Abstract
We propose the DIKWP-TRIZ framework, an innovative extension of the traditional Theory of Inventive Problem Solving (TRIZ) designed to address the complexities of cognitive processes and artificial consciousness. By integrating the elements of Data, Information, Knowledge, Wisdom, and Purpose (DIKWP) into the TRIZ methodology, the proposed framework emphasizes a value-oriented approach to innovation, enhancing the ability to tackle problems characterized by incompleteness, inconsistency, and imprecision. Through a systematic mapping of TRIZ principles to DIKWP transformations, we identify potential overlaps and redundancies, providing a refined set of guidelines that optimize the application of TRIZ principles in complex scenarios. The study further demonstrates the framework’s capacity to support advanced decision making and cognitive processes, paving the way for the development of AI systems capable of sophisticated, human-like reasoning. Future research will focus on comparing the implementation paths of DIKWP-TRIZ and traditional TRIZ, analyzing the complexities inherent in DIKWP-TRIZ-based innovation, and exploring its potential in constructing artificial consciousness systems.
1. Introduction
Since the twentieth century, Theory of Inventive Problem Solving (TRIZ) [1,2] has emerged as a systematic methodology for innovation, gradually attracting widespread attention and being applied across various invention and innovation scenarios. TRIZ has expanded into a comprehensive set of methodologies [3,4,5] and practical experiences [6,7], and has also achieved good results in some other fields such as education [8,9], finance [10,11], biomimetics [12,13], etc. However, due to the diversity and complexity of its methodologies, individuals with a limited understanding of TRIZ and cross-domain innovation often find it difficult to master, potentially overlooking certain details and processes [14]. Moreover, the TRIZ method, in its pursuit of innovation, may sometimes neglect the human Purpose and value orientation inherent in the innovation process [15]. To address these issues, we have synthesized the core ideas and principles of the DIKWP theory [16] and proposed the DIKWP-TRIZ method. This approach aims to transform the innovation methodology of TRIZ into Data innovation, Information innovation, Knowledge innovation, Wisdom innovation, and Purpose innovation within the DIKWP-TRIZ framework. By reducing the essence of invention and innovation pathways to these five innovation directions, we place maximum emphasis on human Purpose and value orientation in the innovation process. This strategy reduces the cognitive burden on users of the TRIZ innovation method, allowing them to focus more on innovations in Data, Information, Knowledge, Wisdom, and Purpose, as well as effectively handling problems characterized by incompleteness, inconsistency, and imprecision (the 3-N problems).
The main contributions of this paper are as follows:
- Integration of DIKWP Model with TRIZ Methodology for Artificial Consciousness Innovation: This paper introduces the DIKWP-TRIZ framework, which integration provides a structured approach for applying the TRIZ principle to cognitive processes, particularly to address the incompleteness issues that exist in the concept to Cognitive Space, such as the incompleteness of solutions caused by searching for solutions without understanding the optimization parameters. By bridging the gap between cognitive modeling and inventive problem solving, this approach offers a novel methodology that enhances innovation capabilities in complex, value-driven contexts.
- Comprehensive Mapping of TRIZ Principles to Cognitive Transformations in DIKWP: The research systematically maps TRIZ principles to various cognitive transformations within the DIKWP model, such as the transition from Data to Knowledge or from Wisdom to Purpose. This mapping clarifies the applicability of each TRIZ principle in cognitive processes among the principles. By proposing a refined set of principles and contextual guidelines, the paper improves the precision and efficiency of TRIZ applications in complex cognitive scenarios, thereby facilitating more effective problem solving and innovation.
- Development of a Methodological Framework for Reducing Redundancies and Enhancing Consistency in TRIZ-DIKWP Applications: This study addressed potential inconsistencies in the application of TRIZ principles within the DIKWP framework by extending the TRIZ invention principle in Semantic Space and using Cognitive Space coverage integrity analysis. The proposed methodological framework includes strategies for integrating overlapping principles and offers decision-making tools to guide practitioners in selecting the most appropriate principles for specific cognitive processes. This structured approach ensures a coherent and systematic application of TRIZ principles, enhancing the overall robustness and effectiveness of the DIKWP-TRIZ methodology.
This paper is organized as follows. Section 2 presents related work, introducing the current applications and limitations of TRIZ and the DIKWP theory. Section 3 provides relevant definitions in research mathods. Section 4 discusses the mapping relationship between DIKWP and TRIZ inventive principles under the assumptions of Cognitive Space. In Section 5, we explored the overlapping TRIZ inventive principles within the DIKWP ∗ DIKWP framework, which represents 25 transformation relationships between Data, Information, Knowledge, Wisdom, and Purpose, specifically focusing on the integration of TRIZ into the DIKWP-TRIZ methodology. By differentiating between the overlaps among TRIZ principles under various transformation contexts, we aim to minimize potential inconsistencies and ensure a more cohesive application of the methodology. In Section 5, we compared and explored the differences between the invention principles of DIKWP-TRIZ and TRIZ through the application of a case study, and compared the two in the construction of future creative AI. Finally, Section 6 concludes the paper.
2. Related Works
2.1. DIKWP Model
Unlike the traditional DIKW (Data–Information–Knowledge–Wisdom) model, prior research [16,17,18] has introduced a series of definitions within the DIKWP framework, which incorporates “Purpose” as an additional element in order to build a Purpose-driven model to analyze and handle problems. This extended model maps the 3-N problems onto Cognitive Space, Semantic Space, and Conceptual Space for detailed description and processing [19]. We can use the DIKWP model to describe 3-N problems in three spaces [19], such as the imprecision of textual descriptions reflected in the conceptual space, and the inconsistency of visual observations and perceptions of cognitive subjects reflected in the cognitive space. By connecting and integrating these three spaces, we can use the DIKWP model to analyze and model in scenarios involving the 3-N problem, thereby offering a more robust approach to complex issues.
Artificial Consciousness (AC), often referred to as machine consciousness, aims to simulate or replicate certain features and functions of human consciousness within artificial systems. While human consciousness may be unique due to biological and sociocultural factors, researchers propose that some aspects of consciousness could, in principle, be modeled in machines [20]. Significant challenges in developing AC include philosophical questions, such as whether consciousness is inherently tied to biological life, and technical hurdles, such as replicating the neural and biochemical mechanisms associated with conscious awareness [21]. Some studies suggest that the evolution of artificial consciousness may require architectures involving complex feedback loops and self-regulation, features found in biological systems [22]. We believe that creativity is one of the uniqueness of human consciousness, and we hope to use the DIKWP model and DIKWP’s research in AC [23,24] to build a creative Artificial Intelligence (AI) system to promote the development of artificial consciousness and make it the foundation of creative ability in AC systems. The DIKWP model has been applied in previous research to various fields, including AC [23], privacy protection [25] and doctor–patient interactions [26], which research reflected the model’s versatility and effectiveness in handling complex Information processing tasks across different domains. The DIKWP model’s ability to model and analyze 3-N problems makes it a valuable tool for advancing knowledge representation and problem solving.
2.2. TRIZ Theory
Since its inception in the Soviet Union in the 1960s, TRIZ has evolved into a systematic methodology for innovation. Its application begins with defining the problem and identifying contradictions, which can be technical (conflicting parameters) or physical (opposing requirements). Using tools like the contradiction matrix [27], TRIZ maps these contradictions to one or more of the 40 inventive principles, which provide strategies for generating solutions. In the semiconductor industry, these principles have been employed to enhance smart factories, addressing issues such as mechanical system substitution and changes in physical and chemical properties [28]. In project management, TRIZ principles have been applied to solve innovative challenges in management and business domains [29]. In the field of additive manufacturing, such as 3D printing, these principles support the creation of new geometries and enhanced functionalities [30]. These solutions are then evaluated and refined to ensure alignment with the desired objectives. By emphasizing ideality—maximizing functionality with minimal resources—and leveraging patterns of system evolution, TRIZ offers a structured and efficient approach to solving complex problems across engineering fields. Despite its widespread application in innovative problem solving across various industries, the TRIZ methodology has certain limitations. Firstly, the 40 inventive principles and related tools of TRIZ were originally designed for engineering and technical problems. When applied to other domains, such as software development and service design, terminology mismatches may occur, necessitating reinterpretation or adaptation for effective use [31]. Secondly, the use of TRIZ tools is complex and requires a high level of expertise, which can make it challenging for beginners to use these tools effectively without appropriate training [32]. In the service sector or non-technical fields, applying TRIZ also requires transforming its tools and principles into new forms that are easy to understand and adapt, adding to its complexity [33]. Moreover, Liang et al. [34] developed a computer-aided TRIZ patent classification method. While this approach improves the efficiency of patent classification by integrating text mining with TRIZ, the complexity and heterogeneity of patent literature may lead to issues in semantic understanding and Data annotation consistency when processing multi-domain patent Data, potentially affecting its accuracy. Ilevbare et al. [14] reviewed the challenges of TRIZ in practical applications, highlighting that its complexity and the requirement for extensive Knowledge backgrounds are key factors hindering its effectiveness. They suggested the need to develop tools that are easier to understand and apply. Similarly, dealing with incomplete, inconsistent, or imprecise content poses a challenge to the TRIZ methodology. Yan et al. [35] proposed an ontology-based inventive problem-solving method that links different Knowledge sources through semantic similarity to resolve Information inconsistencies. Although this method theoretically offers a promising solution, its implementation relies on precise semantic computations and complex Knowledge base management, which may present challenges in large-scale and dynamic real-world applications. Furthermore, they also developed an automated ontology system named IngeniousTRIZ to facilitate the solution of inventive problems [36]. Although this system can automatically populate and manage Knowledge sources within the TRIZ model, enhancing users’ ability to tackle complex problems, its limitation lies in the fact that for engineering problems across different fields, such automated processing may not cover all possible scenarios, requiring additional manual intervention to ensure the applicability of solutions.
3. Research Methodology
DIKWP-TRIZ approaches and solves problems from a more fundamental perspective than TRIZ. Figure 1 illustrates the problem-solving process using the TRIZ theory. The blue arrows represent cognitive processing, and the adjacent labels denote the methodologies or approaches involved in this cognitive process. It is evident that the traditional TRIZ methodology relies heavily on conceptual or hierarchical abstraction to frame the problem and find a solution. The cognitive process then occurs within the Cognitive Space, transforming a general solution into a specific one, often through trial and error, until the problem is resolved.
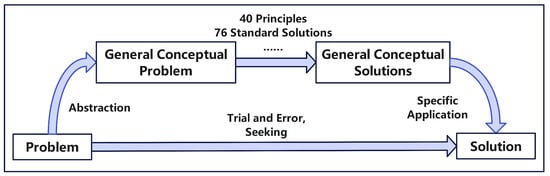
Figure 1.
TRIZ’s problem-solving process.
In contrast, Figure 2 presents the problem-solving process under the DIKWP-TRIZ methodology. Using the DIKWP theory, cognitive agents construct a DIKWP processing model for the 3-N problem. We have developed 25 transformation methods to handle 3-N problems by facilitating the conversion between DIKWP contents (as shown in the bottom left of Figure 2). This construction and mapping process is then translated into corresponding TRIZ invention principles. This approach enhances the applicability of TRIZ by mapping the essential problem-solving semantics to concepts, thereby extending the scope of TRIZ invention principles. Additionally, the generated general solutions incorporate DIKWP conceptual content, ensuring that the solutions are both credible and controllable.
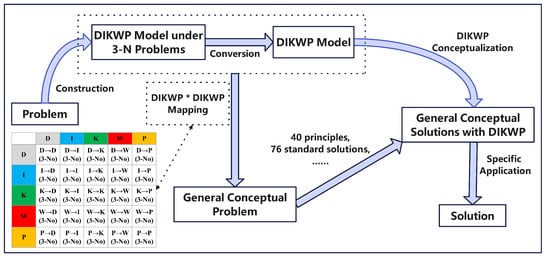
Figure 2.
TRIZ’s problem-solving process.
3.1. DIKWP Conceptualization
3.1.1. Data Conceptualization
In the DIKWP model, Data semantics (DIKWP-Data) represent specific manifestations of shared semantics in cognition. Within the Conceptual Space, Data concepts embody specific facts or observations recognized by cognitive entities, confirmed through their alignment with the conscious (non-subconscious) space of these entities and their correspondence with the shared semantics of existing cognitive concepts. When processing Data concepts, cognitive systems identify and extract shared semantic elements, which serve as labels for these concepts, unifying them based on corresponding shared attributes. For example, when observing a group of sheep, despite variations in size, color, or gender, cognitive processing categorizes them under the concept of “sheep” by identifying shared or probabilistically related semantics. Similarly, in distinguishing between a silicone arm and a human arm, the cognitive process may rely on features like shape or color; however, a lack of functionality, such as rotation, would exclude the silicone arm from the concept of “arm” based on the semantic criterion of rotatability.
The distinction between conceptual and Semantic Spaces reflects different philosophical perspectives on technology. Conceptual Space processing corresponds to natural language communication, but the core function of communication lies in conveying semantics. In the Cognitive Space, effective comprehension of transmitted concepts hinges on semantic correspondence within the Semantic Space of the cognitive entity. However, since the Semantic Space is often subjective and cannot be fully shared through conceptual forms, it is referred to as subjective.
In the Semantic Space, the semantics of Data concepts are manifestations of a shared set of cognitive semantics. There is a shared or approximate semantic attribute set S, defined by a collection of feature semantics:
where represents an individual feature semantic of the Data. The set D is defined as follows:
where each element and D represents the set of specific Data semantics.
In the DIKWP model, the distinction between Data concepts and Data semantics is crucial for transitioning between the Cognitive Space and the processing of conceptual and Semantic Spaces. Data concepts and Data semantics represent specific cognitive objects that directly embody observed facts and Knowledge. The key to this transformation lies in the shared semantics underlying the cognition and conceptualization of these Data concepts. In Cognitive Space, Data objects are the foundation of cognitive processes, moving beyond mere observations or measurements of the world and undergoing explicit conceptual and semantic confirmation. This process also distinguishes between subjective and objective content categories, refining the traditional DIKW model’s approach to Data by emphasizing the close association between Data and specific semantic attributes. Cognitive recognition of Data actively seeks semantic features that match known cognitive objects, thereby highlighting the subjectivity and context-dependence of Data, as well as its value in associating with existing Conceptual Spaces of cognitive entities.
