Research on Defect Detection Method for Composite Materials Based on Deep Learning Networks
Abstract
1. Introduction
- (1)
- We designed a lightweight and highly accurate model for rapidly classifying defects in composite images. The Ghost module extracts features from the input image, calculating a reduced number of parameters. The module utilizes feature map redundancy by employing convolutional operations to generate a segment of the feature map. This is then followed by linear operations to duplicate and enlarge the feature map, thereby reducing the computational load.
- (2)
- We introduce and improve the Efficient Channel Attention (ECA) mechanism. By incorporating the ECA module into the feature extraction process, distinct weights are assigned to each channel of the feature map. The channel-based attention mechanism enhances the accuracy of the model in pattern recognition.
2. Related Works
2.1. Convolutional Neural Network Architecture
2.2. Attention Mechanisms
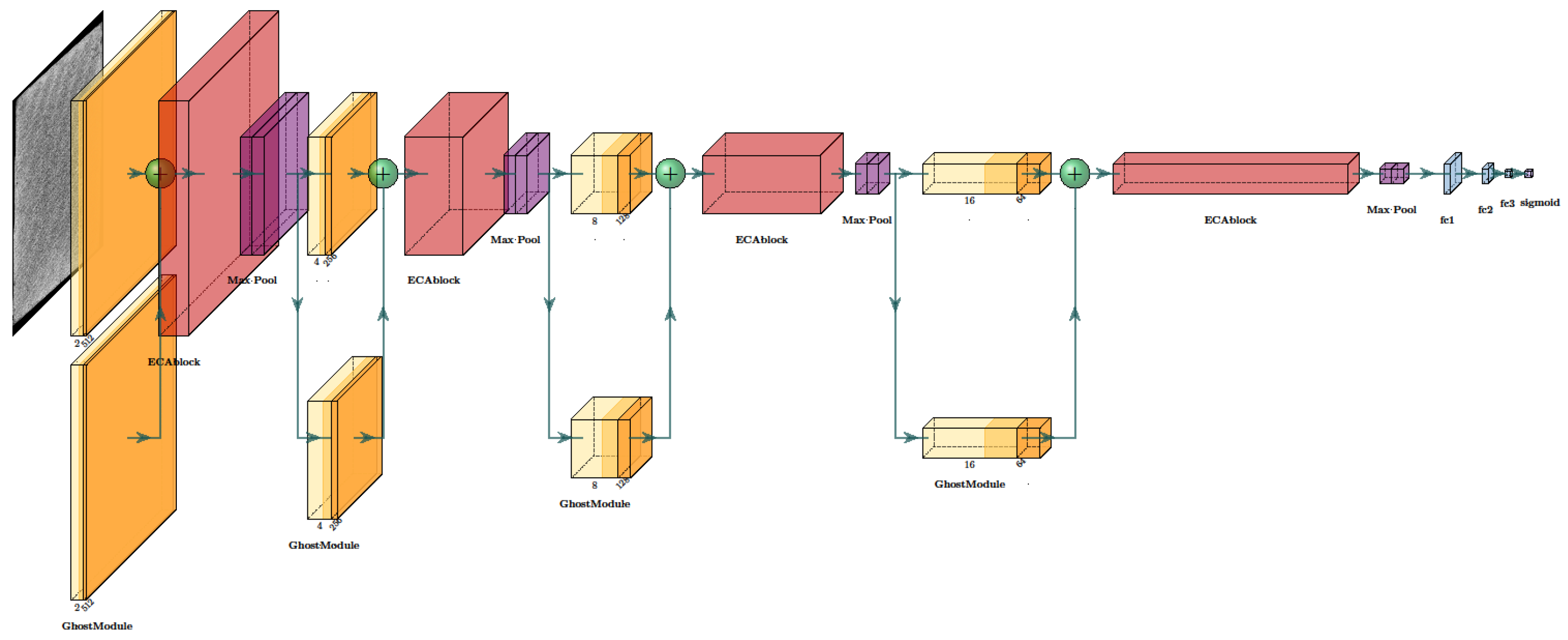
3. ECA Ghost CNN Method
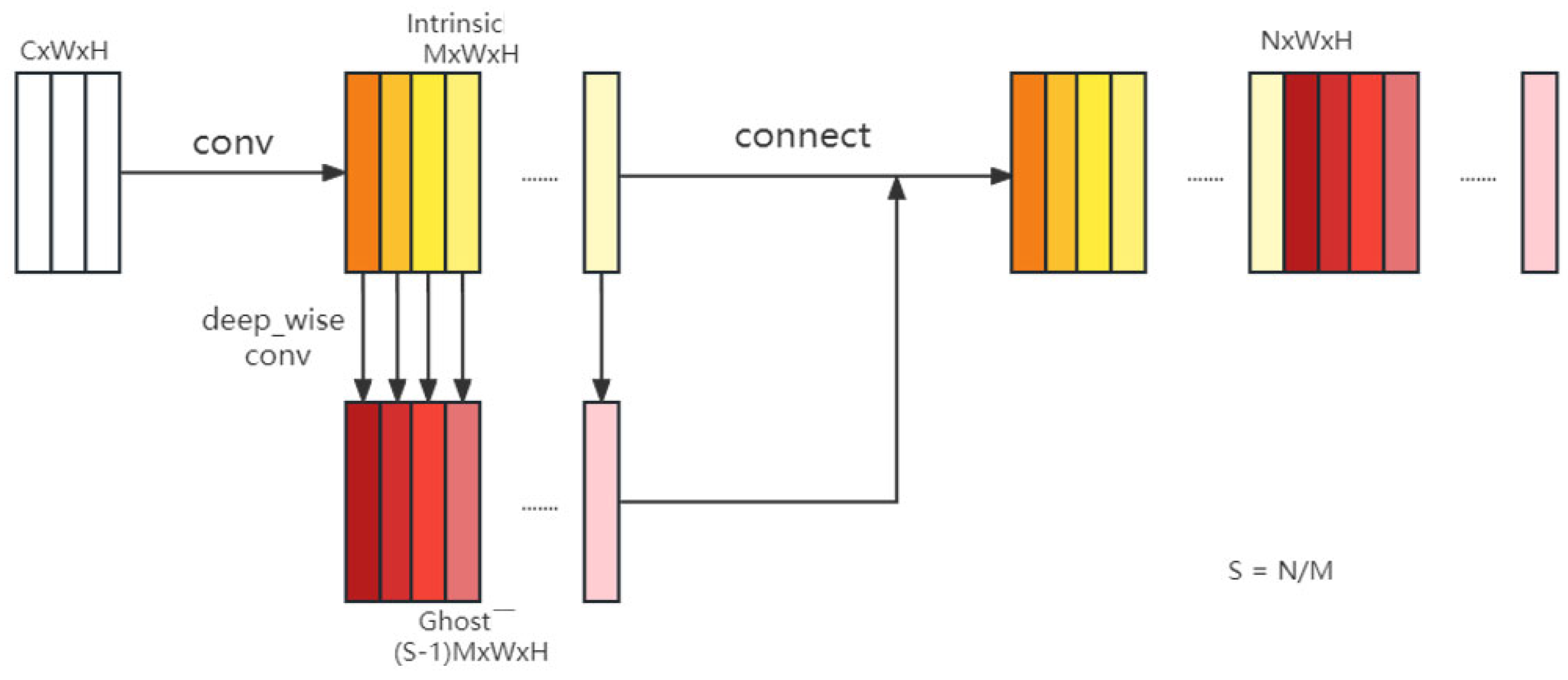
3.1. Ghost Module
3.2. Efficient Channel Attention Module
3.3. Fully Connected Layer and Loss Function
4. Results and Discussion
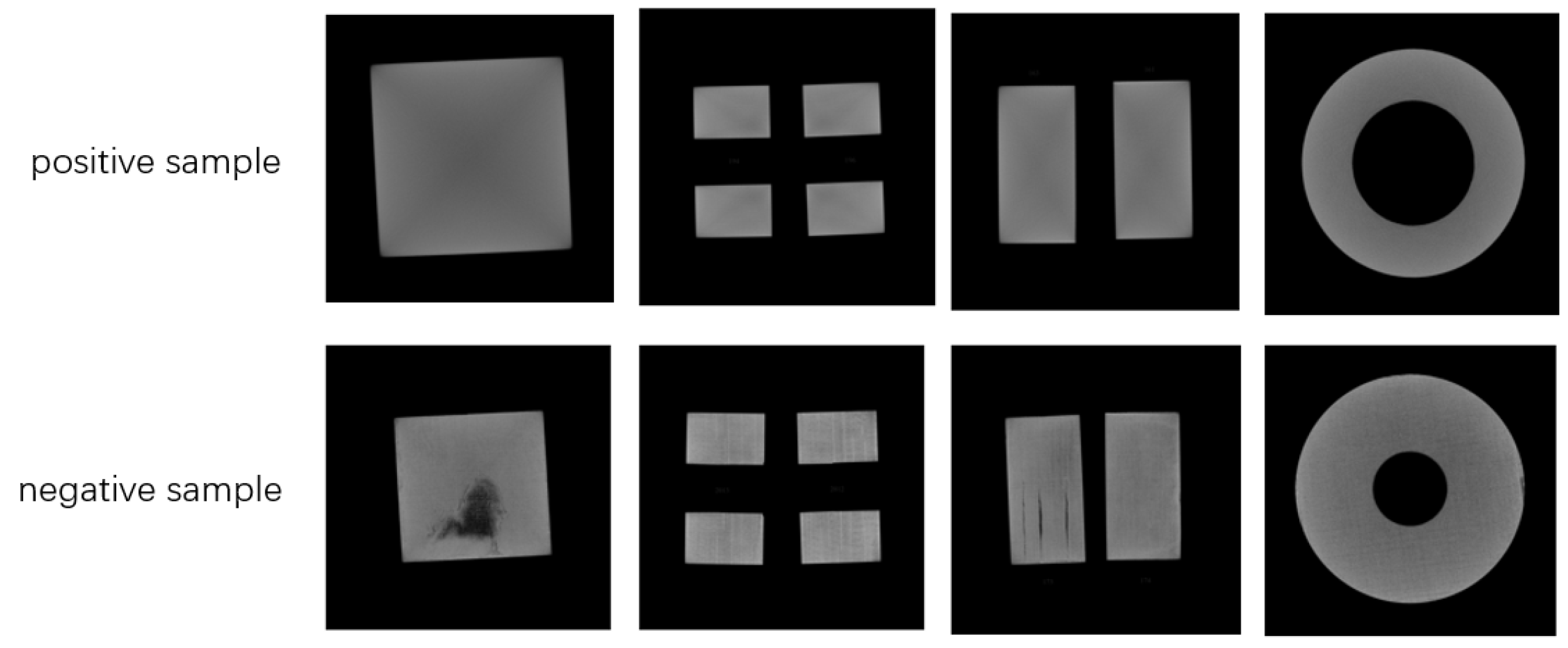
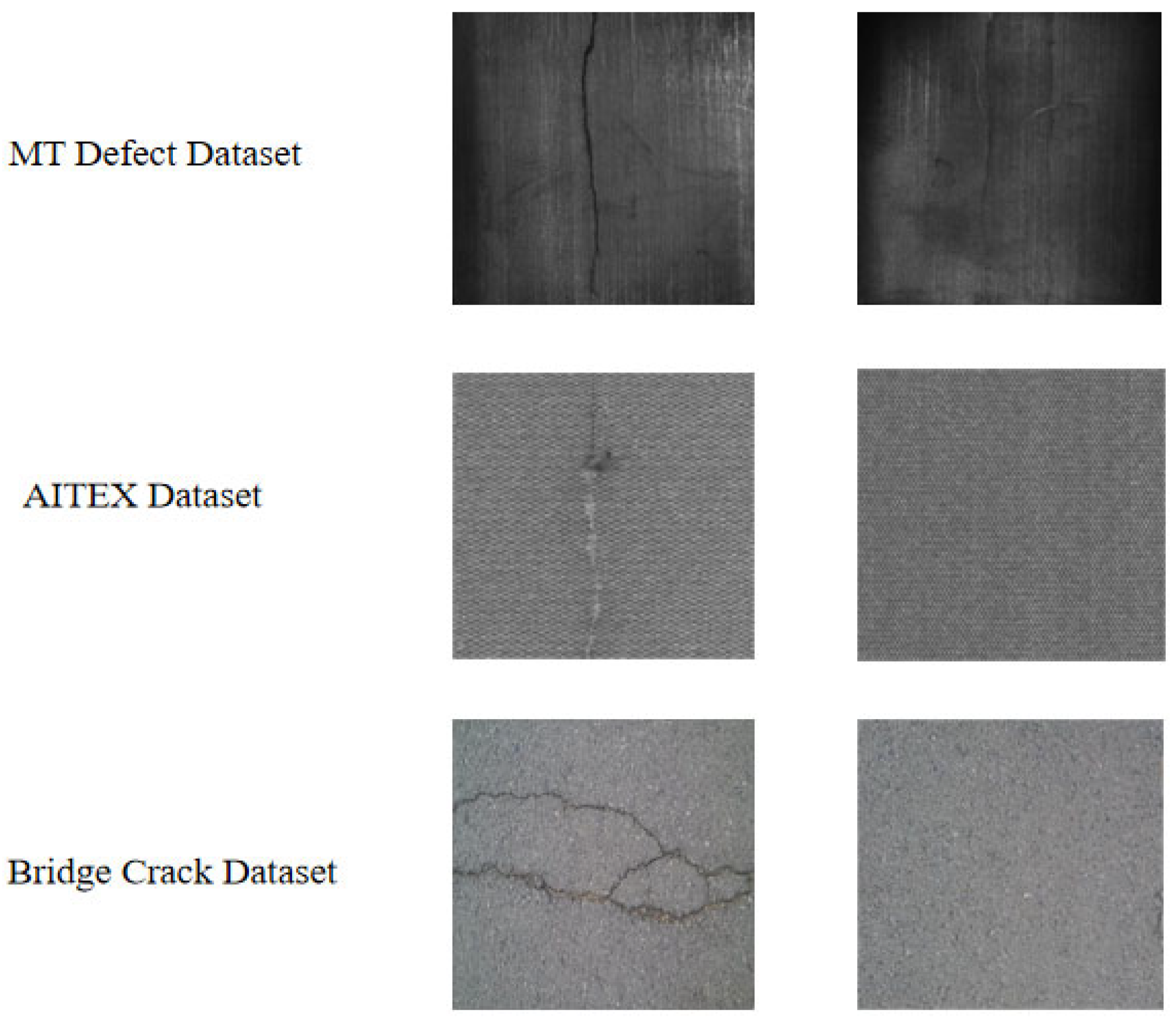
4.1. Datasets
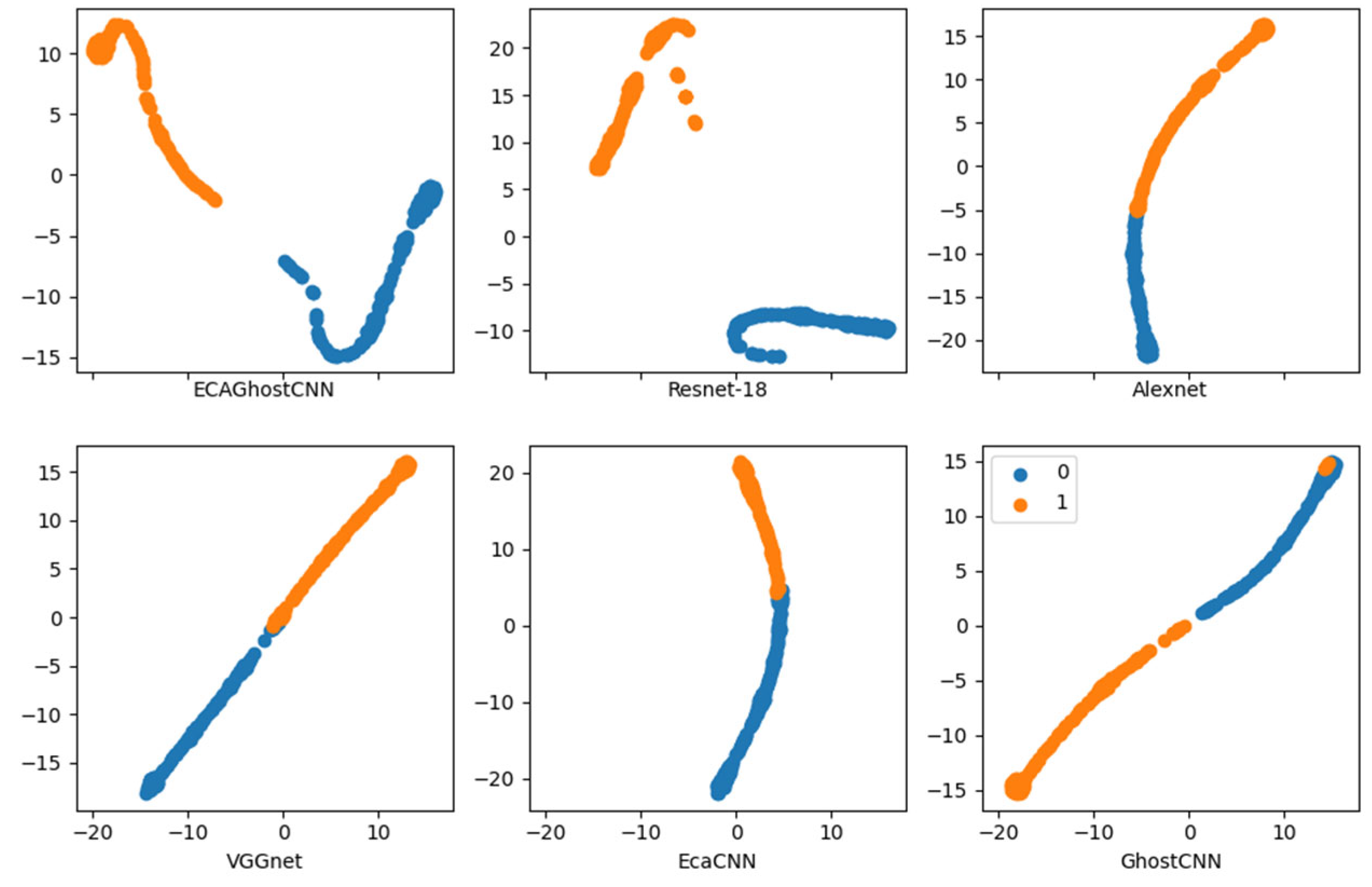
