Formal Analysis of DTLS-SRTP Combined Protocol Based on Logic of Events
Abstract
1. Introduction
- Extension of sequential composition axioms, ordering axioms, and relevant invariants based on the foundation of Logic of Events Theory. Introduction of the concept of invariants and proposal of a proof method for verifying the security of composite protocols.
- Abstraction of the security properties of the DTLS-SRTP protocol using Logic of Events. Formal depiction of the interaction processes of its sub-protocols, DTLS and SRTP, and separate proofs for mutual authentication and confidentiality.
- Proof of the security of the DTLS-SRTP protocol after sequential composition using the proposed composite protocol proof method.
2. Related Work
3. Logic of Events
3.1. Symbol Description
3.2. Basic Definition
3.2.1. Sequence of Events
3.2.2. Event Classes
3.3. Axiom System
3.3.1. Key Axiom
3.3.2. Causal Axiom
3.3.3. Honest Axiom
3.4. Expansion of Logic of Events Theory
3.4.1. Invariant Concept
3.4.2. Sequential Combination Rules
3.4.3. Sorting Rules
3.5. Protocol Authentication Proof Process
- (1)
- Begin by formally describing the protocol, constructing standardized basic sequences for initiators and responders, and defining the strong authentication properties that the protocol needs to verify.
- (2)
- Under the assumption of honest entities, analyze the thread messages and define actions on the selected thread as an instance of the basic sequence. Specify the matching sessions that need to be proven and proceed to demonstrate unilateral authentication for initiators or responders.
- (3)
