Application of Blockchain Technologies in Verification of Software Metrics
Abstract
1. Introduction
2. Related Work
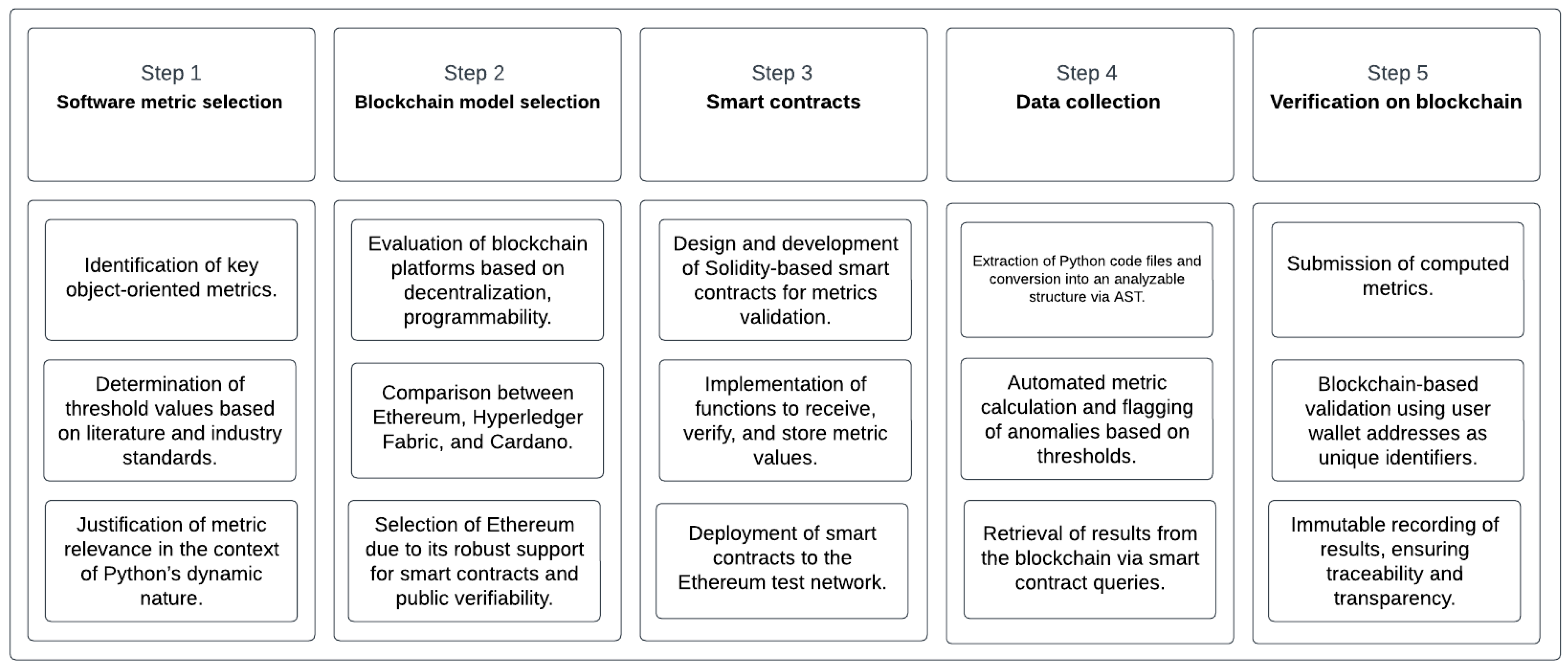
3. Methodology
3.1. Software Metric Selection
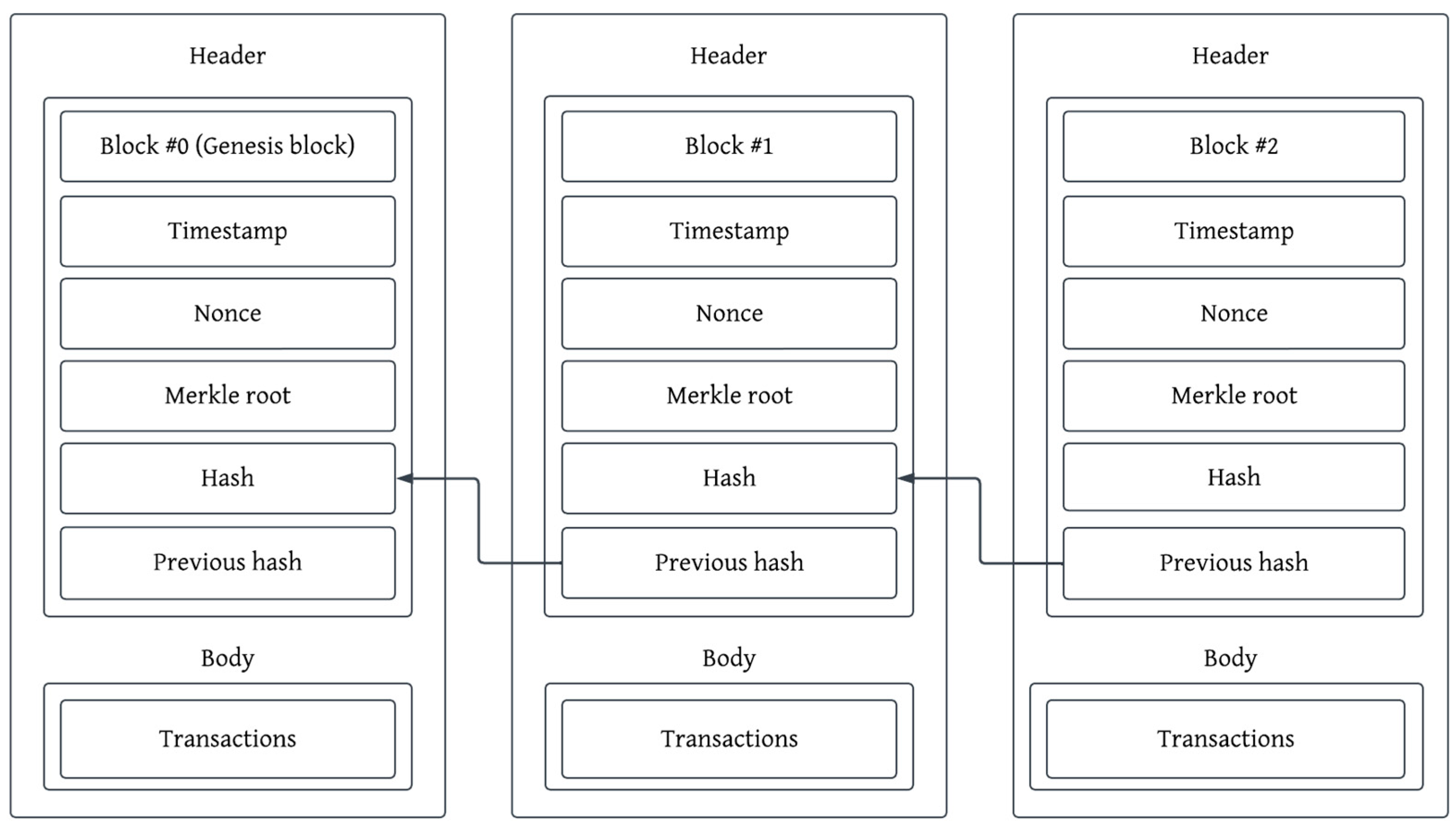
3.2. Verification on Blockchain
3.2.1. Blockchain Model Selection
3.2.2. Smart Contracts
- Transparency: In practice, the conditions defined within a smart contract are clearly accessible to all participants in the blockchain network [33]. Once a contract is deployed, modifying it is not easily feasible. Every transaction executed under the contract is tracked and verified by other nodes in the network, enhancing transparency and reducing the risk of fraud [33]. Moreover, fraudulent practices in software metric verification are becoming increasingly common, highlighting the need for more robust and reliable methods;
- Speed: Smart contracts operate independently of human intervention, with their execution monitored and validated by other nodes. Once the predefined conditions are met, the contract executes automatically [33]. This process is typically triggered by specific events, which activate the contract logic when certain criteria are fulfilled [33];
