5. Experiment and Evaluation
Experiment Setting: The recent study also uses an open (Jackson) queuing network [
41] to theoretically analyze the network with a blockchain network. In our paper, we used the simulation environment to analyze the performance of the entire presented system rather than performing mathematical modeling for the conditions.
Simulation Environment: For evaluation of our presented consensus, we develop an entire heterogeneous network model [
42] because our consensus has a side chain and parallel execution of the election mechanism. We develop a prototype simulation environment in C# to implement the proposed Nazfast consensus. In the implementations, we generated and used a pair of public and private keys for the encryption and decryption process. We implement all the cryptographic algorithms, such as RSA for encryption using a key size of 2048, SHA-256 for hashing output, which is 256 bits long, digital signature for authenticity, Merkle tree root for easy computation, and zero-knowledge proof for validating data. We also apply broadcast delay in our simulation to create a real-time environment. We calculate the propagation delay by using an exponential distribution [
43]. The calculation is provided in the Sea Shield paper [
11].
System Configuration: The proposed consensus is based on the PoS-PBFT blockchain network. This network can be used by any type of organization, large or small. The application of the presented consensus is not limited to cryptocurrency; it can be used in the health industry [
44], internet of things (IoT) [
45], media [
46], government [
47], and so on. Therefore, network nodes can be general-purpose computers and have general configurations; for that reason, we used the lowest system configuration for testing the simulation system.
The system configuration that is used for the entire implementation and testing for the Nazfast has the operating system Microsoft Windows 10 having system type x64-based PC with the Intel(R) Core(TM) i7-7700 CPU @ 3.60 GHz, 3600 MHz, four core(s), and eight logical processor(s). The system has 16.0 GB of installed physical memory (RAM) and 7.06 GB of available physical memory, while total virtual memory in the system is 31.4 GB. However, during the entire network system testing process, we used other configurations for obtaining results as well.
Network Size: We used a minimum node requirement of 500 and a minimum validator requirement of 90 for the simulation. Nodes are required for network system establishment. Nodes become validators, and the election mechanism requires a minimum of 90 validators; therefore, we also keep 90 validators as the minimum validator requirement to complete the process. We may run several simulations; in one simulation, 20 block creation cycles are made.
Number of Transactions: We do not restrict the number of transactions in the block; the network may decide the number of transactions by itself according to the network storage capacity. We run simulations with a minimum number of transactions, such as four to six.
Node Behavior: The system is Byzantine fault-tolerant and may survive under malicious activities by nodes. We evaluated the complete system under different conditions. Malicious activities that are possible in the system, and the node responds to those conditions.
Evaluation:
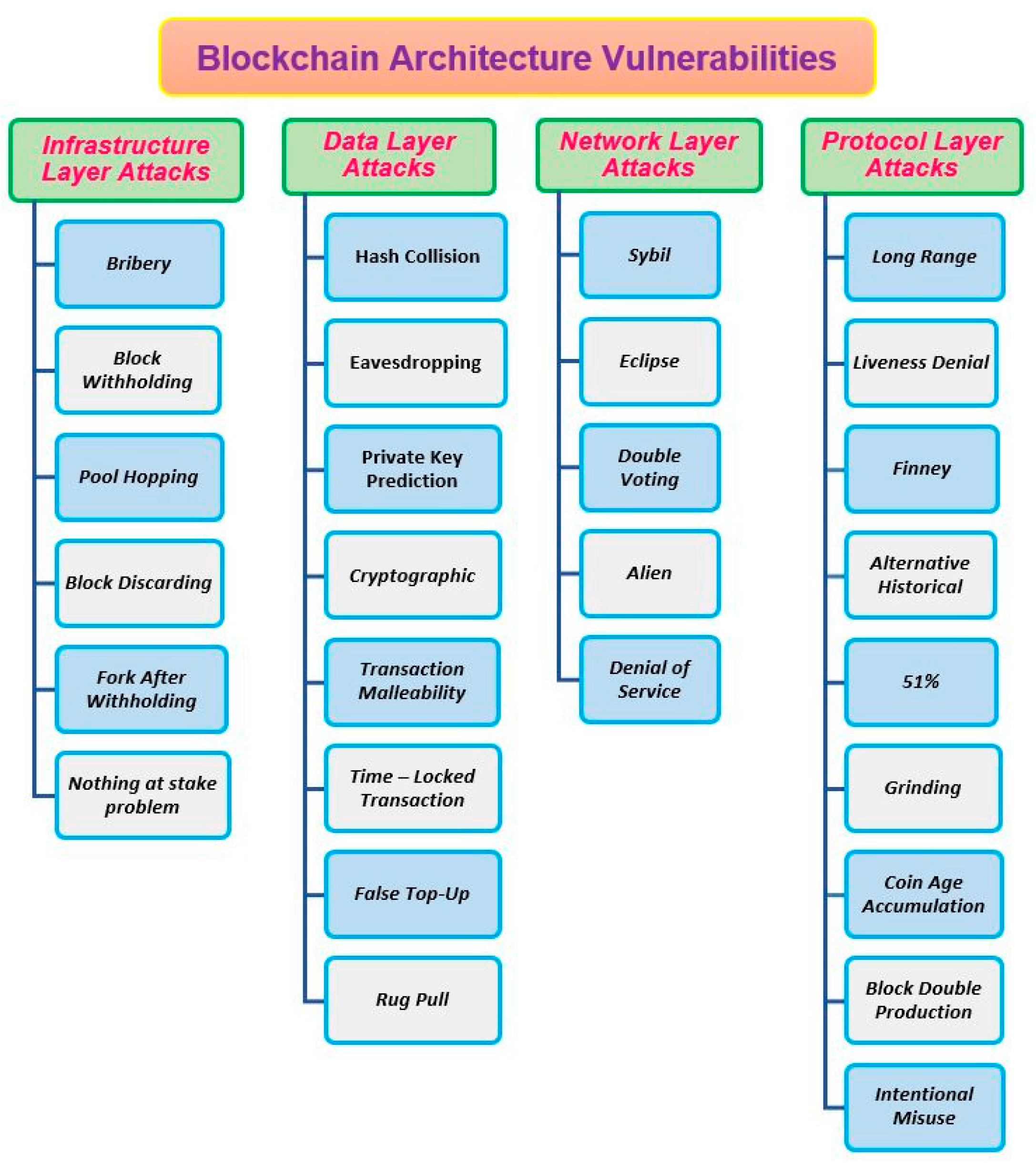
For the entire network security evaluation of the Nazfast system, we divide the blockchain architecture into several layers, similar to a traditional network’s Open System Interconnect (OSI) model [
48], because communication on the blockchain network also consists of different sections. There is no formal architecture layer defined in the literature on the blockchain. Hence, we defined it as an infrastructure layer, data layer, network layer, and protocol layer. All those layers of blockchain architecture are involved in the communication. The application layer may also be considered a blockchain layer. However, we have not worked on the application layer in our proposed work. We have tested our proposed blockchain architecture layers under different conditions to examine the security, scalability, and decentralization of the Nazfast consensus. In this section, we only provide security evaluations. Many attacks are tested on a simulation, and few are controlled logically. We discuss the logically controlled attacks thoroughly in this section. Further evaluations are presented in the discussion section,
Section 7 of the paper.
Figure 9 provides a short overview of security attacks that are discussed in this paper under the umbrella of blockchain architecture. We provide a brief discussion on each security condition result below.
Infrastructure Layer Vulnerabilities
The infrastructure layer is the basic layer of the blockchain, in which hardware and software are included. The infrastructure layer defines the network’s nature because blockchain networks are either private, public, or a consortium of any type [
49]. After nature, the initial infrastructure nodes are the second main module of the blockchain network. Below, we discussed the vulnerabilities that can somehow affect the infrastructure layer of our proposed blockchain network.
Condition: A bribery attack is considered a severe attack in blockchain [
50]. In bribery attacks, validators engage in conspiracies in the network so that they can make other validators biased by performing any type of forgery. By this attack, validators may obtain confirmation of forged transactions in the block by gaining acceptance from other validators. Our consensus may suffer from this attack. The main chain blocks can be forged by bribery. We used some techniques to overcome this attack, as below.
Result: We try to control the bribery attack by selecting block producers in a very challenging way. S&Sem gives all the required control over the block producer selection. It controls the bribery attack by using different techniques, such as the winners of the last election cannot take part, multiplication by a random number, extra bonding time commitment, and so on. The short-range attack is also a type of bribery attack. Our system resists this attack well because when a validator wants to get its staked coin back and unjoin the network as a validator, it first has to pass its extra bonding time duration, and then a validator can get its coin back. Extra bonding time improves security because a longer bonding time reduces short-range attacks. A validator can be easily punished if its coins remain in the stakes for a long time after the election process.
- 2.
Block Withholding Attack
In this type of attack, the attacker becomes part of the block production team but does not produce a block [
51] or a block that has not been received by others for any reason in the system. This type of attack is also possible in our consensus mechanism. Our consensus may suffer from this attack. We tested this attack under multiple conditions and observed the results of the consensus resistance after this attack.
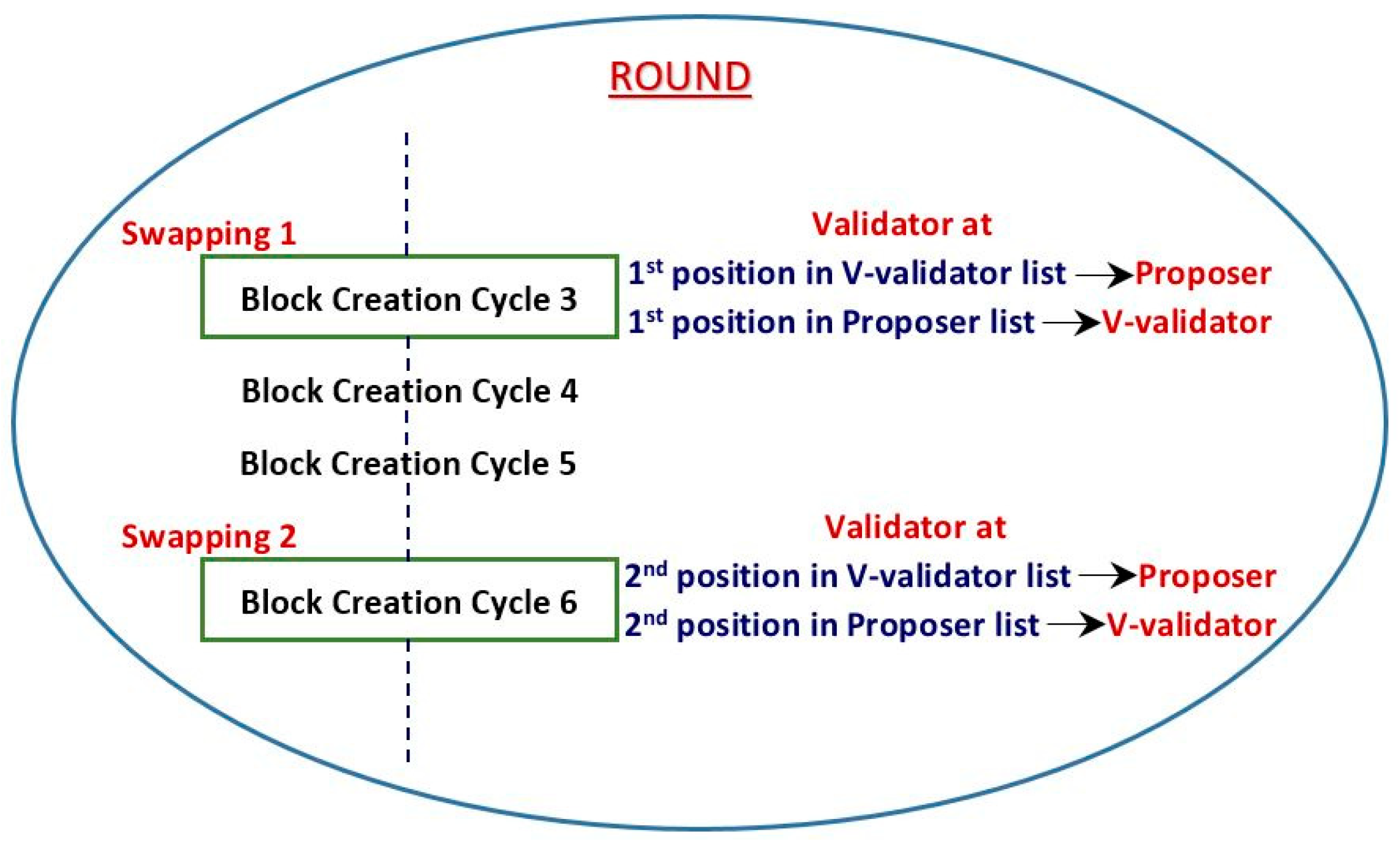
Condition: If the block proposer of the main chain does not produce a block within its specified time.
Result: We tested the issue on different block creation cycle numbers and used a swapping mechanism to solve the issue. We applied the complete swapping mechanism described in
Section 4 and selected new block producers for the block creation cycle.
Condition: If the wildcard entry validator does not receive a proposal or an invalid proposal.
Result: The wildcard will respond if the proposal is valid or not; if the proposal is not valid, it responds nil. If the proposal is not received, it responds with a process error because wildcard response is very important and has to respond in any situation.
Condition: If the block proposal is not sent to all the v_validators of the block creation cycle.
Result: We observe the following two results for this condition:
(a) If more than 2/3 of the V-validators receive the proposal block, then consensus will not stop, and a block will be created in this block creation cycle.
(b) If less than 2/3 of the V-validators did not receive the proposal block, then consensus will be affected and a block will not be created.
Condition: After V-Validators, we have correctors in our system to validate the block. If correctors do not commit, broadcast the block on time, and hold it in the network.
Result: Our system resists this attack by using a reward mechanism. We attracted correctors to receive the election starter title as a reward. Correctors need to complete their jobs the fastest to gain this title. Because the corrector who did the fastest commit job will become the next election starter and would be rewarded by the system, the corrector would do their job as soon as possible. There are also rewards for forgery caught in the block for the correctors in the system. Due to both mechanisms, the probability of completing the consensus on time with honesty becomes high. The security and liveness of the consensus also improve.
- 3.
Pool Hopping Attack
Condition: In this attack, block producers only create blocks when the block rate is high in the system. It may weaken the liveness of the network. Others also try to prevent this attack in their blockchain system by using different techniques such as smart contracts [
52]. Our system may also encounter this attack, and we used different techniques to resist this attack.
Result: In Nazfast, the block producer is already selected by S&Sem. The S&Sem attracts validators to become block producers in many ways, such as to become valid validators and to gain excellency points, they must participate in the election process. Therefore, the rate is just one factor in the system. However, it may become a problem if the Nazfast block producers do not create a block in the network due to rate fluctuation. Hence, we suggested a uniform block production rate in the system to prevent a pool-hopping attack.
- 4.
Block Discarding Attack
In this type of attack, an attacker intentionally discards other blocks in the block creation process so that only pre-decided blocks can get approved in the system [
53]. It is performed by an attacker or a group of attackers in the system. They can forge the transaction by attempting this attack on the blockchain network system. We discuss a few situations of this attack in our consensus.
Condition: If the prevote does not send to the whole V-validators.
Result: There are also two situations.
(a) The consensus gets affected if V-validators of the block creation cycle do not receive prevotes from 2/3 of other V-validators.
(b) The consensus does not get affected if the V-validator receives at least 2/3 prevote of others and does not receive prevote from complete other V-validators of the block creation cycle.