4.2. Comparison of Experimental Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mochizuki, Y.; Torii, A.; Imiya, A. N-Point Hough transform for line detection. J. Vis. Commun. Image Represent. 2009, 20, 242–253. [Google Scholar] [CrossRef]
- Bachofer, F.; Quénéhervé, G.; Zwiener, T.; Maerker, M.; Hochschild, V. Comparative analysis of Edge Detection techniques for SAR images. Eur. J. Remote Sens. 2016, 49, 205–224. [Google Scholar] [CrossRef]
- Ng, H. Automatic thresholding for defect detection. Pattern Recognit. Lett. 2006, 27, 1644–1649. [Google Scholar] [CrossRef]
- Stefan, K.; Petros, K. Simulations of optimized anguilliform swimming. J. Exp. Biol. 2006, 209, 4841–4857. [Google Scholar]
- Lin, H.; Du, P.; Zhao, C.; Shu, N. Edge detection method of remote sensing images based on mathematical morphology of multi-structure elements. Chin. Geogr. Sci. 2004, 14, 263–268. [Google Scholar] [CrossRef]
- Najar, F.; Bourouis, S.; Bouguila, N.; Belghith, S. A Comparison Between Different Gaussian-Based Mixture Models. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October 2017–3 November 2017. [Google Scholar]
- Li, S.; Lu, T.; Fang, L.; Jia, X.; Benediktsson, J. Probabilistic Fusion of Pixel-Level and Superpixel-Level Hyperspectral Image Classification. IEEE Trans. Geosci. Remote Sens. 2016, 54, 7416–7430. [Google Scholar] [CrossRef]
- Mortaza, M.; Akbar, A.; Ramin, R. Time-Frequency Analysis of EEG Signals and GLCM Features for Depth of Anesthesia Monitoring. Comput. Intell. Neurosci. 2021, 2021, 8430565. [Google Scholar]
