Abstract
Self-sovereign identity (SSI) is an emerging model for digital identity management that empowers individuals to control their credentials without reliance on centralized authorities. This work presents YouGovern, a blockchain-based SSI system deployed on Binance Smart Chain (BSC) and compliant with W3C Decentralized Identifier (DID) standards. The architecture includes smart contracts for access control, decentralized storage using the Inter Planetary File System (IPFS), and long-term persistence via Web3.Storage. YouGovern enables users to register, share, and revoke identities while preserving privacy and auditability. The system supports role-based permissions, verifiable claims, and cryptographic key rotation. Performance was evaluated using Ganache and Hardhat under controlled stress tests, measuring transaction latency, throughput, and gas efficiency. Results indicate an average DID registration latency of 0.94 s and a peak throughput of 12.5 transactions per second. Compared to existing SSI systems like Sovrin and uPort, YouGovern offers improved revocation handling, lower operational costs, and seamless integration with decentralized storage. The system is designed for portability and real-world deployment in academic, municipal, or governmental settings.
1. Introduction
Identification and authentication mechanisms are fundamental in both the physical and digital realms, acting as the cornerstones of security and access control [1,2]. In the physical world, governments issue official documents such as passports, driver’s licenses, and national IDs, which serve as definitive proof of an individual’s identity [3]. Conversely, in the digital realm, major corporations like Google, Facebook, and Microsoft provide authentication services that manage user identities across various platforms [4,5]. The global self-sovereign identity (SSI) market is experiencing rapid growth, driven by the increasing demand for secure and user-centric digital identity solutions. Recent projections indicate that the market will expand from USD 3.49 billion in 2025 to approximately USD 1153.07 billion by 2034, reflecting a CAGR of 90.52% during this period [6]. This surge is attributed to rising concerns over data privacy, the proliferation of digital services, and the need for robust identity verification mechanisms. These digital identities allow users to access services, perform transactions, and interact online with a semblance of security. However, this centralized control also means that these entities have the power to modify, revoke, or misuse identity privileges, often without the user’s consent or knowledge, posing significant risks to privacy and autonomy [7,8].
The Internet is such a valuable tool in our daily lives. We use it to access media, connect with friends and colleagues, manage finances, learn, and more. Still, the web, as we know it, implements centralized models to access this information. To a high degree, it is on servers and is operated by corporations. Centralization may pose a main concern for censorship [9,10]. Since the content is hosted on just a few sites, it is easier for governments to block it. In 2017, the Turkish government ordered Internet providers to block Wikipedia due to its unfavorable representation of the country [11]. Centralization of the web is not a positive thing, but it was adopted because of what it can offer. The users want pages to load in an instant, and everything must be provided with the highest quality possible. Server centralization allows for full control of how quickly the content can be provided. As privacy is continuously coming to the foreground and is emerging as one of the main users’ (and citizens’) requirements, distributed models are attracting attention [12].
The 2016 Report of the UN Special Rapporteur on Freedom of Opinion and Expression is a strong statement of the importance of freedom of expression on the Internet [13]. Once blocking lists are introduced, they can grow. There have been attempts to block sites containing not only hate speech and advocacy of terrorism, but also political debate, information on minority rights, alleged defamation, purported copyright infringement—even the “sacred texts” of Scientology. Data misuse occurs when individuals or organizations use personal data beyond their stated intentions.
A “Self-Sovereign Identity (SSI)” is an identity that is not dependent on any central authority and cannot easily be removed by one administration [14]. On the contrary, SSI is an entirely distributed and portable digital identity [15]. It typically has six variables.
- An identity model in which its data is owned or controlled by any individual organization or thing—a centralized authority does not control it.
- The owner of the identity system cannot remove an identity.
- Identity owners retain all the personal information stored in their accounts.
- The system does not require an intrinsic authority to trust the nature of the integrity, protection, privacy, and identity of the owners—identity owners may use their data, as well as select who may access and manage their identity online.
- Modifications are easy to make for the challenge-response part (verification process).
- The transparency is preserved by rapidly providing six sections of the: (i) anchor, (ii) credibility, (iii) entity, (iv) self-limit, (v) zero-knowledge proof (ZKP), and (vi) ZKP itself.
The implementation of blockchain-based identity management models has extended the concept of the SSI paradigm to cover more than just cyberspace [16,17]. With SSI, people can take back control of their electronically distributed data whenever they choose. Blockchain-based SSI implies that full user control will take decentralized identity a step further by giving users control of their identifiers as well as their data [18]. The incorporation with official identification is another potential. For instance, the EU supports the verification of identities through the European electronic identities (eID) and the eIDAS regulation, tools, and mechanisms, as well as the International Civil Aviation Organization (ICAO) endorsed “ePassport” or electronically machine-readable travel documents (eMRTD) infrastructure. Now, there are several considerations to integrate these solutions and use them via a blockchain-based solution [18].
While the one who is in control of SSI is the individual, he/she can publish/disseminate information to the press, his/her employer, the healthcare services, security companies, etc. The user can give them whatever data they want and does not give them what he/she does not want. Identity and access control management methods have often changed over time, based on how much privacy they needed to maintain. Over time, there have been several such methods in which their confidentiality has increased over their evolution, such as centralized, federated, self-sovereign, and then blockchain-based self-sovereign. Security primitives, such as public-key encryption and hash functions, are exploited for the implementation of digital identity control. Among other functionalities, they can assure identity-based records’ authenticity, attest to their records’ integrity, and share records with smart contracts.
The long-term goals of self-sovereign identity are [18,19]:
- Decentralization allows entities to manage themselves and eliminates unnecessary targets or single points of failure. It will enable you to control your digital identifiers without relying on external authorities to access your data and sell it to others.
- Privacy enhances the security of data.
- Security enables a necessary degree of trust in decentralized identifier (DID) documents.
- Proof-of-stake allows DIDs to provide identity and information integrity when communicating.
- Discoverability increases entities’ ability to find their self-identity.
- Interoperability allows existing tools and software to be used.
- The portability system is system-agnostic, independent, and able to support all types of DIDs and DID methods.
- Simplicity means it is easy to understand, implement, deploy, and maintain the technology.
Credentials, including verification information, are securely stored and are readable by computers. This system offers users the opportunity to maintain their own identities. Documentation requires attestation from another party, but it is attested by the self as well. Documents are signed using digital certificates. The signature provides proof that the identity of the cardholder is genuine. The public key is verified by confirming the private key belonging to the credential’s owner. Verifiers trust the issuer; therefore, they approve the certificate.
Decentralized identity mechanisms will have a significant impact on business operations and government policymaking in the coming decade [20]. DID uses public-key cryptography to ensure its security (a public and an associated private key). For verifiable claims, DID is enabled for digitally signed verification. An entity issues a bond to a buyer. Several elements are involved in a DID verification, such as a decentralized identifier, a signing key, a collection of authentication methods, a timestamp, and a signature (for integrity). Many projects in the industry, including early ecosystems and consortia, are following this approach, like the decentralized identity base (DIF), Indy Project, Aries Project, and the W3C solution [21]. In some cases, SSI makes sense as a more secure way to authenticate transactions. Critical streamlining workflows lacking standardization of data and communication credentials can be useful in another personal context. Data is a liability and a customer-driven workflow.
The central problem addressed by this work is the lack of user-controlled identity systems that are scalable, cost-effective, and compatible with decentralized infrastructure. Existing solutions often depend on centralized verification authorities, lack revocation mechanisms, or operate within permissioned environments. This paper aims to design, implement, and evaluate a decentralized self-sovereign identity system that supports verifiable credentials, privacy-preserving access control, and standards-based interoperability. The core research objective is to assess whether a fully decentralized SSI framework can be realized on a semi-decentralized blockchain, i.e., the Binance Smart Chain (BSC) [22], while maintaining low operational costs and compliance with W3C specifications. The guiding hypothesis is that such a system can offer practical advantages over existing frameworks by balancing decentralization, usability, and performance.
In this paper, we present YouGovern—a blockchain-based SSI. It was developed as a decentralized application that runs on the BSC network. YouGovern is designed as a standards-compliant prototype that implements core principles of self-sovereign identity (SSI). The system focuses on four primary objectives [23,24]: secure credential issuance, privacy-preserving access control, interoperability with decentralized web technologies, and practical deployability. The architecture integrates W3C-compliant decentralized identifiers (DIDs), smart contract–based role enforcement, and decentralized storage through IPFS and Web3.Storage. Although the current implementation is a prototype, its modular structure and use of widely supported blockchain components allow it to be extended or adapted for production use in governmental, educational, or civic contexts. The decentralized application enables users to upload their data to the blockchain. Then, everyone (e.g., an authority or a digital service) who wants to gain access makes a related request, and the owner authorizes or declines this action. The whole procedure is transparent and is visualized to the user. To validate that the smart contract is secure and legal for the blockchain, several tests were utilized. A client-side framework was created that enables users to communicate with our smart contract by connecting to the network, which provides them with guidance on what to do. This work does not aim to introduce new cryptographic models or consensus algorithms but instead offers a practical, deployable SSI system that integrates and operationalizes existing standards to address real-world identity challenges.