Condition: Not all prevote sender’s validators send pre-commit to the correctors.
Result: The block will not be created by correctors if a minimum of 2/3 pre-commit is not received by V-validators.
Condition: All correctors do not send a commit.
Result: The corrector cannot proceed if it does not receive all the commits for the block. After a timeout, the block will be discarded if it does not receive all commits.
- 5.
Fork After Withholding Attack (FAWA)/Selfish Mining
Condition: In a fork withholding attack, in this type of attack, the attacker holds the valid block and does not release it to the network. Instead, they keep it private. After some time, the attacker releases the withheld valid blocks to the network to create a fork in the system [
54]. This attack was found in early consensus mechanisms, such as in Bitcoin [
1]. This attack is almost similar to a selfish mining attack [
55]. It is also a high-severity attack in the previous blockchain consensus. An adversary creates/mines the valid block and does not broadcast it to the network. Upon broadcasting the blocks, they create a fork, and it can hijack the main chain. Both attacks are similar in disrupting the network and the block propagation issues but only differ in their strategies. We discuss both attacks on our consensus together in the conditions below. If the block producer holds the block and does not produce on time and tries to create a fork in our network system.
Result: To create a successful fork in the network system, several valid blocks should be broadcast together. Our system is resistant to this attack because we only allow one block at a time. Every block creation cycle has a block producer to produce a block. If it does not broadcast a block in its turn, the block will be useless because, at the end of every block creation cycle, the block that does not get committed should be dissolved by the block creator and the transaction returned to the pool. However, if the block producer keeps the block for further broadcast, it is also not possible. We used a strong block producer selection process in our consensus that does not allow block producers to get reelected again easily.
- 6.
Nothing-at -Stake Problem (Attack)
Condition: Most of the previous PoS-based consensus algorithms face an issue that is called the nothing-at-stake problem. In which an adversary tries to create an alternative chain to gain profit by losing nothing. It does forgery in the system with nothing to lose [
56]. Others try to solve this issue by using different techniques [
57]. Our consensus resists this issue in different ways.
Result: Our network system used Sea Shield to save bond transactions, and we used a long process to release the bond. If the validator needs to take their stake back, the network will stop the validator from any type of contribution as a validator and make them stop until they complete the unjoin process. The total time calculation of S&Sem also contributes to resisting nothing-at-stake problems because it contains coin age and the extra bonding time factor of the validator.
Data Layer Vulnerabilities
In a blockchain network, transactions are considered a main component of the data layer. There are multiple choices of data storage available in the blockchain, on-chain and off-chain. Both have their advantages and disadvantages [
58]. We suggest on-chain storage for our proposed work because it provides immutable and transparent data. To increase the security of the data, the blockchain uses different cryptographic techniques to secure its data from any forgery. We apply the cryptography technique ‘zero-knowledge proof’ [
37] to verify the data. This technique proves the data without revealing it. We used this technique in many places to maintain the privacy of the system. We also used multiple cryptographic techniques to secure the data. Below, we discussed these techniques.
Hash Collision Attack: The hash collision attack affects the data layer of the blockchain. When two or multiple inputs have similar hash values, it is called a hash collision attack. To avoid this attack, we used the SHA-256 secure hash algorithm to hash the data layer in the proposed system. The SHA-256 algorithm [
59] for hashing in the complete system also improves the authenticity of the system.
Eavesdropping Attack: It is considered a low-severity attack in blockchain networks. In this attack, an adversary tries to gain sensitive information to disrupt the network. To avoid such a type of attack, cryptography algorithms’ symmetry and asymmetry [
60] are mainly used to encrypt the network data. We used strong encryption asymmetry algorithms such as the Rivest–Shamir–Adleman(RSA) algorithm [
61], to protect our network system.
Private Key Prediction: The RSA algorithms used public keys [
62] and private keys [
63] for the encryption and decryption process. The encryption depends on the private key in the system. The private key should be kept secret and should not be easily guessed by anyone else. We used a strong cryptographic pseudorandom number generator [
64] to avoid a private key prediction attack.
We used cryptography techniques to reduce attacks on our proposed blockchain network system data. However, our proposed system data layer may be attacked under the conditions below. We tested the conditions and derived the possible solutions to the issue according to our network system.
In this type of attack, an adversary tries to gain access to the sensitive data by breaking the cryptographic processes that guard these data [
65]. These attacks weaken the authenticity, integrity, or validity of the system. We also tested some conditions that may encounter cryptographic attacks. We apply the strongest encryption, decryption, and hashing algorithms as a prevention from cryptographic attacks in the consensus.
Condition: If the block is not sent by the block proposer.
Result: Every receiver validator first confirms whether the block is sent by the proposer or not by checking the digital signature [
39] of the block. If the block is not sent by the proposer, the block will be rejected by others.
Condition: If an invalid transaction is received in the block.
Result: After the verification of the block sender, if the block is sent by the proposer, then the receiver validator will validate the block by checking the transaction validity by zero-knowledge proof [
37] and report forgery if necessary.
- 2.
Transaction Malleability Attack
It is a very critical attack on blockchain consensus. In this type of attack, the adversary tries to change their ID before block confirmation to obtain the deposit twice from the network. This attack has been addressed by others as per their work [
66]. Our network system may also encounter a situation related to this attack. The situation arises when the validator changes its identity from validator to node in the network.
Condition: We have seen a special transaction that is performed by an unjoin validator in Sea Shield [
11]. The unjoin block of the validator chain is created with an unjoin transaction by a validator. It is like a dummy transaction because the validator does not receive the stake amount at the same time when the transaction is made. Generally, the transaction is considered as confirmed just after the block finalization, and the receiver may use its amount, but in the Sea Shield, the host will release the stake amount to the unjoin validator after the complete unjoin process. The unjoin block is posted in the network, but the receiver has to wait for the complete unjoin process of Sea Shield to use that unjoin bond coin. In this situation, the unjoin validator may claim that it did not receive an amount from the network and try to obtain twice the amount from the network or use that amount before the host released it to the validator because it was present in the unjoin block.
Result: For the security and integrity improvement of our network, we introduced a transaction posted by the host in the main chain of Nazfast after releasing the stake to the unjoin validator. We added this transaction in the block of the main chain so that the unjoin validator will not claim that it did not receive the amount from the host. The transaction holds the proof that the host has released the amount to the unjoin validator. The main chain block validation committee also validates the transactions of the block that used the unjoin coin of any previous network validator to stop forgery in the system.
- 3.
Time-Locked Transaction Attack
Condition: In this type of attack, an adversary uses coins that are in locked form in the network. The coin is not allowed to be used for some specified amount of time, such as when one party has padlocked some tokens for a specified time and attempts to spend them before their release time [
67]. In our consensus, we have bonded coins in the network. The validator may try to use that bonded stake before unjoining the network. However, we resist the attack by using the approach below.
Result: This attack is not possible in our system because we used a validator chain, and all the bonded stake transactions are present in the chain. All V-validators and correctors have this chain. Also, the host has posted a transaction on the main chain that has details of the unjoin validator’s coin. While validating transactions of the block, they can validate the transaction from the validator chain and the main chain, and if they find forgery, they can reject the transaction.
- 4.
False Top-Up Attack
Condition: It is a critical exploit that can squeeze all the coins from the blockchain system, in which an adversary makes a false transaction in the system and obtains the right coins [
68]. Suppose this attack is successful; it can cause significant damage to the system. We used wildcard entry validator to resist this attack in the system, as discussed below.
Result: The purpose of the wildcard entry validator is to improve the security of the consensus process. If someone tries to dishonestly select all 30 validators, there is a possibility that the wildcard entry validator will be honest and report the dishonesty of others. There is also a time constraint to make the wildcard entry validator dishonest by others because the wildcard entry validator joins just before the block creation cycle, so it is not pre-determined by any other member of the network. This feature also improves its security.
- 5.
Rug Pull Attack
Condition: A rug pull attack is considered the deadliest attack in blockchain [
69]. The attacker stacks a good/fancy token in the blockchain. However, after some time, when the network trusts the node and shifts its token/amount/reward to the attacker, the attacker instantly withdraws the amount and leaves the system by performing any type of forgery. We can also encounter this risk in our proposed consensus because it uses coin staking in the network for nodes to become validators, so we consider the following solution to reduce the security risk of the network.
Result: The system used Sea Shield consensus to save the nodes’ records in the validator chain when they become validators or leave their responsibilities as validators in the system. It used an extra bonding time concept and a long procedure to join and unjoin the network while taking care of the network security. By using Sea Shield consensus, rug pull attacks becomes very difficult in the network.
Network Layer Vulnerabilities (P2P)
The network layer creates an environment for data transmission within the entire blockchain network. The peer-to-peer network architecture [
70] makes data communication possible in the blockchain network. The blockchain uses many security measures to maintain the confidentiality of the data. Every piece of data that is received in the network does not get accepted because there are many security checks available in the blockchain. After all verification processes, the data will be accepted in the system. The trusted execution environment (TEE) ensures the integrity of the data transmission in the network. Below, we discuss the vulnerabilities that are possible in our presented mechanism network layer.
Condition: A Sybil attack is a very acute vulnerability of the blockchain system, in which an adversary may control many nodes of the network system by creating multiple identities to do forgery or misconduct [
53]. Our presented consensus can be threatened by Sybil attacks. We try to avoid this attack at some points of our consensus, such as in the block producer selection part, as below.
Result: S&Sem gives protection from Sybil attacks. It uses the concept of a vote flag that mitigates false identity forgeries in the network during the block producer selection. The vote flag is a combination of multiple elements and is only released to those validators who do not request to unjoin the network. The validator who is already about to leave the system cannot become part of the election mechanism competition. The list of active validators is released by Sea Shield to the S&Sem because it contains all the details of the active validators in the system. The Sea Shield keeps track of all the active validators of the system so that the network restricts them from participating in the voting process. After using the vote flag in the system, it will become very difficult for users to create their multiple IDs or vote in the system. The details of the vote flag are discussed in the paper [
12].
- 2.
Eclipse Attack
Condition: This attack is performed in the network layer of the blockchain. The adversary tries to manipulate nodes one after the other. The adversary disconnects a node from the network and connects it to a malicious node in the network [
71]. In this attack, the adversary attacks a single node or a selected part of the network. Our consensus may be attacked by this condition.
Result: In our consensus, we used the concept of host. The host updates the network peers before every election process. We have observed it in step 1 (network setting) of the S&Sem process. If this attack happens in our network system. The network will soon be able to get its original form back. This attack will not last long in our proposed blockchain network.
- 3.
Double Voting Attack
Condition: This attack happens in the blockchain network that uses a voting mechanism to select the block producers. The adversary may broadcast multiple votes in the system during voting so that the system may crash, delay, or lose liveness. We can also encounter this problem in our consensus because we used an election mechanism in our consensus to select a block producer. We resist this attack in the following way.
Result: The election mechanism used voting in the selection process. Hence, the election mechanism results directly affect our consensus. Therefore, S&Sem used a check duplicity round in the election mechanism to stop this attack [
12]. We also inherit all the reward systems of the S&Sem in our network. Therefore, we attract validators by rewards to find duplicity in the voting process. It also controls malicious activities in the system.
- 4.
Alien Attack
Condition: A blockchain network contains many nodes, which can be near or far, according to the network. Sometimes, it becomes hard for nodes to distinguish themselves in the network due to the pool population. Therefore, this attack is also called a peer pool population attack. This attack was first identified by the SlowMist Team. This population leads to an alien attack on the network. Alien nodes distract real nodes of the network. They can appear between two nodes, apply a delay, and cause falsification [
72]. Below, we discuss the attack on our network.
Result: We have also proposed a blockchain network consensus. It could have more nodes and can deal with this situation. Furthermore, in our network, the validator plays a very important role, and they have to get each other for the S&Sem election and Nazfast consensus; therefore, an alien attack has to be controlled. ID chain is considered to be the best solution for this issue. We used a validator chain to save the validator’s record so that every validator has a unique ID, and all the other network validators have access to this information because the validator chain is also a blockchain. By using a validator chain with Sea Shield consensus, the network validators will not get confused or disturbed due to the pool population attack because of any alien in the network, and also, aliens would not create any conflict between peers. The network also constantly updates and manages its peers for continuous improved progress.
- 5.
Denial of Service Attack
Condition: It is a low-severity attack in the blockchain. In this attack, an adversary tries to attack the system by creating numerous requests to the network. The network gets flooded due to over-requests, and as a result, it will be out of service [
73]. Other proposed solutions, according to their network, such as [
74], have been proposed for efficient and flexible DDoS mitigation solutions. In our consensus, we also deal with this situation at some point.
Result: It is possible in all four phases of the Nazfast consensus. Any committee member may broadcast multiple votes or proposals to the network in any phase. The other committee member will only consider the first received proposal or vote in any phase, and discard the remaining others. It may slow down the system, but the network may come out of this condition. The system may punish the adversary by checking the digital signature.
Protocol Layer Vulnerabilities (Consensus)
The protocol layer is an essential part of the blockchain network. A consensus mechanism determines how peers reach decisions in the network. There are many protocols available in the literature for different types of blockchain networks, such as CE-PBFT [
75], ReVo [
76], Proof of Fairness [
77], and FuzzyChain [
78]. We also present a consensus mechanism in this paper for a PoS-based blockchain network with improved efficiency. As we discussed, this is the main component of the blockchain, and it should not be attacked. However, our presented mechanism may be attacked in different ways. Below, we evaluate the conditions that can affect our system and its countermeasures.
Condition: In this attack, an adversary tries to create a fork in the blockchain. The new branch contains a partially or completely different history from the base chain. Such as consider our main chain Nazfast (Nf) blocks (Nf0, Nf1, Nf2, Nf3, …., Nfn). An adversary tries to transform Nf into Nf’ consisting of k ≥ n blocks so that (Nf’0, Nf’1, Nf’2, Nf’3, …., Nf’k) [
79]. With time, the branch becomes longer and succeeds the blockchain. The adversary may have confirmed forged transactions in the system by using this fork. Our system may encounter and resist this attack as below.