- Security: Leveraging advanced cryptographic methods and the intrinsic properties of blockchain, such as immutability, smart contracts provide a high level of security [33]. The contents of a smart contract cannot be retroactively modified by any party, and execution occurs autonomously and deterministically [33].
3.3. Data Collection for Verification
- methodology for source code analysis and software metric extraction;
- process of data verification using smart contracts;
- approach for retrieving data from the blockchain for result validation.
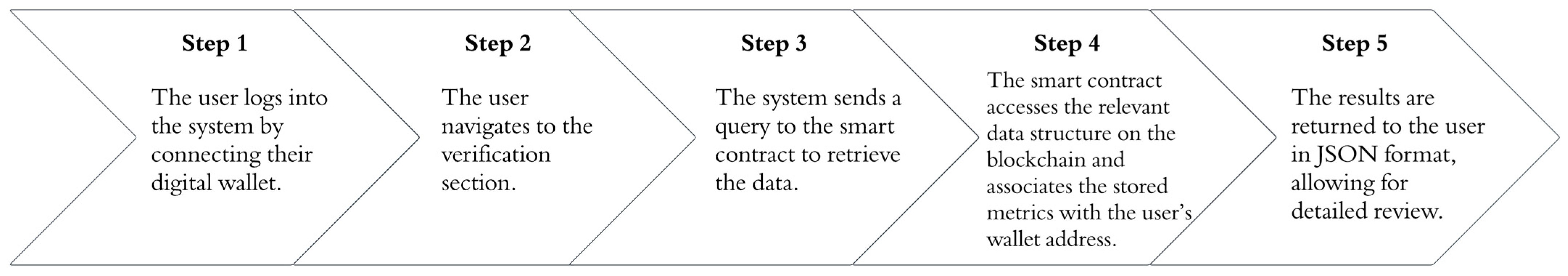
- The user logs into the system by connecting their digital wallet;
- The user navigates to the verification section;
- The system sends a query to the smart contract to retrieve the data;
- The smart contract accesses the relevant data structure on the blockchain and associates the stored metrics with the user’s wallet address;
- The results are returned to the user in JSON format, allowing for detailed review.