Within the DIKWP model, the semantics of cognitive Data objects from the Cognitive Space are viewed as specific manifestations of shared semantics in the cognitive process. This perspective emphasizes that Data are not merely records of observations or facts, but the results of semantic matching and conceptual confirmation by cognitive entities (humans or AI systems) in both conceptual and Semantic Spaces. The key to confirming Data concepts lies in the shared semantics between the cognitive and Semantic Spaces, allowing for the classification of specific objects under the same Data concept despite external differences.
Data concepts are foundational conceptual units in the DIKWP cognitive process, while Data semantics serve as foundational semantic units. Together, they play a central role in directly observing and recording the real world, from cognitive recognition to the confirmation of Data concepts in generating and applying concept-based natural language representations. Cognitive entities, through both conscious and subconscious processes, recognize and classify Data concepts by identifying shared semantic attributes. Cognitive science emphasizes how cognitive systems (including neural processes and pattern recognition mechanisms) process and recognize Information, with subconscious pattern recognition and conscious analysis combined to explain recognition based on shared semantic features. For instance, despite differences in color or size, humans recognize apples through subconscious pattern recognition and can explain this recognition by referring to key semantic features such as shape or texture. This illustrates how the cognitive system uses shared Data semantics in the Semantic Space to construct conceptual representations in natural language.
In the DIKWP framework, Data concepts are specific mappings of shared semantics in the cognitive process, resolving the traditional confusion between semantics and concepts. Data concepts are closely linked to the semantic processing of cognitive entities, emphasizing that their value lies not in their physical attributes but in how they bridge the conceptual and Semantic Spaces within the cognitive system. Interaction between individual and collective consciousness is fundamentally an interaction between semantic and Conceptual Spaces, either consciously or subconsciously. Data concepts, as symbolic expressions of shared or probabilistically similar semantic sets, enhance the efficiency of cognitive communication, particularly in engineering contexts where specific semantic sets are represented as symbols.
3.1.2. Information Conceptualization
In the DIKWP model, the concept of Information (DIKWP-Information) corresponds to one or more “distinct” semantics in cognition. The Information semantics of an Information concept refer to the association of semantics within the Semantic Space of a cognitive entity Cognitive Space, linked with recognized DIKWP cognitive objects. This process occurs through the entity’s cognitive purposes, either establishing identical cognition (corresponding to Data semantics) or distinct cognition, confirmed probabilistically or through logical judgment. This distinction forms new semantic associations, as “new” is considered a form of “different” semantics.
When processing the concept or semantics of Information, cognitive entities identify differences between input contents (such as Data, Information, Knowledge, Wisdom, or Purpose) and recognize DIKWP cognitive objects, classifying Information according to these various “distinct” semantics. For example, in a parking lot, although all vehicles can be grouped under the concept of “car”, each vehicle’s position, usage, owner, condition, payment history, and experiences represent distinct cognitive differences corresponding to unique Information semantics, driven by different cognitive purposes within the Semantic Space. These variations in semantics often exist within the cognitive entity’s perception but may not always be explicitly articulated. For instance, a patient with depression may describe feeling “low spirits” to reflect a subjective increase in the intensity of negative emotions compared to past experiences. However, this concept of “low spirits” may not convey the same Information semantics to another cognitive entity, resulting in a subjective interpretation that may differ from the target’s understanding.
Mathematically, the processing of Information semantics within the DIKWP model follows a Purpose-driven transformation. In the Semantic Space, the processing of Purpose-Driven Information semantics () for DIKWP content involves mapping inputs X to outputs Y:
where X represents the set or combination of Data, Information, Knowledge, Wisdom, and Purpose semantics (DIKWP content), and Y represents newly generated DIKWP semantics. This mapping highlights the dynamic and constructive nature of Information semantics generation.
In the DIKWP model, Information semantics reflect the expression of distinct semantics within cognition. Through the cognitive Purpose of the entity, Information semantics connect the existing semantics of Data, Information, Knowledge, Wisdom, or Purpose to recognized cognitive objects, generating new semantic sets or combinations. This process not only involves recombination and semantic transformation (including forming cognitive understanding through semantic connectivity) but also dynamically creates new DIKWP cognitive semantics, contributing to continuous cognitive understanding.
The generation of Information semantics focuses on linking sets or combinations of different Data, Information, Knowledge, Wisdom, or Purpose semantics through specific cognitive purposes. This process confirms cognitive understanding within the Cognitive Space, involving associations, comparisons, and conceptual correspondence between observed phenomena and existing DIKWP content. In AI systems, this corresponds to forming cognitive understanding by analyzing the relationships between DIKWP content through algorithms, extracting valuable Information semantics.
Information semantics processing is a dynamic cognitive process that links DIKWP content semantics to existing cognitive objects through the cognitive entity’s subjective purposes, generating valuable semantic associations. The true value of Information lies in its function as a bridge between Data, Information, Knowledge, Wisdom, and Purpose, revealing how cognitive entities establish semantic connections with DIKWP content.
In cognitive science, various theories explain Information semantics processing. For example, Conceptual Integration Theory explores how new meanings and understandings emerge by integrating Information from different sources. Similarly, by combining an individual’s behavior (DIKWP content semantics) with contextual Information, cognitive entities gain clearer insights into their purposes. Cognitive linguistics, through theories such as Metaphor Theory and Blending Theory, studies how new meanings are created through metaphorical and conceptual integration in language. In AI, algorithms are designed to simulate how humans construct new cognitive models through DIKWP content semantics.
The generation of Information semantics involves interactions between DIKWP content semantics and DIKWP-to-DIKWP semantic interactions. This process encompasses not only the reorganization and reinterpretation of DIKWP content but also a dynamic, Purpose-driven cognitive activity. Through this, cognitive entities can identify new patterns and associations, expanding their cognitive understanding. The constructive and dynamic nature of Information semantics generation reflects the active interpretation or semantic connection of DIKWP content.
3.1.3. Knowledge Conceptualization
In the DIKWP model, the semantics of Knowledge (DIKWP-Knowledge) correspond to one or more “complete” semantics within the Cognitive Space. These Knowledge semantics represent the cognitive entity’s understanding and interpretation of relationships between cognitive objects of DIKWP content, achieved through semantic abstraction and integrity processes. This involves making certain assumptions that lead to the formation of cognitive inputs, which arise from interactions with existing DIKWP content semantics and correspond to “complete” semantics that reflect cognitive integrity in higher-order Cognitive Spaces.
When processing Knowledge concepts, cognitive entities abstract at least one concept or pattern corresponding to complete semantics through observation and learning. For example, while it may be impossible to observe every swan to confirm they are all white, in the Cognitive Space, the cognitive entity can make assumptions (higher-order cognitive activities) based on observed instances, assigning ”complete” semantics to these observations. This leads to the formation of Knowledge semantics, such as the rule “all swans are white”, even without exhaustive observational Data. Knowledge thus acts as a bridge, transforming a state of non-understanding into one of understanding, grounded in comprehensive semantics, and strengthened through validation.
The construction of Knowledge relies not only on the accumulation of Data and Information but, more importantly, on abstraction and generalization processes within cognition, allowing the cognitive subject to uncover the essence and intrinsic connections of things. Knowledge exists at both individual and collective levels, shared and transmitted through culture, education, and societal interaction. Knowledge semantics refers to the structured understanding formed through deep processing and internalization of DIKWP content, corresponding to “complete” semantics in the Semantic Space.
Within the DIKWP framework, Knowledge is defined as a deep understanding of the world and a mastery of complete semantics, aligning with Aristotle’s notion of formal cause. This philosophical perspective suggests that the essence and Purpose of things can be comprehended through reason and experience, reflecting a profound grasp of the world’s underlying principles.
The formation of Knowledge rules in the DIKWP model represents the cognitive subject’s understanding of the intrinsic laws and essence of reality. Philosophically, Knowledge is both a product and a driving force of cognitive processes, guiding the cognitive entity in navigating the complexities of the real world. The development and application of Knowledge reveal how cognitive subjects adapt to and engage with the deeper regularities of reality through semantic understanding.
3.1.4. Wisdom Conceptualization
In the DIKWP model, Wisdom (DIKWP-Wisdom) is defined as Information pertaining to ethics, social morality, human nature, and related aspects. It embodies a form of Information derived from cultural norms and societal values, contrasting with the relatively fixed extreme values of the present time or individual cognitive values. In the Cognitive Space, Wisdom semantics are determined by integrating Data, Information, Knowledge, Wisdom, and Purpose. The core of Wisdom in both human and AI systems lies in constructing a human-centered value system, aimed at fostering a community with a shared future for humanity. This value system forms the foundation for constructing, differentiating, validating, refining, and developing individual and collective cognitive, semantic, and Conceptual Spaces of DIKWP content semantics, guiding the decision-making process.
For instance, when making decisions based on specific DIKWP content, cognitive subjects must consider a broad range of factors—such as ethics, morality, and feasibility—rather than focusing solely on the technical or efficiency-based aspects of the DIK elements. Wisdom, denoted as W in the decision function, correlates Data, Information, Knowledge, Wisdom, and Purpose, producing an optimal decision :
where W represents a decision function that generates the optimal decision and D, I, K, W, P represent Data, Information, Knowledge, Wisdom, and Purpose, respectively, reflecting the comprehensiveness and goal-oriented nature of value-driven decision making. This aligns with cognitive linguistics research on how morals and values are communicated and interpreted through language.
In the DIKWP model, Wisdom is regarded as a holistic construct grounded in core human values, integrating ethical, moral, and individual considerations. It encompasses not only the application of Data, Information, and Knowledge but also the balance of diverse factors, including ethical and moral dimensions, within the decision-making process. Wisdom semantics processing involves making judgments and decisions by synthesizing Data, Information, and Knowledge with individual or collective values and ethical principles.
In the field of AI, Wisdom semantics processing is crucial to the development of advanced decision-making artificial consciousness systems or ethical AI. These systems incorporate multiple factors based on human-centered principles to offer solutions that are intelligent and aligned with ethical standards.
In cognitive science, the processing of Wisdom semantics corresponds to managing DIKWP content semantics through the lens of human development, value systems, moral judgments, and social contexts. Wisdom content is more than a mere accumulation of DIKWP elements; it addresses how to process DIKWP semantic content in the Semantic Space, guided by a vision of building a human community, beginning from the Cognitive Space. For example, in addressing climate change, the application of Wisdom entails using the cognitive subject’s understanding of environmental science (Knowledge), assessing both long-term and short-term consequences (Information), and making decisions (Information) based on ethical and social responsibility (Wisdom).
The formation of Wisdom in both cognitive subjects and social groups relies not only on the cognitive capabilities of individuals and collectives in understanding DIKWP content semantics but also on their ability to interact with, deeply understand, and reflect on their environment, cultural background, and social relationships as they relate to DIKWP content.
In the DIKWP model, Wisdom plays a pivotal role in decision making, integrating considerations of ethics, morality, and values. It underscores the inextricable link between Data, Knowledge, and Information with value orientations in practical applications, reminding cognitive subjects that cognition is not solely about the pursuit of truth, but also about exploring the ideal way of human life. This notion resonates with Aristotle’s concept of “phronesis” or practical Wisdom, which emphasizes the capacity to make the best ethical judgments and decisions in specific contexts.
3.1.5. Purpose Conceptualization
In the DIKWP model, the semantics of Purpose (DIKWP-Purpose) are represented as a tuple (Input, Output), where both the Input and Output consist of semantic elements related to Data, Information, Knowledge, Wisdom, or Purpose. The semantics of Purpose encapsulate stakeholders’ understanding of DIKWP content in relation to a phenomenon or problem (Input) and the objectives they aim to achieve through processing and resolving that issue (Output). When cognitive agents engage with Purpose semantics, they interpret the Input DIKWP content in a Semantic Space according to predefined goal (Output) semantics. Through learning and adaptation in processing DIKWP content, the output semantics progressively align with the specified goal semantics.
Purpose can be mathematically modeled as , with Input and Output representing the semantic contents of Data, Information, Knowledge, Wisdom, or Purpose. A transformation function T facilitates the transition from Input to Output, based on the input content and predefined objectives:
This formulation emphasizes the dynamism and goal-oriented nature of cognitive processes, providing a mathematical framework for understanding and designing cognitive systems with specific objectives.
Purpose represents the intentionality and directionality of cognitive activities, serving as the driving force behind individual and systemic actions. It not only defines the trajectory from the current state to a desired state but also reveals the underlying motivations and direction of cognitive processes. This goal-driven approach highlights the proactive and creative nature of cognitive agents as they process DIKWP semantic content. Rather than passively receiving Information, cognitive agents actively pursue specific objectives, shaping how they interpret and manipulate Data, Information, Knowledge, Wisdom, and Purpose itself. Purpose thus guides not only the collection and processing of Data and Information but also the development of Knowledge and the application of Wisdom.
The concept of Purpose introduces a teleological perspective, suggesting that cognitive activities are not arbitrary Data-processing events but are directed toward achieving specific goals or fulfilling needs. In the DIKWP framework, the inclusion of Purpose enriches the model’s dynamism, highlighting the subjectivity and intentionality of cognitive activities. It implies that cognitive agents actively seek, select, and interpret DIKWP content based on clearly defined goals and purposes within the Semantic Space.
Purpose-driven processing offers a structured framework for understanding cognitive activities from a dynamic, goal-oriented perspective. It aligns with theories such as Action Theory in Cognitive Linguistics, enabling the DIKWP model to not only explain existing cognitive phenomena but also guide future cognitive actions, optimizing strategies and behaviors to achieve specific objectives. In AI systems, identifying Purpose and designing goal-oriented behaviors are essential for implementing intelligent functions, such as understanding user queries in natural language processing (NLP) or optimizing pathways to achieve goals in planning algorithms. In the study of artificial consciousness, recognizing and simulating human Purpose-driven behavior is critical for developing advanced cognitive capabilities.
From a philosophical standpoint, Purpose is not merely a predefined goal of action but reflects the fundamental driving force behind individual existence and behavior. It embodies free will and aspirations for the future, acting as the intrinsic motivator in the interaction between individuals and the world. The existence of Purpose underscores the subjectivity and creativity of cognitive processes, revealing the deeper meanings behind human actions. This notion aligns with Aristotle’s concept of final causes, which posits that everything has a Purpose or ultimate reason for existence. It also resonates with Hegel’s teleological view, where reality is driven by the unity of opposites, achieved through self-realization and self-negation in purposive action. Additionally, it corresponds with existentialist philosophy, which emphasizes individual choice and Purpose as defining aspects of existence.
In the DIKWP model, Purpose reflects that cognitive activities are not merely responses to external stimuli but are actively constructed based on individual goals, values, and purposes. This dimension of the model captures the complexity and intentionality of human cognition and behavior, emphasizing that the pursuit of Purpose is a key driver in both human and artificial cognitive processes.
