of the 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, Ukraine, 24–27 May 2018; pp. 67–73. [Google Scholar]
- Kruse, C.S.; Frederick, B.; Jacobson, T.; Monticone, D.K. Cybersecurity in healthcare: A systematic review of modern threats and trends. Technol. Health Care 2017, 25, 1–10. [Google Scholar] [CrossRef] [PubMed]
- CVE.ORG. CVE. Available online: https://www.cve.org/About/Overview (accessed on 24 June 2024).
| Normative | Key Variables |
|---|---|
| ISO 27701 | Privacy Information Management, Personal Data, Medical Devices |
| ISO/IEC 27799 | Health Information Security, Personal Health Information (PII), Healthcare Sector |
| ISO 13485 | Quality Management Systems, Risk Management, Medical Devices, Software Security |
| ISO/IEC 27001 | Information Security Management, Sensitive Information, ISMS (Information Security Management System) |
| ISO/IEC 82304-1 | Health Software, Quality Requirements, Safety Requirements, Information Security Standards |
| ISO/IEC 27002 | Information Security Controls, Best Practices, Confidentiality, Integrity, Availability |
| ISO/IEC 80001-1 | Risk Management, IT Networks, Medical Devices, Interoperability, Information Security |
| Normative Standard | Key Variables Identified |
|---|---|
| NIST Cybersecurity Framework (CSF) | Cybersecurity in critical infrastructure—Risk management—Security protections—Continuous improvement of cybersecurity programs—Applications in medical devices |
| NIST SP 800-63-3 | Digital identity—Authentication—Access control—Data privacy |
| NIST SP 800-53 Rev. 5 | Security controls—Information privacy—Information system protection—Risk management for medical systems—Medical device information security |
| NIST SP 800-37 Rev. 2 | Risk management in medical devices—Cybersecurity throughout the lifecycle—Privacy risk management—Lifecycle-based security approach |
| NIST SP 1800-1 | Protection of electronic health records (EHRs)—Security in mobile and wearable devices—Protection of personal health data—Security architectures for mobile devices |
| NIST SP 800-82 Rev. 2 | Industrial Control Systems (ICS) security—Protection of medical devices in industrial environments—ICS risk management—Compliance with industrial security standards |
| NIST SP 800-88 Rev. 1 | Secure data disposal—Media sanitization—Protection of sensitive data in medical devices—Data disposal policies for medical devices |
| NIST SP 800-30 Rev. 1 | Risk assessment—Threat and vulnerability identification—Risk mitigation methods—Medical device security assessment |
| NIST SP 800-66 Rev. 1 | HIPAA compliance—Protection of protected health data—Security in handling medical data—Security rules for devices handling health information |
| Normative | Key Variables |
|---|---|
| HIPAA (1996) | Health insurance portability, fraud reduction, healthcare security, privacy standards, health info |
| Privacy Rule (2000) | Protected Health Information (PHI), data protection, use and disclosure limits, patient’s rights |
| Security Rule (2003) | Administrative security measures, physical security measures, technical security measures, PHI confidentiality, integrity, availability |
| National Identifier Rule (2004) | PHI security measures, identifier standards, administrative security, technical security |
| Transactions and Codes Rule (2000) | Electronic healthcare transactions, healthcare codes, standardization, administrative processes |