- Ravikumar, S.; Ramachandran, K.I.; Sugumaran, V. Machine learning approach for automated visual inspection of machine components. Expert Syst. Appl. 2011, 38, 3260–3266. [Google Scholar] [CrossRef]
- Zhang, X.; Ding, Y.; Lv, Y.; Shi, A.; Liang, R. A vision inspection system for the surface defects of strongly reflected metal based on multi-class SVM. Expert Syst. Appl. 2011, 38, 5930–5939. [Google Scholar]
- Pathirage, C.S.N.; Li, J.; Li, L.; Hao, H.; Liu, W.; Ni, P. Structural damage identification based on autoencoder neural networks and deep learning. Eng. Struct. 2018, 172, 13–28. [Google Scholar] [CrossRef]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Spatial Pyramid Pooling in Deep Convolutional Networks for Visual Recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2015, 37, 1904–1916. [Google Scholar] [CrossRef] [PubMed]
- Hao, S.; Zhou, Y.; Guo, Y. A brief survey on semantic segmentation with deep learning. Neurocomputing 2020, 406, 302–321. [Google Scholar] [CrossRef]
- Xing, J.; Jia, M. A convolutional neural network-based method for workpiece surface defect detection. Measurement 2021, 176, 109185. [Google Scholar] [CrossRef]
- Lin, J.; Yao, Y.; Ma, L.; Wang, Y. Detection of a casting defect tracked by deep convolution neural network. Int. J. Adv. Manuf. Technol. 2018, 97, 573–581. [Google Scholar] [CrossRef]
- Wang, T.; Chen, Y.; Qiao, M.; Snoussi, H. A fast and robust convolutional neural network-based defect detection model in product quality control. Int. J. Adv. Manuf. Technol. 2018, 94, 3465–3471. [Google Scholar] [CrossRef]