The rest of the manuscript is structured as follows. Section 2 presents prior work and relevant literature. Section 3, Section 4 and Section 5 describe the design, implementation, and experimental evaluation of the proposed SSI solution. Section 6 discusses this work and future extensions. Finally, Section 7 concludes this study.
2. Background Theory and Related Works
This section reviews the history of Web Applications, particularly decentralized ones. Decentralized applications are now building on blockchains, which allow many programs to run when a rule is met. It also points to similar decentralized web applications that will be compared with our work.
2.1. Background Theory
2.1.1. Centralized Approach—Web Application Paradigm
Usually, when someone communicates with a web application, a browser must talk to the network’s central server [25]. The application’s code will be stored on one server, and this data will be held in a centralized database, as shown in Figure 1. Also, if anyone tries to use the application, he/she need to speak to the central server. It is how a web application works; it is not useful to create an SSI this way. Firstly, since all the data in the database might change at any moment, the users’ information could shift, or it could be entirely deleted. Secondly, the framework code could change at any moment, which implies that SSI principles could change. It is incorrect to construct a centralized SSI application because of these problems. Therefore, a decentralized application has to be developed to solve the issues and ensure users’ integrity, privacy, and anonymity.
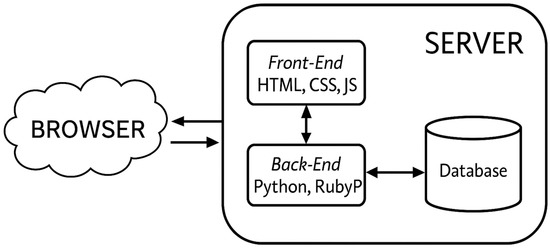
Figure 1.
Ordinary web application.
2.1.2. Distributed Approach—Blockchain Solution
Blockchain solves these issues, and it is a safer option to create an SSI identity application [26,27]. Not all the data is stored on the central server, but it is decentralized instead [28,29]. It is distributed through any computer connected to the blockchain. When connected to the blockchain network, the computer acts as a node. The computer is part of the blockchain network, as shown in Figure 2. It communicates to all other nodes, which share some of the same responsibilities as a web server in the centralized approach. Blockchain uses a public, distributed ledger, which means storing all information within a distributed data storage network (a block). In the distributed public ledger, both the network nodes act simultaneously to ensure the security of all public ledger data [30]. This is crucial to an SSI application because it ensures that it will always be known that an account has submitted the transaction every time a user submits critical information.
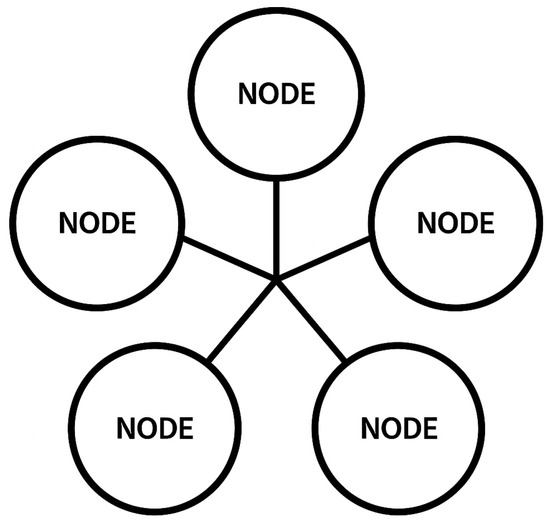
Figure 2.
Blockchain network.
It will also provide confidence that the information will be saved to the correct user and will be registered forever. Since all the data is exchanged through blockchain devices, the blockchain is a database. Since all the nodes connect on the blockchain to each other, it is also a network. Instead of a conventional web model, someone might think of blockchain as a network and database all in one. Consequently, it is far easier to construct our SSI application on the blockchain in this decentralized way so that someone can use it confidently.
As we previously mentioned, all the data on the BSC blockchain is decentralized and secured. Code on the blockchain is considered public and cannot be altered [31], which means that people can write code on the blockchain, and it will be immediately downloaded and executed by other nodes in the network.
2.1.3. Smart Contract
BSC allows developers to write code that will be executed on a BSC virtual machine with smart contracts [22]. It is where all the business logic and our application will lie. All code is written; it is responsible for the reading and writing of value transfer data and the execution of any business logic that has been programmed [8,32]. A smart contract is like a web-based microservice. The Smart Contract is a utility that controls the data stored in the blockchain. It is also a smart contract because it reflects what happened earlier as part of the insurance application. A contract in which users can upload their files, and once they do, they must permit someone else to access them. Smart contracts are written in the BSC and coded with a specific programming language known as Solidity [33]. Solidity will be used by YouGovern to construct distributed applications (dapps) and smart contracts.
These are the lines of code that are deposited on an Ethereum Virtual Machine (EVM) [23]. It executes automatically when prearranged conditions are met. However, at the most rudimentary level, they are computer programs that run as they have been set up to run by the individuals who developed them. The advantage of smart contracts is most apparent in business associations [34]. In this way, they are usually used to enforce some type of agreement so that all contributors can be certain of the outcome without an intercessor’s involvement.
However, the easiest way to clarify what a smart contract ensures is through an example. If we have ever bought a car at a dealership, there are numerous steps involved, and it can be an annoying process. If one cannot pay for the car outright, he/she will have to get financing. This may require a credit check, and he/she will have to fill out numerous forms with personal information to verify his/her identity. Literally, this buyer will have to interact with many different people, plus the salesperson, money broker, and lender. To be paid for their work, several commissions are added to the actual price of the car. Henceforth, it could be seen as a network of nodes or computers that executes the actions when programmed conditions have been met and confirmed, like releasing funds to the parties, registering a car, sending or receiving notifications, etc. The blockchain is then effective once the transaction is confirmed.
For a second example, let’s assume that Alex and Ben bet on whether it will rain or not. Alex says there will be rain tomorrow, while Ben says it will not rain tomorrow. They strike a bargain that if there is rain tomorrow, then Ben must pay Alex $10, and if there is no rain tomorrow, then Alex must pay $10 to Ben. However, if Ben loses and refuses to pay the $10 as they both agreed, then what can they do without fighting? An alternative way can be to go to a lawyer to make the agreement legal. If one refuses to pay, they will have to go to jail or pay a fine, such as an extra $10. Remember, they must also pay for the lawyer and any legal papers. This is costly. A smart contract would be a better solution. When certain conditions are met, the smart contract will pay the money to the winner. There will be no fighting and no need to pay any third-party expenses. Everything will be reliable and accurate with fewer expenses.
As a last example, one can consider the case of renting an apartment. If the person living in an apartment does not pay before the fifth of the coming month, then he/she will lose access to that apartment. The smart contract would automatically revoke his/her access to that apartment.
2.1.4. Account in BSC
This subsection further presents the technical details of the BSC regarding the supported account types. There are two types of accounts (externally owned and contract accounts) as they are described in the two following subsections, respectively.
Externally Owned Accounts
Externally Owned Accounts (EOAs) are considered user-type accounts (for users) and are linked to a cryptographic key pair created upon account creation. An EOA has a public key and a private key. It is identified by a wallet address (what a wallet is will be discussed later) and accessed by a private key. The individuals who hold this private key can transfer signed transactions and Ether from this account.
However, a public key is used to reference the account and call externally owned account addresses, whereas the private key on the other side is used to sign a transaction before executing any kind of transaction on the network to prove validity. EOA has balances that hold Ether cryptocurrency.
Contract Accounts
A smart contract is a kind of account that is controlled and operated by an EOA. When a smart contract is deployed in BSC, it is executed by EVM on nodes. A smart contract is considered an independent agent executed by the EVM BSC virtual machine and is a core foundation and the main building block of any decentralized application (dapp). Once the code is deployed on the blockchain, the BSC virtual machine will maintain this and run it when invoked by EOA.
