Enhancing Multi-Key Fully Homomorphic Encryption with Efficient Key Switching and Batched Multi-Hop Computations
Abstract
1. Introduction
1.1. Related Works
1.2. Motivations
1.3. Our Contributions
2. Preliminaries
2.1. Notation
2.2. Ring Learning with Errors
2.3. Polynomial Chinese Remainder Theorem
2.4. Multi-Key Fully Homomorphic Encryption (MKFHE)
- Setup: . The setup algorithm takes the security parameter as input and outputs the public parameters . These public parameters are implicitly used by other algorithms in the scheme.
- Key Generation: . The key generation algorithm takes the public parameters as input and generates a public key and a secret key for each participating party. Each party holds its own secret key while sharing the public key.
- Encryption: . The encryption algorithm takes a message and the corresponding public key as inputs, encrypting the message to produce a ciphertext .
- Evaluation: . The evaluation algorithm allows for computations on multiple ciphertexts , each encrypted under a (possibly repeated) public key from the set , where denotes the number of distinct public keys involved. It performs homomorphic operations on these ciphertexts based on a given circuit , producing a new ciphertext that is the encrypted result of the computation.
- Decryption: . The decryption algorithm takes a ciphertext and the corresponding secret keys for the participating parties as input, decrypting the ciphertext to recover a plaintext message .
2.5. Gadget Decomposition
2.6. IND-CPA Security
- 1.
- The challenger runs , and sends the public key to .
- 2.
- sends two equal-length messages to the challenger.
- 3.
- The challenger samples a uniform bit , computes the challenge ciphertext , and sends to .
- 4.
- outputs a guess bit . The experiment outputs 1 if , and 0 otherwise.
3. New Multi-Key Variant of BGV
3.1. Improved Multi-Key BGV
- : For a given , , and , where denotes the RLWE dimension, is a bound on the circuit depth, and is the security parameter, define a sequence of ciphertext moduli recursively as for , where each is an integer. Specifically, the largest modulus is . Let the error distribution be a -bounded spherical discrete Gaussian distribution over the ring , where the bound satisfies . Let be the plaintext modulus, chosen such that is coprime with every . Let be a gadget decomposition function associated with the gadget vector . For each level , uniformly sample a random vector . Output the public parameters .In practical deployments, the algorithm is executed once in a trusted setup phase, during which the public parameters are generated. This setup may be performed by a trusted third party (e.g., a cloud service provider) or collaboratively via a distributed multi-party protocol. Once established, the public parameters remain fixed and publicly known.
- : The key generation algorithm is executed independently by each party without requiring any interaction or coordination with others. For each level (from down to 0) and for the -th party, the secret key is sampled as , ensuring that is invertible in . A noise vector is drawn as . The public key is then computed by , where . Thus, the key generation algorithm outputs pairs for each party .As detailed in [23,32], efficient algorithms exist to verify whether an element in is invertible and to compute its inverse. Moreover, when setting , elements that belong to are invertible with overwhelming probability. We point out that since is a distribution over , and is defined as , the sampled secret key is naturally an element of [5,33].
- : The encryption algorithm is performed locally by each data owner. For a plaintext , sample a random element , and noise . Then, for party at level , compute the ciphertext as .Here, and denote the first component of the vectors and , respectively.
- : The ciphertext extension algorithm is performed by the evaluator, such as a cloud server or another computation entity. Suppose is a ciphertext at level associated with parties. To extend this ciphertext to support parties (with ), construct and output an extended ciphertextby setting and for , while for all satisfying . This construction guarantees thatThus, the extended ciphertext encrypts the same underlying plaintext at the same level while now being associated with parties.
- : The decryption algorithm is jointly executed by all involved parties. Given an -key ciphertext at level associated with parties, along with the corresponding secret keys , the plaintext is recovered by computing
- : The modulus switching algorithm is executed by the evaluator. Given a ciphertext at level , computefor , where denotes the rounding operation, and output the ciphertext at level .In BGV-type schemes, reducing the inner modulus from to decreases the internal noise by roughly the factor . The modulus switching technique ensures that the resulting ciphertext can still be decrypted under the same secret key without affecting the correctness of the underlying plaintext, enabling continued homomorphic computations at the lower level. A detailed correctness proof for modulus switching can be found in [5].
- : The homomorphic evaluation algorithm is executed by the evaluator. Let denote the circuit provided as input for homomorphic evaluation on ciphertexts . Each ciphertext (where ) is at a particular level and was originally encrypted under a subset of the parties’ keys. The algorithm proceeds as follows:
- If any ciphertexts are at higher levels than others, apply the necessary key switching or modulus switching procedures so that all ciphertexts are converted to a common level .