- Cha, Y.J.; Choi, W.; Suh, G.; Mahmoudkhani, S.; Büyüköztürk, O. Autonomous Structural Visual Inspection Using Region-Based Deep Learning for Detecting Multiple Damage Types. Comput. Aided Civ. Infrastruct. Eng. 2018, 33, 731–747. [Google Scholar] [CrossRef]
- Jiao, L.; Zhang, F.; Liu, F.; Yang, S.; Li, L.; Feng, Z.; Qu, R. A Survey of Deep Learning-Based Object Detection. IEEE Access 2019, 7, 128837–128868. [Google Scholar] [CrossRef]
- Zhu, G.; Wei, Z.; Lin, F. An Object Detection Method Combining Multi-Level Feature Fusion and Region Channel Attention. IEEE Access 2021, 9, 25101–25109. [Google Scholar] [CrossRef]
- Liu, G.; Han, J.; Rong, W. Feedback-driven loss function for small object detection. Image Vis. Comput. 2021, 111, 104197. [Google Scholar] [CrossRef]
- Hu, J.; Shen, L.; Albanie, S.; Sun, G.; Wu, E. Squeeze-and-Excitation Networks. IEEE Trans. Pattern Anal. Mach. Intell. 2020, 42, 2011–2023. [Google Scholar] [CrossRef]
- Wang, Q.; Wu, B.; Zhu, P.; Li, P.; Zuo, W.; Hu, Q. ECA-Net: Efficient Channel Attention for Deep Convolutional Neural Networks. In Proceedings of the 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Seattle, WA, USA, 13–19 June 2020. [Google Scholar]
- Woo, S.; Park, J.; Lee, J.; Kweon, I. CBAM: Convolutional Block Attention Module. In European Conference on Computer Vision; Springer: Cham, Switzerland, 2018. [Google Scholar]