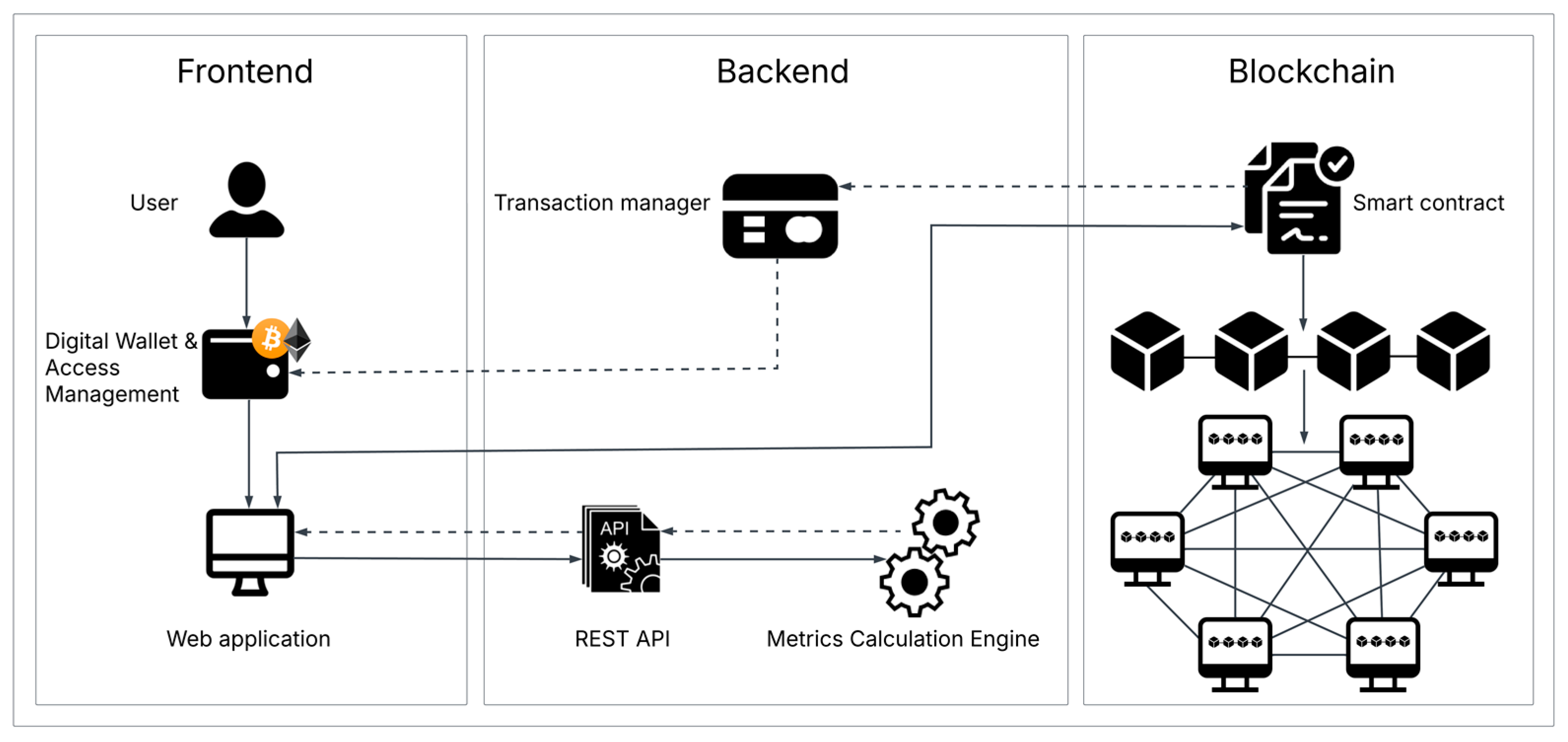
3.4. System Architecture
3.5. Validation of the Metrics
3.6. Technologies Used in Software Development
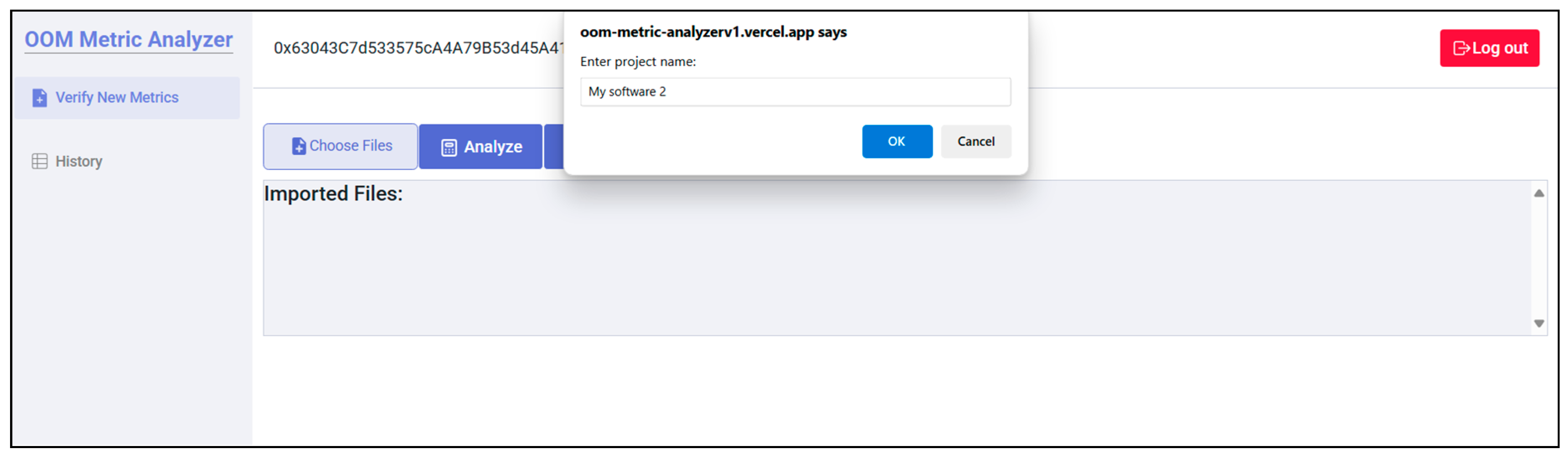
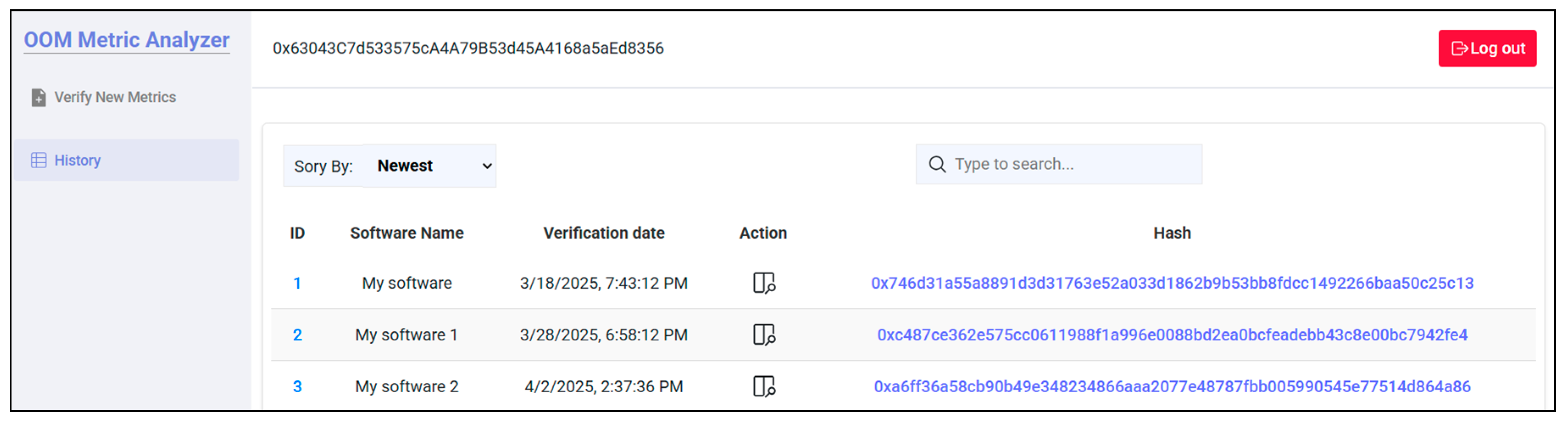
4. Use Case Study: OOM Metric Analyzer
- Choose Files: Select the software files to be analyzed.
- Analyze: Compute software metrics for the selected software.
- Reset: Clear the calculated metrics and reset the analysis.
- Verify: Verify the computed metrics by submitting them to the blockchain.