- Confirm whether the matching events comply with the current matching session. If they do, proceed with subsequent proofs. If not, continue filtering matching sessions until the current matching event satisfies weak matching.
- (4)
- With the weak matching confirmed, analyze the matching length during the protocol interaction process. Prove strong matching sessions based on relevant axioms and rules in Logic of Events.
- (5)
- If the strong authentication property for one party is successfully proven, proceed to prove the strong authentication property for the other party. If only one party satisfies the strong authentication property, it indicates that the protocol as a whole still does not meet the strong authentication requirement. Successful proof in both directions is necessary for the overall strong authentication property of the protocol to be established.
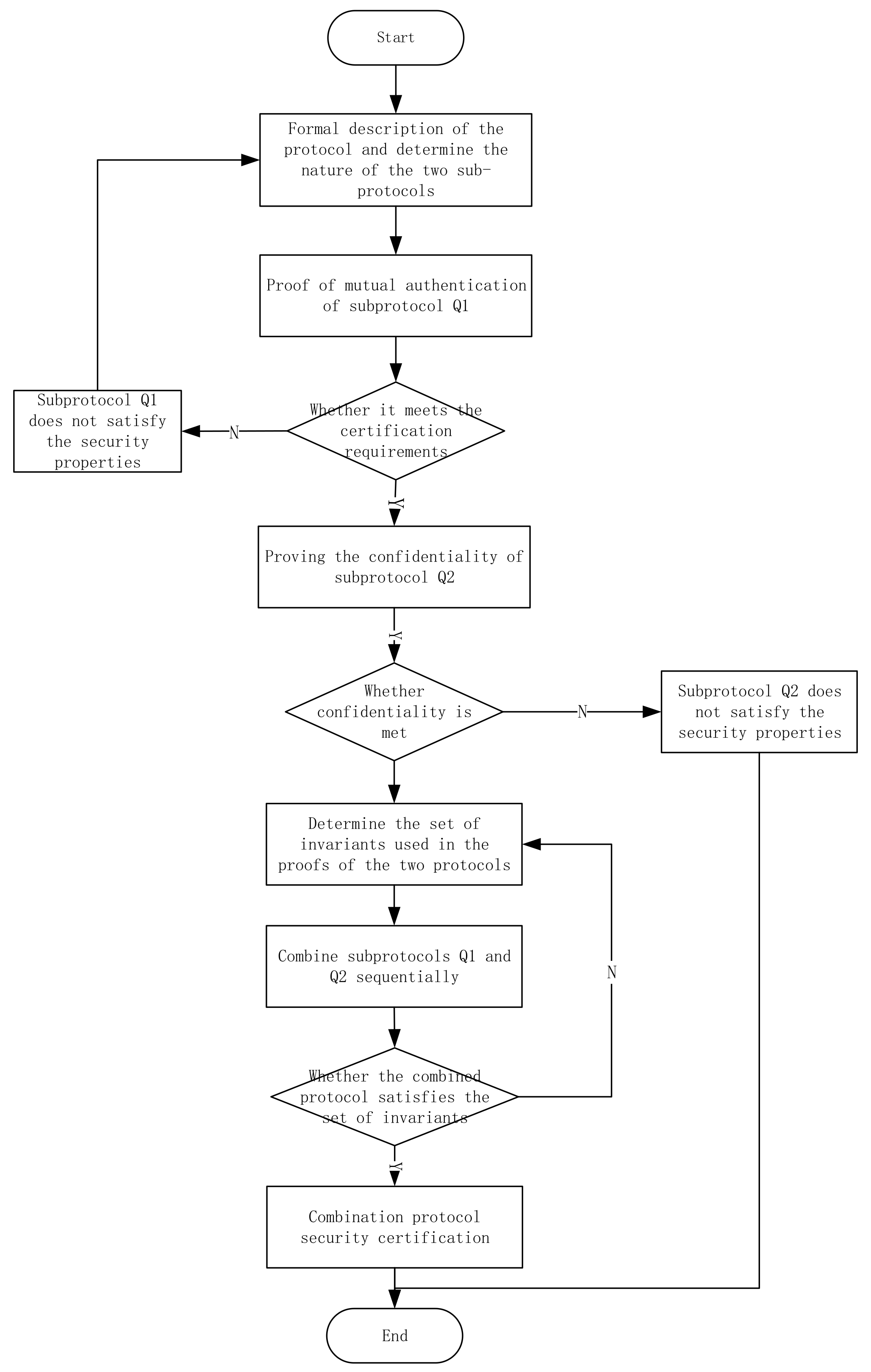
4. Combination Protocol Proof Method
- (1)
- Construct and prove the security properties of each protocol and separately.
- (2)
- Identify the invariant sets and used in the proof of security properties for the two sub-protocols. The formulas contained in these sets are typically proven using honest rules in both protocols.
- (3)
- Independently verify that the security properties of the two sub-protocols are preserved in the invariant set . If the postcondition of protocol matches the precondition of protocol , apply the ordering rule to sequentially compose them.
- (4)
- Prove that the invariant set holds for the security properties of the composite protocol Q. The specific process of proving the protocol combination based on Logic of Events is shown in Figure 2.