- Huang, Y.; Qiu, C.; Guo, Y.; Wang, X.; Yuan, K. Surface Defect Saliency of Magnetic Tile. In Proceedings of the 2018 IEEE 14th International Conference on Automation Science and Engineering (CASE), Munich, Germany, 20–24 August 2018. [Google Scholar]
- Zou, Q.; Zhang, Z.; Li, Q.; Qi, X.; Wang, Q.; Wang, S. DeepCrack: Learning Hierarchical Convolutional Features for Crack Detection. IEEE Trans. Image Process. 2019, 28, 1498–1512. [Google Scholar] [CrossRef] [PubMed]
- Protopapadakis, E.; Voulodimos, A.; Doulamis, A.; Doulamis, N.; Stathaki, T. Automatic crack detection for tunnel inspection using deep learning and heuristic image post-processing. Appl. Intell. 2019, 49, 2793–2806. [Google Scholar] [CrossRef]
- Zhao, X.; Dong, C.; Zhou, P.; Zhu, M.; Ren, J.; Chen, X. Detecting Surface Defects of Wind Tubine Blades Using an Alexnet Deep Learning Algorithm. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, E102.A, 1817–1824. [Google Scholar] [CrossRef]
- He, J.; Li, S.; Shen, J.; Liu, Y.; Wang, J.; Jin, P. Facial Expression Recognition Based on VGGNet Convolutional Neural Network. In Proceedings of the 2018 Chinese Automation Congress (CAC), Xi’an, China, 30 November 2018–2 December 2018. [Google Scholar]
- Li, M.; Tang, C. A hybrid training method based on deep learning for medical images classification. In Proceedings of the 2022 IEEE 5th International Conference on Information Systems and Computer Aided Education (ICISCAE), Dalian, China, 23–25 September 2022. [Google Scholar]