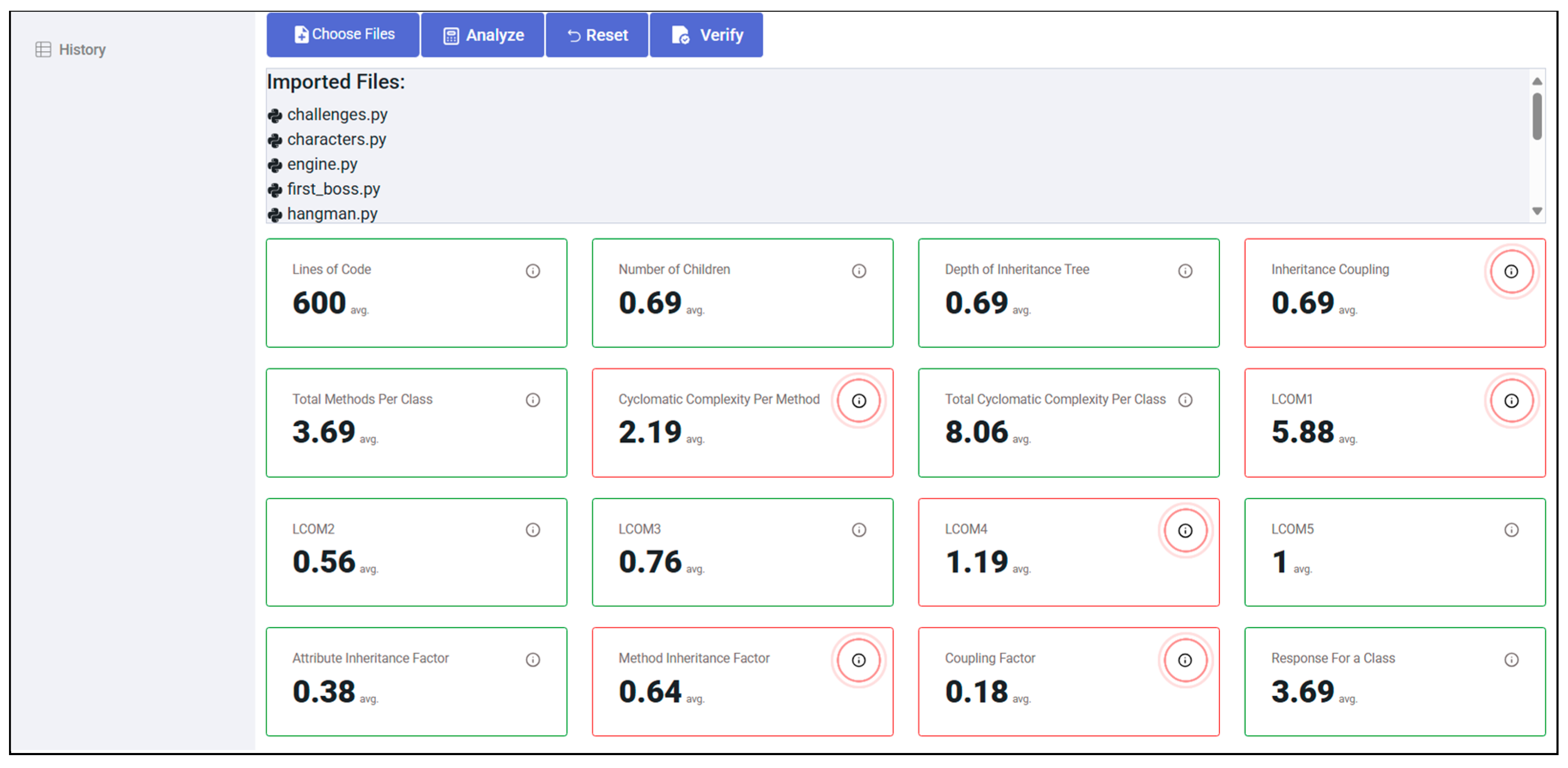
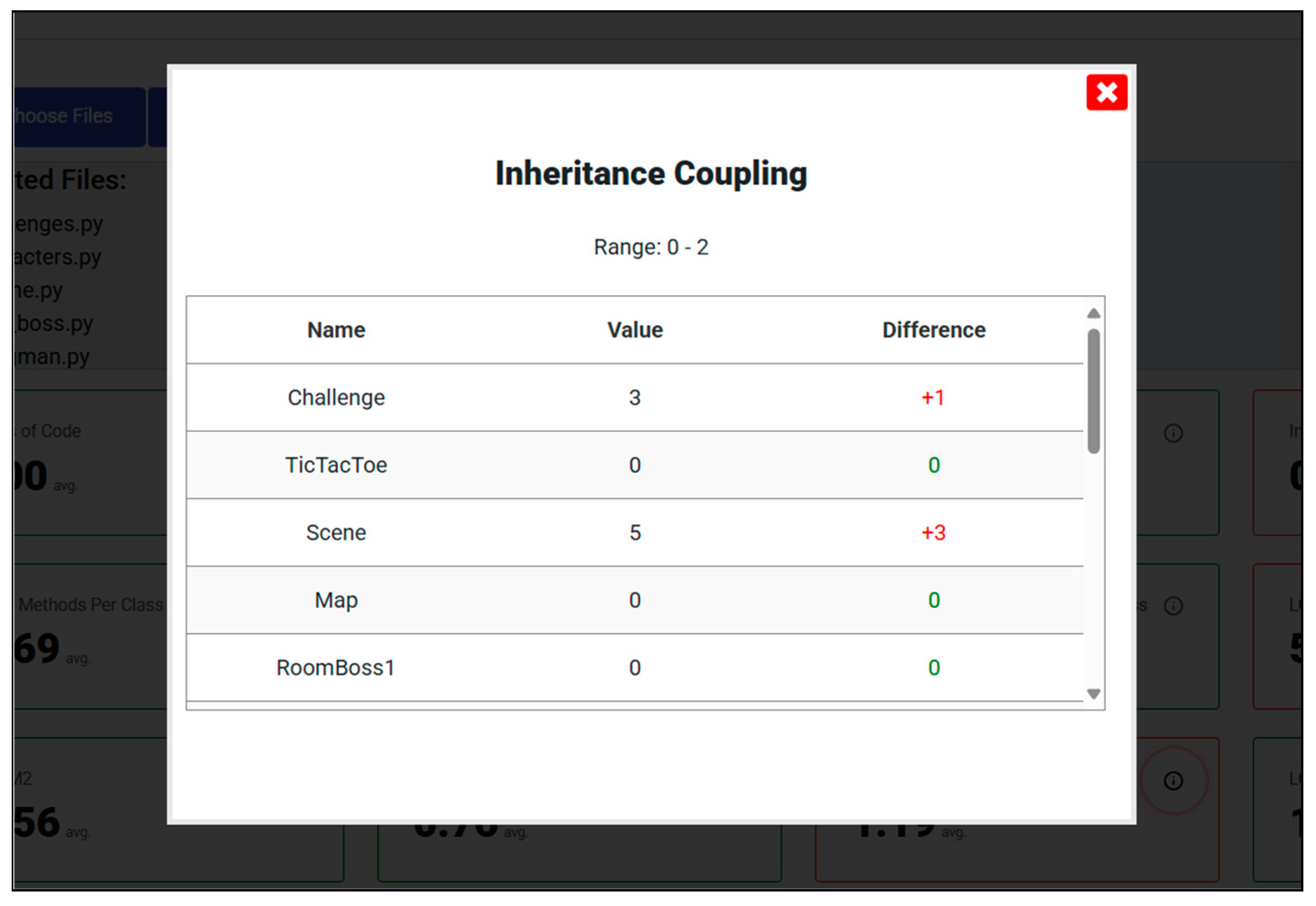
Analysis of Obtained Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| LOC | Lines of Code |
| NOC | Number of Children |
| DIT | Depth of Inheritance Tree |
| TMC | Total Methods per Class |
| IC | Inheritance Coupling |
| CCc | Cyclomatic Complexity per Class |
| CCm | Cyclomatic Complexity per Method |
| LCOM | Lack of Cohesion of Methods |
| MIF | Method Inheritance Factor |
| AIF | Attribute Inheritance Factor |
| CF | Coupling Factor |
| RFC | Response For Class |
| AST | Abstract Syntax Tree |
| ETH | Ethereum |
| REST API | Representational State Transfer Application Programming Interface |
| BMVS | Blockchain-Based Metric Validation Scheme |
| ZKPs | Zero-Knowledge Proofs |
| DOM | Document Object Model |
| AI | Artificial Intelligence |
References
- Hossain, S.S.; Ahmed, P.; Arafat, Y. Software Process Metrics in Agile Software Development: A Systematic Mapping Study. In Computational Science and Its Applications—ICCSA 2021; Gervasi, O., Ed.; Springer International Publishing: Cham, Switzerland, 2021. [Google Scholar]
- Fenton, N.E.; Pfleeger, S.L. Software Metrics: A Rigorous and Practical Approach, 3rd ed.; CRC Press: Boca Raton, FL, USA, 2014. [Google Scholar]
- Galin, D. Software process quality metrics. In Software Quality Assurance; Springer International Publishing: Cham, Switzerland, 2018; pp. 448–475. [Google Scholar]
- Salin, H.; Rybarczyk, Y.; Han, M.; Nyberg, R.G. Quality metrics for software development management and decision making: An analysis of attitudes and decisions. In Proceedings of the International Conference on Product-Focused Software Process Improvement, Cham, Switzerland, 11–13 December 2022; pp. 525–530. [Google Scholar]
- Singh, G.; Singh, D.; Singh, V. A study of software metrics. IJCEM Int. J. Comput. Eng. Manag. 2011, 11, 22–27. [Google Scholar]
- Alphonce, M. Enhancing Software Quality through Early-Phase of Software Verification and Validation Techniques. Int. J. Technol. Syst. 2024, 8, 1–15. [Google Scholar] [CrossRef]
- Srinivasan, K.P.; Devi, T. Software metrics validation methodologies in software engineering. Int. J. Softw. Eng. Appl. 2014, 5, 87. [Google Scholar] [CrossRef]
- Tao, H.; Chen, Y.; Wu, H. Theoretical and empirical validation of software trustworthiness measure based on the decomposition of attributes. Connect. Sci. 2022, 34, 1181–1200. [Google Scholar] [CrossRef]
- Verma, S.; Yadav, D.; Chandra, G. Introduction of formal methods in blockchain consensus mechanism and its associated protocols. IEEE Access 2022, 10, 66611–66624. [Google Scholar] [CrossRef]