- For each ciphertext , invoke the ciphertext extension algorithm to extend into an extended ciphertext that is related to the union of all parties involved across these ciphertexts. This step ensures that all input ciphertexts are associated with the same set of parties.
- For each involved party , compute its level- evaluation key .
- To evaluate the circuit gate by gate, simply apply the homomorphic operations and (detailed immediately below) on the extended ciphertexts.
- After processing all gates in , output the final ciphertext , which encrypts the result of on the original plaintexts under the secret keys of all involved parties.
- : For two ciphertexts and in , output their component-wise sum .
- : Given ciphertexts and in along with the public keys and evaluation keys , compute the tensor product with components for all . Then, compute , and finally output .
- For each party , the challenger generates key pairs , and sends the public keys to the adversary .
- The adversary selects two plaintexts , and specifies a public key to be used for encryption.
- The challenger samples a uniform bit , and returns the ciphertext to .
- outputs a guess bit . The experiment outputs 1 if , and 0 otherwise.
- All key generation and public key disclosure steps remain unchanged.
- The adversary submits the same two plaintexts and public key as in Hybrid 0.
- The challenger samples the same bit , but now computes , and returns it to .
- outputs a guess bit . The experiment outputs 1 if , and 0 otherwise.
3.2. Novel Methods for Evaluation Key Generation and Key Switching
- : For a party at level , sample a random element , a random vector , and noise vectors . Compute , , and . Then, output the evaluation key .
- : The key switching algorithm is executed by the evaluator. Consider a tensored ciphertext with each , which is associated with the secret keys , and a set of public keys together with evaluation keys for . To produce a standard ciphertext at level that is associated with the secret keys , perform the following steps:
- Set the first component as , and for each , assign .
- For each , update .
- For each , compute , and subsequently update .
- For the intermediate ciphertext , set and for each , compute .
- Output the resulting ciphertext .
3.3. Redesigning Homomorphic Multiplication
- : Consider two ciphertexts and in , together with a set of public keys and evaluation keys for . To produce the multiplied ciphertext at level that is associated with the secret keys , proceed as follows:
- Set the first component as , and for each , assign .
- Compute and .
- For each , update .
- For each , update .
- For the intermediate ciphertext , set and for each , compute .
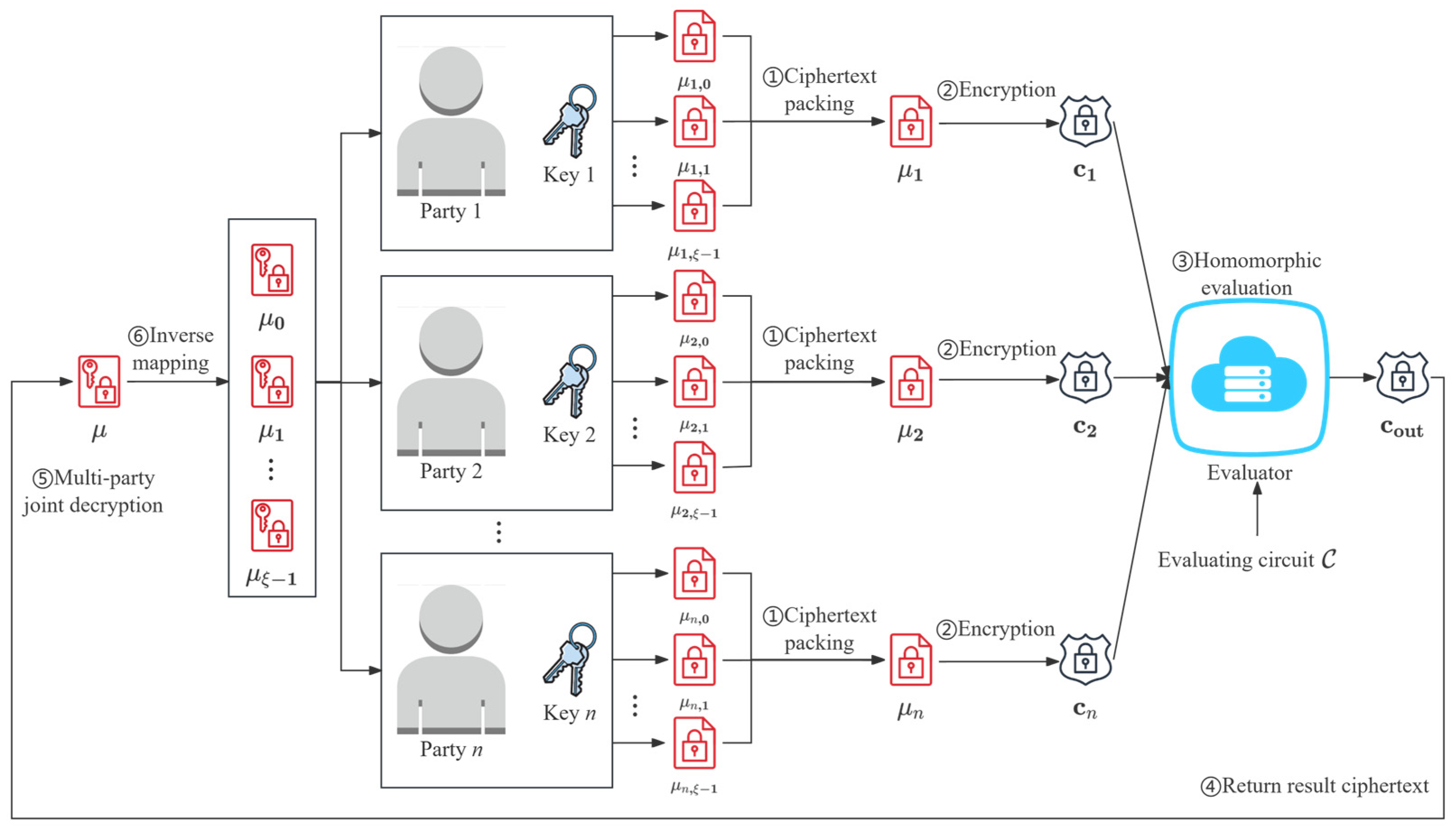
4. Batched MK-BGV Scheme
4.1. Ciphertext Packing Based on Polynomial CRT
4.2. Improved Batched Multi-Key BGV