Dapp is a distributed application; it is distributed in every way. Data sharing in the Peer-to-Peer (P2P) network is done across devices in the network, and it is decentralized. A user-side application can be developed, containing a web page developed in the markup language HyperText Markup Language (HTML) and in the scripting languages CSS and JavaScript. In this case, instead of having a server operating the nodes locally, they will be connected to blockchain nodes built into a target point [35,36], as shown in Figure 3. The code for the decentralized application can be written with a smart contract. A local blockchain is used to support a smart contract. Accounts are allowed in the network to use the application and update the related personal information.
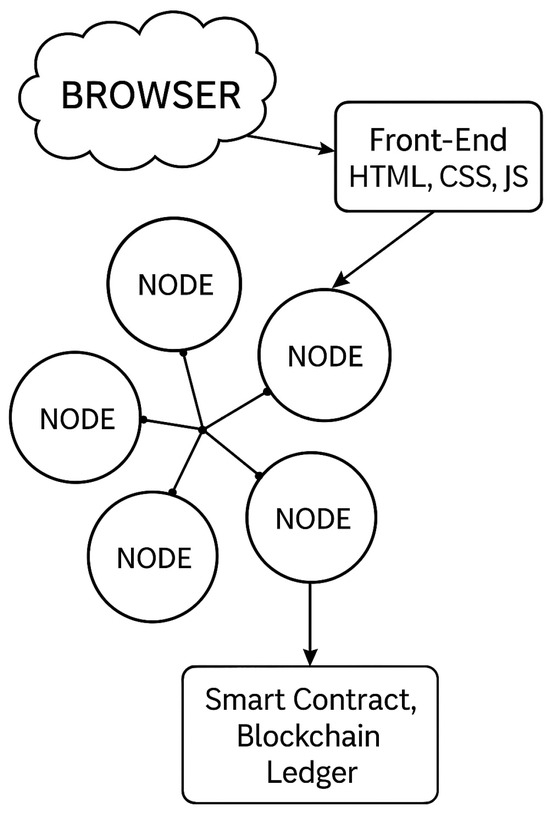
Figure 3.
Decentralized Web Application.
2.2. Related Work
Digital identity is an essential component of any digital platform. However, this field was one of the hardest to master and to adequately establish the identity of any individual on the web, as well as in the real world. Throughout the years, many Identity Management models have been used. No model has been able to establish the exact function of personal data storage and identity management until recently. The potential effects of globalization on identity have affected security, privacy, and safeguarding [37]. Many enhancements have been brought forth to SSI, including usability, security, and privacy for everyone who uses it. Besides, it stores all confidential information in a user-owned and managed Digital Wallet. Digital wallets are like physical wallets that contain all digital credentials. However, digital credentials are signed and verified digitally, more easily in the digital wallet than their physical counterparts.
The latest SSI frameworks do not include a mediator, only a person-to-person arrangement [38]. In the Federated IDM 2.0, for instance, two specifications have been proposed [39,40]. The two popular solutions [14], called uPort [41] and Sovrin [42], are compared and analyzed in Table 1. uPort has been built on the BSC public blockchain without authorization [41]. Sovrin has been built on the Hyperledger Indy, permitted by the public [42].

Table 1.
Correlation between uPort and Sovrin.
The new IDM 3.0 framework needs to be carefully evaluated for its various aspects. Christopher Allen suggested the Ten Principles for SSI [43], which provided an implementation framework for the concept of self-supreme identity. Furthermore, as shown in Table 2, the Sovrin Foundation [38] grouped in a white paper three categories: security, monitoring, and portability. However, in this sense, persistence does not interfere with Allen’s “right to be forgotten”. It may as well be listed separately since control and consent must be created, as well as access and removal of identity.

Table 2.
Principles of SSI.
Domain Name System–Identity Management (DNS–IdM) [44] is a scheme of Identity Management based on smart contracts. This helps users preserve their identities related to distinctive characteristics, achieving the self-sovereign concept. With respect to protection and privacy, DNS–IdM has promising results [44]. DNS–IdM can avoid traditional security threats and the drawbacks of existing decentralized identity management systems because of its decentralized existence. For identity management, this method provides a domain name system-like experience. A person can use real-world attributes of his/her identity via DNS–IdM to generate a digitized identification that can be used by various companies to authenticate a user and offer their services based on validated criteria. DNS–IdM varies from conventional schemes of identity management as well as the current advancements in the blockchain-based identity systems, by utilizing the blockchain as a trustworthy and stable network to store identities while using smart contracts to obtain identities from their respective recipients safely.
Most conventional schemes of Identity Management primarily focus on mediators to validate statements concerning identity characteristics that, once checked, remain true even though the beneficiaries have revoked or modified them. However, identity systems that are based on blockchain depend entirely on the users’ acknowledgment of their identification attributes or their approval of the details being monitored. DNS–IdM gives clients the ability to control their identification details. For suppliers of services, that would make it possible for any of them to utilize already presented identity attributes and to request them directly from beneficiaries through smart contracts when the needed features do not exist. The entire identity management process (e.g., the persistence of attributes, requests, and verification) is seamlessly enforced by integrating authorization and unauthorized blockchains with intelligent contracts. The blockchain’s intrinsic properties, including resistance, longevity, and traceability, render the DNS-IdM secure and trustworthy.
Recent innovations have introduced blockchain consensus models tailored for constrained environments such as wireless networks and 6G systems. For example, symbiotic blockchain consensus (SBC) leverages cognitive backscatter communication to enable sustainable consensus operations in power-limited and spectrum-constrained contexts [45,46]. While these designs primarily target network efficiency and spectrum sharing, their integration into identity frameworks could pave the way for ultra-lightweight decentralized identity in edge and IoT scenarios.
Existing SSI solutions such as uPort, Sovrin, and Microsoft ION offer varying degrees of decentralization, interoperability, and governance. However, these systems still exhibit significant limitations. uPort lacks native revocation mechanisms and fine-grained access control; Sovrin relies on a permissioned ledger, limiting its openness and scalability; and Microsoft ION, while decentralized, does not incorporate smart contract–based permission management or integrated data storage. Moreover, many existing systems do not offer seamless integration with decentralized file systems such as IPFS, limiting their flexibility in storing and sharing large verifiable credentials. These gaps highlight the need for a modular, low-cost, and access-controlled SSI framework—requirements addressed by YouGovern through its use of BSC, role-based smart contracts, and hybrid storage.
3. The YouGovern SSI Solution
3.1. Design
In the Design Stage, we will show the details for how the project will be managed and governed. Design differs from the Operational Planning Stage in that things at a higher level are about managing the YouGovern solution.
For example:
- How will decisions be made, and who has the authority?
- If the Implementation Phase must happen in August, then when does the money have to be secured to start?
- What staff training is required and when?
The following section presents the architecture of YouGovern.
3.2. Saving Data into Blockchain
A blockchain gathers information in groupings, often known as blocks, that hold sets of data. When a block’s storage capacity is reached, it is chained onto the previously filled block, producing a data chain known as the “blockchain” [47]. All new information that follows the newly added block is compiled into a newly formed block, which is then added to the chain once it is complete, as shown in Figure 4. It links all blocks by storing the previous hash and timestamp; the timestamp should be greater than the previous block. The transaction root contains the hash of the Merkle Tree, and the Merkle Tree has all hashed transactions in that block. This is called transaction processing; one can just check the validity of the block by checking the header hash of the block because the header hash contains the hash of all items in that block. In many cases, the blockchain is modelled as a chain of header hashes, and one header hash is connected to the previous header hash.
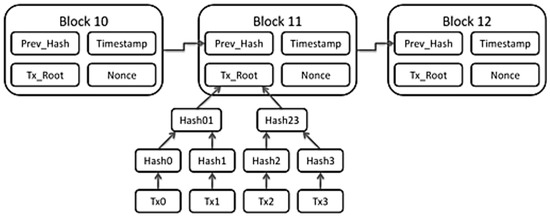
Figure 4.
Blockchain Storage Explanation.
3.3. Use Case Model
Use case models are models of how several types of users interrelate with the system to solve a problem. The use case model shown in Figure 5 defines the journey of the user to this web application. A user first signs in or signs up with his MetaMask account, and his address is recorded in the blockchain; he can also change their account address. Then he needs to enter all detailed information about himself. There is also an option to upload a file to IPFS, in which the hash of the file is internally stored in a smart contract. Now, other users can send a request to see that data by sending a request transaction from a function. Then the owner of the data will see the request, and he can accept or reject that request. If the user who requested the data gets his request approved, then he can download the file containing all the data for a particular user only.