3.2. Mapping TRIZ Principles to DIKWP Transformations
We will aim to systematically identify the correspondence between specific TRIZ principles and distinct DIKWP transformations. The objective is to elucidate how each principle can be effectively applied to cognitive processes associated with the five key elements of the DIKWP model: Data, Information, Knowledge, Wisdom, and Purpose. By aligning each DIKWP transformation with one or more TRIZ principles, a structured framework that leverages the strengths of both models can be constructed, thereby optimizing cognitive processing and fostering innovative activities.
The anticipated mapping process is expected to reveal the frequent recurrence of certain TRIZ principles across various DIKWP transformations. Such recurrence may indicate potential overlaps or redundancies among principles, which could undermine the effectiveness of individual principles or lead to confusion in practical applications. To address this issue, the study will explore strategies for integrating overlapping principles. This may involve consolidating similar principles into a unified concept or subdividing them into more granular sub-principles. These improvements are intended to enhance the clarity and precision of the TRIZ-DIKWP mapping, ensuring that each principle is distinctly defined and its application within the DIKWP context is both unambiguous and efficient.
Furthermore, the research will include detailed case analyses to demonstrate the practical application of the mapped principles across different cognitive scenarios. These case studies will not only validate the effectiveness of the theoretical mappings but also illustrate how the combination of TRIZ principles and DIKWP transformations can generate innovative solutions in complex cognitive processes. The ultimate goal is to establish a robust methodological framework that enables practitioners to systematically apply TRIZ principles within the DIKWP model, thereby facilitating more effective problem-solving and decision-making processes.
3.3. Cognitive Space Coverage Integrity Analysis
The method will employ a comprehensive evaluation method using a matrix to assess the integrity of Cognitive Space coverage. The 5 ∗ 5 matrix represents the potential interactions between the elements of the DIKWP model, enabling a systematic examination of the extent to which the TRIZ principles cover various cognitive transformations across the entire Cognitive Space. The primary objective of this analysis is to ensure that the TRIZ principles provide thorough coverage of all possible cognitive transformations, thereby preventing any gaps or blind spots that could impede the innovation process.
The theoretical foundation of this analysis is rooted in the concept of Cognitive Space coverage integrity, which posits that for an innovation methodology to be effective, it must encompass all relevant types of cognitive transformations. This includes transformations ranging from basic Data processing to more complex, Wisdom- and Purpose-driven cognitive activities. By systematically evaluating the presence or absence of TRIZ principles in each cell of the DIKWP matrix, the study will identify areas where certain types of cognitive transformations are inadequately addressed. This assessment will offer valuable insights into the completeness and effectiveness of the TRIZ principles when applied within the DIKWP framework.
Based on these findings, the study will propose enhancements or modifications to the existing TRIZ principles to ensure comprehensive Cognitive Space coverage. This may involve the introduction of new principles tailored to address specific gaps, or the refinement of existing principles to better align with the nuanced requirements of DIKWP transformations. The ultimate aim is to develop an optimized set of TRIZ principles that can comprehensively and effectively support all cognitive processes defined within the DIKWP model.
3.4. Application of DIKWP-TRIZ
We demonstrate the application of the DIKWP-TRIZ framework through a case study and compare its methods with traditional TRIZ methods. By utilizing the DIKWP model, the problem is analyzed in terms of its objectives, ensuring a comprehensive exploration of potential solutions through the systematic organization of congruent and divergent semantic elements. These insights are then mapped to the inventive principles of TRIZ to establish a connection between DIKWP transformations and TRIZ problem-solving strategies. The application is illustrated through a case study, where shared semantic elements are analyzed and transformed into a clear, Purpose-driven framework. Unlike the conventional TRIZ method, which heavily depends on user cognition and the completeness of parameter definition, DIKWP-TRIZ systematically transforms problem data into knowledge-driven solutions that emphasize Purpose and integrity. It showcases the enhanced capability of DIKWP-TRIZ to systematically generate innovative solutions while reducing the cognitive burden on users, making it a more versatile and comprehensive framework for problem solving.
4. Mapping and Coverage Analysis of TRIZ Rules in DIKWP
4.1. Mapping the 40 TRIZ Principles to the DIKWP Model
The research methodology will involve identifying which TRIZ principles are applicable to specific DIKWP transformations. In Table A1 in the Appendix A, we provide a comparison of TRIZ invention principles. Each DIKWP transformation can be guided by one or more TRIZ principles to optimize the cognitive process. To address this, we will explore possible solutions such as merging overlapping principles or creating sub-principles to improve clarity and distinction.
4.1.1. Data (D) → Data (D)
The transformative process explores the conversion of Data, as a set under the same semantics, into various interpretations within a cognitive subject, as well as how existing Knowledge guides the collection and interpretation of these Data. This bidirectional transformation process emphasizes the dynamic interaction among Data and aims to establish a continuous cognitive improvement cycle. The following are several TRIZ principles related to this transformation process, along with their application examples:
- Principle 1: SegmentationThis principle involves dividing large datasets into smaller, more manageable segments to facilitate detailed analysis and obtain targeted insights. This strategy helps optimize resource utilization and enhances the efficiency of the analytical process [37].
- Principle 2: ExtractionExtracting necessary subsets or key Data elements from large datasets to focus attention on core Information, avoiding distractions caused by irrelevant Data [38,39]. This method significantly improves both the speed and effectiveness of Data processing.
- Principle 5: MergingIntegrating datasets from different sources to create a more complete and robust dataset. This not only enhances the overall accuracy of the Data but also increases its utility, providing a solid foundation for decision making [40].
- Principle 10: Preliminary ActionsPreprocessing the Data, such as cleansing, standardization, or structural adjustment, prior to formal analysis to ensure the smoothness and effectiveness of subsequent Data operations. This step is essential in Data analysis, as it directly impacts the quality of the final results. For instance, in Data mining, preprocessing steps like Data cleaning, normalization, and integration are essential for reducing noise and inconsistencies, which are common in large datasets. Proper preprocessing improves the performance of Data analysis and mining algorithms, leading to more robust findings. Additionally, preprocessing also includes standardization, which ensures that all Data points are on the same scale, enhancing the accuracy of analytical models and decision-making processes [41].
- Principle 12: EquipotentialityWe have extended the semantic content of this principle here, which is to reduce excessive content flow, complexity, and inconsistency through certain optimization strategies, such as layering or preset boundaries, in order to improve the coordination of the entire system. For example, in software development in Domain-Driven Design [42] mode, all sub-business domain models with the same level are divided into the same equipotential surface. In addition, a unified domain modeling language can be established to ensure that domain experts and developers have the same understanding of the same term.
- Principle 18: Mechanical vibrationWe have expanded the semantic content of this principle by adding a specific mechanism to randomize or denoise the data content, ensuring that the entire system operates at its optimal state. For example, in the protection algorithm for Differential Privacy [43], researchers use Differential Privacy technology to protect individual data without significantly affecting the statistical results and try to avoid individual data leakage as much as possible [44].
- Principle 26: CopyingThe main principle is to use a simple, inexpensive, and easy-to-manufacture replica instead of an expensive or complex original. This principle is reflected in the concept of metaverse [45], which models display targets through computer graphics technology to form data-driven content, allowing users to achieve immersive experiences through virtual reality- or augmented reality-related technologies.
- Principle 30: Flexible Shells and Thin FilmsWe have expanded the semantics of this principle by isolating and processing specific data content from other data content under certain conditions, in order to prevent the environment in which specific content is located by directly accessing that content. For example, in encryption application scenarios, the application of Homomorphic Encryption [46] technology is extremely important, as it can be used and searched without affecting its confidentiality.
4.1.2. Data (D) → Information (I)
The transformation of Data into Information involves the cognitive subject distinguishing Data under different semantic contexts to obtain the corresponding Information semantics. This process requires not only technical support but also a deep understanding of the Knowledge embedded within the Data. Below are several TRIZ principles and their specific applications related to this transformation process:
- Principle 3: Local QualityFocus on analyzing specific Data subsets to generate detailed Information. This approach can reveal insights that might be overlooked from a global perspective, providing in-depth understanding at a local level. For example, in large-scale market research Data, examining the behavior patterns of a particular consumer group can uncover unique preferences and needs, thereby informing product customization. For example, a study on large-scale software engineering Data demonstrated the benefits of splitting Data into smaller, more homogeneous subsets, resulting in improved model performance and more accurate predictions [47].
- Principle 5: MergingIntegrate Data points from various sources to form a coherent and valuable Information system, facilitating a comprehensive understanding of the subject matter. For instance, combining user behavior Data, geographical Information, and social media feedback can help companies build a more comprehensive user profile, thereby enhancing the effectiveness of marketing strategies [48].
- Principle 7: Nested DollCognitive subjects are able to nest multiple data fields together, progressively forming contrasting content and constructing different semantic expressions. For example, a company’s sales report can reflect the content that users want to understand and compare at once through multiple layers of nesting.
- Principle 9: Preliminary Anti-ActionThe principle of preliminary anti-action in TRIZ, which involves preprocessing steps like filtering out noise or irrelevant Data, is crucial to enhancing the clarity and quality of Information. For instance, techniques such as noise reduction in various applications, like hyperspectral imaging, improve the analysis of key signals by eliminating non-white noise prior to formal analysis [49]. Additionally, noise filtering algorithms can significantly improve Data quality, especially in scenarios involving imbalanced Data or chaotic signals, thereby enhancing the subsequent Data analysis [50]. These preprocessing steps are essential for ensuring the authenticity and reliability of Information, reducing potential biases during analysis, and improving the overall quality of results [51].
- Principle 17: Another DimensionBy utilizing multidimensional representations of data, such as visualization tools or multi-layer models, content with the same semantics can be presented and differentiated through another dimension, revealing deeper insights and providing rich and detailed understanding. For example, using 3D charts to display trend changes in time series data, or using heat maps to illustrate the strength of correlations between variables, can help analysts more intuitively grasp data characteristics [52].
- Principle 28: Mechanics SubstitutionAutomate Data processing tasks using algorithms and tools to efficiently transform large amounts of Data into meaningful Information. With the advancement of machine learning and AI technologies, such automated methods have become an indispensable part of modern Data analysis, significantly enhancing the speed and accuracy of Information extraction [53].
- Principle 35: Parameter ChangesBy altering the measurement standards, formats, or parameters of Data, new Information semantics can be revealed. In financial market analysis, applying different smoothing parameters to historical trading Data can distinguish between short-term and long-term market fluctuations. For example, using moving averages with different periods (such as 5-day and 200-day moving averages) can identify short-term market volatility and long-term trends, thereby providing a basis for investment decisions [54].
4.1.3. Data (D) → Knowledge (K)
The cognitive subject systematically analyzes Data semantics by identifying their similarities and differences, thereby organizing them into structured Knowledge and forming a logically coherent Knowledge system. Through this process, the cognitive subject not only categorizes and integrates disparate Data points but also establishes a comprehensive and interconnected framework of Knowledge. This structured organization facilitates a deeper understanding of the relationships and underlying patterns within the Data, ultimately contributing to the development of a cohesive and consistent Knowledge system that can support complex decision-making and reasoning processes. The following are several TRIZ principles related to this transformation process, along with their application examples:
- Principle 6: UniversalityExtract general principles or models from specific Data points and extend localized insights to broader contexts. For example, in collaborative environments such as cross-functional software development teams, applying universal principles from one industry can enhance team Knowledge sharing and efficiency across different sectors [55].
- Principle 24: IntermediaryUtilize intermediate models, such as simulations or analytical frameworks, as bridges between raw Data and refined Knowledge to facilitate the understanding and interpretation of complex datasets. For example, in financial risk management, intermediary models like stochastic differential equations are used to model economic scenarios and bridge the gap between complex raw Data and actionable insights [56].
4.1.4. Data (D) → Wisdom (W)
The cognitive subject integrates ethical and value judgments to generate goal-aligned, wise decisions through the semantic analysis of Data. This process requires not only a profound understanding of the Data itself but also the integration of experience and intuition to achieve a comprehensive cognition that transcends specific contexts. The following are several TRIZ principles closely related to this transformation process, along with their specific applications:
- Principle 40: Composite MaterialsWe extend the semantics of materials to transform them into Data, while composites are expanded into multiple channels or methods serving as Data sources. Correspondingly, in Information technology, this process involves integrating various Data sources and analytical models to generate comprehensive, high-quality decisions guided by Wisdom. This approach is exemplified in applications such as financial risk management [57] and the formulation of optimized traffic management strategies [58], where diverse Data inputs and sophisticated analysis converge to produce holistic, informed decisions.
4.1.5. Data (D) → Purpose (P)
The cognitive subject or process identifies and analyzes common semantics among Data to clarify objectives and purposes, thereby guiding the formulation of future strategies. This ensures that the output of goal setting remains consistent within the scope of the identified semantics. By maintaining alignment with the semantic framework, the cognitive subject can develop coherent and Purpose-driven strategies that are well grounded in the underlying Data patterns, thus enhancing the effectiveness and precision of decision-making processes.
- Principle 4: AsymmetryWe can prioritize subsequent objectives based on the relevance of Data collection and analysis activities to the intended Purpose, ensuring that resources are concentrated in high-impact areas. This approach allows for a strategic allocation of efforts, maximizing the effectiveness of decision making and optimizing outcomes by focusing on areas that most significantly contribute to achieving the desired goals [59].
- Principle 11: In-advance cushioningStakeholders utilize historical traffic and log Data from the same period in previous years to proactively prepare Data systems and infrastructure, supporting anticipated goal-driven demands and enhancing flexibility and readiness. For instance, in e-commerce platforms, to accommodate the surge in traffic during upcoming shopping seasons, stakeholders may upgrade server capacity and optimize database architecture in advance. These proactive measures ensure that the system can handle high concurrent access loads, thereby maintaining performance and reliability under increased demand [60,61].
- Principle 15: DynamismMaintain a flexible Data strategy that can evolve with changing purposes or goals, ensuring its ongoing relevance and effectiveness. For example, in a rapidly changing market environment, regularly evaluating and adjusting Data analysis models to reflect the latest market demands and trends enables the organization to base its decisions on the most up-to-date Information. For instance, the concept of asymmetric resource allocation is also applicable in situations involving emergency medical services. During mass casualty incidents, allocating resources based on prioritization, such as through column generation models, maximizes lifesaving capacity [62].