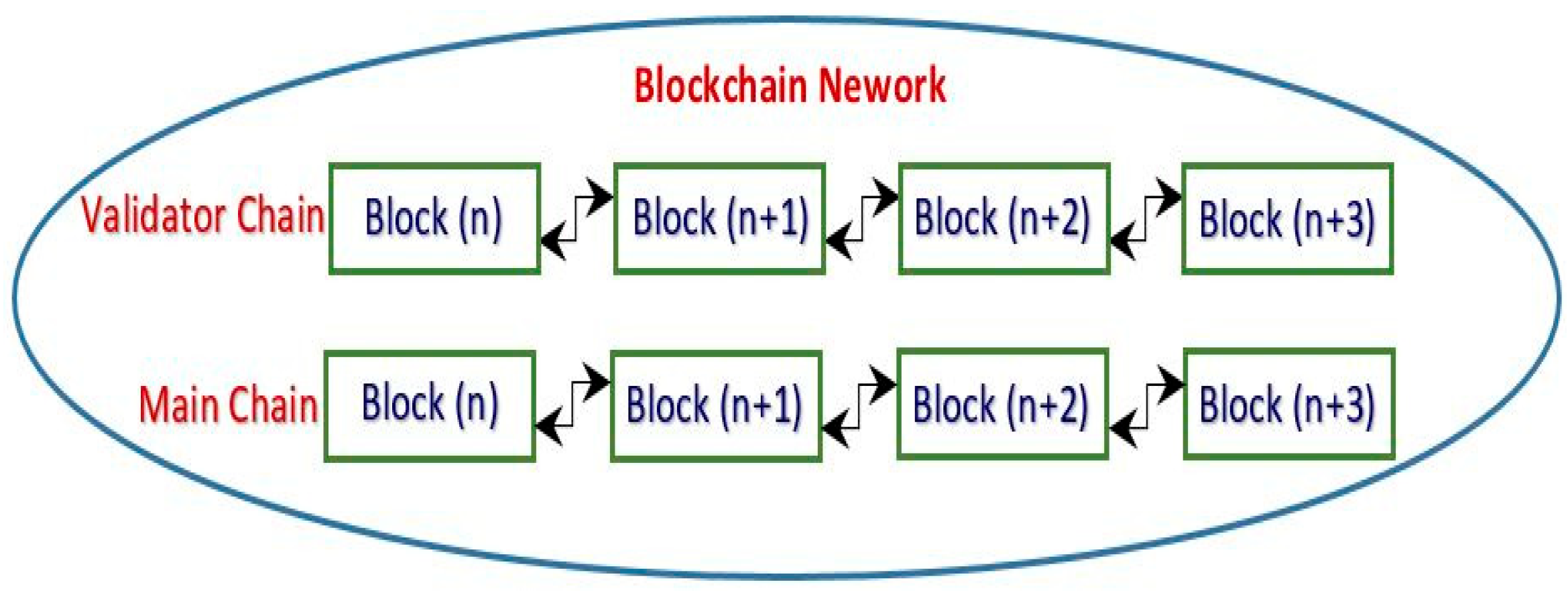
Result: Our system is resistant to this attack. The proposed network used two consensuses: Sea Shield for the validator chain and Nazfast for the main chain. Both consensuses are resilient to forking. We already described the forking issue of Nazfast in the discussion section of the paper and the forking issue of Sea Shield in the paper [
11]. Mainly, the proposed architecture of both consensuses does not create a fork in the network. We control this attack in our system by not allowing forking in the blockchain. We control the issue by not creating a fork because Sea Shield results are used by entire networks such as S&Sem and Nazfast. The Nazfast consensus used S&Sem election results, and S&Sem used Sea-Shied outputs. Therefore, we designed the fork without consensus. Due to its fork-free nature, it is also resilient to long-range attacks.
- 2.
Liveness Denial
Condition: This attack happens when, intentionally or unintentionally, the block production in the blockchain network stops. It leads to a temporary or permanent network shutdown [
80,
81]. We also deal with the situation in our proposed work.
Result: Nazfast consensus required S&Sem results to complete the process. For any reason, if S&Sem cannot work and the Nazfast runs out of the block producers’ list, then the block production will be stopped in the network. To resist this situation, we suggested holding three elections before the start of the next round.
- 3.
Finney Attack
Condition: In this attack, an adversary pre-mines/creates a block with a transaction and creates an identical transaction before the pre-mined block is broadcast to the network. It will cause a transaction forgery in the system [
82]. This attack is common in previous blockchain consensus, such as in the PoW consensus [
83]. It is like a class of double-spending attacks [
84]. Below, we discuss how our system resists this attack.
Result: This situation may not be created in our system because the block producers are selected by the strong S&Sem. It is very difficult to pre-determine who will get selected for the block production in the next election by S&Sem, and if they become the block producer, they would have very little time to manipulate the system. Nodes are unaware of their selection, so when they become a block producer, they will create a block with the recent transactions that are present in the pool and broadcast it in their turn. For instance, if it happens, then the block validators and correctors of the block will check the transaction validity. Each block creation cycle has only one block, and the finalized block is broadcast to the whole network. All transactions in the network are considered invalid/unconfirmed until they become part of any block. Therefore, the identical transaction has not created any problem and gets rejected when it becomes part of any future block.
- 4.
Alternative Historical Attack
Condition: This attack is also called a block reorganization attack in many places. This attack requires huge computing power to perform. In this attack, an adversary sends a transaction to the recipient and simultaneously tries to create a fork in the network with the transaction that returns the same amount. Suppose the adversary succeeds in creating a longer chain than the main chain. The forged transaction will be confirmed in the network [
85]. It is also a type of double-spend attack.
Result: Our network is resistant to this type of attack because it does not allow forks. Every block creation cycle has its height number, and only one block is created at one height. The network will not increase the height number until the block is created and finalized by all committees of that block creation cycle number. Only the block that obtains its final commit is broadcast in the whole network. Every node has the same previous block hash in the network. So, if the block producer creates a block with a different previous block hash, the V-validator and corrector will apply forgery on that block producer at the time of validation. Suppose all the V-validators and correctors together try to validate a block that has a different previous block hash created by an adversary block producer and give its final commit; then the host will stop it because we have a host entity in the network that has all the records of the main blockchain, and the host confirms the previous block hash in every block before broadcasting it in the network to control the forking. The network nodes can also raise complaints about the different previous block hash in the received block to control any type of forgery in the network. This attack is only possible if the adversary has control of more than 2/3 of the total network nodes, and achieving such significant control over the network is not a piece of cake.
- 5.
51% Attack
Condition: This attack is the most highly severe attack in the blockchain consensus. Almost every blockchain consensus encounters this type of attack in its network. In this attack, a single entity has very high powers in the network. It might be because of its high stakes or computational power in the network. It can lead to a 51% attack [
86], in which the majority has the ruling power of the network. Our consensus may resist this attack under the following conditions.
Result: This attack affects the decentralized nature of the blockchain network. Our consensus tries to avoid the influence of a single entity in the network by using S&Sem. The S&Sem has multiple factors to get selected for the block producer, such as total time calculation, stake value, voting, and randomization. Because of all these factors, a single entity cannot control the whole system.
- 6.
Grinding Attack
Condition: Grinding attacks are also very dangerous for blockchain networks [
87]. A validator may precompute the protocol so that it can manipulate the block producer selection process to select it as the block producer/slot leader for the next block creation cycle. Some protocols use randomness to avoid this attack [
88]. We also control the attack in our network with the below solution.
Result: We used S&Sem in our network, and S&Sem reduces grinding attacks since it is very difficult to pre-determine the block producer in the network. The S&Sem process creates so many constraints for the validators that they cannot become block producers by forgery. It is not easy for the validator to manipulate the network and become a block producer by using any incorrect approach in S&Sem.
- 7.
Coin Age Accumulation Attack
Condition: In a coin age accumulation attack, a validator may have enough time and resources so that it can manipulate the system by its powers. The attack is also addressed by others in the literature, such as [
57]. In this attack, due to the saturation of resources, an adversary can easily be selected for the block producer/slot leader in the selection. The Initial consensus of PoS used the coin age mechanism in its consensus for block validator selection, such as PPcoin [
89]. Coin age calculation depends on the number of coins. Coin age calculation is used to strengthen the consensus by encouraging long-term participation in the network. We also used this technique in our election mechanism, S&Sem. The coin age technique is very useful for engaging the validators long-term in the network. It improves the liveness of the network. However, due to coin age calculation for validator selection, it may lead to coin age accumulation attack [
90,
91].
Result: By using S&Sem and Sea Shield together, we control this attack in our system. The S&Sem used other parameters with coin age calculation, such as stake value, extra bonding time commitment, vote value, and randomness. Coin age calculation is also secured by Sea Shield because we use a validator chain to store coin age, stake value, and extra bonding time in the network; therefore, manipulation is not possible with the data record.
- 8.
Block Double Production Attack
Condition: In this attack, a block producer produces many blocks simultaneously at a single height to pollute the network system [
92]. It can lead to other attacks in the system as well, such as short-range or long-range. Our system may encounter this attack.
Result: Our block producer may create and broadcast multiple blocks together at their turn to the block-validating committee of the network. Our system will resist this attack logically. Our network system allows one block at one height during the block creation cycle. If any member of the block creation committee receives multiple blocks from a similar sender (sender confirmation by the digital signature of the block), it will only consider the first block that it has received from it and discard the remaining received blocks. The block creation cycle will only proceed for a block that has 2/3 prevote. If a block obtains a 2/3 prevote among other blocks from the committee, the other blocks definitely cannot obtain the required prevote from the network and automatically get discarded from the system; the only block that will proceed further is the only valid block. The system may punish the block producer if it finds an intentional block double production attack from the block producer in the network.
- 9.
Intentional Misuse
Intentional misuse is also considered a security risk in blockchain. The validator intentionally forged the system by using any wrong means. Many types of intentional misuse are available in the blockchain [
93], such as 51% vulnerabilities, liveness attacks, and Selfish mining. We evaluated a few intentional attacks that can damage our proposed network system, such as the proposer creating a forged block and sending it to V-validators. We tested this scenario under two different conditions.
Condition: The proposer creates an unfair block and sends it to a few V_validators.
Result: If only a few validators receive a forged block, consensus will not stop, and a block will be created. However, if forgery is confirmed by any V-validator, the host will check whether it is a network attack or from the proposer itself. If the proposer attacks, the proposer will be punished by the network.
Condition: The proposer sends a forge block to more than 2/3 V_validators.
Result: The network will confirm the forgery; if it is not a network attack, then the proposer will be punished for creating the forged block.
We have other intentional mistakes that can emerge in our system, such as those we discuss below.
Condition: The corrector sends an incorrect forgery report to the host.
Result: The proposer created a fair block, and all but a few correctors sent a forgery report to the host to receive the forgery reward. The host will confirm and apply a penalty to those correctors who sent incorrect forgery reports to the host.
Condition: The Wildcard validator tries to become dishonest while selecting the next wildcard validator.
Result: In our proposed system, every wildcard entry validator selects the next wildcard entry validator from a pool where their identities are hidden from the system. The wildcard validator selects the next wildcard anonymously. However, if somehow the wildcard entry validator does any planned attack, such as selecting a malicious validator as a wildcard entry intentionally for the next block creation cycle. The system has 2/3 liveness; hence, the wildcard entry validator response cannot affect the block creation cycle. However, this situation would not last long because the system updates the pool randomly with the hidden identities just before every wildcard entry selection, so that no one knows the true identity of the wildcard before selection. Moreover, the system also broke the sequence after the 20-block creation cycles, and the election starter will select the next wildcard entry validator from the pool. The election starter is also unknown, and who the election starter will be will be revealed at the end of the 20-block creation cycles. Therefore, in the first block creation cycle of every round 1, the election starter selects the wildcard entry validator to stop the intentional attack in the system.
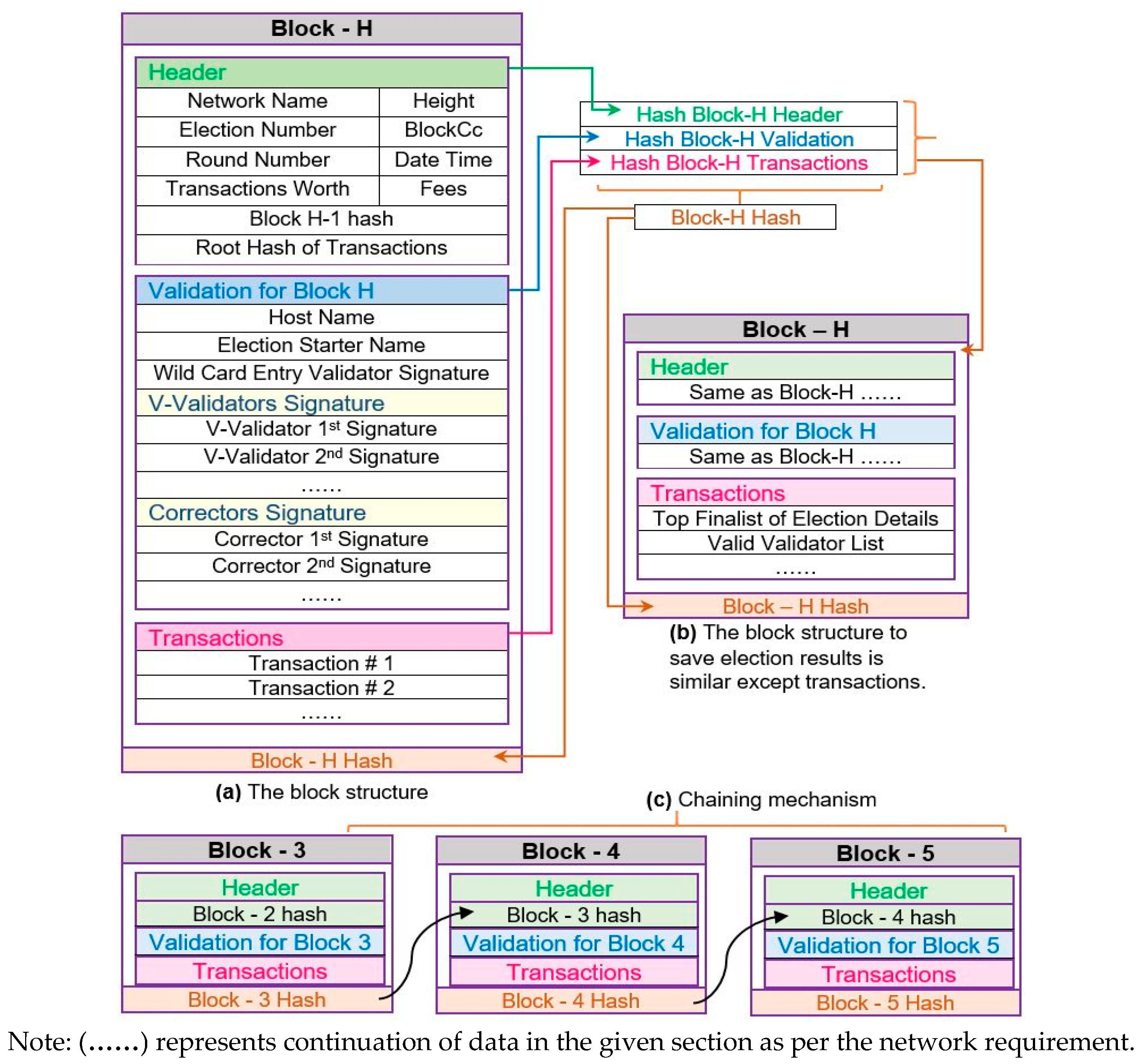
We are summarizing the list of vulnerabilities in
Table 5 that can affect the block finalization time and validators’ participation in the network. We have already discussed that the system may be affected by these attacks; however, it will soon recover from the attack. Because our system has the capacity to resist and recover from the attacks, as we explained above.
6. Discussion
Comparison with Tendermint on Security Aspects
Our presented consensus is different in many ways from the Tendermint consensus. Below is the list of the differences between our consensus and the Tendermint consensus. These changes feature the Tendermint consensus to improve the security of the entire presented network system.
In our proposed system, to mitigate the risk of forging due to a pre-determined block proposer by-election mechanism, correctors and the additional concept of wildcard entry validator with V-validator are used in the consensus mechanism. These security measures are not present in the Tendermint consensus. Although Tendermint consensus does not use an election mechanism for block proposer selection, instead, it uses a round-robin algorithm to select the block proposer. Still, there is a chance of forgery due to the block proposer in the network. We used these concepts to improve the security of the Nazfast consensus. Beyond the V-Validator set of a block for validation, Correctors are an additional block security verifier in the block creation cycle. Any intentional forgery due to pre-determined proposers will also be controlled in the network by a wildcard entry validator.
- 2.