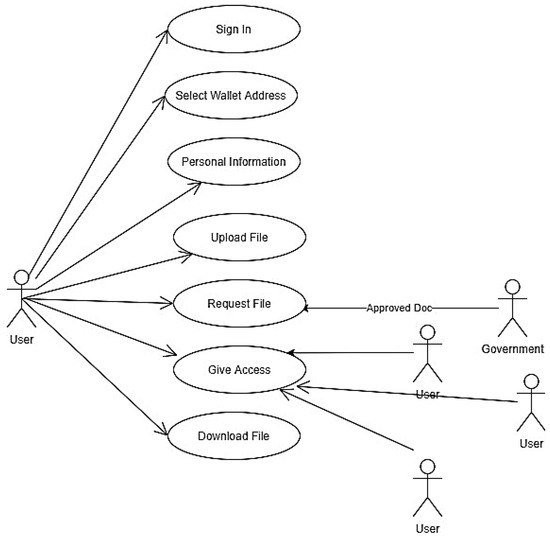
Figure 5.
Use Case Diagram with respect to the User.
3.4. Use Case Essential
The essential use case is also known as a business use case. It is a simplified, abstract, generalized use case that captures the intentions of a user in the desired technology and performs independently (Table 3).

Table 3.
Essential Use Cases.
3.5. Use Case Elaborated
Use cases are elaborated by adding details to the contact between the user and the software system, as shown in Figure 6. The user first signs in or signs up with his MetaMask account, and his address is recorded in the blockchain; he can also change his account address. Then he needs to enter all the detailed information about himself. There is also an option to upload a file to IPFS, in which the hash of the file is internally stored in a smart contract. Now, other users can send a request to see that data by sending a request transaction from a function. Then the owner of the data will see the request, and he can accept or reject that request. If the user who requested the data gets his request approved, then he can download the file containing all the data for a particular user only.
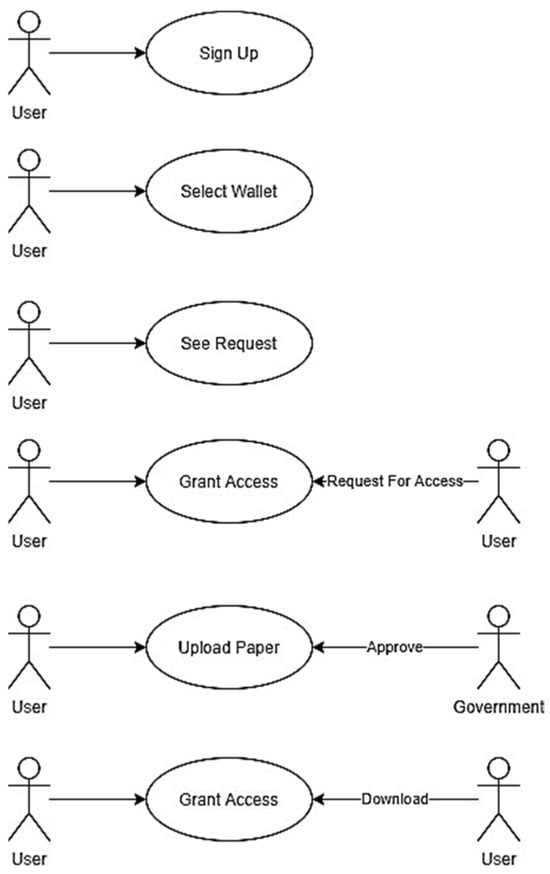
Figure 6.
Elaborated Use Cases.
In the context of YouGovern, an “authority” refers to a designated smart contract role or a verified blockchain address with the capability to issue or validate credentials. Verification occurs when the authority queries the DID registry and the content hash of the user’s credentials, checking integrity against IPFS-stored data. Only addresses registered in the trusted issuer list within the smart contract can perform verification or approval actions. This trust model is enforced cryptographically via signature validation and enforced access rules. For example, a university acting as an authority can verify a graduate’s credentials by calling the verification function, which cross-checks the DID, credential hash, and issuer identity.
4. Implementation
The YouGovern system is developed on Binance Smart Chain (BSC), leveraging smart contracts to establish a decentralized framework for self-sovereign identity management. This section details the technical implementation, including the development environment setup, smart contract deployment, and user interaction interfaces.
Figure 7 illustrates the overall architecture of YouGovern. The system comprises a web-based client, a suite of smart contracts deployed on BSC, a DID registry, and decentralized storage integrated with IPFS and Web3.Storage. User interactions—such as identity registration, credential issuance, or access revocation—are initiated from the browser interface and signed via MetaMask. Transactions are recorded on the blockchain, where smart contracts enforce permission rules and update the state of DID records. Metadata and verifiable credentials are serialized in JSON format and stored off-chain using IPFS, with content-addressable hashes linked on-chain. API interactions follow a RESTful schema, allowing standard HTTP calls to query DID status, retrieve credentials, or submit identity updates.
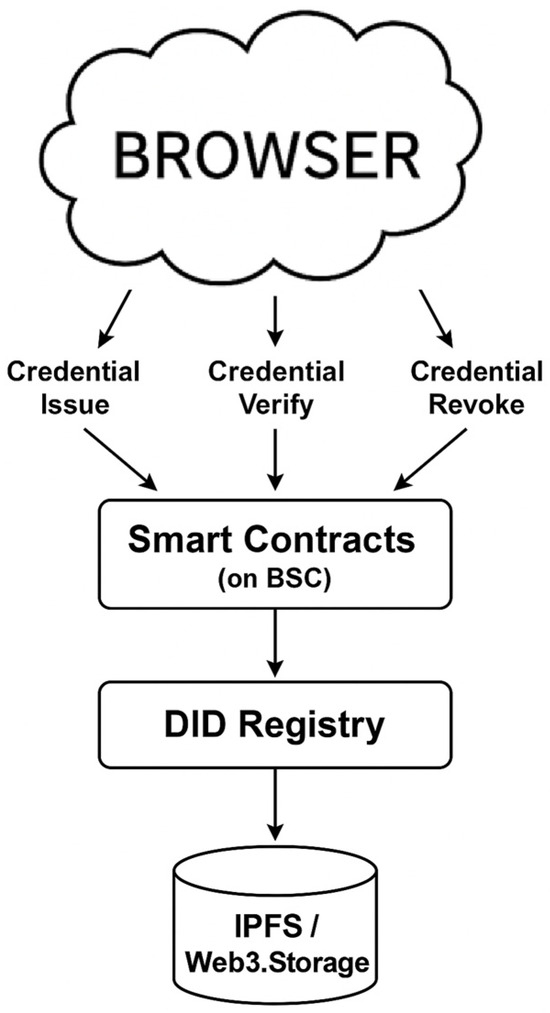
Figure 7.
YouGovern architecture.
4.1. Development Environment
YouGovern was developed using a robust technology stack to support the creation, testing, and deployment of smart contracts. The main tools include:
- Truffle Suite: Used for compiling, migrating, and testing smart contracts. It integrates with Ganache, a personal Ethereum blockchain that simulates various network conditions.
- Solidity: The programming language used to implement smart contracts on BSC, valued for its security features and suitability for contract-based logic.
- Node.js and npm: Serve as the runtime environment and package manager, respectively, facilitating the management of project dependencies.
- React.js: Used to develop a responsive, user-friendly front-end interface for interacting with the blockchain.
4.2. Smart Contract Deployment
Deploying smart contracts is important in establishing YouGovern on a secure and decentralized foundation. Deployment begins with contract initialization, during which roles and permissions are defined using the OpenZeppelin library to enforce secure role-based access control. The contract constructor sets up key roles such as administrators and validators, which are essential for system governance. Additionally, the contract logic is optimized to reduce gas costs by minimizing transaction data and streamlining computation.
4.3. User Interface and Interaction
The YouGovern user interface is designed to be intuitive and accessible, allowing users to manage their identities without requiring deep technical expertise.
- MetaMask Integration: A significant component of the YouGovern user interface is its integration with MetaMask (Figure 8), a widely used Ethereum wallet that facilitates secure and direct user interactions with the blockchain via a browser extension. MetaMask acts as a bridge between the browser and the BSC, allowing users to securely manage their identities and perform transactions without needing to trust third-party web servers. The interface guides users through the process of setting up MetaMask, ensuring they can securely sign transactions and authenticate their actions on the blockchain, thereby maintaining privacy and control over their data.
 Figure 8. MetaMask.
Figure 8. MetaMask. - InterPlanetary File System (IPFS): To enhance the security and decentralization aspects of identity management, YouGovern incorporates the IPFS, a peer-to-peer protocol for storing and sharing data in a distributed file system (Figure 9). IPFS is used to store identity documents and other user data in a way that ensures data permanence and reduces reliance on centralized storage solutions. When a user uploads a document, it is broken into blocks and distributed across the network, making it resilient to node failures and censorship. The integration of IPFS with YouGovern allows for a decentralized, owner-controlled storage solution, aligning with the principles of self-sovereign identity by giving users full control over their personal information.