5. Formal Analysis of DTLS-SRTP Combined Protocol
5.1. DTLS-SRTP Protocol Analysis
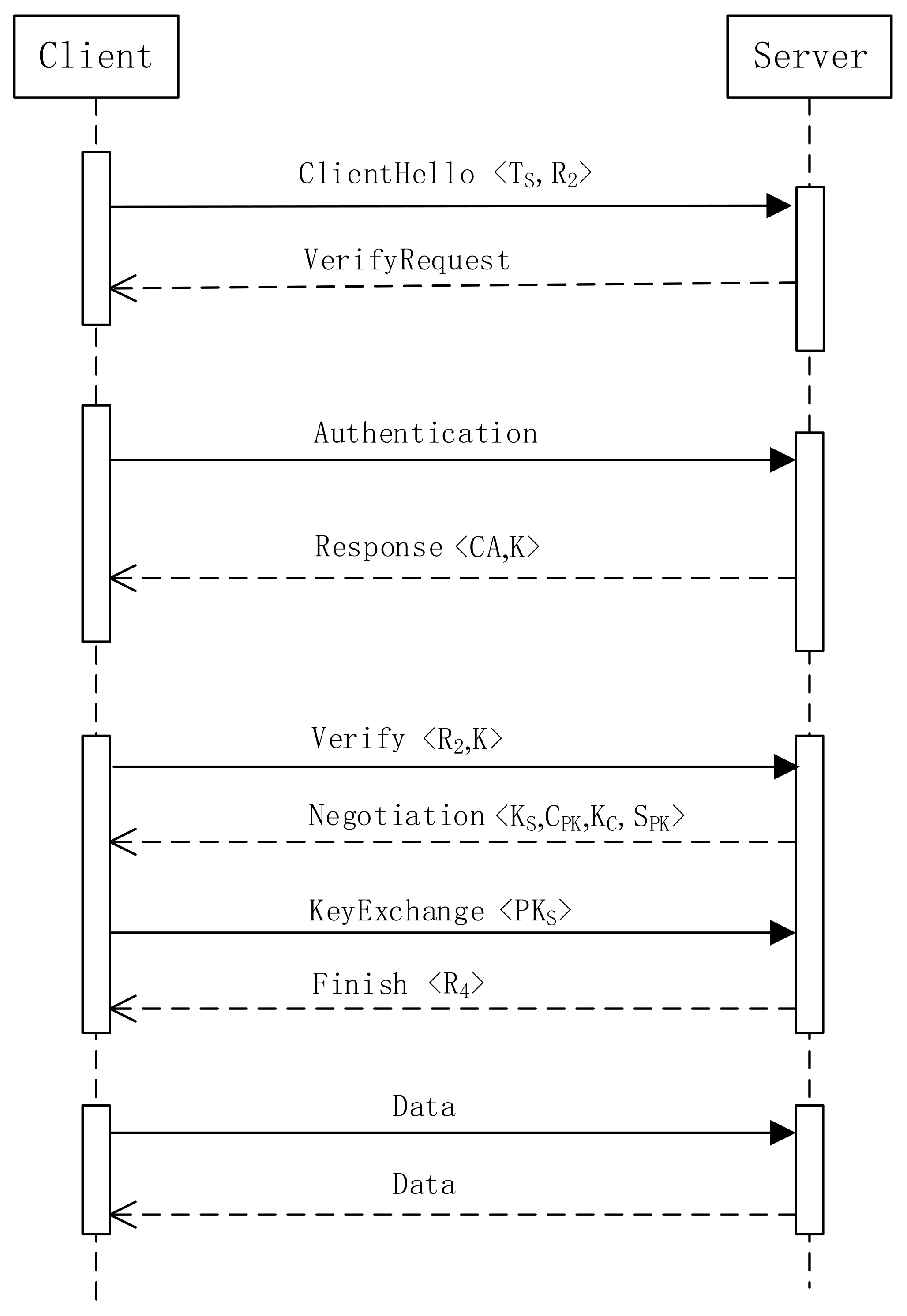
- (1)
- The client and server establish a connection by initiating a handshake negotiation to establish a secure communication channel. During the handshake, the client sends a timestamp and a random number to the server.
- (2)
- The server sends information containing the digital certificate and the session key K to the client.
- (3)
- The client verifies the digital certificate . Upon successful verification, it encrypts the random number using the key K and sends it to the server. Data encrypted with the public key can only be decrypted by the server’s private key. Once the DTLS handshake is successful, the communicating parties share session data.
- (4)
- The server verifies the client’s digital certificate and decrypts the encrypted using its private key. At this point, the handshake phase is completed, and the key exchange phase begins.
- (5)
- After the DTLS protocol connection is established, the SRTP protocol requires a set of encryption keys and authentication keys to ensure the confidentiality and integrity of media data. The shared key is calculated through an encryption algorithm with the following formula: , where , , , and are encryption parameters negotiated by the SRTP protocol.
- (6)
- Using the derived encryption key , the client encrypts a message and sends it to the server. The server also sends an encrypted message to the client. Once both parties successfully decrypt the messages, the protocol’s key exchange phase is complete, and secure transmission of communication data can begin.