Saving the Election Record
The validator set that validates the block in the network changes over time. In Tendermint, knowing the validator set that validates the particular previous block in a chain is a slow process and also computationally data-intensive. We need to download all previous blocks before that specific block and verify by checking the digital signature and hashes. Execute the corresponding transaction to obtain the change in the validator set so that the exact validator set of the block can be achieved [
94]. In our proposed mechanism, the election result will be the validator set for block creation cycles. We saved the election result in the main chain block to resolve any future conflict or dispute between validators. It will be fast and take less computation than other methods to get the validator set in the future. Also, we used a swapping mechanism and wildcard entry validator concept in the block creation process, which is why the election result must be saved so that we can trace the validation set of a particular block easily. Election results should also be saved in the blockchain system as a permanent record for future penalties and punishments against any forgery to improve the overall security of the network.
- 3.
Anonymous Block Forgery Catcher
In Tendermint, we have not found any way to catch forgeries after a block is broadcast into the network. Once the block is released to the network, it is finalized and cannot be altered. However, there is still a chance of forgery in the block due to the block validation set falsification. We use the concept of a block forgery catcher in the network to control any misconduct in the network system. After the broadcast, the forged block can be identified and punished by the network by using the anonymous block forgery catcher. Our blockchain network system also perceives the feature of no editing in the block after block finalization in the network. After the confirmation of forgery, the network will not edit the false block; instead, it creates a new block and adds it to the chain that contains all the falsification details of the forged block. The block will be created and validated as a regular block by the recent block creation committee of the network. The network will also punish the block proposers and the committee for the false block.
- 4.
Validation Committee Signatures
Tendermint adds the last block commit in the block to keep signatures safe. It collects all the commits of the last block and adds them into the recent block. During this time, the commits can be lost or edited. The committee can also be changed. The block proposer and validation committee signatures are very important in our proposed network. Therefore, to avoid any destruction, we completed the block with all its signatures by the proposer in the same block creation cycle under the block validation committee. Due to this, no validator signature of the validation section would be lost or edited.
Scalability
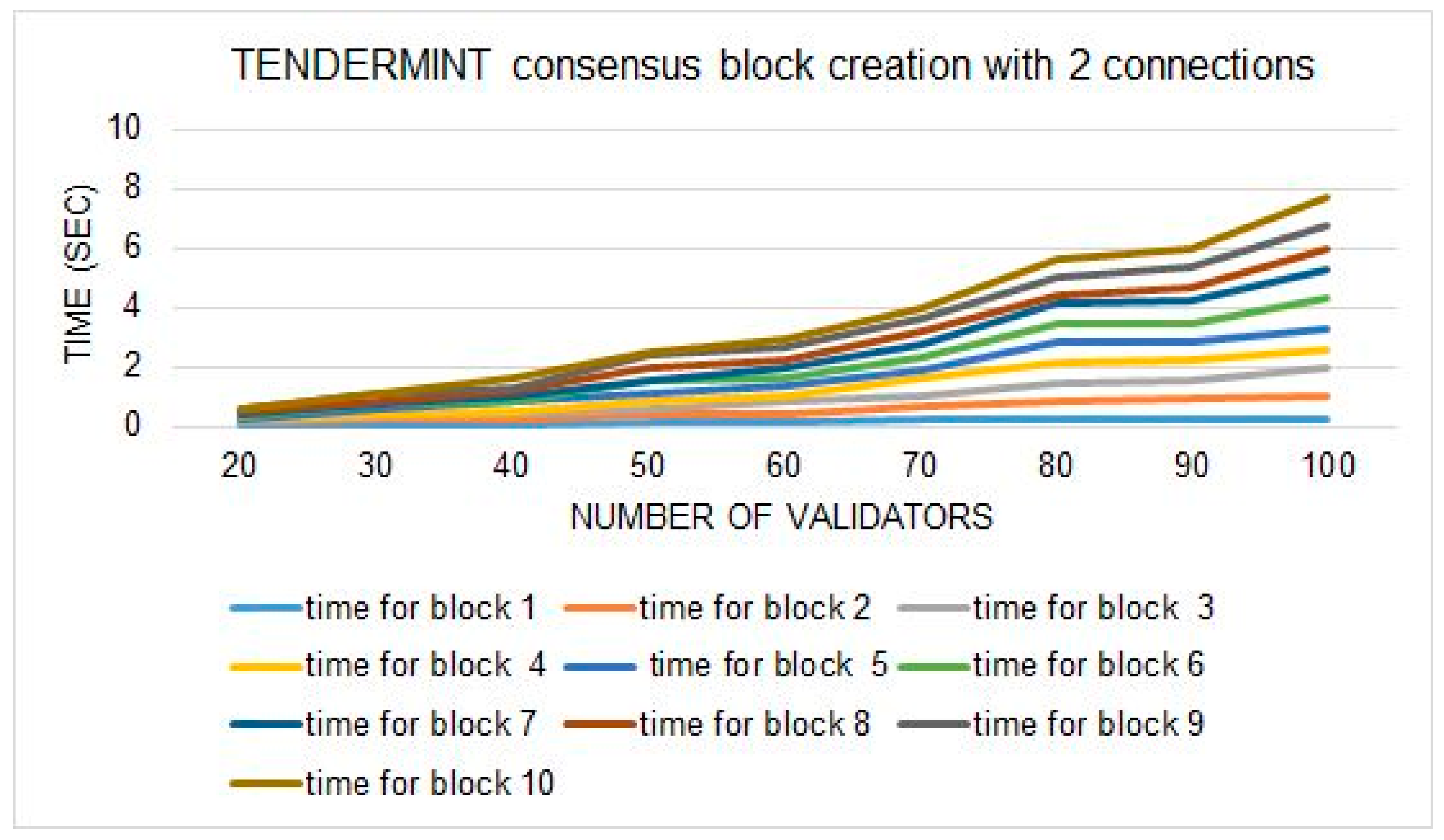
Tendermint is considered an efficient and fault-tolerant consensus among the consensus family of blockchains. We used Tendermint as our main comparison consensus in our work because we used the concept of multiple phases in Nazfast, such as Tendermint. Tendermint consensus provides liveness in the presence of malicious nodes. We simulate and observe the behavior of Tendermint consensus under different conditions in our work. We observe the consensus time by different network arrangements, as
Figure 10 shows the block creation time with two connections, and
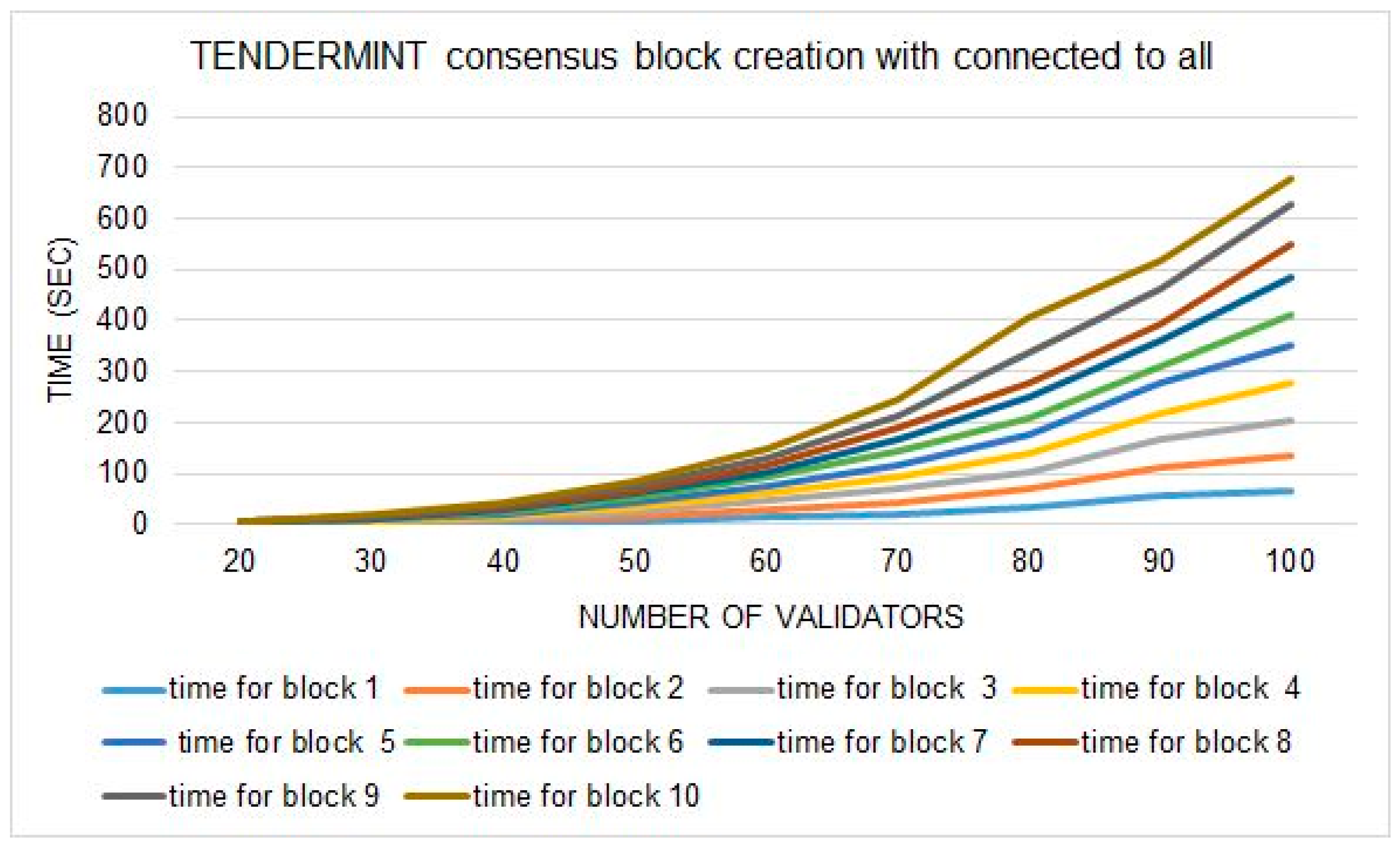
Figure 11 shows the block creation time with all others in the network having a propagation time of 0.2. The simulation process shows a significant difference in both results. We observe variation in the block creation time due to the change in the number of connections in the network.
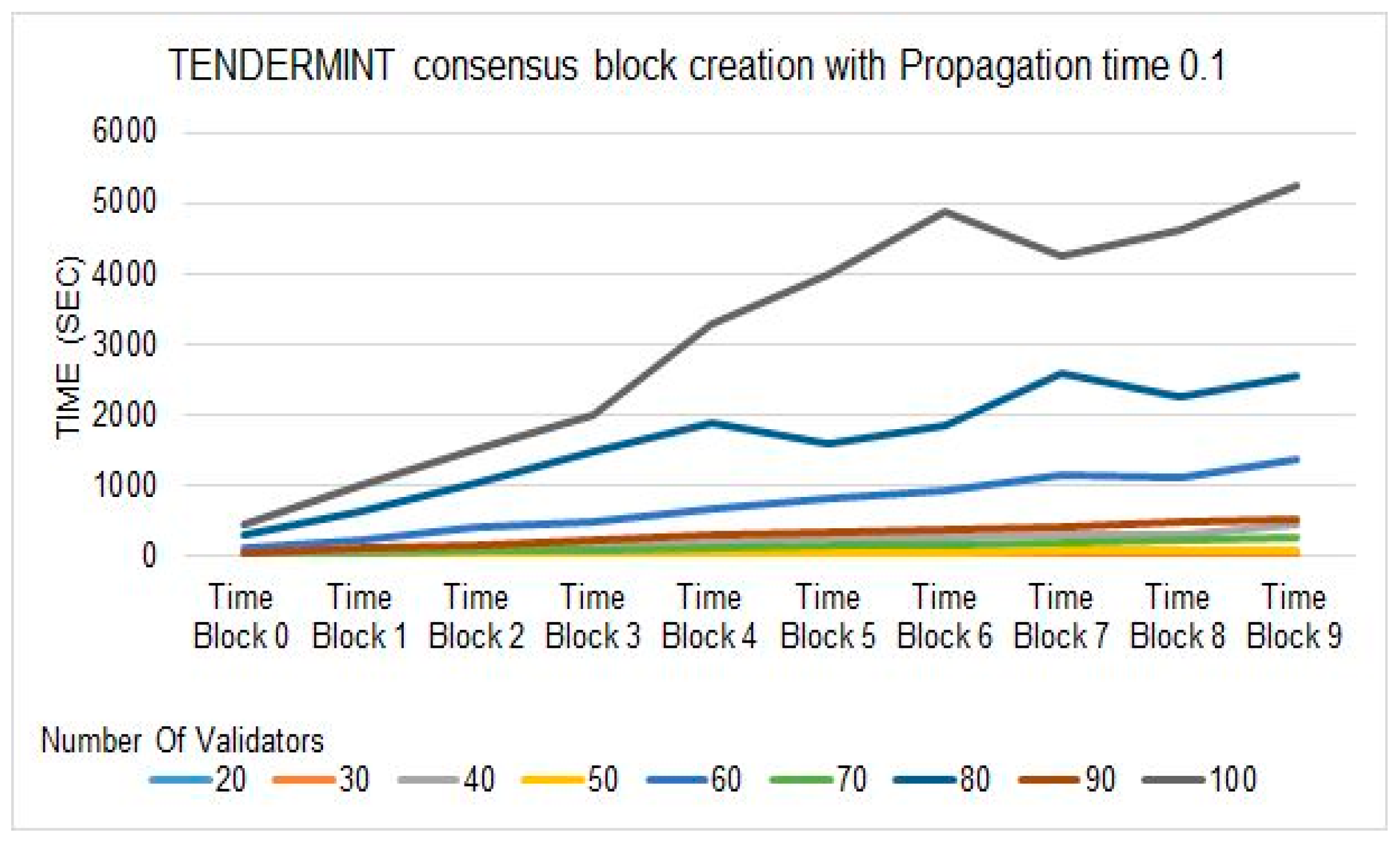
Figure 12 shows the block creation time change with respect to different numbers of connections in the network, having similar validator numbers and propagation time. It depends on the application network and which network arrangement will be used to deploy the blockchain. To achieve maximum execution time for better results of simulations, we used maximum connections in execution to complete the further simulation process. The block creation time is also affected by the propagation delay time of a network. We used 0.1 as a propagation time in the simulation with connections to all validators in
Figure 13. In
Figure 13, we may observe that it takes a little different time than
Figure 11 results. However, to achieve more realistic results, we used 0.2 propagation time throughout our simulations.