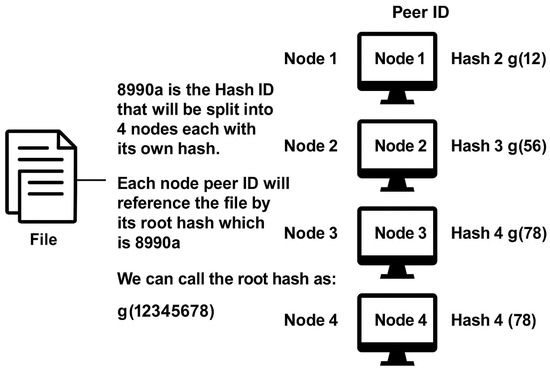 Figure 9. IPFS Structure.
Figure 9. IPFS Structure.
While IPFS enables decentralized content-addressed storage, it does not inherently ensure long-term data persistence. To address this, YouGovern integrates with Web3. Storage [48], which combines IPFS with Filecoin-based incentives to keep files pinned over time. This integration ensures that user-uploaded identity data remains reliably available across the network. Additionally, the system optionally supports encrypted backup storage through institutional nodes, such as public sector servers, providing a fallback in cases of widespread node unavailability. This hybrid model preserves user control and data sovereignty while enhancing resilience against data loss.
4.4. Testing and Security
Ensuring the reliability and security of the YouGovern platform involves comprehensive testing and security measures. All aspects of the smart contracts are covered by extensive testing using the Mocha and Chai frameworks, which help verify the functionality of all contract functions and their ability to handle errors effectively. Additionally, the smart contracts undergo rigorous security audits before launch to identify and rectify potential vulnerabilities, crucial for preventing issues like reentrancy attacks and ensuring the overall integrity of the platform.
To comply with the W3C DID specification, YouGovern includes mechanisms for revocation and key rotation. Each DID stored on-chain is associated with an active status and version history. In case of key compromise, a user can revoke the current key by submitting a “revokeDID()” transaction, which deactivates the identifier. A subsequent “rotateKey(newKey)” transaction can then bind a new public key to the same identity. These functions are built into the system’s smart contracts, ensuring transparency, traceability, and compliance with decentralized identity standards (see Listing 1).
| Listing 1. DID revocation sample code. |
| function revokeDID(address user) public onlyOwner { didRecords[user].active = false; emit DIDRevoked(user); } function rotateKey(address oldKey, address newKey) public onlyOwner { require(!didRecords[oldKey].active, "Old key must be revoked first"); didRecords[newKey] = didRecords[oldKey]; didRecords[newKey].active = true; emit KeyRotated(oldKey, newKey); } |
Access control in YouGovern is implemented through smart contract methods that allow users to authorize specific verifiers or entities to access selected credentials. The “grantAccess()” function allows a DID owner to whitelist an external address, while “verifyData()” allows verifiers to query authorized data (see Listing 2). These functions include appropriate role checks and event logging, and are protected by OpenZeppelin’s ReentrancyGuard to prevent recursive calls. We also ensure that gas limits are considered by optimizing contract storage and avoiding deep nesting in logic.
| Listing 2. Access control sample code. |
| mapping(address => mapping(address => bool)) public accessPermissions; function grantAccess(address verifier) public { accessPermissions[msg.sender][verifier] = true; emit AccessGranted(msg.sender, verifier); } function verifyData(address user) public view returns (string memory) { require(accessPermissions[user][msg.sender], "Access not granted"); return didRecords[user].dataHash; } |
4.5. Deployment and Real-World Application
Upon completion of testing, the YouGovern system is deployed on the BSC mainnet. The selection of this network is due to its compatibility with Ethereum tools, enhanced transaction speed, and reduced costs. Post-deployment, the system is continuously monitored for performance and security issues, with regular updates applied to address new security threats and enhance functionalities.
The user can create an account and log in to the platform. Figure 10 depicts YouGovern’s client dashboard. Thereupon, the user can start uploading IPFSs (Figure 11), where access to them will be managed by YouGovern.
Figure 10.
Client Dashboard.
Figure 11.
Upload IPFS.
5. Experimental Evaluation
The effectiveness of the YouGovern solution is critically assessed through comprehensive experimental evaluations, focusing on functionality, security, and user interaction within the self-sovereign identity framework. This section details the methodologies used in the testing phase, the results obtained, and the implications of these findings for the real-world application of the system.
5.1. Testing Framework and Methodology
The testing framework for YouGovern combined both automated and manual approaches to ensure a comprehensive evaluation of the system. Unit testing was carried out using the Mocha framework, allowing each smart contract component to be independently verified for correctness and reliability. These tests helped confirm that the contracts performed as intended across various scenarios and maintained proper interaction with the BSC. After unit testing, integration tests were conducted to evaluate how system components interacted, helping to detect any functional mismatches or performance issues.
At the same time, the React-based user interface underwent thorough usability testing to verify the proper functioning of graphical elements. This included checks for interface responsiveness, input validation, and the overall navigation flow to ensure a smooth user experience. To strengthen security, independent blockchain security firms conducted audits targeting potential vulnerabilities, such as reentrancy attacks, arithmetic overflows, and inadequate access control. Additionally, automated tools like MythX and OpenZeppelin were used for static analysis and security scanning, further reinforcing the system’s resilience against threats.
The experimental evaluation of YouGovern confirmed the reliability, usability, and security of the system across multiple dimensions. All smart contract components passed unit and integration tests without failure, and transactions were consistently processed with low latency on the Binance Smart Chain. The React-based interface was well-received in user testing, demonstrating clear navigation, efficient identity management, and responsive design. Security audits conducted by third-party firms revealed only low-severity issues, all of which were promptly addressed. No critical vulnerabilities were found, affirming the robustness of the design and implementation. User feedback highlighted the benefits of self-sovereignty, particularly in terms of privacy and control, while also praising the ease of use and intuitive interface.
These findings support YouGovern’s readiness for real-world deployment. The scalability and cost-efficiency of BSC provide a solid foundation for expanding the system to broader user bases without compromising performance. The secure architecture, combined with user-centric design, positions YouGovern as a compelling solution for decentralized identity management. Figure 12 and Figure 13 illustrate how governmental verification and access delegation processes are seamlessly handled within the platform. In summary, the detailed testing and evaluation of YouGovern underscore its efficacy as a self-sovereign identity solution, validating both its technical and functional capabilities and reinforcing its potential to revolutionize identity management practices globally.
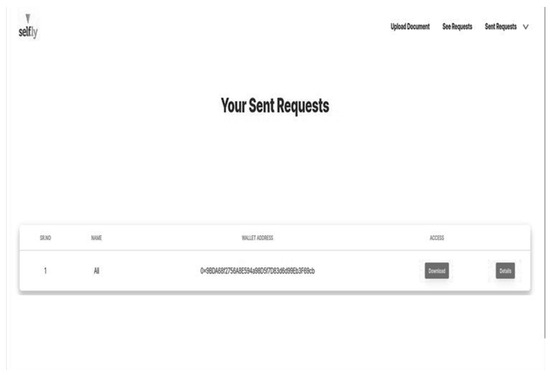
Figure 12.
Access request view.
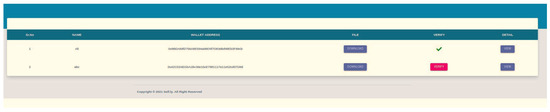
Figure 13.
Dashboard To Verify Data.
5.2. Comparative Evaluation of SSI Frameworks
To provide context for YouGovern’s capabilities, we compare its core architectural and operational features with four prominent SSI frameworks: Microsoft ION [49,50], Sovrin [42], uPort [41], and DNS-IdM [44]. Table 4 presents a summary of the comparison across key dimensions, including decentralization, revocation support, identity storage, interoperability, and transaction costs.

Table 4.
Comparison of SSI Frameworks.
Although YouGovern leverages a semi-decentralized blockchain (BSC) for scalability and cost-efficiency, it maintains strict compliance with W3C DID standards and supports advanced capabilities such as smart contract–based access control, revocation, and hybrid decentralized storage via Web3.Storage. Microsoft ION benefits from Bitcoin’s high decentralization and tamper resistance, but lacks integrated access control mechanisms and incurs slower confirmation times due to Bitcoin’s base-layer constraints. Sovrin introduces a well-defined governance framework and identity guardianship features, but is constrained by its permissioned validator pool, which may limit openness and inclusivity. In contrast, uPort simplifies identity creation using Ethereum and IPFS but lacks robust revocation and recovery processes. DNS-IdM provides a domain-name-centric identity layer but relies on centralized DNS updates and lacks decentralized credential verification. Collectively, these comparisons highlight YouGovern’s balance between operational autonomy, scalability, and compliance with SSI principles.