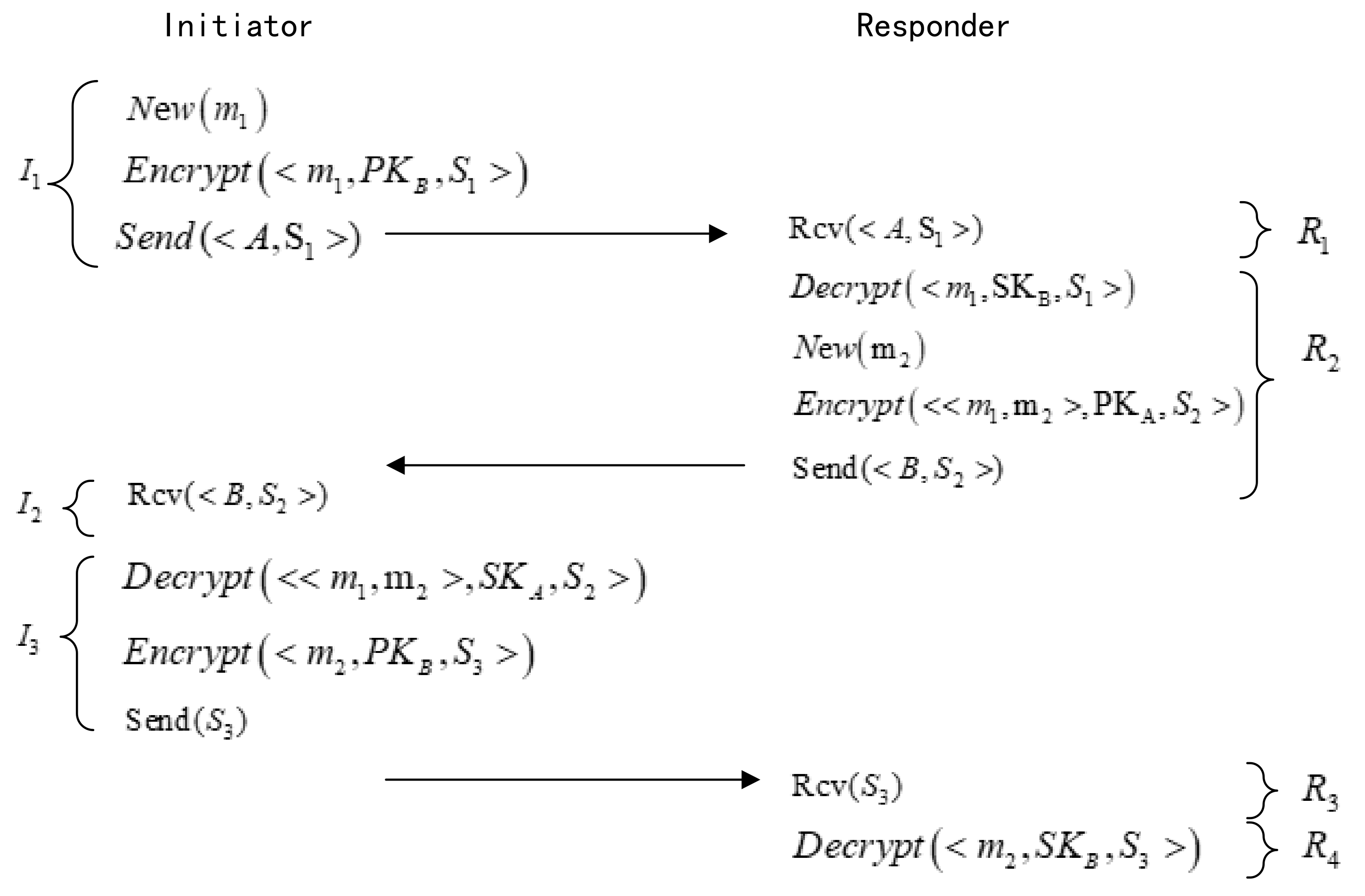
5.2. DTLS Protocol Mutual Authentication Certificate
5.3. SRTP Protocol Confidentiality Certification Process
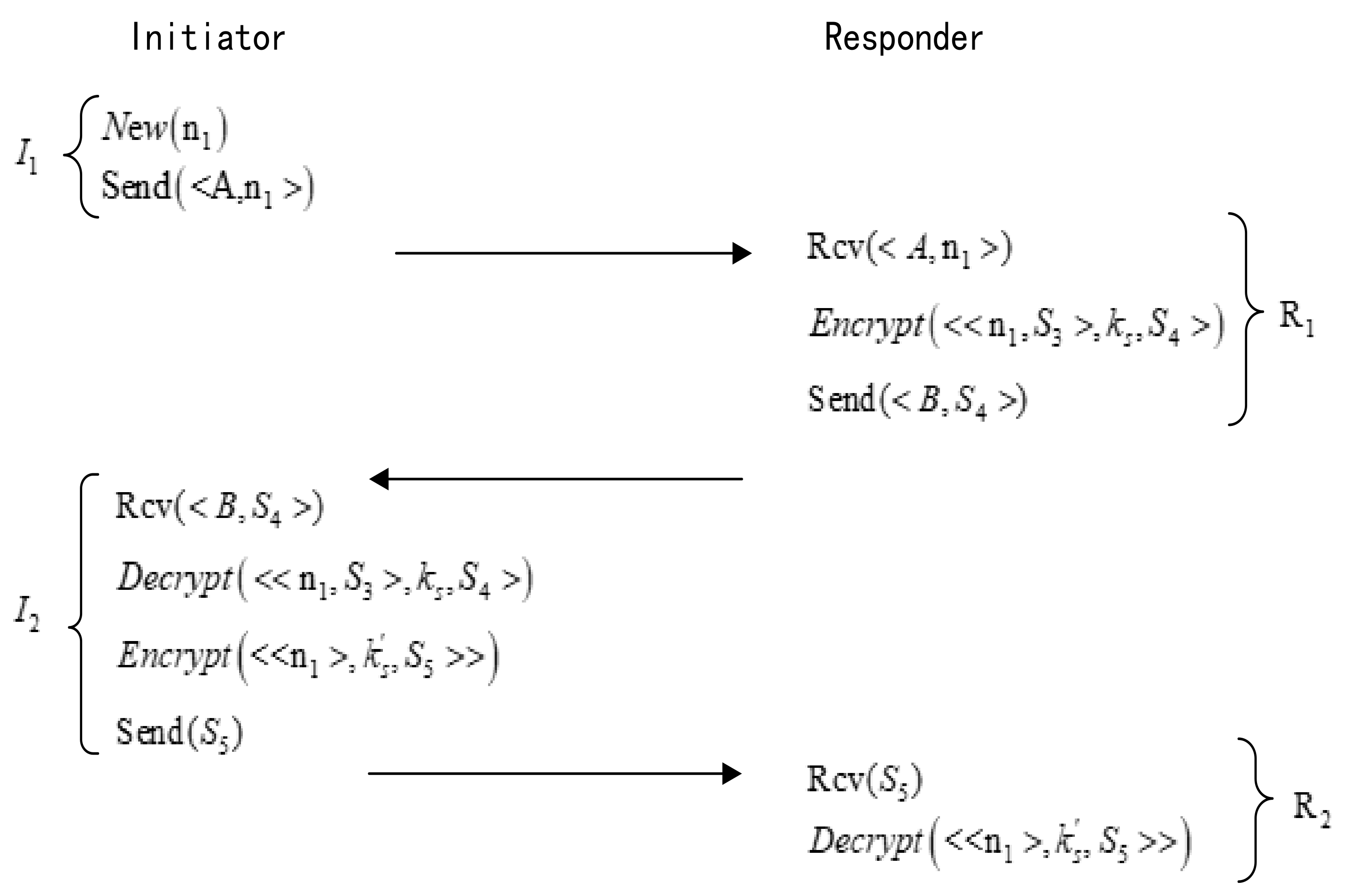
- (1)
- Since subjects A and B have previously negotiated the key in the preceding subprotocol, subject A sends the random number to subject B.
- (2)
- Subject B encrypts the random number using the key and sends the encrypted message to A.
- (3)
- After receiving the ciphertext, subject A decrypts it using the decryption key , obtaining the random number n, which is then encrypted and sent to subject B.
- (4)
- Subject B verifies the consistency of the sent and received random numbers, and upon confirmation, begins communication with subject A using the key . The formal description of the SRTP protocol using Logic of Events theory is illustrated in Figure 6 below.
5.4. Sequential Combination of DTLS and SRTP
5.5. Results and Analysis
- PCL is limited in proving the authenticity of signature protocols only and cannot analyze other non-signature authentication protocols. In contrast, LoET can analyze the authenticity of both signature and non-signature protocols.