| Breach Notification Rule (2009) | PHI breach notification, affected individuals, HHS notification, media notification, unsecured PHI breach |
| Normative | Key Variables |
|---|---|
| Good practices for the security of healthcare services | Security in professional services, Consulting, Audits, Technical support, Cybersecurity training, Restricted access policies, Continuous risk management |
| Remote care systems | Telemedicine, Remote patient monitoring, Secure connections, Robust authentication, Protection of personal and health data |
| Building management systems | Physical infrastructure of buildings, HVAC management, Lighting, Security, Network segmentation, Continuous monitoring, Software updates |
| Clinical information systems | Clinical information, Electronic Health Records (EHRs/EMRs), Role-based access control, Data encryption, Audit of access and modifications |
| Cloud services | Cloud services, Health data storage, Vendor security assessment, Encryption, Disaster recovery plans |
| Identification systems | Identity verification, Multi-factor authentication, Identity management, Monitoring of authentication activities |
| Industrial control systems | Industrial processes in healthcare facilities, Network segmentation, Real-time monitoring, Regular system updates |
| Medical devices | Connected medical devices, Patient data management, Security by design, Data encryption, Threat monitoring |
| Mobile client devices | Mobile devices in healthcare, Secure applications, Mobile device management policies, Malware protection |
| Network equipment | Network equipment in healthcare IT infrastructure, Firewalls, Network segmentation, Firmware and software updates |
| Key Variables | Description |
|---|---|
| Fundamental Principles | Since its adoption in 2016 and enforcement in 2018, the GDPR has established principles for processing personal data, ensuring that it is lawful, fair, transparent, and limited to specific purposes. |
| Informed Consent | Requires that users expressly, informally, and freely consent to the processing of personal data, especially in the sensitive context of medical data. |
| Rights of Interested Parties | Ensures rights such as access, rectification, erasure, and data portability, allowing individuals to control their personal information. |
| Data Security | Requires the implementation of appropriate technical and organizational measures to protect personal data against loss or unauthorized access, which is essential for medical devices handling sensitive data. |
| Data Protection Impact Assessments (DPIA) | Establishes the need to conduct impact assessments when data processing involves high risks to individuals’ rights and freedoms, including situations that may arise with medical devices. |
| Responsibility and Compliance | Manufacturers and suppliers must demonstrate compliance with GDPR requirements, maintain records of processing activities, and cooperate with data protection authorities. |
| Category | Variables Key |
|---|---|
| Adaptability and Customization | Adaptability |
| Compliance and Certification | Assessment and Certification |
| Structure and Controls | Control-Based Structure |
| Approach to Security | Integral Approach |
| Sector Application | Multi-Sectoral Application |
| Risk Management | Risk Management Orientation |
| CVE | Model | Type of Attack | Normatives |
|---|---|---|---|
| CVE-2025-2230 | Philips Intellispace Cardiovascular | Replay attacks, authentication bypass | HITRUST: AC-1, AC-4; NIST SP 800-53: AC-2; ISO 27001: A.9.1 |