- : For a given , , and , where denotes the RLWE dimension, is a bound on the circuit depth, and is the security parameter, define a sequence of ciphertext moduli recursively as for , where each is an integer. Specifically, the largest modulus is . Let the error distribution be a -bounded spherical discrete Gaussian distribution over the ring , where the bound satisfies . Let be the plaintext modulus, chosen such that is coprime with every . Let be a homomorphic gadget decomposition function associated with the gadget vector . The mappings and are isomorphisms between and . For each level , uniformly sample a random vector . Output the public parameters .
- : For each level (from down to 0) and for the -th party, output secret-public key pairs .
- : For a plaintext vector , compute the aggregate plaintext . Then, for party at level , compute the ciphertext as .
- : Suppose is a ciphertext at level associated with parties. To extend this ciphertext to support parties (with ), construct and output an extended ciphertext .
- : Given an -key ciphertext at level associated with parties, along with the corresponding secret keys , the aggregate plaintext is recovered by computing . Subsequently, the complete set of plaintext messages across the slots is obtained via the inverse mapping
- : Let denote the circuit provided as input for homomorphic evaluation on ciphertexts . Each ciphertext (where ) is at a particular level and was originally encrypted under a subset of the parties’ keys. To produce the output ciphertext, compute , where every invocation of the homomorphic multiplication is replaced by our new multiplication algorithm .
5. Parameter and Performance Analysis and Comparison
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, MD, USA, 31 May–2 June 2009; pp. 169–178. [Google Scholar]
- Hamlin, A.; Shelat, A.; Weiss, M.; Wichs, D. Multi-key searchable encryption, revisited. In Proceedings of the Public-Key Cryptography–PKC 2018: 21st IACR International Conference on Practice and Theory of Public-Key Cryptography, Rio de Janeiro, Brazil, 25–29 March 2018; Proceedings, Part I. Springer International Publishing: Berlin/Heidelberg, Germany; pp. 95–124. [Google Scholar]
- Froelicher, D.; Troncoso-Pastoriza, J.R.; Raisaro, J.L.; Cuendet, M.A.; Sousa, J.S.; Cho, H.; Berger, B.; Fellay, J.; Hubaux, J.P. Truly privacy-preserving federated analytics for precision medicine with multiparty homomorphic encryption. Nat. Commun. 2021, 12, 5910, Erratum in Nat. Commun. 2021, 12, 6649. [Google Scholar] [CrossRef] [PubMed] [PubMed Central]
- Graepel, T.; Lauter, K.; Naehrig, M. ML confidential: Machine learning on encrypted data. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 28–30 November 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 1–21. [Google Scholar]
- Brakerski, Z.; Gentry, C.; Vaikuntanathan, V. (Leveled) fully homomorphic encryption without bootstrapping. ACM Trans. Comput. Theory (TOCT) 2014, 6, 13. [Google Scholar] [CrossRef]
- Brakerski, Z. Fully homomorphic encryption without modulus switching from classical GapSVP. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 868–886. [Google Scholar]
- Fan, J.; Vercauteren, F. Somewhat practical fully homomorphic encryption. Cryptology ePrint Archive 2012. Available online: https://eprint.iacr.org/2012/144 (accessed on 4 April 2025).