- Yacouby, R.; Axman, D. Probabilistic extension of precision, recall, and f1 score for more thorough evaluation of classification models. In Proceedings of the First Workshop on Evaluation and Comparison of NLP Systems; Association for Computational Linguistics: Stroudsburg, PA, USA, 2020; pp. 79–91. [Google Scholar]

| Model Name | Classification Accuracy |
|---|---|
| Alexnet [27] | 81.25% |
| VGGnet [28] | 80.00% |
| Resnet-18 [29] | 92.50% |
| ECAGhostCNN | 93.75% |
| Model Name | Running Time |
|---|---|
| Alexnet | 45.32 ms |
| VGGnet | 37.34 ms |
| Resnet-18 | 16.65 ms |
| ECAGhostCNN | 10.17 ms |
| Module Name | Model Size (#Params) | MAdd | FLOPs | MemR + W(B) |
|---|---|---|---|---|
| GhostModule 1 | 76 | 39,845,888.00 | 20,971,520.00 | 24,117,552 |
| ECAblock 1 | 1 | 0.00 | 0.00 | 0 |
| MaxPool 1 | 0 | 786,432.00 | 1,048,576.00 | 5,242,880 |
| GhostModule 2 | 452 | 59,244,544.00 | 30,146,560.00 | 12,584,720 |
| ECAblock 2 | 3 | 0.00 | 0.00 | 0 |
| MaxPool 2 | 0 | 393,216.00 | 524,288.00 | 2,621,440 |
| GhostModule 3 | 1704 | 55,836,672.00 | 28,180,480.00 | 6,298,272 |
| ECAblock 3 | 3 | 0.00 | 0.00 | 0 |
| MaxPool 3 | 0 | 196,608.00 | 262,144.00 | 1,310,720 |
| GhostModule 4 | 6608 | 54,132,736.00 | 27,197,440.00 | 3,172,160 |
| ECAblock 4 | 3 | 0.00 | 0.00 | 0 |
| MaxPool 4 | 0 | 98,304.00 | 131,072.00 | 655,360 |
| FC1 | 2,097,216 | 4,194,240.00 | 2,097,152.00 | 8,520,192 |