- Liu, X.; Yu, W. A Review of Research on Blockchain Consensus Mechanisms and Algorithms. In Proceedings of the 9th International Conference on Intelligent Informatics and Biomedical Sciences (ICIIBMS), Okinawa, Japan, 2–5 December 2024; pp. 1–10. [Google Scholar] [CrossRef]
- Jangid, H.; Sharma, M.R. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the National Conference On Data Science and Network Security (NCDSNS), Tiptur, India, 28–29 July 2023. [Google Scholar]
- Liu, S.; Zheng, Q. A study of a blockchain-based judicial evidence preservation scheme. Blockchain Res. Appl. 2024, 5, 100192. [Google Scholar] [CrossRef]
- Assiri, M.; Humayun, M. A blockchain-enabled framework for improving the software audit process. Appl. Sci. 2023, 13, 3437. [Google Scholar] [CrossRef]
- Kanellopoulos, Y.; Antonellis, P.; Antoniou, D.; Makris, C.; Theodoridis, E.; Tjortjis, C.; Tsirakis, N. Code quality evaluation methodology using the ISO/IEC 9126 standard. arXiv 2010, arXiv:1007.5117. [Google Scholar] [CrossRef]
- Atanasijevic, S. Kvalitet u Razvoju Softvera, Kao Integralni Deo Softverskog Inženjerstva. Comtrade Digital Services, Belgrade, Serbia. 2022; unpublished work. [Google Scholar] [CrossRef]
- Antal, G.; Tóth, Z.; Hegedűs, P.; Ferenc, R. Enhanced bug prediction in JavaScript programs with hybrid call-graph based invocation metrics. arXiv 2024, arXiv:2405.07244. [Google Scholar] [CrossRef]
- Oliveira, P.; Aguiar, A.; Lima, F.; Ferreira, H.S. Evaluating code complexity and maintainability of dynamically-typed languages. J. Syst. Soft. 2019, 158. [Google Scholar]
- Colakoglu, F.N.; Yazici, A.; Mishra, A. Software product quality metrics: A systematic mapping study. IEEE Access 2021, 9, 44647–44670. [Google Scholar] [CrossRef]
- Yılmaz, R.; Buzluca, F. A fuzzy logic-based quality model for identifying microservices with low maintainability. J. Syst. Softw. 2024, 216, 112143. [Google Scholar] [CrossRef]
- Magableh, A.A.; Ata, H.A.B.; Saifan, A.A.; Rawashdeh, A. Towards improving aspect-oriented software reusability estimation. Sci. Rep. 2024, 14, 13214. [Google Scholar] [CrossRef] [PubMed]
- Gezici, B.; Tarhan, A.K. Systematic literature review on software quality for AI-based software. Empir. Softw. Eng. 2022, 27, 66. [Google Scholar] [CrossRef]
- Yilmaz, S.F.; Kozat, S.S. PySAD: A Streaming Anomaly Detection Framework in Python. arXiv 2020, arXiv:2009.02572. [Google Scholar]
- Sultana, K.Z.; Anu, V.; Chong, T.Y. Using software metrics for predicting vulnerable classes in java and python based systems. Inf. Secur. J. A Glob. Perspect. 2024, 33, 251–267. [Google Scholar] [CrossRef]
- Peng, Y.; Gao, C.; Li, Z.; Gao, B.; Lo, D.; Zhang, Q.; Lyu, M. Static inference meets deep learning: A hybrid type inference approach for python. In Proceedings of the 44th International Conference on Software Engineering, Pittsburgh, PA, USA, 25–26 May 2022; pp. 2019–2030. [Google Scholar]