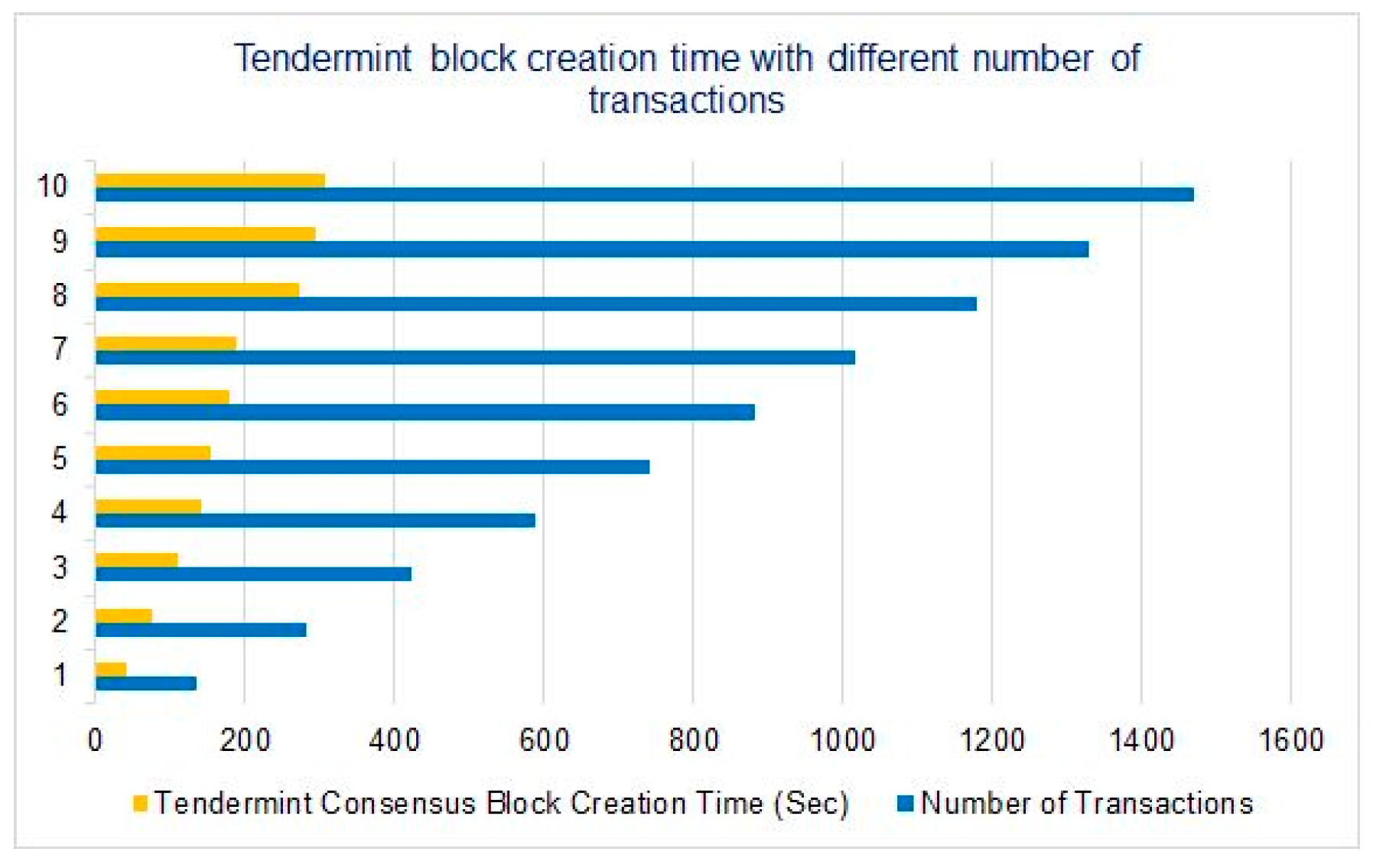
We also observed that Tendermint consensus block creation time is affected by the number of transactions in the blocks.
Figure 14 shows the block creation time with respect to the number of transactions in the block. The consensus takes more time according to the number of transactions, due to the transaction validation process in the consensus. We evaluate Tendermint consensus from the inside, and we find from
Figure 10,
Figure 11 and
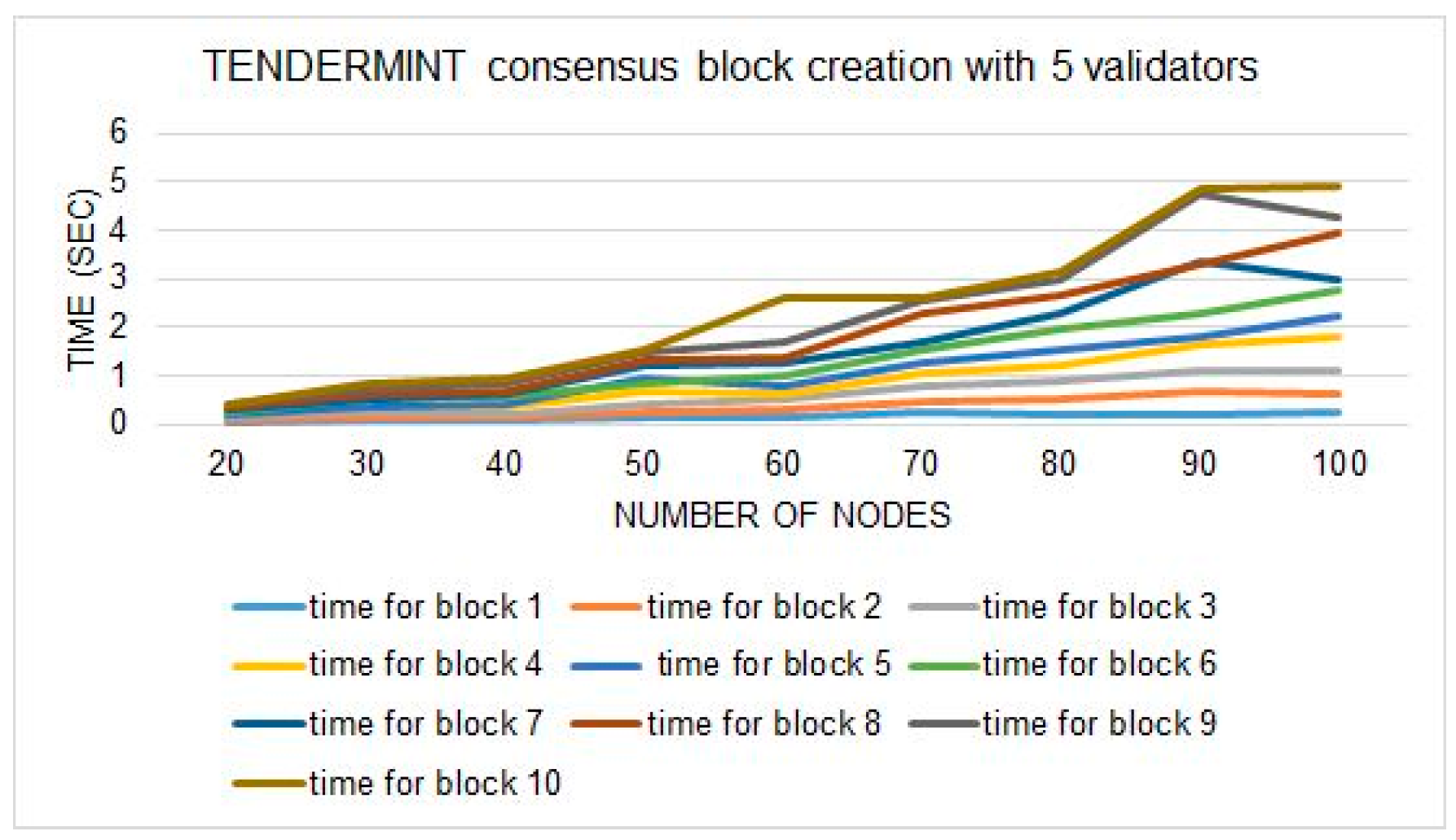
Figure 13 that Tendermint consensus block creation time majorly increases with the increase in validators in the system. It is happening because the consensus involves all the validators of the system in the block-creation process. Therefore, we run the Tendermint simulation with the minimum requirement to achieve the least block creation time of Tendermint, such as five validators, three transactions, two connections, and a 0.2 propagation delay.
Figure 15 shows the simulation results with minimum initialization; we observe an average of 1.2 s as the minimum time for block creation in the Tendermint consensus. However, as the number of validators increases, the block creation time increases, and the throughput decreases. It will eventually drop the blockchain network performance. In the Nazfast consensus, we try to overcome the time increment problem to improve the scalability of the consensus. Our presented consensus is different in many ways from the Tendermint consensus to improve the scalability issue. Below, we present the major differences that we made in our consensus in comparison with the Tendermint consensus.
Comparison with Tendermint on Scalability Aspects
The consensus used BFT layers for block finalization to improve security, such as the Tendermint consensus. The BFT layer has a high communication overhead rate. It reduces throughput and improves network latency. Tendermint uses network validators to sign the block for validation. It also increases block finalization time and reduces the throughput of the network. We also used the BFT layer for security; therefore, to improve the throughput of the complete consensus, we reduced and fixed the number of validators for the consensus to improve the scalability of the network. We used only fifteen V-validators, one wildcard entry validator, and five correctors in every block validation process instead of involving complete validators of the network. Hence, we have achieved block finalization in very little time.
If we increase the number of validators in the validation process, the throughput time will be increased. They are directly proportional to each other.
where k is the non-zero, positive constant of proportionality.
In such a case, where the values Nv
1 and Nv
2 of Nv correspond to the values Bt
1 and Bt
2 of Bt, respectively, then it turns into the following:
Therefore, the reduced and fixed number of validators in the Nazfast consensus leads to a higher throughput with less communication overhead in the proposed network.
- 2.
Only five correctors for a commitment
In Tendermint consensus, all the validators of the system are involved in the validation process. It creates strong broadcasting pressure in the network. The communication overhead is also very high. In our proposed work, to reduce the total time of a block creation cycle, we reduce the number of validators in the commit phase. During the block creation cycle, “check validity phase”, V-validators of the recent block creation cycle send their vote, which is pre-committed to correctors rather than to each other. Each V-validator sends their vote to five correctors instead of sending it to the remaining 14 V-validators and the wildcard entry validator. It reduces message broadcasting pressure and improves scalability. Also, it increases the consensus’s security because five new validators commit a block as correctors and check its correction for any forgery.
- 3.
Timesheet concept
We used the additional concept of corrector in the Nazfast consensus to improve the security that the Tendermint consensus does not use. However, we do not want to increase the throughput time of the network due to the work of correctors in the consensus mechanism. Therefore, we used the idea of maintaining a timesheet to speed up the commit process. Correctors speed up the commit process to gain the next election-starter reward. Due to the reward mechanism, the correctors’ work does not get delayed, and the throughput of the complete mechanism increases.
By applying all those techniques, we have succeeded in blocking finalization in a very small amount of time with almost similar latency in the network.
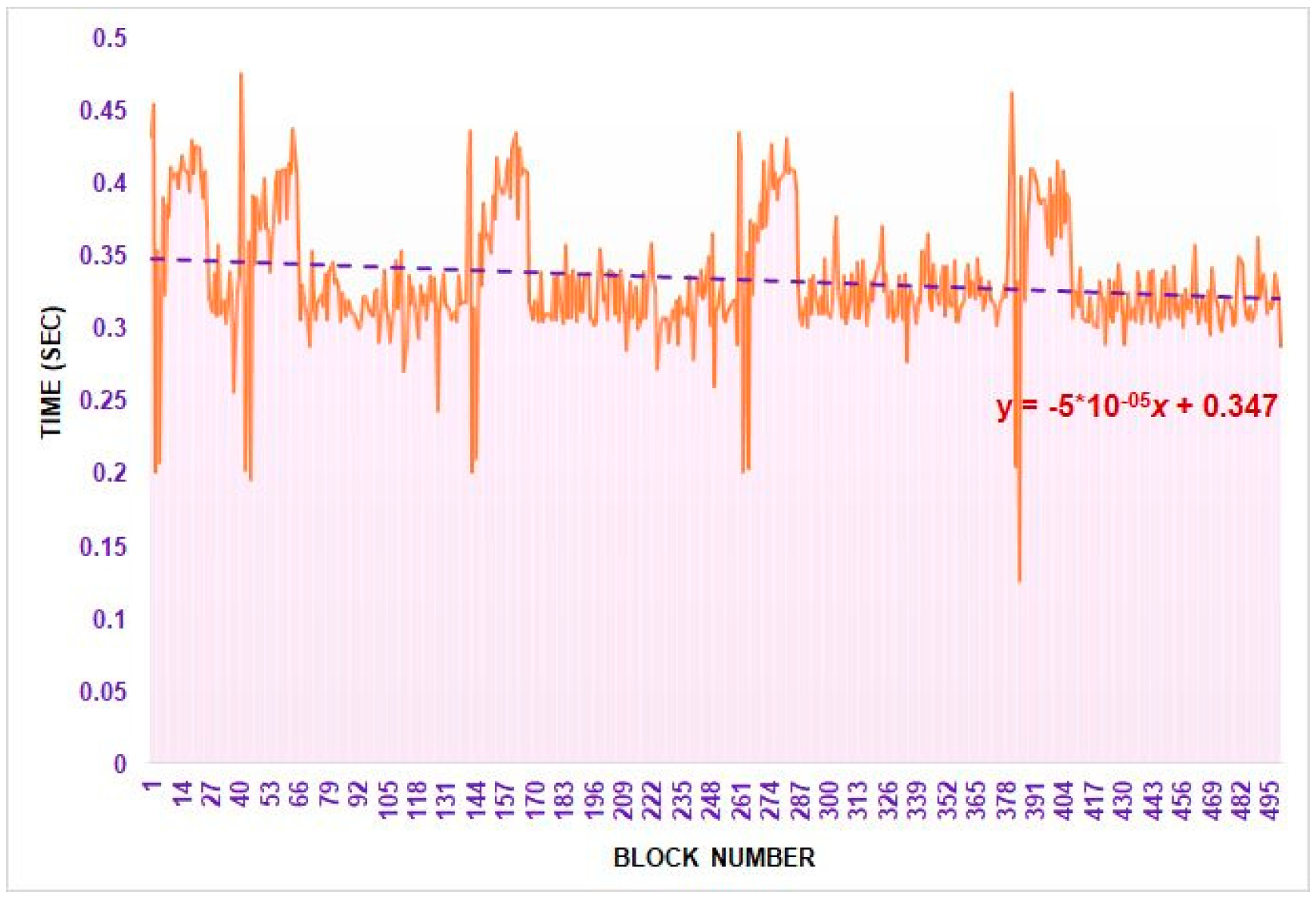
Figure 16 shows the block creation time by the Nazfast consensus. We have observed an average of three block finalizations in 1 s on a small number of validator sets.