- PCL lacks a definition for the pre-order behavior sequences of threads, leading to a lack of rigor in modeling the interaction actions among entities in cryptographic protocol instances. This deficiency fails to ensure the correlation between different basic sequences. In contrast, LoET explicitly defines the thread mechanisms for formal modeling of cryptographic protocols. The specification of thread states is achieved through atomic independence, ensuring the rigor of the modeling.
- PCL, during the analysis of cryptographic protocols, can only capture a partial content of the security properties, demonstrating a lesser capability in characterizing protocol security properties compared to LoET.
6. Conclusions and Future Work
- Extension of Logic of Events theory rules: Building upon the existing Logic of Events theory, we expand the predicate formulas to characterize the states of protocol principals. The extensions include predicates for expressing message freshness and the primacy of send events. We provide corresponding formal definitions, enhancing the analytical capabilities of Logic of Events theory and reducing complexity and redundancy in protocol analysis.
- Introduction of a proof method for Logic of Events combined protocols: Extending the original proof of mutual authentication in Logic of Events theory, we introduce an expanded proof system for secrecy. This extension encompasses the characterization of message confidentiality and explicit reasoning about potential attacker behaviors. We introduce sequential composition rules to describe the security properties of combined protocols. These enhancements and innovations contribute to a more powerful and expressive Logic of Events theory, providing an effective framework for analyzing and proving the security properties of composite protocols like DTLS-SRTP.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cortier, V.; Delaune, S.; Dreier, J.; Klein, E. Automatic generation of sources lemmas in Tamarin: Towards automatic proofs of security protocols 1. J. Comput. Secur. 2022, 30, 573–598. [Google Scholar] [CrossRef]
- Gancher, J.; Sojakova, K.; Fan, X.; Shi, E.; Morrisett, G. A Core Calculus for Equational Proofs of Cryptographic Protocols. Proc. ACM Program. Lang. 2023, 7, 866–892. [Google Scholar] [CrossRef]
- Datta, A.; Derek, A.; Mitchell, J.C.; Roy, A. Protocol composition logic (PCL). Electron. Notes Theor. Comput. Sci. 2007, 172, 311–358. [Google Scholar] [CrossRef]
- Xiao, M.; Chen, Q.; Li, Z.; Chen, Y.; Xu, R. Formal Security Analysis of ECC-Based RFID in Logic of Events Theory. Electronics 2023, 12, 3286. [Google Scholar] [CrossRef]
- Yang, K.; Xiao, M.; Zhong, X.; Zhong, Y. A novel formal logic for formal analysis of timeliness in non-repudiation protocols. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101664. [Google Scholar] [CrossRef]
- Linlin, Z.; Weimin, L.; Wei, Z.; Shaowei, L. The implementation of a secure RTP transmission method based on dtls. In Proceedings of the 2013 Third International Conference on Instrumentation, Measurement, Computer, Communication and Control, Shenyang, China, 21–23 September 2013; pp. 379–383. [Google Scholar]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brünig, M.; Carle, G. A DTLS based end-to-end security architecture for the Internet of Things with two-way authentication. In Proceedings of the 37th Annual IEEE Conference on Local Computer Networks-Workshops, Clearwater, FL, USA, 22–25 October 2012; pp. 956–963. [Google Scholar]
- Dowling, B.; Fischlin, M.; Günther, F.; Stebila, D. A cryptographic analysis of the TLS 1.3 handshake protocol. J. Cryptol. 2021, 34, 37. [Google Scholar] [CrossRef]
- Yao, M.m.; Zhang, J.; Weng, X. Research of formal analysis based on extended strand space theories. In Proceedings of the International Conference on Intelligent Computing, Nanchang, China, 3–6 August 2019; Springer: Cham, Switzerland, 2019; pp. 651–661. [Google Scholar]