- Suman, A.K.; Patel, M. An Introduction to Blockchain Technology and Its Application in Libraries. SSRN Electron J. 2021. [Google Scholar] [CrossRef]
- Narayanan, G.; Cvitić, I.; Peraković, D.; Raja, S.P. Role of blockchain technology in supply chain management. IEEE Access 2024, 12, 19021–19034. [Google Scholar] [CrossRef]
- Nakamoto, S. A Peer-to-Peer Electronic Cash System; White paper; Bitcoin: Nashville, TN, USA, 2008. [Google Scholar]
- Baset, S.A.; Desrosiers, L.; Gaur, N.; Novotny, P.; O’Dowd, A.; Ramakrishna, V.; Wu, X.B. Blockchain Development with Hyperledger: Build Decentralized Applications with Hyperledger Fabric and Composer; Packt Publishing Ltd.: Birmingham, UK, 2019. [Google Scholar]
- Li, D.; Wong, W.E.; Guo, J. A survey on blockchain for enterprise using hyper ledger fabric and composer. In Proceedings of the 6th Int. Conf. on Dependable Systems and Their Applications (DSA), Harbin, China, 22–23 September 2020; pp. 71–80. [Google Scholar]
- Gilbert, C.; Gilbert, M.A. Advancing Privacy Standards Through Education: The Role of Academic Initiatives in Enhancing Privacy Within Cardano’s Blockchain Ecosystem. Int. Res. J. Adv. Eng. Sci. 2024, 9, 238–251. [Google Scholar]
- Ta, M.T.; Do, T.Q. A study on gas cost of ethereum smart contracts and performance of blockchain on simulation tool. Peer Peer Netw. Appl. 2024, 17, 200–212. [Google Scholar] [CrossRef]
- Hussain, S.; Tahir, S.; Masood, A.; Tahir, H. Blockchain-enabled secure communication framework for enhancing trust and access control in the internet of vehicles (IoV). IEEE Access 2024, 12, 110992–111006. [Google Scholar] [CrossRef]
- Kirli, D.; Couraud, B.; Robu, V.; Salgado-Bravo, M.; Norbu, S.; Andoni, M.; Kiprakis, A. Smart contracts in energy systems: A systematic review of fundamental approaches and implementations. Renew. Sustain. Energy Rev. 2022, 158, 112013. [Google Scholar] [CrossRef]
- Marijan, D.; Lal, C. Blockchain verification and validation: Techniques, challenges, and research directions. Comput. Sci. Rev. 2022, 45, 100492. [Google Scholar] [CrossRef]
- Xue, Y.; Wang, J. Design of a Blockchain-Based Traceability System with a Privacy-Preserving Scheme of Zero-Knowledge Proof. Secur. Commun. Netw. 2022, 2022, 5842371. [Google Scholar] [CrossRef]
- Rajala, O. Impact of React Component Libraries on Developer Experience—An Empirical Study on Component Libraries’ Styling Approaches. Master’s Thesis, Aalto University, Espoo, Finland, 2024. [Google Scholar]
- Caschetto, R. An Integrated Web Platform for Remote Control and Monitoring of Diverse Embedded Devices: A Comprehensive Approach to Secure Communication and Efficient Data Management. Ph.D. Thesis, Politecnico di Torino, Torino, Italy, 2024. [Google Scholar]