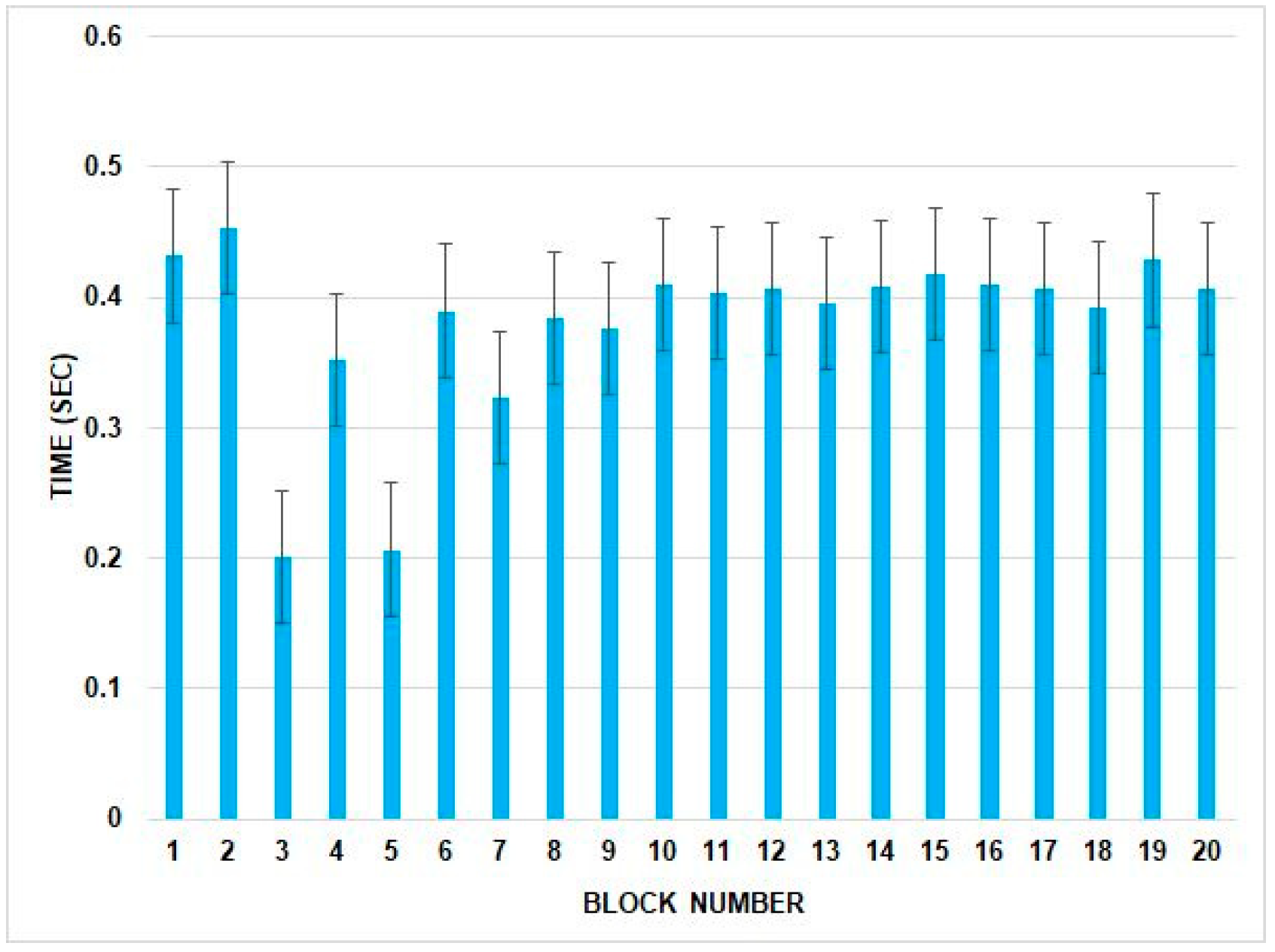
The block producers may create their block with transactions any time after the election process result declaration in the network and broadcast it in their respective block creation cycle. Therefore, the observed time for block creation starts with the block proposal and ends at the final commit state of the new height phase. We calculated the confidence level of our results by considering a 95% alpha value. Given the confidence interval rate, the results ensure that 95% of samples are in the range from 0.333745948 ± 0.177220195 for block creation with a similar number of validators.
Figure 17 shows the block creation time with the error bar of the Nazfast consensus.
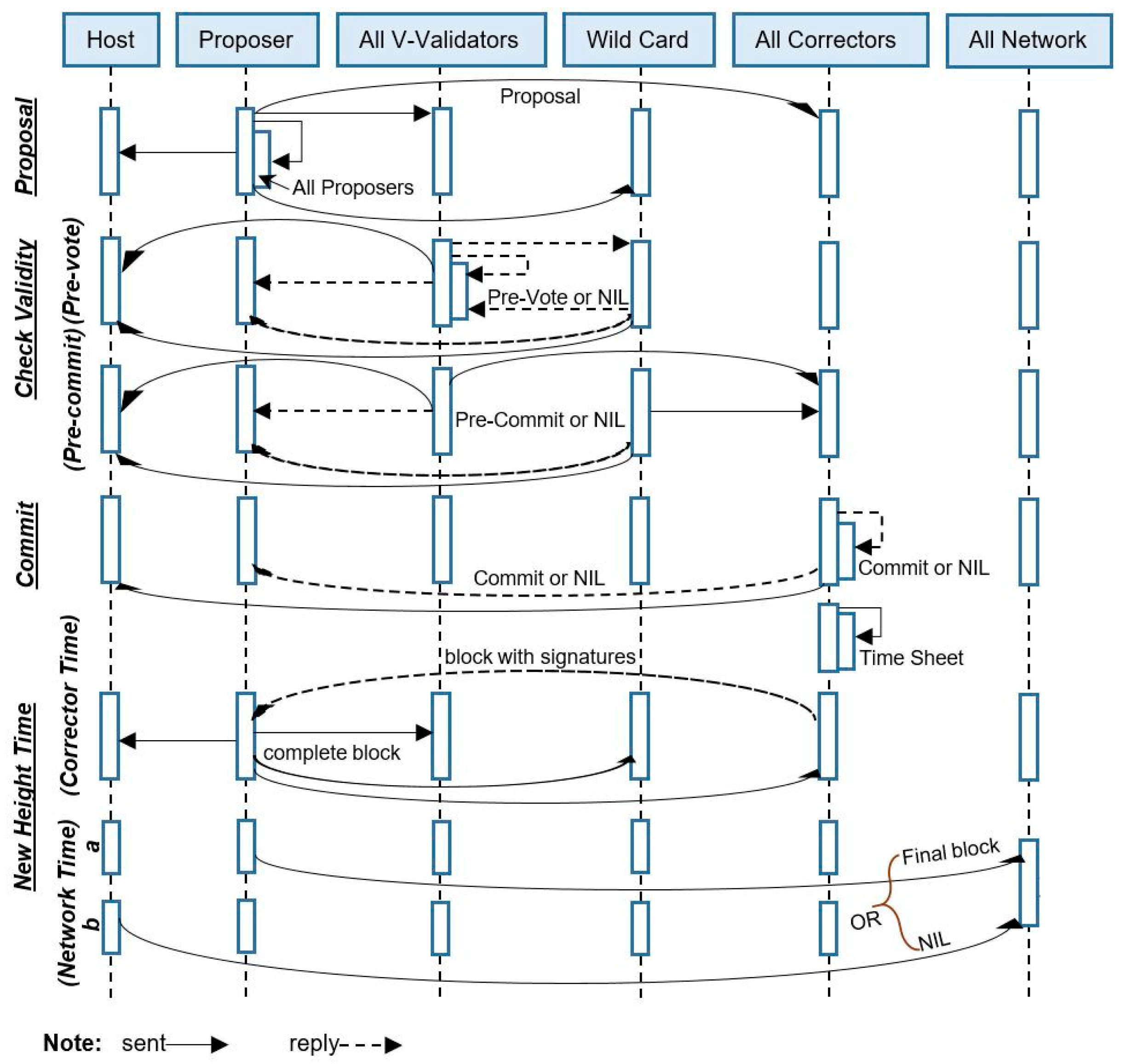
In our presented consensus, one block creation cycle consists of many phases.
Figure 18,
Figure 19,
Figure 20,
Figure 21 and
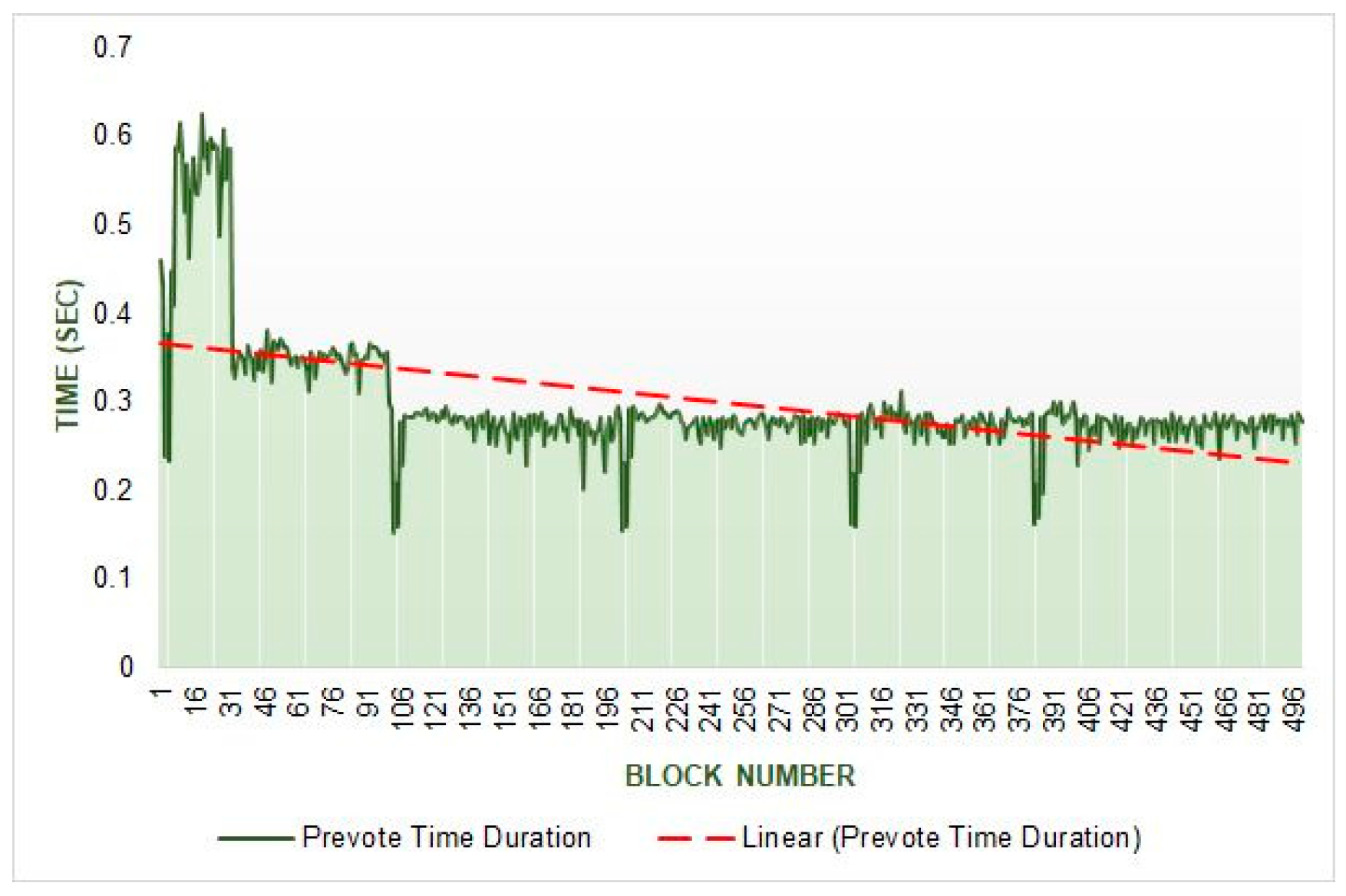
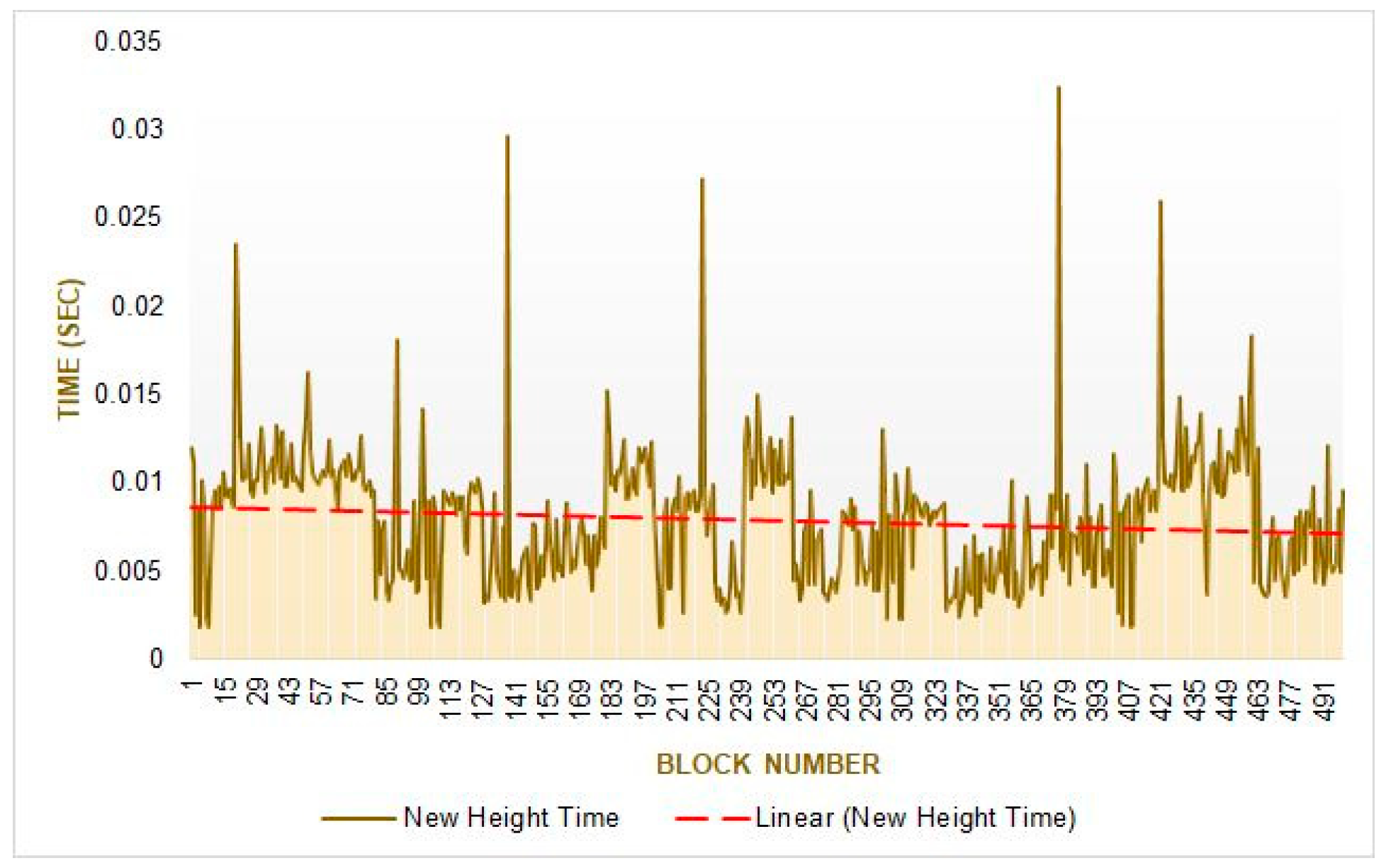
Figure 22 show the time of each phase during a block creation process. We used 500 test samples to calculate the average results with a 0.2 propagation delay while connected to all other network validators. We observe that the proposal phase takes an average of 0.027822161 s to complete. The check validity phase has two stages, prevote and precommit, prevote takes an average of 0.296942 s, and pre-commit takes an average of 0.01747 s. The commit phase takes an average of 0.004887 s, and the new height takes an average of 0.00781 s. The system bounds the maximum time for a phase; after that, it will automatically time out. The system may also fix the minimum time for each phase to dissolve. We have recorded and presented the average minimum time taken for each phase on the simulator. From
Figure 23, we have observed that the prevote phase takes the longest time among all. The prevote takes more time because the validators first validate the block in this phase and then confirm with their prevote in the system.