- Principle 29: Pneumatics and HydraulicsWe have expanded the semantics of this principle to include the concept of increasing the degrees of freedom of the target. Adjusting the degrees of freedom of the system through external data-driven means to achieve the desired goals or intentions. For example, in the field of software engineering, the goal of commonly used Inversion of Control during the development process is to delegate key dependencies to specific containers for management and control through external means, reducing coupling [63].
4.1.6. Information (I) → Data (D)
In the Cognitive Space, Information is transformed into Data through semantic differentiation and contextual processing, thereby concretizing semantic content into a Data form. The semantic distinctions within the Information serve as the basis for generating specific Data, enabling a more precise representation of abstract concepts in a structured and quantifiable manner.
- Principle 10: Preliminary ActionBased on the differentiated content of Information semantics, specific datasets that may be required in the future can be generated in advance. For example, by collecting meteorological Information, agricultural Data models can be developed beforehand, such as generating Data on the projected impact of rainfall and temperature variations on crop yields [64]. This proactive approach provides robust Data support for agricultural decision making, enabling stakeholders to make informed choices based on predictive insights.
- Principle 22: Blessing in DisguiseNegative or anomalous elements within Information can be transformed into specific Data points for further analysis and decision making. For instance, by identifying anomalies in business operations, such as production delays, specific operational Data can be generated or retrieved to optimize production processes. This targeted approach enables a deeper understanding of underlying issues and supports the development of more effective strategies for process improvement and risk mitigation [65].
4.1.7. Information (I) → Information (I)
This phase discusses the process of refining and reorganizing Information to enhance its quality and utility. This process involves not only optimizing the Information itself but also improving its structure and presentation to facilitate better understanding and effective communication. The following are several TRIZ principles related to this transformation process and their specific applications:
- Principle 13: The Other Way RoundIn the transformation of Information to Information, principle 13 is mainly reflected in the reorganization of information flow or structure to promote a better understanding of complex concepts and more effective communication. For example, in the previous studies and improvement of business information flow [66,67], stakeholders were able to better understand and use corresponding workflows, which promoted business development and improved efficiency.
- Principle 17: Another DimensionThe cognitive subject can employ various forms of representation, such as charts and diagrams, to transform one type of differentiation into another, providing multiple perspectives and deeper insights into the Information. For example, in Data visualization, representing Information across different dimensions, such as through multidimensional scaling and graph visualizations, can help users better understand high-dimensional Data. A study on visualizing dimension coverage in exploratory analysis demonstrated that representing Data visually with multiple perspectives helps analysts form new questions and gain deeper insights into datasets [68]. In market research, combining bar charts and pie charts can enhance the analysis by offering different viewpoints on the same Data. For instance, visualizing research topics using a three-dimensional strategic diagram enabled researchers to gain a more nuanced understanding of interdisciplinary research areas and emerging trends [69]. This multi-faceted approach enhances the ability to analyze complex Data and facilitates more informed and strategic decision making.
4.1.8. Information (I) → Knowledge (K)
This process represents the cognitive subject’s transformation of structured Information semantics into organized Knowledge. It highlights the importance of transitioning from Information to Knowledge and the application of this Knowledge in new informational domains. This transformation is a fundamental aspect of constructing Knowledge semantics. Below are several TRIZ principles related to this transformation process and their specific applications:
- Principle 15: DynamismThe Information represents different semantics, and as information updates, the complete semantics corresponding to its knowledge represent our gradually clearer understanding of the world. Therefore, the transformation of information into knowledge represents the continuous expansion of the integrity of knowledge boundaries. And the dynamism of Principle 15 corresponds well to this point. For example, many studies on the prediction and characteristics of protein molecules are constantly expanding human understanding of the field of biomolecules [70,71]. In order to record such dynamics, researchers have constructed corresponding databases to record these dynamic changes [72].
- Principle 24: IntermediaryThis principle in the conversion refers to the use of frameworks or models to transform information into knowledge, serving as a bridge between raw information and structured understanding. For example, in the field of education, developing a curriculum as a framework to guide student learning can help integrate dispersed learning materials into a systematic knowledge system [73].
4.1.9. Information (I) → Wisdom (W)
This process involves integrating Information with ethical considerations, social values, and other factors to transform it into wise decisions within complex contexts. Wisdom is not merely a pathway for the realization of Information; it also requires the consideration of long-term objectives and multiple value judgments. This comprehensive approach ensures that decision making is guided by both practical insights and a deeper alignment with ethical and societal principles.
- Principle 23: FeedbackThrough feedback expressed through different semantic contents, we can assess the strengths and weaknesses of individuals or parts under similar conditions, and adjust or screen corresponding strategies or solutions accordingly. For example, in the scenario of autonomous driving, when facing multiple optimization objectives, researchers obtain the latest input information through feedback and choose the best driving strategy in a timely manner [74,75].
- Principle 32: Color ChangesWe extend the semantics of color to the realm of presentation, such as modifying the format or framing of Information to enhance the effectiveness of Wisdom-based communication. This approach, which may include storytelling or contextualization, makes the Information more engaging and impactful, thereby conveying it more effectively to the audience. For example, in marketing campaigns, communicating a product’s core values through a brand narrative, rather than simply listing its features, can create a deeper resonance with consumers [76].
4.1.10. Information (I) → Purpose (P)
Through the analysis and comprehension of Information semantics, specific goals and action purposes are generated based on the semantic differentiation of the Information. The transformation process from Information to Purpose involves extracting key semantic distinctions from the Information and formulating goal-oriented action plans. This process ensures that critical insights are translated into actionable strategies, aligning cognitive understanding with purposeful behavior.
- Principle 16: Partial or Excessive ActionsAdjust the level of effort in Information processing according to the specific requirements of the objective, ensuring that the Information is neither excessive nor insufficient. This means determining the scope and depth of Information collection and analysis based on the importance and required detail of the objective. For example, in software project management, if the goal is to evaluate the cost-effectiveness of a project, efforts should be focused on collecting Data directly related to costs and benefits, avoiding the collection of excessive unrelated Data to improve the efficiency and relevance of Information processing [77].
- Principle 32: Color ChangesWe extend the semantics of color to the realm of presentation. Modify the presentation of Information according to the objective to enhance the clarity and impact of Information transmission. This principle emphasizes the importance of presentation format, suggesting that Information should be expressed or visually represented in a way that better aligns with the needs of the target audience. For example, in corporate annual reports, to better convey the company’s performance and future outlook to shareholders, key financial Data can be presented using charts, timelines, and other visual tools to make the Information more intuitive and understandable [78,79,80].
4.1.11. Knowledge (K) → Data (D)
This process refers to the cognitive subject’s use of the completeness of Knowledge semantics to reverse-engineer or refine expressions, thereby generating Data points that support the Knowledge system. The transformation from Knowledge to Data typically involves extracting specific facts, metrics, and verification Data from structured Knowledge. This approach enables the precise representation and empirical validation of abstract Knowledge constructs, facilitating the alignment of theoretical frameworks with tangible, Data-driven evidence.
- Principle 8: Anti-weightWe have expanded the semantic content of this principle here, which is to achieve a solution to the problem through certain compensation methods. Therefore, in the conversion of knowledge to data, the idea of transforming complete content into consistent semantic content is often used in distributed processing. For example, in a distributed file system, to reduce the burden on a single storage system, complete content can be stored separately on each node through specific policies, which allows each node to undertake a small portion of the storage task, reducing the burden on individual nodes [81].
- Principle 9: Preliminary Anti-ActionUsing the completeness of knowledge semantics to filter out identical semantic content that does not belong to the knowledge system, in other words, the knowledge system pre-screens irrelevant data to ensure that only valuable data are collected and analyzed. This method not only improves data processing efficiency but also prevents irrelevant data from affecting the decision-making process. For example, before training an AI model, we need to preprocess the dataset in order to use our existing knowledge system to filter out data that do not match the actual situation.
- Principle 25: Self-serviceApply existing Knowledge systems to autonomously guide Data collection and processing, reducing the need for external intervention. For instance, in the design of intelligent sensor networks, pre-set algorithms can be used to automatically identify important Data streams and prioritize them, thereby optimizing resource allocation and enhancing the system’s adaptive capabilities [82,83].
- Principle 27: Cheap Short-living ObjectsData represent the same semantic content, and the conversion of knowledge to data through this principle represents the transformation from complex and complete to simple and lightweight. For example, in streaming media services, in order to reduce video content transmission time or bandwidth, service providers often use efficient video compression algorithms [84] to compress videos into smaller data formats while preserving semantic integrity as much as possible.
4.1.12. Knowledge (K) → Information (I)
By analyzing Knowledge nodes and their relationships, these elements are concretized into semantic content specific to a given context, thereby generating concrete Information. The transformation from Knowledge to Information typically involves simplifying and contextualizing complex Knowledge structures to meet the requirements of specific applications. This process may include extracting domain-specific Information from a Knowledge base or converting theoretical Knowledge into practical guidelines, ensuring that abstract concepts are translated into actionable insights tailored to particular scenarios.
- Principle 3: Local QualityThe key nodes and relationships within the Knowledge structure are concretized into Information content, aimed at addressing specific problems or application contexts. This process typically involves extracting critical components from the body of Knowledge and transforming them into actionable Information semantics that can be directly applied. By converting essential Knowledge elements into practical Information, this approach ensures that theoretical insights are effectively utilized in real-world scenarios. For example, in the field of software engineering, Domain-Driven Design [42] is one of the manifestations of local quality. Software development teams start from the business and abstract business knowledge into domain models to guide development. Through in-depth understanding and refinement of the domain, they can more accurately identify which parts need special attention and optimization in the business knowledge by reflecting different semantics. In addition, each subdomain under the DDD design can be independently designed and implemented. This modular design approach helps to concentrate resources and efforts on optimizing key modules, thereby improving the overall quality of the software system.
- Principle 13: The Other Way AroundGenerating specific Information content based on the inverse logical relationships within Knowledge is particularly useful in handling anomalies and reverse reasoning scenarios. This process involves reverse-analyzing causal relationships within the Knowledge base to produce Information that can explain or predict specific phenomena. For example, leveraging maintenance Knowledge to perform reverse reasoning can generate diagnostic Information about equipment failures, such as potential causes and corresponding solutions for a particular type of malfunction. This enables technical personnel to quickly identify the root cause of an issue, providing effective support in troubleshooting and decision making during equipment failures [85].
4.1.13. Knowledge (K) → Knowledge (K)
The transformation process emphasizes the targeted nature of Information processing, ensuring that the acquisition, analysis, and presentation of Information all serve specific objectives. The following are several TRIZ principles related to this transformation process and their specific applications:
- Principle 22: Blessing in DisguiseUtilize challenges or limitations in knowledge as opportunities to develop deeper understanding or new methods. This approach emphasizes the potential for breakthroughs in solving problems and obstacles, advancing knowledge through critical thinking and innovation. For example, in technological innovation, traditional file systems cannot meet business needs, and companies developed their own file systems [81,86]. Therefore, by exploring alternative solutions or developing new methods, they promote the progress of related technologies and expand people’s understanding of file systems.
- Principle 34: Discarding and RecoveringUpdate Knowledge by eliminating outdated concepts and incorporating new findings, maintaining a robust and up-to-date Knowledge base. This method underscores the importance of Knowledge renewal, retaining core Knowledge while continuously discarding obsolete parts and adding the latest research outcomes. For example, in medical education, with the release of new clinical research results, teaching content should be promptly updated by removing disproven theories and including the latest medical practices [87].
4.1.14. Knowledge (K) → Wisdom (W)
The cognitive subject integrates Knowledge with multiple factors, such as ethics and social values, to generate wise decisions that align with long-term goals and complex contexts. The transformation from Knowledge to Wisdom requires careful consideration of the practical applicability of Knowledge semantics and diverse value orientations. This process ensures that decision making not only leverages factual Knowledge but also aligns with broader ethical and societal principles, enabling the formulation of nuanced and contextually appropriate strategies.
- Principle 15: DynamismAllow Knowledge and Wisdom to co-evolve over time, adapting to new Information and changing contexts to maintain their relevance and effectiveness. This means that Knowledge and Wisdom should not be static but should continually update and develop in a changing environment. For instance, in medical research, as new discoveries emerge, existing treatment methods need to be constantly adjusted to align with the latest scientific understanding [88].
- Principle 40: Composite MaterialsWe extend the semantics of materials to analyze and transform Knowledge content. Combine diverse sources of Knowledge to develop a more nuanced and comprehensive form of Wisdom, integrating multiple perspectives and experiences. This approach highlights the importance of interdisciplinary Knowledge integration and cross-domain learning, where the fusion of Knowledge from different fields creates richer Wisdom. For example, in public policy making, integrating Knowledge from social sciences, economics, and ethics can lead to more comprehensive and sustainable policy measures [89,90].
4.1.15. Knowledge (K) → Purpose (P)
The transformation from Knowledge to Purpose emphasizes the dynamic interaction between Knowledge and objectives, ensuring that the accumulation and application of Knowledge better serve the strategic needs of organizations or individuals. The following are several TRIZ principles related to this transformation process and their specific applications:
- Principle 25: Self-serviceWe can leverage the completeness of knowledge semantics to construct goals that can be autonomously adjusted or redefined, allowing goal setting to exhibit flexibility and adaptability based on new insights. For example, Computer Vision-based object recognition algorithms [91,92] can find corresponding targets and recognize them based on the knowledge learned during training.
- Principle 31: Porous MaterialsWe will expand and extend the porous semantics. Therefore, this invention principle can be defined as maintaining the openness of objectives to the influx of new Knowledge, allowing goals to dynamically adjust and optimize as understanding evolves. This method emphasizes the plasticity and adaptability of objectives, ensuring that goals are continually updated as new Knowledge is acquired. For instance, in corporate strategic planning, regularly reviewing changes in the external environment and internal capabilities enables timely adjustments to the company’s development direction to respond to market changes [93].
- Principle 35: Parameter ChangesBy utilizing the semantic integrity of knowledge, parameters are adjusted to remain within the current knowledge system and improve the overall goal of the system, resulting in outputs that meet expectations [94].
4.1.16. Wisdom (W) → Data (D)
The process involves interpreting Data through Wisdom to gain profound insights, while also discussing how Wisdom can guide Data collection and interpretation. It requires not only a deep understanding of the Data itself but also the integration of experience and intuition to form a comprehensive cognition that transcends specific contexts. The following are several TRIZ principles closely related to this transformation process, along with their specific applications:
- Principle 6: UniversalityWisdom is the information content with values, which is used in this principle to standardize or define universal expressions or contents of the same semantics, and can also integrate multiple independent data points into a coherent understanding beyond individual cases. For example, in the media field, in order to reach a wider audience of people of different ages, educational backgrounds, etc., corresponding adjustments need to be made to the expression methods and channels of the displayed data [95].