5.3. Security Threat Analysis and Mitigations
In addition to role-based access controls and DID compliance, YouGovern incorporates design strategies to defend against several high-severity threats common in decentralized identity systems. These include:
- Sybil Attacks: Although the current version of YouGovern does not implement on-chain identity weighting mechanisms, access to verification actions is restricted to registered validators and approved smart contract roles, limiting the scope of Sybil vector exploitation.
- Phishing and Smart Contract Spoofing: To prevent impersonation via malicious contracts, YouGovern uses contract whitelisting, ensuring users only interact with signed and verified entities. Smart contract addresses are transparently published and verifiable via BscScan.
- MetaMask Spoofing and UI Manipulation: The front-end integrates security cues such as address checksums, signer origin warnings, and verification badges for known DIDs to help users distinguish trusted connections. Enhanced UX patterns reduce the chance of user consent errors during transaction signing.
- Reentrancy and Input Validation: All critical functions, especially those involving state changes (e.g., identity revocation or access grants), are protected with OpenZeppelin’s ReentrancyGuard. Inputs are sanitized, and all authorization flows follow a checks-effects-interactions pattern to mitigate runtime manipulation.
5.4. Quantitative Cost Analysis
To assess the operational feasibility of the YouGovern system, we conducted a quantitative cost analysis focusing on gas consumption, decentralized storage overhead, and backend hosting requirements. Table 5 summarizes the estimated costs for the most common identity-related operations on the BSC and IPFS (as of April 2025, average gas price ~5 Gwei [51]).

Table 5.
Gas Costs on BSC.
Also, other infrastructure costs may include:
- IPFS and Storage Overhead:
- ○
- Average document size: 1 MB (e.g., encrypted identity document).
- ○
- Estimated IPFS/Filecoin storage cost via Web3.Storage: ~$0.02/month per document.
- ○
- Hybrid backup (institutional fallback node): negligible added cost when co-hosted.
- Hosting Infrastructure:
- ○
- The front-end (React-based) and API gateway (Node.js/Express) are designed for lightweight deployment using serverless or containerized environments (e.g., Heroku, Vercel, AWS Lambda).
- ○
- Monthly operational cost for a medium-scale deployment (~10,000 active users) is projected under $50/month when using a decentralized-first strategy with minimal centralized backup reliance.
These quantitative estimates demonstrate that the cost overhead of deploying and maintaining YouGovern is low enough to support wide-scale adoption, even for low-budget organizations such as municipalities, academic institutions, or NGOs.
5.5. Performance Simulation and Stress Testing
To evaluate the scalability and responsiveness of YouGovern under varying load conditions, we conducted a series of stress tests using Ganache and the Hardhat testing frameworks [52]. These tests simulated concurrent user operations, such as identity creation, permission grants, and data verifications, executed in short bursts to assess system behavior under pressure.
The test environment was implemented using Ganache CLI running on localhost to simulate a full Ethereum-like blockchain. Transactions were issued through RPC clients such as MetaMask and Remix, while stress testing was performed using Hardhat test runners to emulate concurrent user interactions. Gas costs and latency were logged for each contract execution.
The results are summarized in Table 6. No significant performance degradation or functional failures were observed under simulated stress. Minor latency spikes occurred during rapid bursts, primarily due to RPC queue delays, which were mitigated by retry logic.

Table 6.
Simulation results.
These results confirm that YouGovern can handle moderate transaction volumes while maintaining reliability and responsiveness, making it suitable for deployment in real-world, medium-scale identity management scenarios.
6. Discussion and Future Work
6.1. Comparative Analysis
BSC was selected as the underlying platform due to its efficient transaction throughput, low gas fees, and full compatibility with the Ethereum Virtual Machine (EVM). These characteristics enable scalable and cost-effective deployments without sacrificing smart contract flexibility. In comparison, Ethereum offers higher decentralization but at significantly higher operational costs and lower throughput, making it less practical for low-cost identity services. Hyperledger Indy is more suitable for permissioned enterprise environments but introduces additional governance and deployment complexity. Although BSC’s Proof of Staked Authority (PoSA) model introduces some centralization, it allows for rapid prototyping and practical field deployment. The architecture of YouGovern remains blockchain-agnostic and can be migrated to other infrastructures as requirements evolve.
The BSC has experienced a significant surge in activity and popularity. Developed by the Binance Smart Contracts team, BSC supports a variety of decentralized applications, ranging from finance markets to token exchanges, drawing many users from the Ethereum-based platforms. This section provides an exhaustive analysis of the advantages of BSC over Ethereum [53,54], explaining why many are transitioning to this new platform.
BSC is designed for widespread adoption and boasts impressive scalability, which was evident during Ethereum’s high transaction fees period, known as DeFi summer. These high fees hindered participation and slowed down the growth of decentralized finance, prompting the need for a more accommodating network like BSC. Additionally, transaction costs and gas prices on BSC are notably lower than those on Ethereum. The average gas price on BSC is merely a fraction of that on Ethereum, making it a more attractive option for retail markets and decentralized apps (dapps) with smaller budget requirements [55].
Moreover, BSC offers complete compatibility with Ethereum, allowing users to use the same wallet addresses and smart contracts on both networks. Unlike Ethereum, BSC facilitates a straightforward link between various blockchains through p-Tokens (p-Network), removing barriers and fostering a seamless flow of users and liquidity between different ecosystems. This interoperability feature of BSC, combined with its efficient cross-chain transfer capabilities, enhances user experience and liquidity management [56].
In conclusion, the rapid expansion and increasing user engagement on BSC highlight its advantages over Ethereum. With lower transaction costs, faster block times, and enhanced scalability, BSC presents itself as a superior alternative for hosting decentralized applications, promising a broad market reach and substantial impact on the future of blockchain technology. Table 7 summarizes the comparison of the two networks.

Table 7.
Comparison of BSC & Ethereum Network.
6.2. Future Extensions
SSI represents a transformative and forward-thinking approach to managing individual digital identities, solving many issues inherent in traditional identity management systems in terms of regulation, technology, and security. By integrating digital wallets and decentralized ledger technologies such as blockchain, YouGovern allows individuals to control and manage all of their digital assets independently, with enhanced privacy and sovereignty.
This new model of identity management not only facilitates fast and secure access to digital versions of identity documents, academic diplomas, and property titles but also allows individuals to manage tokenized fiat currencies and cryptocurrencies. Blockchain networks provide cryptographic proofs of the existence and ownership of digital credentials and assets, which increases the trust, interoperability, security, and efficiency of electronic transactions while maintaining privacy.
Considering the regulatory environment, there is a pressing need to develop and update policies around electronic transactions and data privacy. Despite significant advancements, many regions, including Latin America and the Caribbean, still lack comprehensive regulations on data protection. Thus, it is crucial to focus on these areas to provide a secure framework for the deployment of SSI solutions.
Moving forward, organizations such as ISO, ITU, NIST, and the European Union predict rapid growth in activities surrounding self-sovereign identity. The likelihood is that soon, management of all digital assets could be done through a mobile wallet, using blockchain to ensure the accuracy and security of transactions. This technological shift presents a significant opportunity for both governments and private sector entities to take proactive steps towards adopting and implementing SSI solutions.
Although YouGovern is currently deployed on BSC for its low-cost and high-speed capabilities, we acknowledge that BSC’s Proof of Staked Authority (PoSA) model introduces partial centralization due to its limited validator pool. This may seem to challenge the principles of SSI. However, YouGovern’s architecture is designed to be portable across different blockchain platforms. Future versions of the system may migrate to more decentralized infrastructures such as Ethereum 2.0 or Hyperledger Indy. Furthermore, the system architecture ensures that identity ownership and control remain user-centric through smart contract logic, mitigating the risks posed by infrastructure-level centralization.
In terms of decentralization, BSC operates with a limited number of validators (21 active) under the PoSA model, introducing risks of validator collusion. In contrast, Ethereum’s Proof of Stake (PoS) involves thousands of validators distributed globally, significantly reducing the risk of coordinated manipulation. Hyperledger Indy, although permissioned, distributes trust across multiple governance entities with explicit policies for DID management. While BSC enables rapid prototyping, future versions of YouGovern aim to support interoperability with other platforms through DIDComm and Verifiable Credential frameworks, thereby reducing reliance on a single blockchain and enhancing trust and resilience.