| FC2 | 2080 | 4064.00 | 2048.00 | 8704 |
| FC3 | 33 | 63.00 | 32.00 | 264 |
| Total | 2,108,179 | 214.73 M | 110.56 M | 61.54 |
| Model Name | Classification Accuracy | Average Runtime per Image |
|---|---|---|
| CNN | 71.25% | 19.98 ms |
| GhostCNN | 77.5% | 10.07 ms |
| CNN+PP [26] | 66.2% | 87 ms |
| ECACNN | 88.75% | 21.30 ms |
| Unet [25] | 90.21% | 166.7 ms |
| deepCrack [25] | 93.15% | 141 ms |
| MCuePushU [24] | 98.52% | 549 ms |
| ECAGhostCNN | 93.75% | 10.53 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cheng, J.; Tan, W.; Yuan, Y.; Zhao, Z.; Cheng, Y. Research on Defect Detection Method for Composite Materials Based on Deep Learning Networks. Appl. Sci. 2024, 14, 4161. https://doi.org/10.3390/app14104161
Cheng J, Tan W, Yuan Y, Zhao Z, Cheng Y. Research on Defect Detection Method for Composite Materials Based on Deep Learning Networks. Applied Sciences. 2024; 14(10):4161. https://doi.org/10.3390/app14104161
Chicago/Turabian StyleCheng, Jing, Wen Tan, Yuhao Yuan, Zirui Zhao, and Yuxiang Cheng. 2024. "Research on Defect Detection Method for Composite Materials Based on Deep Learning Networks" Applied Sciences 14, no. 10: 4161. https://doi.org/10.3390/app14104161
APA StyleCheng, J., Tan, W., Yuan, Y., Zhao, Z., & Cheng, Y. (2024). Research on Defect Detection Method for Composite Materials Based on Deep Learning Networks. Applied Sciences, 14(10), 4161. https://doi.org/10.3390/app14104161