- Principle 24: IntermediaryThe cognitive subject can employ Wisdom-driven models or frameworks to analyze Data, offering more refined and contextually relevant insights. For example, in social science research, psychological theoretical models can be applied to interpret survey results. By leveraging the value-driven processes inherent in Wisdom, these models facilitate a deeper exploration of the motivations behind individual behaviors and the social factors that influence them. This approach allows for a more comprehensive and nuanced understanding of complex human dynamics, enhancing the ability to generate meaningful and actionable conclusions [96].
- Principle 25: Self-serviceWisdom can guide Data collection and interpretation, enabling autonomous operations by the cognitive subject and reducing reliance on external guidance. This involves incorporating intelligent decision-making mechanisms into Data processing. For instance, in intelligent traffic management systems, historical traffic flow patterns and emergency response experiences can be utilized to automatically adjust traffic signal control strategies, thereby optimizing traffic flow. This approach enhances system responsiveness and efficiency by enabling adaptive, self-regulating decision-making processes [97].
- Principle 35: Parameter ChangesThe cognitive subject can adjust Data parameters based on insights derived from Wisdom to ensure that Data collection and analysis methods support deeper understanding. For example, in intelligent transportation management systems, historical traffic flow patterns and emergency response experience can be utilized to automatically adjust input parameters for traffic signal control, thereby optimizing traffic flow. This method improves the system’s responsiveness and efficiency by implementing an adaptive and self-regulating decision-making process [97].
4.1.17. Wisdom (W) → Information (I)
Transforming the semantic content of wise decisions into concrete Information expressions involves converting complex decision-making logic, ethical judgments, and other nuanced considerations into contextualized semantic Information that is accessible and easy to communicate. This conversion from Wisdom to Information ensures that sophisticated insights are articulated in a clear and comprehensible manner, facilitating effective dissemination and application across various contexts.
- Principle 16: Partial or Excessive ActionsThe cognitive subject can leverage Wisdom to determine appropriate Information processing methods, ensuring efficient resource allocation. This means that in handling Information, it is crucial to apply measures that correspond to the level of semantic differentiation. For instance, in corporate strategy development, Wisdom can guide which Information requires in-depth exploration based on market trend analysis and which content only needs a high-level overview, thus preventing resource waste or Information overload [98]. This approach optimizes the decision-making process by aligning the depth of Information analysis with strategic priorities and resource availability.
- Principle 22: Blessing in DisguiseLeveraging Wisdom to identify the deeper meanings or hidden value within Information semantics can transform potential problems into opportunities for insight. For example, when faced with negative customer feedback, a wise analysis might uncover new ways to improve products or services, turning challenges into a catalyst for innovation and enhancement. This proactive approach not only addresses immediate concerns but also contributes to long-term growth and development by converting setbacks into strategic advancements [99].
4.1.18. Wisdom (W) → Knowledge (K)
Transforming the principles, strategies, and values inherent in wise decisions into a systematically applicable Knowledge framework involves structuring and systematizing the abstract concepts found within Wisdom-based decision making. This process of converting Wisdom into Knowledge creates reusable Knowledge modules, enabling the consistent application of these insights across different scenarios and contexts. It ensures that the sophisticated understanding embedded in Wisdom is translated into a coherent and operational Knowledge system that can be effectively utilized and adapted for future decision-making processes.
- Principle 3: Local QualityThe cognitive subject transforms high-quality strategies derived from wise decision making in a specific domain into specialized Knowledge systems. For example, in healthcare management, Wisdom-based medical decisions—such as strategies for responding to pandemics—are translated into structured Knowledge systems for managing specific diseases. This may include Knowledge of the allocation of medical resources and patient management tailored to infectious diseases, thereby enabling a more systematic and effective approach to healthcare administration and crisis response [100].
- Principle 23: FeedbackUtilize experiential feedback to refine both Knowledge and Wisdom, enhancing understanding and decision-making abilities through the lessons learned from both successes and failures. This process emphasizes learning and reflection in practice, where continuous trial and error lead to the development of a more mature Knowledge system and wise judgment. For instance, researchers have drawn inspiration from the theory of evolution in nature, utilizing feedback and self-regulation in the process of biological evolution to abstract these theories into evolutionary algorithms for multi-objective optimization [101,102], achieving great success.
4.1.19. Wisdom (W) → Wisdom (W)
This process emphasizes the dynamic and adaptive nature of Wisdom, ensuring that it can effectively guide decision making in an ever-changing environment. The following are several TRIZ principles related to this transformation process and their specific applications:
- Principle 15: DynamismEnable Wisdom to adapt and evolve with changing circumstances, ensuring its continued relevance and effectiveness in guiding decisions. This means that Wisdom is not a static collection of Knowledge but requires adjustment in response to changes in the external environment. For example, in business management, leaders should continuously adjust their management philosophies and strategies in response to market changes and competitive dynamics to maintain the company’s competitiveness. Through dynamic adjustment, Wisdom can better address future uncertainties. Research has shown that businesses that adapt their strategies in response to competitive intensity and market dynamism tend to achieve better performance outcomes [103]. Similarly, a study on business model adaptation highlights how proactive adjustment to environmental threats can significantly improve business performance [104].
- Principle 34: Discarding and RecoveringAbandon outdated or ineffective Wisdom to make room for new insights, ensuring that Wisdom remains a dynamic and flexible cognitive asset. This means being willing to let go of perspectives or methods that are no longer applicable while accumulating new Knowledge. For example, in the field of software engineering, with the development of new technologies and methodologies, old theories and practices may become outdated, requiring timely updating of professional knowledge and abandoning outdated concepts and methods [105].
4.1.20. Wisdom (W) → Purpose (P)
In the Cognitive Space, strategic goals and action guidelines from Wisdom-based decision making can be concretized into target purposes, providing a clear direction for action. The transformation from Wisdom to Purpose involves extracting specific goals and actionable pathways from the broader strategic framework. This process ensures that abstract strategic objectives are translated into well-defined purposes and execution plans, thereby guiding decision-making processes with precise and goal-oriented directives.
- Principle 10: Preliminary ActionThis principle is reflected in the transformation from wisdom to Purpose by setting goals using valuable information content. For example, investment banks and asset management companies will establish market monitoring systems to adopt corresponding hedging strategies before financial market fluctuations occur, in order to avoid potential losses caused by future price fluctuations [106].
- Principle 15: DynamismCognitive subjects need to adjust or redefine their goals based on new values in order to maintain their relevance and effectiveness in a constantly changing environment. This principle emphasizes the dynamic adjustment of goals and suggests updating the original goals when new knowledge or experience arises to better align with the current context. For example, in the medical field, medical institutions need to adjust treatment goals in a timely manner based on factors such as the patient’s age, economic level, and other conditions to avoid unexpected situations [107].
- Principle 20: Continuity of Useful ActionThe cognitive subject transforms wisdom into corresponding intentions through appropriate strategies under limited conditions, enabling it to output reliable goals or effects. For example, for the auto drive system [74], in the context of limited input content and computing power, the Purpose output of the autonomous drive system needs to be aligned under human values [108], so that the decisions of the autonomous drive system output can always conform to human values.
- Principle 33: HomogeneityThe important concept of this invention principle is to transform multiple similar intelligences into consistent knowledge expressions, which can form a synergy and increase efficiency without causing additional side effects. For example, using the Semantic Web [109], adopting unified classification standards and annotation methods to form a consistent knowledge network facilitates the association and inference of knowledge.
- Principle 39: Inert AtmosphereWe extend the semantics of this principle to improve target output efficiency by reducing environmental interference, while also facilitating analysis of the resulting phenomena. This principle embodies the transformation from wisdom to Purpose in the DIKWP model. For example, in the field of computer science, containerization is a lightweight and portable way to configure computing environments. It packages applications and their required libraries, dependencies, and configuration files together, as the simplicity of the environment makes it easy to deploy on various hosts, with consistent performance and reduced testing time costs [110].
4.1.21. Purpose (P) → Data (D)
The cognitive subject transforms Purpose content into specific Data collection requirements and Data formats through goal-oriented analysis. This process of converting Purpose into Data involves translating the semantic content of expected objectives into concrete Data formats and collection plans. By aligning the intended goals with precise Data specifications, this transformation ensures that Data collection efforts are systematically guided to support the achievement of targeted outcomes.
- Principle 10: Preliminary ActionFuture Data collection plans and requirements can be proactively generated based on the content of purposes to ensure that the Data will meet the analytical needs of anticipated goals. In market analysis, for example, new Data collection strategies can be developed in advance based on market expansion purposes, such as gathering Information on emerging market trends and competitor activities. This approach ensures that Data acquisition is strategically aligned with the expected objectives, facilitating more effective analysis and informed decision making [111].
- Principle 19: Periodic ActionThe cognitive subject collects specific data based on periodic similar purposes for analysis or decision making in other aspects. In the context of the Internet of Things, sensors in the system collect status data of monitored devices every once in a while, which is used for the working status of each device [112].
- Principle 21: SkippingWhen facing problems caused by slow efficiency, in order to achieve rapid response, it is often necessary to preset corresponding strategies based on known experience. For example, in personalized recommendation systems, the system can directly recommend content of interest to users based on their preferences, without the need to collect a large amount of user behavior data for analysis first [113].
- Principle 23: FeedbackBased on the feedback mechanisms of the intended goals, supplementary and optimized Data can be generated to create datasets that more accurately align with the objectives. In user experience optimization, for instance, new Data collection requirements can be derived from user feedback to capture additional user behavior Information. This helps refine product design according to the intent of product improvements, ensuring that the Data collected support targeted enhancements and deliver a better user experience [114].
4.1.22. Purpose (P) → Information (I)
The cognitive subject transforms the content of purposes into specific expressions with distinct semantics through decomposition and contextualization. In other words, the conversion from Purpose to Information typically involves translating goals and strategies into semantic Information that is clear, comprehensible, and easy to disseminate. This process ensures that complex purposes are articulated in a way that facilitates understanding and effective communication across different contexts and audiences.
- Principle 6: UniversalityPurposes can be transformed into various reusable standardized Information templates, reflecting semantic differences through distinct, specific purposes. These templates can be adapted to suit different contexts and objectives, allowing for the effective communication of nuanced Information semantics across diverse scenarios [115]. This structured approach enhances the clarity and consistency of Information dissemination while ensuring alignment with varying goals and situational requirements.
4.1.23. Purpose (P) → Knowledge (K)
This transformation involves converting the purposes and action plans embedded within purposes into a structured Knowledge framework and logical system, thereby forming a comprehensive Knowledge base aligned with the intended objectives. The process of transforming Purpose into Knowledge requires concretizing the abstract aspects of the goals into actionable strategies and execution pathways. This ensures that the underlying purposes are systematically integrated into a cohesive and applicable Knowledge system that can be effectively utilized for decision making and implementation.
- Principle 2: Taking OutThe cognitive subject can extract the core goals and strategies from purposes to form independent Knowledge modules. These modules, containing comprehensive semantics, can be used to guide future actions. In corporate management, for instance, the core strategic purposes for company growth can be structured into Knowledge modules, such as market expansion strategies or brand development strategies, to support strategic implementation across various departments. This approach ensures that each department aligns its actions with the overarching strategic vision, facilitating coherent and coordinated organizational growth [116].
- Principle 15: DynamismIn risk management, transforming dynamic risk assessment purposes into a real-time, adaptive risk management Knowledge system is crucial. For instance, a large financial institution must navigate an ever-changing market environment and policy risks, such as macroeconomic fluctuations and international market uncertainties. Traditional static risk management strategies are no longer sufficient to meet the demands of rapidly evolving market conditions. It is essential to translate risk management purposes into a dynamic, continuously updated Knowledge framework that can effectively respond to emerging risks and challenges [19,117].
4.1.24. Purpose (P) → Wisdom (W)
This process integrates the content of purposes with multiple factors such as ethics and social values to form wise decisions that align with long-term objectives. The transformation from Purpose to Wisdom requires a comprehensive evaluation of the feasibility, ethical considerations, and impact on the overall system. It ensures that decisions are sustainable and balanced across multiple dimensions, supporting the long-term strategic vision while maintaining ethical integrity and systemic harmony.
- Principle 36: Phase TransitionsThe transformation from Purpose to wisdom is reflected in the principle that the cognitive subject forms wisdom beyond generalization through its subjective Purpose, that is, it can output value content beyond the general scope through limited resources under specific conditions. For example, when artificial neural networks were first proposed, they were just a simple computational model based on the concept of bionics. After decades of development, models based on artificial neural networks have been applied in various fields and have achieved excellent application results [118].
- Principle 40: Composite MaterialsWe have expanded the semantics of composite materials, transforming them into multidimensional objectives. The cognitive subject comprehensively considers the multidimensional goals embedded within the intentions—such as economic benefits and social responsibility—to generate wise decisions that balance the interests of all stakeholders. This holistic approach ensures that decision making is aligned with diverse objectives, facilitating sustainable and ethically sound outcomes. For example, when generating content for generative AI models, it is necessary to consider economic benefits, social responsibility, and compliance with human ethics and values, in order to avoid ethical and moral issues as much as possible [119]. However, fully considering the above content can construct different paths and solutions, promoting innovation in research related to generative AI.
4.1.25. Purpose (P) → Purpose (P)
This process emphasizes the dynamic adjustment and continuous optimization of purposes, ensuring their adaptability to the constantly changing internal and external environments. The following are several TRIZ principles related to this transformation process and their specific applications:
- Principle 1: SegmentationWhen the cognitive subject is processing purposes, if the purposes are complex or difficult to process at once, they can use principle 1 to transform the purposes into multiple sub-purposes for processing. For example, in software engineering, designers often need to divide software into various sub-functions or sub-modules, with each sub-function or sub-module completing a small part of the overall Purpose while maintaining the same Purpose for the whole [120].
- Principle 14: CircularityThe transformation of this principle between purposes is reflected in transforming the linear structure that emphasizes the relationship between purposes into a circular structure, where all purposes are executed in a cyclic order under certain conditions. For example, in the field of software engineering, CI (Continuous Integration) and CD (Continuous Delivery/Continuous Deployment) belong to the concept of DevOps [121], which refers to the transformation of manual intervention in a series of processes such as code building, testing, deployment, and infrastructure configuration in the traditional development process into automation. Using CI/CD, code can be automatically tested, delivered, and deployed after being modified by developers. Appropriate CI/CD pipelines can minimize computer downtime and enable faster code release [122].