Election Process Scheduling and Scaling to Speed Up the Process:
The election process result is used in the Nazfast consensus mechanism to create and finalize blocks. 20 blocks in two rounds will be made on the result of one election; therefore, after every 20 block creation cycles of Nazfast, the new election result is required to start a new round. The first election should be held and end before the start of the genesis (very first) block creation cycle; otherwise every election for the next two rounds will begin with the start of the current block creation cycle 1 of round 1 and be executed in parallel with the block creation cycles of Nazfast. The election process should end before the end of block creation cycle number 20 of the current round of Nazfast so that the next round may use the result of the current election. If the election has not ended for any reason, the next block creation cycle may have to wait to get started. For any inconvenience, we recommend that three elections should be performed before the genesis block creation cycle of the main chain. In our proposed mechanism, we have observed three block finalizations in 1 s for the main chain in
Figure 16 and
Figure 17, and we need new election results after every 20 block creation cycles.
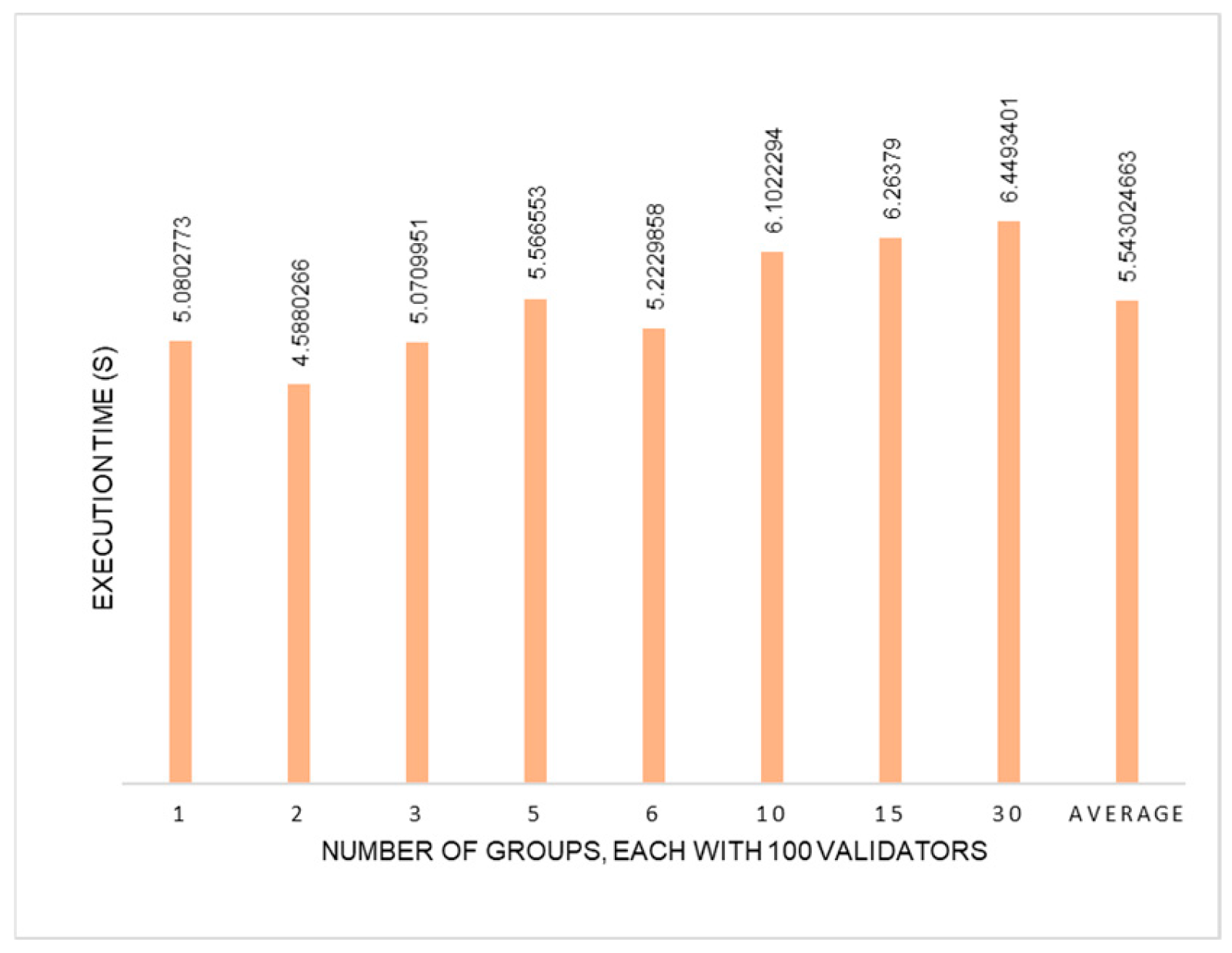
Therefore, we have approximately 6.66 to 7 s of time duration for new election results. We have observed that in
Figure 24, 100 validators take approximately (5.5 + 1) seconds on average with any number of groups, where + 1 s for system settings to complete the election according to the S&Sem. The time duration is satisfactory for this number of validators; however, we observed that in
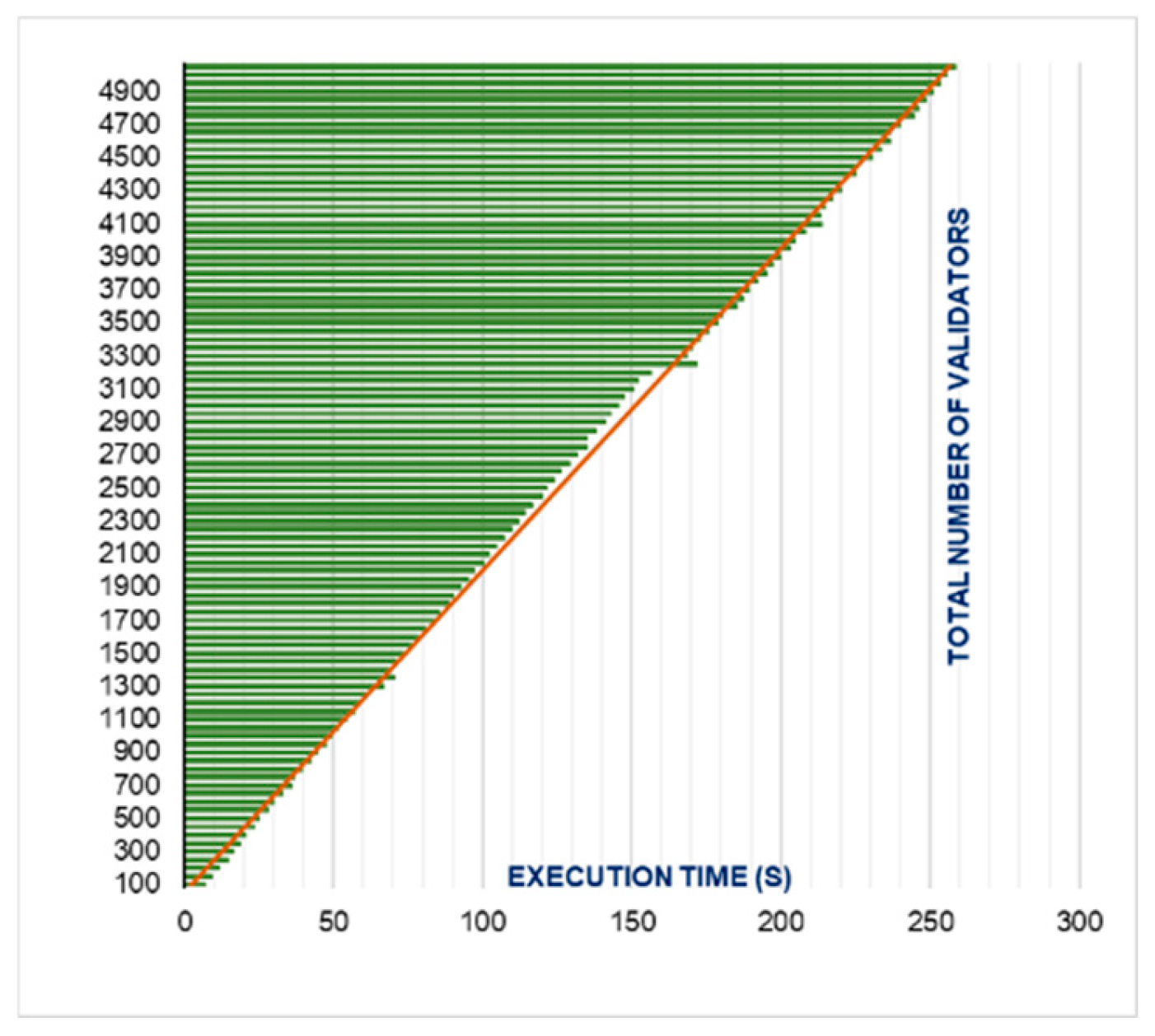
Figure 25, if the number of validators is increased in the network system, the election time is also increased for a similar number of groups. For the time increment, we recommend horizontal scaling, which S&Sem is already using. The election is held in groups in the S&Sem. S&Sem maximum suggests 30 groups for the election. Since all groups work in parallel, we suggest each group should not exceed more than 100 validators for our system. To control delay in the main chain block creation cycle, the election time cannot exceed 7 s in our system. However, if the system encounters an increased number of validators that cannot be fitted into 30 groups, the system should break the validators into more groups so that the election time will not exceed 7 s. If the system breaks validators into more groups, then the top 30 would be selected among all groups’ results for the block creation cycle. The S&Sem proposed many ways of scaling processes to improve the efficiency of the system, such as “Time Scaling with the number of Validators by using horizontal scaling”, “Parallel execution of steps”, and “Parallel Processing of Jobs in Steps”. We inherit all the scaling ways for the election process in our proposed system, which are discussed in the S&Sem paper to increase the presented system’s overall efficiency.
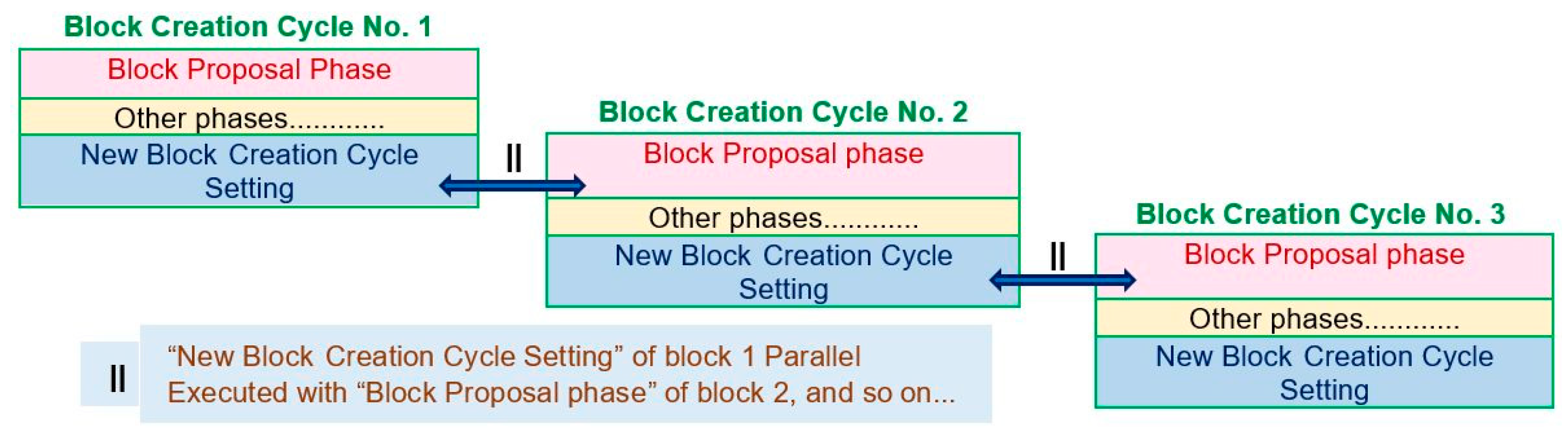
Scaling to Improve Throughput
There are multiple strategies that we used in our presented consensus to speed up the network output. If the network wants to reduce block creation time, we suggest some parallel processing in the block creation phases. We have four phases in the block creation process. In the last new height phase, we have new block creation cycle settings. In this step, only the host is occupied in the new settings, while all others (the validation committee) are free. We suggest that the next block creation cycle may start in parallel with the new block creation cycle setting step, such as in
Figure 26. The next block proposal phase gets started, and the block producer broadcasts the block to the block validation committee while the host is busy with the settings. We have already observed that there is a time bound for the block proposal phase in the block creation cycle. By performing this parallel work, the system may save time and improve the throughput of the network.
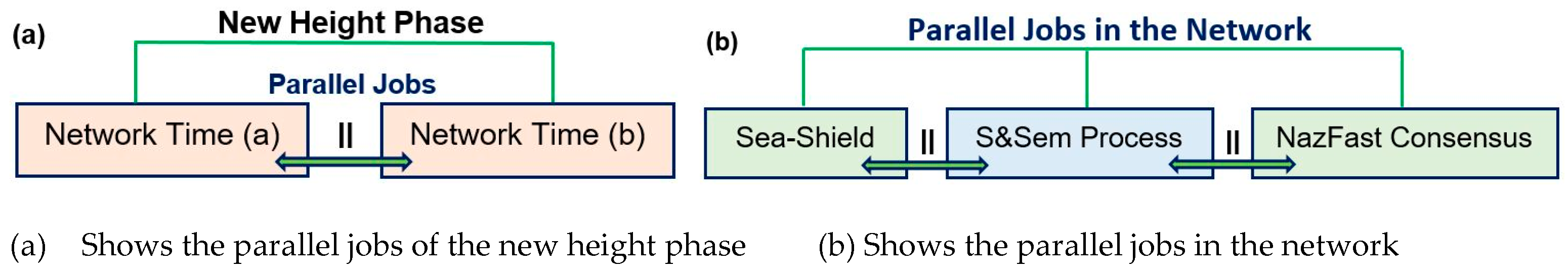
We used parallelism at many places in our presented work to increase our throughput, such as in the new height phase network time (
Figure 27a). We have three major processes in our system, and all three processes also work in parallel (
Figure 27b). We also used parallelism in the S&Sem process to speed up the election mechanism. We try to reduce time to increase network efficiency in terms of throughput.
Communication Message Overhead
The presented consensus is based on the Byzantine fault tolerance technique. This technique involves high-message communication in the system, also called Byzantine atomic broadcast. We used this technique in our distributed system to maintain liveness and fault control. However, the high communication broadcast leads to the low throughput of the system. Therefore, we scale the process to control the high communication overhead by creating a small number of committees in the system for the block creation process. Each broadcast affects the system’s cost, time, and network efficiency. We calculate the total broadcast of the Nazfast consensus to show the network’s efficiency.
Figure 28 shows the overall communication overhead of the Nazfast consensus.
Calculating Efficiency
Big ‘O’ and big omega ‘Ω’ notations are used to find the efficiency of the algorithms [
95]. There are three measures to find the efficiency. Big O for worst, big theta for average, and big omega for best in terms of time. We find the best and worst cases by calculating the communication message overhead of the system. For the best case, ‘Ω’, we calculate the lower bound of the system by reducing any possible extra communication messages during consensus. For the worst case, ‘O’, we calculate the upper bound of the system by counting the maximum communication overhead messages during the consensus.
Worst Case (O): The maximum communication message overhead that is needed to create a block in a consensus process is below.
We can observe from
Figure 28 and present the details of every phase of message communication of each entity. Refer to
Table 6 for the variable details that are used in the below equations.
The worst case takes (a + b + c + d + e + f) in total of (492 + N) messages as the maximum communication message overhead of the system during all phases of the Nazfast consensus.
We used the BFT concept in our consensus mechanism. The BFT concept allows 2/3 of total V-validators to create a block as well; we reduce the number of messages and calculate the minimum message overhead to create a block in the network system.