| CVE-2025-2229 | Philips Intellispace Cardiovascular | Fixed AES-128 encryption key vulnerability | HITRUST: AC-4, SC-7; GDPR: Art. 32; NIST SP 800-53: SC-12, SC-13 |
| CVE-2020-16237 | Philips SureSigns VS4 | Exploitable remotely | HITRUST: AC-4, SC-7; ISO 27001: A.13.1 |
| CVE-2020-16239 | Philips SureSigns VS4 | Exploitable remotely | HITRUST: AC-4, SC-7; ISO 27001: A.13.1 |
| CVE-2020-1624 | Philips SureSigns VS4 | Exploitable remotely | HITRUST: AC-4, SC-7; ISO 27001: A.13.1 |
| CVE-2020-16216 | Philips IntelliVue MX700 and MX800 | Low attack complexity | HITRUST: AC-2, SC-5; NIST SP 800-53: AC-2 |
| CVE-2019-13530 | Philips IntelliVue MX700 and MX800 | Hard-coded password, code download without integrity check | HITRUST: SI-1, AC-6; NIST SP 800-53: AC-5, SC-8; ISO 27001: A.14.2.5 |
| CVE-2020-16214 | Philips IntelliVue MX100 | Low attack complexity | HITRUST: AC-2, SC-5; NIST SP 800-53: AC-2 |
| CVE-2018-19001 | Philips HealthSuite Health Android App, all versions | Inadequate encryption strength | HITRUST: SC-13, AC-12; NIST SP 800-53: SC-12, SC-13; GDPR: Art. 32 |
| CVE-2021-33017 | Philips IntelliBridge EC 40 and 60 Hub | Authentication bypass using an alternate path or channel | HITRUST: AC-1, AC-4; NIST SP 800-53: AC-2 |
| CVE-2022-0922 | Philips E-alert Firmware | No authentication for critical system functionality | HITRUST: AC-4, SC-12; NIST SP 800-53: AC-2 |
| CVE-2018-14803 | Philips E-alert Firmware | Unauthorized disclosure of system information via HTTP headers | HITRUST: AC-5, SC-4; NIST SP 800-53: SC-12; ISO 27001: A.10.1 |
| CVE-2020-6961 | GE Healthcare GE CARESCAPE B450/B650/B850 | Exploitable remotely, low skill level | HITRUST: AC-4, SC-7; NIST SP 800-53: AC-2; ISO 27001: A.13.1 |
| CVE-2020-6962 | GE Healthcare GE CARESCAPE B450/B650/B850 | Exploitable remotely, low skill level | HITRUST: AC-4, SC-7; NIST SP 800-53: AC-2; ISO 27001: A.13.1 |
| CVE-2020-6963 | GE Healthcare GE CARESCAPE B450/B650/B850 | Exploitable remotely, low skill level | HITRUST: AC-4, SC-7; NIST SP 800-53: AC-2; ISO 27001: A.13.1 |
| CVE-2020-6964 | GE Healthcare GE CARESCAPE B450/B650/B850 | Exploitable remotely, low skill level | HITRUST: AC-4, SC-7; NIST SP 800-53: AC-2; ISO 27001: A.13.1 |
| CVE-2020-6966 | GE Healthcare GE CARESCAPE B450/B650/B850 | Exploitable remotely, low skill level | HITRUST: AC-4, SC-7; NIST SP 800-53: AC-2; ISO 27001: A.13.1 |
| CVE-2024-27106 | GE Healthcare EchoPAC | Exploitation activity | HITRUST: AC-5, SI-1; NIST SP 800-53: AC-5, SI-2 |
| CVE-2024-1628 | GE Healthcare Ultrasound devices | OS command injection vulnerabilities | HITRUST: SI-2, AC-5; NIST SP 800-53: SI-3, AC-4 |
| CVE-2020-25179 | GE Healthcare Imaging and Ultrasound Products | Information leak | HITRUST: SI-3; NIST SP 800-53: SI-3; ISO 27001: A.10.1 |
| CVE-2024-3094 | GE Healthcare XZ Utils | Embedded malicious code | HITRUST: AC-4, SC-7; NIST SP 800-53: AC-4, SI-7 |
| CVE-2021-27410 | Welch Allyn Spot Vital Signs 4400 | Exploitable remotely | HITRUST: AC-4, SC-7; ISO 27001: A.13.1 |
| CVE-2021-27408 | Welch Allyn Spot Vital Signs 4400 | Exploitable remotely | HITRUST: AC-4, SC-7; ISO 27001: A.13.1 |
| CVE-2024-1275 | Welch Allyn Vital Signs Monitor | Exploitable remotely | HITRUST: AC-4, SC-7; ISO 27001: A.13.1 |
| CVE-2019-6446 | Dräger Infinity® Delta Series | Probability of exploitation activity | HITRUST: SI-2, SC-5; NIST SP 800-53: SI-4, SC-7 |