- Principle 37: Thermal ExpansionWe have expanded this invention principle to include the concept of elasticity, which means that cognitive agents can construct more solutions by improving target elasticity. This principle can be verified through the transformation of wisdom into Purpose. In the cloud computing scenario, users can adjust the resources required for cloud computing by modifying static parameters or load levels according to their own business needs, while providers need to build an elastic cloud computing environment to meet users’ personalized needs [123].
- Principle 38: Strong OxidantsThe semantic content of Principle 38 has been expanded to include the use of various means to accelerate the process of achieving a certain goal. This principle is reflected in the transformation between intentions. In the field of computer hardware, specific algorithms are accelerated through dedicated processors or instruction sets to achieve fast output results and increase system throughput [124].
4.2. Cognitive Space Coverage Completeness Analysis
The analysis of Cognitive Space coverage completeness involves evaluating how comprehensively a problem-solving framework addresses the various cognitive processes required for effective innovation. In the context of the DIKWP model, Cognitive Space refers to the semantic transformation processes between the different elements in the DIKWSP framework. We utilize the interaction model, along with the mapping results from Section 4.1, to assess the extent to which the mapped TRIZ principles cover these dimensions. This evaluation helps identify areas where traditional TRIZ principles may fall short, as well as domains where the integration of DIKWP and TRIZ provides significant enhancement.
Based on the analysis of the mapping in Section 4.1, we constructed a matrix, as shown in Table 1, where the numbers in each cell represent the corresponding TRIZ inventive principle numbers. However, if we use DIKWP as the entry point, we can leverage the transformation process to map to the various TRIZ inventive principles. By employing a graph search-based approach, it becomes possible to identify the most suitable inventive principles. Figure 3 illustrates the number of alternative paths for innovation methods during the transformation between stages in the DIKWP model. The values and color intensity in each cell represent the number of TRIZ inventive principles applied during the transition from one stage to another. Darker colors indicate that more inventive principles are available for selection, which often suggests a higher degree of overlap or greater uncertainty in the transformation process. For instance, the transformation from Data to Data involves five TRIZ inventive principles, implying that multiple innovation methods can be employed, potentially leading to overlap or excessive branching of innovation pathways. The values and color gradients in each cell signify the number of TRIZ inventive principles applied during the transition from one stage to another. A darker shade implies a greater number of inventive principles used, which often indicates a more complex transformation process or one of higher importance. If a particular inventive principle identified through the search is not a suitable match, the internal transformations between DIKWP elements can still be explored to continue the search, and this process can be iteratively extended.

Table 1.
DIKWP element transformation corresponding to the TRIZ invention principle.
Figure 3.
This figure represents the heatmap matrix mapping between the DIKWP model and TRIZ inventive principles, where the numbers in the matrix indicate the number of covered TRIZ innovation methods.
5. Application of DIKWP-TRIZ
In this section, we conduct a comparative analysis of the usage and cognitive approaches of the TRIZ method and the DIKWP-TRIZ method through a straightforward case study. This case study aims to illustrate that the number of solutions generated by the TRIZ invention principles is influenced by the user’s problem interpretation and the completeness of parameter content within their Cognitive Space. Additionally, we discuss the differences between the two methods from the perspectives of Purpose-driven reasoning and parameter optimization, highlighting the distinct advantages of the DIKWP-TRIZ approach in enhancing problem-solving efficiency and adaptability.
Case: Directly entering the password to unlock can easily be stolen, and the unlocking method needs to be improved.
5.1. TRIZ Method
In this case, we used a 48-parameter contradiction matrix for analysis [27]. If we need to change password unlocking to biometric recognition or special device recognition, etc., the parameter that needs to be improved in this process is Security, and the parameter that prevents deterioration is Operability. The innovative solutions found in the contradiction matrix analysis table include principles 3, 10, 13, and 25, which correspond to Local Quality, Preliminary Action, The other way round, and Self-service, respectively. The parameters requiring improvement may lack completeness, and the effectiveness of solution searching heavily depends on the expertise of TRIZ users. This suggests that relying solely on the contradiction matrix to drive solution searches may not fully address the cognitive demands of users, necessitating more fundamental transformations and processes to enhance solution discovery. By integrating DIKWP-TRIZ, the problem-solving pathway is mapped as transformations between DIKWPs. This mapping aligns with the application of TRIZ’s invention principles, thereby alleviating cognitive load and reducing the complexity of user-driven reasoning to some extent.
5.2. DIKWP-TRIZ Method
The DIKWP model is utilized to analyze the objectives of the problem at hand. By ensuring the comprehensiveness of solutions for the targeted issue, congruent and divergent semantic elements are systematically organized and analyzed to identify potential areas for improvement. This analytical process culminates in the extraction of valuable insights, which are then presented as the solution to the identified DIKWP problem.
Building on the findings detailed in Section 4.1, the transformation methodologies between DIKWP entities involved in this process are systematically mapped to the TRIZ theory of inventive problem solving. This mapping not only deepens the understanding of the internal mechanisms underpinning the DIKWP model but also generates innovative approaches that provide both theoretical foundations and practical strategies for addressing the problem at hand. As a practical application, we first analyze the shared semantic characteristics in cases of password theft, including methods such as spying and keylogging. The representation of these shared semantic elements is as follows:
is the stealing method, which, as the same semantics, refers to the methods of spying and keyloggers. The idea to solve this problem is to improve the unlocking method to avoid theft methods in the same semantic situation mentioned above. Firstly, we need to convert data into a Purpose, which is to output the user’s password through the corresponding input operation,
where is the transformed Purpose, representing the consistent Purpose of all elements in . Then, for the input that satisfies :
where represents the same semantic representation of the stolen password.
After learning the main Purpose, we can adjust the output content in to be inconsistent with the original password content, that is, replace the unlocking method with other results that cannot be obtained through peeping or keyloggers as input content, among which biometric recognition, special device recognition, and other methods can avoid being obtained by elements in . This process converts the originally entered password into high-dimensional integrity input, which means that the integrity content cannot be directly obtained through the methods in , and also satisfies the goal of not being able to unlock directly through the process of all elements in . To meet this requirement, we need to transform the input data into knowledge,
where represents the integrity semantics used as unlock input and represents data with unlock semantics. This process refers to converting the unlocked input data content into complete knowledge content, so as to avoid being stolen by the method in during transmission.
In summary, based on the analysis method in Section 4.1, we compared the principles of TRIZ and DIKWP-TRIZ outputs in Table 2.

Table 2.
Comparison of invention principle output between TRIZ and DIKWP-TRIZ.
5.3. DIKWP-TRIZ Versus TRIZ
5.3.1. Traditional Framework of TRIZ and Its Limitations
In Table 3, the traditional TRIZ framework primarily focuses on physical contradictions, such as the trade-off between strength and weight, while it overlooks more abstract issues like cognition, semantics, and ethics. Moreover, TRIZ’s approach is grounded in handling known, well-defined contradictions within technical systems. Its efficacy diminishes when confronted with incomplete, inconsistent, or imprecise Data. TRIZ assumes an abundance of technical Data to analyze contradictions and apply its principles, making it more suited to optimizing known parameters rather than addressing problems characterized by uncertainty.

Table 3.
Comparative analysis of DIKWP-TRIZ and traditional TRIZ.
5.3.2. Purpose and Ethical Considerations
The DIKWP-TRIZ framework emphasizes the critical dimension of “Purpose”, positioning it as a cornerstone for addressing both technical challenges and broader ethical and societal considerations. As the foundation for advancing creative AI, DIKWP-TRIZ aspires to become a theoretical basis for fostering innovation while ensuring that the technological progress aligns with human values. This intentional incorporation of “Purpose” into the problem-solving process not only guides the creation of innovative solutions but also provides a robust mechanism for addressing ethical dilemmas in the process of invention and innovation. In the context of developing creative AI systems, where the alignment of technological advancements with human-centric values is paramount, DIKWP-TRIZ offers a pathway to integrate ethical reasoning into the innovation cycle. By grounding the framework in a Purpose-driven approach, it encourages a harmonious balance between technological progress and societal well-being, fostering a future where creative AI contributes to sustainable and ethical innovation.
6. Conclusions
In this paper, we proposed the DIKWP-TRIZ framework, which extends the traditional TRIZ methodology by incorporating the DIKWP model’s elements of Data, Information, Knowledge, Wisdom, and Purpose. This integration not only enhances the applicability of TRIZ to complex cognitive processes but also emphasizes the human-centric aspects of innovation, such as value orientation and ethical considerations. Through systematic mapping and the identification of overlapping principles, we have demonstrated how the DIKWP-TRIZ framework can provide a more structured and effective approach to problem solving in scenarios characterized by incompleteness, inconsistency, and imprecision. By differentiating and refining TRIZ principles within the DIKWP framework, we have laid the groundwork for a coherent application methodology that minimizes cognitive burden and maximizes innovation potential. The resulting methodology enables practitioners to systematically apply TRIZ principles to a wide range of cognitive transformations, ultimately facilitating the development of advanced decision-making systems and supporting the evolution of artificial consciousness. Future research will focus on comparative analysis between the DIKWP-TRIZ framework and traditional TRIZ, and extend the 3-N problems to 9-N (No-Complete, No-Inconsistent, No-Improved, No-Relevant, No-Redundant, No-Timely, No-Accurate, No-Accessible, No-Understandable) problems, examining their respective implementation paths and the complexity involved in achieving innovation. Additionally, another key aspect of future work will be to fundamentally change the way definitions are formed, utilizing fine semantic mathematics to help establish more seamless connections between Cognitive Space, Semantic Space, consciousness space, and Conceptual Space. By strengthening the mathematical processing of semantics, this approach will promote more precise and logical innovative results, minimizing ambiguity and uncertainty to the greatest extent possible. This analysis will provide deeper insights into the mechanisms by which DIKWP-TRIZ promotes more subtle and complex innovation processes. Finally, this line of inquiry will establish a solid foundation for constructing artificial consciousness systems based on the DIKWP-TRIZ methodology, advancing the state of the art in creative AI-driven innovation and cognitive modeling.
Author Contributions
Conceptualization, K.W. and Y.D.; methodology, K.W. and Y.D.; formal analysis, K.W.; writing—original draft, K.W.; writing—review and editing, Y.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research project was supported in part by the Hainan Province Key R&D Program (ZDYF2022GXJS007, ZDYF2022GXJS010), in part by the Application and Research on the Deep Integration of Production, Education and Research in Undergraduate Talent Cultivation Mode for DIKWP (J202406) and in part by the Hainan Province Health Science and Technology Innovation Joint Program (WSJK2024QN025).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article; further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A

Table A1.
TRIZ invention principles.
Table A1.
TRIZ invention principles.
| Number | Principle Name |
|---|---|
| Principle 1 | Segmentation |
| Principle 2 | Extraction |
| Principle 3 | Local Quality |
| Principle 4 | Asymmetry |
| Principle 5 | Merging |
| Principle 6 | Universality |
| Principle 7 | Nested Doll |
| Principle 8 | Anti-weight |
| Principle 9 | Preliminary Anti-Action |
| Principle 10 | Preliminary Action |
| Principle 11 | In-advance cushioning |
| Principle 12 | Equipotentiality |
| Principle 13 | The Other Way Round |
| Principle 14 | Circularity |
| Principle 15 | Dynamism |
| Principle 16 | Partial or Excessive Actions |
| Principle 17 | Another Dimension |
| Principle 18 | Mechanical vibration |
| Principle 19 | Periodic Action |
| Principle 20 | Continuity of Useful Action |
| Principle 21 | Skipping |
| Principle 22 | Blessing in Disguise |
| Principle 23 | Feedback |
| Principle 24 | Intermediary |
| Principle 25 | Self-service |
| Principle 26 | Copying |
| Principle 27 | Cheap Short-living Objects |
| Principle 28 | Mechanics Substitution |
| Principle 29 | Pneumatics and Hydraulics |
| Principle 30 | Flexible Shells and Thin Films |
| Principle 31 | Porous Materials |
| Principle 32 | Color Changes |
| Principle 33 | Homogeneity |
| Principle 34 | Discarding and Recovering |
| Principle 35 | Parameter Changes |
| Principle 36 | Phase Transitions |
| Principle 37 | Thermal Expansion |
| Principle 38 | Strong Oxidants |
| Principle 39 | Inert Atmosphere |
| Principle 40 | Composite Materials |
References
- Altshuller, G.S. 40 Principles: TRIZ Keys to Technical Innovation; Technical Innovation Center: Worcester, MA, USA, 1998. [Google Scholar]
- Altshuller, G.S. Creativity as an Exact Science; Gordon and Breach: New York, NY, USA, 1984; p. 228. [Google Scholar]
- Ungvari, S. TRIZ Within the Context of the Kano Model or Adding the Third Dimension to Quality. 1999. Available online: https://www.metodolog.ru/triz-journal/archives/1999/10/e/index.htm (accessed on 6 November 2024).
- Slocum, M.S.; Kermani, A.H. Case Study: Integrating TRIZ Into Six Sigma. 2006. Available online: https://the-trizjournal.com/innovation-methods/innovation-triz-theory-inventive-problem-solving/case-study-integrating-triz-six-sigma/ (accessed on 6 November 2024).
- Domb, E. QFD and Tips/Triz. 1998. Available online: https://the-trizjournal.com/qfd-tipstriz/ (accessed on 6 November 2024).
- Wang, F.K.; Chen, K.S. Applying Lean Six Sigma and TRIZ methodology in banking services. Total Qual. Manag. Bus. Excell. 2010, 21, 301–315. [Google Scholar] [CrossRef]
- Hajime Yamashina, T.I.; Kawada, H. Innovative product development process by integrating QFD and TRIZ. Int. J. Prod. Res. 2002, 40, 1031–1050. [Google Scholar] [CrossRef]
- Sire, P.; Haeffelé, G.; Dubois, S. TRIZ as a Tool to Develop a TRIZ Educational Method by Learning it. Procedia Eng. 2015, 131, 551–560. [Google Scholar] [CrossRef]
- Berdonosov, V. Concept of the TRIZ Evolutionary Approach in Education. Procedia Eng. 2015, 131, 721–730. [Google Scholar] [CrossRef]
- Dourson, S. The 40 Inventive Principles of TRIZ Applied to Finance. 2004. Available online: https://ivm.org.uk/wp-content/uploads/2022/11/40-P-Finance.pdf (accessed on 6 November 2024).