- Nguyen, A.T.P.; Hoang, V.D. Development of code evaluation system based on abstract syntax tree. J. Tech. Edu. Sci. 2024, 19, 15–24. [Google Scholar] [CrossRef]


| Metric Name | Recommended Values |
|---|---|
| Lines of Code | / |
| Number of Children | 3–5 |
| Depth of Inheritance Tree | <5 |
| Total Methods Per Class | 5–15 |
| Inheritance Coupling | 0–2 |
| Cyclomatic Complexity (class) | <50 |
| Cyclomatic Complexity (Method) | 1–10 |
| LCOM1 | 0 |
| LCOM2 | 0–1 |
| LCOM3 | 0–2 |
| LCOM4 | 1 |
| LCOM5 | 0–1 |
| MIF | 0.8 |
| AIF | 0.8 |
| Coupling Factor | 0.1 |
| Response For Class | 100 |
| Metric Name | Current Value | Threshold | Validation | Required Refactoring Action |
|---|---|---|---|---|
| Lines of Code (LOC) | 600 | ≤500 | Invalid | Decomposes into smaller, functionally cohesive units |
| Inheritance Coupling (IC) | 3–5 | ≤0.5 | Invalid | Reduces dependence on inherited members |
| Lack of Cohesion (LCOM1) | <5 | ≤2.5 | Invalid | Groups related behaviors and remove unrelated logic |
| Lack of Cohesion (LCOM4) | 5–15 | ≤1.0 | Invalid | Improves internal method interaction |
| Attribute Inheritance Factor (AIF) | 0–2 | ≥0.5 | Invalid | Increases reuse of inherited attributes |
| All other metrics | Within threshold | / | Valid | / |
| Metric Name | Target Value | Justification |
|---|---|---|
| Lines of Code (LOC) | ≤500 | Reduces complexity and improves maintainability |
| Inheritance Coupling (IC) | ≤0.50 | Ensures minimal tight coupling with base classes |
| Lack of Cohesion (LCOM1) | ≤2.0 | Improves class cohesion and functional clarity |
| Lack of Cohesion (LCOM4) | ≤1.0 | Ensures meaningful interaction among methods |
| Attribute Inheritance Factor (AIF) | ≥0.5 | Promotes effective attribute reuse via inheritance |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Milutinović, J.; Milić, P.; Milenković, V.; Mekić, E.; Matović, A. Application of Blockchain Technologies in Verification of Software Metrics. Appl. Sci. 2025, 15, 5519. https://doi.org/10.3390/app15105519
Milutinović J, Milić P, Milenković V, Mekić E, Matović A. Application of Blockchain Technologies in Verification of Software Metrics. Applied Sciences. 2025; 15(10):5519. https://doi.org/10.3390/app15105519
Chicago/Turabian StyleMilutinović, Jovan, Petar Milić, Vladeta Milenković, Edis Mekić, and Ana Matović. 2025. "Application of Blockchain Technologies in Verification of Software Metrics" Applied Sciences 15, no. 10: 5519. https://doi.org/10.3390/app15105519
APA StyleMilutinović, J., Milić, P., Milenković, V., Mekić, E., & Matović, A. (2025). Application of Blockchain Technologies in Verification of Software Metrics. Applied Sciences, 15(10), 5519. https://doi.org/10.3390/app15105519