- Hagihara, S.; Shimakawa, M.; Yonezaki, N. Verification of Verifiability of Voting Protocols by Strand Space Analysis. In Proceedings of the 2019 8th International Conference on Software and Computer Applications, Penang, Malaysia, 19–21 February 2019; pp. 363–368. [Google Scholar]
- Badimtsi, F.; Canetti, R.; Yakoubov, S. Universally composable accumulators. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 24–28 February 2020; Springer: Cham, Switzerland, 2020; pp. 638–666. [Google Scholar]
- Canetti, R. Universally composable security. J. ACM (JACM) 2020, 67, 28. [Google Scholar] [CrossRef]
- Canetti, R.; Jain, P.; Swanberg, M.; Varia, M. Universally composable end-to-end secure messaging. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 13–18 August 2022; Springer: Cham, Switzerland, 2022; pp. 3–33. [Google Scholar]
- Datta, A.; Mitchell, J.C.; Roy, A.; Stiller, S.H. Protocol composition logic. In Formal Models and Techniques for Analyzing Security Protocols; IOS Press: Amsterdam, The Netherlands, 2011; pp. 182–221. [Google Scholar]
- Yu, L.; Yang, Z.Y.; Zhuo, Z.P. Extension of PCL Theory and Its Application in Improved CCITT X. 509 Analysis. Int. J. Netw. Secur. 2021, 23, 305–313. [Google Scholar]
- Cremers, C.; Düzlü, S.; Fiedler, R.; Fischlin, M.; Janson, C. BUFFing signature schemes beyond unforgeability and the case of post-quantum signatures. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 1696–1714. [Google Scholar]
- Zhang, Z.; de Amorim, A.A.; Jia, L.; Pasareanu, C.S. Automating compositional analysis of authentication protocols. In # PLACEHOLDER_PARENT_METADATA_VALUE#; TU Wien Academic Press: Vienna, Austria, 2020; Volume 1, pp. 113–118. [Google Scholar]
- Gondron, S.; Mödersheim, S. Vertical composition and sound payload abstraction for stateful protocols. In Proceedings of the 2021 IEEE 34th Computer Security Foundations Symposium (CSF), Dubrovnik, Croatia, 21–25 June 2021; pp. 1–16. [Google Scholar]
- Cremers, C. On the protocol composition logic PCL. In Proceedings of the 2008 ACM Symposium on Information, Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008; pp. 66–76. [Google Scholar]
- Cremers, C.; Kiesl, B.; Medinger, N. A Formal Analysis of {IEEE} 802.11’s {WPA2}: Countering the Kracks Caused by Cracking the Counters. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 1–17. [Google Scholar]
- Gallardo, M.d.M.; Merino, P.; Panizo, L. The Role of Abstraction in Model Checking. In Analysis, Verification and Transformation for Declarative Programming and Intelligent Systems: Essays Dedicated to Manuel Hermenegildo on the Occasion of His 60th Birthday; Springer: Cham, Switzerland, 2023; pp. 151–169. [Google Scholar]


| Symbol | Semantics |
|---|---|
| ID | Participants in the agreement |
| Atom | Unpredictable information |
| Data | Plaintext |
| e | Event |
| E | Event set |
| nonce | Random number |
| loc(e) | The location of event e |
| has | Logic contains |
| < | Cause and effect sequence of events |
| || | Logically independent |
| Key(e) | The secret key of the principal of event e |
| bs | Basic sequence |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiao, M.; Zhong, Y.; Li, Z.; Chen, F. Formal Analysis of DTLS-SRTP Combined Protocol Based on Logic of Events. Appl. Sci. 2024, 14, 1804. https://doi.org/10.3390/app14051804
Xiao M, Zhong Y, Li Z, Chen F. Formal Analysis of DTLS-SRTP Combined Protocol Based on Logic of Events. Applied Sciences. 2024; 14(5):1804. https://doi.org/10.3390/app14051804
Chicago/Turabian StyleXiao, Meihua, Yizhou Zhong, Zehuan Li, and Fangping Chen. 2024. "Formal Analysis of DTLS-SRTP Combined Protocol Based on Logic of Events" Applied Sciences 14, no. 5: 1804. https://doi.org/10.3390/app14051804
APA StyleXiao, M., Zhong, Y., Li, Z., & Chen, F. (2024). Formal Analysis of DTLS-SRTP Combined Protocol Based on Logic of Events. Applied Sciences, 14(5), 1804. https://doi.org/10.3390/app14051804