- Xu, M. Design and Implementation of Family Financial Risk Prevention System Based on TRIZ and Wireless Sensor Network. In Proceedings of the 2021 IEEE Conference on Telecommunications, Optics and Computer Science (TOCS), Shenyang, China, 10–11 December 2021; pp. 289–293. [Google Scholar] [CrossRef]
- Smith, C.W.; Vincent, J.F.V.; Mann, D.L. Systematic technology transfer from biology to engineering. Philos. Trans. R. Soc. Lond. Ser. Math. Phys. Eng. Sci. 2002, 360, 159–173. [Google Scholar] [CrossRef]
- Vincent, J.F. Deconstructing the design of a biological material. J. Theor. Biol. 2005, 236, 73–78. [Google Scholar] [CrossRef] [PubMed]
- Ilevbare, I.M.; Probert, D.; Phaal, R. A review of TRIZ, and its benefits and challenges in practice. Technovation 2013, 33, 30–37. [Google Scholar] [CrossRef]
- Chai, K.H.; Zhang, J.; Tan, K.C. A TRIZ-Based Method for New Service Design. J. Serv. Res. 2005, 8, 48–66. [Google Scholar] [CrossRef]
- Fan, K.; Duan, Y. Purpose Computation-Oriented Modeling and Transformation on DIKW Architecture; Springer International Publishing: Cham, Switzerland, 2022; pp. 45–63. [Google Scholar] [CrossRef]
- Mei, Y.; Duan, Y.; Chen, L.; Feng, Z.; Yu, L.; Guo, Z. Purpose Driven Disputation Modeling, Analysis and Resolution Based on DIKWP Graphs. In Proceedings of the 2022 IEEE 24th Int Conf on High Performance Computing & Communications; 8th Int Conf on Data Science & Systems; 20th Int Conf on Smart City; 8th Int Conf on Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Hainan, China, 18–20 December 2022; pp. 2118–2125. [Google Scholar] [CrossRef]
- Guo, Z.; Duan, Y.; Chen, L.; Zhuang, C.; Mei, Y. Purpose Driven DIKW Modeling and Analysis of Meteorology and Depression. In Proceedings of the 2022 IEEE 24th Int Conf on High Performance Computing & Communications; 8th Int Conf on Data Science & Systems; 20th Int Conf on Smart City; 8th Int Conf on Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Hainan, China, 18–20 December 2022; pp. 2126–2133. [Google Scholar] [CrossRef]
- Wu, K.; Duan, Y. Modeling and Resolving Uncertainty in DIKWP Model. Appl. Sci. 2024, 14, 4776. [Google Scholar] [CrossRef]
- Chella, A.; Manzotti, R. Artificial Consciousness. In Perception-Action Cycle: Models, Architectures, and Hardware; Cutsuridis, V., Hussain, A., Taylor, J.G., Eds.; Springer: New York, NY, USA, 2011; pp. 637–671. [Google Scholar] [CrossRef]
- Holland, O.; Gamez, D. Artificial Intelligence and Consciousness. In Encyclopedia of Consciousness; Banks, W.P., Ed.; Academic Press: Oxford, UK, 2009; pp. 37–45. [Google Scholar] [CrossRef]
- Jones, S. On the Evolution of Artificial Consciousness. In Proceedings of the Advances in Artificial Life; Kelemen, J., Sosík, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; pp. 427–431. [Google Scholar]
- Yucong Duan, S.G. Artificial Intelligence vs. Artificial Consciousness from the DIKWP Perspective. 2024. Available online: https://www.researchgate.net/publication/380073777_Artificial_Intelligence_vs_Artificial_Consciousness_from_the_DIKWP_Perspective (accessed on 16 November 2024).
- Wang, Y.; Duan, Y.; Wang, M.; Wei, J.; Zhuang, C.; Liu, Y. Resource Adjustment Processing on the DIKWP Artificial Consciousness Diagnostic System. In Proceedings of the 2023 IEEE International Conference on High Performance Computing & Communications, Data Science & Systems, Smart City & Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Melbourne, Australia, 17–21 December 2023; pp. 1075–1082. [Google Scholar] [CrossRef]
- Duan, Y.; Lu, Z.; Zhou, Z.; Sun, X.; Wu, J. Data privacy protection for edge computing of smart city in a DIKW architecture. Eng. Appl. Artif. Intell. 2019, 81, 323–335. [Google Scholar] [CrossRef]
- Mei, Y.; Duan, Y. The DIKWP (Data, Information, Knowledge, Wisdom, Purpose) Revolution: A New Horizon in Medical Dispute Resolution. Appl. Sci. 2024, 14, 3994. [Google Scholar] [CrossRef]
- Mann, D.; Dewulf, S.; Zusman, A. TRIZ Matrix2003. 2021. Available online: https://www.triz-consulting.de/wp-content/uploads/2021/09/matrix2003-eng_v4.pdf (accessed on 16 November 2024).
- Park, W.B.; Song, Y.W.; Kim, S.B.; Lee, K.H.; Hu, J.H. Considerations on the Smart Factory and the Use of TRIZ 40 Inventive Principles: Focusing on Site Improvements in the Field of Semiconductor Industry. Asia-Pac. J. Converg. Res. Interchange 2023, 9, 15–26. [Google Scholar] [CrossRef]
- Reusch, P.J.A.; Zadnepryanets, M. TRIZ 40 inventive principles application in project management. In Proceedings of the 2015 IEEE 8th International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Warsaw, Poland, 24–26 September 2015; Volume 2, pp. 521–526. [Google Scholar] [CrossRef]
- Kretzschmar, N.; Chekurov, S. The applicability of the 40 TRIZ principles in design for additive manufacturing. In Proceedings of the 29th DAAAM International Symposium, Zadar, Croatia, 24–27 October 2018; pp. 888–893. [Google Scholar] [CrossRef]
- Beckmann, H. Method for Transferring the 40 Inventive Principles to Information Technology and Software. Procedia Eng. 2015, 131, 993–1001. [Google Scholar] [CrossRef]
- Livotov, P.; Chandra Sekaran, A.P.; Mas’udah. Lower Abstraction Level of TRIZ Inventive Principles Improves Ideation Productivity of Engineering Students. In Proceedings of the New Opportunities for Innovation Breakthroughs for Developing Countries and Emerging Economies; Benmoussa, R., De Guio, R., Dubois, S., Koziołek, S., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 526–538. [Google Scholar]
- Gazem, N.; Rahman, A.A. Improving TRIZ 40 Inventive Principles Grouping in Redesign Service Approaches. Asian Soc. Sci. 2014, 10, 127–128. [Google Scholar] [CrossRef][Green Version]
- Liang, Y.; Tan, R.; Wang, C.; Li, Z. Computer-aided classification of patents oriented to TRIZ. In Proceedings of the 2009 IEEE International Conference on Industrial Engineering and Engineering Management, Hong Kong, China, 8–11 December 2009; pp. 2389–2393. [Google Scholar] [CrossRef]
- Yan, W.; Zanni-Merk, C.; Cavallucci, D.; Collet, P. An ontology-based approach for inventive problem solving. Eng. Appl. Artif. Intell. 2014, 27, 175–190. [Google Scholar] [CrossRef]
- Yan, W.; Liu, H.; Zanni-Merk, C.; Cavallucci, D. IngeniousTRIZ: An automatic ontology-based system for solving inventive problems. Knowl.-Based Syst. 2015, 75, 52–65. [Google Scholar] [CrossRef]
- Yang, Q.; neng Chen, W.; Gu, T.; Zhang, H.; Deng, J.D.; Li, Y.; Zhang, J. Segment-Based Predominant Learning Swarm Optimizer for Large-Scale Optimization. IEEE Trans. Cybern. 2017, 47, 2896–2910. [Google Scholar] [CrossRef]
- Liu, Z.; Kerr, B.; Dontcheva, M.; Grover, J.; Hoffman, M.; Wilson, A. CoreFlow: Extracting and Visualizing Branching Patterns from Event Sequences. Comput. Graph. Forum 2017, 36, 527–538. [Google Scholar] [CrossRef]
- Carter, G.; Galas, D.; Galitski, T. Maximal Extraction of Biological Information from Genetic Interaction Data. PLoS Comput. Biol. 2009, 5, e1000347. [Google Scholar] [CrossRef]
- Morrel-Samuels, P.; Francis, E.; Shucard, S. Merged Datasets: An Analytic Tool for Evidence-Based Management. Calif. Manag. Rev. 2009, 52, 120–139. [Google Scholar] [CrossRef]
- Milligan, G.W.; Cooper, M. A study of standardization of variables in cluster analysis. J. Classif. 1988, 5, 181–204. [Google Scholar] [CrossRef]
- Evans, E. Domain-Driven Design: Tackling Complexity in the Heart of Software; Addison-Wesley Professional: Boston, MA, USA, 2004. [Google Scholar]
- Dwork, C. Differential Privacy. In Proceedings of the Automata, Languages and Programming; Bugliesi, M., Preneel, B., Sassone, V., Wegener, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 1–12. [Google Scholar]
- Dong, J.; Roth, A.; Su, W.J. Gaussian differential privacy. J. R. Stat. Soc. Ser. (Stat. Methodol.) 2022, 84, 3–37. [Google Scholar] [CrossRef]
- Mystakidis, S. Metaverse. Encyclopedia 2022, 2, 486–497. [Google Scholar] [CrossRef]
- Ogburn, M.; Turner, C.; Dahal, P. Homomorphic Encryption. Procedia Comput. Sci. 2013, 20, 502–509. [Google Scholar] [CrossRef]
- Bettenburg, N.; Nagappan, M.; Hassan, A. Towards improving statistical modeling of software engineering data: Think locally, act globally! Empir. Softw. Eng. 2015, 20, 294–335. [Google Scholar] [CrossRef]
- Arrigo, E.; Liberati, C.; Mariani, P. Social Media Data and Users’ Preferences: A Statistical Analysis to Support Marketing Communication. Big Data Res. 2021, 24, 100189. [Google Scholar] [CrossRef]
- Liu, X.; Bourennane, S.; Fossati, C. Nonwhite Noise Reduction in Hyperspectral Images. IEEE Geosci. Remote. Sens. Lett. 2012, 9, 368–372. [Google Scholar] [CrossRef]
- Van Hulse, J.; Khoshgoftaar, T.M.; Napolitano, A. A Novel Noise Filtering Algorithm for Imbalanced Data. In Proceedings of the 2010 Ninth International Conference on Machine Learning and Applications, Washington, DC, USA, 12–14 December 2010; pp. 9–14. [Google Scholar] [CrossRef]
- Xiong, H.; Pandey, G.; Steinbach, M.; Kumar, V. Enhancing data analysis with noise removal. IEEE Trans. Knowl. Data Eng. 2006, 18, 304–319. [Google Scholar] [CrossRef]
- Ventocilla, E.; Riveiro, M. A comparative user study of visualization techniques for cluster analysis of multidimensional data sets. Inf. Vis. 2020, 19, 318–338. [Google Scholar] [CrossRef]
- Garouani, M.; Ahmad, A.; Bouneffa, M.; Hamlich, M.; Bourguin, G.; Lewandowski, A. Towards big industrial data mining through explainable automated machine learning. Int. J. Adv. Manuf. Technol. 2022, 120, 1169–1188. [Google Scholar] [CrossRef]
- Avramov, D.; Kaplanski, G.; Subrahmanyam, A. Moving average distance as a predictor of equity returns. Rev. Financ. Econ. 2021, 39, 127–145. [Google Scholar] [CrossRef]
- Ghobadi, S.; D’Ambra, J. Modeling High-Quality Knowledge Sharing in cross-functional software development teams. Inf. Process. Manag. 2013, 49, 138–157. [Google Scholar] [CrossRef]
- Jamshidian, F.; Zhu, Y. Scenario Simulation: Theory and methodology. Financ. Stoch. 1996, 1, 43–67. [Google Scholar] [CrossRef]
- Kuester, K.; Mittnik, S.; Paolella, M.S. Value-at-Risk Prediction: A Comparison of Alternative Strategies. J. Financ. Econom. 2005, 4, 53–89. [Google Scholar] [CrossRef]
- Neumann, T.; Ebendt, R.; Kuhns, G. From finance to ITS: Traffic data fusion based on Markowitz’ portfolio theory. J. Adv. Transp. 2016, 50, 145–164. [Google Scholar] [CrossRef]
- Wudhikarn, R. An efficient resource allocation in strategic management using a novel hybrid method. Manag. Decis. 2016, 54, 1702–1731. [Google Scholar] [CrossRef]
- Mohan, S.; Alam, M.F.; Fowler, J.; Gopalakrishnan, M.; Printezis, A. Capacity Planning and Allocation for Web-Based Applications. Decis. Sci. 2014, 45, 535–567. [Google Scholar] [CrossRef]
- Liu, T. Cross-Border Internet of Things E-Commerce Warehouse Control System Based on TRIZ Theory. Sci. Program. 2021, 2021, 2656508:1–2656508:10. [Google Scholar] [CrossRef]
- Sung, I.; Lee, T. Optimal allocation of emergency medical resources in a mass casualty incident: Patient prioritization by column generation. Eur. J. Oper. Res. 2016, 252, 623–634. [Google Scholar] [CrossRef]
- Sobernig, S.; Zdun, U. Inversion-of-control layer. In Proceedings of the 15th European Conference on Pattern Languages of Programs, Irsee, Germany, 7–11 July 2010; Association for Computing Machinery: New York, NY, USA, 2010. EuroPLoP ’10. p. 21. [Google Scholar] [CrossRef]
- Balducci, F.; Impedovo, D.; Pirlo, G. Machine Learning Applications on Agricultural Datasets for Smart Farm Enhancement. Machines 2018, 6, 38. [Google Scholar] [CrossRef]
- Gupta, N.; Anand, K.; Sureka, A. Pariket: Mining Business Process Logs for Root Cause Analysis of Anomalous Incidents. In Proceedings of the Databases in Networked Information Systems; Chu, W., Kikuchi, S., Bhalla, S., Eds.; Springer: Cham, Switzerland, 2015; pp. 244–263. [Google Scholar]
- Naticchia, B.; Corneli, A.; Carbonari, A. Framework based on building information modeling, mixed reality, and a cloud platform to support information flow in facility management. Front. Eng. Manag. 2020, 7, 131–141. [Google Scholar] [CrossRef]