- Gentry, C.; Sahai, A.; Waters, B. Homomorphic encryption from learning with errors: Conceptually-simpler, asymptotically-faster, attribute-based. In Proceedings of the Advances in Cryptology–CRYPTO 2013: 33rd Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; Proceedings, Part I. Springer: Berlin/Heidelberg, Germany, 2013; pp. 75–92. [Google Scholar]
- Cheon, J.H.; Kim, A.; Kim, M.; Song, Y. Homomorphic encryption for arithmetic of approximate numbers. In Proceedings of the Advances in Cryptology–ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 3–7 December 2017; Proceedings, Part I. Springer: Berlin/Heidelberg, Germany, 2017; pp. 409–437. [Google Scholar]
- Chillotti, I.; Gama, N.; Georgieva, M.; Izabachene, M. Faster fully homomorphic encryption: Bootstrapping in less than 0.1 seconds. In Advances in Cryptology–ASIACRYPT 2016: 22nd International Conference on the Theory and Application of Cryptology and Information Security, Hanoi, Vietnam, 4–8 December 2016; Proceedings, Part I; Springer: Berlin/Heidelberg, Germany, 2016; pp. 3–33. [Google Scholar]
- López-Alt, A.; Tromer, E.; Vaikuntanathan, V. On-the-fly multiparty computation on the cloud via multikey fully homomorphic encryption. In Proceedings of the Forty-Fourth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 19–22 May 2012; pp. 1219–1234. [Google Scholar]
- Clear, M.; McGoldrick, C. Multi-identity and multi-key leveled FHE from learning with errors. In Proceedings of the Advances in Cryptology—CRYPTO 2015: 35th Annual Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2015; Proceedings, Part II. Springer: Berlin/Heidelberg, Germany, 2015; pp. 630–656. [Google Scholar]
- Mukherjee, P.; Wichs, D. Two round multiparty computation via multi-key FHE. In Proceedings of the Advances in Cryptology—EUROCRYPT 2016: 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 8–12 May 2016; Proceedings, Part II. Springer: Berlin/Heidelberg, Germany, 2016; pp. 735–763. [Google Scholar]
- Peikert, C.; Shiehian, S. Multi-key FHE from LWE, revisited. In Proceedings of the Theory of Cryptography Conference, Beijing, China, 1–3 November 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 217–238. [Google Scholar]
- Brakerski, Z.; Perlman, R. Lattice-based fully dynamic multi-key FHE with short ciphertexts. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 190–213. [Google Scholar]
- Chen, L.; Zhang, Z.; Wang, X. Batched multi-hop multi-key FHE from ring-LWE with compact ciphertext extension. In Proceedings of the Theory of Cryptography: 15th International Conference, TCC 2017, Baltimore, MD, USA, 12–15 November 2017; Proceedings, Part II. Springer: Berlin/Heidelberg, Germany, 2017; pp. 597–627. [Google Scholar]
- Li, N.; Zhou, T.; Yang, X.; Han, Y.; Liu, W.; Tu, G. Efficient multi-key FHE with short extended ciphertexts and directed decryption protocol. IEEE Access 2019, 7, 56724–56732. [Google Scholar] [CrossRef]
- Chen, H.; Chillotti, I.; Song, Y. Multi-key homomorphic encryption from TFHE. In Proceedings of the Advances in Cryptology–ASIACRYPT 2019: 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Proceedings, Part II. Springer: Berlin/Heidelberg, Germany, 2019; pp. 446–472. [Google Scholar]
- Chen, H.; Dai, W.; Kim, M.; Song, Y. Efficient multi-key homomorphic encryption with packed ciphertexts with application to oblivious neural network inference. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 395–412. [Google Scholar]
- Kim, T.; Kwak, H.; Lee, D.; Seo, J.; Song, Y. Asymptotically faster multi-key homomorphic encryption from homomorphic gadget decomposition. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; pp. 726–740. [Google Scholar]
- Hoffstein, J.; Pipher, J.; Silverman, J.H. NTRU: A ring-based public key cryptosystem. In Proceedings of the International Algorithmic Number Theory Symposium, Portland, OR, USA,, 21–25 June 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 267–288. [Google Scholar]
- Regev, O. On lattices, learning with errors, random linear codes, and cryptography. J. ACM (JACM) 2009, 56, 34. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On ideal lattices and learning with errors over rings. J. ACM (JACM) 2013, 60, 43. [Google Scholar] [CrossRef]
- Zhou, T.; Chen, L.; Che, X.; Liu, W.; Zhang, Z.; Yang, X. Multi-key Fully Homomorphic Encryption Scheme with Compact Ciphertexts. Cryptology ePrint Archive 2021. Available online: https://eprint.iacr.org/2021/1131 (accessed on 4 April 2025).