One of the key challenges in decentralized identity systems is account recovery in the event of key compromise or loss. Unlike centralized systems, where identity can be revoked and reissued by the provider, SSI systems must embed user-driven recovery. In YouGovern, we plan to implement a social recovery mechanism that allows users to assign trusted guardians who can jointly approve key restoration. Alternatively, a multi-signature scheme involving independent verification channels is under consideration. Future iterations of the platform will explore these approaches and evaluate their effectiveness in user studies focused on usability and security trade-offs.
Future extensions of YouGovern could explore integration with next-generation consensus mechanisms such as SBC, which has demonstrated significant gains in energy efficiency and latency reduction in wireless networks [46]. These innovations may enable the deployment of self-sovereign identity systems in mobile, low-power, or ad hoc environments such as smart cities and 6G infrastructure.
In conclusion, while the YouGovern solution sets a robust foundation for self-sovereign identity, ongoing development, standardization, and integration are needed to fully realize the potential of this technology. Continued innovation and exploration in this field will likely unlock vast opportunities, transforming how personal identity and transactions are managed on a global scale.
7. Conclusions
In response to the growing complexities and vulnerabilities of centralized identity management systems, this paper introduces YouGovern, a blockchain-based Self-Sovereign Identity (SSI) solution. Although YouGovern does not propose new theoretical constructs, it delivers an effective integration of blockchain-based identity components into a functioning, standards-aligned system, highlighting a viable pathway for transitioning conceptual SSI models into real-world practice. Employing the BSC and leveraging the decentralized capabilities of smart contracts, YouGovern empowers individuals to manage their digital identities with enhanced security and autonomy. This system not only maintains privacy through the use of W3C decentralized identifiers (DIDs) but also supports traditional access control functions, effectively bridging the gap between user privacy and functional accessibility. The significant contributions of YouGovern include the implementation of a robust, user-centric identity management framework that mitigates the risks associated with centralized control, while providing a scalable and cost-effective solution. Looking ahead, the paper suggests future extensions into integrating digital wallets and enhancing regulatory frameworks to further support the widespread adoption of SSI solutions, promising a profound transformation in how personal identity and transactions are managed globally.
Author Contributions
Conceptualization, N.P. (Nikos Papatheodorou) and G.H.; methodology, N.P. (Nikos Papatheodorou) and G.H.; software, N.P. (Nikos Papatheodorou); validation, G.H.; investigation, N.P. (Nikos Papatheodorou); writing—original draft preparation, G.H. and N.P. (Nikos Papadakis); writing—review and editing, G.H.; supervision, N.P. (Nikos Papadakis). All authors have read and agreed to the published version of the manuscript.
Funding
This work has received funding from the European Union’s Horizon 2020 research and innovation programmes under grant agreements No. 101128070 (CONSOLE) and No. 101070599 (SecOPERA).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Abbreviations
The following abbreviations are used in this manuscript:
| BSC | Binance Smart Chain |
| dapp | Distributed application |
| DID | Decentralized identifier |
| DNS–IdM | Domain Name System–Identity Management |
| eID | European electronic identities |
| eMRTD | Electronically machine-readable travel documents |
| EOA | Externally Owned Accounts |
| EVM | Ethereum Virtual Machine |
| ICAO | International Civil Aviation Organization |
| HTML | HyperText Markup Language |
| IPFS | InterPlanetary File System |
| P2P | Peer-to-Peer |
| PoSA | Proof of Staked Authority |
| SSI | Self-Sovereign Identification |
| VC | Verifiable Credential |
References
- Chenchev, I.; Aleksieva-Petrova, A.; Petrov, M. Authentication Mechanisms and Classification: A Literature Survey. Springer Intell. Comput. 2021, 285, 1051–1070. [Google Scholar]
- Papaioannou, M.; Zachos, G.; Essop, I.; Mantas, G.; Rodriguez, J. Toward a secure and usable user authentication mechanism for mobile passenger ID devices for land/sea boarder control. IEEE Access 2022, 10, 38832–38849. [Google Scholar] [CrossRef]
- Dubey, A.; Saquib, Z.; Dwivedi, S. Electronic authentication for e-Government services—A survey. In Proceedings of the 10th IET System Safety and Cyber-Security Conference 2015, Bristol, UK, 21–22 October 2015. [Google Scholar]
- Josang, A. IAM—Identity and Access Management. In Springer Cybersecurity Technology and Governance, 1st ed.; Josang, A., Ed.; Springer: Cham, Switzerland, 2025; pp. 191–214. [Google Scholar]
- Hatzivasilis, G. Password Management—How Secure Is Your Login Process? In Proceedings of the ESORICS 2nd Model-driven Simulation and Training Environments for Cybersecurity (MSTEC) 2020, Guildford, UK, 17 September 2020. [Google Scholar]
- Precedence Research. Self-Sovereign Identity (SSI) Market Size, Share and Trends 2025 to 2034. Available online: https://www.precedenceresearch.com/self-sovereign-identity-market?utm_source=chatgpt.com (accessed on 16 May 2025).
- De Filippi, P.; Hassan, S. Blockchain Technology as a Regulatory Technology: From Code is Law to Law is Code. First Monday 2016, 21, 1–16. [Google Scholar] [CrossRef]
- Bandara, E.; Liang, X.; Foytik, P.; Shetty, S.; De Zoysa, K. A Blockchain and Self-Sovereign Identity Empowered Digital Identity Platform. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–9. [Google Scholar]
- Wang, F.; De Filippi, P. Self-Sovereign Identity in a Globalized World: Credentials-Based Identity Systems as a Driver for Economic Inclusion. Front. Blockchain 2020, 2, 28. [Google Scholar] [CrossRef]
- MacKinnon, R. Consent of the Networked: The Worldwide Struggle for Internet Freedom; Basic Books: New York, NY, USA, 2012. [Google Scholar]
- Wikipedia. Block of Wikipedia in Turkey. Available online: https://en.wikipedia.org/wiki/Block_of_Wikipedia_in_Turkey (accessed on 4 March 2025).
- Ahmed, S.; Lee, S. The inhibition effect: Privacy concerns disrupt the positive effects of social media use on online political participation. New Media Soc. 2023, 27, 203–224. [Google Scholar] [CrossRef]
- Kaye, D. Report of the Special Rapporteur on the Promotion and Protection of the Right to Freedom of Opinion and Expression. UN Human Rights Council, A/HRC/32/38. 2016, pp. 1–23. Available online: https://digitallibrary.un.org/record/842541 (accessed on 4 March 2025).
- Liu, Y.; Lu, Q.; Paik, H.Y.; Xu, X. Design Patterns for Blockchain-Based Self-Sovereign Identity. In Proceedings of the European Conference on Pattern Languages of Programs (EuroPLop’20), Virtual, Germany, 1–4 July 2020; article 16. pp. 1–14. [Google Scholar]
- Giannopoulou, A.; Wang, F. Self-sovereign identity. Internet Policy Rev. 2021, 10, 1–10. [Google Scholar] [CrossRef]
- Kuperberg, M.; Kemper, S.; Durak, C. Blockchain Usage for Government-Issued Electronic IDs: A Survey. In Proceedings of the International Conference on Advanced Information Systems Engineering (CAiSE), Rome, Italy, 3–7 June 2019; pp. 155–167. [Google Scholar]
- Rodriguez Garzon, S.; Yildiz, H.; Küpper, A. Decentralized Identifiers and Self-Sovereign Identity in 6G. IEEE Netw. 2022, 36, 142–148. [Google Scholar] [CrossRef]
- Kuperberg, M. Blockchain-Based Identity Management: A Survey from the Enterprise and Ecosystem Perspective. IEEE Trans. Eng. Manag. 2019, 67, 1008–1027. [Google Scholar] [CrossRef]
- Schlatt, V.; Sedlmeir, J.; Feulner, S.; Urbach, N. Designing a Framework for Digital KYC Processes Built on Blockchain-Based Self-Sovereign Identity. Inf. Manag. 2022, 59, 103553. [Google Scholar] [CrossRef]
- Zwitter, A.; Hazenberg, J. Decentralized Network Governance: Blockchain Technology and the Future of Regulation. Front. Blockchain 2020, 3, 12. [Google Scholar] [CrossRef]
- W3C Verifiable Credentials Working Group (VCWG). Available online: https://www.w3.org/2017/vc/WG/ (accessed on 4 March 2025).
- Binance. An Introduction to BNB Smart Chain (BSC). Binance Academy. 2024. Available online: https://academy.binance.com/en/articles/an-introduction-to-bnb-smart-chain-bsc (accessed on 4 March 2025).