Best Case (Ω): The minimum requirement needed to create a block in a block creation cycle is below.
We only send a message to the initial six proposers because proposers need to receive the block within the time; otherwise, the swapping mechanism is activated for the new proposer assignment. We also send messages to 2/3 V-validators and the wildcard entry validator because they are required to give prevotes.
We only send and receive messages to 2/3 V-validators and wildcards for the prevote phase.
2/3 V-validator and corrector send and receive with wildcard validator
Only correctors receive and send messages themselves.
We can only reduce V-validator in corrector time because all others are necessary according to consensus.
The best case takes (a + b + c + d + e + f) in total of 298 + N messages as the minimum message overhead of the system. We reduced 194 messages to improve system’s performance.
We only considered the message that is involved in the block creation process. We compromised security for the best-case message calculations. The application network of Nazfast can omit these messages; however, it will weaken the block creation process’s safety and the overall security of the network as well. Therefore, we simulated with 492 + N messages to obtain our throughput results.
Reducing NIL message broadcast
We also suggested that if the block has not been created in the corrector time, the network may reduce the NIL message broadcast from the network time of the New-height phase. It saves the message broadcasting pressure, but it will create problems and increase the chance of forking in the system because network nodes would not know that the block is not created in this block creation cycle, or they did not receive the block. Therefore, we sent NIL for every block creation cycle that does not create the block. We also suggested that the application network may omit the NIL broadcast from the revote and the pre-commit phase. Tendermint consensus also uses NIL messages against unworthy/invalid blocks in the prevote, pre-commit phases. However, it increases the message communication broadcast. To reduce the message broadcast pressure. If the block response has not been sent by V-Validator or V-Validator finds the block unworthy and it does not send NIL, the network will automatically consider it as NIL. Reducing the nil message broadcast eventually improves the system’s throughput, and it leads to improved efficiency.
Decentralization
Decentralization in a blockchain network means the network cannot be controlled by any single entity. We used a consensus mechanism to reach an agreement on such networks. We present the Nazfast consensus for PoS-based networks. A PoS-based blockchain network focuses on strong decentralization because it does not require heavy machinery to operate like PoW [
1] consensus. In the previously presented consensus for PoS consensus in the literature [
18,
96,
97], almost all the validators or validators’ set of the network took part in the consensus process to improve network decentralization. We also try to enhance the decentralization aspect of our blockchain network by using many ways that are discussed below, with a comparison of Tendermint consensus.
Comparison with Tendermint on Decentralization Aspects
Tendermint consensus uses a large size of validation set to increase the decentralization aspect of the network. However, due to a large validator set, the throughput decreased, and it also lowered the network efficiency. To improve the scalability of the consensus, we reduced and fixed the number of validators in the consensus. It increased the network’s throughput of Nazfast. However, it decreased the network decentralization. The presented consensus used a very small committee size that strongly affects the decentralization aspect of the network. The system controlled this issue by using an election mechanism in the network to select the block production committee. The S&Sem involves all the nodes in the election to improve decentralization. The S&Sem used many techniques to improve the decentralization in the network, such as providing a chance for less coinage validators in the network to participate in the competition by restricting the last election result finalists from competing again in the next election. Competition must be between three times the number of validators selected from the group, so that each finalist goes through a competition in the network. There are many attractions used by validators that participated in the election competition to obtain votes from other nodes. These attractions also maintain liveness, and due to the involvement of others in the voting, it improves the decentralization aspect of the network as well.
- 2.
Fork control to improve network stability and decentralization
Tendermint consensus may have forks due to many reasons in the network, such as a temporary fork, a fork due to the partition of resources, or a fork due to the forging of validators. Tendermint consensus may suffer from these forks, but the consensus recovers its state quickly by resolving issues. In our presented consensus, Forking does not happen because blocks have a timestamp sequence number, and each block creation cycle has only one block at one height. No two blocks are created or broadcast at a similar time in the network for the same height. Due to this, if the network received a block with increased height, such as block 13 after block 11, it may ask the network about the missing block 12. Therefore, if the block has not been received, the node may request its peer node or network host to send it a missing block. We also broadcast NIL for the block creation cycle that does not create the block. Nil broadcasting clarifies the network if the block has been created or not in this block creation cycle.
Comparison with Tendermint on Liveness Aspects
Fault Tolerance:
The presented network system is based on Byzantine fault tolerance. The Byzantine fault tolerance means our network still achieves consensus in the presence of malicious nodes in the system. We use the concept of 2/3 percent at many places so that our system does not collapse due to small malicious activity by someone in the network. We also used different techniques to maintain the liveness of the network, which are discussed below.
Tendermint uses a round robin mechanism for block producer selection. If the block producer does not produce a block, the system suffers because block creation is the fundamental part of a blockchain network. To maintain the liveness of the Nazfast consensus, we add a swapping mechanism. Every block creation cycle has its pre-specified block proposer. If the block is not produced by the block producer for any reason, the swapping mechanism is used to select a new block producer to produce the block for this cycle. Due to this mechanism, every block creation cycle has a block, and the blockchain network system remains alive.
- 2.
The block gets dissolved to achieve liveness
In Tendermint consensus, if the block does not get confirmed, the transactions get stuck in the block for a long time before confirmation. In our consensus, we used another way to overcome this issue. We had the block dissolved by its block producer. When a block does not commit in a block creation cycle, the block gets dissolved in the new height phase by its own block creator. Due to this mechanism, no orphan blocks remain in the blockchain network, and unconfirmed transactions do not get stuck for a long time waiting to obtain their confirmation in the network.
- 3.
No locking mechanism to improve liveness
Tendermint uses a locking mechanism in multiple ways, mainly at voting rounds. The validator used a locking mechanism to show its support for a specific proposal and does not give a vote to any other proposal. We remove this concept from our consensus because in our presented consensus, every block creation cycle has only one block; hence, no locking mechanism is required in any phase. We do not keep blocks in a pending state for confirmation in our consensus.
- 4.
Valid validator concept
We used the concept in S&SEm [
12] of a valid validator to become a participant in the election competition. Therefore, every validator needs to become a valid validator in the network. To become a valid validator, it has to give a vote in the elections. Due to this condition, all the validators of the network have to be active in the network. For this reason, the whole network’s liveness is improved.
Incentive mechanism of our consensus
Validator nodes play a vital role in the PoS-based blockchain network. It creates blocks for the network by using a consensus mechanism. Their presence ensures the liveness of the blockchain. Almost all blockchain networks use incentives for nodes to become validator nodes in the network. Incentivization is the main component of any blockchain architecture to attract validators. Our presented blockchain network also has an incentive mechanism to stabilize the network. We have different types of incentives in our system for validators, such as excellency points and rewards. Also, to control the forgery and malicious behavior of nodes in the network, we also used penalty/coin slashing in the network. We have discussed each below.
Rewards and penalties for each entity
If the block gets accepted by the corrector and added to the blockchain ledger as a new block, all V-validators and wildcard entry validators that send pre-commit to this block will receive their rewards and excellency points at the end of the block creation process. The V-validators that did not participate in the pre-commit phase, although they were in the selected 15 V-validators for this block creation cycle, would not receive rewards and excellency points.
- 2.
Corrector Rewards and Penalties
The corrector that first found any guilt or forgery in the block creation process receives a bonus forgery reward, plus a corrector reward, and also a bonus excellency point with a corrector point. The other corrector that found the forgery after the first corrector would receive a routine block corrector reward and an excellency point. The network would punish by imposing a penalty on those correctors that did not find forgery in the block while the block is claimed as forged by any other corrector and all those v-validators that gave a pre-commit to this forged block and the proposer of the block. With a penalty, they would also decline in their excellency scale due to a penalty point deduction from their excellency scale.
- 3.
Block Reward Distribution
In Sea Shield, a validator may share its reward for creating a block in the main chain. We also encourage this rule in our network system. Those nodes that took an interest in creating blocks of Sea Shield will be eligible to receive a part of the reward from the validator that creates a block in the main chain. We used Sea Shield to become a node in a validator in our network. Sea shield consensus needs nodes’ active participation to maintain the liveness of the network. Therefore, the Nazfast consensus block producer may share its block reward with the node that supports it in becoming a validator in the Sea Shield consensus.
Comparison with Other Networks
Our presented consensus is based on proof of stake—Byzantine fault tolerance (PoS-BFT). Our presented consensus used a reduced number of validators by using an election mechanism to accelerate the consensus process. Below, we compare our work with the consensus that lies under the same family of Tendermint and with other major consensus available in the network.
Comparison with the Same Family of Consensuses
The EOS.IO uses a voting mechanism to select block producers and PBFT for block finalization. EOS.IO was presented by Ian Grigg in 2017 [
98]. The EOS.IO software (v.1.0.0.) (block.one) used the DPoS [
99] algorithm for the block creation process. They used a voting mechanism to select 21 block producers for one round to create blocks. Block producers encourage token holders to vote for them, such as offering rewards or attractions to give them a vote, or using many other ways. The selected block producers produced blocks in a round-robin fashion. The EOS used PBFT (Practical Byzantine Fault Tolerance)-style consensus for block finalization. Every block goes through the commit and pre-commit phases to decide the validity of the block. The block also required 15 other block producers to sign the block for finalization. The EOS.IO produces blocks every 0.5 s. If the block has not been produced, a 0.5 s gap in the blockchain network is observed. Our presented consensus used the swapping mechanism to reduce the time gap and select new block producers. We have already discussed the comparison of Tendermint with Nazfast consensus in the discussion section. Quorum IBFT [
16] means IBFT consensus used for the Quorum blockchain. IBFT has a higher throughput than PBFT. However, it has many issues, such as centralization due to validators, because of the dynamic set of validators in the system, and network management becomes challenging. We also used the block creation committee that changes after two rounds; therefore, we saved the election result in the main chain and used Sea Shield for complete details. Avalanche [
9] consensus used the gossip protocol with a repeated random sampling method. Each node uses a subset of validators from the network to confirm the state of the transaction. Due to this, it leads to centralization issues in the network. However, it has a good throughput. In our system, we provide improved decentralization in our consensus. Hyperledger Fabric [
100] used the PBFT approach. It used a leader and multiple phases to commit a block. Due to the BFT approach, it has a high communication overhead and low scalability. We solve these issues in our consensus by providing high throughput with less communication overhead. Stellar (FBFT) [
17] is a blockchain network that uses FBFT consensus. The FBFT consensus is also based on the BFT concept. The consensus faces issues like governance and centralization risks. In our presented consensus, we try to overcome these issues.
Overall Comparison with Other Consensuses
Casper consensus has two versions. Casper friendly finality gadget [
101] and Casper the correct by construction [
102]. In the initial case, the Casper FFG used PoS with Pow style for block finalization, but later in CBC, it became completely PoS. Casper FFG has slower block production compared with other networks. However, Casper CBC has improved the block production rate. However, our presented consensus has a higher throughput than Casper’s. Polkadot [
8] used a parachain model. It has a relay chain (main chain). Consensus has been achieved in the main chain. It also has many parachains. Parachains are individual blockchains that run parallel to the main chain. It is considered an improved consensus. However, it has issues such as centralization and governance complexity. We solve all these in our consensus with improved throughput. Algorand [
96] used a cryptographic sortation mechanism to select the leaders for block creation. It provides instant finality to the transactions. Due to the sortation mechanism, fewer coinage validators have a lower chance of participating in the consensus. However, we provide fewer coinage validators to participate in the mechanism. A raft [
103] consensus mechanism is also used as a leader to coordinate the consensus process. They select a leader through a process, and the leader commits the log/block after receiving acknowledgments from others. Raft uses leaders for processing clients’ requests. If the leader failed to process, a new leader would be selected, and it would create a delay in the system. We used a swapping mechanism to ensure the liveness of the system. The raft also has a scalability issue; throughput degrades eventually with the increase in the network size. Laksa [
104] consensus is based on PoS consensus. The consensus is designed for large-scale blockchain systems. They optimize the protocol by creating committees. They select committees so that the system has improved decentralization and scalability. Since multiple committees work simultaneously, coordinating and justifying their actions without any system will lead to mismanagement in the network. To some extent, we also used parallel processing in the system. However, we used the host and election starter concept in the system to reduce any mismanagement in the system. We have Aptos [
105], Shardeum [
106], and SuiLutris [
107] blockchain networks in the literature that provide high throughput. Such as the Aptos blockchain network, which utilizes the Tetra BFT consensus mechanism to achieve block consensus. For fast finality, it uses parallel transaction processing. It uses a PoS style for validator selection in the consensus. It has sub-second finality because it has the Tetra BFT consensus mechanism. Shardeum consensus is designed for a fast, secure, and scalable blockchain network. The Shardeum blockchain network uses two consensus mechanisms for block finality. Shedeum utilizes a sharding mechanism to permit linear scalability and fast transaction processing. Sui Lutris is a smart contract platform. It integrates consensusless agreement with a high-throughput consensus protocol to achieve high efficiency. It is a hybrid architecture emerging blockchain. Sui Lutris is the upgraded version of Sui [
108]. Sui Latris used parallel execution of transactions in the blockchain network to gain high throughput. However, these are highly scalable blockchain networks, but still less than our system throughput. Solana [
109] used PoH [
110] and PoS in the block creation. Using them together, it provides a very high throughput, but it requires high hardware specifications to handle the large number of transactions and maintain the validator’s performance. However, we do not use heavy machinery in our consensus. Our consensus is efficient without wasting energy on heavy computations. We have presented a system that efficiently resolves the issues of these consensuses, such as providing strong decentralization, high throughput, and a secure system that does not require heavy machinery to process as well.
We are trying to improve all aspects of blockchain. We already discussed the security evaluation in comparison to others in
Section 6 and decentralization in
Section 7. We present a scalability comparison in
Table 7 with other blockchains’ consensus under the same family, such as EoS.IO, Tendermint, PBFT (Hyperledger Fabric, San Francisco, CA, USA), Stellar FBFT, Quorum IBFT, and Avalanche. We also compared with other major consensuses that are different in terms of architecture available in the literature, such as Proof of Work (Bitcoin, Frigate Bay, Saint Kitts and Nevis), Proof of Stake (Ethereum, Zug, Switzerland), Delegated Proof of Stake (Bitshare, Blacksburg, VA, USA), Raft, Algorand, Polkadot (NPoS), Solana (PoH + PoS), Casper (CBC), Casper FFG (Ethereum 2.0), LAKSA, Aptos (Tetra BFT + PoS), Shardeum, and Sui Lutris. As per the literature study [
111], performance is still a critical issue of blockchain. We have observed from a complete
Table 7 that our presented blockchain network consensus system has high throughput; it takes less time than any other consensus of the same family and with others as well.
Deployment in the real-world network
The deployment of blockchain is based on the type of network it is using. There are many blockchain networks available in the real world, such as Bitcoin [
1], Ethereum [
4], and Ethermint [
117]. All were deployed according to their need. The general deployment of any blockchain network requires many stages. It has a backend deployment, a frontend deployment, and blockchain network configurations. For a completely operational blockchain, it has a ledger, peer network, membership services, wallets, events, system management, and system integrations. There are multiple actors, such as the operator, developer, end user, and data storage, in the blockchain network that operate complete components of the network. It depends on the application network and how it uses the Nazfast consensus in its network. Either users or front-end software are used to operate the network for the Nazfast consensus. The Nazfast consensus can be deployed under the PoS blockchain umbrella architecture. It does not need any special hardware, nor does it have any special requirements for deployment. It can be implemented in our traditional peer-to-peer environment settings.