- Racu, R.; Ernst, R. Scheduling Anomaly Detection and Optimization for Distributed Systems with Preemptive Task-Sets. In Proceedings of the 12th IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS’06), San Jose, CA, USA, 4–7 April 2006; pp. 325–334. [Google Scholar] [CrossRef]
- Sarvghad, A.; Tory, M.; Mahyar, N. Visualizing Dimension Coverage to Support Exploratory Analysis. IEEE Trans. Vis. Comput. Graph. 2017, 23, 21–30. [Google Scholar] [CrossRef]
- Feng, J.; Mu, X.; Wang, W.; Xu, Y. A topic analysis method based on a three-dimensional strategic diagram. J. Inf. Sci. 2020, 47, 770–782. [Google Scholar] [CrossRef]
- Senior, A.W.; Evans, R.; Jumper, J.; Kirkpatrick, J.; Sifre, L.; Green, T.; Qin, C.; Žídek, A.; Nelson, A.W.; Bridgland, A.; et al. Improved protein structure prediction using potentials from deep learning. Nature 2020, 577, 706–710. [Google Scholar] [CrossRef]
- Jumper, J.; Evans, R.; Pritzel, A.; Green, T.; Figurnov, M.; Ronneberger, O.; Tunyasuvunakool, K.; Bates, R.; Žídek, A.; Potapenko, A.; et al. Highly accurate protein structure prediction with AlphaFold. Nature 2021, 596, 583–589. [Google Scholar] [CrossRef]
- Varadi, M.; Bertoni, D.; Magana, P.; Paramval, U.; Pidruchna, I.; Radhakrishnan, M.; Tsenkov, M.; Nair, S.; Mirdita, M.; Yeo, J.; et al. AlphaFold Protein Structure Database in 2024: Providing structure coverage for over 214 million protein sequences. Nucleic Acids Res. 2023, 52, D368–D375. [Google Scholar] [CrossRef]
- Parke, H.M.; Coble, C.R. Teachers designing curriculum as professional development: A model for transformational science teaching. J. Res. Sci. Teach. 1997, 34, 773–789. [Google Scholar] [CrossRef]
- Yoo, S.W.; Kim, C.; Choi, J.; Kim, S.W.; Seo, S.W. GIN: Graph-Based Interaction-Aware Constraint Policy Optimization for Autonomous Driving. IEEE Robot. Autom. Lett. 2023, 8, 464–471. [Google Scholar] [CrossRef]
- Xu, Q.; Liu, Y.; Pan, J.; Wang, J.; Wang, J.; Li, K. Reachability Analysis Plus Satisfiability Modulo Theories: An Adversary-Proof Control Method for Connected and Autonomous Vehicles. IEEE Trans. Ind. Electron. 2023, 70, 2982–2992. [Google Scholar] [CrossRef]
- Zhang, Y.; Reynolds, M.; Lugmayr, A.; Damjanov, K.; Hassan, G.M. A Visual Data Storytelling Framework. Informatics 2022, 9, 73. [Google Scholar] [CrossRef]
- Mansor, Z.; Arshad, N.H.; Yahya, S.; Letchmunan, S. Validated agile cost management success factors in software development projects. Int. J. Adv. Intell. Paradig. 2018, 11, 5–18. [Google Scholar] [CrossRef]
- Kim, J.; Spence, M.T.; Marshall, R. The Color of Choice: The Influence of Presenting Product Information in Color on the Compromise Effect. J. Retail. 2018. [Google Scholar] [CrossRef]
- Cookson, R. Framing Effects in Public Goods Experiments. Exp. Econ. 2000, 3, 55–79. [Google Scholar] [CrossRef]
- Zouaoua, D.; Crubleau, P.; Mathieu, J.P.; Thiéblemont, R.; Richir, S. TRIZ and the difficulties in marketing management applications. In Proceedings of the PICMET 2010 Technology Management for Global Economic Growth, Phuket, Thailand, 18–22 July 2010; pp. 1–10. [Google Scholar]
- Ghemawat, S.; Gobioff, H.; Leung, S.T. The Google file system. In Proceedings of the Nineteenth ACM Symposium on Operating Systems Principles, Bolton Landing, NY, USA, 19–22 October 2003; pp. 29–43. [Google Scholar]
- Faigl, J.; Hollinger, G.A. Autonomous Data Collection Using a Self-Organizing Map. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 1703–1715. [Google Scholar] [CrossRef]
- Shah, K.; Francesco, M.D.; Kumar, M.J. Distributed resource management in wireless sensor networks using reinforcement learning. Wirel. Netw. 2013, 19, 705–724. [Google Scholar] [CrossRef]
- Chen, Y.; Murherjee, D.; Han, J.; Grange, A.; Xu, Y.; Liu, Z.; Parker, S.; Chen, C.; Su, H.; Joshi, U.; et al. An Overview of Core Coding Tools in the AV1 Video Codec. In Proceedings of the 2018 Picture Coding Symposium (PCS), San Francisco, CA, USA, 24–27 June 2018; pp. 41–45. [Google Scholar] [CrossRef]
- Zihui, W.; Rong, C. Research of the failure cause analysis and solving model based on TRIZ & AFD. In Proceedings of the 2010 International Conference On Computer Design and Applications, Qinhuangdao, China, 25–27 June 2010; Volume 5, pp. V5-617–V5-620. [Google Scholar] [CrossRef]
- Bonwick, J.; Ahrens, M.; Henson, V.; Maybee, M.; Shellenbaum, M. The zettabyte file system. In Proceedings of the 2nd Usenix Conference on File and Storage Technologies, San Francisco, CA, USA, 31 March–2 April 2003; Volume 215. [Google Scholar]
- Zhu, R.; Wang, Y.; Wu, R.; Meng, X.; Han, S.; Duan, Z. Trends in high-impact papers in nursing research published from 2008 to 2018: A web of science-based bibliometric analysis. J. Nurs. Manag. 2020, 28, 1041–1052. [Google Scholar] [CrossRef]
- Benton, M.L.; Abraham, A.; LaBella, A.L.; Abbot, P.; Rokas, A.; Capra, J.A. The influence of evolutionary history on human health and disease. Nat. Rev. Genet. 2021, 22, 269–283. [Google Scholar] [CrossRef]
- Hu, L.; Huang, W.b.; Bu, Y. Interdisciplinary research attracts greater attention from policy documents: Evidence from COVID-19. Humanit. Soc. Sci. Commun. 2024, 11, 383. [Google Scholar] [CrossRef]
- Petersen, A.M.; Ahmed, M.E.; Pavlidis, I. Grand challenges and emergent modes of convergence science. Humanit. Soc. Sci. Commun. 2021, 8, 194. [Google Scholar] [CrossRef]
- Jiang, P.; Ergu, D.; Liu, F.; Cai, Y.; Ma, B. A Review of Yolo Algorithm Developments. Procedia Comput. Sci. 2022, 199, 1066–1073. [Google Scholar] [CrossRef]
- Jiang, H.; Learned-Miller, E. Face Detection with the Faster R-CNN. In Proceedings of the 2017 12th IEEE International Conference on Automatic Face & Gesture Recognition (FG 2017), Washington, DC, USA, 30 May–3 June 2017; pp. 650–657. [Google Scholar] [CrossRef]
- Vidal, R.; Salmeron, J.L.; Mena-Nieto, A.; Chulvi, V. Fuzzy Cognitive Map-based selection of TRIZ (Theory of Inventive Problem Solving) trends for eco-innovation of ceramic industry products. J. Clean. Prod. 2015, 107, 202–214. [Google Scholar] [CrossRef]
- Yin, X.; Niu, Z.; He, Z.; Li, Z.; Lee, D. An integrated computational intelligence technique based operating parameters optimization scheme for quality improvement oriented process-manufacturing system. Comput. Ind. Eng. 2020, 140, 106284. [Google Scholar] [CrossRef]
- Meppelink, C.S.; van Weert, J.C.; Haven, C.J.; Smit, E.G. The Effectiveness of Health Animations in Audiences With Different Health Literacy Levels: An Experimental Study. J. Med. Internet Res. 2015, 17, e11. [Google Scholar] [CrossRef]
- Nezlek, J. Multilevel Random Coefficient Analyses of Event- and Interval-Contingent Data in Social and Personality Psychology Research. Personal. Soc. Psychol. Bull. 2001, 27, 771–785. [Google Scholar] [CrossRef]
- Hamidi, H.; Kamankesh, A. An approach to intelligent traffic management system using a multi-agent system. Int. J. Intell. Transp. Syst. Res. 2018, 16, 112–124. [Google Scholar] [CrossRef]
- Huang, Z.; Lu, X.; Duan, H. Mining association rules to support resource allocation in business process management. Expert Syst. Appl. 2011, 38, 9483–9490. [Google Scholar] [CrossRef]
- Jabbour, S.; El Mazouri, F.E.; Sais, L. Mining Negatives Association Rules Using Constraints. Procedia Comput. Sci. 2018, 127, 481–488. [Google Scholar] [CrossRef]
- Spanos, S.; Dammery, G.; Pagano, L.; Ellis, L.A.; Fisher, G.; Smith, C.L.; Foo, D.; Braithwaite, J. Learning health systems on the front lines to strengthen care against future pandemics and climate change: A rapid review. BMC Health Serv. Res. 2024, 24, 829. [Google Scholar] [CrossRef]
- Huang, L.; Suh, I.H.; Abraham, A. Dynamic multi-objective optimization based on membrane computing for control of time-varying unstable plants. Inf. Sci. 2011, 181, 2370–2391. [Google Scholar] [CrossRef]
- Zhao, J.; Zhang, H.; Yu, H.; Fei, H.; Huang, X.; Yang, Q. A many-objective evolutionary algorithm based on three states for solving many-objective optimization problem. Sci. Rep. 2024, 14, 19140. [Google Scholar] [CrossRef]
- Cui, A.; Griffith, D.; Cavusgil, T. The Influence of Competitive Intensity and Market Dynamism on Knowledge Management Capabilities of Multinational Corporation Subsidiaries. J. Int. Mark. 2005, 13, 32–53. [Google Scholar] [CrossRef]
- Saebi, T.; Lien, L.B.; Foss, N. What Drives Business Model Adaptation? The Impact of Opportunities, Threats and Strategic Orientation. Long Range Plan. 2017, 50, 567–581. [Google Scholar] [CrossRef]
- Cico, O.; Jaccheri, L.; Nguyen-Duc, A.; Zhang, H. Exploring the intersection between software industry and Software Engineering education—A systematic mapping of Software Engineering Trends. J. Syst. Softw. 2021, 172, 110736. [Google Scholar] [CrossRef]
- Jaramillo-Restrepo, J.; Jiménez-Gómez, M.; Acevedo-Prins, N. Stock portfolio hedging with financial options. Indones. J. Electr. Eng. Comput. Sci. 2020, 19, 1436–1443. [Google Scholar] [CrossRef]
- Mangoni, A.A. Comprehensive Geriatric Assessment and Personalized Medicine; Springer International Publishing: Cham, Switzerland, 2018; pp. 69–77. [Google Scholar] [CrossRef]
- Menon, C.; Alexander, R. A safety-case approach to the ethics of autonomous vehicles. Saf. Reliab. 2020, 39, 33–58. [Google Scholar] [CrossRef]
- Shadbolt, N.; Berners-Lee, T.; Hall, W. The Semantic Web Revisited. IEEE Intell. Syst. 2006, 21, 96–101. [Google Scholar] [CrossRef]
- Casalicchio, E.; Iannucci, S. The state-of-the-art in container technologies: Application, orchestration and security. Concurr. Comput. Pract. Exp. 2020, 32, e5668. [Google Scholar] [CrossRef]
- Lutz, C.; Bodendorf, F. Analyzing industry stakeholders using open-source competitive intelligence—A case study in the automotive supply industry. J. Enterp. Inf. Manag. 2020, 33, 579–599. [Google Scholar] [CrossRef]
- Amin, S.U.; Hossain, M.S.; Muhammad, G.; Alhussein, M.; Rahman, M.A. Cognitive Smart Healthcare for Pathology Detection and Monitoring. IEEE Access 2019, 7, 10745–10753. [Google Scholar] [CrossRef]
- Cao, B.; Zhao, J.; Lv, Z.; Yang, P. Diversified Personalized Recommendation Optimization Based on Mobile Data. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2133–2139. [Google Scholar] [CrossRef]
- Liang, L.; Ke, Y. User behavior data analysis and product design optimization algorithm based on deep learning. Int. J. Interact. Des. Manuf. (IJIDeM) 2023, 1–13. [Google Scholar] [CrossRef]
- de Mello, B.H.; Rigo, S.J.; da Costa, C.A.; da Rosa Righi, R.; Donida, B.; Bez, M.R.; Schunke, L.C. Semantic interoperability in health records standards: A systematic literature review. Health Technol. 2022, 12, 255–272. [Google Scholar] [CrossRef] [PubMed]
- Earl, M.J. Knowledge Management Strategies: Toward a Taxonomy. J. Manag. Inf. Syst. 2001, 18, 215–233. [Google Scholar] [CrossRef]
- Sun, J.; Li, H.; Adeli, H. Concept Drift-Oriented Adaptive and Dynamic Support Vector Machine Ensemble With Time Window in Corporate Financial Risk Prediction. IEEE Trans. Syst. Man Cybern. Syst. 2013, 43, 801–813. [Google Scholar] [CrossRef]
- Wu, Y.C.; Feng, J.W. Development and application of artificial neural network. Wirel. Pers. Commun. 2018, 102, 1645–1656. [Google Scholar] [CrossRef]
- Oniani, D.; Hilsman, J.; Peng, Y.; Poropatich, R.K.; Pamplin, J.C.; Legault, G.L.; Wang, Y. Adopting and expanding ethical principles for generative artificial intelligence from military to healthcare. NPJ Digit. Med. 2023, 6, 225. [Google Scholar] [CrossRef]
- Sackur, J.; Dehaene, S. The cognitive architecture for chaining of two mental operations. Cognition 2009, 111, 187–211. [Google Scholar] [CrossRef]
- Ebert, C.; Gallardo, G.; Hernantes, J.; Serrano, N. DevOps. IEEE Softw. 2016, 33, 94–100. [Google Scholar] [CrossRef]
- Mustyala, A. CI/CD Pipelines in Kubernetes: Accelerating Software Development and Deployment. EPH—Int. J. Sci. Eng. 2022, 8, 1–11. [Google Scholar]
- Barnawi, A.; Sakr, S.; Xiao, W.; Al-Barakati, A. The views, measurements and challenges of elasticity in the cloud: A review. Comput. Commun. 2020, 154, 111–117. [Google Scholar] [CrossRef]
- Wang, C.; Gong, L.; Jia, F.; Zhou, X. An FPGA Based Accelerator for Clustering Algorithms With Custom Instructions. IEEE Trans. Comput. 2021, 70, 725–732. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).