| CVE-2024-23619 | IBM Merge Healthcare eFilm Workstation | Execute code | HITRUST: SI-1, AC-5; NIST SP 800-53: SI-5, AC-6 |
| CVE-2024-23622 | IBM Merge Healthcare eFilm Workstation | Buffer overflow | HITRUST: SC-8, SI-5; NIST SP 800-53: SC-7, SI-7 |
| CVE-2024-23621 | IBM Merge Healthcare eFilm Workstation | Buffer overflow | HITRUST: SC-8, SI-5; NIST SP 800-53: SC-7, SI-7 |
| CVE-2024-38348 | CodeProjects Health Care hospital Management System v1.0 | SQL injection vulnerability | HITRUST: AC-6, SI-1; NIST SP 800-53: SI-3, AC-4 |
| CVE-2024-38347 | CodeProjects Health Care hospital Management System v1.0 | SQL injection vulnerability | HITRUST: AC-6, SI-1; NIST SP 800-53: SI-3, AC-4 |
| CVE-2025-0683 | Contec Health CMS8000 Patient Monitor | Exposure of private personal information | HITRUST: SI-1, AC-5; NIST SP 800-53: AC-2, SI-4 |
| CVE-2025-1204 | Contec Health CMS8000 Patient Monitor | Hidden functionality | HITRUST: AC-6, SC-5; NIST SP 800-53: AC-5 |
| CVE-2025-0626 | Contec Health CMS8000 Patient Monitor | Attempts to bypass network settings | HITRUST: SC-5, AC-4; NIST SP 800-53: AC-4, SC-7 |
| CVE-2024-12703 | Schneider Electric SE RemoteConnect and SCADAPackTM x70 Utilities | Remote code execution via deserialization | HITRUST: AC-5, SC-7; NIST SP 800-53: SI-5, SC-8 |
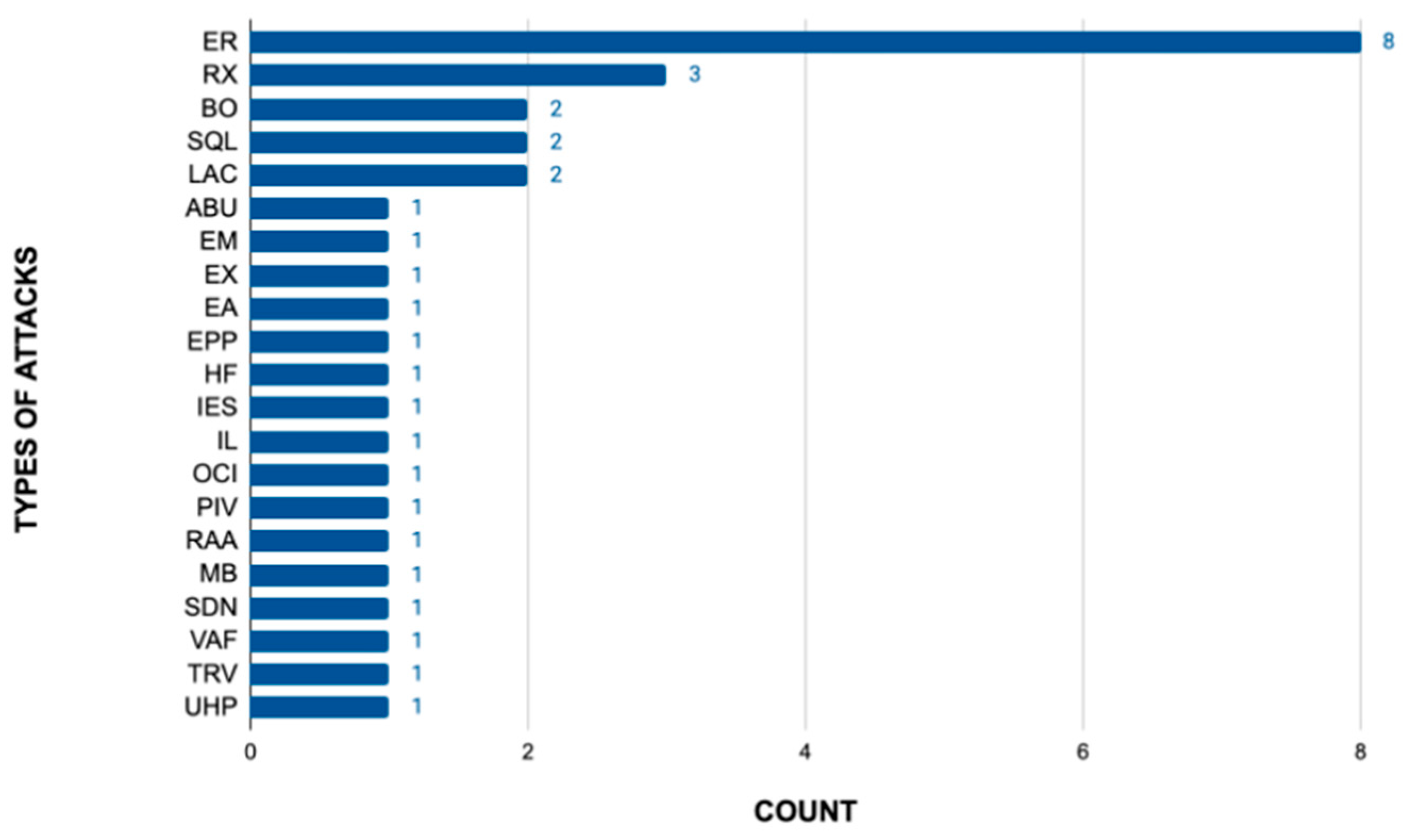
| Types of Attacks | Abbreviation |
|---|---|
| Exploitable remotely/low skill level to exploit | ER |
| Remote exploit | RX |
| Buffer overflow | BO |
| SQL injection vulnerability | SQL |
| Low attack complexity | LAC |
| Authentication bypass using an alternate path or channel | ABU |
| Embedded malicious code | EM |
| Execute code | EX |
| Exploitation activity | EA |
| Exposure of private personal information to an unauthorized actor | EPP |
| Hidden functionality | HF |
| Inadequate encryption strength | IES |
| Information leak | IL |
| OS command injection vulnerabilities | OCI |
| Probability of exploitation activity | PIV |
| Replay attacks and authentication bypass | RAA |
| The “monitor” binary in the firmware of the affected product attempts to mount to a hard-coded, routable IP address | MB |
| The software does not perform any authentication for critical system functionality | SDN |
| The vulnerability allows for an unauthorized disclosure of system information through HTTP headers | VAF |
| Token reuse vulnerability | TRV |
| Use of hard-coded password, download of code without integrity check | UHP |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ulloa-Zamora, M.; Barría-Huidobro, C.; Sánchez-Rubio, M.; Galeazzi, L. Integral Security Pillars for Medical Devices: A Comprehensive Analysis. Appl. Sci. 2025, 15, 6634. https://doi.org/10.3390/app15126634
Ulloa-Zamora M, Barría-Huidobro C, Sánchez-Rubio M, Galeazzi L. Integral Security Pillars for Medical Devices: A Comprehensive Analysis. Applied Sciences. 2025; 15(12):6634. https://doi.org/10.3390/app15126634
Chicago/Turabian StyleUlloa-Zamora, Marcela, Cristian Barría-Huidobro, Manuel Sánchez-Rubio, and Lorena Galeazzi. 2025. "Integral Security Pillars for Medical Devices: A Comprehensive Analysis" Applied Sciences 15, no. 12: 6634. https://doi.org/10.3390/app15126634
APA StyleUlloa-Zamora, M., Barría-Huidobro, C., Sánchez-Rubio, M., & Galeazzi, L. (2025). Integral Security Pillars for Medical Devices: A Comprehensive Analysis. Applied Sciences, 15(12), 6634. https://doi.org/10.3390/app15126634