- Asharov, G.; Jain, A.; López-Alt, A.; Tromer, E.; Vaikuntanathan, V.; Wichs, D. Multiparty computation with low communication, computation and interaction via threshold FHE. In Proceedings of the Advances in Cryptology—EUROCRYPT 2012: 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Proceedings 31. Springer: Berlin/Heidelberg, Germany; pp. 483–501. [Google Scholar]
- Gentry, C.; Halevi, S.; Smart, N.P. Fully homomorphic encryption with polylog overhead. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Micciancio, D.; Peikert, C. Trapdoors for lattices: Simpler, tighter, faster, smaller. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Bajard, J.C.; Eynard, J.; Hasan, M.A.; Zucca, V. A full RNS variant of FV like somewhat homomorphic encryption schemes. In Proceedings of the International Conference on Selected Areas in Cryptography, St. John’s, NL, Canada, 10–12 August 2016; Springer International Publishing: Cham, Switzerland, 2016. [Google Scholar]
- Halevi, S.; Polyakov, Y.; Shoup, V. An improved RNS variant of the BFV homomorphic encryption scheme. In Proceedings of the Topics in Cryptology-CT-RSA 2019: The Cryptographers’ Track at the RSA Conference 2019, San Francisco, CA, USA, 4–8 March 2019; Proceedings. Springer International Publishing: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Ducas, L.; Micciancio, D. FHEW: Bootstrapping homomorphic encryption in less than a second. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Goldwasser, S.; Micali, S. Probabilistic encryption. J. Comput. Syst. Sci. 1984, 28, 270–299. [Google Scholar] [CrossRef]
- Stehlé, D.; Steinfeld, R. Making NTRU as secure as worst-case problems over ideal lattices. In Proceedings of the Advances in Cryptology—EUROCRYPT 2011: 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 15–19 May 2011; Proceedings 30. Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Brakerski, Z.; Vaikuntanathan, V. Fully homomorphic encryption from ring-LWE and security for key dependent messages. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
| Scheme | Public Key Size | Ciphertext Size | Evaluation Key Size | Security |
| BP16 [15] | IND-CPA with circular security assumption | |||
| CZW17 [16] | IND-CPA | |||
| LZY+19 [17] | IND-CPA | |||
| CCS19 [18] | IND-CPA with circular security assumption | |||
| CDKS19 [19] | IND-CPA with circular security assumption | |||
| ZCC+21 [24] | IND-CPA with circular security assumption | |||
| IND-CPA | ||||
| IND-CPA |
| Scheme | Evaluation Key Generation Material Size | Computational Complexity (Number of Scalar Operations) | Number of Gadget Decompositions in Key Switching | |
| Joint Evaluation Key Generation | Homomorphic Multiplication | |||
| CZW17 [16] | ||||
| LZY+19 [17] | ||||
| CCS19 [18] | ||||
| CDKS19 [19] | ||||
| ZCC+21 [24] | ||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, L.; Huang, R.; Wang, B. Enhancing Multi-Key Fully Homomorphic Encryption with Efficient Key Switching and Batched Multi-Hop Computations. Appl. Sci. 2025, 15, 5771. https://doi.org/10.3390/app15105771
Zhou L, Huang R, Wang B. Enhancing Multi-Key Fully Homomorphic Encryption with Efficient Key Switching and Batched Multi-Hop Computations. Applied Sciences. 2025; 15(10):5771. https://doi.org/10.3390/app15105771
Chicago/Turabian StyleZhou, Liang, Ruwei Huang, and Bingbing Wang. 2025. "Enhancing Multi-Key Fully Homomorphic Encryption with Efficient Key Switching and Batched Multi-Hop Computations" Applied Sciences 15, no. 10: 5771. https://doi.org/10.3390/app15105771
APA StyleZhou, L., Huang, R., & Wang, B. (2025). Enhancing Multi-Key Fully Homomorphic Encryption with Efficient Key Switching and Batched Multi-Hop Computations. Applied Sciences, 15(10), 5771. https://doi.org/10.3390/app15105771