- Buterin, V. Ethereum Whitepaper. Ethereum.org. 2014, pp. 1–46. Available online: https://ethereum.org/el/whitepaper/ (accessed on 4 March 2025).
- Busayatananphon, C.; Boonchieng, E. Financial Technology DeFi Protocol: A Review. In Proceedings of the Joint International Conference on Digital Arts, Media and Technology with ECTI Northern Section Conference on Electrical, Electronics, Computer and Telecommunications Engineering (ECTI DAMT & NCON), Chiang Rai, Thailand, 26–28 January 2022; pp. 267–272. [Google Scholar]
- Heiss, J.; Muth, R.; Pallas, F.; Tai, S. Non-Disclosing Credential On-Chaining for Blockchain-Based Decentralized Applications. In Proceedings of the 20th International Conference on Service-Oriented Computing (ICSOC 2022), Seville, Spain, 29 November–2 December 2022; pp. 351–368. [Google Scholar]
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media: Sebastopol, CA, USA, 2015. [Google Scholar]
- Thorve, A.; Shirole, M.; Jain, P.; Santhumayor, C.; Sarode, S. Decentralized Identity Management Using Blockchain. In Proceedings of the 4th International Conference on Advances in Computing, Communication Control and Networking (ICAC3N), Greater Noida, India, 16–17 December 2022; pp. 1–7. [Google Scholar]
- Hatzivasilis, G.; Ioannidis, S.; Fysarakis, K.; Spanoudakis, G.; Papadakis, N. The Green Blockchains of Circular Economy. Electronics 2021, 10, 2008. [Google Scholar] [CrossRef]
- Alexandris, G.; Katos, V.; Alexaki, S.; Hatzivasilis, G. Blockchains as Enablers for Auditing Cooperative Circular Economy Networks. In Proceedings of the 23rd IEEE International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD 2018), Barcelona, Spain, 17–19 September 2018; pp. 1–7. [Google Scholar]
- Kietzmann, J.; Archer-Brown, C. From hype to reality: Blockchain grows up. Bus. Horiz. 2019, 62, 269–271. [Google Scholar] [CrossRef]
- Halpin, H.; Piekarska, M. Introduction to Security and Privacy on the Blockchain. In Proceedings of the IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), 2017, Paris, France, 3 July 2017. [Google Scholar]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Bauer, D.P. Solidity. In Getting Started with Ethereum, 1st ed.; Springer: Berkeley, CA, USA, 2022; pp. 13–16. [Google Scholar]
- Li, Z.; Dong, X.; Jin, D.; Zhong, W.; Dai, C. Management platform for second-use of retired power battery based on IPv6 and blockchain technology. In Proceedings of the IEEE 5th Information Technology and Mechatronics Engineering Conference (ITOEC) 2020, Chongqing, China, 16 July 2020; pp. 1465–1469. [Google Scholar]
- Metcalfe, W. Ethereum, Smart Contracts, Dapps. In Blockchain and Crypto Currency, 1st ed.; Springer: Singapore, 2020; pp. 77–93. [Google Scholar]
- Khan, S.N.; Loukil, F.; Ghedira-Guegan, C.; Benkhelifa, E.; Bani-Hani, A. Blockchain smart contracts: Applications, challenges, and future trends. Peer-Peer Netw. Appl. 2021, 14, 2901–2925. [Google Scholar] [CrossRef]
- Windley, P. Fixing the Five Problems of Internet Identity. Technometria, 2017. Available online: https://www.windley.com/archives/2017/10/fixing_the_five_problems_of_internet_identity.shtml (accessed on 4 March 2025).
- Tobin, A.; Drummond, R. The inevitable rise of self-sovereign identity. Sovrin Found. 2016, 18, 1–23. Available online: https://sovrin.org/wp-content/uploads/2018/03/The-Inevitable-Rise-of-Self-Sovereign-Identity.pdf (accessed on 4 March 2025).
- Nitin, N.; Jenkins, P. A secure mobile cloud identity: Criteria for effective identity and access management standards. In Proceedings of the 4th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 29 March–1 April 2016. [Google Scholar]
- Naik, N.; Jenkins, P. Securing digital identities in the cloud by selecting an apposite Federated Identity Management from SAML, OAuth and OpenID Connect. In Proceedings of the 11th IEEE International Conference on Research Challenges in Information Science (RCIS), Brighton, UK, 10–12 May 2017; pp. 163–174. [Google Scholar]
- Naik, N.; Jenkins, P. uPort open-source identity management system: An assessment of self-sovereign identity and user-centric data platform built on blockchain. In Proceedings of the IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 12 October–12 November 2020; pp. 1–7. [Google Scholar]
- Windley, P. Sovrin: An Identity Metasystem for Self-Sovereign Identity. Front. Blockchain 2021, 4, 626726. [Google Scholar] [CrossRef]
- Buchmann, N.; Rathgeb, C.; Baier, H.; Busch, C.; Margraf, M. Enhancing Breeder Document Long-Term Security Using Blockchain Technology. In Proceedings of the IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), Turin, Italy, 4–8 July 2017. [Google Scholar]
- Kassem, J.A.; Sayeed, S.; Marco-Gisbert, H.; Pervez, Z.; Dahal, K. DNS-IdM: A Blockchain Identity Management System to Secure Personal Data Sharing in a Network. Appl. Sci. 2019, 9, 2953. [Google Scholar] [CrossRef]
- Luo, H.; Sun, G.; Chi, C.; Yu, H.; Guizani, M. Convergence of Symbiotic Communications and Blockchain for Sustainable and Trustworthy 6G Wireless Networks. IEEE Wirel. Commun. 2025, 32, 18–25. [Google Scholar] [CrossRef]
- Luo, H.; Zhang, Q.; Sun, G.; Yu, H.; Niyato, D. Symbiotic Blockchain Consensus: Cognitive Backscatter Communications-Enabled Wireless Blockchain Consensus. IEEE/ACM Trans. Netw. 2024, 32, 5372–5387. [Google Scholar] [CrossRef]
- Paik, H.-Y.; Xu, X.; Bandara, H.M.N.D.; Lee, S.U.; Lo, S.K. Analysis of Data Management in Blockchain-Based Systems: From Architecture to Governance. IEEE Access 2019, 7, 186091–186107. [Google Scholar] [CrossRef]
- Anand, M.V.; Mithun, S.; Shree, L.S.D.; Ranjith, M. Survey on connecting to the decentralized storage using IPFS protocol with web 3 technology. In Proceedings of the International Conference for Advancement in Technology (ICONAT), Goa, India, 24–26 January 2023; pp. 1–4. [Google Scholar]
- Identity Foundation. ION, 2021. Available online: https://identity.foundation/ion/ (accessed on 16 May 2025).
- Thomas, A.M.; Ramaguru, R.; Sethumadhavan, M. Distributed Identity and Verifiable Claims Using Ethereum Standards. Inven. Commun. Comput. Technol. 2022, 311, 621–636. [Google Scholar]
- YCharts. Binance Smart Chain Average Gas Price. YCharts 2025. Available online: https://ycharts.com/indicators/binance_smart_chain_average_gas_price (accessed on 16 May 2025).
- Nair, L.V.; Mittal, H.K. Feasibility of Test-Driven Development in Agile Blockchain Smart Contract Development: A Comprehensive Analysis. In Proceedings of the First International Conference on Technological Innovations and Advance Computing (TIACOMP), Bali, Indonesia, 29–30 June 2024; pp. 264–277. [Google Scholar]
- Patnaik, S.; Wang, T.S.; Shen, T.; Panigrahi, S.K. Blockchain Technology and Innovations in Business Processes. In Smart Innovation, Systems and Technologies, 1st ed.; Springer: Singapore, 2021; Volume 219. [Google Scholar]
- Harris, C.G. Cross-Chain Technologies: Challenges and Opportunities for Blockchain Interoperability. In Proceedings of the IEEE International Conference on Omni-layer Intelligent Systems (COINS), Berlin, Germany, 23–25 July 2023. [Google Scholar]
- Yusandika, A.D.; Bhuiyan, A.H.; Laskar, P.S. Onchain Analysis: A Comparative Study of Decentralized Exchange (DEX) Activities on Ethereum, Solana, and Binance Smart Chain (BSC). Blockchain Artif. Intell. Future Res. 2025, 1, 23–34. [Google Scholar] [CrossRef]
- Cernera, F.; La Morgia, M.; Mei, A.; Sassi, F. Token spammers, rug pulls, and sniper bots: An analysis of the ecosystem of tokens in ethereum and in the binance smart chain ({BNB}). In Proceedings of the 32nd USENIX security symposium (USENIX security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 3349–3366. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).